International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
S.S. Swethapriyadarshni1, S.Swathi Priya2 , P.Yuvarani3 , K.Hemapriya4 1
Panimalar Institute of Technology 4Assistant Professor, Dept. of Computer Science Engineering, Panimalar Institute of Technology, Chennai, TamilNadu, India ***
Abstract Cloud is a Centralized Architecture Server, which serves as a platform for every user of the cloud wanted to store data and sensitive information’s in safe secured storage space. The next logical stage in the growth of on demand information technology services and products is cloud computing. Cloud computing will rely on virtualized resources to a considerable extent. Cloud computing allows IT skills to be reused, and it always includes current computing services such as distributed and grid computing. Users can perform a keyword based search over encrypted material with searchable encryption. The majority of currently available searchable encryption systems are based on a single cloud server approach, which has some drawbacks, such as a single point of failure and hostile insiders. The multi cloud server strategy, on the other hand, provides more data availability and security. However, transferring existing keyword search strategies to the multi cloud will result in higher storage and search expenses, with no discernible improvement in data security. In addition, unlike single cloud, a challenge in a multi cloud environment is how to adequately check query integrity when certain cloud servers return inaccurate or incomplete data. We offer an iterative encryption approach to assure file privacy even if numerous cloud services collude with one another to ensure data security.
Key Words: Cloud computing, Cloud Server, Encryption, Decryption, Multicloud, AES
Cloudcomputinghasseveralattributes,blockchain,forwardapproach,andcryptosystem basedapproachesareaccustomedto preservingsecurity.Thecloudinfrastructurehasseveralcharacteristicsthey'reremotelyhosted,ubiquitous,andcommodified. Currently,severalfirmsaredeliveringcloudservicesexampleGoogle,Microsoft,etc…Virtualizationisanassociatedegree abstraction of execution of the cloud, so virtual machines are used. To preserve the info, the info is encrypted before outsourcingittothecloud.Cloudsourcingisturningintoagiantdealasaresultofitshighscaleusageandhasinexpensive suppliers.Therearealsoproblemsconcerningthepolicyandaccessthatareovercomebythecloudorganization.Oneofthe mainchallengesofthecloudistheconstantnetthroughoutthestorageofinformation.CloudComputingisthesought after networkaccesssplitpoolorganizedcomputingriches.
With searchable encryption, users can do a keyword based search across encrypted material. The bulk of searchable encryptionsolutionscurrentlyavailablearebasedonasinglecloudserverarchitecture,whichhasseveraldisadvantagessuch asasinglepointoffailureandhostileinsiders.Theuseofseveralcloudservers,ontheotherhand,increasesdataavailability andsecurity.Transferringexistingkeywordsearchstrategiestothemulticloud,ontheotherhand,willincreasestorageand searchcostswhileprovidingnonoticeableimprovementindatasecurity.OneoftheseservicesisAmazonElasticCompute Cloud(EC2),whichallowsuserstohaveavirtualclusterofcomputersavailableatalltimesthroughtheInternet.OnAWS, virtualcomputershavehardwarecentralprocessingunits(CPUs)andgraphicsprocessingunits(GPUs)forprocessing,aswell aslocal/RAMmemory,harddisk/SSDstorage,achoiceofoperatingsystems,networking,andpre loadedapplicationsoftware suchaswebservers,databases,andcustomerrelationshipmanagement(CRM).Theproject'sgoalistointegratekeyword searchacrossvariouscloudssothatuserscanquicklylocateaspecificfileordata,andtopreventtheinvolvementofthird partiessothatdataissecureandprotected.
Withoutneedingtolearntheplaintexts,searchableencryptionallowsacloudservertoconductkeywordsearchesonbehalfof datausersoverencrypteddata.Themajorityofcurrentlyavailablesearchableencryptionsystems,ontheotherhand,only supportsingleorconjunctivekeywordsearches,andthefewschemesthatcanperformexpressivekeywordsearchesare computationallyinefficientbecausetheyarebuiltfrombilinearpairingsovercomposite ordergroups.Inexistingsystems,an expressivepublic keysearchableencryptiontechniqueintheprime ordergroupsoutperformsexistingschemessignificantly byallowingkeywordsearchrulestobedefinedinconjunctive,disjunctive,oranymonotonicBooleanformulas.Whenauser
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
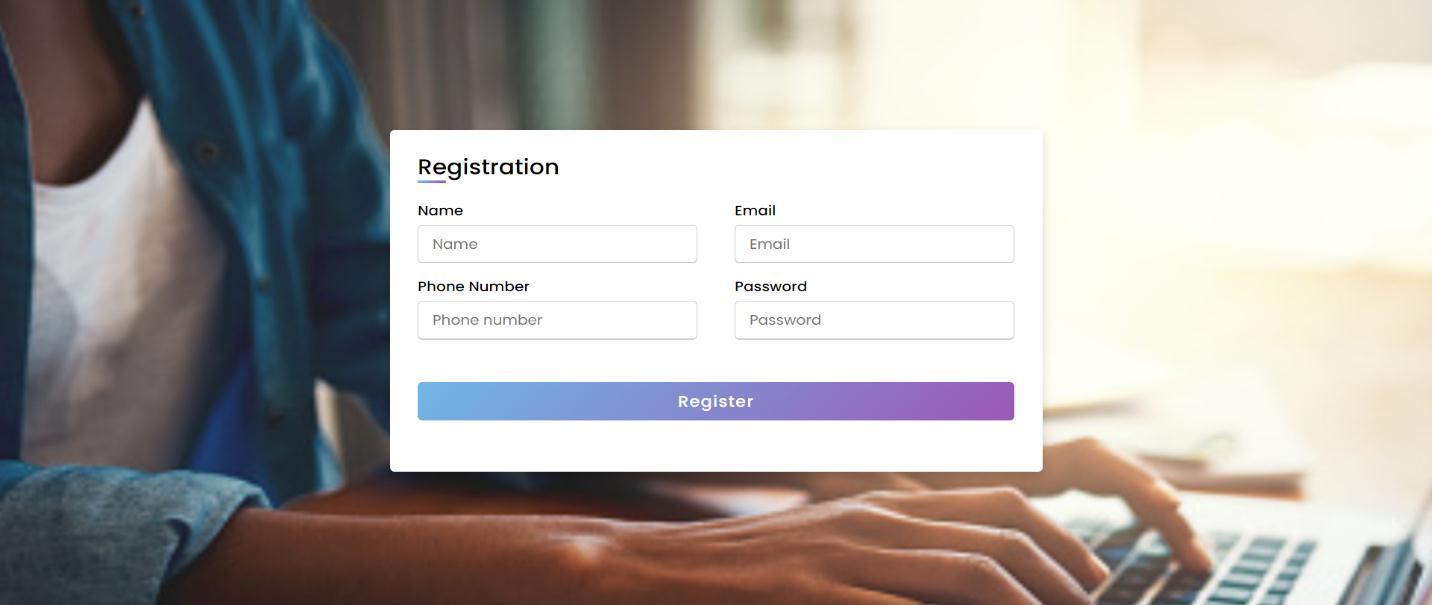
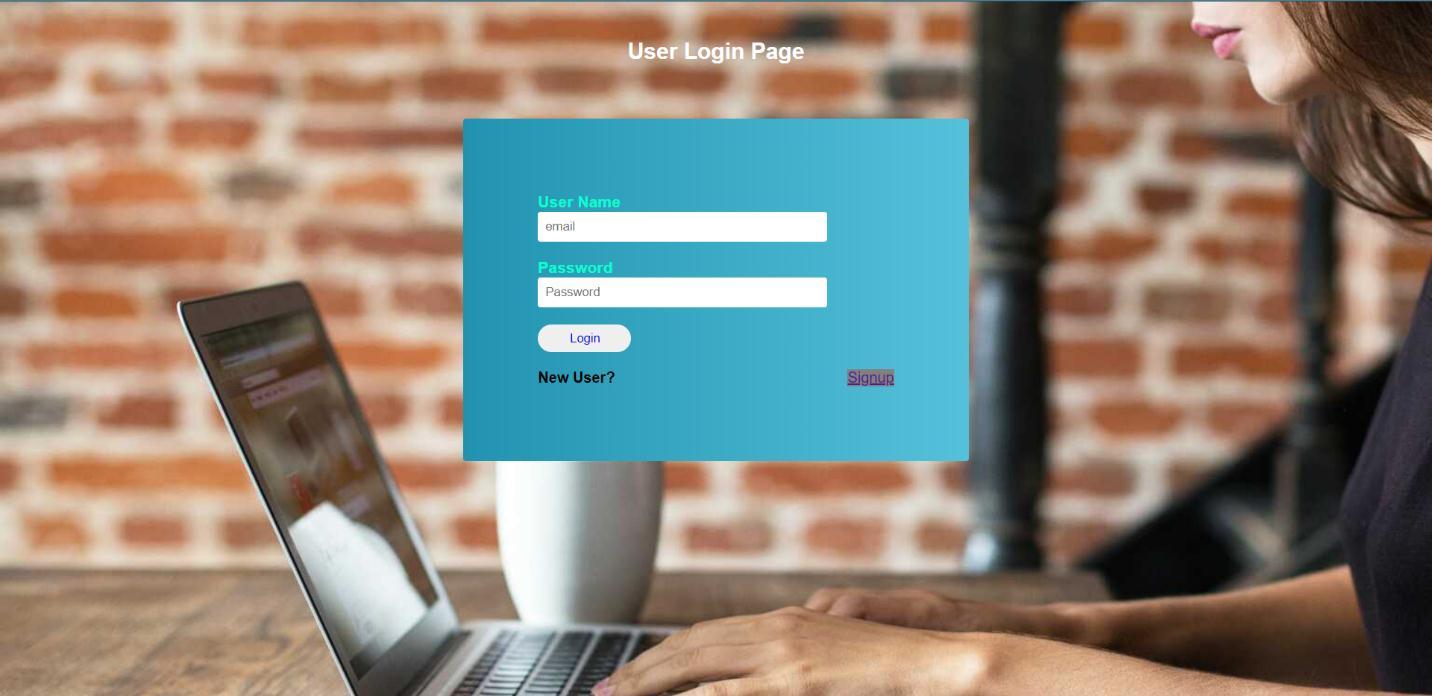
obtainsdatafromaconcernedpersonviatheinternet,unknownorinvalidusersmaygainaccesstothedatastoredonacentral serverordatabase.Itcouldresultindatabeinglostoralteredbyathirdparty.MostexistingPEKSmethods,regardlessof searchauthorisation,focusondataconsumers'richsearchfunctionalities.Theframeworkallowsclientstosendencrypteddata tothecloud,allowsuserstosearchfordocumentsusingdifferentkeywords,andallowsthemtochecktheserver'sresponse.
Encryptingafile,thenmakingncopiesofit,anddistributingthencopiestoncloudserversisastraightforwardfiledistribution solutioninnumerousclouds.Userscanstillretrievethefileevenif(n 1)cloudserversareofflineinthissituation,indicatingthat thisdistributionmechanismishighlyreliable.Thecloudserverismerelyawarethatifitengagesinunethicalbehavior,itwill almostcertainlybediscovered.Thesuggesteddesignreducesstorageoverheadonboththeclientandusersides.Theretrieval timelowersasthenumberofdocumentsincreases,cuttingstoragecostsforbothparties.However,thismethodnecessitatesan excessiveamountofstorageoverhead.Furthermore,becauseeachcloudserverhasaccesstotheentireencryptedfile,webuilda secureandreliablefiledistributionstrategyinvariouscloudstostrikeabetterbalancebetweenstorageoverhead,privacy,and reliability.Wepresentaniterativeencryptionstrategyinspiredbythetwo layerencryptionschemetopreservetheprivacyof datafilesevenifnumerouscloudserversstartacollusionattackatthesametime.Inthissystem,userscanalsoproduceaunique codetogainaccesstoarecordfromanauthorizedindividual.Itwillprovideuserswithasafeaccessmethodaswellasprotect unknownindividualsfromdangerousactivities.

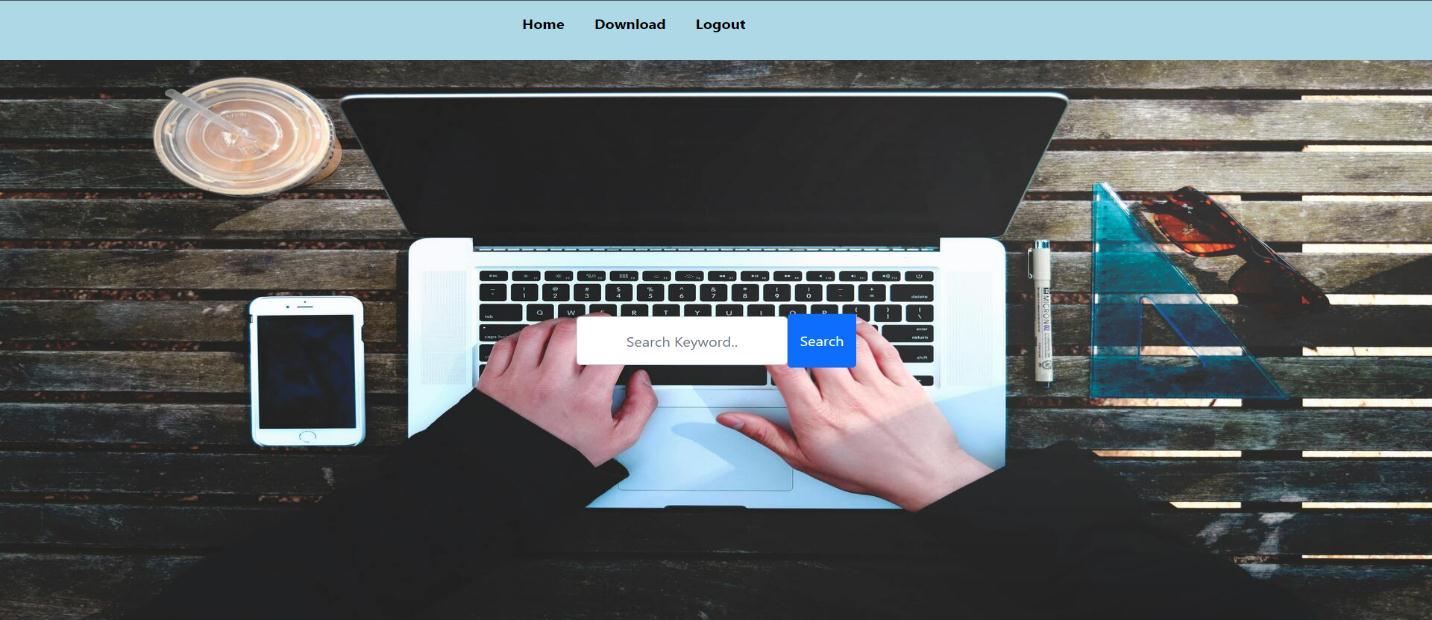
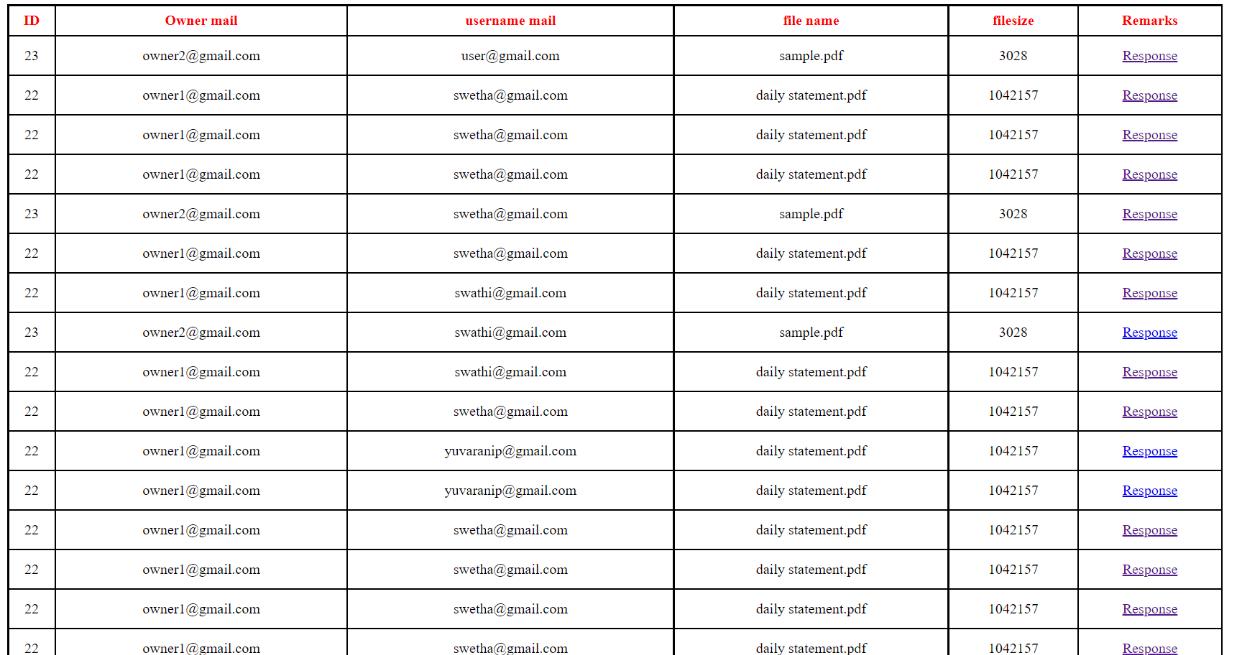
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

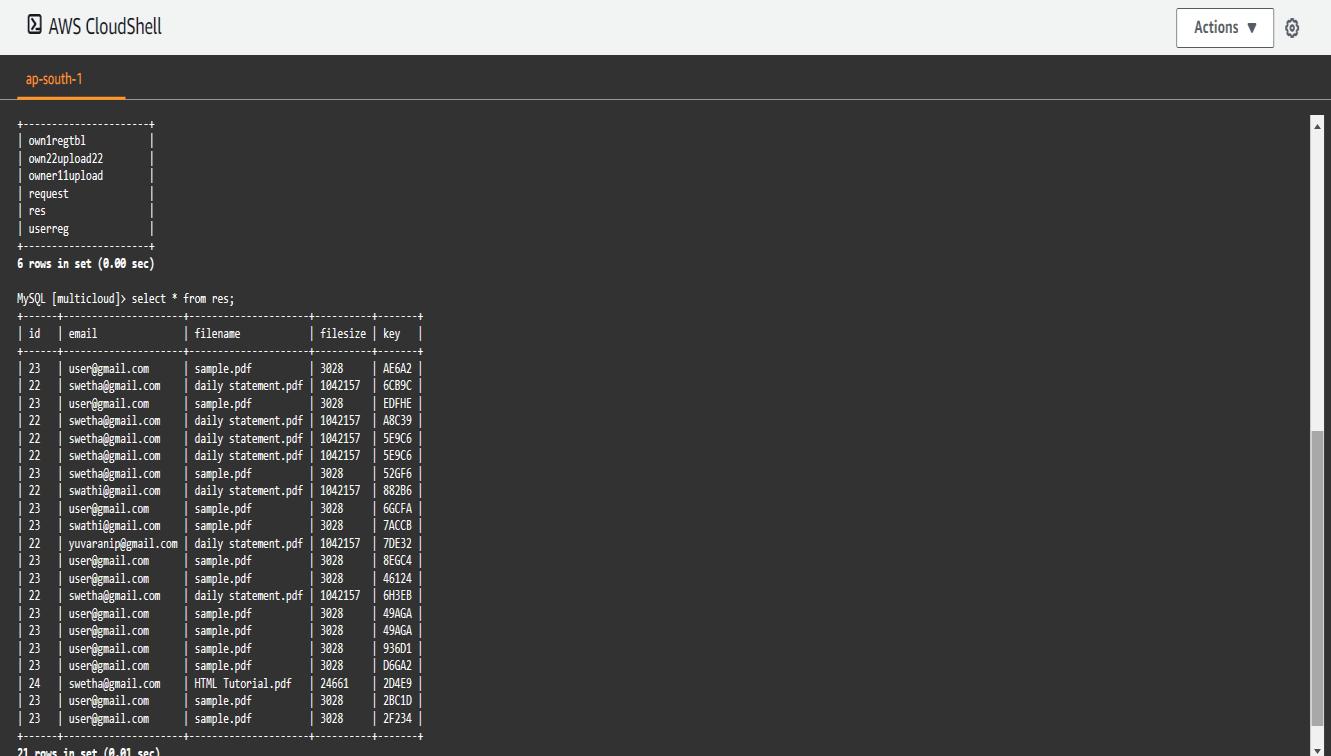
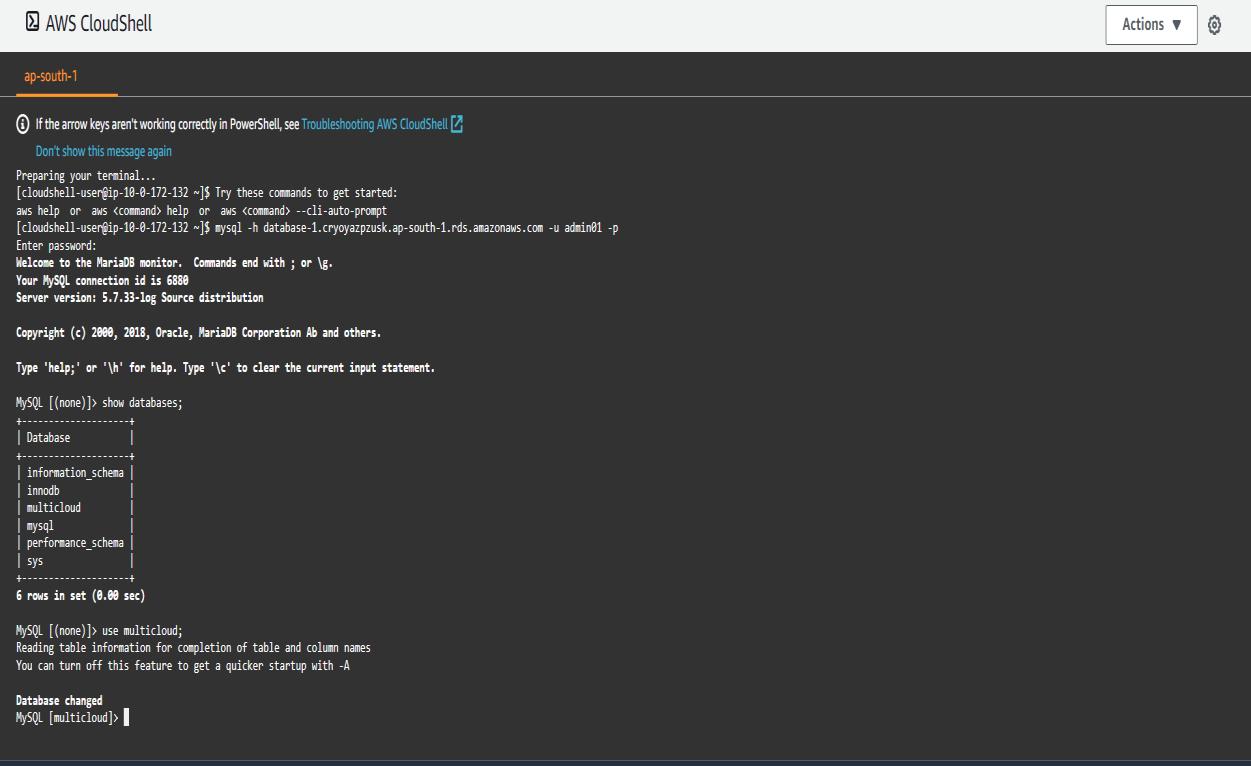
Output 6:FetcheddatafromAWSCloudshell
Inthis,weproposeasolidandcertainkeywordsearchconspireindifferentmists,whichpermitstheinformationclientto performcatchphrasesearchinasafe,dependable,andunquestionableway.Tobeginwith,weproposeasolidanddependable documentappropriationconspire,whichguaranteessecuritythroughiterativeencryptionanddependabilitybypresentingRS deletioncodeinnovation.Second,weplanaBloomchanneltreefilestructureandextendittoamulticloudclimate.Third,we execute a viable trustworthiness confirmation calculation that can rapidly check the respectability of inquiry results and recognizeperniciouscloudservers.Atlonglast,wedosecurityinvestigationandexploratoryassessmenttocheckthesecurity andviabilityofourplan.Forthefuturework,first,wewillinvestigatea quickerandmoreeffectiverecorddissemination conspire that permits clients to bear lower reproduction costs. Second, we will stretch out the protected hunt plan to accomplishfluffyquestion,positioninginquiry,andmultiwatchwordquestion.
[1].YunhongZhou,ShihuiZheng,andLichengWang,"Privacy PreservingandEfficientPublicKeyEncryptionwithKeyword Search BasedCP ABEinCloud",13October2020.
[2]. Qingji Zheng Shouhuai Xu Giuseppe Ateniese, "VABKS: Verifiable Attribute based Keyword Search over Outsourced EncryptedData",theUniversityofTexasatSanAntonio,USASapienzaUniversityofRome,ItalyandJohnsHopkinsUniversity, USA.
[3].Mrs.ZabihaKhan,AssistantProfessor,Dept.ofCSE,GhousiaCollegeofEngineering,Karnataka,India,Ms.KamalaKumari, B.K,RumanaIffath,SaimaAhmed,ZaibaTabassumUGStudentsGhousiaCollegeofEngineering,Ramanagaram,"Reviewof Attribute basedKeywordSearchAuthorizationinCloud",www.ijert.orgNConPCS 2017ConferenceProceedingsSpecialIssue 2017.
[4]. XINRUIGE,JIA YU, CHENGYUHU,HANLIN ZHANG, ANDRONGHAO, 1.College ofComputer Scienceand Technology, QingdaoUniversity,Qingdao266071,China,"EnablingEfficientVerifiableFuzzyKeywordSearchOverEncryptedDatainCloud Computing",dateofcurrentversionSeptember7,2018.
[5].Lincei,ChungenXu,LeiXiaolingYu,andCongZuo,"VerifiableIdentity BasedEncryptionwithKeywordSearchforIoTfrom Lattice",Accepted:24February2021.
[6].ShangpingWang,JianYe,YalingZhang,China,"Akeywordsearchableattribute basedencryptionschemewithattribute updateforcloudstorage"May24,2018.
Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
[7].RuiZhang,RuiXue,TingYuyz,andLingLiux,"PVSAE:APublicVerifiableSearchableEncryptionServiceFrameworkfor OutsourcedEncryptedData",Qatar,Email:tyu@qf.org.qaCollegeofComputing,GeorgiaInstituteofTechnology,Atlanta,GA, USA,Email:lingliu@cc.gatech.edu.
[8]. A Shiny, Jayanth Das, M Venkat Aravind, C A Anirudh Srivatsaa, M Rahul, "Cloud Server Misbehavior Detection Using RankedKeywordSearchResultsVerification",InternationalJournalofEngineeringandAdvancedTechnology(IJEAT)ISSN: 2249 8958,Volume 8Issue 4,April2019.
[9].R.SaiVenkataSivaKumar,T.P.Anithaashri,"EnhancementOfCloudDataSearchUsingSymmetric KeyBasedVerification", Chennai,anithaashritp.sse@saveetha.com,EuropeanJournalofMolecular&ClinicalMedicineISSN2515 8260Volume07, Issue08,2020.
[10].DeviThiyagarajan,R.Ganesan,"USERVERIFIABLEMULTIPLEKEYWORDSEARCHSCHEMEUSINGTHEMERKLETREE FOROUTSOURCEDDATAINTHECLOUD",InternationalJournalofTechnology(2017)4:591 600ISSN2086 9614,(Received: November2015/Revised:February2017/Accepted:July2017).
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
