International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Abstract - Previously, patient reports were submitted to hospitals in the form of documents. There will be more space to keep patient reports. When an old patient comes to the hospital, it takes a lot of time to find his document. Its total wastage of paper. The documentation report is not secure. anyone can destroy the document easily and can stop all this, we have come up with a new idea. It's called an E health cloud solution. Each patient report will save on the cloud. This Data will be safe and secure. It is accessible very easily Cloud computing is a new way of delivering computing resources and services Many managers and experts believe it has the potential to improve healthcare services, advance healthcare research, and transform health information technology. The information is critical for making decisions and providing the best possible care to patients. Cloud computing is a cost effective method for collecting, storing, and exchanging real time data between healthcare organizations. Cloud infrastructure is characterized by high throughput and large storage volumes, both of which are critical for effective data analysis of large patient populations. Security and sequestration are the major enterprises that are answered using pall grounded healthcare services. Data security continues to be one of the top enterprises for cloudcomputing, an issue that is been boosted by recent high profile attacks in healthcare. The encryption result has to be quick and easy to provision and give high situations of protection without immolating network performance. It's another way to give a critical subcaste of security to cover the guests. In this work, we're interested in data encryption in the healthcare pall. Authentication is the first step for data security, through which druggies can establish evidence of identity before data access from the system. In a pall computing terrain, conventional authentication styles don't give strong security against the moment's most ultramodern means of attack. Cloud needs a dynamic approach for stoner authentication, which should includemorethanoneauthenticationcredential. we propose a data security armature with a robust, dynamic, and doable Multi Factor Authentication scheme which integrates further than one factor like OTP for cloud stoner authentication.
Key Words: Health Care, Cloud Computing, AES Algorithm, Patient History Reports, MFA.
Inthisproject,thehospitalcanjustusetheservicesofthe cloud to upload patient data. In healthcare system can manage the administration and required IT requirements thathavethepotentialtoretrievethereal timeinformation of patients without any delay. The uploaded data we can accessthroughthecellularnetworkandremotedeviceswe cansharethemedicalhistoryofapatienthelpsdoctorsto treat a patient properly. The e health (electronic health) systemisoneofmanycloudservicesthatstoresandshares patientmedicaldatabetweenhealthcareserviceproviders andpatientsusingcomputerorelectronicsystemsandcloud technology. The health data/patient records are kept in a semi trusted third party supplier that is the cloud. Therefore,itssecurityhasbecomethemainconcernasthe datashouldnotbeaccessibletoanunauthorizedpersonTo remaincost effective,efficient,andtimelywhileproviding high quality services, health care, like any other service industry, requires continuous and systematic innovation. Manymanagersandexperts predictthatcloudcomputing can improve health care services, benefit healthcare research,andchangethefaceofinformationtechnology(IT). Several informatics breakthroughs have shown that cloud computinghasthepotentialtosolvetheseproblems.Despite the many benefits associated with cloud computing applications for health care, there are also management, technology,security,andlegalissuestobeaddressed.
Already, persistent reports were submitted to healing withintheframeofdifficultduplicatearchives.Therewillbe morespacetokeepunderstandingreports.Whenanancient persistentcomestotheclinic,ittakesapartofthetimeto discoverhisreport.Itaddsuptothewastageofpaper.The hardcopydocumentationreportisn'tsecure.Anybodycan annihilatethearchiveseffectively.Soanticipatethis,wehave comeupwithanideacalledanE healthcarecloudsolution. Each patient's report will spare on the cloud. In this, information will be secure and secure. It is available exceptionallyeffortlessly.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Duringawritingoverview,wegatheredaportionofthedata aboutthebasichealthcareapplicationandhowitworksasa system.
BigHealthApplicationSystembasedonHealthInternetof Things and Big Data. By using this paper, we got that the world is facing problems, such as uneven distribution of medical resources. This paper presents the big health operationsystemgroundedonthehealthInternetofeffects andbigdata.Thesystemarchitecture,keytechnologies,and typicalapplicationsofbighealthsystemareintroducedin detail.Itwillindicatecurrentstatusofhealthisfromhealth to low risk status, to high risk status of your health. To collectprimarymedicalservices,bighealthcouldusemobile medical health systems, big data, wearable devices, and a newgenerationofmobilecommunicationstechnology.This systemonlycollecttherealtimedataandprocessit.
3.2Survey on Internet of things for Smart Healthcare: Technologies, Challenges, and Opportunities.
Internet of Things for Smart Healthcare: Technologies, Challenges, and Opportunities. This check paper also presentsthestate of the artexplorationrelatingtoeach areaofthemodel,assessingtheirstrengths,sins,andoverall felicity for a wearable IoT healthcare system. Security, privacy, wearability, and low power operation are among the challenges that healthcare IoT faces, and recommendationsforfutureresearchdirectionsaremade. Themethodchosenmusthavenonegativeconsequencesfor the human body. This information should be sent to a database where it can be securely accessed by relevant parties(caretakersordoctors). Inthispaper,wefoundout thatthePreviouspatientdata/historycannotbestored.
Inthispaper,theyfocusedonanextensivereviewofcurrent and existing literatures of various approaches and mechanisms being used to handle security and privacy related matters in e Health Security and privacy requirements as recommended by Health Insurance PortabilityandAccountabilityActnwerealsodiscussedand provided. reflections and recommendations were made regarding the review process and unborn directions on securityandsequestrationofe Healthinpallcomputingwas alsohanded. Itprovides Highsecurity and privacy.Inthis limiteddatacanbestored.
Thispaperpresentsdevelopmentofsmarte healthsystem for Covid 19 epidemic. It's a smart Telemedicine system wherecasecanconsultwithcroakersstayingathomeThe doctorsarespecializedandhighlyprofessionalintheirfield. Websitehasblogandshopsitewheredoctorpostdifferent health issue to make awareness among the society and patientcanbuytheirmedicine.Inthispaperthedoctortreat patientthroughvideocalling.Thereisablogsystemwhere thearticleispublishedbydoctors.Itisamonitoringsystem sodatacan’tbesaved.
Examine the existing healthcare applications in order to developareliablesystemthatimprovestheconsistencyof patient doctorcommunication.Createareliablesystemfor storing patient data in the cloud. Using various network scenarios, evaluate the performance of proposed routing protocols. To overcome the drawbacks of existing applications,comparetheproposedhealthcareapplication. Datasecurityremainsoneofthemostpressingconcernsfor cloudcomputing,a problem thathasbeen exacerbated by recenthigh profileattacksinthehealthcareindustry.Oneof the most pressing concerns for cloud computing is data security,whichhasbeenexacerbatedbyrecenthigh profile attacksinthehealthcareindustry.Theencryptionsolution mustbesimpletosetupandprovidehighlevelsofsecurity withoutslowingdownnetworkperformance.It'syetanother way to protect clients by adding an additional layer of security.We'reinterestedindataencryptioninthecloudfor healthcare.Authenticationisthefirststepindatasecurity, allowinguserstoestablishproofofidentitybeforegaining accesstosystemdata.Traditionalauthenticationmethodsdo not provide strong security in the cloud computing environmentagainsttoday'smostmodernformsofattack. Asaresult,thecloudrequiresadynamicapproachtouser authentication that includes multiple authentication credentials.Weproposeadatasecurityarchitecturewitha Multi FactorAuthenticationschemethatintegratesmultiple factors such as OTP for cloud user authentication that is robust,dynamic,andfeasible.
TheAdvancedEncryptionStandard(AES)wascreated by the US National Institute of Standards and Technology (NIST) in 2001 as a specification for the encryption of electronicdata.Despitebeingmoredifficulttoimplement, AESiswidelyusedtodaybecauseitismuchstrongerthan DESandtriple DES.TheAEScypherisablockcypher.The keycanbe128,192,or256bitslong.Dataisencryptedin 128 bitblocks.SubBytes,ShiftRows,MixColumns,andAdd RoundKeyarethefourstepsineachround.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
1. Sub Bytes: This is where the substitution is put into action.Eachbyteisreplacedbyanotherbyteinthisstep.(A lookup table, also known as the S box, is used.) This substitutioniscarriedoutinsuchawaythatabyteisnever substitutedbyitself,norbyanotherbytethatcomplements thecurrentbyte.Asbefore,theresultofthisstepisa16byte (4x4matrix).Thepermutationisimplementedinthenext twosteps.
2. Shift Rows: Thisisexactlywhatitsoundslike.Acertain number of times each row is shifted. The first row isn't shiftedinanyway.Thesecondrowisshiftedtotheleftonce more.Thethirdrowhasbeenshiftedtothelefttwice.The fourthrowhasbeenshiftedthreetimes.
3. Mix Columns: This is where the matrix multiplication happens. Each column is multiplied by a specific matrix, resulting in a change in the position of each byte in the column.Inthefinalround,thisstepisskipped.
4. Add Round Keys: Thepreviousstage'sresultantoutput isXORedwiththecorrespondingroundkey.The16bytes arenotconsideredagridinthiscase,butrather128bitsof data.
Therounds'stagescanbeeasilyundonebecausetheyhave an opposite that, when performed, reverses the changes. Depending on the key size, every 128 blocks go through 10,12, or 14 rounds. The following are the stages of each roundofdecryption:InverseMixColumns,ShiftRows,and Inverse Sub Byte are all added to the round key. The encryptionanddecryptionprocessesareverysimilar.Itis carriedoutinthereverseorder.
1. Inverse Mix Columns: This step is similar to the Mix Columns step in encryption, but the matrix used in the operationisdifferent.
2. Inverse Sub Bytes: An inverse S box is a lookup table thatisusedtosubstitutebytesduringdecryption.
Inthesystemarchitectureweareimplementedsomepages asfollows,
6.1
WecreatedthehomepageusingHTMLandCSSlanguage anditisusedforoursystemdetailsandaccessingthelogin page.
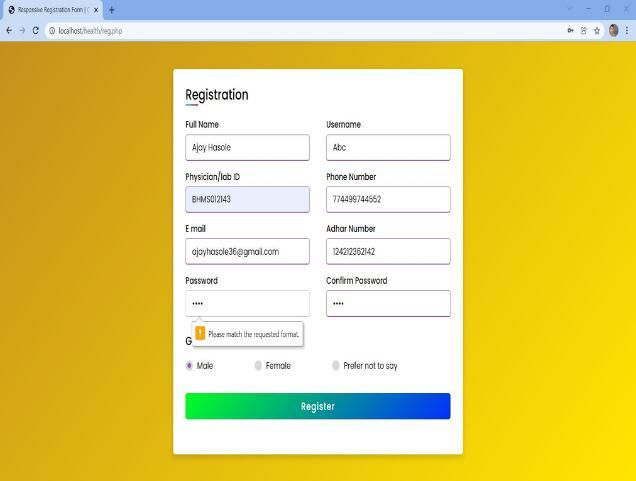
6.2 Registration page:
Thismoduleiscreatedforuserscancreatetheiraccount on the website for getting a username and password. To loginintooursystem.
6.3 Login page:
This page was created for accessing the system by the authorizeduserusingausernameandpassword.
6.4
Inthismodule,wecanstoretheuser'sdatainencrypted format in the database and retrieve data in decrypted format.
6.5 E mail confirmation:
It'susedafterregistrationusercangettheconfirmation mailforasuccessfullycreatedaccountinthesystemandget theusernameandpassword.
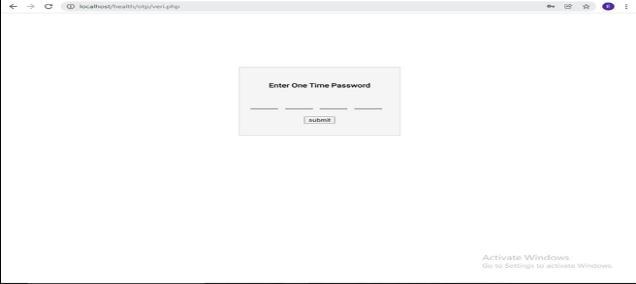
6.6 OTP authentication:
Weareprovidingmultifactorauthenticationforsecurity purposes.
Itisforaccesstothewebsite.Wegivethepatientlogin andPhysicianloginbuttons.Inthehomepagemodule,we give the doctor login and the patient login along with the contactus,aboutus.
7.2
In the Physician and patient registration module, a patientordoctorcreatestheiraccountontheE healthcloud
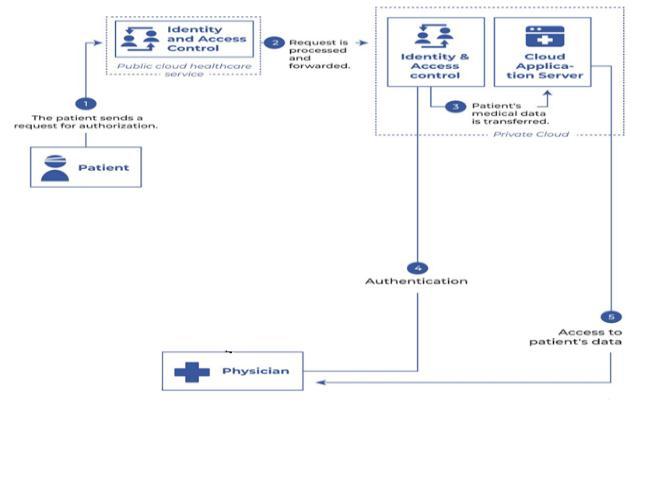
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

solutionwebsite.Tologinintoanaccount,auserhastogive their Aadhar number as a login id and give the password he/shegivesatthetimeofregistration.
Fig -2: RegistrationModule
Inthismodule,wecanstoretheuser'sdatainencrypted format in the database and retrieve data in decrypted format.
Physicians and patients can log in also using OTP. It's useful for quick login and it is also useful for when a user forgottheiridandpassword.
7.6
Weareusingthecloudservicetostorepatientdata.And it can access by an authorized person anywhere. In our project,weusedthegoodcloudservicewhichisAWScloud service. Particular amazon E3 is used because it gives 12 monthfreecloudstorageservices.
8.1
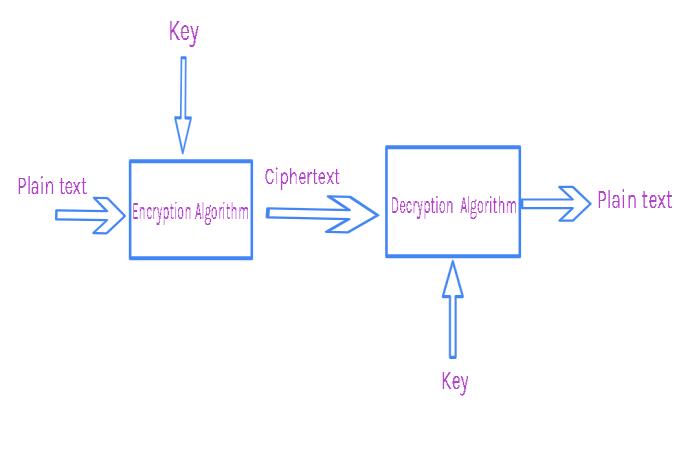
Plain text is sent by the sender for encryption and is encryptedusinganencryptionalgorithm.TheKeyisa128 bit block cipher key that is added to the plain text for encryption. The encryption algorithm is applied to the Sender side for encryption. The decryption algorithm is appliedtothereceiversidefordecryption.Theciphertextis an encrypted /converted plain text with a key using an encryptionalgorithm.
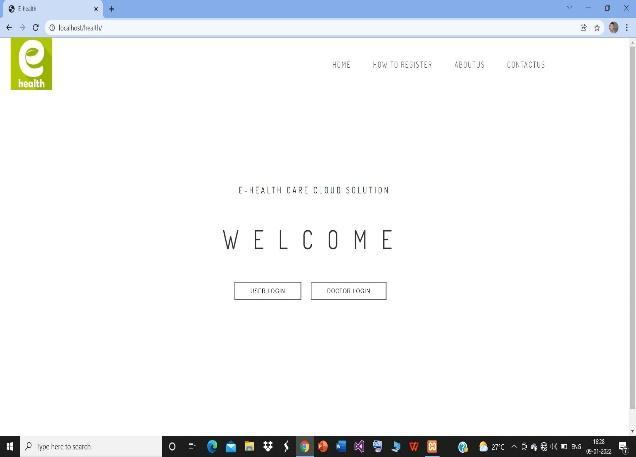
Physicians and patients can log in to the system using their idand password given byoursystem. The physician canstorethedataofthepatientinthecloud.Apatientonly readthedataintothesystem.
WecreatedahomepageusingHTMLandCSSlanguage anditisusedforoursystemdetailsandaccessingthelogin page.
Thismoduleiscreatedfortheusercancreatehisaccount on the website for getting a username and password. To loginintothesystem.
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
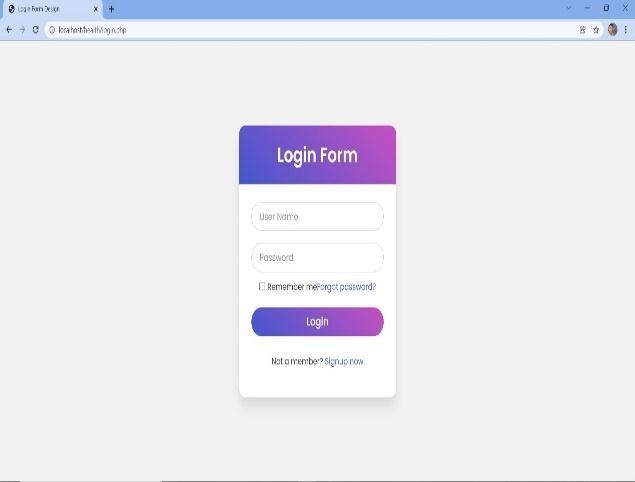

Thispagewascreatedforaccessingoursystemonlyfor theauthorizeduserusingausernameandpassword.
Fig 6: RegistrationForm
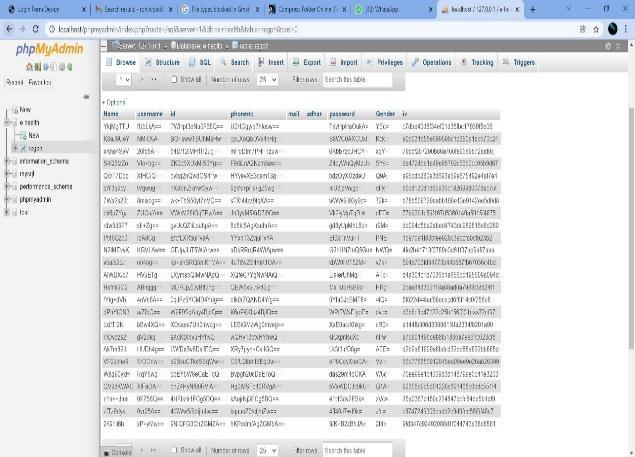
Inthismodule,wecanstoretheuser'sdatainencrypted format in the database and retrieve data in decrypted format.Inthisproject,aMySQLdatabaseisusedinthatthe PhpMyAdminadminpanelisusedforbetterperformance.
Fig -9: LoginForm
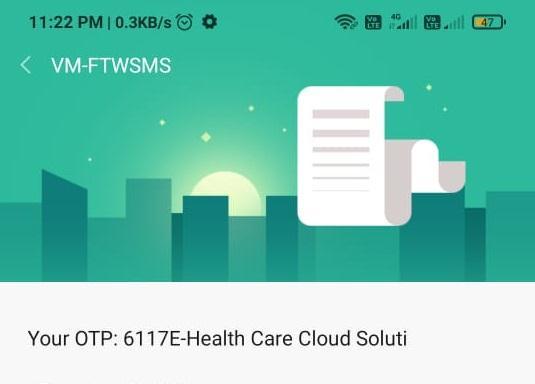
In the OTP generation module, we are providing multifactor authentication for security purposes. In OTP generationtheOTPisalwaysgeneratedwhentheuserwants tologintothesystem.WeusedtheFastSMSserviceforthe OTPgeneration.
Fig 7: DataBaseStoreEncrypteddata
It'susedafterregistrationusercangettheconfirmation mailforasuccessfullycreatedaccountinasystemandget theusernameandpassword.
Fig 10: OTPGeneration
Fig -8: RegistrationConfirmationMail
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Everybodyhastobewelleducatedandconcernedalmost the quality of care. Everybody implies patients and their families, shopper operators and advocates, wellbeing experts,chairmenofwellbeingplansandoffices,buyersof wellbeing care administrations, and policymakers at all levels.Themessagestothesegroupsofonlookersare1)that thequalityofcarecanbemeasuredandmade stridesand that quality of care thought to not be overlooked in the interestoffetchedcontrol.Fortifyingthesemessagesimplies makingbeyondanydoubtthatqualityofcareremainsonthe wellbeingcare deliverymotivation,withcleardistinguishing proofofthedangersandopeningsthatareposturedbythe changesinwellbeingcarewithintheJoinedtogetherStates. Itmoreoverimpliesportrayinghowwell beingplans,well being care organizations, and clinicians ought to be responsibletopatientsandsocietyand,ontheotherhand, how people can take suitable obligation for their claimed well being.
[1] BigHealthApplicationSystemBasedonHealthIoTs and Big Data. https://www.ieee.org.comY. Ma, Y. Zhang, J. Wan, D. Zhang, and N. Pan, Robot and cloud assisted multi modal healthcare system,'' ClusterCompute.
[2] Vinit Atul Shevade, D. A. Kulkarni: Redundancy PreventionandSecureAuditofEncryptedBigData in HDFS Cloud using Cloud Guard+ System. https://www.sciencepubco.com/
[3] IoTforSmartHealthcare:Technologies,Challenges, ,Opportunities.http://www.ieeeexplorer.ieee.org. inJ.Zhou,Z.Cao,X.Dong,andA.V.Vasilakos,Security andprivacyforcloud basedIoT:Challenges,''IEEE Communicate.
[4] Security and Privacy Preserving Challenges of e Health Solutions in Cloud http://www.engpaper.in/www.ieeepels.orgI.X.Yi, Y.Miao,E.Bertino,andJ.Williamson,``Multiparty privacyprotectionforelectronichealthrecords,''in Proc.IEEEGlobalCommunicate.
[5] Development of Smart e Health System for Covid19pendamic.http://www.ieeecas.org.in/www. ieeemce.org.
[6] Y.Zhang,M.Chen,S.Mao,L.Hu,andV.Leung,CAP: Community activity prediction based on big data analysis, IEEE Netw, vol. 28, no. 4, pp. 52 57, Jul./Aug.2014.
[7] J. Wang, Y. Zhang, J. Wang, Y. Ma, and M. Chen, „PWDGR:Pair wisedirectionalgeographicalrouting basedon wirelesssensornetwork,‟IEEEInternet ThingsJ.,vol.2,no.1,pp.14 22,Feb.2015.
[8] D.V.Dimitrov,„MedicalInternetofThingsandbig datainhealthcare,‟HealthcareInform.Res.,vol.22, no. 3, pp. 156 163, Jul2016.[Online].Availablehttp://ww.ncbi.nlm.nih.g ov/pmc/articles/PMC4981575.
[9] Y.J.Fan,Y.H.Yin,L.D.Xu,Y.Zeng,andF.Wu,„IoT basedsmartrehabilitationsystem,‟IEEETrans.Ind. Informat.,vol.10,no.2,pp.1568 1577,May2014.
[10] PolisenaJ,CoyleD,CoyleK,McGillS(2009)Home telehealth for chronic disease management: a systematic review and an analysis of economic evaluations.IntJTechnolAssessHealthCare.
[11] FinkelsteinSM,SpeedieSM,PotthoffS(2006)Home telehealth improves clinical outcomes at a lower cost for home healthcare. Telemed J e Health12(2):128136.
[12] Peter M Yellow lees, "Successfully developing a telemedicinesystem",JournalofTelemedicineand Telecare,vol.11,no.7,pp.331 335,2005.
[13] BH Stamm, "Clinical applications of telehealth in mentalhealthcare",ProfPsycholResPract,vol.29, no.6,pp.536,1998.
[14] SMFinkelstein,SMSpeedie,andSPotthoff,"Home telehealthimproveclinicaloutcomesatalowercost forhomehealthcare",Telemed J e Health,vol.12, no.2,pp.128 136,2006.
[15] AnIntroductiontotheBasicsofVideoConferencing, 2012, 28 Jan 2014, [online] Available:http://www.polycom.co.uk/content/dam /polycom/common/documents/brochures/video basics br engb.pdf.
[16] W.U. Hasan, M. Sultan Khaja, S. Ahmed and M.M. Khan, "Wireless Health Monitoring System", 2nd Borneo International Conference on Applied MathematicsandEngineering,2018.
[17] Fayezah Anjum, Abu Saleh Mohammed Shoaib, Abdullah Ibne Hossain and Mohammad Monirujjaman Khan, "Online Health Care", 8th AnnualComputingandCommunicationWorkshop andConference(CCWC),2018.
[18] E.Stefanov,M.vanDijk,A.Juels,andA.Oprea,"Iris: Ascalablecloudfilesystemwithefficientintegrity
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
checks," in Proceedings of the 28th Annual Computer Security Applications Conference, ser. ACSAC'12.NewYork,NY,USA:ACM,2012,pp.229 238.
[19] Advanced Encryption Standard (AES) GeeksforGeekshttps://www.geeksforgeeks.org/ advanced encryption standard aes
[20] Tanveer Reza, Sarah Binta Alam Shoilee, Sirajum Munira Akhand and Mohammad Monirujjaman Khan, "Development of Android Based Pulse Monitoring System", Second International Conference on Electrical Computer and CommunicationTechnologies(ICECCT),2017.
[21] L.F.Wei,H.J.Zhu,Z.F.Cao,X.L.Dong,W.W.Jia,Y.L. Chen,andA.V.Vasilakos,"Securityandprivacyfor storage and computation in cloud computing," InformationSciences,2014,vol.258,pp.371 386, doi:10.1016/j.ins.2013.04.028
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
