International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Sujithra K M1& Mr. Sivaprasad Manivannan I2 12nd YEAR PG STUDENT, Rohini College of Engineeringand Technology
ASSISTANT PROFESSOR Rohini College of Engineeringand Technology
Abstract The overwhelming advancement of web based business breeds cybercrime. Online payment fraud recognition, a test looked by on the web administration, assumes a significant part in quickly developing web based business. Conduct based techniques are perceived as a promising strategy for online installment misrepresentation recognition. Be that as it may, it is a major test to construct high goal social models by utilizing bad quality conduct information. In this work, we mostly address this issue from information upgrade for social displaying. Remove fine grained co event connections of value based credits by utilizingan informationchart.Moreover, theheterogeneous organization implanting to learn and improve addressing complete connections. Especially, we investigate tweaked network installing plans for various kinds of conduct models, for example, the populace level models, individual level models, and summed up agent based models. The exhibition gain of our strategy is approved by the investigations over the genuine dataset from a business bank. Itcanassist delegateconduct models with working on fundamentally the exhibition of web based financial installment misrepresentation recognition. To the best of our insight, this is the primary work to acknowledge information upgrade for differentiated conduct models by carrying out network installing calculations on property levelco eventconnections.
Online payment services have entered into individuals lives. The expanded comfort, however, accompanies intrinsic security chances [1]. The cybercrime including online installment benefits frequently has the attributes of broadening, specialization, industrialization, camouflage,situation,andcross locale,whichmakesthe security anticipation and control of online installment very testing [2]. There is a pressing requirement for acknowledging powerful and far reaching on the online payment
fraud detection. The behavior based technique is perceived as a powerful worldview for online installment extortion recognition . By and large, its benefits can be summed up as follows: Firstly, conduct based strategies take on the non interruption recognitionplantoensuretheclientexperiencewithout client activity in the execution cycle. Furthermore, it changestheextortiondiscoverydesignfromone timeto persistent and can check every exchange. Thirdly, regardless of whether the fraudster mirrors the day to day activity propensities for the person in question, the fraudster should go amiss from the client conduct to acquire the advantage of the person in question. The deviationcanberecognizedbyconductbasedstrategies. Atlonglast,thisconductbasedtechniquecanbeutilized helpfully as a subsequent security line, instead of supplantingwithdifferentsortsofrecognitionstrategies. Notwithstanding, the adequacy of conduct put together techniquesfrequentlydependsintenselywith respectto theadequacyofclientsocialinformation[4].Truly,client social information that can be utilized for online installment extortion recognition are in many cases bad qualityorconfinedbecauseofthetroubleofinformation assortment and client protection prerequisites [5]. As theprimarycommitmentofourworktoreallymodelthe co events among value based credits for elite execution social models. For this reason, to embrace the heterogeneous connection organization, an extraordinary type of the information diagram [6],to successfully address the co events. Here, a network hub (or say an element) compares to a trait esteem in exchanges, and an edge compares to a heterogeneous relationship between various characteristic values. Albeittheconnectionorganizationcancommunicatethe information all the more properly, it can't at long last settle the information defect issue for conduct demonstrating, that is to say, it affects improving the first bad quality information. A viable information portrayal safeguarding these thorough connections can go about as a significant mean of social information improvement. present network portrayal learning (NRL), which successfully catch profound connections
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
[7]. Profound connections compensate for bad quality information in misrepresentation identification and work on the presentation of misrepresentation identification models. By working out the likeness between inserting vectors, more potential connections could be construed. It part of the way tackles the information defect issue. Notwithstanding information upgrade, NRL changes the conventional organization investigation from the falsely characterized element to the programmed learned highlight, which separates profoundconnectionsfromvariousexchanges.
Thefinal performanceofbehavioral modelingforonline fraud detection directly depends on the harmonious cooperation of data enhancement and model enhancement.Differenttypesofbehavioralmodelsneed matching network embedding schemes to achieve excellent performance. This is one of the significant technical problems in our work. We aim to investigate the appropriate network embedding schemes for population level models, individual level models, and models with different generalized behavioral agents. Morespecifically,forpopulation levelmodels,wedesign a label free heterogeneous network to reconstruct onlinetransactionsandthenfeedthefeaturesgenerated in embedding space into the state of the art classifiers based on machine learning to predict fraud risks; while, for individual level models, we turn to a label aware heterogeneous network that distinguishes the relations betweenattributesoffraudulenttransaction,andfurther designmultiplenaïveindividual levelmodelsthatmatch the representations generated from the label aware network.Furthermore, wecombinethe population level and individual level models to realize the complementary effects by overcoming each other’s weaknesses.
Many researchers concentrated on individual level behavioural models to detect abnormal behavior which is quite different from individual historical behavior. These works paid attention to user behavior which was almostimpossibletoforgeattheterminal,orfocusedon user online business behavior which had some different behavioural patterns from normal ones. Vedran et al. [19] explored the complex interaction between social and geospatial behavior and demonstrated that social behavior could be predicted with high precision. Yin et al. [4] proposed a probabilistic generative model combining use spatiotemporal data and semantic information to predict user behavior. Naini et al. [7]
studiedthetaskofidentifyingtheusersbymatching the histograms of their data in the anonymous dataset with the histograms from the original dataset. Egele et al. [8] proposed a behavior based method to identify compromises of high profile accounts. Ruan et al. [3] conducted a study on online user behavior by collecting and analyzing user clickstreams of a well known OSN. Rzecki et al. [20] designed a data acquisition system to analyze the execution of single finger gestures on a mobile device screen and indicated the best classification method for person recognition based on proposed surveys. Alzubaidi et al.[9] investigated the representative methods for user authentication on smartphone devices in smartphone authentication including seven types of behavioral biometrics, which are hand waving, gait, touchscreen, keystroke, voice, signature and general profiling. These works mainly detected anomalous behaviors at the population level that are strongly different from other behaviors, while theydidnotconsiderthattheindividual levelcoherence of user behavioral patterns can be utilized to detect online identity thieves. Mazzawi et al. [10] presented a novel approach for detecting malicious user activity in databasesbycheckinguser’sself consistencyandglobal consistency. Lee and Kim [21] proposed a suspicious URL detection system to recognize user anomalous behaviors on Twitter. Cao et al. [11] designed and implemented a malicious account detection system for detectingbothfakeandcompromisedrealuseraccounts.
Zhou et al. [12] proposed an FRUI algorithm to match users among multiple OSNs. Stringhini et al. [22] designed a system named EVILCOHORT, which can detectmaliciousaccountsonany onlineservicewiththe mapping between an online account and an IP address.
Meng et al. [23] presented a static sentence level attentionmodelfortext basedspeakerchangedetection by formulating it as a matching problem of utterances before and after a certain decision point. Rawat et al. [24] proposed three methodologies to cope up with suspicious and anomalous activities, such as continuous creation of fake user accounts, hacking of accounts and other illegitimate acts in social networks. VanDam et al. [25] focused on studying compromised accounts in Twitter to understand who were hackers, what type of contentdidhackerstweet,andwhat featurescouldhelp distinguish between compromised tweets and normal tweets. They also showed that extra meta information could help improve the detection of compromised accounts.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Under the real time requirement of online payment fraud detection, it is intolerable to perform network embedding operation for every new transaction due to the response latency lead by large computing overhead. Thus, the uniqueness of transaction number (i.e., identifier) directly destroys the possibility of adopting network embedding online. There is no need to embed the identifier, say the transaction number, into the vector space, since it’s not a valid feature to represent userbehavioralpatterns.Interestedintheco occurrence relationships among different behavioral entities rather thantherelationshipbetweenauniqueidentifierand its entities. Therefore, we need generate a new derivative network of transaction attributes based on the native graph, preparing for the network embedding. To propose a novel effective data enhancement scheme for behavioral modeling by representing and mining more fine grained attribute level co occurrences. Adopt the heterogeneous relation networks to represent the attribute level co occurrences, and extract those relationships by heterogeneous network embedding algorithms in depth. To devise a unified interface between network embeddingalgorithmsand behavioral models by customizing the preserved relationship networks according to the classification of behavioral models. Implement the proposed methods on a real worldonlinebankingpaymentservicescenario.
The fraud detection issue in a regular example of online installmentadministrations,i.e.,onlineB2C(Businessto Client) installment exchanges. Here, to procure the casualty's cash, cheats ordinarily contrast from the person in question's everyday way of behaving. This is thecrucial suspicionof the plausibilityofconduct based extortion location. Based on this presumption, the examination local area is committed to planning social models to recognize actually the distinction concerning personal conduct standards. The principal challenge of this issue is to fabricate a great conduct model by utilizing inferior quality social information. Normally, from the two perspectives, there are two relating ways of taking care of this issue: information improvement and modelimprovement.
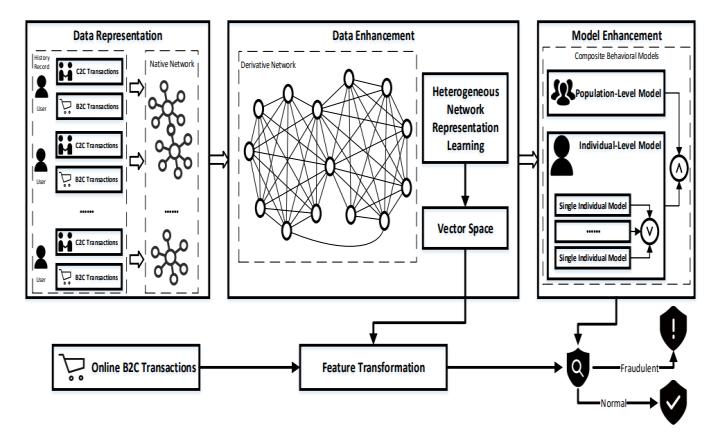
In this work, target contriving the comparing information upgradeplansforthecuttingedgeconduct modelsthatgo about as the all around perceived approaches of model improvement [14]. All the more explicitly, to understand information upgrade for conduct displaying successfully, we take on the connection diagram and heterogeneous organizationinsertingmethodstoaddressandminemore finegrained co events among value based ascribes. Then, at that point, in view of the upgraded information, the comparing social models (or improved conduct models) can be embraced to acknowledge misrepresentation discovery. Thereout, as outlined in Fig. 1, the entire progression of the information driven misrepresentation identification framework comprises of three primary parts: information portrayal, information upgrade and modelinformationupgrade.
Online payment transaction records are typically social information that comprise of various elements addressing the properties in exchanges. Lossless Native Graph. Each quality of an exchange is viewed as the element.Foreveryexchange,welayouttheconnections between every substance and its identifier, e.g., the exchange number. Moreover, we join every identifier a nametosignifywhetherthisexchangeisfalseortypical. As indicated by the property of exchanges, the arrangement of exchanges, meant by T , can be isolated intotwodisconnectedsubsets,i.e.,theordinaryandfake exchange sets, signified by T0 and T1. Since an element might show up in various exchanges, we utilize the co
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
eventrelationshiptoadditionallyassociatethediagrams shapedbyvariousexchanges.
In this work, use network implanting procedures to understand the information upgrade for conduct demonstrating. The organization construction to be protectedoughtstillupintheairbeforeanorganization implanting activity is sent off. The organization implantingthatprotectstheorganizationconstructionof local chart can't straightforwardly help social demonstrating for online installment misrepresentation identification. Under the continuous necessity of online installment extortion identification, it is unbearable to perform network inserting activity for each new exchangebecauseofthereactioninactivityleadbyhuge processing upward. In this manner, the uniqueness of exchange number (i.e., identifier) straightforwardly obliterates the chance of taking on network implanting on the web. There is compelling reason need to insert the identifier, say the exchange number, into the vector space,sinceit'sanythingbutasubstantialcomponentto address client standards of conduct. Redone Derivative Networks. In the information we gathered, there are bothB2CandC2Cexchanges.TheextentofcheatsinC2C exchanges is tiny to that in B2C exchanges. In addition, the component of C2C misrepresentation exchanges is basicallynotthesameasthatofB2Cones.Subsequently, limit the extent of this work into online B2C false exchangeDetection.UseC2Cexchangesasadvantageous (excessive) data for separating the connections among conduct specialists of B2C exchanges, i.e., account numbers,fromthelocaldiagram.
Inthiswork,weorderclientsocialmodelsintotwosorts as per the granularity of conduct specialists, i.e., the populace level model and individual level model. Populace Level Models. The populace level models distinguish the extortion by identifying the populace level social irregularities, e.g., conduct exception recognitionandabuselocation.Theclassifiersinviewof social information can go about as this sort of models. For information upgrade for them, we really want just information refactoring for classifiers by safeguarding theco eventrecurrenceofsocialcredits.Tothisend,we create a subsidiary organization where the vertices are exchange credits and the edges with loads address the cooccurrence recurrence, failing to assess exchange names. Individual Level Models. The individual level
models distinguish the extortion by recognizing the conduct abnormalities of people. They are viewed as a promising worldview of extortion location. The viability vigorously relies upon the adequacy of social information. To assemble the individual level standard/typical conduct models, we really want address the routineness and ordinariness of exchange socialinformation.Then,weoughttoconsiderthemarks while producing the subordinate organization. Separate positive connections created from T0 and negative connectionsproducedfromT1.Thepositiverelationship improves the connection between's the specialists in question, while the negative relationship debilitates the relationship. say such a subsidiary organization is mark mindful.
A single agent behavior model can only give a certain fraud judgment. The normal judgment may not reliabledue to the release of transactions that cannot be checked. In this work, we imitate the one veto mechanism to synthesize the final results returned by multi agent models. That is only an agent behavioral model returns a judgment marked as fraud, the final resultismarkedfraud.
The transaction is detected as fraudulent transactions if and only if the result from both models are judged as fraudulenttransactions.The consistencyofjudgmenton fraudulent transactions reduces the probability of misjudgmentof normal transactions,andensuresthatit has better performance than a single model, i.e., the population model or individual model. For different performance objectives, other combinations can be also tried,whichwillbereservedforfutureresearch.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
dataset. They outperform the stateof the art classifiers with lightweight feature engineering methods. Therefore, our methods can also serve as a feasible paradigm of automaticfeatureengineering.
There are some interesting issues left to study: (1) An interestingfutureworkistoextendthedata enhancement scheme into other types of behavioral models, e.g., the group level models and generalized agent based models, except the population level and individual level models studied in this work. (2) It would be interesting to investigate the dedicated enhancement schemes for more advancedindividual level models,sincethe adoptednaive individual level model does not fully capture the advantages of the proposed data representation scheme based on the techniques of heterogeneous network embedding. (3) It is anticipated to demonstrate the generality of the proposed method by applying it to differentreal lifeapplicationscenarios.
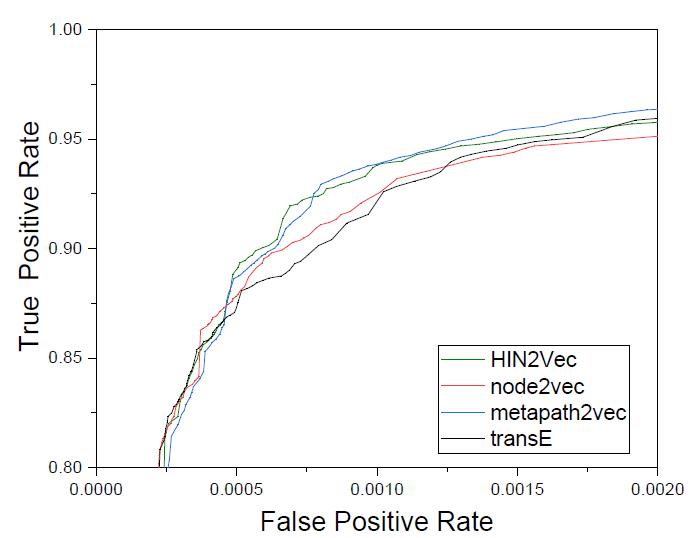
ROC curves of different network embedding methods in the population level model. We observe that all models cooperating with different network embedding methods have a similar performance. HIN2Vec and metapath2Vec havea betterperformancethannode2vec andtransE.The lower performance of node2vec mainly stems from its inability to distinguish the types of nodes. In transE, the method focuses on resolving relationships between different entities but taking no account of the weight of relationships. Most embedding methods are feasible as dataenhancements,withonlyslightdifferencesintermsof performance.
For behavioral models in online payment fraud detection, An effective data enhancement scheme by modeling co occurrence relationships of transactional attributes. Accordingly, we design customized co occurrence relation networks, and introduce the technique of heterogeneous network embedding to represent online transaction data for different types of behavioral models, e.g., the individual levelandpopulation levelmodels.Themethods are validated by the implementation on a real world
[1]B.Cao,M.Mao,S.Viidu,andP.S.Yu,“Hitfraud:Abroad learning approach for collective fraud detection in heterogeneous informationnetworks,”inProc.IEEEICDM 2017, New Orleans, LA, USA, November 18 21, 2017, pp. 769 774.
[2] M. A. Ali, B. Arief, M. Emms, and A. P. A. van Moorsel, “Does the online card payment landscape unwittingly facilitatefraud?”IEEESecurity&Privacy,vol.15,no.2,pp. 78 86,2017.
[3]X.Ruan,Z.Wu,H.Wang,andS.Jajodia,“Profilingonline socialbehaviorsforcompromisedaccountdetection,”IEEE Trans. Information Forensics and Security, vol. 11, no. 1, pp.176 187,2016.
[4]H.Yin,Z.Hu,X.Zhou,H.Wang,K.Zheng,N.Q.V.Hung, and S. W. Sadiq, “Discovering interpretable geo social communities for user behavior prediction,” in Proc. IEEE ICDE 2016, Helsinki, Finland, May 16 20, 2016, pp. 942 953.
[5]Y. A.DeMontjoye,L.Radaelli,V.K.Singhetal.,“Unique intheshoppingmall:Onthereidentifiabilityofcreditcard metadata,”Science,vol.347,no.6221,pp.536 539,2015.
[6] A. Khodadadi, S. A. Hosseini, E. Tavakoli, and H. R. Rabiee, “Continuous time user modeling in presence of badges: A probabilistic approach,” ACM Trans. Knowledge DiscoveryfromData,vol.12,no.3,pp.37:1 37:30,2018.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072

[7] F. M. Naini, J. Unnikrishnan, P. Thiran, and M. Vetterli, “Where you are is who you are: User identification by matching statistics,” IEEE Trans. Information Forensics andSecurity,vol.11,no.2,pp.358 372,2016.
[8] M. Egele, G. Stringhini, C. Kruegel, and G. Vigna, “Towards detecting compromised accounts on social networks,”IEEETrans.DependableandSecureComputing, vol.14,no.4,pp.447 460,2017.
[9] A. Alzubaidi and J. Kalita, “Authentication of smartphone users using behavioral biometrics,” IEEE Communications Surveys and Tutorials, vol. 18, no. 3, pp. 1998 2026,2016.
[10] H. Mazzawi, G. Dalaly, D. Rozenblatz, L. Ein Dor, M. Ninio, and O. Lavi, “Anomaly detection in large databases usingbehaviouralpatterning,”inProc.IEEEICDE2017,pp. 1140 1149.
[11]Q.Cao, X.Yang,J. Yu,andC.Palow,“Uncoveringlarge groups of active malicious accounts in online social networks,”inProc.ACMSIGSAC2014,pp.477 488.
[12]X.Zhou,X.Liang,H.Zhang,andY.Ma,“Cross platform identification of anonymous identical users in multiple social media networks,” IEEE Trans. Knowledge and Data Engineering,vol.28,no.2,pp.411 424,2016.
[13] T. W¨ uchner, A. Cislak, M. Ochoa, and A. Pretschner, “Leveraging compression based graph mining for behavior based malware detection,” IEEE Trans. Dependable Secure Computing, vol. 16, no. 1, pp. 99 112, 2019.
[14] T. Chen and C. Guestrin, “Xgboost: A scalable tree boosting system,” in Proc. ACM SIGKDD 2016, CA, USA, August13 17,2016,pp.785 794.
[15] B. Jia, C. Dong, Z. Chen, K. Chang, N. Sullivan, and G. Chen, “Pattern discovery and anomaly detection via knowledge graph,” in Proc. FUSION 2018, Cambridge, UK, July10 13,2018,pp.2392 2399.
[16] P. Cui, X. Wang, J. Pei, and W. Zhu, “A survey on network embedding,” IEEE Trans. Knowledge and Data Engineering,vol.31,no.5,pp.833 852,2019.
[17] M. Abouelenien, V. P´erez Rosas, R. Mihalcea, and M. Burzo, “Detecting deceptive behavior via integration of discriminative features from multiple modalities,” IEEE Trans. Information Forensics and Security, vol. 12, no. 5, pp.1042 1055,2017.
[18] W. Youyou, M. Kosinski, and D. Stillwell, “Computer basedpersonalityjudgmentsaremoreaccuratethanthose made by humans,” PNAS, vol. 112, no. 4, pp. 1036 1040, 2015.
[19] V. Sekara, A. Stopczynski, and S. Lehmann, “Fundamental structures of dynamic social networks,” PNAS,vol.113,no.36,pp.9977 9982,2016.
[20] K. Rzecki, P. Plawiak, M. Niedzwiecki, T. Sosnicki, J. Leskow, and M. Ciesielski, “Person recognition based on touch screen gestures using computational intelligence methods,”InformationScience,vol.415,pp.70 84,2017.
[21] S. Lee and J. Kim, “Warningbird: Detecting suspicious urls in twitter stream,” in Proc. NDSS 2012, San Diego, California,USA,February5 8,2012,vol.12,pp.1 13.
[22] G. Stringhini, P. Mourlanne, G. Jacob, M. Egele, C. Kruegel, and G. Vigna, “EVILCOHORT: detecting communities of malicious accounts on online services,” in Proc.USENIXSecurity2015,Washington,D.C.,USA,August 12 14,2015,pp.563 578.
[23] Z. Meng, L. Mou, and Z. Jin, “Hierarchical RNN with static sentence level attention for text based speaker change detection,” in Proc. ACM CIKM 2017, Singapore, November06 10,2017,pp.2203 2206.
[24] A. Rawat, G. Gugnani, M. Shastri, and P. Kumar, “Anomaly recognition in online social networks,” International Journal of Security and Its Applications, vol. 9,no.7,pp.109 118,2015.
[25] C. VanDam, J. Tang, and P. Tan, “Understanding compromisedaccountsontwitter,”inProc.ACMWI2017, Leipzig,Germany,August23 26,2017,pp.737 744.