International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
¹Associate Professor, Department of Computer Science Engineering, Jeppiaar Engineering College, Chennai 600119 2,3,4 Student of Computer Science and Engineering department , Jeppiaar Engineering College, Chennai 600119
Deceitful financial tasks can make gigantic misfortunes to the bank and further influence the economy adversely. Consider the possibility that Block chain Technology and Machine Learning could be consolidated to distinguish dubious financial movement and stop exchanges at the source. That is the very thing that these appropriately expects to do is to execute the block chain to safely store exchange history, For speedy and effective identification of exceptions, which demonstrate dubious action by calculations facilitated by AI. Indeed, even a solitary false activity adversely affects the economy and influences all residents adversely. For this reason we should stand firm to forestall false financial exercises. One technique for doing this is to utilize Artificial Intelligence, especially Machine Learning, in the financial area. We then, at that point, join it with Block anchor innovation to guarantee secure financial exchanges from now on. This will make extortion identification fast, simple and more productive, The Private Permissioned Block chain contains all information in regards to the exchanges and can be recovered progressively. A supported K-implies bunching calculation is applied to the block chain to recognize inconsistencies and point out fake exchanges. The Apache light stage offers strong figuring that empowers the cycle to happencontinuously.
Keywords fraudulent transactions, blockchain, machine learning,SVM,Supervised
Recognizing false exercises has for some time been examined. False exchanges harm the economy and decrease individuals' trust in putting resources into bitcoin and other internet-based arrangements. False exercises are regularly suspected by business members or entrepreneurs. Blockchain individuals need to know about deceitful exchanges and forestall extortion and misrepresentation. Many AI strategies have been proposed to tackle the issue,
however a portion of the outcome are promising [4], yet without any result. This article looks at the presentation of various techniques for AI, like SVM, Certificate Tree, Naïve Base, and Logistic Regression, and analyzes a couple inside and out strategies to recognize false exercises in the organization. Such relative exploration will assist with deciding the best calculation for contrasting reality and the speed of computation. We want to check out clients and exercisesthatcanaddtofakeexercises.
M.S.W. Balagolla; W.PC. Fernando; R.M.N.S. Ratnayake; M.J.M.R.P Wijesekera; A.N.Senarathne; K.Y.Legal administrators[1]ProtectVisabyblockchain.Thistask has a chain estimation technique, as existing ventures are inadequate in size, What’s more the response will be to recognize deceitful exercises to distinguish the charge card, and the framework will battle extortion beforefakeweb basedexchanges.
Zheng and H.Dal [2] Blockchain Technology Summary; Building on the Future. This article gives a full outline of the suspension innovation. We initially give a rundown of the document strategy and analyze the overallagreementcalculationutilizedinvariousways.
Qi M. Dubbed, M. Sukhar, N.Safaulin Wang [3] Blockchain advancement: A bibliometric study. The aftereffects of this article highlight various possible ramifications for directing key standards for new and experienced scientists. Prior to sending off an explorationprojectlateron.
A.Kosba,A,MilloperatorandZ.Wen,Hawk.A standard model has its own advantages. We support the presentation of standard models when creating programminglocallybased.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

V.Yakuma and G.Ntou Danso [5] Avoidance of Mastercard misrepresentation. This report gives a framework to recognizingmisrepresentationinchargecarddatautilizinga non reconnaissanceorganization(NN)innovation.
Michael Ostapowicz Kamil ikbikowsk [6[ as of late, the utilization of blockchain innovation has drawn a great deal of consideration. They will actually want to trade esteem and supplant paper with the customary financial framework. Nonetheless, the capacity to trade esteems on the blockchain is significant for the whole frameworkandshouldbereliedupon.
MayankRaikwar,SubhraMazumdar[7]Thearrangementtohinder the course of protection.Asof late,industrialists have been giving closeconsiderationtothecounteractioninnovationasitisutilized to foster customary establishments, Insurance agencies are one of the most conventional and manageable types of protection. Its capacitiesarehazy,paper based,andinadequateinviewofhuman associationanddifferentattributes.
Vukolike, Marco [8] Re pondering Values, The present status of undertakings, particularly the latest overall set of laws, has its impediments: the shrewd agreements work in grouping, all gatherings use knowledge, the arrangements are substantial, the trustischangedandunaltered,andtheabsenceofachoicetocarry outthesavvycontractsisanotkiddingissue.
C.D.Rattle,V.A.BakshiandL.Braine[9]Typeofscholarlyagreement: fundamentalprerequisitesand technique for drawing.The kind of shrewd agreement that supports savvy agreements can be executed as per the measures to coordinate the standard agreement with the standard code. In this article, we will take a gander at a potential diagram for putting away and sending a brilliant agreement. This is the initial move towards empowering thefoundationofashrewdagreementinthebusiness.
K.Christidis and M. Deveciciotis [10] Smart Internet end understanding.Consideringthenewgainsavailableforuse,weare investigation whether these variables apply to the Internet of Things(IoT) industry. Blockchain is when non believed individuals can conversewithoneanotherwithoutbeingreliable.
Watanabe, S. Fujimura [11] Termination Agreement: Provision of lines for use in Smart Contracts. This technique incorporates another strategy settledafter utilizing dependablescores,andthis new technique makes a blend of different techniques joined with the stock technique. This permits you to forestall infringement on propertyandguaranteesecurity.
E.Lamberti,W.Gatteschi[12]Temporarysuspensionor non suspension isa matter fordifferent offices. In this paper, we show the upsides and downsides of data innovation, and it is dependent upon IT experts who choose whether to involve this innovation in their business. The application cases chosen for a specific line of protection organizations are investigated and a large portion of the application rules are general and canbeutilizedindifferentregions.
C.Christian. E. Androulaki, C. Cachin Introduced the Extended Application System. It upholds arranged conventionsandpermitstheframeworktoconsolidate case applicationswithformats. Clothing is additionally the primary framework to quit utilizing dispersed programming that doesn’t have a local frameworkand isintendedtosendoffanapplicationinplainlanguage.
L.S.Sankar, M.Sindhu [15] Study of the Protocol of Consensus on Suspension Programs. The concurred conventionisthereasonforsuspension.Theypickhow theblockchainfunctions.Scientistsarekeenonfinding new innovations and tracking down better Byzantine conventions. It’s really smart to make an all around acknowledged convention or to play a program that executesconcurrentlyuponconventions.
In the current framework, when you attempt to run ML puttogethercontextualinvestigationswith respect to a customary premise, over handling might happen on the groundsthatthe data isputaway in a standard circle based information base. Examining this information utilizing standard ML strategies requires the most common way of erasing, altering, and mechanizing (ETL) the exchange of data to a logical dataset(OLAP),inwhichtheinformationtobebroken down should be impromptu, which can cause a few blunderswhenfinished.
In existing systems, when attempting to implement continuous learning Mouse cases, there may be an extreme processing bottleneck because the data is typically stored in a standard disk based transactional database (OLTP). Performing analysis on this data usingtraditionalMethodstypicallyrequiresanextract, transform, and load (ETL) process to move the data
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
into an analytical database (OLAP), where the data can be analyzedshouldbeunpredictable,theycausesomeerrordue tooverlappingdata.
In the framework, bank false exchanges lead to high misfortunes and,therefore,totheeconomy.To Stayawayfromthis,weshould utilize the most recent innovation. From the above tests, we can seethatbyutilizingastraightforwardAIcalculationinthefinancial area and joining liquidation innovation, we can undoubtedly see what’supwithbankingtasksandforestallextortion.
● Wrapper should get more accuracy and the selection processshouldbeefficient.
● Trainingsetsshouldbeeasilyrepresentative
● Classshouldbeequallybalanced.
● Managementofthedataparameterswillbeoptimized.
● Singlelevelcodingshouldbemoreimprovised.
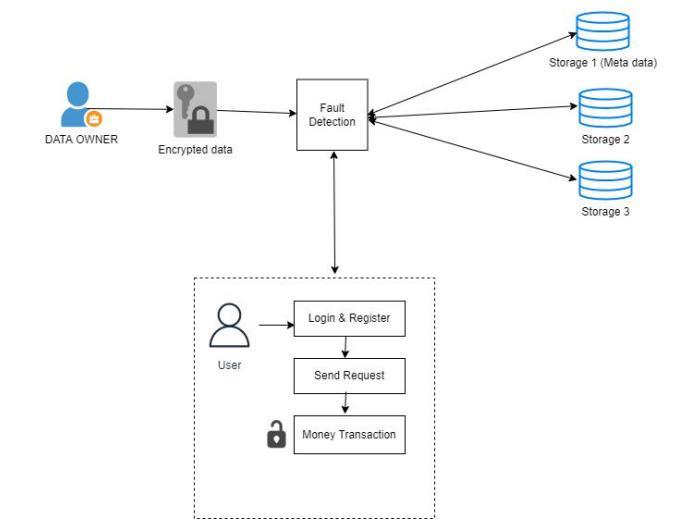
Figure.1.ArchitectureDiagram
AIcanbeutilizedtouncoverorexaminedataputaway inan organization. We should execute a shrewd financial undertaking that gathers data from different sources like sensors,savvygadgets,IoTgadgets,and blockchain.Ongoing investigation or speculations. Information stockpiling in systems administration decreases mistakes in ML demonstrating on the grounds that everything looks great, impersonation, or clamor in network information, which is an essential necessity in an obvious AI strategy. The Reinforcement Learning we give is an AI subdomain usually
utilized in games and impersonation. RL works with the administrator program to create commonsense (strategy) compensation procedures for the climate. The strategy introduced in this study utilizes Direct Training (DRL). Conventional RL doesn’t have an immediate bearing on the presentation of the representatives; however the exhibition of the past windows in the DRL is utilized as an answer for the workers. Utilizing DRL, the analysts had the option to play out an expense arranging measure with an arrangement of environmental change transformation throughoutsomestretchoftime(everyday).
Blockchain this permits members to affirm and check. The item is free and moderately costly. Impairing privatedatasetdatautilizingsharedandprivateserver seal.Itisfortifiedbyatypicalassociationupheldbythe benefit of all. Such a model will work with difficult workintheeventofvulnerabilityaboutthesecurityof the members. The utilization of blockchain takes out therequirementforunendingredundancyofadvanced resources;Hecontendsthateveryunitofcostismoved just a single time, tackling the issue of numerous long stretchesoftwofolduse.Suspensionischaracterizedas the demonstration of sharing worth. This cost based suspension can be quicker, more secure, and less expensive than the conventional framework. The association can keep on keeping the proprietor connected with, as it makes a necessary delicate and receipt archive to more readily match the trade understanding.
Control and confidentiality: Large scale information investigation is a troublesome method for dissecting enormous, shifted or huge information to recognize data, for example, classification, questions, market patterns, and client inclinations that assist organizations with settling on business choices. Enormous scope information examination and progressed investigation incorporate complex applications and elements like prescient displaying, factual calculations, and how to upheld by planners, analysts, and different experts examine the improvement of execution, just as different types of datathatarenotusuallyutilizedinBIandexamination. Encryption and confirmation control are equivalent to protection and avoidance. Data can be with regards to things that are dependable and problematic. Encryption affirmsthatmain believed associationscan
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

get to data. Access control attempts to hinder admittance to data. Halting data is typical for those in control. Encryption strategies should be more impressive than control techniques. Encryption presents genuine difficulties to data protection.
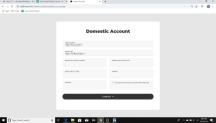
Money transactions are secured and protected by the administrator, no one can hack the system and do an illegal transaction. The most anticipated class out of all expectations is time efficiency during the transaction. We achieved single level coding with more efficiency and wrapper with more accuracy so thattheselectionprocessshouldbemoreefficient. Figure.2.Homepage
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
[7] A Blockchain Framework for Insurance Process,02 April2018,MayankRaikwar;SubhraMazumdar.
[8] Vukolić and Marko,Rethinking permissioned blockchains,17,Dec2017.
[9] Smart contract templates: essential requirements anddesignoptions,12Aug2016,C.D.Clack,V.A.Bakshi andL.Braine.
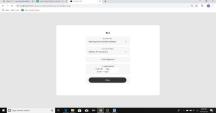
Figure.7.MoneyrequestandAcknowledgment
Our scope is to conduct theoretical analysis and extensive experiments on different datasets with different learners, and our approaches show promising results. In this we also observe existing concepts like e computational and memory efficient randomized feature selection algorithms based on semi randomized selection, warm up, and cool down techniques also beenanalyzedbythiswegetbetter resultsthanprevioussystems. We apply our proposed feature selection approach on real datasets. In this application, we apply our algorithms for polymer property prediction through data; it is a crucial step of a data driven machine learning approach where the geometric and chemical information on the polymers are converted to a numericalrepresentation.
[1] E.M.S.W Balagolla,W.P.C Fernando,R.M.N.S Rathnayake, M.J.M.R.P Wijesekera, A. N. Senarathne, K.Y. Abeywardana” Credit CardFraudPreventionUsingBlockchain”May2021.
[2] Zheng and H. Dal.” An Overview of Blockchain Technology: ArchitectureConsensusandFutureTrends”October2018.
[3] Qi M. Dabbagh, M. Sookhar and N. Safaulin Wang.” The EvolutionofBlockchain:ABibliometricStudy”December2019.
[4] Kosba, A. Miller and Z. Wen, Hawk.” The Blockchain Model of Cryptography and Privacy Preserving Smart Contracts” November 2020.
[5] W. Yaokumah and G. Ntow Danso” Credit Card Fraud Prevention”August2020.
[6] Michał Ostapowicz,Kamil Żbikowski,Detecting Fraudulent AccountsonBlockchain,ASupervisedApproach,29October2019
[10]Blockchainsandsmartcontractsfortheinternetof things,20May2016,K.ChristidisandM.Devetsikiotis
[11]Blockchaincontract:Securingablockchainapplied tosmartcontracts,Watanabe,S.Fujimura,April2016.
[12] Blockchain or not blockchain that is the question of the insurance and other sectors,F. Lamberti, V. Gatteschi,Dec2017.
[13] Blockchain cryptography and consensus,C ,Christian,Aug2017
[14] Architecture of the hyperledger blockchain fabric, Aug2016.
[15] Cryptography and protocols in hyperledger fabric 6January,2017,E.Androulaki,C.Cachin.
[16] Survey of consensus protocols on blockchain applications,L.S.Sankar,M.Sindhu,Jan2017.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3543
