International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p-ISSN:2395-0072
Abstract: Many wireless device networks (mainly networks of mobile sensors or networks that are deployedtowatchcataclysmsituations)aredeployedin Associate in Nursing arbitrary and unplanned fashion. Foranydeviceinsuchanetworkwillfindyourselfbeing adjacent node to the other device node within the network.to determine a secure communication between each combine of adjacent sensors node in such a network, everydevice node x within the network has to storen 1rangeofbilaterallysymmetrickeysthatdevice node x shares with all the opposite device nodes, wherever n is that the range of device nodes within the giftnetwork.
This memory storage demand of the keying protocol is varied, particularly once n is massive and therefore the accessible storage in every device node is modest. Previouseffortstorevampthiskeyingprotocolandscale back the amount of keys to be hold on in every device node have made protocols that are liable to impersonation,eavesdropping,andcollusionattacks.
Inthispaper,wehaveatendencytogiftatotally secureprotocolmechanismwherevereverydevicenode hastostore(n+1)/2keys,thatisfarbutthen 1keysthat requiretobeholdonineverydevice withintheoriginal communicationprotocol.
we have a tendency to conjointly show that in any absolutelysecurekeyingprotocol,everydevicenodehas tostoreaminimumof(n 1)/2keys.
Keywords: sensor, key sender, encryption, decryption, sensor networks, MWSN, plain text, cipher text, grid, probabilistic,keyingprotocol
Whensensing elementnodeswishtospeak withone another,therehasgottobeasecureassociationthathas gottobeestablishedbetweennodes.
Constantisthatthecasewiththesensingelementnodes. Communication between sensing element nodes has got to be shielded from external attacks once establishing a session of communication between one another. Communication nodes (Sensors) area unit small devices with little size, less computation power, and a transmissionvary.
Moreover, the positions of Communication nodes (Sensors) needn't be constant and they'll be moving or
dynamicallyshiftwithrelevancetime.So,it’sineluctable thattheinfohastobetransferredandunbrokencorrect and secure. Within the period once sensors were initial introduced there have been several issues associated withsecurity.
The info that was being communicated Either was too huge in volume or the secure transmission was sufferingascarcityofcorrectcare.
Therefore, the conception of Cryptography was introduced.
Cryptography ensured that the info that's being communicated is secure and additionally the info size is additionallylittle.
Sensors: Sensor’s area unit called devices that calculate a physical amountandconvert it intoan electrical wave signal which may be understood and skim by a receiver oratool.
it's typically required to speak confidential knowledge firmly while not being attacked by external world. Examples: Heat Sensors, measuring system (Battle fields),SecurityAlarmSystems
Sensor Networks: A sensor network is designed with a communication infrastructure planned to record, monitor conditions at multiple locations. Multiple detection stations called sensor nodes exist in a sensor network, each of which is lightweight, tiny, and easy to carry devices. Every sensor node is equipped with a power source and transducer. The transducer produces electrical signals based on sensed phenomena and physical effects. The microcomputer processes and stores the sensor output. The power for each sensor device is obtained from the electric utility or from a battery.
Mobile wireless device networks aka MWSNs area unit sometimesoutlinedasawirelessdevicenetwork(WSN) withinwhichthedevicedevices(nodes)areaunitsimply movable.
MWSNsareaunitANrisingfieldofanalysisindistinction to their well established forerunner and that they area unit smaller. Several of their applications area unit similar,likepoliceworkorenvironmentalwatching.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Key distribution within Sensor Networks:
Within wireless detector network (WSN) style Key distribution is a crucial issue. thanks to power and memorylimitations,thekeyshavetobecompelledtobe organizedtocreateatotallypracticalnetwork.
Keydistribution(distributionofkeys todetector nodes) happensbeforereadying.
Initially, sensors observe they’re within sight sensors within the network and transmit the knowledge to the key sender. For secure transmission, the Key Sender thengeneratessecretkeysandsendsthemtoindividual detectornodes.
In cryptography, secret writing is that the method of coding messages or info in such some way thatsolelyapprovedpartieswillscanit
In Associate in Nursing secret writing theme, the message or info, mentioned as plaintext, is encrypted victimization Associate in Nursing secret writing algorithmic rule, turning it into Associate in Nursing undecipherableciphertext.
Decryption: the data that has been encrypted into a secret format is understood because the method of secret writing. Decoding needs a secret key or parole; therefore solely licensed users will solely decode knowledge. In easy that means, it's the conversion of ciphertextintoplaintext.
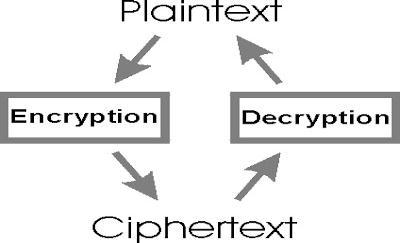
regular key to cypher and decode their transferred knowledge messages. Since a selected sensing element node solely encompasses a set of shared keys and doesn’t have its own universal key it's at risk of impersonationattack.
Everysensingelementisallottedasingularnumberthat is employed to coordinate a definite node during a exceedinglyinavery}two dimensionalhouseandevery regular key's additionally allotted an symbol that is thoughtasGridKeyingProtocol,
Then a sensing element node x stores a regular key K if andaslongastheidentifiersofxandKsatisfydefinitely givenrelation.
Once two adjacent sensors have to be compelled to transfer the info, the 2 sensing element nodes establish common keys and use a mix of these shared keys as a regularkeytodecodeandcypherknowledgemessages.
The grid keying protocol has 2 benefits. First, this protocol will defend against impersonation global organization like the probabilistic protocol and might defendagainsteavesdropping justliketheprobabilistic protocol.
Second,everysensingelementnodeduringthisprotocol should store solely O(log n) regular keys, wherever n is thattheno.ofsensorswithinthenetwork.However,the most issue with grid keying protocol is it should not shielditselffromcollisionattack.
Two main protocols were advising within the past to reduce the quantity of hold on keys in every sensing element node within the network. We tend to sit down with these 2 protocols because the subjective Grid Keying Protocol and Keying Protocol. Every sensing element within the network stores multiple keys that squaremeasurechosenwilly nillyfromanoversizedset ofkeyswithintheProbabilisticKeyingProtocol.
Once 2 aspects by sensing element nodes got to communicate, the 2 sensors nodes acknowledge the shared keys then use a mix of their common keys as a
In our proposed paper we want to show that there could be a system with a keying protocol that reduces the number of keys maintained within the sensorto(n+1)/2keys.Theextraandverypredominant featurethathasbeenintroducedisthatofaKeySender. All Sensor Networks has a corresponding Key Sender associated with it. Every sensor node has to be registered within the Key Sender. The Key Sender then distributes/shares the keys to the sensor nodes within thenetwork.Withthehelpofthekeysdistributedbythe KeySenderthesensorscommunicateandtransferswith theothersensors.
We use ix and Iy to symbolize the identifiers of sensor nodes ‘x’ and ‘y’, respectively, in this network. Each two sensors, say sensor nodes ‘x’ and ‘y’, share a symmetric key denoted K(x, y) or K(y, x). Only the two sensor nodes ‘x’ and ‘y’ know their shared key K(y, x). Andifsensornodes‘x’and‘y’everbecomeneighborsin the network, then they can use their shared symmetric keyK(y,x)toperformtwofunctions:
1) Mutual Authentication: Sensor ‘x’ authenticates sensor‘y’,andsensoryauthenticatessensor‘x’.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
2) Confidential Data Exchange: Encrypt and then decrypt all the transferred data messages between ‘x’ and‘y’.Intherestofthissection,wewantedtoshowthat if the shared symmetric keys are designed to have a “special structure”,then eachsensor needstostoreonly (n+1)/2 shared symmetric keys. We need to introduce two new concepts before we present the special structure of the shared keys, : “Universal Keys” and “a circular relation, named below, over the sensor identifiers”.Eachsensornode‘x’inthenetwork keepsa symmetrickey,calledtheuniversalkeyofsensor‘x’.The universal key of sensor node ‘x’, denoted ‘ux’, is known only to sensor node ‘x’. Let Ix and iy be two distinct sensor node identifiers. Identifier ix is said to be below identifierIyifoneofthebelowconditionsholds:
1)Ix<Iy and(Iy Ix)<n/2
2)Ix>Iy and(Ix Iy)>n/2
The below relation is better explained by an example. Consider the case where n / 3. In this case, the sensor identifiersare0,1,2
Wehave:
Identifier0isbelowidentifiers1and2. Identifier1isbelowidentifiers2and0. Identifier2isbelowidentifiers1and0.
Theorem 1: If there exists a try of distinct however adjacentsensors‘x’and‘y’withdistinctiveidentifiers‘Ix’ and‘Iy’severallythentheBelowconditionholdstrueas follows:
•‘Ix’isbelow‘Iy’
•‘Iy’isbelow‘Ix’
Theorem 2: Sincethereexists‘nsensors,everydetector ‘x’ with symbol ix has (n 1)/2 detector identifiers Iy belowit.
Theorem 3: In accordance with Theorem one,the numberofdetectorswithsymbolsixbelowthesensor‘y’ withidentifierIyis(n 1)/2.
Theorem 4: If a detector symbol ix for detector ‘Ix’ is below a detector symbol ‘Iy’ then the detector ‘x’ has to store the biradial Key ‘ky, x’/ H (‘Ix’|uy) among it. Then the detector ‘y’ has to reckon the biradial Key to verify thedetector‘x’.ThebiradialKey‘k(y,x)’isholdonsolely in‘x’.
Theorem 5: Asmentionedearlier,everydetector‘x’has to store single Universal Key and (n 1)/2 biradial Keys
‘k(y, x)’ so as to speak with detector ‘y’ (NOTE: the detectorsymbolixoughttobebelow‘Iy’).
Each and each device ‘x’ are given the subsequent data before the sensors square measure deployed inside the network:
1)Onedistinctsymbolixwithinthevary0 (n 1)
2)Oneuniversalkeymarriedwoman
3)(n 1)/2trigonalkeysK(y,x)/H(‘Ix’|uy)everyofthat is shared between device ‘x’ and another device ‘y’ (where ix is below Iy). If the sensors ‘x’ and ‘y’ square measure adjacent and need to speak with one another, then they need to implement the Mutual Authentication protocolthathasthesubsequentsteps:
Step1:device‘x’selectsa randompresentnxandsends a hullo message that's received by device ‘y’. x >y: hello(‘Ix’|nx)
Step 2: device ‘y’ selects a random present Empire State andsendsahullomessagethat'sreceivedbydevice‘x’.x >y:hullo(‘Iy’|ny)
Step 3: device ‘x’ determines whether or not ix is below iy. Then it either fetches K(y, x) from its memory or computesit.Finally,device‘x’sendsa verify message to device‘y’.x >y:verify(‘Ix’;‘Iy’;H(Ix|Iy|ny|K(y,x)))
Step 4: device ‘y’ determines whether or not iy is below ix. Then it either fetches Bluegrass State,x from its memoryorcomputesit.Finally,device‘y’sendsa verify message to device ‘x’. x >y: verify (Iy| Ix |H ((Iy| Ix |nx|Ky,x))
Step 5: device ‘x’ computes H (Iy| Ix |nx|K(y, x)) and compares it with the received H(Iy|Ix|nx|K(y, x)). If they're equal, then device ‘x’ concludes that the device claiming to be device ‘y’ is so device ‘y’. Otherwise, no conclusionisreached.
Step 6: device ‘y’ computes H(Ix | Iy |ny|K(y, x)) and compares it with the received H(Ix | Iy |ny|K(y, x)). If they'reequal,then‘y’concludesthatthedeviceclaiming tobe device ‘x’isso device ‘x’. Otherwise, no conclusion isreached.
Sensors ‘x’ and ‘y’ can now start exchanging data accordingtothefollowingdataexchangeprotocol:
Step 1: Sensor‘x’combinesthenonceny withthedatato besent,encryptsthecombineddatausingthesymmetric
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
key K(y, x), and sends the result in a data message to sensor‘y’.
x >y:data(Ix |Iy |K(y,x)(ny|text))
Step 2: Sensor‘y’combinesthenoncenx withthedatato besent,encryptsthecombineddatausingthesymmetric keyKy,x,andsendstheresultinadatamessagetosensor ‘x’.
x >y:data(Iy |Ix |K(y,x)(nx|text))
According to our keying protocol, described in Section III, each sensor in the network is required to store only (n+1)/2keys.Thus,thetotalnumberofkeysthatneedto bestoredwithinthenetworkisn(n+1)/2.
Theorem 6: There should be a minimum of n(n 1)/2 keysthataretobestoredwithinthesensornetwork.
Theorem 7: According to any keying protocol (which is uniform) has to store at least (n 1)/2 keys within it to communicatewithitsadjacentsensors.
DES(the encryption Standard)could bea cruciform block cipher developed by IBM. The formula uses a 56 bit key to encipher/decipher a 64 bit block of information.Thesecretiscontinuallyconferredasa 64 bitblock,eacheighthlittlebitofthatisneglected.
However, it's usual to line every eighth bit so every cluster of eight bits has Associate in Nursing odd range of bits set to one. The formula is best suited to implementation in hardware, in all probability to discourageimplementationsincomputercode,thattend tobeslowbycomparison.
However, fashionable computers square measure thus quick that satisfactory computer code implementations square measure without delay offered isthatthemostgenerallyusedcruciformformulawithin the world, despite claims that the key length is just too short.
Ever since DES was 1st declared, contention has raged concerning whether or not fifty six bits is long enoughtoensuresecurity.Thekeylengthargumentgoes likethis.ForwardthatthesolepossibleattackonDESis toundertakeeverykeysuccessivelytillthecorrectoneis found,then1,000,000machineseverycapableoftesting 1,000,000 keys per second would realize (on average) onekeyeachtwelvehours.
Most affordable folks may realize this rather comforting and a decent live of the strength of the
formula. Those who consider the exhaustive key search attack to be a real possibility (and to be fair the technologytodosuchasearchisbecomingareality)can overcome the problem by using double or triple length keys. In fact, double length keys have been recommendedforthefinancialindustryformanyyears.
Use of multiple length keys leads us to the Triple DESalgorithm,inwhichDESisappliedthreetimes.Ifwe consider a triple length key to consist of three 56 bit keysK1,K2,K3thenencryptionisasfollows:
• Encrypt with K1
• Decrypt with K2
•EncryptwithK3
Decryptionisthereverseprocess:
• Decrypt with K3
• Encrypt with K2
•DecryptwithK1
Setting K3 equal to K1 in these processes gives us a doublelengthkeyK1,K2.SettingK1,K2andK3allequal to K has the same effect as using a single length (56 bit key).Thus itis possiblefor a systemusing triple DES to becompatiblewithasystemusingsingle DES.
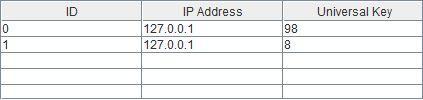
Key Sender: It detects the sensors gift in its region and updates their details in its table. Here we have a tendency to used java simulation to form associate interface to key sender. Symbolically it should look like(beforesensorsdetectionandwhendetection)
Figure3: KeySender table before detection
IDisthat the distinctivevariety given to every device,IP address is that the logical address and universal is the evenkeyusedforcodinganddecoding
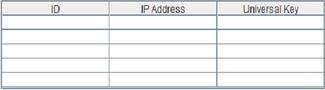
KeySenderTableoncedevicedetection:
Figure4: Key sender table after clients/sensors are detected
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
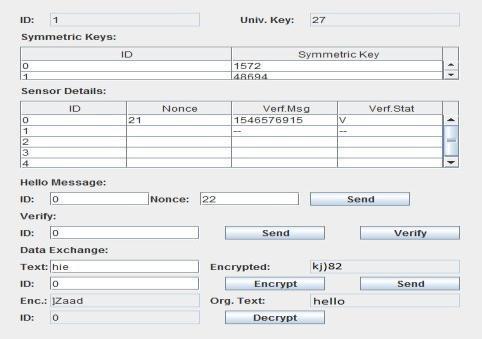
Here we take 2 sensor nodes or clients (say receiver 0 and receiver 1) which are detected by the key sender. The key sender then calculates the universal keys(as showninfig 4)andsendsthemtotherespectiveclients
Figure5:Receiver0
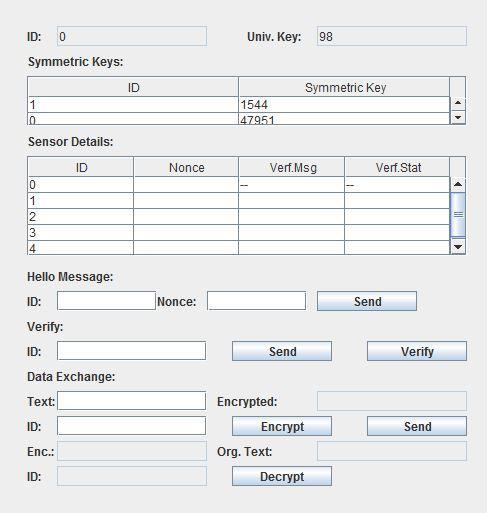
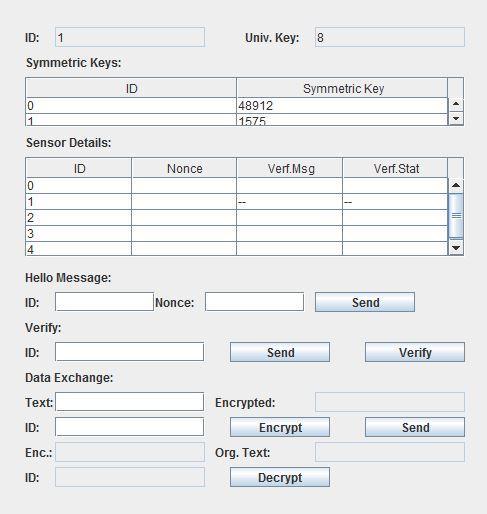
Figure8:Receiver1 with keys updated
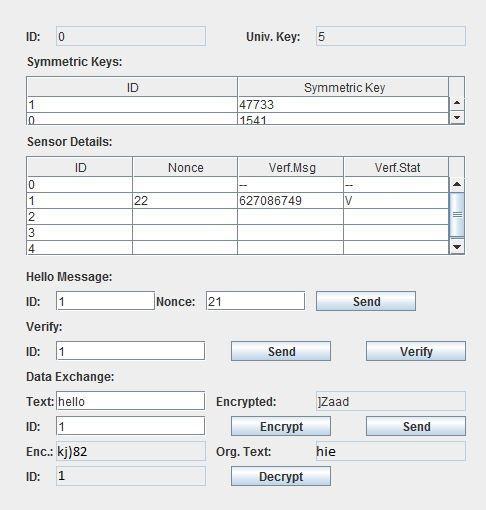
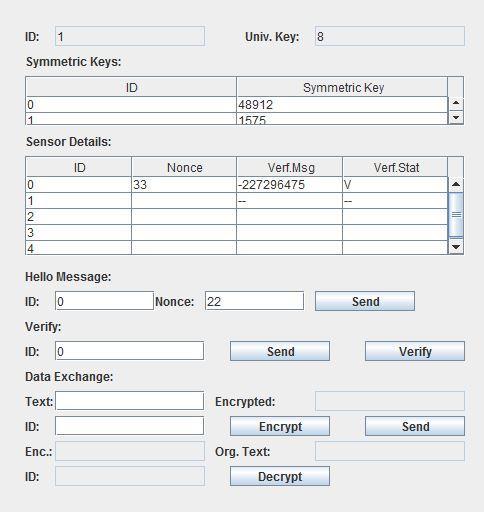
After the keys square measure is updated each of the nodes has to be compelled to attest to one another for that they send verification messages and ensure the authentication.
once authentication is finished message transfer is finishedvictimizationsecretwritinganddecoding
Message transfer done by Receiver0 original message is hello, it is encrypted and sent. The encrypted message fromReceiver1isdecrypted
Figure6:Receiver1
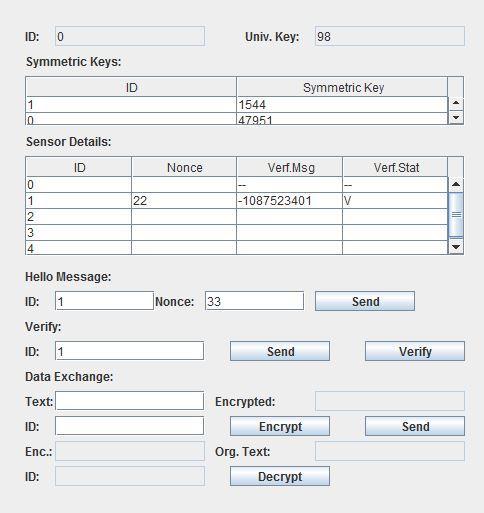
After the key sender sends the symmetric keys to both thereceiverstheclientsnowlooklike
Figure9: Receiver0 sending and receiving messages
Message transfer done by Receiver1 original message is hie, it is encrypted and sent. The encrypted message fromReceiver0isdecrypted
Figure7:Reciever0 with keys updated
Figure10: Receiver1 sending and receiving messages
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Wheneverareceiver0desirestospeakwithreceiver2, it cannot communicate directly,1st of all the receiver0 should communicate with receiver1 so the receiver1 communicatesthatmessagewithreceiver2
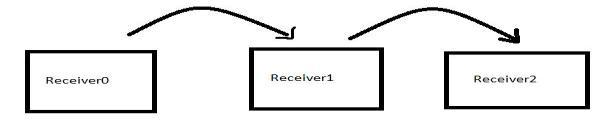
Figure9: nodes communication
Typically, each sensor in a sensor network with nsensors needs tostore n 1shared symmetrickeys to communicating securely with each other. Thus, the number of shared symmetric keys stored in the sensor network is n (n 1). However, the optimal number of shared symmetric keys for secure communication, theoretically,is(n2)=n(n 1)/2.
Although there have been many approaches that attempttoreducethenumberofsharedsymmetrickeys, they lead to a loss of security: they are all vulnerable to collusion.
In this paper, we show the Secure minimal or Lightweight Key Agreement protocol for sensor networks, that needs to store only (n + 1)/2 shared symmetric keys to each sensor. The number of shared symmetric keys stored in a sensor network with n sensors is n (n + 1)/2, which is close to the optimal number of shared symmetric keys for any key distributionschemethatisnotvulnerabletocollusion.
Itmaybenotedthatinadditiontothelownumber ofkeysstored,andtheabilitytoresistcollusionbetween sensors,ourkeyingprotocolhastwofurtheradvantages.
Firstly, it is uniform: we store the same number of keys in each sensor. Secondly, it is computationally cheap and thus suitable for a low power computer such as a sensor: when two sensors are adjacent to each other, the computation of a shared symmetric key requiresonlyhashing,whichisacheapcomputationand can be done fast. As our protocol has many desirable properties, such as efficiency, uniformity, and security, we call this protocol the Secure minimal or Lightweight KeyAgreementprotocolforsensornetworks
Communication within Sensor Networks by Using Key Distributorbych.d.naiduijcsit2014.
Theremainingreferencesare:
1. Taehwan Choi, H. B. Acharya, and Mohamed D. Gouda, “The Best Keying Protocol “, December 2011IEEE
2. http://en.wikipedia.org/wiki/Sensor Sensors
3. SensorNetworksbyMargaretRouse.
4. http://en.wikipedia.org/wiki/Mobilewirelesssens ornetwork MWSNs
5. “KeyDistributionMechanismsforWirelessSensor Networks” by Seyit A., C¸Amtepe and BulentYener
6. Communication within Sensor Networks by Using Key Distributor by M.V. Kishore in International Journal of Computer Science and Information Technologies, Vol. 5 (4),2014,49064910
7. “Cryptography and Network Security”, Fourth EditionbyWilliamStallings
8. L. Gong and D. J. Wheeler, “A matrix key distributionscheme,”JournalofCryptology,vol.2, pp.51 59,January1990.
9. “Advanced Encryption Standard” by Douglas Select
10. http://en.wikipedia.org/wiki/Advanced_Encrypti on_Standard#cite_note fips 197 4.
11. “Comparative Study of Energy Aware QoS for Proactive and Reactive Routing Protocols for MobileAd hocNetworks”.InternationalJournalof ComputerApplications(0975 8887)Volume31 No.5,October2011.
12. Steganography Detection using Functional Link Artificial Neural Networks, International Journal ofComputerApplications(0975 888),Volume47 No.5June2012.
13. Secure Group Communication using Multicast Key Distribution Scheme in Adhoc Network, International Journal of Computer Applications. (0975 8887) Volume1 No.25,Nov2010.
14. ANovelDualPhaseMechanismforDataTransmissionto Provide Compression and Security by M.V. Kishore in International Journal of Advanced Research in Computer Science and Software Engineering Volume 3, Issue 12, December2013ISSN:2277128X
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072


Dr.K.N.S. LAKSHMI Currently working as Professor from Department of computer scienceandEngineeringatSanketikaVidya ParishadEngineeringcollege





B. SAI KRISHNA Pursuing B tech from Department of computer science and Engineering at Sanketika Vidya Parishad Engineeringcollege
P. DURGA MALLESWARI Pursuing B tech fromDepartmentofcomputerscienceand Engineering at Sanketika Vidya Parishad Engineeringcollege
R. SHANKAR Pursuing B tech from Department of computer science and Engineering at Sanketika Vidya Parishad Engineeringcollege
Ch. AMITH Pursuing B tech from Department of computer science and Engineering at Sanketika Vidya ParishadEngineeringcollege