International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
1G. Naga Lakshmi, 2P. Ruchitha, 3G. Lavanya, 4CH. Sai Greeshmanth, 5R. Bhanu Prakash
1 Assistant professor, Dept of ECE, DVR & Dr Hs MIC college of technology, Andhra Pradesh, India 2,3,4,5 Dept of ECE, DVR & Dr. Hs MIC college of technology, Andhra Pradesh, India ***
Abstract - Watermarking technology has attracted more and more attention in various research fields Like information security. At this time, we protect the remote sensing data by using watermarking technology. As remote sensing data is delicate, it is necessary to enforce some management for authenticity and ownership. Particularly for the copyright protection, illegal use, and legitimacy identification of remote sensing image data. Therefore, this project proposes to use image watermarking technology to achieve comprehensive security protection of remote sensing image data, although the use of cryptography technology rises the applicability and security of watermarking technology. The remote sensing data is a representation of parts of the earth’s surface as seen from space. The watermarking process is used for hiding digital information. A watermarking is a logo, text, or pattern. That is purposely covered in another image. Its purpose is to make it tougher for the original image to be imitative or used without authorization. Cryptography is the process of protecting information by transforming it into a secure format. Which provides an alternative solution for ensuring tamper resistance, and the ownership of intellectual property. And the tamper recognition will aware you when your device is being restricted by employees or other individual seeks. The untried results show that the arrangement of remote sensing image digital watermarking technology has good performance in the faintness and robustness of watermarking
Key Words: MATLAB, Satellite Image Detection, Digital WatermarkingIn new years, every person’s attention has traveled to the internet.It’sasimpleandfastwaytosendandaccessdata and information all around the world. This information is mostlydigital(text,images,audio,video).Everyoneutilizes theinternet,whetherforpersonalorprofessionalreasons. Asaresult,protectinguserdatafromunauthorizedaccessis vital.Whendidwegetupbackthen?Howcanweprovethat weowntheinformation?Toderiveanexplanation.Adigital watermarking procedure is used to protect data so that it cannotbeaccessedorduplicatedbyanunauthorizedperson for malevolent purposes. A watermark is a piece of data included in digital media. The subject is a data related portion of information. The proposed study looks at new ways for digital watermarking in both the spatial and transforms domains. The improvement in information technologyhasmadeitverysimpletoservedigitaldata.As
timegoesby,datasanctuarycobwebsgetmoreprotected.It is vital to protect multimedia data from attacks such as counterfeiting, piracy, and malicious alternation. Digital security can respond to a wide range of assaults and procedures.Watermarkingisupperofthem.Awatermarkis alabel,tag,orinformationthatseemsonadocument.
Awatermarkdataisplacedintodigitalmedia.Thethingisa pieceofdata relatedinformation(anylabel,citations,author name, id). The recommended investigation studies novel enhancementstodigitalwatermarkingmethodsinboththe spatial and transform domains. The advancement of informationtechnologyhasmadethesharingofdigitaldata quitesimple.Dataprotectionstalenessbecomesmoresecure asdevelopmentprogress.Protectingmultimediadatafrom assaults such as counterfeiting, privacy, and malicious manipulation is critical. To provide a response to a large range of attacks and mechanisms. A watermark is an indication,atag,oraninformationampulethatisinjected intomultimediadata toprotecttheoriginal material from unauthorizedchangeanddistribution.
Adigitalwatermarkmustbehonestlyunaffectedbychanges to the carrier signal in order to spot media files with copyright information. If accuracy is required, a fragile watermark would be used in its place. Steganographic techniques are used in steganography and digital watermarkingtosubtlyencodedatainearsplittingsignals. Steganography and digital watermarking both use steganographictechniquestosecretedatainnoisysignals. Unlike steganography, which seeks faintness to human senses,digitalwatermarkingprioritizesrobustness.Digital watermarkingisasubmissiveprotectionapproachsincea digital replica of data is identical to the original. It simply labelsdatawithoutdegradingitorrestrictingaccesstoit.
Sourcetrackingisoneapplicationofdigitalwatermarking. At each point of distribution, a watermark is placed in a digitalsignal.Ifacopyoftheworkislater discovered,the watermark can be extracted from the copy, and the distributionsourcecanbedetermined.Thismethodissaid to have been used to track down the source that can be determined.Thismethodissaidtohavebeenusedtotrack down the source of illegally copied movies. Sources monitoringateachpointofdistribution,awatermarkcanbe extractedfromthecopy ,andthedetermined.Thismethod issaidtohaveusedbeentotrackdownthesourceofillegally copiedmovies.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

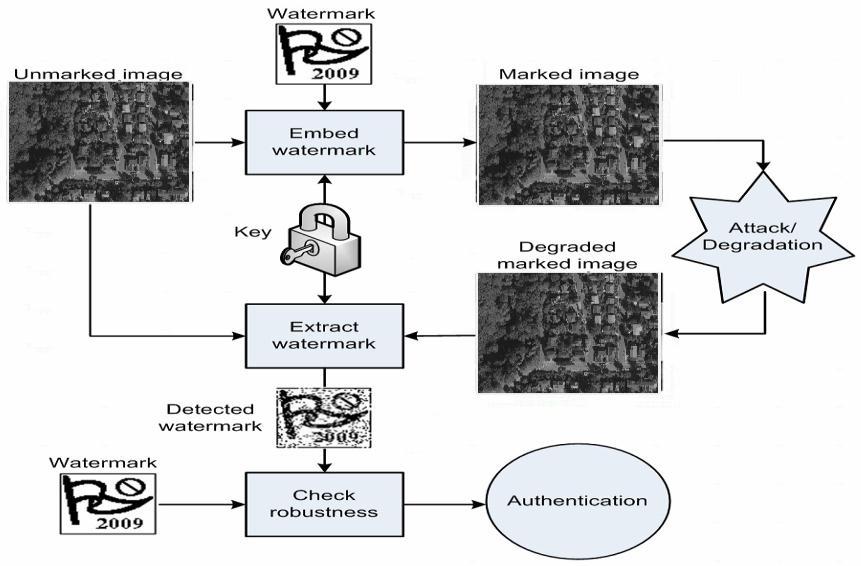
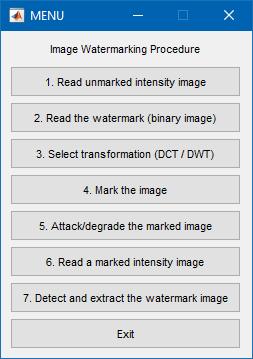
The inserting process inserts the watermark in the text reasonably and generates a watermark important. The flowchartoftheproposedwatermarkembeddingprocessis shown. TheImagegainingprocessacquiresthewatermark imagewhichcanbetheemblem,sign,orfingerprintofthe originalcopyrightowner….
Fig 1:Flowchart
The tenure "Digital Watermark" was created by Andrew Terkel and Charles Osborne inDecember 1992.Thefirstsuccessfulembeddingand extraction of a steganographic spread spectrum watermark were demonstratedin1993byAndrewTerkel,CharlesOsborne
Watermarksareidentificationmarksproducedduringthe papermakingprocess.The firstwatermarks appeared in Italy during the 13th century, but their use rapidly spread acrossEurope. They stayed used as a resource to recognizethe papermaker or the craft league that industrial the paper.The symbols often werecreated by a wire seamed onto the paper Mildew.Watermarks linger to be used today as producer's symbols and to avoid forgery.
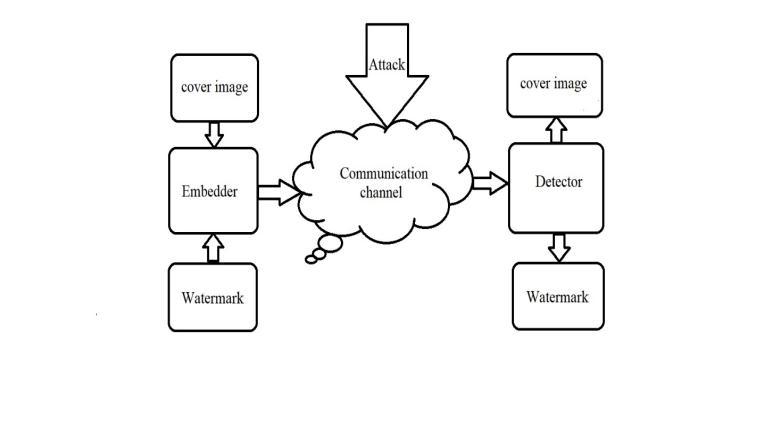
Awatermarkembedderandawatermarkdetectorarethe twomaincomponentsofthedigitalwatermarkingsystem.A watermark is putinto thecover signal using a watermark embedder, and the existence of the watermark signal is
detected using a watermark detector. During the developmentofembeddingandnoticingwatermarks,apiece called a watermark significant is used. With the advancement of satellite remote sensing technology in recent years, remote sensing images have increasingly reflected their features of fast and easy access. Floating picturesandsatellitepicturesarethemostcommontypesof remotesensingimages,whichgenerallyrecordgeographic, environmental, resource, military, and other information vitaltothenationaleconomyandpeople'sconfrontation.In rapports of land administration, figures show that by engaging satellite images, the time necessary for land mergingiscutinhalfassociatedwithoutdatedmethods,and thecostistensoftimeslesser.
As per the outcome, remote detecting images will play an importantroleinmerging.Currently,remotesensingimages are only employed as a spatial data input system for processing.Theanalysisandprocessingdataarejustsaved as photos to complete the basic electrification. The initial remote sensing image and the processed image are both poorlyprotected.Itisvitaltopayattentionnotonlytothe safety of remote sensing pictures but also to their organization.Remotesensingimagedataissensitive,soitis necessarytoenforcesomemanagementforauthenticityand ownership. In the sought after, when companies have to obtainsomedata,watermarkingcanbeusedto foilillegal usersfromillegallydispensingandusingdata.
At the same time, watermarking technology can identify manipulationbyremotelysensingdata.Theaxiom"Digital watermarking" was designed by the inquiry labs, that invented this advanced technology. However, as photographershavebeenutilizing"watermarking"foralong time, this wording causes a lot of confusion in the digital photographyworld.Thesetwotypesof"watermarking"are notsubstitutable
A digital watermark is a piece of information that will be embeddedinasignal,whileinsomeproperties,thetenancy digital watermark mentions the difference between the watermarkedsignalandthecoversignal.Thehostsignalis
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
the signal where the watermark will be inserted. Watermarkingsystemsareusuallybrokendownintothree stages:embedding,attack,anddetection.Whenanalgorithm accepts the host and data to be embedded, it creates a watermarkedsignal.
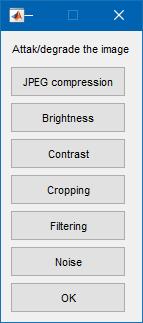
At thatpoint the watermarked fundamental signal is transmitted or kept, usually spread to another person. If this separate modifies, this is called an occurrence Although themodification may notbe mean, the tenure enchantment gets up from copyright protection applications, where tertiaryrevels may try to eliminate the digital watermark complete modification. There are numerous imaginable modifications, for example, a lossyfirmness of the data (in which resolution isdiminished), cropping an image or video, orintentionallyaddingnoise.
Detection (also known as extraction) is a method that attemptstoextractthewatermarkfromtheassaultedsignal. The watermark is still present and can be recovered provided the signal was not altered during transmission. Uniformunknownthemodifications remainedsimple,the withdrawal technique is robust digital watermarking systems should be able to produce the watermark appropriately.Anyalterationtothesignalshouldcausethe extractionmethodtofailinfragiledigitalwatermarking.
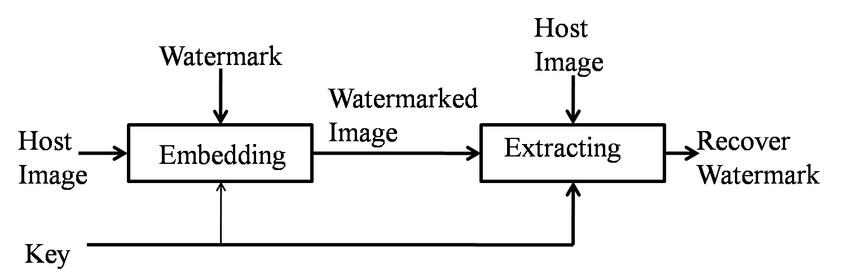
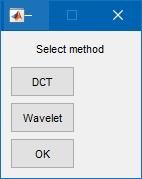
The way of watermark creation is using a watermarking critical and the watermarking algorithm, to yield the watermarkeddigitalimage.Theinsertingprocessvarybased on which image domain is being processed, e.g., the terrestrial,incidencefield,orthewavelets.Dependingonthe embedding method measurable (single bit) or readable (multi bit) watermarks are being incorporated into the digital images. A watermark implanting technique is a procedure for inserting a watermark into a coverup document.
communication of the information conveyed by the watermark. There are various types of attacks on watermarkingschemes:Basicattacks,RemovalAttacks,legal attacks, Geometric attacks, Protocol Attacks, and CryptographicAttacks.
Basic spells take advantage of strategy flaws in inserting techniques.Simplemealspectrumtechniques,forexample, can withstand amplitude and noise addition but are susceptibletotimingerrors.Becausethetechniquerelieson on chip signal synchronization, adjusting the synchronizationcanresultinthelossofembeddeddata.Itis possible to change the length of an audio file without changingthepitch,whichcanbeaneffectiveattackonaudio files.
Legalattacksrefertoanattacker'sabilitytocastdoubton the watermarking scheme in court. These spells trust on presentandfuturelegislatureoncopyrightlawsanddigital informationownership,thecredibilityoftheownerandthe attacker,theowner'sfinancialstrengthversustheattacker's, expertwitnesses,andthelawyers'capability.Atrulyrobust watermarkingschememustlimitanattacker'sabilitytocall intoquestiontechnicalevidencepresentedincourt.
Removal sessions purpose at the complete elimination of thewatermark data from the watermarked datawithout instant the security of the watermarkingalgorithm (e.g., without the crucial used for watermarkembedding).That is, no allowance, even exorbitantly multifaceted, can recuperate the watermark information from the attacked data. This grouping contains denoising,quantization (e.g., for firmness), demodulation,and collusionfits.Not allof these approaches always come close to their goal of complete watermark removal, but they may damage thewatermarkinformationmeaningfully.
Cryptographic attacks aim to break the security methods used in watermarking schemes, allowing the embedded watermark information to be removed or misleading watermarkstobeembedded.
Inwatermarkingvocabulary,an“attack”isanyprocessing that may impair the detection of the watermark or
The effort to challenge the complete watermarking applicationthought.Invertiblewatermarksareusedinone type of protocol attack. Inversion works by the attacker removing his watermark from the watermarked data and claimingownershipofthewatermarkeddata.Thiscanlead toconfusionaboutwhoactuallyownsthedata.Theauxiliary
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
eruptionisanothertypeofproprietyattack.Inthiscase,the goal is not to destroy or impair the detection of the watermark, but to approximate, a watermark from watermarkeddataandcopyittosomeextradatareferredto as board verifications. The duplicate occurrence is used when a lawful watermark in the board data can be bent without algorithmic information of the watermarking technologyordataofthegoalstatistics
Etiquette attacksthe determination ofthe aggressive comprehensive notion of thewatermarkingrequest. One typeofdecorumattackisbasedonthethoughtofinvertible watermarks.Thenumeraloverduethetransposalisthatthe aggressor withdraws his personalwatermarksince the watermarkeddataandautonomiestobetheproprietorof thewatermarkedinformation Thecopyoccurrenceisvalid whena validwatermark in the goal data canbeproduced with neither algorithmic knowledge of the watermarking technologynortheknowledgeofthewatermarkingkey.
Thewatermarkdetectionandextractionmoduledetermine whetherornotthedatacontainsaspecifiedwatermarkand whether or not the watermark can be extracted. The module'sinputcanbeabannedimage,akey,awatermark, oranoriginalimage,andtheoutputcanbeawatermarkor somekindofcredibilityvalue.Itindicatesthepossibilityof thedatacontainingthespecifiedwatermark.
Theknowledge of wavelettransformand the collection of inserting incidence bands make use of the Hammer keep rottenness process. The image is fragmented into mouth features LHn, HLn, HHn and estimate constants LLC on N scales, and N=1, 2,…N. LL are the minutiae gotten after sievinginthebottommostfrequencyband.HHretainsthe detailedinformationafterfilteringinbothlevelandvertical directions
MATLAB is a complex practical computationlinguistic and collaborating environment for algorithm expansion, data imagining, datastudy, and mathematical computation. By means of MATLAB, you can crack technical calculation difficulties earlier than with old style programming languages, such as C, C++, and Fortran.
MATLAB is a data analysis and visualization tool with extensive support for matrices and matrix operations. In total,MATLABisanimportantprogramminglanguagewith unresolved design skills. One of the reasons MATLAB has become suchanimportant toolistheuseofcollections of MATLABprogramsdesignedtosupportaspecifictask.These collectionsofprogramsarementionedastoolcabinets,and theimageindulgencetoolboxisofparticularinteresttous. TosomeextentthaninterpretingallofMATLAB'sskills,we will frontier ourselves to that business with image management. As wanted, we will familiarize functions, instructions,andmethods.AMATLABfunctionisakeyword thatacceptsvariousparametersandreturnssometype of output, such as a matrix, string, or graph. Such purposes containsin,im read,andim close.Therearemanyfunctions inMATLAB,andaswewill see, writingourown issimple (sometimes necessary). The atmosphere is the typical statistics type in MATLAB, and all data are assumed to be matricesofsomekind.Images,ofcourse,arematriceswith grey values (or possibly RGB values) as their elements. MATLABconsiderssinglevaluestobematrices,whereasa stringissimplyamatrixofcharacters,thelengthofwhichis the string. We will aspect at the more general MATLAB commands in this chapter, and we will discuss images in laterchapters.When you start up MATLAB, you have a blankwindowcalledtheCommandWindow_inwhichyou enter commands. Given the huge quantity of MATLAB connotations and the varied stricturestheycanrevenue,a command linestyleboundaryismuchmoreefficientthana complexsequenceofpull downmenus
You can use MATLAB in a wide range of applications, including signal and image processing, communications, control design, test and measurement financial modeling, and analysis. Add on tool chest (collections of special purposeMATLABfunctions)spreadtheMATLABsituationto solvepreciselessons ofhitches intheseapplicationareas. MATLAB provides many landscapes for documenting and allocatingyourwork.YoucanintegrateyourMATLABcode with other languages and claims, and distribute your MATLABproceduresandapplications.
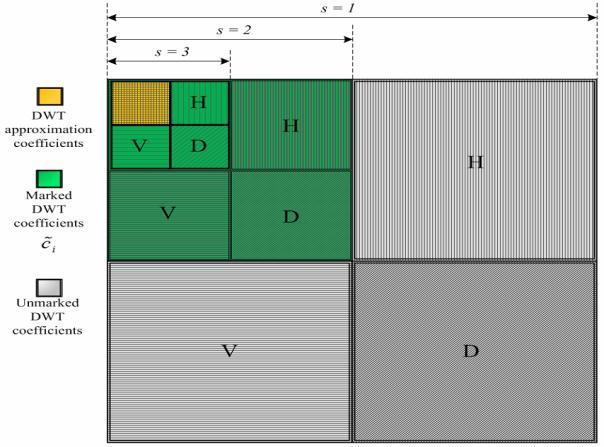
Fig: dwtcoefficientsforone8x8blockimage
OnceoccupiedwithimageriesinMATLAB,therearemany clothestoretaintrendyattentionsuchasladinganimage, using the precise process, transferrable the data as dissimilardatatypes,howtoshowanimage ,andchanging between different image setups. Image Dispensation Tool
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
chesttransportsacomprehensivesetofreference standard proceduresandgraphictoolsforimageallowance,analysis, picturing, and procedure development. You can achieve image improvement, image deblurring, feature detection, noise reduction, image division, spatial alterations, and image registration. Many determinations in the tool breakfrontaremultithreadedtotakethebenefitofmulticore andmultiprocessorcomputers.andgraphictoolsforimage processing, examination, visualization, and algorithm development.Yourcanistercompletedualincrease,image deblurring, feature detection, sound decrease, image subdivision,spatialtransformations,andimageregistration. Manymeaningsinthetoolchestaremultithreadedtotake gainofmulticoreandmultiprocessorcomputers.
·RGBImagetoIntensityImage(rgb2gray)
·RGBImagetoIndexedImage(rgb2ind)
·RGBImagetoBinaryImage(im2bw)
·IndexedImagetoRGBImage(ind2rgb)


·Indexed Image to Intensity Image (ind2gray) ·Indexed ImagetoBinaryImage(im2bw)
·Intensity Image to Indexed Image (gray2ind) ·Intensity ImagetoBinaryImage(im2bw)
·Intensity Image to RGB Image (gray2ind,ind2rgb)
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
and knowledgeprovidedthroughouttheProject.Herskill and knowledge in communication and signal process make valuable comments and suggestions thathavebeenveryusefulinsolvingproblemsencountered duringtheDevelopment
I stay thankful to DR. K. SRINIVAS, Principal, andProf D. PANDURANGA RAO, CEO, forprovidingme with theopportunitytocompletethisproject. I also extend my thanks to all faculty members of Electronics and Communication Engineering facultymembers for their valuable guidance and encouragement in this Development.
Iwouldidenticaltopickmyhonestthankstoallmy groups for unraveling their data,valuablecontributions,andhelp withthisDevelopment.
Finally, I want to express my gratitude to myfamilyfor their unwavering support and assistance during my academic career and for their ongoing support and encouragementofthisprogress




If the information is implanted in the unique image, the strengthofthecommunicatedimageisdesigned.Ifthereis binarydatafixedintheimage,thedevelopmentcontinues otherwise,theimagecontainsnodata.
At present day data can be replicatedsimply due to the collaboration and alphanumericcommunication of software data Thismaterial makes alphamerical image watermarking asignificantfieldofinquiry.


Digital image watermarking using many methods has been valuable as a significant tool for image authorization, honesty verification, restricted detection, copyrightsafety,anddigitalsafetyofanimage.
AppendixBincludesreferences,aswellasresearchpapers from which we derived the foundational research for thisproject.
I'd like to take this time to thank the individuals listed below for their invaluable charities andsupport with this project. Originally, I would like torecognize my project manager, Ms. G. Naga Lakshmi, M. Tech for his guidance and support, especially for the valuable ideas
Furthermore, to improve strength along with security, researchers should focus onevolvingnew,advanced techniques.
[1] Z.L. Zhou, C.N. Yang, B.J. Chen, X.M. Sunbathe, Q. Liu, Q.M.J.Wu,Effectiveandefficientimagereproductionfinding through hostility to subjective spin, IEICE Trans. Inf. Syst. E99 D(6)(2016)1531 1540.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
[2] C. Qin, C.C. Chang, P.Y. Chen, Self embedding fragile watermarking with healing functionality primarily based totallyonadaptivebitallocationmechanism,SignalProcess. 92(4)(2012)1137 1150.
[3] J. Li, X.L. Li, B. Yang, X.M. Sun, Segmentation primarily based picture copy pass forgery detection scheme, IEEE Trans.Inf.ForensicsSecure.10(3)(2015)507 518.
[4] J.W. Wang, T. Li, Y.Q. Shi, S.G. Lain, J.Y. Ye, Forensics characteristic evaluation in quaternion wavelet area for distinguishing photographic snapshots and pc graphics, MultimediaToolAppl.(2016).
http://dx.doi.org/10.1007/s11042 016 4153 0.
[5] C. Qin, X.Q. Chen, D.P. Ye, J.W. Wang, X.M. Sun, A novel picture hashing scheme with perceptual robustness the usage of block truncation coding, Inform. Sci. 361 362 (2016)84 99.
[6]C.Qin,P.Ji,X.P.Zhang,J.Dong,J.W.Wang,Fragilepicture watermarkingwithpixel smartrestorationprimarilybased totallyonoverlappingembeddingstrategy,SignalProcess. 138(2017)280 293.[7]Y.Q.Shi,X.L.Li,X.P.Zhang,H.T.Wu, B. Ma, Reversible facts hiding: Advances withinside the beyonddecades,IEEEAccess4(2016)3210 3237.
[7]C.Qin,C.C.Chang,T.J.Hsu,Reversiblefactshidingscheme primarilybasedtotallyonexploitingmodificationpathwith steganographicsnapshots,MultimediaToolsAppl.74(15) (2015)5861 5872.
[8]L.X.Luo,Z.Y.Chen,M.Chen,X.Zeng,Z.Xiong,Reversible picturewatermarkingtheusageofinterpolationtechnique, IEEE Trans. Inf. Forensics Secure. 5 (1) (2010) 187 193. [10]C.Qin,Y.C.Hu,ReversiblefactswerehidinginVQindex desk with lossless coding and adaptive switching mechanism,SignalProcess.129(2016)48 55.
[9]LX,Luo,Z.Y Chen,M.Chen,X.Zeng,Z. Xiang Revocable image watermarking using exclamation technique, IEEE Trans.Inf.ForensicsSecure.5(1)(2010)187 193. [10]C. Qin,Y.C.Hu,RevocableinformationbeatinginVQdirectory table with lossless coding and adaptive switch device, IndicationProcedure 129(2016)48 55.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
