International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
S.Thiruvenkatasamy1, L.Barathkumar2, P.Navinkumar3, K.Ranjith4, A.Vigneshwaran5
1Assistant Professor, Dept.of Computer Science and Engineering(CSE), Nandha College of Technology, TamilNadu, India
2,3,4,5UG Student, Department of CSE, Nandha College of Technology, TamilNadu, India ***
Abstract - In recent years, the blockchain has gained popularity, and its underlying consensus algorithms have become the subject of research. Most consensus mechanism research is now focused on public blockchains and is based on existing consensus mechanisms or complex distributed algorithms. Various application scenarios based on the consortium blockchain have been developed, although few researchers have focused on proprietary consistency algorithms. Electronic voting has gradually replaced paper voting to avoid redundancy and inconsistencies. Due to security and privacy vulnerabilities noticed over time, the historical viewpoint offered in the last two decades implies that it has not been as successful. This paper proposes a methodology for ensuring data security by employing effective hashing techniques. This paper introduces the concepts of block formation and block sealing. The implementation of a block sealing concept aids in the customization of the blockchain to match the requirements of the polling process. It is advised that aconsortium blockchain be used, which ensures that the blockchain is held by a governing body (e.g., an election commission) and that unauthorized access from the outside is impossible. The framework suggested in this study uses the customizable blockchain technique to discuss the effectiveness of the polling process, the value of hashing algorithms, block formation and sealing, data accumulation, and result declaration. It claims to understand blockchain's security and data management concerns and to provide a better representation of the electronic voting process.
Key Words: Blockchainvoting,I voting,E voting,Rankedvotingsystems,SHA,Futurevoting.
Theimplementationofe votinghasthesameobstaclesasanyother"e" relatedtopic,suchase government.Legislatorsor administratorsmayanticipatesimplyuploadingapaperversionofaserviceorprocesson theinternet.Unfortunately,the realityismorecomplicated,andnowhereisthismoretruethanelectronicvoting.Institutionssuchasthe'ElectionCommission' wereestablishedinmanyparliamentarydemocraciestoimprovethevotingprocess.
Alongwithestablishingtheprocedureandlegislationforconductingelections,theinstitutionsestablishedvotingdistricts, electoralprocesses,andballotingsystemstoaidintheconductoftransparent,free,andfairelections.Sincetheinceptionofthe votingsystem,theconceptofsecretvotinghasbeenintroduced.
Becausepublicfaithindemocraticsystemsisgrowing,publictrustinvotingsystemsmustn'tdeteriorate.SincetheCommitteeof MinistersadoptedtheCouncilofEuropeRecommendationonlegal,operational,andtechnicalstandardsfore votingin2004, therehavebeennumerousdevelopmentsinthefieldofe voting.
Some countries no longer use e voting, while others have experimented with it and decided not to implement it. Other countries,ontheotherhand,arecontinuingtorunpilotprogramsandimplemente voting.Otherelections,suchasstudent councilsoryouthboards,haveusedelectronicvoting.Somecountriesororganizationswanttostartpilotinge votingschemes buthaven'tlookedintoallthepossibilities.Thisdocumentwaswrittenspecificallyforthem.
Wewilladoptaprocesstoaddressthefollowingactivities.
Thesystemmodelinghelpsindrawingtheentiresystemonpapertodevelopa deep understandingofthesystemandto identifyerrorsandflawsthatcanbeobservedbeforethesystemcanbeimplemented.
The e voting process requires the features like privacy, security, anonymity, and verifiability as the core function of this solution, it is important that the choice of the underlying technology is consistent to meet these challenges. It has been identifiedthatBlockchaintechnologysufficientlydealswithallsuchchallenges.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Basedonthesystemmodel,thesystemwillbedevelopedandwillbeintegratedwiththebaselinetechnology.
Any voting system should have voter authentication. A voting system must ensure that a voter:
Isexactlywhotheyclaimtobe
Hastherighttovotewhenauthenticatingthem.
Hasnotyetvoted
Asystemthatdoesnotauthenticatevoterswillbeunabletopreventduplicatevoting,voterimpersonation,andanotherelection tampering.Inoldervotingsystems,pollingstationstafffrequentlyconfirmvoteridentitymanually.Inonlinevotingsystems, however,digitalidentityverificationtechniquesshouldbeimplemented.
A person's identity can now be verified using the following information:
Digitalidentification
Keystopersonalsecurity
Authenticatedmobiledevices
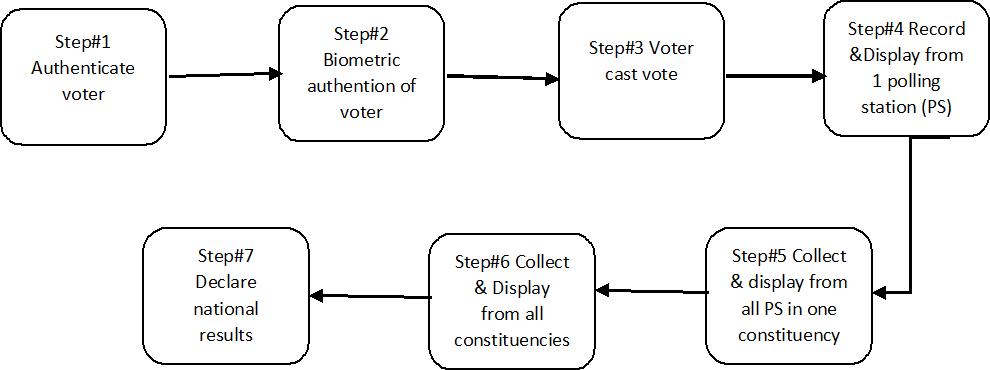
Thevoterisrouted(Fig 1)tothevotingscreentocasthisballotafterpassingtheauthenticationcheck.Eachcandidate'sname andrelevantpartyinsigniaaredisplayedonthevotingmachine,andthevotercanvoteashelikes.Thevoter'svoteisrecorded ontheconfirmationscreen,andthevoter'sconfirmationis sought.
a) Avotercan onlyvoteonce, andonce thatvote ismade, thevoter'svoting record is marked as"voted,"making it impossibleforthemtovoteagain.Avoter'snamecanbeblockedorremovedfromthelistofeligiblevotersforthe currentelectionsafterhehascasthisvote.
Hedevelopedamethodinwhichvoterscanvotemanytimes,witheachvotecancelingthepreviousoneinhis workon internetvoting.Ifthevotingprocedureistobecompletedinonedayandroughly110millionpeoplearerequiredtovote,asin Pakistan,thisdoesnotappeartobeapracticalapproach.
b)Thepollingprocesscontinuesuntilthevotingtimeendsorallvotersonthevoterlisthavecasttheirballots.
c)Thepollingstationresultsareannounced,togetherwiththevotetotalsforeachcandidate.Theprocessisrepeatedfor allvotingstationsintheconstituency,withthesumofallpollingstationresultsdeterminingtheconstituency'soutcome. Similarly,alloftheconstituencyresultsarepooledtoprovidenationalelectionresults.Thevotingprocedureandthe resultsaredepictedinthisdiagram.
d)Fig 2illustratesthemethod'sthree layeredoperation.Thefirstlayer(Who)definesthesystem'sparticipants,suchas voters,pollingemployees,andpollingmachines,whocaninteractwiththepollingprocess.Thesecondlayer(How)is focusedondeterminingthenecessarytoolsandtechnologiestoensurethattheprocessrunssmoothly.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
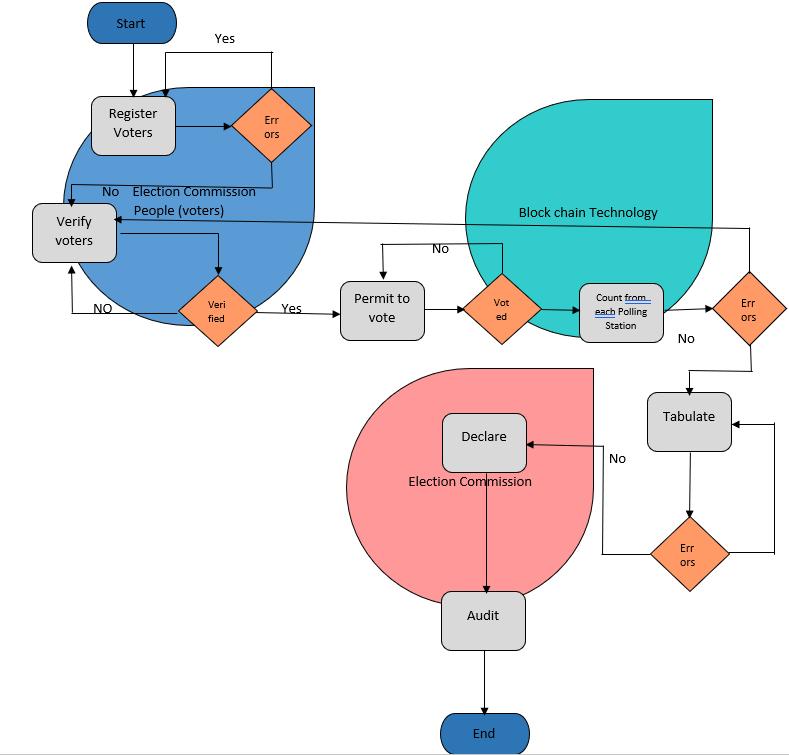
Fig-2 : Theelectronicvotingprocesswithinstitutionsinvolved
Previouseventsinaperson'slifehavebeentimestampedandconnected.Theyareimpossibletoreverseorduplicateinanyway. Manyothersarealsoawareoftheevents'correctnessandmaydouble checkthefactsifnecessary.Theblockchaincomesinto playhere,asitcreatesanirreversible,distributed,publicledgertostoredatachunks.Theeventscanberepresentedasdata blocksthatareconnectedtoformaninvisibleblockchainofourlives.Acomputationalblockchainissimilarinconcept.Inthe past,acomputationalblockchainwasanopenanddistributedledgerthat,dependingontheconditions,couldbeaccessedand amendedbyanybody.Thegoalistoestablishatrust basedsysteminwhichrecordscannotbealtered.
Thethreetypesofblockchainarepublicblockchain,privateblockchain,andconsortiumblockchain.Publicblockchains,suchas BitcoinandEthereum,allowanyone,fromanywhere,tojoinandberelievedathisdiscretion.This isdemonstratedbythe complicatedmathematicalfunctions.Theprivateblockchainisthecorporation'sinternal publicledger,andthecompanythat ownstheblockchainprovidesaccesstoit.Blockconstructionandminingaremuchfasterinaprivateblockchainthaninapublic blockchainsincetherearefewernodes.Insteadofconsensus,membershipstandardsaredevelopedtobettermanageblockchain transactionsintheconsortiumblockchain,whichexistsamongcorporationsorgroupsoffirms.Thisstudyusesaconsortium sincetheblockchainwillberegulatedbyanationalauthorityinthecountry.
Theblockchain'sfoundationistheblock.Thetransactionstobewrittentothesystemarecontainedinthebodyofablock,which hasaheaderandabody.Theblock'sheadercontainsinformationabouttheblock,suchastheprevioushash,noncevalue,and difficulty,aswellasthetimestampsoftheblockandtransactions.Thelengthoftheblockisunknown.however,itisthoughtto bebetween1and8megabytes.Theblock'sheaderuniquelyidentifiestheblocktobeput.
The technique of converting an arbitrary and variable size input to a fixed size output is known as hashing. Encryption converts data into a secure format that cannot be read unless the recipient possesses a key. The data can be any size in
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
encryptedformandistypicallyjustaslongasitisunencrypted.ByusingSHA 256hashing,a512 bitstringofdatacanbe turnedintoa256 bitstring.
Table 1 : Hashingalgorithms.
Name Input block size Message limit (bits) Hash code size
MD5 512 264 128
SHA 1 512 264 160 SHA 256 512 264 256 SHA 512 1024 2128 512
TheMD5algorithmgivesa128 nitor32 characterhashoutputandiswidelyusedforhashing.MD5,whichcameafterMd2, Md3,andMd4,isthemostcurrentalgorithminthesequence.Thealgorithmwasdesignedasacryptographichashingapproach. however,ithasweaknessesthatlimitthenumberofuniquehashvaluesitcangenerate,makingitvulnerable.In1996,Hans DobbertincreatedtheRIPEMD(RaceIntegrityPrimitiveEvaluationMessageDigest)familyofhashalgorithms.Thisapproach was developed as a safer alternative to MD5. Some of the versions that have emerged throughout time are RIPEMD 128, RIPEMD 160,RIPEMD256,andRIPEMD 320.
The MD5 technique is frequently used for hashing and produces a 128 nit or 32 character hash output. The most recent algorithminthesequenceisMD5,whichcomesafterMd2,Md3,andMd4.Althoughthetechniquewasintendedtobeusedfor cryptographichashing,ithasflawsthatlimitthenumberofuniquehashvaluesitcangenerate,renderingitvulnerable.Hans DobbertindevelopedtheRIPEMD(RaceIntegrityPrimitiveEvaluationMessageDigest)hashalgorithmfamilyin1996.This methodwascreatedtobeasaferalternativetoMD5.RIPEMD 128,RIPEMD 160,RIPEMD256,andRIPEMD 320aresomeof thevariationsthathaveappearedovertime.
Theproofofworkideadealswithmining/blockcreationinsuchawaythatitcanbedemonstratedthatasignificantamountof effortwasputintosolvingthemathematicalissuegivenbytheblockchain'sdevelopment.Witheachnewblockconstructed,the mathematicaldifficultygrows,makingblockconstructionachallengingandgratifyingactivity.Tointroduceincreasinglevelsof complexity,hashfunctions,Markletrees,andthenoncevalueareused.
Theproofofstakeconceptisbasedontheblockchain'sidentificationofstakes.Theownersofassetshaveahigherpriority whenitcomestoformingblocks.It'simpossibletodismissthenotionthatafewblockauthorscontroltheentireblockchain throughtheirholdings.Thismethodcanbeemployedinaconsortiumblockchainoraprivateblockchainwheretheholding corporationsneedadministrativeaccess.
Theproofofstakeconceptisbasedontheblockchain'sidentificationofstakes.Theownersofassetshaveahigherpriority whenitcomestoformingblocks.Thismethodcanbeemployedinaconsortiumblockchainoraprivateblockchainwherethe holdingcorporationsneedadministrativeaccess.
The proofs described above are commonly used in bitcoin mining and are well known in the literature. However, the applicationofblockchainvariesinvariousindustries,andtheproofspresentedinthissectionmaynotbeapplicableinpractice; however,basedonthenatureoftheapplication,amodificationtotheimplementationmayberequested.Theanswertothe questionisdeterminedbythenatureoftheapplicationareawhereblockchaintechnologywillbedeployed.
Thisstudyexaminestheuseofblockchaininsecureelectronicvoting,anditisfoundthatthecurrentblockchainmayrequire somechangesforthefollowingreasons.CreationofBlock,Blockcreationisacriticalpartoftheelectionprocess;withoutit, voterswillbeunabletorecordtheirballots.Asaresult,thebricksmustbeconstructedwithoutfirstsolvingthemathematical
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
puzzlesthatcomprisetheevidenceoflabor.Proofofstakeandproofofburnwillbeirrelevantbecauseeachproducedblockwill beheldbyasingleindividual,asitwillbeaconsortiumblockchain.SealingofBlocks:
Voterscancastballots,andtheirchoicesarerecordedinblocks.Theblocksmustbesealedusinghashfunctions,theMerkle tree,andthenoncefunctiononcethepollingperiodhasended.Sealingisnotmentionedinanyoftheextanttheories.
Becausethevotingprocesstakesbetween8and10hours,theblocksmustbeconstructed,sealedand securedduring thatperiod.Proofofwork,proofofstake,andproofofburnarenotsuitableforuseintrustworthyelectronicvotingsincethey requirealengthyprocesstoapply.
Afterthepollingprocessiscompletedandtheresultsarepublished,therewillbenoneedtocontinueminingorblock generation.Theproofoflaborandproofofstakealgorithmsconsume(waste)asubstantialamountofcomputationalresources overtimebecausetheyrecursivelyrepeatthemselves.Becausethesuggestedsystemusesfewresources,itiscost,time,and energy efficient.
Giventhelimitationsofexistingalgorithms,it'svitaltobuildanalgorithmthatcansolvetheproblemwhilealsoovercoming thelimitationsofexistingalgorithmswhenappliedtothefieldoftrustworthiness.Thepreviousblock'shashismixedwitha freshrandominteger,andtheresultishashedonceagaintoensurethatthehashoutcomefunctioncannotbesolvedwithoutthe abilitytotackleNP hardproblems.
Thegoalofblockchain basedelectronicvotingistoprovideasafevotingsystemthatcangainthetrustofallstakeholders, includingvoters,politicalparties,andgovernmentagencies.
Thesecurityofthecastingvoteisensuredthroughblockcreation,blocksealing,andcontenthashing.Theproducedblockis secureandemploystheSHA 256algorithm.TheblocksaresealedwiththeSHA 256algorithm'suniquehashes,whichare knowntobesufficientlysecureforthee votingprocess.
Intermsofacceptinganddeliveringthehashvaluethatisusedtostitchtheblockwiththechain,eachblock(exceptthefirstand lastblock)isassociatedwiththenextandpreviousblock,buildingMerkletrees.
Fig3 Block2…n=hash(hash(pairsoftransactions)+hash(Block(n 1))+RandomNumber(lengthn+2)
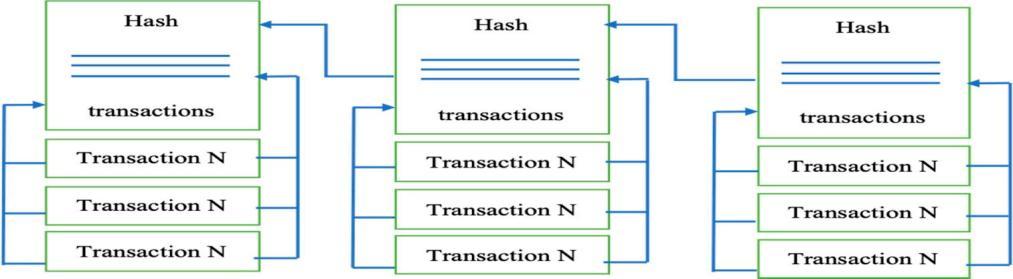
Themethodforsealingtheblocksisdemonstrated.Thesealedblockreflectstheactualblockonceithasbeensealed.Thesealed blocksarerepresentedinsuchawaythattheyarelinkedusingachainedhashkey,withthekeyfromoneblockbeingutilizedby thenextblocktogeneratethenexthash,andsoonuntilalloftheblocksarecompleted.
Duringtheprocessofapplyingthehashfunctiontothetransactions,apairoftransactions(sequential)arechosenandthehash functionisappliedtothem.Allpairsoftransactionsaresequentiallyhashed,andahashiscreatedusingtheSHA256method basedonallhasheddata.It'stimetouseablock'shashafterit'sbeengenerated.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Fig 4: Conversionofblockstosealedblocks.
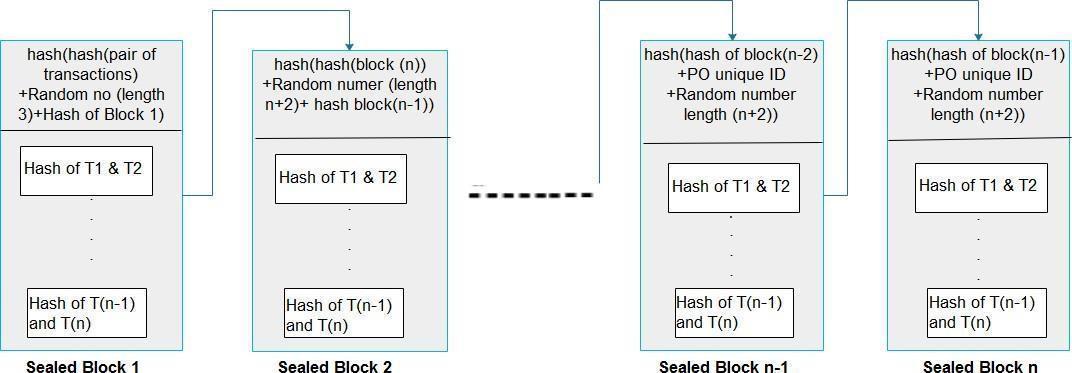
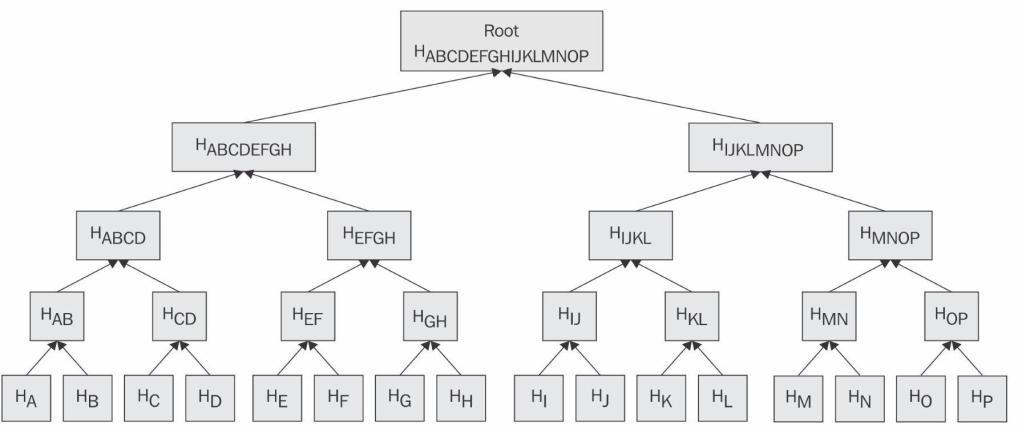
Fig 5: Distributedblockstructure.
Thankstotheblockchain'sexcellentnodeorganization,thefindingsarederivedfromthedatastoredontheblocks.The chainofblocksatthebottomcollectsdataincontainers(blocks)thatareseriallyconnectedbyanalgorithm.
AMerkletree,ontheotherhand,isretainedtotracktheblock'sdistributionanddegreeofbreakdown.Fig4depictsthe logicalallocationofnationalassemblyseatsandpollingplacesineachnationalassemblyseat.
Fig5showstheMerkletreerepresentationofthesystem,anditcanbeobservedthateachtransaction'srecordissaved atthetoplevel,i.elevel0.Thenationalseatsaredepictedatlevel1,whereaspollingstationsinanyregionaredepictedat level2.
Eachtransactioninanyblockcanbedirectlydiscoveredanddocumentedbykeepingthemdispersedandopenfortransactions whilepreservingthecontentswiththeBSJCtechniqueofproofofcompletion.Toincreaseandmaintainvotertrust,itisvitalto tellvotersabouttheresultsoftheirballots.Tomaketheprocessvisible,atrailofthevoterswhocasttheirvotesisestablished attheendofthepollingsession.
Severalassumptionsareconsideredinthisresearch.
a) Thevoterunderstandshisconstitutionalrightsandthepollingprocess.Withinthetimelimit,eachvotermustbe abletovote.
b) Allvoterinformationispublicandavailableforverification.Thedatamustbesubmittedbythedatamanagement
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
agencyatthenationallevel.Itisalsoexpectedthatinternetconnectivityisalwaysavailable,withnocommunication delaysorpausesduetointernetoutages.
c) Pollingofficialsshouldbefamiliarwiththetechnologyandabletohelpvotersthroughtheprocedure.
The purposeof thisstudy is to examineand evaluate electronic votingsystems basedon blockchain technology. First, the blockchainconceptanditsapplicationsarediscussed,followedbyexistingelectronicvotingmethods.Theblockchain'spotential toimproveelectronicvoting,presentsolutionsforblockchain basedelectronicvoting,andfutureresearchroutesonblockchain basedelectronicvotingsystemsareallimportantconsiderations.Legislators,technologists,civilsociety,andthegeneralpublic mustallthinkdeeplyaboutsomeissues.Thisresearchproposedaframeworkbasedonanadaptableblockchainthatcanaddress challengesinthepollingprocesssuchaschoosingasuitablehashalgorithm,choosingblockchainupdates,managingvotingdata, andvotingprocesssecurityandauthentication.Becauseofitsadaptability,blockchainhasbeenabletoadapttothedynamicsof electronicvoting.
[1] Nakamoto, S. Bitcoin: A Peer to Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf. (accessedon28July2020).
[2] Prashar,D.;Jha,N.;Jha,S.;Joshi,G.;Seo,C.IntegratingIoT,andblockchainforensuringroadsafety:Anunconventional approach.Sensors2020,20,3296.[CrossRef]
[3] Mohanta,B.K.;Jena,D.;Panda,S.S.;Sobhanayak,S.Blockchaintechnology:Asurveyonapplicationsandsecurityprivacy challenges.InternetThings2019,8,100107.[CrossRef]
[4] Hussain,H.A.;Mansor,Z.;Shukur,Z.ComprehensiveSurveyAndResearchDirectionsOnBlockchainIoTAccessControl. Int.J.Adv.Comput.Sci.Applications.2021,12,239 244.[CrossRef]
[5] Schinckus,C.Thegood,thebadandtheugly:Anoverviewofthesustainabilityofblockchaintechnology.EnergyRes. Soc.Sci.2020,69,101614.[CrossRef]
[6] Typographicdimensionsandconventionalwisdom:Adiscrepancy?TechnicalCommunication46(1):67 74.Wright, Patricia.1988.Issuesofcontentandpresentationindocumentdesign.InHandbookofhuman computerinteraction,ed. M.Helander,629 652.NewYork:North Holland.Wright,Patricia.1998.
[7] Printedinstructions:Canresearchmakeadifference?InVisualinformationforeverydayuse:Designandresearch perspectives,ed.HarmJ.G.Zwaga,TheoBoersema,andHenrietteC.M.Hoonout,45 66.London:TaylorandFrancis. Zimmerman,DonaldE.andTerriPrickett.2000.
[8] Ausabilitycasestudy:Prospectivestudents’useofauniversitywebpage.Innings:STC’s47thAnnualConference. SocietyforTechnicalCommunication.http://www.stc.org/ConfProceed/2000/PDFs/00099.pdf(accessedDecember4, 2007).
[9] M.Feldhofer,S.Dominikus,andJ.Wolkerstorfer,‘‘StrongauthenticationforRFIDsystemsusingtheAESalgorithm,’’ inCryptographic Hardware and Embedded Systems.2004,pp.357 370.
[10] Y.SteinandH.Primo,‘‘Programmabledataencryptionengineforadvancedencryptionstandardalgorithm,’’U.S.Patent 7508937B2,2009.Accessed:Aug.1,2018.[Online].Available:https://patents.google.com/patent/US7508937B2/en [10]B.Shehzad,K.M.Awan,M.I. U.Lali,andW.Aslam,‘‘Identificationofpatternsinfailureofsoftwareprojects,’’ J. Inf. Sci. Eng.,vol.33,no.6,pp.1465 1480,2017.
[11] A.M.Abdullatif,B.Shahzad,andA.Hussain,‘‘Evolutionofsocialmediainscientificresearch:Acaseoftechnologyand healthcareprofessionalsinSaudiUniversities,’’ J. Med. Imag. Health Inform.,vol.7,no.6,pp.1461 1468,2017.
[12] B.Shahzad,‘‘Identificationofriskfactorsinlargescalesoftwareprojects:Aquantitativestudy,’’ Int. J. Knowl. Soc. Res., vol.5,no.1,pp.1 11,2014.
[13] A.B.ShahzadandA.Said,‘‘Applicationofquantitativeresearchmethodsinidentifyingsoftwareprojectfactors,’’ Int. J.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Inf. Technol. Elect. Eng.,vol.1,no.1,pp.30 33,2012.
[14] K. Saleem, A. Derhab, J. Al Muhtadi, and B. Shahzad, ‘‘Human oriented design of secure machine to machine communicationsystemfore healthcaresociety,’’ Comput. Hum. Behav ,vol.51,pp.977 985,Oct.2015.
[15] K.Saleem,A.Derhab,J.Al Muhtadi,B.Shahzad,andM.A.Orgun,‘‘Securetransferofenvironmentaldatatoenhance humandecisionaccuracy,’’ Comput. Hum. Behav.,vol.51,pp.632 639,Oct.2015.
[16] R.A.Abbasi et al.,‘‘Savinglivesusingsocialmedia:AnalysisoftheroleofTwitterforpersonalblooddonationrequests anddissemination,’’Telematics Inform.,vol.35,no.4,pp.892 912,2018.E.
[17] Alwagait,B.Shahzad,andS.Alim,‘‘ImpactofsocialmediausageonstudentacademicperformanceinSaudiArabia,’’ Comput. Hum. Behav.,vol.51,pp.1092 1097,Oct.2015.
[18] B.ShahzadandE.Alwagait,‘‘Doesachangeinweekenddayshaveanimpactonsocialnetworkingactivity?’’ J. UCS,vol. 20,no.15,pp.2068 2079,2014.
[19] Z.Zheng,S.Xie,H. N.Dai,X.Chen,andH.Wang,‘‘Blockchainchallengesandopportunities:Asurvey,’’ Int. J. Web Grid Services, vol. 14, no. 4, pp. 352 375, 2018. [20] D. Johnson, A. Menezes, and S. Vanstone,‘‘Theelliptic curve digital signaturealgorithm(ECDSA),’’ Int. J. Inf. Secure.,vol.1,no.1,pp.36 63,Aug.2001.
[20] J.Barcelo,‘‘Userprivacyinthepublicbitcoinblockchain,’’ J. Latex Class Files,vol.6,no.1,p.4,2007.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
