International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Abstract The user on social media has saw a boom in recent time with increase in number of users of the net and emerges as the major networking platform of our era. But it also has its own repercussions on society and the mental health of a person such as online abuse, harassment, scamming, private information leaks and trolling. Cyberbullying affects a person both physically and mentally, particularly for girls and students, and sometimes escalated to their suicide. Online harassment has a huge bad impact on society. No of cases have occurred in different parts due to online bullying, such as sharing private information, abusing someone online, and racial discrimination. So, there is a need for identification of bullying on social apps and this has become a major concern all over the world. Our motive for this research is to compare different techniques to find out the most effective technique to detect online harassment by merging NLP (natural language processing) with ML (machine learning).
Key Words: Cyber bullying, Machine Learning, NLP, Social apps.
Onlineappsforsocializingareaplacewherewecanexpressourthoughtsandopinionsandcanevenshareourpersonallives withanotherperson[1].Wecanaccesssocialmediawiththehelpofinternetconnectioninourphones,laptops,PCs,tablets etc.Themostwell knownonlinemediaincorporatesFacebook1,Twitter2,Instagram3,Tik Tok4,etc.Thesedays,web based mediaisengagedwithvariousareaslikeCoaching[2],Entrepreneurship[3],andfurthermorefortherespectableobjective[4]. Onlinemediaislikewiseimprovingtheworld'seconomythroughsettingoutmanynewpositionopendoors[5].
1https://www.facebook.com/ 2https://twitter.com/ 3https://www.instagram.com/
Albeitweb basedmediahasagreatdealofbenefits,itlikewisehasafewdownsides.Utilizingthismedia,malignantclientslead exploitative and deceitful demonstrations to offend and harm their notoriety. As of late, cyberbullying emerges as the significantweb basedsocialappsissue.
Cyberbullyingordigitalbadgeringalludestoanelectronicstrategyfortormentingorprovocation.Cyberbullyinganddigital badgeringareotherwisecalledinternettormenting.WiththeboomandadvancementofthesocialappslikeTwitter,Facebook, cyberbullyinghasbecomenormalinthelife,especiallyinthelifeofstudents.
RoughlyhalfoftheyoungpeopleinAmericaexperiencecyberbullying[6].Thistormentingintellectuallyaffectsthecasualty [7].Thecasualtiespickrecklessbehaveslikeself destructioninlightofthefactthattheinjuryofcyberbullyingwhichisdifficult tobesuffered[8].Subsequently,theidentifyingandavoidanceofcyberbullyingisessentialtosecureyoungsters.
Accordingtosituation,werecommendacyberbullyingrecognitionsysteminviewofAItorecognizewhetherornotatext connectswithcyberbullying.WehaveexploredafewAIalgorithmsinourresearchtofindoutthebestoneamongthemwhich canbeusedtodetectcyberbullyingmoreprecisely.Wedirectexaminationswithdatasetsfromtwittercommentsandremarks. Inexecutioninvestigation,weutilizetwodistinctivecomponentvectorsBOWandTF IDF.TheoutcomesshowthatTF IDF highlightgivespreferableexactnessoverBOWwhereSVMgivespreferredexecutionoversomeotherAIcalculationsusedfor ourresearch.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Restoftheresearchiscoordinatedinthefollowingpattern.Section2outlinestheconnectedworks.Section3presentsthe subtletiesofthegivenAIcomparison.Section4showsthefinalresultsofresearch.Section5finishesupthepaperandfeatures somepotentialworkwhichcanbedoneinfuture.
ThereareafewdealswithAIbaseddigitaltormentingidentification.AregulatedAIcalculationwasproposedutilizingasackof wordswaytodealwithidentifyingthecontextandintentionofthewriterofthetext[9].Thiscalculationshowsscarcely61.9% of exactness. MIT (Massachusetts Institute of Technology) directed a venture called Ruminati [10] utilizing SVM to detect cyberbullyingofTwitterremarks.Thescientistjoinedlocationwithrationalthinkingbyaddingsocialparameters.Theafter effectofthisundertakingwasimprovedto66.7%precisionforapplyingprobabilisticdisplaying.Reynoldsetal.[11]discoveran evenmoreeffectivecyberbullyingtechniquewithanincreasedaccuracyof78.5%.Thedecisiontreeandoccasion basedmentor isutilizedbycreatortoaccomplishthisaccuracy.Toimproveonlineharassmentrecognition,thecreatorofresearch[12]has utilizedcharacters,feelingandopinionofelement.
Afewprofoundlearning basedmodelswereadditionallyacquaintedwithidentifythecyberbullying.ProfoundNeuralNetwork based model is used for detecting online bullying by utilizing genuine information [13]. The creators first investigate cyberbullyingmethodicallythenusedthatdatatolearntheAIaboutautomaticdetectionofbullying.Badjatiyaetal.[14]has introducedatechniqueinvolvingprofoundNeuralorganizationmodelsforidentifyingdisdaindiscourse.Aconvolutionalneural organization basedmodelisusedtoidentifyonlinebullying[15].Thecreatorsutilizedwordinsertingwherecomparativewords havecomparativeinstalling.Inamulti modularsetting,Chengetal.[16]papertheoriginalstudyofonlinebullyingidentification bycooperativelytakingadvantageofweb basedmediainformation.Thistest,nonetheless,isdifficultbecauseoftheintricate blendofbothcross modularrelationshipamongnumerousstrategiesandunderlyingconnectionsbetweendifferentweb based interactiveconversations,arrangementofvariouscomplexmodelsandmodesofconversations.TheyproposeBully,online harassmentdetectionframeworktocomeoutofthedifficulties,whichfirstchangemulti modesofsocialappsinformationasa diverseorganizationandafterwardattemptstodohubimplantingportrayalsontothatinformation.
Numerouswritingsaboutonlineharassmentfocusedonexaminationofwhatiswrittenthroughoutrecentmanyyears.But Cyberbullying,bethatasitmay,isnowchangingnowitnotonlypresentintheformoftextonly.Theassortmentoftormenting informationoffriendlystagescan'tbeachievedonlybytextdetectingalgorithmsonly.
Wangetal.[17]recommendedamulti modesdetectionframeworkthatcoordinatesmultipletypesofdata,forexample,gif, images,vulgarcomments,timevia onlinemedia toadapttothemostrecentkindofharassment.Specifically,theyremove printedattributes,yetadditionallyapplyprogressiveconsiderationorganizationstocatchtheinformalorganizationmeeting capacityandencodevarioustypesofdataincludinggifs,pictures.Thecreatorsmodelthemulti modesharassmentdiscovery structuretoforaddressingthesenewkindofonlinebullyingwaysotherthantext.
UtilizingNeuralNetworkstoworkwiththeidentificationofweb basedharassingbecomeacommonnormtoday.TheseNeural NetworksoriginallyfoundedexclusivefororrelatedtoothertypesofLayersbyuseofLong Short Term Memorylayers.Buanet al.[18]presentedanothermodelfortheNeuralNetworkthatcanbeusedinwords basedmediatoidentifywhetherthereis onlinebullyingornot.TheideaisbaseduponcurrentmodelsthatcombinethestrengthofLong Short Term Memorylayerswith Coevolutionarylayers.Alongwiththis,thedesignincludestheuseofstackedcenterlayers,whichshowsthattheirreview improvestheNeuralNetwork'sperformance.Adifferenttypeofenactmentstrategyisalsorememberedforourplan,thatis classified"SVMlikeinitiation"ByinvolvingtheweightL2regularizationofastraightactuationworkintheactuationlayeralong withutilizingamisfortunework,the"SVMlikeaccuracy"isachieved.
MakinganAIframeworkwiththreeunmistakablehighlights,byRaisietal.[19]solvestheissueofcomputationconnectedwith badgeringidentificationininterpersonalorganizations.(1)Inthistypethekeyexpressionswhichisgivenbyexpertwhich distinguishbullyingfromnon bullying,withminimalsupervisionrequired.(2)Atotalno.oftwostudentswhoco traineach other,inwhichonestudentstudythecontentofthelanguageoftextandthesecondstudentlooksatsocialconstructionaspect. (3)Onpreparingnonlinearprofoundmodels,thiscoordinatedecentralizedwordandcharthubportrayals.Upgradingagenuine capacitythatconsolidatesco preparingalongwithweaksupervision,andthemodelistrained.
Cyberbullyinghasasoflatebeenidentifiedbyclientsofonlineinterpersonalorganizationsassignificantmedicalofissueof public and the production of compelling discovery model with extensive scientific merit. Al et al. [20] have presented an assortmentofspecificTwitter inferredhighlightsincludingconduct,client,andtweetcontent.Theyhaveassembledadirected AIanswerforthediscoveryofcyberbullyingonTwitterbasedorganization.Asshownbytheirappraisal,inviewofhighlights proposedbythem,theirsetuprecognitionframeworkworkingundertherecipienttrademarkacquiredresultswithalocale bendof0.943andanf measureof0.936.
For those impacted, cyber bullying can create serious mental issues in the person. So, there is a need to plan Automated approachesfortherecognitionofcyberbullying.Albeitlatecyberbullyingidentificationendeavorshavesetupbrandnew
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
algorithmsfortexthandlingtoidentifycyberharassment,thereareasyetcoupleofendeavorswhenitcomestorecognizecyber bullyingofvisualmeansi.e.,usingimagesetc.Singhetal.[21]revealedthatimagescomponentssupporthighlightvectorsin identificationofonlineharassmentinviewofearlyinvestigationofapublic,namedonlinebullyingdataset,whichcanhelpin predictingonlinebullying.Whencyberbullyingisturningouttobeanever increasingnumberofnormal ininterpersonal organizations,itisthefateofoutrageoussignificancetopromptlyrecognizeandresponsivelyreactuponthis.Theworkin[22] exploredhowFuzzyFingerprints,anewmethodwithrecordedviabilityinsimilarundertakings,workswhiledistinguishing literaryharassmentinsocialsites.
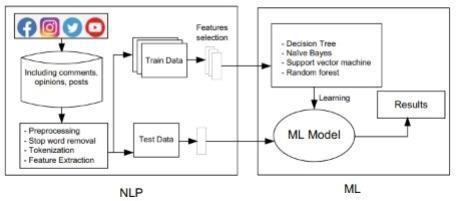
Theaimofthisprojectistoclassifyasetofdataascyberbullyingornotandtocomparefivemachinelearningalgorithmsand findthemostaccurateonefortheclassification.
Wewilldevelopthisprojectwiththehelpofpythonandwebtechnology.UsinghtmlandCSS,wewilldesignanddevelopthe webinterfacesfortheproject.Thenafterpreparingthewebinterfaces,wewillsearchanddownloadthedatasetthatweneed toclassify.Afterdownloadingthedataset,wewillpre processthedataandthentransfertoTf Idf.Thenwewillgeneratecodes forthemachinelearningalgorithms(NaiveBayes,DecisionTree,RandomForest,SVM,DNNModel)usingpython.Sohere,we areusingpythonasbackendandforfrontendhtml,CSSetc. Thereal worldpostsortextcontainnumberofunnecessarysymbolsortexts.Forinstance,emojisandsymbolsarenotneeded todetectcyberbullying.Hence,firsttheyareremovedandthenmachinelearningalgorithmsareappliedfortheidentification ofbullyingtext.Inthisphase,thetaskistoremoveunnecessarycharacterslikesymbols,emojis,numbers,linksetc.Andafter thosetwoimportantfeaturesofthetextisprepared:
•Bag of Word: Themachinelearningalgorithmsarenotgoingtoworkdirectlywithtexts.So,wehavetoconverttheminto someotherformlikenumbersorvectorsbeforeapplyingmachinelearningalgorithmtothem.Inthiswaythedataisconverted byBag of Words(BOW)sothatitcanbereadytouseinnextround.
•TF IDF:Oneoftheimportantfeaturestobeconsideredisthis.TF IDF(TermFrequency InverseDocumentFrequency)isa statisticalmeasuretoknowtheimportancethatawordcarriesinadocument.
Inthismodelwewillapplyfiveefficientalgorithmsusedinmachinelearningnamely RandomForest,Decisiontree,Naive Bayes,SVMandDeepNeuralNetworksModel(DNN)tocomparethemandfindthemostaccuratealgorithmamongthem.The algorithmhavinghighestaccuracyisdiscoveredamongthefivealgorithmsusingpublicdatasets.
Thistreeclassifiercanbeutilizedinbotharrangementandrelapse.Itcanassistwithaddressingthechoiceandchooseboth. Decisiontreehasadesignwhichresemblesatreelikestructureinwhichtheparent/roothubisacondition,anddescending parenthubisleaf/branchhubwhichisachoiceofthecondition.Forex.Iftheroothubisthecointhanitsbranchhubwillbe theoutcomeofthecoini.e.,headandtail.Arelapsetreeyieldstheanticipatedincentiveforatendedtoenter.
ThisisaproductiveAIcalculationinviewofBayeshypothesis.Itpredictsabouttheprobabilityofoccurringofaneventbased upon the event which already occurred previously. And when we add naïve assumption into it became the Naïve Bayes classifier.
Innaïvebayesassumptionweconsiderthateacheventisindependentofeachotherandisgoingtomakeanequalcontribution tofinalresult.Thebestuseofitistheclassificationoftextwhichrequiredahighdimensionaltrainingdataset.Asstatedearlier itconsiderthateacheventisindependentsoitcannotbeusedforeventshavingrelationshipbetweenthem.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Itisaclassifierwhichcomprisesofdifferentchoicetreeclassifiers.Itiscreatedbyusingsubsetofdataandthefinaloutputof thatdataisbasedonmajorityrankingmeansthehighervotes.Itisslowerthanthedecisiontreewhichwehavediscussed earlierasitcontainsnotonlyonebutalargenumberofdecisiontreewhichcomestogethertoformaforestandhencethe namerandomforest.Thegreaternumberofdecisiontreearegoingtobepresentinrandomforestthemoreprecisetheoutput isgoingtobe.Unlikedecisiontreeitdoesn’tuseanysetofrulesorformulastoshowtheoutput.
SupportVectorMachine(SVM)isaregulatedAIcalculationwhichcanbeappliedinbothorderandrelapsethesameachoice tree.Itcanrecognizetheclassesextraordinarilyinn layeredspace.Alongtheselines,SVMproducesamorepreciseoutcome thandifferentcalculationssignificantlyquicker.Byandby,SVMdevelopssetanofhyperplanesinalimitlesslayeredspaceand SVM is executed with part which changes an information space into the necessary structure. For instance, Linear Kernel involvestheordinaryspotresultofanytwoexamplesasfollows:
K (y,yi)=aggregate(y∗yi)
Itconsistsofmanylayeredcomputationswhichisperformedtogether.Aneuralnetworkhaslayersknownas:hiddenlayers, inputlayersandoutputlayersandincaseifthehiddenlayeristwoormorethetwothanwecancallitasdeepneuralnetwork. ItcanbeconsideredastheimprovedversionofANN(ArtificialNeuralNetwork).Thismodelhasrecentlybecomeverypopular duetoitsaccuracyoverotheralgorithms. WhiletrainingthedatasetonDNNmodelaninputvectorisneedtobecollected.Thetrainingconsistsoftwopassesforward passandbackwardpass.Inforwardpassanon linearactivationlayeriscalculatedfrominputtooutputlayeronebyone.In backwardpasswemoveinreverseorderfromoutputlayertoinputlayerwhilecalculatingtheerrorfunction.
Inthisresearchwehaveusedfivemachinelearningalgorithmandstudiedthemcarefullytofindoutthealgorithmwithbest accuracyamongallfiveofthem.Tofindoutwhichalgorithmisbestwetrainedeachoneofthemonsamedatasetsothatwe cancomparethemwitheachothermoreprecisely.ThefivealgorithmsareDNN,SVM,RF,DTandNBsofirstwearegoingto usethesealgorithmsondatasetonebyoneandthenwewilldiscusstheresultshownbyeachoneofthemtofindoutwhichone isbestamongthem.
Thedatasetusedforthisstudyisdownloadedfromwebsitecalledkaggle.com[27].Thedatasetcontainstwotypesofsetwhich arebullyingtextandnon bullyingtext.Thegoalistoidentifyallthebullyingtext.
•Non-bullying Text: Thetextwhichisnotdemeaningorhurtfulbutisalegitcomplimentorrespectfulcriticismoftheworkof anindividual.Forexample,commentssuchas“Thisgirliscute”aresomewhathumaneanddemeaning.
•Bullying text: Thecommentswhichishurtfulandabusiveinnatureorarepromotingracism,bodyshaming,casteism,slut shamingetc.comesinthecategoryofbullyingtext.Forexample,"Thisbitchisugly",“youshoulddie”arethe textwhichis straightupbullyingsomeonewhichcanaffecttheirmentalhealthseverely. So,withtheuseofpythonmachinelearningpackagesalgorithmsknownastroubleshootingalgorithmisimplemented.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
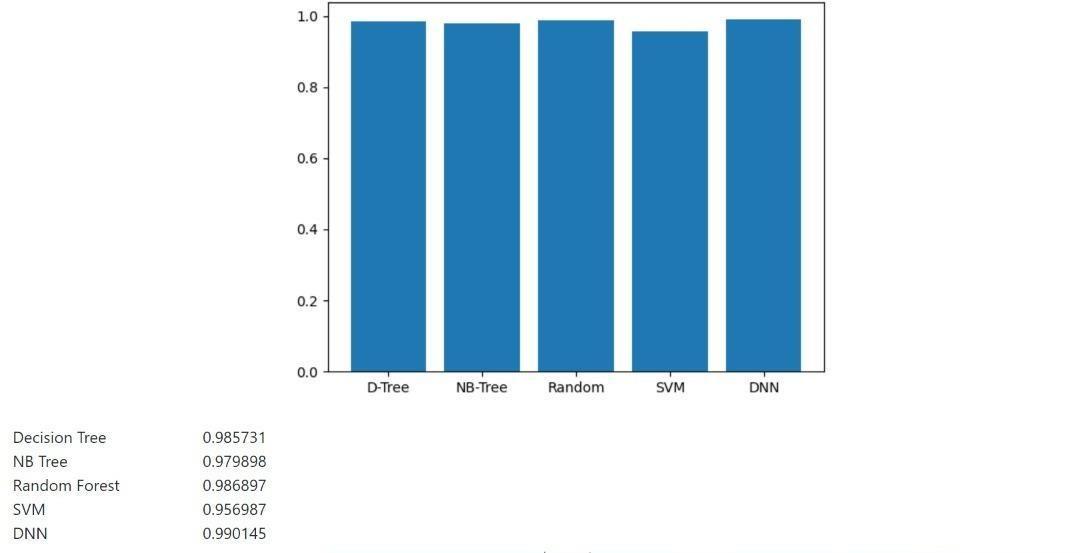
InthegivengraphshowninChart 1.Wearecomparingallthefivealgorithmswitheachothertofindoutwhichalgorithmisbest amongallfive.ThisgraphhasbeenplottedwiththehelpofMatplotlibrary.Weobservedthatamongthefivemachinelearning algorithms,DNNModeloutperformstheotherswhileRandomForestcomessecond,DecisionTree third,NaïveBayescomes secondlastandSVMistheleastaccurate.SoaccordingtothisresultwecansafelysaythatitisbettertouseDNN Modelfor detectingthecyberbullyingthananyotheralgorithm.
Chart 1:AccuracygraphofMLalgorithms
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
Astheusersofsocialmediaisincreasingdaybydayalongwith itcyberbullyingrelatedcasesisalsoincreasingonsocialmedia withitsgrowingpopularityandtheincreasingusageofsocialmediabyyoungpeople.Itisnecessarytodeviseanautomated methodofdetectingcyberbullyinginordertoavoidtheharmfuleffectsofcyberbullyingbeforeit’stoolate.Assometimesthe consequencesofcyberbullyingcanbeasbadasthesuicidebythepersonthatisbullied.So,keepinginmindtheimportanceofa systemwhichcandetectthecyberbullyingandonlineharassment,wearegoingtostudydifferentMLalgorithmsandtheir effectivenessincomparisonwitheachothertopredicttheiraccuracyonagivendatasettofindoutthebestamongthem.After studying all the five algorithms and their results we come to a conclusion that DNN model perform best in detecting cyberbullyingwithanaccuracyof0.990145andalongwiththesecond bestperformingalgorithmcomesouttoberandom forestalgorithmwithanaccuracyof0.986897. So,wecanuseanyofthesetwoalgorithmstodetectthecyberbullyingandonlineharassmenttogetthehighestaccuracywhile SVMistheleastaccurateamongallofthem.
AlltheworkandresearchdoneinthisprojectissupportedbyM.I.E.T(MeerutInstituteofEngineeringandTechnology),Meerut.
[1] C.Fuchs,socialmedia:Acriticalintroduction.Sage,2017.
[2] N.Selwyn,“Socialmediainhighereducation,”TheEuropaworldoflearning,vol.1,no.3,pp.1 10,2012.
[3] H. Karjaluoto, P. Ulkuniemi, H. Keinanen, and O. Kuivalainen, “An ¨ tecedents of social media b2b use in industrial marketingcontext:customers’view,”JournalofBusiness&IndustrialMarketing,2015.
[4] W.AkramandR.Kumar,“Astudyonpositiveandnegativeeffectsofsocialmediaonsociety,”InternationalJournalof ComputerSciencesandEngineering,vol.5,no.10,pp.351 354,2017.
[5] D.Tapscottetal.,Thedigitaleconomy.McGraw HillEducation,2015.
[6] S.Bastiaensens,H.Vandebosch,K.Poels,K.VanCleemput,A.Desmet,andI.DeBourdeaudhuij,“Cyberbullyingonsocial networksites.anexperimentalstudyintobystanders’behavioralintentionstohelpthevictimorreinforcethebully,” ComputersinHumanBehavior,vol.31,pp.259 271,2014.
[7] D.L.HoffandS.N.Mitchell,“Cyberbullying:Causes,effects,andremedies,”JournalofEducationalAdministration,2009.[8]
[8] S.HindujaandJ.W.Patchin,“Bullying,cyberbullying,andsuicide,”Archivesofsuicideresearch,vol.14,no.3,pp.206 221, 2010.
[9] D.Yin,Z.Xue,L.Hong,B.D.Davison,A.Kontostathis,andL.Edwards,“Detectionofharassmentonweb2.0,”Proceedingsof theContentAnalysisintheWEB,vol.2,pp.1 7,2009.
[10] K.Dinakar,R.Reichart,andH.Lieberman,“Modelingthedetectionoftextualcyberbullying,”inInProceedingsoftheSocial MobileWeb.Citeseer,2011.
[11] K.Reynolds,A.Kontostathis,andL.Edwards,“Usingmachinelearningtodetectcyberbullying,”in201110thInternational ConferenceonMachinelearningandapplicationsandworkshops,vol.2.IEEE,2011,pp.241 244.
[12] V.Balakrishnan,S.Khan,andH.R.Arabnia,“Improvingcyberbullyingdetectionusingtwitterusers’psychologicalfeatures andmachinelearning,”Computers&Security,vol.90,p.101710,2020.
[13] S.AgrawalandA.Awekar,“Deeplearningfordetectingcyberbullyingacrossmultiplesocialmediaplatforms,”inEuropean ConferenceonInformationRetrieval.Springer,2018,pp.141 153.
[14] P.Badjatiya,S.Gupta,M.Gupta,andV.Varma,“Deeplearningforhatespeechdetectionintweets,”inProceedingsofthe 26thInternationalConferenceonWorldWideWebCompanion,2017,pp.759 760.
[15] M.A.Al AjlanandM.Ykhlef,“Deeplearningalgorithmforcyberbullyingdetection,”InternationalJournalofAdvanced ComputerScienceandApplications,vol.9,no.9,2018.
[16] L. Cheng, J. Li, Y. N. Silva, D. L. Hall, and H. Liu, “Xbully: Cyberbullying detection within a multi modal context,” in ProceedingsoftheTwelfthACMInternationalConferenceonWebSearchandDataMining,2019,pp.339 347.
[17] K. Wang, Q. Xiong, C. Wu, M. Gao, and Y. Yu, “Multi modal cyberbullying detection on social networks,” in 2020 InternationalJointConferenceonNeuralNetworks(IJCNN).IEEE,2020,pp.1 8.
[18] T. A. Buan and R. Ramachandra, “Automated cyberbullying detection in social media using a sum activated stacked convolutionlstmnetwork,”inProceedingsofthe2020the4thInternationalConferenceonComputeandDataAnalysis, 2020,pp.170 174.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN: 2395 0072
[19] E.RaisiandB.Huang,“Weaklysupervisedcyberbullyingdetectionusingco trainedensemblesofembeddingmodels,”in 2018IEEE/ACMInternationalConferenceonAdvancesinSocialNetworksAnalysisandMining(ASONAM).IEEE,2018,pp. 479 486.
[20] M.A.Al garadi,K.D.Varathan,andS.D.Ravana,“Cybercrimedetectioninonlinecommunications:Theexperimentalcase ofcyberbullyingdetectioninthetwitternetwork,”ComputersinHumanBehavior,vol.63,pp.433 443,2016.
[21] V.K.Singh,S.Ghosh,andC.Jose,“Towardmultimodalcyberbullyingdetection,”inProceedingsofthe2017CHIConference ExtendedAbstractsonHumanFactorsinComputingSystems,2017,pp.2090 2099.
[22] H.Rosa,J.P.Carvalho,P.Calado,B.Martins,R.Ribeiro,andL.Coheur,“Usingfuzzyfingerprintsforcyberbullyingdetection insocialnetworks,”in2018IEEEInternationalConferenceonFuzzySystems(FUZZ IEEE).IEEE,2018,pp.1 7.
[23] S.R.SafavianandD.Landgrebe,“Asurveyofdecisiontreeclassifiermethodology,”IEEEtransactionsonsystems,man,and cybernetics,vol.21,no.3,pp.660 674,1991.
[24] I.Rishetal.,“Anempiricalstudyofthenaivebayesclassifier,”IJCAI2001workshoponempiricalmethodsinartificial intelligence,vol.3,no.22,pp.41 46,2001.