International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056


International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

1Professor, Department of Telecommunication Engineering, Dr. Ambedkar Institute of Technology, Bangalore, Karnataka, India
2, 3, 4, 5Undergraduate Student, Department of Telecommunication Engineering, Dr. Ambedkar Institute of Technology, Bangalore, Karnataka, India
Prashanth C R1 , Deepika S2 , Jagruth S3 , Jalaja M4 , Rachana S L5 ***
Abstract Currently, the military federations are taking assistance of robots within the risk prone areas which aren't effective when done by army men. In the proposed system the idea is based on the chameleon’s Camouflagetechnique.Oneof the most aims is to implement an autonomous camouflaged technology based wireless multifunctional robot that can be controlled through a PC i.e., the camera captures the image and the robot will change its color according to the surrounding ground hue detected at the rear end.Camouflage robot plays a huge role in saving human loses also the robot can serenely enter into the enemy area and send information via camera to the controller. The dark vision camera is used for surveillance purposes. The scope lies within the enemygun targeting to trace the intruders along with landmine identification. The camouflage robot basically works as a subsidy for the military. Thus, in the proposed model we enforce an AI expert multi sensor data fusion based decision making system to track enemy movement and conduct reconnaissance in unknown areas of a war zone.
Key Words: Camouflage, Artificial Intelligence, ZigBee module, LED’s, Laser gun, Arduino Microprocessor (ATMega 328).
In the modern combat techniques employed by numerous militant forces across the globe, stealth and the ability to maneuverininaccessibleareasplayakeyrole.Armyrobotis anautonomousrobotcomprisingofawirelesscamerathat canbeusedasaspy.
The idea of the proposed system is to implement a camouflagedtechnology basedwirelessmultifunctionalarmy robot capable of disguising itself to infiltrate the enemy campsiteembeddedwithAIfeatures.Thewordrobotmeans "Amachinewhichiscapableofperforming complexseriesofactionsautomaticallythatisprogrammable by a computer." These robots used in defense are usually employed with integrated systems, including cameras, sensors, and video screens. The main motive behind CamouflageRobotistosubstitutehumanlossesinterrorist attacks or military operations. Camouflage robot acts as a virtualspywhichmayfaintlyenterintotheenemyareaand send information via camera to the controller. Robots are
oftenmadetointeractandcooperatemorecloselywiththe citizenrybyincorporatingadditionalfeatureslikerobustness andautonomy.
Aversatileperceptionandrecordingofvariousparameters duringthisrobotareaccomplishedemployingamulti sensor platform. In this system, an interfacing module is incorporatedtoremotelysensethethingparametersusing IOT.Sinceit'sexceptionallyhardtodetectitbyanunadorned humaneye,theCamouflagerobotisoftenalsowon'ttestthe variedsecuritysystemsdevelopedwithinthemarket&act as a measure to evaluate its efficiency. Engineering camouflage aims is to form the detection and recognition target difficult within the machine assisted eye searching targetwithinthemassivebreadthbackgroundaround.
The purpose is to implement the system (model) for a particular face and distinguish it from a large number of stored faces with some real time deviations as well. This model consists of a mobile robot, restrained by the web, which features a camera mounted and a PIR sensor for detectingthelivingbodies.Theuserwillbeabletocontrol the robot through the internet, thus, providing wireless controloftherobot.
Face recognition is one of the most promising fields in computer vision plays an important role in conveying identityandemotions.Facedetectionisacomputercoding technologythatdeterminesthelocationandsizeofhuman faces in a given image format. It detects only the facial featuresandignorestherest.
Human capabilities are very good at recognizing and rememberingfacesdespitethepassageoftime.Hence,itis essentiallybeneficial ifthecurrentcomputertechnologies becomerobustashumansinfacedetections.
Trainingamachinelearningalgorithmcantakeagreatdeal ofdatatoachievemaximumoptimizationandreduceerror. In this paper, we will try to differentiate between the implementationofdifferentalgorithmsinOpenCV.OpenCV providesusthefreedomtorunonanyplatformthatsupports theexecutionofpythoncoding.Itcanbeusedonmachines with Windows, mac OS or, Linux. Here we discuss three algorithms, Haar cascades and Local Binary Pattern Histogram (LBPH) and, Eigen face. These algorithm performanceswereevaluatedbasedonsomeparameters.In
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3540
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
oursimulationsinOpenCV,theexamplesshownarereal time andimagesarecapturedbyusingaUSBcamera.
Prem Kumar has proposeda reviewed systemsusedcolor detection sensor which requires the object to be close to detectthecoloroftheobjectusingZigbeeTechnology[1].
Akshay Ravindran has proposed the camouflaging feature makesitdifficulttodetecttherobotbytheunaidedhuman eye. The color sensor detects the color of surrounding surfaces&determinesthecolorofsurroundings[2].
M.Jagtap has proposed the various techniques and comparisonofMachineLearningalgorithmsbasedoncertain parameters and the performances of algorithms in face detectionforautomation[3].
S.Bhargavi has explained an idea for automated border controltorepresentoneareainthedigitaltransformationof border control Additionally, it has been based on artificial intelligenceandthesafetyoftherobot[4].
Theuniquepropertyoffacedetectionisquiterobustdespite largevariationsinvisualstimulusduetochangingconditions such as environment, aging and, other natural factors (beards, mustache, hairstyles and, spectacles). Facial recognition can be practiced to a larger extent on video footageinreal timeformorepeople[5].
Our main aim is to enhance the communication between soldiers and military room by using advanced and highly efficient,powerfulsystems.
monitorthetrespassers.Theautomaticguntargetingsystem willenhancebordersecurityusingautomation.Apartfrom this,themainfeatureisthecamouflagetechnique;i.e.itcan reproduce the color accordingly with the ground surface, based on the hue color hence being camouflaged to the outside world. We've used LEDs that will diffuse uniform colors,coupledtosensorsthatwillpreciselyidentifythecolor of the bottom. On the opposite hand, AI assisted common operatingpicturewouldcataloganddisplayadispositionof friendlyandenemyforces,automaticallybuiltandupdated through an enormous data approach. Here the model is redesignedtocompelthemachinetoperformmultitaskso that along with checking for several parameters for monitoring,italsocarriesoutothersignificanttasksonits ownusingIOT.
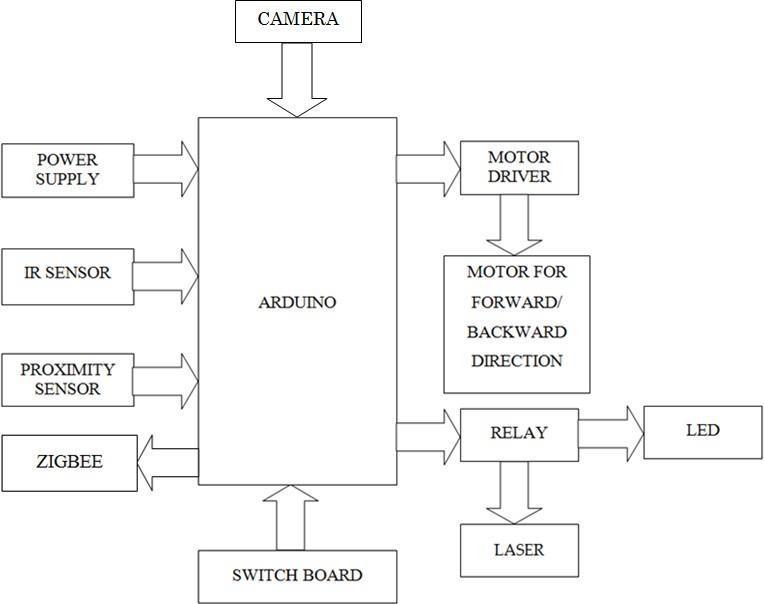
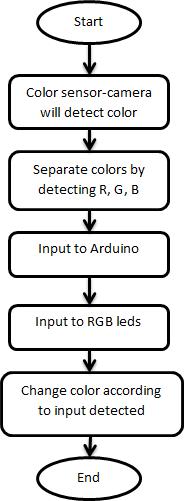
Block diagram comprises arduino, an open source electronics platform based on easy to use hardware and software, camera for capturing the images, IR sensor to sensethepresenceofhumans,proximitymetal sensorfor metalidentification,therelayactsasaswitchforbothLED and laser, DC motor for backward and forward direction with H Bridge and, Zigbee acts as an information trans receiverwithapowersupply.
To design a camouflaging robot that uses face recognitiontodetectentryoftrespassersattheborders.
Ourrobotshouldassistsoldiersandtrytopreventthe damagethatmightariseduetoterroristattacks(intruders), hiddengroundbombs.
Ability to change its color (LED’s) while in motion accordingtothesurroundingenvironment.
A GunTargetingsystemisanAI baseddetectionandtargets thelivingobjectoranymovementinhighlysecuredareas.
Thispaperdescribestheworkingofthearmyrobotasshown in Fig.3.1 and Fig.3.2. The principle is based on Artificial Intelligence ,Surveillance, and Reconnaissance i.e. to track enemy movement and conducting reconnaissance in unknownareasofawarzone.Theprojectaimsistodesign, develop and, implementation of an autonomous smart surveillance system with AI assisted decision making and camouflage using Haar classifier and LBPH algorithm to
Fig 3.1:BlockDiagramofCamouflageRobot
Fig -3.2: BaseStation
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3541

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

The camouflage robot uses arduino Microprocessor (ATMega328)boardandworksonpythonlanguage.Eachof the programming languages used in this robot has its workingprocesslike(motorcontrol,cameramovement,and displaycontrol).
All the input and output actions are performed by the developed robot whereas on the PC side all the image processingisdone.Therobotismountedwithinputdevices likeacamera,obstaclesensorand,proximitysensortocollect alltherequireddataforprocessing.Thecomputerthendoes theprocessingofthereceiveddatausingvariousalgorithms for image processing. HAAR Cascade algorithm and Local Binary Pattern Histogram (LBPH) algorithm are primary algorithm techniques used to determine the color of the backgroundandthisdataistransmittedtotherobot.Allthe transmissioniscompletedseriallyusingaZigbeetransceiver. Therobotcanoutputthereceivedcolorbychangingthecolor ofLEDscoveringthemodel.Thisisdonebyturningononeof thethreerelayspresentontherobot.
This algorithm is achieved by creating the database, then trainingthedatabase,andfinally,recognitionisperformed. The integral image consists of having a small unit's representationofagivenimage.

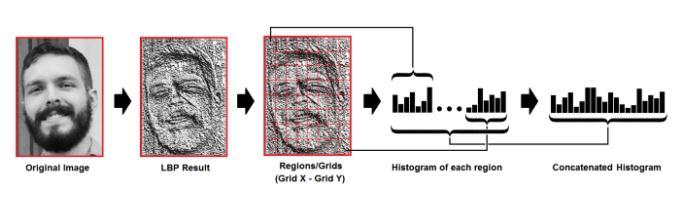
LBPHlocal binary pattern histogramalgorithm is used for front and side face recognition of the dataset. The first computationalstepoftheLBPHistocreateanintermediate imagethatdescribestheoriginalimagehighlightingthefacial characteristics.
Todoso,thealgorithmusesaconceptofaslidingwindow, basedontheparameters radius and neighbors.
Cascade classifier is one of the fewest ML object detection algorithmswherethespeedofcomputationishighforface detectiontotraintheclassifiertoruninreal time.Thekeyto itshighperformanceistheuseofanintegralimage,which onlyperformsbasicoperationsinaverylowprocessingtime. This can be used in surveillance systems with distributed camerasandaback endserverinwhichthedetectiontakes place. The speed of computation is high for face detection wherealotofpositiveandnegativeimagesareusedtotrain the classifier. It lies on the principle of computing the differencebetweenthesumofwhitepixelsandthesumof blackpixels.Themainadvantageofthismethodisthefast sumcomputationusingtheintegralimage.Theyareadjacent rectanglesinaparticularpositionofanimage.
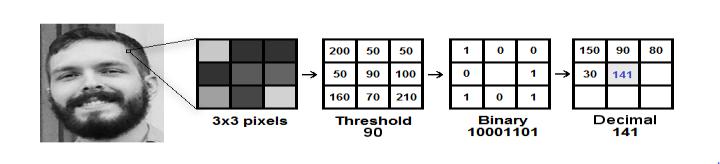
TheoriginalLBPHoperatorlabelsthepixelsofanimageby keeping the 3x3 neighborhood or it can be also said as a matrix.Eachpixelhasavaluethatcanvarydependingupon theimageandpixelquality.Themiddlepixel"90"ischosen which has eight neighbors, subtract these neighbor values with90ifthevalueislessthanzeroputitaszeroandifthe valueismorethanzeroputitasone.Followingthearrow direction in figure 1.1, you will get the binary number as 00110101i.e.141inadecimalsystem.Now,usingtheimage generatedinthelaststep,wecanusethe Grid X and Grid Y parameterstodividetheimageintomultiplegrids,ascanbe seeninthefollowingimage:
Fig 4.2.2:ExtractingtheHistograms
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Wecanusevariousapproachestocomparethehistograms (calculate the distance between two histograms), for example,Euclideandistance,chi square,absolutevalue,etc. Inthisexample,wecanusetheEuclideandistance(whichis quiteknown)basedonthefollowingformula:
it is in 90 degrees of first and so on.Each column is considered an image, duplicate face, and this is called eigenface.
So the algorithm output is the ID from the image with the closest histogram. The algorithm should also return the calculated distance, which can be used as a ‘confidence’ measurement.
Amajorproblemthatitfacesisthatthedataismostlynoisy (i.e. pose, angle, lighting condition). Random images are chosen,butinsuchamannerthattheyhaveafaceinit,thatis not in a truly random way. We define the characteristic feature as eigenface, these characteristics include the presenceofobjectslikethenose,eye,mouthinafaceaswell as the relative distance between objects. PCA (Principal ComponentAnalysis)whichisamathematicaltoolisusedfor theeigenfacealgorithm.Itprovidesfeaturestorecreateand rebuildanyoriginalimagefromthetrainingsetbycombining eigenfaces. That way only if a face adds in the right proportionalmannercanwerecaptureanoriginalface.The imagesusedasinputshouldbeofthesamesizeintermsof pixelandgrayscaleasthatoftrainedimages.OneofPCA's mainadvantagesisitslowsensitivitytonoiseanditsability toreducethedimension.TheEuclideandistancemethodis used to calculate the distance between the eigenvector betweeneigenfaces.Ifthedistanceissmall,thenthesubject is identified, whereas too large distance indicates that the modelrequiresmoretrainingtoidentifythesubject.
The implementation of the Army Robot is based on camouflage techniques and the flowchart explains the schematicview.Toachievethesegoals,LED’s areusedi.e., primarilyRGB,whichcandiffuseuniformcolorsbyusinga webcam followed by morphological transform and then detectionofthecolorsinreal time.
Theuniquefeatureiscomputedbysubtractingtheaverage face from each image vector. The Average human face propertyisshownbytheresultantmatrix.Nowwefromthe result we find the covariance matrix. PCA is used in eigen analysis.Theresultisintheformofthecovariancematrix.
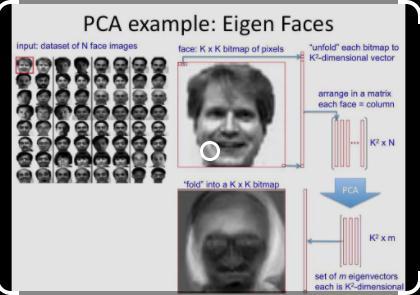

Ithasthehighestvarianceasthefirsteigenvectorandthe secondeigenvectorisindirectionofthenexteigenvectorand
Hence,thisfeaturemakesitdifficulttodetecttherobotbythe nakedhumaneye,canaccessalltheimportantinformation fromotherparties,andalsohelpsinhidingfromtheenemy’s insight
Oneofthemostscathingproblemsfacedbysoldiersisthe identificationorremovaloflandminesthatarepresentonor underthegroundduringwarfields,naturaldisasters,land development. Therefore, it takes high priority to detect landmines in the ground and remove them carefully with sensors. For safeidentification, non touch based detection technologies are required. These methods help in the detectionoflandminesinthesignalsobtainedbynon touch based
sensors, such as proximity metal detectors. The robot will stopanddetectsassoonasanymetalisidentified.
In gun targeting, there are two separate operation modes: InteractiveandMotionDetection.Interactiveplayavitalrole in controlling the dc motor remotely using computer and motiondetectionusesOpenCVi.e.,computervisiontotrack livingobjectsthatmoveinfrontofthecamera.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3543

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Laserisusedforguntargetingupto360degrees,ifatallthe captured image sent for processing by the robot does not match with the faces present in the database folder, robot labels them as an intruder and per forms gun targeting action.
Fig 4.4.2:AI basedGunTargetingFlowchart
Theaboveflowchartillustratesthealgorithmbehind the gun targeting using laser, which mimics face detection basedgunactionofthecamouflagerobot.
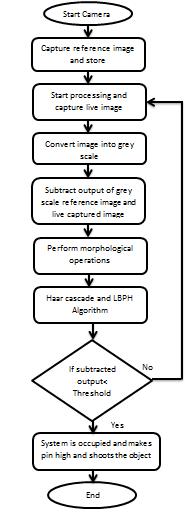
Chart 5.1:AlgorithmPerformanceinanUnconstrained Environment
Resolution Detected faces Recognition rate
At15pixel 28/101 27.7%
At20pixel 54/101 53.4% At30pixel 57/101 56.4% At35pixel 89/101 88.1%
Table -5.2:AccuracyresultofHaar cascade
Resolution Detected faces Recognition rate
At15pixel 12/101 11.8%
At20pixel 38/101 37.5% At30pixel 56/101 55.4% At35pixel 76/101 75.2%
Table 5.3:AccuracyresultofLBPHresult
Theimpactofrainontheimagecauseslossofimagecontrast andcolorfidelity.Asaresult,itisdifficulttomaketheimage visible with adequate quality. While there is evidence of removing the effect of rain on video or data with multiple frameimagesinliterature.Theoverallaccuracyofallfacial recognition (FR) methods was analyzed in foggy, cloudy, rainy,sunny,andspecificconditions(imagescapturedwhen the weather was not sunny or cloudy) Eigenface had the lowestperformanceintermsofaccuracy(86.60%).Similarly, incloudyweather,LBPHhasthebestperformance(96.6%), whileEigenfacedisplayedthelowestperformanceintermsof accuracy the experimental results show that facial recognition(FR) in an unconstrained situation using Eigenface(EF)andLocalbinarypatternhistogram(LBPH)is challenging. LBPH showed the highest accuracy on both LUDBdatasets(imagescapturedindifferentweather)and thedataset(containingunconstrainedimages)
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3544
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
(2) ComparisonofthepixelvaluesofHaar&LBPHvs Eigenfacerecognitionrates
Pixel values Haar cascade Accuracy LBPH Accuracy
At15pixel 27.7% 11.8%
At20pixel 53.4% 37.5%
At30pixel 56.4% 55.4%
At35pixel 88.1% 75.2%
At45pixel 94% 87.1%
Table 5.4: HaarcascadeandLBPH
inanunconstrainedenvironmentcomparedtotheeigenface (75 90%). The mobility of the defense bot with AI like featurescoversallaspectsoftraversingvariousterrainsof theallplaneforagivenaltitudelevelofatangibleplatform meantformovements.
We have achieved our objective by designing a multifunctional army robot that executes chameleon camouflaging features with locomotion, landmine identification,andperformingguntargetinguponintruder detection.WecanseeanAIexpertmulti sensordatafusion baseddecision makingsystemtotrackenemymovementin the border area. Real time data processing is done using Zigbee trans receiver technology, making it low of cost to rebuild. Based on overall results, it can be concluded that Haar cascade and LBPH with the robot exhibit an overall fasterRecognitionrateanddetectionspeed.Thepercentage offacedetectioninculcatingHaarandLBPHissignificantly higher 27.7% 34.6% than the eigenface algorithm. From here,wecansaythattheAI basedCamouflageRobotfaceis moreaccurateandreliablewhenplayedtogethercompared tootheralgorithmsinthestudyforfacedetection.Thus,the proposedautonomoussystemassistsoursecurityforcesand soldiersandkeepsthenationawayfromthefoe.
Chart -5.2:ComparisonofHaarandLBPHofPixelvalues VsAccuracy
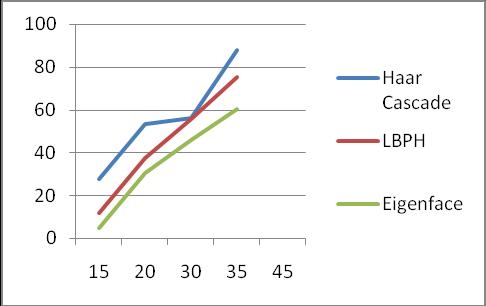
Asthedetectionratewasincreasingtherateofrecognition foreachpixelvalueincreased.Afterthesimulationsofthe algorithms,HaarandLBPHusingOpencvaremoreaccurate thanEigenface,Fromtheaboveresults,itshowsthatthehit rateofHaarwas94%andLBPHwas87.1%comparedto Eigenface59.4%atoptimumlightingcondition.Ifthelight intensityisequaltoorabove45pixels,wegetthemaximum accuracy rate. The result from the table shows that Haar embedded with LBPH is more robust in achieving a high recognitionratecomparedtoeigenface.Thepercentageof face detection using Haar was almost 8% more than the LBPHalgorithm.
ThispaperdiscussesthecamouflagingfeaturecataractingAI basedalgorithmsthatisbeenusedforsurveillance,faceand landmine detection, with automatic gun targeting Haar features and Local Binary Patterns Histogram (LBPH). We also observe that when we inculcate AI based LBPH with Haarcascadewegetthebestrecognitionratecomparedto eigenfacebyvaryingthelightintensitiesaccordinglyinthe scopeofourstudy.AComparativestudyhasshownthatthe haarandLBPHalgorithmsperformancerateishigh85 100%
We would like to express our sincere gratitude to the Management, Principal, Dr. Ambedkar Institute of Technology,Bengaluruforthefacilitiesprovidedandtheir support. Also we would like to thank the Head of the Department,TelecommunicationEngineeringandfaculties fortheirencouragementandsupport.
[1] Premkumar. M “Unmanned Multi Functional Robot Using ZigBee Adopter Network For Defense And Application”InternationalJournalofAdvancedResearchin ComputerEngineering&Technology(IJARCET)volume2, issue1,January2015.
[2]AkashRavindranandAkshayPremkumar“Camouflage Technology”(IJETCSE)ISSN:0976 1353Volume8,Issue1 ,April2015.
[3] A.M.Jagtap,AStudyofLBPH,Eigenface,Fisherfaceand Haar like features for Face recognition using OpenCV, InternationalConferenceonIntelligentSustainableSystems ICISS2019.
[4]S.BhargaviandS.Manjunath“DesignofanIntelligent Combat Robot for War Field" International Journal of Advanced Computer Science and Application, volume 2, no.8,2011.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3545

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

[5] Shantanu K. Dixit, “Design and Implementation of e surveillance Robot for Video Monitoring and Living Body Detection”,InternationalJournalofScientificandResearch Publication,volume4,issue4,April2014,ISSN2250-3153.
[6] S. A Joshi, AparnaTondarkar, Krishna Solanke, RohitJagtap, “Surveillance Robot for Military Application”, International Journal Of Engineering And Computer ScienceISSN:2319 7242,Volume.7,issue.5,May2018.
[7] Shantanu K. Dixit,“Design andImplementation of e surveillanceRobotforVideoMonitoringandLivingBody Detection”,InternationalJournalofScientificandResearch Publication,Volume4,issue4,April2014,ISSN2250 3153
[8] Kunal Borker1, Rohan Gaikwad2, Ajaysingh Rajput3, “Wireless Controlled Surveillance Robot" International Journal of Advanced Research in Computer Science and Management Studies. ISSN: 2321 7782, volume.2, issue.2, February2014.
[9] F.Xu,H.Li,C. M.Pun.H.Hu,Y.Li,Y.Song,andH.Gao,"A newglobalbestguidedartificialbeecolonyalgorithmwith applicationinrobotpathplanning."AppliedSoftComputing, vol.88,p.106037,2020.
[10]MdManjurulAhsan,YueqingLi,JingZhang,MdTanvir Ahad,KishorDatta Gupta,“EvaluatingthePerformanceof Eigenface,Fisherface,andLocalBinaryPatternHistogram Based Facial Recognition Methods under Various Weather Conditions”Technologies2021.

Dr. PRASHANTH C R Professor,Department of Telecommunication Engineering Dr.AmbedkarInstituteofTechnology, VTU,Bangalore


Undergraduate Student, Department of Telecommunication Engineering, Dr.AmbedkarInstituteofTechnology.
Undergraduate Student, Department of Telecommunication Engineering, Dr.AmbedkarInstituteofTechnology.

Undergraduate Student, Department of Telecommunication Engineering, Dr.AmbedkarInstituteofTechnology
UndergraduateStudent,Department Of Telecommunication Engineering, Dr.AmbedkarInstituteofTechnology.