International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072
1Professor Department of CSE, BITM Ballari 2,3,4 Student Department of CSE, BITM Ballari ***
ABSTRACT - Cloud Computing is an evolution in computing with a rich family tree. Since the era of the mainframe the industry and computing has evolved in dramatic ways. The concept of cloud computing offers scalable resources dynamically as a service over the internet. The main economic benefits of cloud is that it offers low capital investment and low operational cost. Data security for cloud service encompasses several aspects including secure channels, access controls and encryption. The security in cloud will alternate from higher risk to lower risk and security controls has to be continuously reviewed to support the changes and evolving threat capabilities. There are many data protection approaches used to ensure maximum data protection by reducing risks and threats. The proposed system provides security to data in android devices and also in the cloud environment by adopting cryptographic techniques. We are proposing a simple system that encrypts and decrypts the text files to store and access through cloud. The proposed system enabled trains of information security like confidentiality, integrity and availability of data in cloud computing environment.
KEY WORDS: CloudComputing,cryptographictechniques, AES,Encryption,Decryption.
Virtual environment is a system that uses remote servers ontheinternettostore,manageandaccessthedataonline rather than local drives. Virtual storage is a system that has more memory which is used to store large or bulk data. Here data security is an important aspect. Cloud storageisanexampleofvirtualenvironment.Softwareand databasesrunsonthecloudserverwhichcanbeaccessed over internet. Thestorageandcomputingofdatadoesn’t takesplaceonthedeviceinsteadontheserversinthedata center, hence users can access data stored in cloud from anydevice.Dataprotectionincloudplaysamajorrole.Itis theprocessofsecuringdataincloudenvironmentwithout consideringanyfactorslikedatalocation,stateofdataand its management that may be internal or external by third party. Cloud computing is used for efficient and smooth
runningofbusinessalongwithinfrastructureandsoftware support to computing systems. Various fieldssuchasdata storage, education, entertainment, social networking as well as management have great uses of cloud computing. TherearemanymobileCloudComputingapplicationsthat do not even require a laptop or personal computer to be accessed from. Nowadays companies have moved from building and managing their own data center to storing data in the cloud. The sensitive data in the cloud environmenthostssecurityconcernslikedatabreach,data theft, application vulnerabilities and malware proliferation. Cloud security is a collection of security measures designed to protect the data that includes authentication of devices, access for data and resources. Vulnerabilities in cloud can be seen because of lack of cloud security awareness among operators, customers, managersortechnicalvulnerabilities.
Thesystem forimproving Cloudsecurityusing biometrics andencryption system collectsbiometricsample fromthe user at client side and applies minutiae algorithm that extracts features form biometric sample and verify it in clouddatabase.Ifverificationissuccessfulthesystemsend login request to server. The cloud authentication server randomlygeneratedOTP andthen encryptstheuserdata usingAdvancedEncryptionStandardandsendsencrypted data to user. Using OTP sent by server through HTTP gateway the user can decrypt or convert encrypted data intoreadableformatasmentionedin[1].
Data security in cloud computing is related to virtualization, storage in public cloud and multitenancy. Hypervisor a special function is required to run the OS as virtual machine and can become a primary target if vulnerable. If it gets compromised then whole system can be compromised and hence the data. Another risk in virtualization is the allocation and de allocation of resources. Usually Clouds implement centralized storage facilitieswhichcanbeappealingforhackers.Multitenancy is one of the major advantage as well as risk to data in
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072
cloud computing. Several authentication techniques are in use to avoid multitenancy issues. Data security in cloud involves more than encryption and depends upon SaaS, PaaSand IaaS.It is difficult toprotect the data at rest and issues arising due to data at rest can be resolved by maintainingaprivatecloudwithcontrolledaccess.Datain Transmit can be protected by various encryption strategiesasmentionedin[2].
Threats in cloud computing environment includes data breach, data loss, account or service traffic hijacking, insecure interface and API’s, malicious insiders, insufficientduediligence,sharedtechnologyvulnerability, lock inandacquisitionofcloudproviders.Attacksincloud environment includes denial of service, attack on hypervisor,resourcesfreeingattacks,sidechannelattacks andattacksonconfidentialityismentionedin[3].
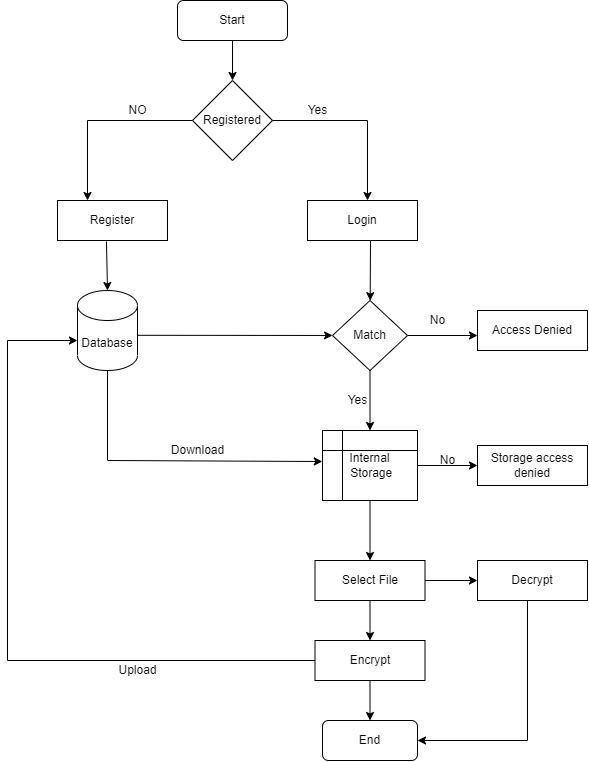
As mentioned in[4], the system has been split into four parts namely the system preparation process, Key Establishment Unit that is to the data owner, uploading data to public cloud and downloading data from public cloud. The data owner installs Cloud Management Client applicationthatencryptsdataprioruploadingthedataand decrypts after downloading it from public cloud. This eliminates the problem of data breach and key disclosure risks.
Registration: The application needs to identify the user to save their data in the cloud. To enable this, we use firebase authentication that provides backendservices.Customauthenticationoffirebase makes authentication easy for the users. The user hastoprovideusernameandsetanewpasswordto register for the first time. The password must contain minimum of 6 characters and has to be matched with confirmation field provided. As the userregisters the credentials will be stored in the firebasethathelpsforfuturelogin.Ifanyofthefield isleftemptyanappropriatetoastisdisplayedtothe user.Iftheuserisalreadyregistered,theycanmove directlytologinframebyclickingon'HaveAccount? Login'buttoninregisterpage.Registeredusercanbe checkedinthefirebaseconsole.
Login: It allows a user to gain access to the application when they enter validdetails. The login screen consists of two text fields one for entering username and other for password. If either of the text fields are empty then an appropriate error is displayed to the user. The registered user has to provide valid credentials for logging into the application. Otherwise, login will be failed. Only registered users can login in to the application. Whenanyoftheregistereduserforgetspasswordin thatcasetheapplicationprovidesawaytoresetthe password. When user clicks on 'forgot password' the application ask the user formail id and check thatuserinfirebase.Ifexistinguser,amailissentto respective user that contains a link to reset the password. After changing the password user can easilyloginintotheapplication.
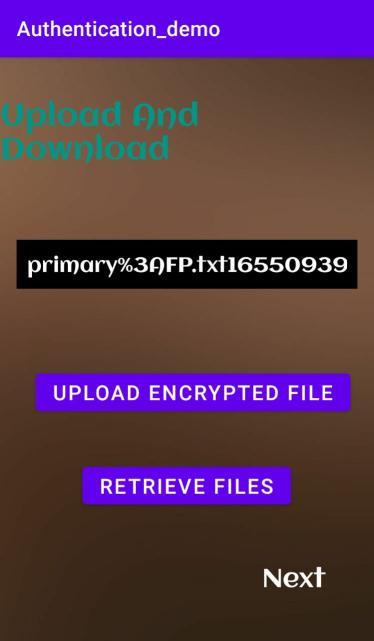
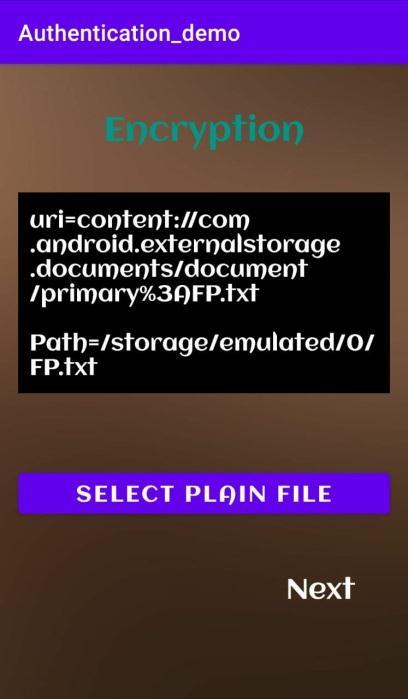
Encryption: After login, the user has to select the doc file to be encrypted. If the field is leftemptyan appropriatemessageisdisplayedtotheuser.Storage permissions need to be grantedby the user before selectingafilefrominternalstorage.AESalgorithm willbeappliedto selectedfileandencryptiontakes place. The encrypted file will be stored in the internalstoragewith.txtextension.
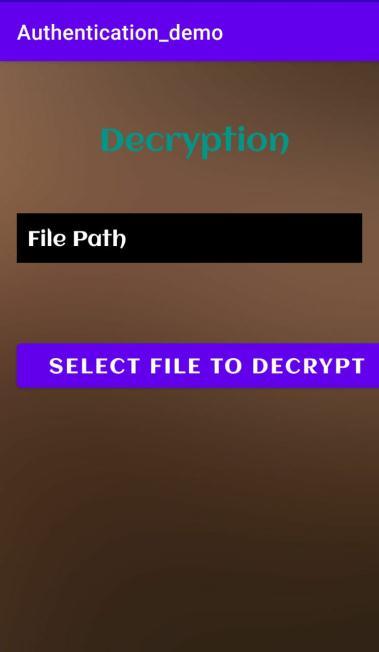
Decryption: Aftertheuserencryptsafile,ifthefile is to be decrypted then the user should select the required encrypted filefromthelist. AESalgorithm will be applied to the selectedfile and decryption takes place. The decrypted file will be stored in the internalstoragewith.txtextension.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072
Enhancing data security in cloud is the main concern and there are two distinct encryption methods like symmetric and assymetric techniques that provides a solution. Symmetric encryption method is also called as secret key algorithm or private key cryptography that requires sender and receiver to have access to a same key where bothhavetoensurethatkeyisstoredsecurely.Assymetric encryption technique is also called as public key cryptographythatusestwokeysforencryption(publicand private key). Public key is freely available to anyone, whereas the private key remains with the intended recipientsonly,whoneedittodecryptthemessage.
AES, RSA, Triple DES, Blowfish and Twofish are some of thecryptographicalgorithms.
The proposed system uses AES to ensure data security in virtualenvironment.
AES:TheAdvancedEncryptionStandard(AES)isatrusted standard algorithm that is extremely efficient in 128 bit form and also uses 192 and 256 bit keys for encryption purpose.Itisdefinedasgotostandardforencryptingdata inprivatesectorasitisinvulnerabletoalltypesofattacks exceptbruteforce.Eachcipherencryptsanddecryptsdata in blocksof128 bitsusingcryptographickeys of128,192 and256bits,respectively.Thereare10roundsfor128 bit keys,12roundsfor192 bitkeysand14roundsfor256 bit keys. One round consists of several steps that include substitution, transposition and mixing of the input plaintexttotransformitintofinalciphertext.Thefirststep intheAESencryptioncipherissubstitutionofdatausinga substitution table followed by shifts in data rows. The third step is concerned with mixing columns and the last transformation is performed on each column using a differentpartoftheencryptionkey.
Triple DES: Triple DES is a symmetric key block cipher that is successor to Data Encryption Standard (DES) algorithm which applies DES algorithm three times to everydatablock
RSA: RSAisapublic keyencryptionasymmetricalgorithm which was invented by Rivest, Shamir and Adleman. This algorithmisfrequentlyusedtosecureconnectionbetween VPN clients and servers as well as seen in web browsers, emailandothercommunicationmedium.
Blowfish: Blowfish is a symmetric key block cipher that was designed to replace DES. It was created by Bruce
Schneier that uses single encryption key to encrypt/decryptandprovidesagoodencryptionrate.
Twofish: Twofish is a successor to Blowfish which is a symmetric key block cipher with a block size of 128 bits and with a variable key length. It uses a single key that converts plain text to cipher text that cannot be understood before decoding. This algorithm uses pre computedandkeydependentsubstitutionboxes.
Fig4.1:Fingerprint

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056
Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN:2395 0072
Inafast pacedgrowingdigitalworlditiscrucialtoprotect digital information from manipulation and unauthorized access. Cloud is the latest technology that has immense benefits andthereareareasof concern related to security and privacy that are unanswered and open. In consequence, we are developing an application that provides security in cloud by using cryptography and authenticationtechniques.
1. Md. Alamgir Hossain & Md. Abdullah Al Hasan (2020):Improvingclouddatasecuritythroughhybrid verification technique based on biometrics and encryption system, International Journal of Computers and Applications, DOI: 10.1080/1206212X.2020.1809177
2. Albugmi,Ahmed&Alassafi,Madini&Walters,Robert & Wills, Gary. (2016). Data Security in Cloud Computing.10.1109/FGCT.2016.7605062.
3. E. Datta and N. Goyal, “Security attack mitigation framework for the cloud”, 2014 Reliability and Maintainability Symposium, 2014, pp. 1 6, doi: 10.1109/RAMS.2014.6798457.
4. Celiktas, Baris & Celikbilek, Ibrahim & Ozdemir, Enver. (2019). A Higher Level Security Protocol for Cloud Computing. 97 101. 10.1109/UBMK.2019.8907019.