International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
ONLINE DOCUMENT VERIFICATION
1,2,3 Affiliated By AKTU, Dept of Computer Science, Ghaziabad, Uttar Pradesh, India (Students, Dept of Computer Science, Krishna Engineering College, Ghaziabad, Uttar Pradesh, India) ***
ABSTRACT
Overtheyearstherehavebeenagreatneedofeasyandfastedmeansofverifydocuments(likemarksheets,certificatesetc.) toreducethelevelofdocumentsforgeryandtoeasethestressandalsosavethetimeofverificationwhichisdonemanually today.Incaseofresultandcertificatesanemployeroranybodyconcernwillhavetocomeorsenddelegatetoschooltoverify a particular certificate, some employer never did and this has resulted on accepting a forge certificate. The system can be implemented as a standalone site and/or an application or can also be embedded in an already existing institution official website.
This software is basically a verification service to ease the work of verification process in all the fields and to decrease the paper workload. Verification process in other words is very important nowadays for a lot of companies. It actually allows companiestovalidatetheinfoprovidedbytheiremployeesaretrueandcorrectwithoutanydiscrepancies.
IMPLEMENT: ThiswillbeimplementedbyusingabackenddatabaseofMySQLwitha PHPcodeandwillconsistofawebpageforitseaseuse.Itwouldhavethefollowingusertypes:
• Adminwillbasicallyapproveverifierloginandgivefinalapprovalforasubmitteddocument.
• Theverifierwillvalidatethedetailsandattachmentsthathavebeenuploadedbyaloggedinusers.
• Theuserwillregisterandonceregisteredtheywillhaveadashboardforrulesandsystemguide.
Infuturethis project will canactasa core to everysoftware requiring database.In thiswecanadda downloadoption for a specificcategoryaspertherequirementsofthecandidateswhosedocumentswearefetching
KEYWORDS: InformationSystem,Verification,OnlineVerificationandValidation,Authentication,FraudDetection
I. INTRODUCTION
ONE of the most frequently used means of exchanging information among people is the Internet. This method of electronic data transmission breaks all the distance barriers. Furthermore, everyone should be able to browse the same websites and have the opportunity for equal user experience in the Internet. In other words, the Internet should be usable by everyone. OnlineDocumentVerificationsystemrepresentsthedirection offuturedocumentauthenticatingdevelopment.Promotionof OnlineDocumentVerificationsystemwillimprovethespeedandquality (Nwachukwu NwokeaforK.C,December 2015) Its background is centered on the need to adopt online verification system that will save the huddles of manual verification method.
Thiswillenableanybodytoverifyaninstitutioncertificateonline,withouthavingtocomedowntotheschool/institutiontodo soortocarryoriginaldocumenteverywhere.Allthatisrequiredtologintotheverificationportaland,thentheoriginalcopy ofthatwillbedisplayedonthescreenalongwiththemessageaspertheauthenticityofthedocument.
If the document is valid then the document will be displayed with the message that the document submitted by the user is validandauthenticate.Butifthedocumentnumberisinvalid,thefollowingmessagewillbedisplayedonthescreen“Invalid
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
document as per our records as we don’t have details of this person, it is either you made a typing mistake or the owner haven’tprovidedthecorrectinformation,Verifyandtryagain
II. METHODOLOGY
Documentverificationistheelementarystepthathastobedoneafterenrollmentorregistrationinanyorganizationorwhere verificationismustlikepassportoffice,bordersstations,duringanybanktransactionandmanymore.Forthiswecanuseany unique thing for identification like Aadhar card, Passport, PAN number and other things. We use 12 digit Aadhar card number for identification in this. Whole system will be online and mechanized , the system will be personlized to have each certificates that are linked to the student’s detail . Our software should automatically verified all the required documents by enteringtheaadharnumber.Thissoftwareiswebbasedaswellasmobileapplication.Anypersonororganizationthatwant to check the authentcity of the documnents that enter the aadhar number as shown in fig 1 . Its main objective to make verificationeasyforourselfsandtheorganizationbyusingthissoftwareTooptimizethe processbyconsideringvarioususer constraintsaswellasotherinformationlikelocationofactivities,theirduration,andtravelsignalstrengthdependingonmode ofinternetconnectivity
III. MODELING AND ANALYSIS
SHA 256
The SHA 256 compression function operates on a 512 bit message block and a 256 bit intermediate hash value. It is essentiallya256 bitblockcipheralgorithmwhichencryptstheintermediatehashvalueusingthemessageblockaskey.Hence therearetwomaincomponentstodescribe:
(1) theSHA 256compressionfunction,and
(2) theSHA 256messageschedule
Wewillusethefollowingnotation
BitwiseXOR BitwiseAND BitwiseOR BitwiseComplement
Mod2^32addition
Rightshiftbynbits
Rightrotationbynbits
Table1:NotationforSHA 256
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
a) Asthissoftwareisconnectedtothecentralserversoyoucanaccessthedocumentanytimeandanywhere.
b) Asthissoftwareisavailableforwebaswellasmobileapplication
IV. RESULT
The system needs various hardware and software. The Hardware consists of Operating system like windows, Linux etc. and the project contain web server, XAMPP win32 7.0.9 0 VC15 installer for (Apache Web Server). The functional requirements consist of webpage and the web application. The system will identify the documents like marksheet and other government certificates.
The certificates stored in the database and it can only access by the admin, the user can upload the document and the rest process is done by the other authorities like for marksheet of CBSE verified by CBSE authorities etc. The software contains differentmodulesandeverymodulehasitsspecificfunctionality.Everycompanyhasitsownidandpassword,theycanverify documentseasily.Ifanycompanywantstoidentifythedocument,thenthe Tokenisgeneratedontheusersideandbyusing thatToken the companycanalsoidentify the candidate’s documents, buttheycan’tupdate,change or deletethecandidate’s certificates.Theresultoftheprojectandtestresultsareasfollows:
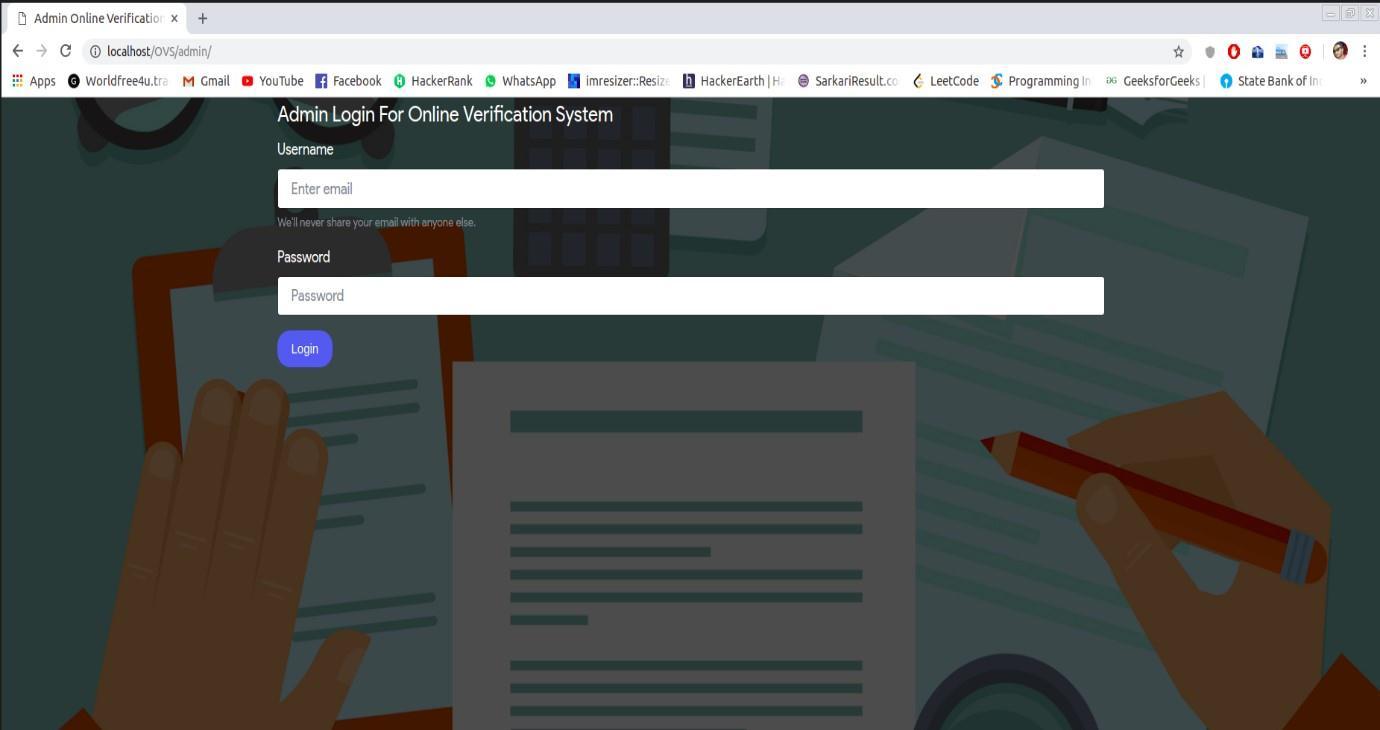
a) Login and registration
Thisistheadminfrontpagewhichwill beusedforonlineverificationofdocument.Itcontainsregistrationpage forthe newuserandloginpagefortheexistinguser.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072

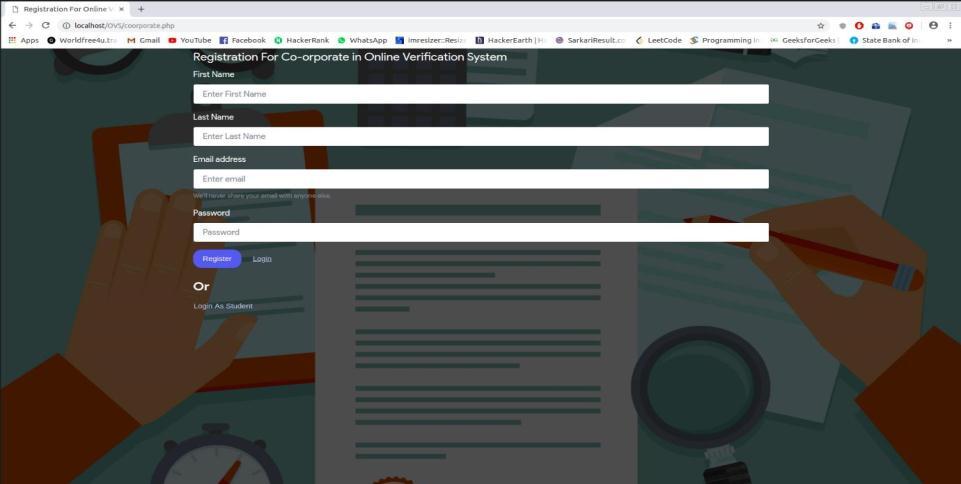
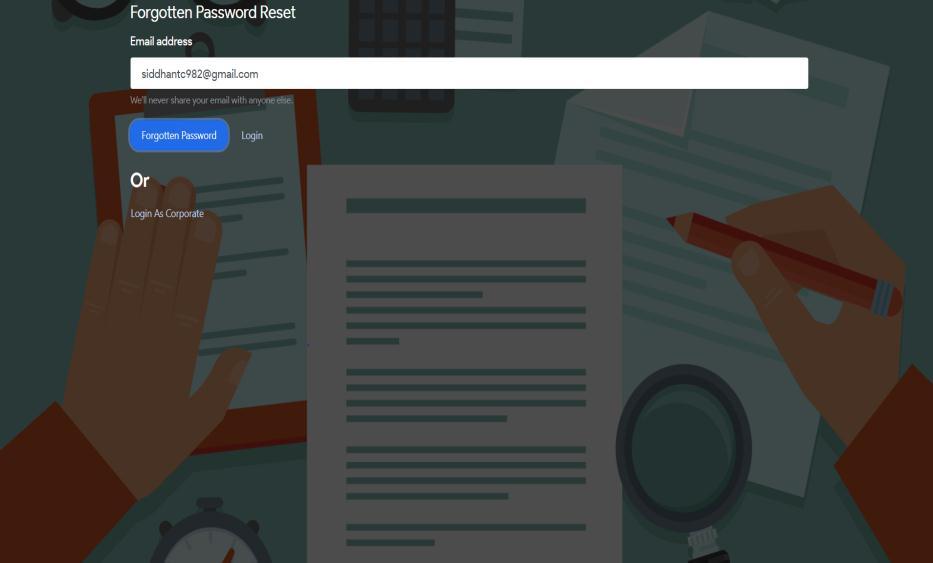
Fig 5 : shows the registration for online verification
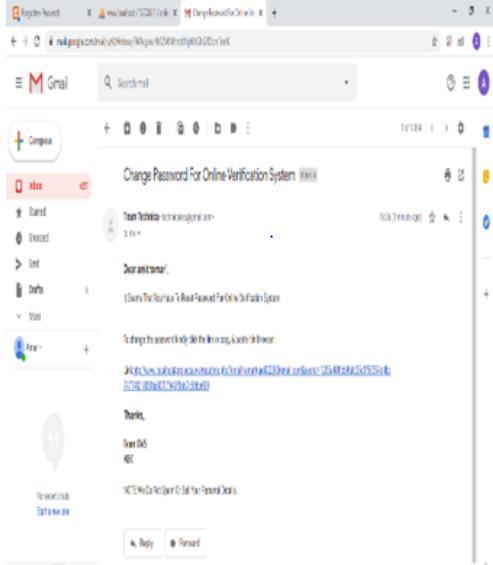
b) Notification and verification link to change Password
Thisinterfacewillpopupwhenuserclicksthe“forgottenpassword”link.Theverificationlinkforthepasswordchangewill be senttotheregisteredemailid,theusercanchangethepasswordfromthelink.Fig4.andFig.5displaytheusernotificationand verificationlinktochangethepassword.
Fig 6 : User notification to Change Password
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Fig 7: Verification Link to Change Password
c) Document Verification
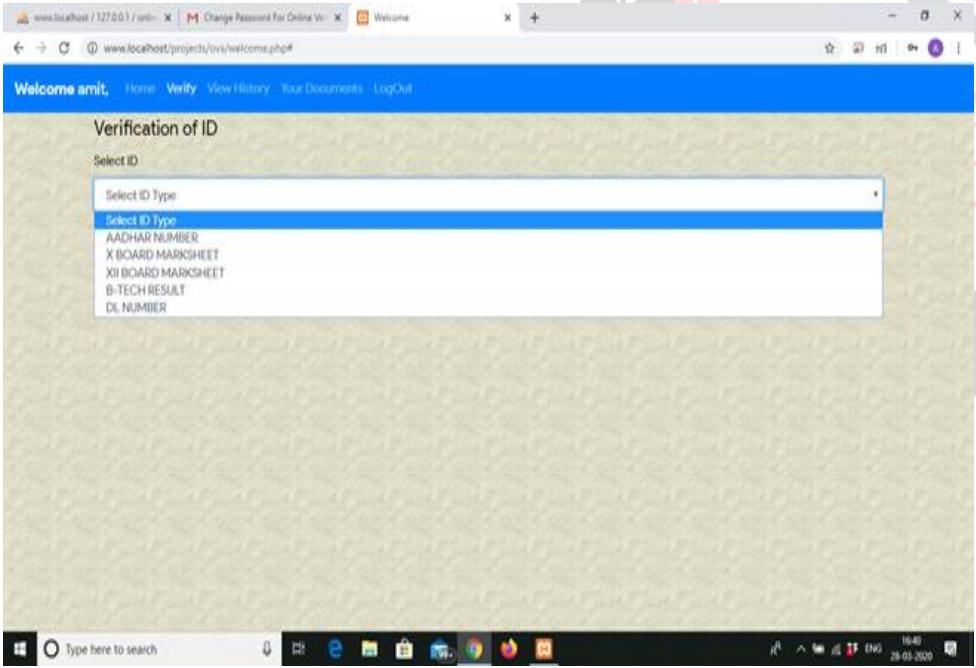
Aftersuccessfulregistration,thesystemwillshowtypeofdocumentandusercanselectthedocumentfromthe givenoption andthencansuccessfullyuploaditonthesystemandafterthatsystemwillverifythatdocument.Fig.3.showstheDocument verificationprocess.
Fig 8 : Document verification
d) Token generated for verifying document
TheTokenisgeneratedfortheverificationpurpose,whenanycorporateoranyotheruserisidentifyingourdocuments.The Token is generated for 30 minutes and the company can only identify user document, they don’t have any access for the deletionandupdationofanydocuments.Fig.6.showstheTokengeneratedforverifyingcertificate.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072

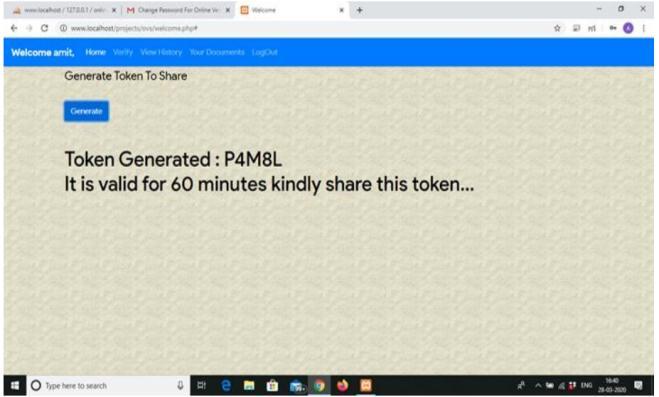
Fig 9 : Token generated for verifying Document
V. CONCLUSION
Theproposedverificationsystemhelpsthepotentialclientstoverifytheirdetailsovertheinternet Itgivestherealpossibility toverifythedocumentscanbeplacedinsecureenvironment.Thissystemishandyatthoseareaswheremanpowerisneeded. This system provides the online platform to store the documents and certificates, by which a user can easily carry his/her documentswithoutphysicallycarryingthem.ThissystemenablesanyorganizationtomeetlegalobligationsincludingCounter TerrorismFinancingandAnti MoneyLaundering.Itsavestime and money, reduce many errorsat minimum bycomparing it withmanualmethodwithareductionfactor.Thecredentialsarevisuallyverifiedifpresentedphysicallyorcheckedagainstthe authentic data source if presented online. Any individual, can easily verifies the authenticity and validity of the documents givenbytheperson.TheauthorizedaccesscanonlybegivenafterOTPverification.Beforethesubmissionofdocuments,they wouldbeverifiedasthedocumentswouldbeprovidedbytheactualpersonaswellasweourselveswouldbeverifyingthem personally.SecurityofthepersoncanbeassuredasthesessionwouldbeloggedoutafteralimitedtimeafterOTPverification andtore accessthedocumentsOTPverificationisrequiredagain.Takingscreenshotisalsonotallowedduringtheaccessing ofthedocuments.OnlineVerificationsystemoffersuserconvenienceandsignificanteasetoemployersastheycangetoriginal documents more easily and faster than standard manual authentication methods. All though computerized verification systemshavea numberofleadsovermanualones,thereafewchallengesthatmustbeovercomeinorderthattheirbenefits may be fully realized. First of all, there is the high initial cost of running such a system, as it is typical for all computerized systems.Hence,thissystemprovidestwofacilitiestotheuserlikestoringdocumentsonlineandverifyingthemonlineaswell astheywouldbesecurealso. VI. REFERENCES
