International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
***
Abstract - Face Recognition/Identification has been a fast thriving, challenging and interesting domain in real time applications. A large number of face recognition algorithms have been developed in the recent decades. It has diverse application areas likesurveillance,security, entertainment etc. The software on face identification is useful in airports,banks, offices, educational institutions for screening the people who are entering and exiting these places. Most of the Countries like Germany, Australia, etcusethistechnology[1].Authorities have placed booths for face identification at borders and customs for automating the control system for passport verification and this becomes animportantachievementinthe context of ongoing covid 19 pandemic. Human face is a dynamic object that has a large degree of variability in its appearance as facial features of every individualaredifferent, and this makes face recognition a challenging and ready to improve problem in the computer vision field. As in the face recognition/identification field, accuracy and speedboth play an important role as well as it is the main issue. The goal of this paper is to evaluate different techniques of face recognition and provide a better solutionforimage andvideo based face detection with greater accuracy, better response time and a step forward in betterment of society and protection of the society.
Key Words: Face, Recognition, algorithms, identification, image,software.
Over the years, a lot of security measures have been developedthathelpinholdingconfidentialdatasecuredand restrictingthechancesofasecuritybreach.Facerecognition, whichisoneofthefewbiometricmethodsthatacquirethe meritsof bothhigh accuracyandlow intrusiveness,it isa computer program that engages a person’s face to automaticallyidentifyandverifythepersonfroma digital image or a video frame from a video source [2, 3 4]. It equatestheselectedfacialfeaturesfromtheimageandaface database,oritcanalsobeahardwarewhichisdesignedto authenticateaperson.Thistechnologyisacommonlyused biometrics system for authorization, authentication, verificationandidentification.Alotofcompanieshavebeen adoptingfacerecognitionintheirsecuritycameras,access controls and many more. Facebook has been using face recognitionintheirwebsiteforcreatingadigitalprofilefor thepeopleusingtheirwebsite.Indevelopedcountries,the law enforcement creates a face database to be used with theirfacerecognitionsystemtocompareanysuspectwith
the database. On other hand, in Malaysia, thumbprint identification is used to identify any suspect for the case. However, because of infinite knowledge through internet usage, most criminals are informed of thumbprint identification.Therefore,they becomecharierofleavinga thumbprint by wearing gloves except for unpremeditated crimes.[5] A criminal record or any record consists of available distinct knowledge about an individual, it also consists of a photograph of thesame.Foridentification of any criminal, we need to have knowledge regarding the person,whicharegivenbywitnesses.Identificationcanbe donebyusingvariousmodeslikefingerprintscanning,DNA tests, etc [1]. Our paper focuses on the Face Identification method to extract information from the image of the individualanduseitasameansofidentificationratherthan anyotheridentificationmethod.Afaceidentificationsystem will access the available database which consist of photographsandthencompare thosetotheoneswhichit hascapturedorinreal timetofindamatchonlyifthematch exists.Foreveryimage,thiscanbedonebymeasuringthe width,heightoftheface,alsothevalueoftheeyecolourby usingvariousratios,differentformulasthatcanbeusedfor identificationofthefaceaswellasitwillhelpinfindingthe approx.age,gender,etc.also.Thesoftwarewillworkintwo phases. First is called face detection and the other is Comparison. Face detection is the ability of a machine (computer) to independently identify and extract the featuresofafaceinanimageorvideo.Theotherphaseofthe processconsistsofcreatingaprintlikefingerprint,butitis of the image and then compares that imager print with available database accurately [2]. This System is used for pinpointingthecriminalsinspiteofitslocationuntilhe/she iscapturedbyanycamerasandaid governmentauthority forfurtherinvestigations.Also,wearestoringtheseimages ofthecriminalsasakeepsafeinourdatabasealongwiththe personal details and we are also hell bent to keep this databaseatotherdifferentlocationssoifonegetscorrupted or hacked, we can use the others which are stored at locationsknowtoonlysomeindividualsaroundtheworld. This project intends to identify the criminal based on the existingrecordofthesameandcreatinganewrecordifno previousrecordexisted.
The main purpose of research on computer vision is to develop an automated face identification system which canequallyandwill surpasshumanperformanceinfuture. Thisproblemhasbeenstudiedforthepasttwodecades.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Theapproachesthathadbeenusedsofarcandividedinto twocategoriesthatis:
The model based one attempts to find and mark the geometricalparametersbymeasuringthefacialpartsandthe appearancebasedontheintensity basedparameterssuchas eigen coefficient for recording the face. Because of the changesinlighting,expression,etc.conditionsthefaceofthe humancanbealteredconsiderably[6].
TheFaceidentificationsystemisnotanewfield,asanearly prototypewhichusesfeature basedapproachwasdeveloped overa100yearsagobyAlphonseBertillon,ashedevelopeda system of measurement of the physical aspects of the criminals using which they can identify them. He takes photographsofseparateaspectsofthefacelikenose,eyes, chin, forehead, different profiles etc. of the criminal and stores them in his “database.” But this database was examinedbyhumansnotbycomputers,butstill,itusesthe same biometric approach that the modern recognizing systemuses.
Theseapproachesarebeingusedinobjectdetectionsystems whichalsousecomputervisionfordetectionofanyobject andbasedonitsfeaturespecifyingitasaplant,ball,table,etc.
Pointtobenotedisthatfacerecognitionisdifferentthanface detection:
● Face Detection:themainpurposeinthisistofindtheface i.e.Itslocationandsizeinaphotographandextractthesame tobeusedintherecognitionalgorithm.
● Face Recognition:withthealreadyextractedinformation which is also cropped, resized, and mostly converted to grayscale,thisalgorithmisaccountableforfindingthetraits whichcanappropriatelydescribetheimage.
The face recognition application can be operated in two modes:
● Verification or corroboration of the facial image: This estimatestheinputimagewiththefacial imageassociated with the user who is requiring the corroboration. This is statedas1x1comparison[6].
● Identification or Recognition of face: it compares the inputimagewiththepreloadedimagesinthedatabaseand aimstofindthematchinguser.Itisa1xNcomparison.
There are many different types of face algorithm that exists,like[4]:
● Eigenface(1991)
● Fisherface(1997)
● ScaleInvariantFeatureTransform(SIFT)(1999)
● SpeedUpRobustFeatureTransform(SURF)
● LocalBinaryPatternHistograms(LBPH)
● Etc,
Each of the above mentioned algorithms uses different approachestoextracttheinformationfromtheimageandfor performing the matching with the input image. However, methodsusedbyEigenfaceandFisherfacesaremostlythe sameandthesameisalsotrueforSIFTandSurfmethods[7].
● Eigenface and Fisherfaces:EigenfaceusesPCA(Principal Component Analysis) that is a dimensionality reduction methodwhichreducesthedimensionsofthelargedatasetof images,byconvertinglargesetofvariablesintosmallerones butitstillcontainsmostoftheinfoofthelarge dataset[8], whereasFisherfacesusesFLD(FisherLinearDiscriminant) whose working is mostly same as Eigenface, but it works betterfortheclassificationofdifferentaspectsoftheimage orobject[8].
● SIFT and SURF:Thesemethodsextractthelocal feature pointsoftheeyesandthenclassifytheinvariantkeypointsin theimageoftheeyesandthenindicatethesepoints,createa local pattern around these points, and use them for identification. In this the KNN Algo (K nearest neighbor algorithm)isusedfortheclassificationpurpose[9].Butfor our system we are using the LBPH algorithm as we have foundittobemuchmoreefficientandhasalargescopeof improvementwhichcanbedoneasitiseasytoo.
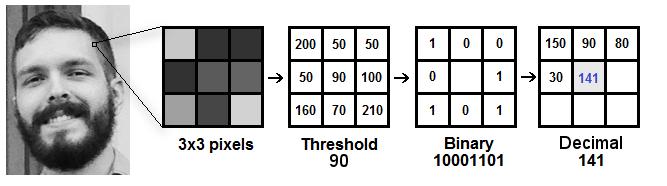
● LBPH (Local Binary Pattern Histogram): TheLBP(local binary Pattern) is a simple but also very efficient texture operator as it labels the pixels of the photograph by thresholdingtheneighborplacesofeachpixelandregards theoutputresultasabinarynumber[10].Thisalgorithmwas firststatedin1994andtillnowitisrecognizedasthebest and most powerful feature for texture classification. And furtheritisfoundthatwhenthisalgorithmincombination with HOG (Histogram of Oriented Gradients) descriptor is used,itsperformancetodetectthesimilaritiesimprovesfor some datasets. But using the combination of LBP and histogramwecanrepresenttheimageofthefacebyasimple datavector.
Stepsareasfollowed:
1. Parameters:thisalgorithmusesfourparameters:
a. Radius:radiusisusedtoconstructthelocalbinarypattern incircularformandtorepresentradiusaroundthecentral pixel.Itissetto1.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
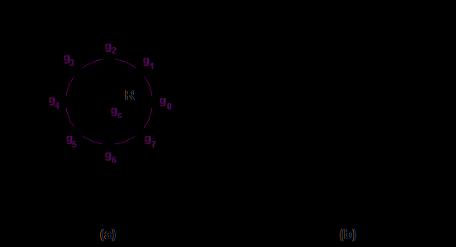
b. Neighbor: it is the cluster of points that constructs the circular binary pattern. Point to note the more sample pointsweincludethemorethecomputationalcostincreases.
c. Grid X: the number of cells in the horizontal direction. More cells mean more finer the grid, and higher the dimensionalityoftheoutputfeaturevector.
d. Grid Y:thenumberofcellsinverticaldirection.

2. Training:Firstly,weneedtotrainthealgorithm.Andto do so, we need some training dataset that comprises the facialimageofthepersonwewanttorecognize,and,inour case,weneedtheimageofthecriminal.Andwealsoneedto setanIDorsometypeofnumberforeachimage.
3. Applying the LBP:Thefirststepincomputation ofthe algoistoconstructaswiftimagewhichdescribesthenative imageinawellmanner,byplayingupthefacialfeatures,and for doing all this the LBHP uses the concept of a sliding window,whichmostlydependsontheradiusandneighbour parameter.
Forexample
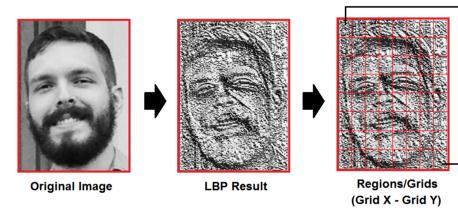
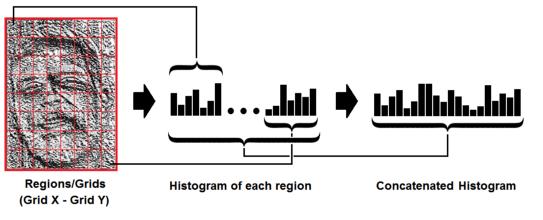
4. Histograms extraction: By using the image which was generatedinthepreviousstep,weusetheparametersofGrid X and Y for dividing the image into multiple grids like the belowgivenimage:
5. At last, performing the recognition of face: Since the algorithm has already been trained in the previous steps. Everydistinguishedhistogramthatiscreatedisusedinthe representation of each image from the training dataset. Similarlyforeverynewimageweperformthesamesteps.
● For finding the data of the criminal we just need to comparetheinputimagewiththehistogramofeveryimage andthewhichisclosestisgivenasoutput.
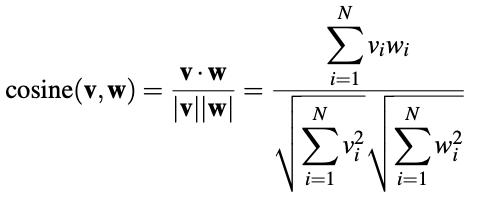
● There are various approaches to calculate the distance between the histograms, like Euclidean distance, cosine similarities,Manhattandistance,absolutevalue,chi square, etc.
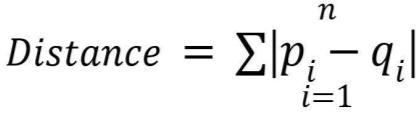


Euclideandistance: Cosinesimilarity:
Manhattandistance:
Chi square:
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
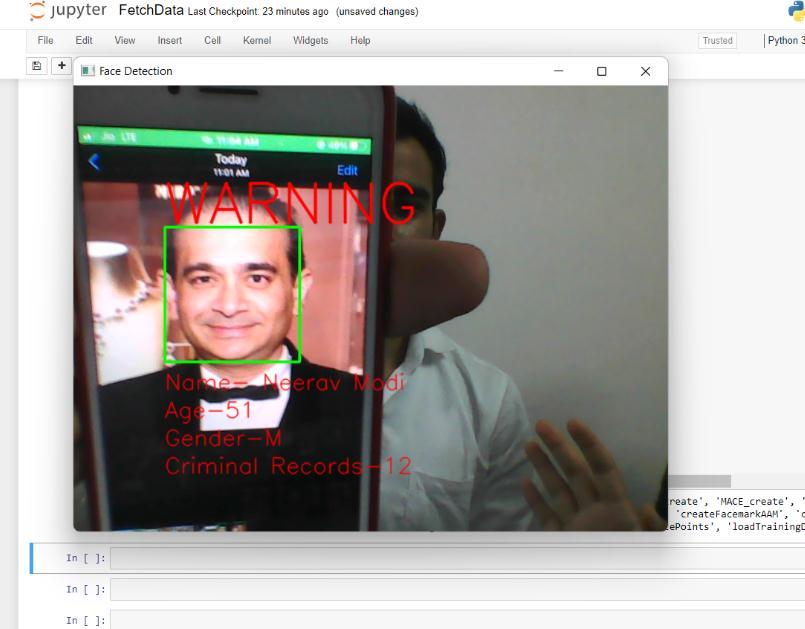
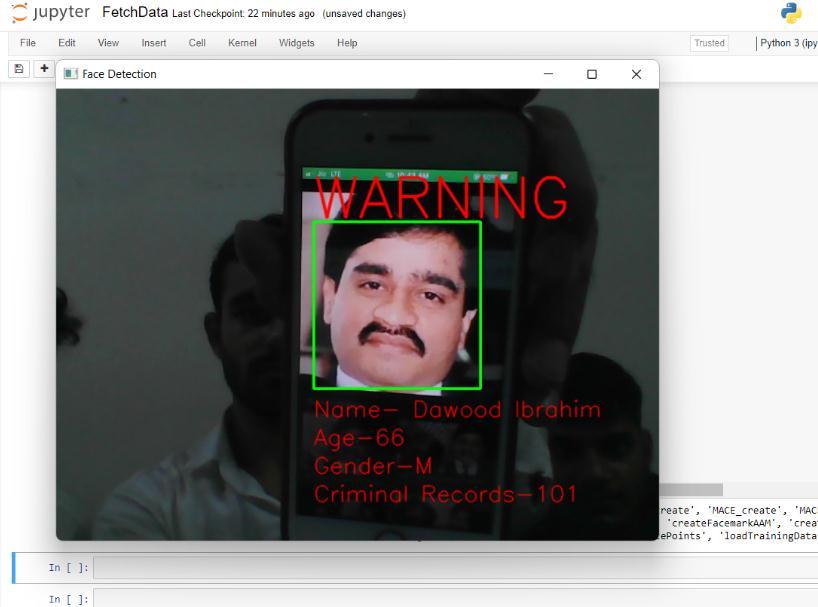
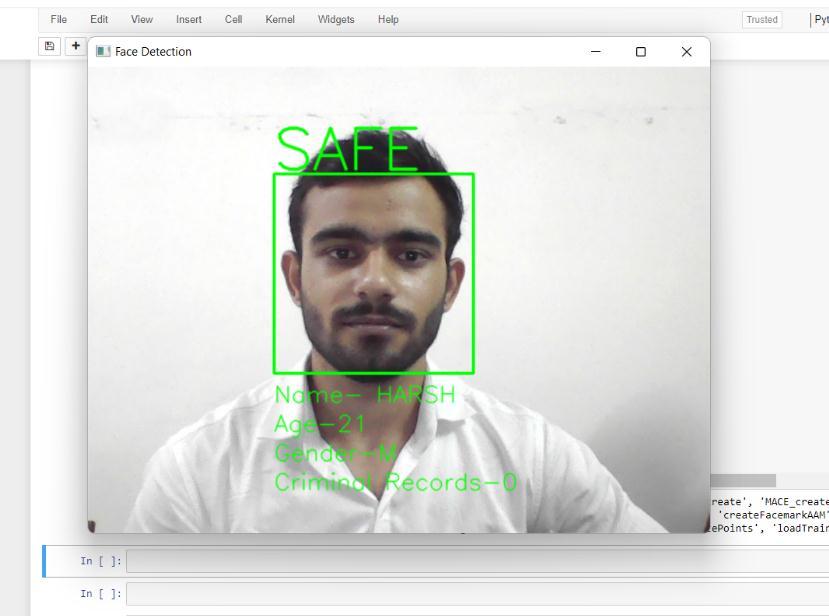
Asaresult,wehavedevelopedasystemthatiscapableof identifying, detecting, verifying the face of a criminal and showingitsinformationafterretrievingitfromthedatabase. Belowaresomescreenshotswhichweretakenwhiletesting andtrainingthesystem.
In the above we are just trying to show the points or the parameters that the system is taking as a reference for makingthehistogramsoftheinputimage.
Nomatterhowwelltrainedthere’salwaysascopeoferrorin Facerecognitionprograms.Recklesslyrelyingonthismodel mayturnouttobecatastrophicfortheAuthorities. Asthe photographs are uploaded via the internet it makes the application severely crippled if there’s no access to the internet.Deployingandintegratingthissystemtoitsfullest potential requires massive funding and research. Despite gettingorhavingsuchdrawbacks.Themorethissystemgets used,themoreitsdatabaseincreasesandthemoreusefulit becomes along the line. Right now, face recognition programsareobviouslyfarbelowwhatahumancando,but it’salsoobvious thatmachinelearningis improving every dayandisalreadymuchbetterinsome tasksthanwhata human can do. Therefore, it’s a plausible conclusion that facialrecognitionprogramsmaysomedaysurpassus.
[1] Guillaumin, M., Verbeek, J.J., Schmid, C.: Is that you? metriclearningapproachesforfaceidentification.In:ICCV. (2009).
[2] S. H Lin, “An Introduction to Face Recognition Technology”,InformingScienceSpecialIssuesonMultimedia InformingTechnologies,3:1,(2000).

[3] R. Rathi, M. Choudhary & B. Chandra, “An Application of Face Recognition System using Image Processing and Neural Networks”, International Journal ComputerTechnologyApplication,3:1,(2012),pp.45 49.
[4]R.A.Hamid&J.A.Thom“Criteriathathaveaneffect on users while making image relevance judgements”, in Proceedings of the fifteenth Australasian Document ComputingSymposium,(2010),pp.76 83.
[5]NurulAzmaAbdullaha,Md.JamriSaidi,NurulHidayahAb Rahmanb,ChuahChaiWenc,andIsredzaRahmiA.Hamidd “Face recognition for criminal identification: An implementation of principal component analysis for face recognition”,AIP Conference Proceedings 1891, 020002 (2017).
[6]AdrianaKovashkaMargaretMartonosi Feature Based Face Recognition for Identification of Criminals vs. IdentificationforCashlessPurchase.
[7] Davis, J.V., Kulis, B., Jain, P., Sra, S., Dhillon, I.S.: Information theoreticmetriclearning.In:ICML.(2007).
[8]ASurveyofFaceRecognitionTechniquesRabiaJafri*and HamidR.Arabnia*.
[9]Wang,X.,Tang,X.:Bayesianfacerecognitionusinggabor features.(2003)70 73.
[10] Face Recognition with Learning based Descriptor ZhiminCao11TheChineseUniversityofHongKongQiYin2∗ 2 ITCS, Tsinghua University Xiaoou Tang 1,3 3Shenzhen Institutes of Advanced Technology Chinese Academy of Sciences,ChinaJianSun4MicrosoftResearchAsia.
[11] D. DeCarlos, D. Metaxas, and M. Stone. An anthropometricfacemodelusingvariationaltechniques.In ComputerGraphicsProceedingsSIGGRAPH98,pages67 74, 1998.
[12]S.DiPaola.Extendingtherangeoffacialtypes.Journalof VisualizationandComputerAnimation,2(4):129 131,1991.
[13] T.F. Cootes, G.J. Edwards, and C.J. Taylor. Active appearance models. In Burkhardt and Neumann, editors, ComputerVision ECCV98Vol.II,Freiburg,Germany,1998. Springer,LectureNotesinComputerScience1407.
[14] G.J. Edwards, A. Lanitis, C.J. Taylor, and T.F. Cootes. Modellingthevariabilityinfaceimages.InProc.ofthe2nd Int.Conf.onAutomaticFaceandGestureRecognition,IEEE Comp.Soc.Press,LosAlamitos,CA,1996.
[15]Moghaddam,B.,Jebara,T.,Pentland,A.:Bayesian face recognition.PatternRecognition33(2000)1771 1782
[16]Phillips,P.J.,Moon,H.,Rizvi,S.A.,Rauss,P.J.:Theferet evaluation methodology for face recognition algorithms. PAMI22(2000)1090 1104
[17] Wang, X., Tang, X.: A unified framework for subspace facerecognition.PAMI26(2004)1222 1228
[18] Wang, X., Tang, X.: Subspace analysis using random mixturemodels.In:CVPR.(2005)
[19] C.S. Choi, T. Okazaki, H. Harashima, and T. Takebe. A systemofanalyzingandsynthesizingfacialimages.InProc.
IEEE Int. Symposium of Circuit and Systems (ISCAS91), pages2665 2668,1991.
[20]Li,Z.,Tang,X.:Bayesianfacerecognitionusingsupport vectormachineandfaceclustering.In:CVPR.(2004)
[21]Weinberger,K.Q.,Blitzer,J.,Saul,L.K.:Distancemetric learning for large margin nearest neighbor classification. Volume(2005)207 244
[22]D.Beymer,A.Shashua,andT.Poggio.Example based imageanalysisandsynthesis.A.I.MemoNo.1431,Artificial Intelligence Laboratory, Massachusetts Institute of Technology,1993.
[23]J.SivicandA.Zisserman,“VideoGoogle:Atextretrieval approachtoobjectmatchinginvideos,”inProc.ICCV,vol.2, 2003,pp.1470 1477.
[24]Ying,Y.,Li,P.:Distancemetriclearningwitheigenvalue optimization. Journal of Machine Learning Research 13 (2012)1 26
[25] Criminal Face Recognition System Alireza Chevelwalla[1] , Ajay Gurav[2] , Sachin Desai[3] , Prof. SumitraSadhukhan[4]DepartmentofComputerEngineering RajivGandhiInstituteofTechnology.Versova,Andheri(W), Mumbai 400053.
[26] Rabia Jafri* and Hamid R. Arabnia* A Survey of Face RecognitionTechniques.
[27] Computational Vision: Archive.” 17 Mar 2005. http://www.vision.caltech.edu/htmlfiles/archive.html.
[28] P.J. Burt and E.H. Adelson. Merging images through pattern decomposition. In Applications of Digital Image Processing VIII, number 575, pages 173 181. SPIE The InternationalSocietyforOpticalEngineering,1985.
[29]Cox,IngemarJ.,JoumanaGhosn,andPeterN.Yianilos. “Feature BasedFaceRecognitionUsingMixture Distance.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
