International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 05 | may 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 05 | may 2022 www.irjet.net p-ISSN: 2395-0072
Srikar Banka1 , Smit Parikh2 , Isha Gupta3 , Sambhaji Sarode4
1 ,2,3 Student & Dept.of Computer Science and Engineering, MIT ADT University, Pune Maharashtra, India 4 Professor & Dept.of Computer Science and Engineering, MIT ADT University, Pune Maharashtra, India
Abstract: A system of facial recognition is a computer program for a person to automatically recognize or verify from a digital image or a video source. This can be done by comparing selected face characteristics from the picture and the face database. Face recognition is one of the most important biometric methods. The recognition function is performed by obtaining the facial features from an image of the user’s face. However, the current facial authentication system, for instance, the attendance system that uses an image based approach, has a few drawbacks especially by hacking and granting access to an unauthorized person who does not work in that industry. The proposed system would build a video based mechanism based on the drawbacks of the current existing system by establishing a dynamic face authentication system. During the user verification, it will be checked by video instead of checking photos in this proposed system. As a result, this system will be more secure for access control. This system can be used in industries, residential, and many more.
Keywords: Face Authentication, Dynamic System, Video BasedApproach.
The level of security implemented in any project management software [32] determines how secure the project is going to be. This includes the privacy and confidentiality of our data, as well as infrastructure security,andnetworkstability.Weneedtounderstandthe risks and what cyber criminals are searching for, to understandsecuritybetter.Whileransomware(encrypting files and demanding money to get them back) and major frauds dominate the headlines, something far and less apparent is what most companies face. The offenders simply want to steal our data as well as our business and personalinformation.
Hackers and scammers will open us up if there is toolittlesecurity.Buttoomuchsecuritycanlimitourown team's access to the data that they need. Only when securityisregularlyaddressedandreferredtoatanystage of the planning and implementation of a project, then only can the awareness increase. Facial recognition limits and restrictsaccesstoinformationtothosewhoownit.Itmade authentication fairly simpler, with nothing much to be fittedandlotsofinformationwithinminutestoreach.
Thefacialauthenticationprogramhasbeenusedin thetopinstitutionsandworkplacesasatestofsecuritiesto ensure there is no space for vandalism. This type of softwareleavesnoroomforhumanerroratallandisabig helping hand. Authentication is the method of deciding whether someone is really who or what they believe themselves to be. The authentication method gives control of system access by checking if the user data matches the credentials throughout the authenticated user database or authenticationserverprogram.Authenticationisimportant because it allows businesses to safeguard their networks byallowingonlyauthenticatedusersorprocessestoaccess their protected resources, which can involve computer systems,networks,databases,websites,andothersoftware or services based upon the network. The password based vulnerabilitiesinauthenticationaresometimessolvedwith smarter usernames and password rules such as minimum length and difficulty stipulations, such as capitals and symbols. Password based authentication and authentication based on knowledge are more vulnerable thansystemsthatneedmultipleseparatemethodologies.
In paper [9], there are different types of authentications such as Two factor authentication, Multi factor authentication, One Time Password authentication, API authentication, Public key Cryptography, and biometrics authentication. In Biometric authentication, there are many types such as: 1) Signature Dynamics, 2) Eye Scans, 3) Fingerprint Recognition, 4) Hand or palm geometry,5)VoiceRecognition,and6)FacialRecognition. Someotherauthenticationtypesare:
1. EmailAuthentication
2. DatabaseAuthentication
In paper [25], cloud computing has an on demand delivery over the online platform of wages as you go IT service providers, which increase costs. Rather than procure, own as well as operate physical cloud servers, a cloudservicelikeAmazonWebServices(AWS)canacquire internet services including computing, storage, and databasesystems,asrequired.
There are some benefits to this. We could swiftly change resources from service providers like processing, storing, as well as database systems to the IOTs, machine learning, data lakes, as well as for analytics, and much more,andhence,itprovides agility. Withcloudservices,to
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume:09Issue:05 | May2022 www.irjet.net p-ISSN: 2395-0072
interactwithfutureaccesslevelsofcorporatetasks,wewill not have to excessively provide resources upside. To expand and shrink capability as the business needs shift, we will instantly reduce the operating costs of those tools thereby providing us elasticity. Cloud computing enables us to swap capital expenditure economic costs (like data centers and physical servers), and charge for using its servicesforaloweramount.Hence,itis cost saving.
In most of the existing solutions [14], the face authentication system is static and image based. When a personcomesinfrontofthecamera,thefaceofthatperson getscaptured,and itgetscheckedwiththe faceimagethat is uploaded to the database; if the person is verified, then the person is allowed to enter and if the person is not verified, then the person is not allowed to enter. Here, the imageprocessingmethodisusedforfaceauthentication.
Thedrawback oftheexistingsystem[20]isthatit isnotsecure,evenwithadditionalsecurityinthesystem.A hacker can easily hack the system and then upload a fake profile of a person that he or she desires, who could be a criminal. Once the profile is uploaded, then that person could enter the building and no one would know that the personisunauthorized.
However, the video stream processing of facial images has already been gaining growing attention in biometric technology. A possible outcome of using data integrity that’s present in the video frames to focus on improving still picture systems is an instant advantage whenusingvideodata.Whileasubstantialamountofstudy hasbeenperformedincomparingstillfacialphotos,theuse offacedetectionvideosismuchlessinvestigated.Thevery first stage of video based face recognition (VFR) is to conductidentification,whereagatheringofvideosisjump matchedtoidentifythepossiblesuspectinalloccurrences.
Incommon,VFR methods[16]canbedividedinto twogroupsdependingonhowweexploitthewiderangeof informationpresentinavideoframe:sequence based,and (ii)set based,thenata topstandard,whatseparatesthese different objectives is not whether they use temporal features.
So,byusingthismethod,thesystemwillbeableto checktheAWSbucketwherethevideoisstoredsothatthe person who is at the gate is granted access or is rejected accordingly.
Based on the above reading, we proposed a face authentication system dynamically using the video based method.

● From this system (Fig, 1), a safer way to facial authenticationcanbeofferedtoindustries,offices, buildings,andresidentialapartments.
● In the existing system [4], the user’s picture is captured by the camera at the entrance. Then the system checks if the user is registered or not by checking his/her picture from the database. This methodisproventocompromisesecurityattimes.
● In the working of the security protocol (Fig. 1) when a user reaches the entrance, the camera at the entrance will capture the user’s face to allow his/her entry. A video based approach is used in the proposed solution, in which a video is taken and saved into the AWS Bucket. Then, the video is checked frame by frame dynamically with the other existing videos present inside the AWS bucket.Andthisfootageispickedupdirectlyfrom
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 05 | may 2022 www.irjet.net p-ISSN: 2395-0072
CCTV cameras present in the industry, office, etc. foramoresecuresystem.
● If the user is registered, then he will be granted accesstoenterthepremises.Andiftheuserisnot registered, an alert will get generated to the security team that he/she is not authorized or not registered. The alert will get generated on a web portal for the Security Team to keep track of the security.
● So,thesecurityteamdetermineswhethertoallow a person inside or not after the alert is witnessed.
Iftheindividualisallowed,thenanewuserwitha newIDiscreatedandthevideoissavedinsidethe AWSbucket[25][26].
● Ifanunregisteredusercomestovisitthepremises after the working hours, the user will not be allowed inside. The video of the user that is capturedwillgetdeleted.However,his/herpicture will be capturedandthe nameandthetime of the visit will get stored in the database for security purposes

● In the video based approach figure (Fig. 2), the video is checked frame by frame dynamically with the other existing videos present inside the AWS bucket.Andthisfootageispickedupdirectlyfrom CCTV cameras present in the industry, office, etc. foramoresecuresystem.
● In the existing systems [5], static facial authenticationmethodsarebeingused.However,a dynamicfacial authenticationmethod will beused intheproposedsystem.
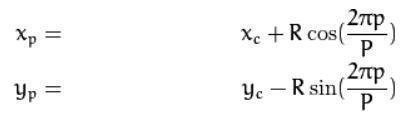
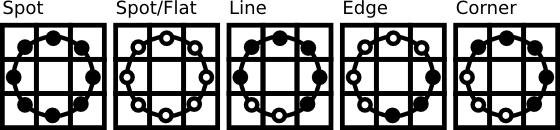
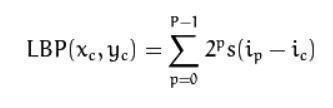
Local Binary Pattern (LBP) [29] is a fast and convenient way operator that identifies the pixels in the image bythresholdingalmosteverypixel'sneighbourhood aswellasconsiderstheoutcomeasabinarynumber
Algorithm description of LBP: A more normal descriptionofLBPcanbewrittenas: with the help of xc and yc as central pixel with intensity ip andic oftheneighbourpixelSissignfunctiondefinedas:
Thisdefinitionhelpsyouto captureanimagewith very fine grained descriptions. The authors were able to compete for texture classification with state of the art tests.Itwasnotedsoonaftertheoperatorwaswrittenthat a fixed neighbourhood fails to encode information that variesinsize.Therefore,theoperatorhasbeengeneralized in[AHP04]touseavariableneighbourhood. The idea istomatchanarbitrarynumberofnearestneighbourswith a variable radius on a circle, which allows the following neighbourhoodstobecaptured:
Foragivenpointxc andyc,thepositionneighbourxc,yc,pϵP can be calculated by:
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3534

Volume:09Issue:05 | May2022 www.irjet.net p-ISSN: 2395-0072


where R is the radius of the circle and P is the number of samplepoints.
The LBP operator is by default robust against monotonous gray scale transformation. By looking at the LBPpictureofadigitallytransformedimage,wecaneasily noticehowanLBPimagelookslike.

Thestepstocreatethedatasetare:
1. ReadallthevideosfromtheAWSbucket.
2. Extract unique user ID and also images of the personcontainingtheuniqueuserID.
3. Read all the person's images, and apply face detectiontoeachofthem.
4. Add each face to face vector with the unique user IDofthecorrespondingindividual.
OpenCV (Open Source Computer Vision Library) [30] is also an open source computer vision and application library for machine learning. OpenCV was designedtoprovideasharedcomputervisionplatformand to promote its use of machine perception in commercial applications. As a BSD licensed software, OpenCV [30] allowstheuseandmodificationofthecodeforcompanies.
OpenCV face recognizer [31] accepts information in a given format to know which face belongs to which person.Ithastwovectorstoit:
● Oneisahuman'sface.
● Thesecondisthelabelsofanintegerforeachface.
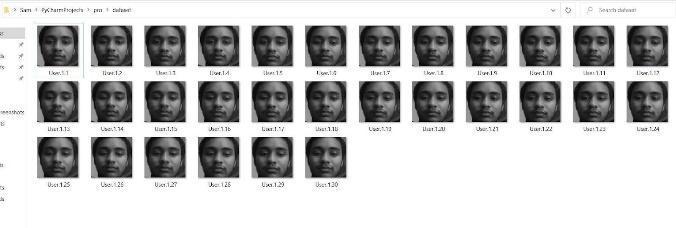
Indatagathering(Fig.4),thefaceisdetectedinthe stored video which is downloaded from the S3 storage provided by the AWS services. Then, 30 images of that detectedfacearecaptured,whichwillgetusedfortraining themodel.
All the 30 images will get stored in the dataset folder witha uniqueusernumberand will getuploadedin thedatabase.
In the face dataset module (Fig. 3), the process of data gathering is explained which will be required for creatingafacedataset.
The data gathering figure (Fig. 4) depicts how the faceisdetectedandhowtheuniqueuseridisusedtostore thefacedataset.
30imagesarecapturedfromthevideo(Fig.5).and this is how the face dataset can get stored in the specific userdatasetfolder,respectively.
IntheAWSbucket(Fig.6), afterthedatasetfolder iscreated,theentirefolderisuploadedtothebucketunder theimages'folder.

e-ISSN: 2395-0056
Volume: 09 Issue: 05 | may 2022 www.irjet.net p-ISSN: 2395-0072
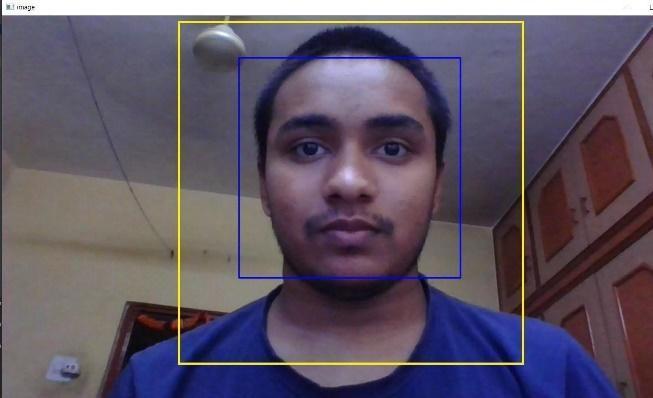
Intheface recognition module(Fig.9),thesystem detects the face to check whether the face is detected or not.
OpenCV uses a different type of face recognition method,theyare:
1. Eigenface
2. Fisherface
3. LocalbinarypatternHistogram(LBPH)
In this project, the local binary pattern histogram (LBPH)methodhasbeenused.
The images which are stored in the dataset folder are then used to train the model which can detect that particularperson.
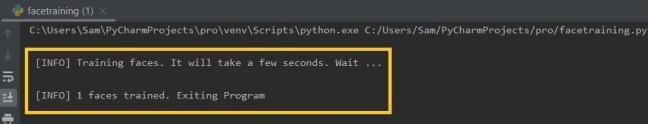
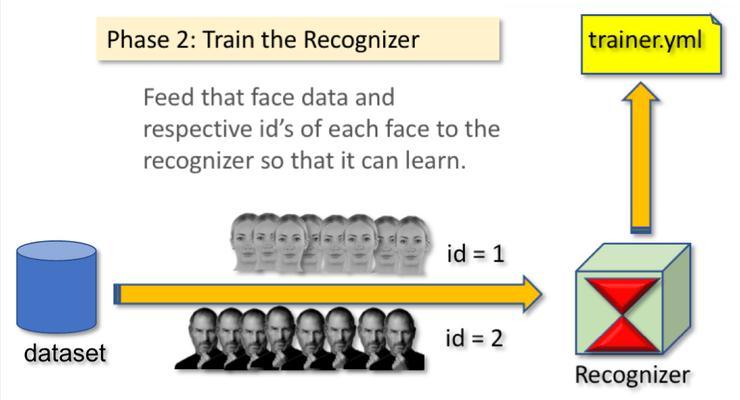
Inthefacetrainingmodule(Fig.7),thetrainerwill get the dataset and the assigned user id for training and storingthedatainthetrainer.ymlfile.
Then, the system takes the help of the trained model (trainer.yml file) to check from the database whetherthepersonisrecognizedornot.

Once the face dataset module is initialized, the Haarcascadetrainerwillgetusedtotrainingourmodel.
The training facial dataset (Fig. 8) depicts the process of training, which takes a few seconds to get trained.Thetimetotraindependsonthenumberofimages presentinthedatabase.
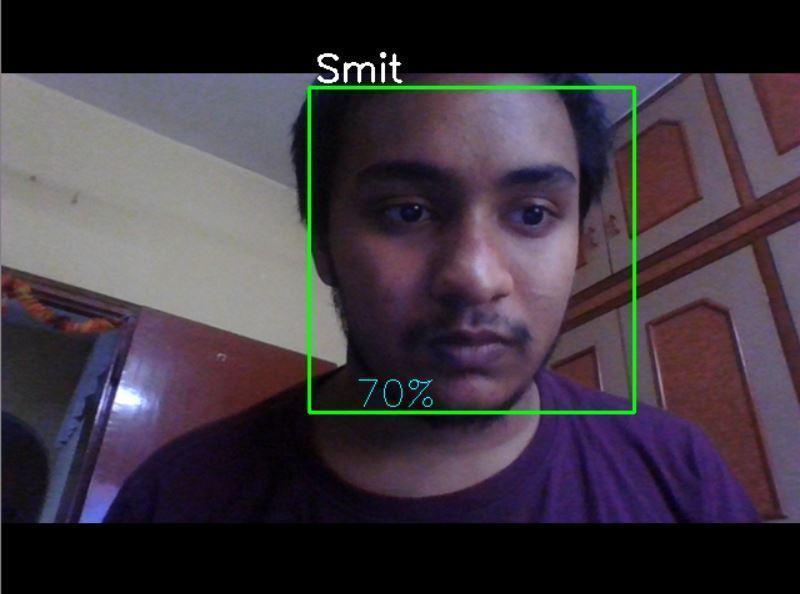
In the recognition accuracy figure (Fig. 10), after using the given face dataset, gathered from the uploaded video and trained dataset file, we got the recognition accuracy of 70% from the webcam. The recognition accuracywillincreaseforhigherqualitycameras.
The integrated module workflow figure (Fig. 11) shows how all the integrated modules will work together, right from the data gathering of the face dataset to the facialrecognitionoftheperson.
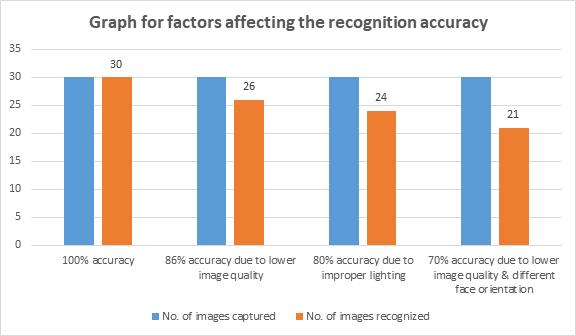
The table for factors affecting the recognition accuracy (Table 1) shows us about the performance evaluationofourproposedvideo basedmethod.
Table 1 - Table of factors affecting the recognition accuracy.
No. of test images

No. of recognize d images Accuracy Remark
Dataset1 (30) 30 100%
Dataset2 (30) 26 86%
Dataset3 (30) 24 80%
Duetotheusageof a higher camera quality.
Duetolowerimage quality captured from a general webcam.
Due to different illumination conditionscaptured from a general webcam.
The bar graph (Fig. 13) is a graphical representation of the factors that affect the recognition accuracythatcanbeobservedinTable1.
Dataset4 (30) 21 70%
Duetodifferentface orientation&lower image quality condition captured from a general webcam.
The pie chart for the recognition rate (Fig. 12) is the representation of the average the recognition accuracy ratefromTable1.
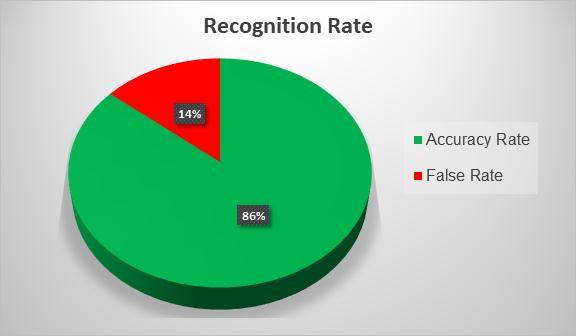
Here, we get a false rate of 14% on an average because of the low camera quality as well as varying illumination conditions. However, we would easily be able to achieve a false rate of 5% or less with superior camera quality.
Faceauthenticationtechnologieshavetraditionally been associated with extremely expensive, top secure applications. The core technologies have advanced today andduetoinnovationandrisingprocessingpower,thecost of equipment is dropping dramatically. Many face authentication technology implementations are now cost effective,dependable,andhighlyaccurate.

Thissystemcanbeusedefficientlytoprovidesafe and reliable protection. It can, therefore, be used in many organizations as a key to security solutions, as it can recognize and convey people's identities. Hence, this rectifiesthedrawbacksoftheexistingsystems.
This paper has portrayed a survey related to face authentication. Here, we have surveyed the paper related to existing face authentication systems and their drawbacks. Therefore, there is a need for an efficient securitysystemforfacial authentication basedonthecons oftheexistingsystems.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 05 | may 2022 www.irjet.net p-ISSN: 2395-0072
[1] AReal TimeFrameworkforHumanFaceDetection and Recognition in CCTV Images by Rehmat Ullah, Hassan Hayat, Afsah Abid Siddiqui, Uzma Abid Siddiqui, Jebran Khan, Farman Ullah, Shoaib Hassan, Laiq Hasan, Waleed Albattah, Muhammad Islam,andGhulamMohammadKaramiin2022.
[2] Face Detection and Recognition Algorithm in DigitalImageBasedonComputerVisionSensorby DiLuandLiminYanin2021.
[3] Face Recognition and Identification using Deep Learning Approach by KH Teoh, RC Ismail, SZM Naziri, R Hussin, MNM Isa, and MSSM Basir in 2021.
[4] Identity authentication on mobile devices using face verification and ID image recognition by Xing Wua, Jianxing Xua , Jianjia Wanga , Yufeng Lia , WeiminLiaandYikeGuoin2019.
[5] A novel optical two factor face authentication schemebyGauravVerma,DajiangLuin2019.
[6] FaceAuthentication method by Julien Doubletand JeanBeaudetin2018.
[7] Face authentication device having database with smallstoragecapacitybyTakayukiKasein2018.
[8] A face recognition Approach Using Deep Reinforcement Learning Approach for User Authentication by Ping Wang, Wen Hui Lin, Kuo MingChaoandChi ChunLoin2017.
[9] An overview of various Authentication Methods and Protocols by Dwiti Pandya, Khushboo Ram NarayanandSnehaThakkarin2015
[10] An Automate System for Unconstrained Video Based Face Recognition by Jingxiao Zheng, Rajeev Ranjan, Ching hui Chen, Jun cheng chen, CArols D. CastilloandRamaChellappain2019
[11] AvideodatabaseofmovingfaceandpeoplebyA.J. O’Toole, J. Harns, S. L. Snow, D. R. Hust, M. R. Pappas,J.H.AyyadandH.Abdiin2005
[12] “IJB S: IARPA Janus Surveillance Video Benchmark,” by N. D. Kalka, B. Maze, J. A. Duncan, K. J. O'Connor, S. Elliott, K. Hebert, J. Bryan, and A. K.Jainin2018.
[13] “An all in one convolutional neural network for faceanalysis,”byR.Ranjan,S.Sankaranarayanan,C.
D. Castillo, and R. Chellappa, in 12th IEEE FG, vol. 00,May2017
[14] “Deep face recognition,” by O. M. Parkhi, A. Vedaldi,andA.ZissermaninBMVC,2015.
[15] “Unconstrained face verification using deep CNN features,” by J. C. Chen, V. M. Patel, and R. Chellappa,inWACV,March2016.
[16] “Video Based face association and identification,” byC. H. Chen, J. C. Chen, C. D. Castillo, and R. Chellappa,12thFG,2017.
[17] “Neural aggregation network for video face recognition,” J. Yang, P. Ren, D. Zhang, D. Chen, F. Wen,H.Li,andG.Hua,inCVPR,2017.
[18] “Trunk branch ensemble convolutional neural networks for video based face recognition,” by C. DingandD.TaoinCoRR,2016.
[19] “Face recognition in unconstrained videos with matched background similarity,” by L. Wolf, T. Hassner,andI.MaozinCVPR,2011.
[20] Face Recognition Based attendance System by Nandhini R, Duraimurugan and S.P.Chokkalingam in2019.
[21] Real Time Face Recognition: An End To End ProjectbyMarceloRovaiin2018.
[22] IoE Enabled Smart Embedded System: An InnovativeWayofLearningbyRathodA.,AyareP., Bobhate R., Sachdeo R., Sarode S., Malhotra J. in Information and Communication Technology for Sustainable Development. Advances in Intelligent Systems and Computing, vol 933, pp. 659 668, Springer,Singaporein2020.
[23] RedefiningsmartnessintownshipwithInternetof Things & Artificial Intelligence: Dholera city by Raghav B.,Manish P.,Vasu G.,Vishal K.,Jyoti M.andSambhajiS.,in6thInternationalConference on Energy and City of the Future (EVF’2019), E3S WebofConferences170,06001IN2020.
[24] Reliable and Prioritized Data Transmission Protocol for Wireless Sensor Networks by S. Sarode, J. Bakal and L. Malik in Proceedings of the International Congress on Information and Communication Technology, Volume 439 of the seriesAdvances in Intelligent Systems and Computingpp535 544,June2016.
[25] Survey paper on cloud computing security by NimitKauraandAbhishekLalin2017
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3538

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume:09Issue:05 | May2022 www.irjet.net p-ISSN: 2395-0072
[26] ASurveyPaperonSecurity inCloudComputing:A Bibliographic Analysis by Krutika K Shah, Rutvij H JhaveriandVahidaUVadiyain2016.
[27] A Survey Paper on Data security in Cloud ComputingbyVijayGhorpade,VishvajitDalimbkar andRajaniSajjanin2016.
[28] A Comprehensive Survey on Security in Cloud Computing by Gururaj Ramachandra Mohsin IftikharandFarrukhAslamKhanin2017.
[29] Face Recognition: Understanding LBPH Algorithm byKelvinSaltondoPradoin2017.
[30] https://opencv.org/about/
[31] OpenCV Face Recognition by Adrian Rosebrock in 2018.
[32] Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks by MohamedAbomharaandGeirM.Køienin2015.