International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net
p ISSN:2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056
Volume: 09 Issue: 05 | May 2022 www.irjet.net
p ISSN:2395 0072
1,2,3 Student, Computer Science Engineering, MIT School of Engineering, MIT ADT University, Pune, Maharashtra, India
4 Professor, Computer Science Engineering, MIT School of Engineering, MIT ADT University, Pune, Maharashtra, India ***
Abstract - Nowadays, there has been a rise in the disruptive activities that have been happening. Due to this, security has been given principal significance. Public places like shopping centres, roads, banks, etc are increasingly being equipped with CCTVs to guarantee the security of individuals. Subsequently, this inconvenience is making a need to computerize this system or make it smart through learning with high accuracy. Since constant observation of these surveillance cameras by humans is a near impossible task, this will help to detect any threat or suspicious activity in the recorded video and thus create a smart surveillance over the area. Some of the literatures in this topic shows the presence of few works which have implemented to make a smart surveillance system. But they are divided into different types of anomalies and detection methods. Therefore, a need for Bibliometric survey in the area of Anomaly detection using Deep learning is necessary to track the research trends, progress and scope of the future research. This paper conducts Bibliometric study for “Anomaly Detection using UCF Crime dataset” by extracting documents of total 385 from Dimensions database using keywords like anomaly detection, UCF Crime dataset, image processing, artificial intelligence and deep learning. The study is conducted since the last decade that is 2012 2021 for the research analysis. Through this study it is observed that there is a vast scope for researchers, surveillance providing companies and public sector to study the used cases and implement anomaly detection to provide a smart surveillance system.
SmartCCTVsystemsincludeimplementingself learningtothe normal surveillance systemsusingdeeplearning. Self learningsystemscanincludemanytypesofimplementations.Theycollecttheinformationbasedonmovementsand peoplevisibleintheCCTVcameraandprovideinformationonthesame.Somesurveillancesystemsusethefacedetection system to detect face structures of known people. If any unknown person is detected it will notify the user about their presenceinthesurveillancearea.Itisusedtoprovideaccesstoonlyauthorisedpersonsinthesurveillanceareaandkeep aneyeforunauthorisedpeople.Theyhavealsointroduceddifferenttechniquestomakefasterandaccuratefacedetection inrealtimesurveillance[1,3,4].
Along with the face detection system there was also an introduction of object detection system for smart surveillance using deep learning techniques. It can detect different types of objects like bags, weapons or any suspicious object in the surveillance videos. Implementing both face detection system and object detection system together made a good implementation of smart indoor surveillance system [3]. A lot of comprehensive study related to both systems has beendonebyapplyingvariousdeeplearningtechniquestoattainthebestresultsandimplementthesame[6].
To attain a smart outdoor surveillance it was necessary to detect the motion of the objects and people in the camera and learn them. A motion detection system which detects the motion of every person in the vicinity of the surveillancecameraandtellstheuserabouteachmovementofthatpersoninrealtime.Itcandetectwhetherthepersonis sitting, standing, running, jumping, etc. Each movement of the person is recorded in the surveillance system [2]. Further researchwasdoneonhowtodetectiftheperson’sorintruder’sfaceiscoveredwithamaskoranythingandcapturetheir movement.Alsoitwasabletodetectthemovementofthepersoninthelowlightconditionslikeatthenighttime[5].
Recently, in the area of smart CCTV there has been a lot of researches related to Anomaly detection system. AnomalyDetectionSystemisdefinedasareal timesurveillanceprogramdesignedtoautomaticallydetectandaccountfor thesignsofoffensiveordisruptiveactivitiesimmediately.Ithelpsustodetectanomaliesinrealtimesurveillance.Itisan
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
Page200

International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
emergingfieldforoutdoorsurveillancesystems.MostofthestudyrelatedtoanomalydetectionisdoneusingUCF Crime dataset. Many attempts are done to improve the quality of anomaly detection through various deep learning and feature extraction techniques to achieve higher accuracies [7,8]. The anomaly detection system is our area of interest as it is a recent study related to smart CCTV. Including this system in the normal surveillance system will provide a great insight into different business ideas for surveillance providing companies in the market competition. Moreover, there is a vast scopeofdevelopmentintheareaofsmartsurveillanceforfuturework
The anomaly detection system is our area of interest in the field of smart CCTV and we will be providing a bibliometric analysis for the same. The Bibliometric study helps to know the quantitative analysis of the progress of the researchworkdoneinaspecificareathroughtheliteratureavailableinarticles,journals,conferencepapers,monographs, booksandpeer reviewedworks.Wecanusestatisticaltoolsandmethods,totrackthedevelopmentsinthisspecificarea.
ThesearethefollowingpointsmentionedasthegoalsofthisBibliometricanalysis:
Togaininsightintheresearchworkdoneinanomalydetectionsystems.
Toknowaboutthecountrieswhichhaveprovidedresearchinthisarea.
Toknowabouttheauthorscontributingtothisfieldofresearch.
Toidentifyandknowaboutdifferenttrendsofpublicationsbasedontheirorganization.
Toperformacitationanalysisinthisareaofresearch.
This paper represents a Bibliometric survey along with some literature survey for anomaly detection system in smart CCTV. Section 1 is the Introduction of the topic Anomaly detection. Section 2, shows the data collection related to anomaly detection using UCF Crime dataset. Section 3, represents the Bibliometric analysis in the form of Statistical analysis,Geographicalanalysis,Networkanalysisandcitationanalysis.Here,analysisisdoneonthedatawhichisobtained from the Dimensions database. Section 4 shows the literature survey done for the topic. Section 5 includes discussions fromtheanalysis.Section6containsthefuture work relatedtothetopic.InSection 7,thelimitationsarementionedand Section8presentstheconclusionofthepaper.Lastly,referencesarementionedattheendofthepaper.
Wecollecteddocumentsof ourtopicfromnumerous platformsandwebsiteslikeGoogleScholar,Scopus,Webof Science, IEEE, Science Direct, Dimensions and many more. These papers consist of the statistical information of the publisheddocumentswhichcanbechosenfortheBibliometricanalysis.Thesewebsitescontaintheresearchpapersinthe form of the articles, journals, review papers, edited books, conference papers, etc. Some of the research papers can be accessedbygivingsomefeeorareopenaccess.
Here, in this paper we have used Dimensions database which contains enormous data for the Bibliometric analysis.[10]
Table 1: ListofPrimaryandSecondaryKeywords
Primary Keyword “AnomalyDetection”
Secondary Keyword
AN D “UCF Crimedataset”
“ImageProcessing”
“ArtificialIntelligence”
OR “ComputerVision”
“DeepLearning”
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
Weusedthelistofmostlytheprimarykeywordsmentionedabovetosearchresultsrelatedtothedomainsbased insecondarykeywordsintheDimensionsapplication.
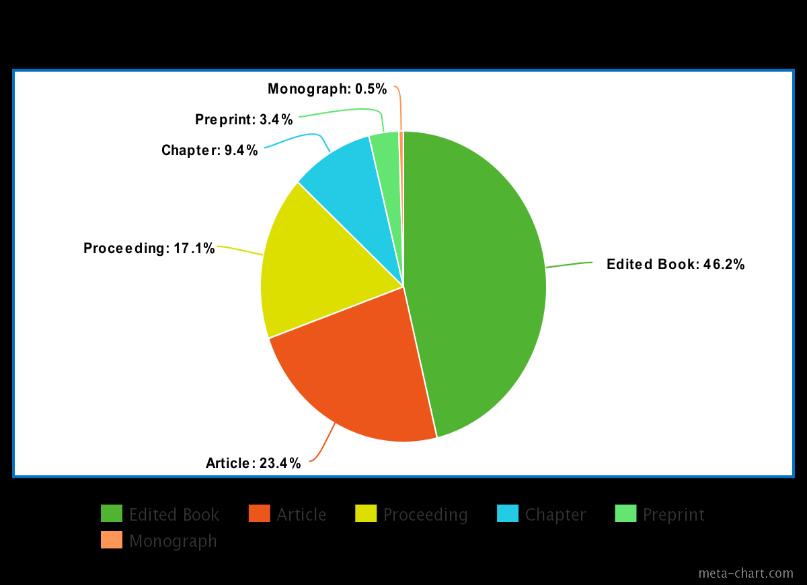
Dimensionsdatabaseisusedtofindoutthedocuments.Usingkeywords,itgivesatotalof385documentsintotal. Out of the 385 documents found in the dimensions application, these are different publication types mentioned in the Figure1.Wegot178documentsof‘EditedBooks’,90documentswhichareintheformof‘Article’,66documentsoftype ‘Proceeding’,36documentsoftype‘Chapter’,13documentsoftype‘Pre print’and2documentsoftype‘Monograph’.
Source:https://app.dimensions.ai(assessedon4January2022)
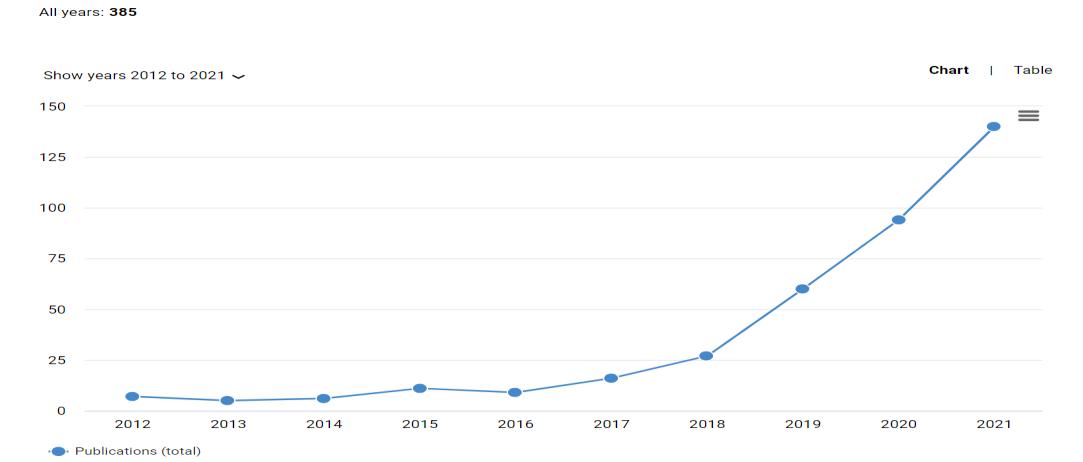
Figure2shows,thedocumentsforAnomalyDetectioninUCF CrimeDatasetshowsaninterval from2013tothe year2021.Thegraphrepresentsthenumberofdocumentspublishedinthelastyearsinthisspecific area.On analyzing, the most of the research work was carried out from 2018 to 2021. However, this finding shows that less work has been doneinthespanof2013to2017.
Source:https://app.dimensions.ai(assessedon4January2022)
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
To initiate the research, in the field of “Anomaly detection” technology using “UCF Crime dataset” an analysis is required to be carried out that contains data and information about this topic. The aim of this analysis will help to know where the studies have been conducted and the future direction. This analysis will help to analyse the development and growth in detection techniques and advancements in accuracy and dataset. The Bibliometric analysis will help in discovering new trends in this domain. The Bibliometric analysis provides insights into the contributionofvariousinstitutes,countries,authors,journals,subjectcategoriesintheresearchfield.Inthisanalysis, dataarecollectedfromtheDimensionsdatabaseusingthekeywords.
For geographic location analysis, Vos Viewer tool[9] is used to create the mapping of the countries based on its citations. Here, the inputs required is the bibliographic mapping of the data collected from Dimensions. From the given inputs,amapcanbegenerated,indicatingregionswherethemostoftheresearchworkiscitedaccordinglygivingusthe idea inwhichcountriesmostoftheresearchwork isdone.Inthemappingbelow,it showsthecountrieswhose research work is mostcited by other countries in the area ofAnomalyDetectionusingUCF Crimedataset[11]. In VosViewer,we keptminimumnumberofdocumentsofacountryas2.Wegotintotal34countriesoutofwhichonly20metthethreshold andproducethefollowingresult.
Figure 3: GeographiclocationsbasedoncitationofresearchworkforAnomalydetectioninUCF CrimeDataset Source:http://app.dimensions.ai(assessedon4January2022).
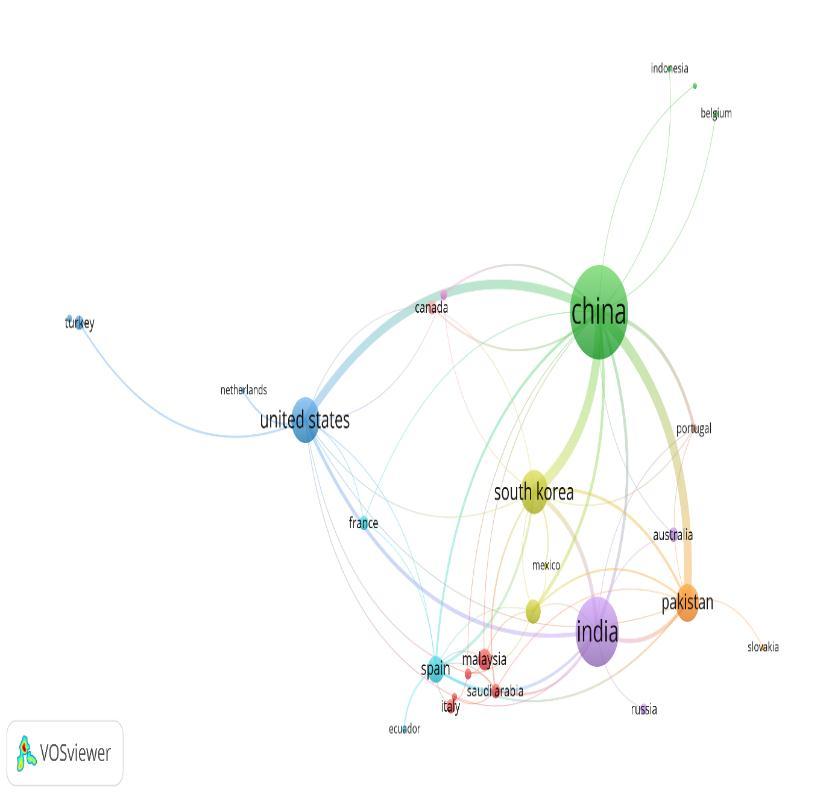
Figure3showsmappingof geographical regionofthecitationofpublishedpapers.ItisdrawnusingVosViewer tool. This mapping of countries based on their research counts and citation. It is observed that maximum research work hastakenplaceinChinaandIndiafromwherethemostofresearchworkiscitedbyothercountries.Mildresearchwork hastakenplaceincountrieslikeUnitedStatesofAmerica(USA),SouthKoreaandPakistan,and minimumworkhasbeen carriedoutinrestoftheothercountriespresentinthemaplikeSpain,Malaysia,Mexico,SaudiArabia,Australia,etc.
The top 5 countries from where most of the research work is cited are China, India, United States of America (USA),SouthKoreaandPakistan.Therefore,thesearealsothetop5countriestoproducethemostresearchinoursubject.
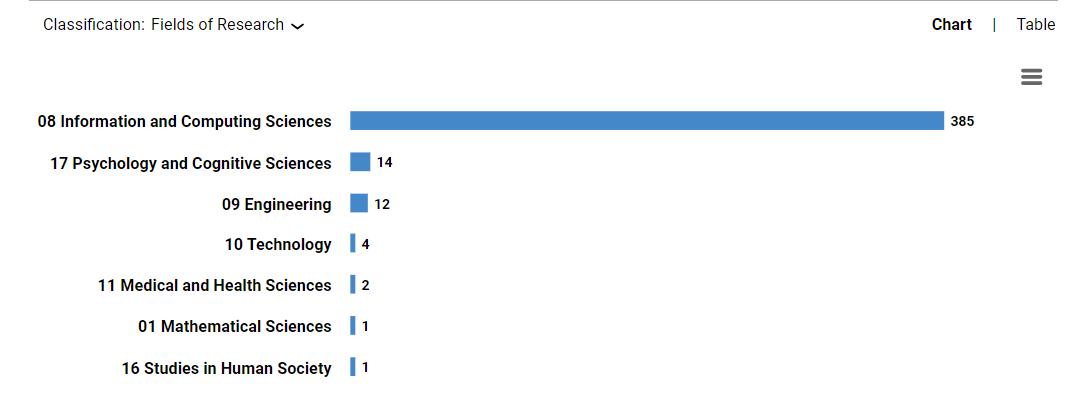
Figure 4 shows, the work is done in the subject area for Anomaly Detection using UCF Crime Dataset. From the barchart,itisclearthatthe maximumwork andresearchhasbeenimplementedin InformationandComputingScience,
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
followed by Psychology and Cognitive Sciences. But the major research work is done in the field of Information and ComputingScienceswhichisrequiredbyusandisusedasthedataforthebibliometricanalysis.
Source:http://app.dimensions.ai(accessedon4January2021)
Network Analysis is a group of Techniques, which is used to show relations among authors and to analyze their association,usingthegraphicalrepresentation.Severaltoolsareused,suchasGephiandVOSViewer.Thedataisextracted fromDimensionsforAnomalydetectionusingUCF Crimedataset.
VOSViewerisopen sourcesoftwarethatcanbedownloadedfromtheVOSviewerwebsite.Itisusedforanalyses, to create Bibliometric network. The data file can be imported to VOSViewer, which is extracted from the Dimensions database. The editor consists of three kinds of visualization: Network visualisation, Overlay visualization, and Density visualization.[9]
Figure 5 represents a cluster of the number of occurrences of co authors appearing among the papers. The relationshipoftheworkisshownbetweentheauthors.Thelinkrepresentstheauthors’workonthedocumentstheyhave published.Here,theminimumnumberofdocumentswassetto2,outof701authors70authorsmeetthethresholdvalue.
Source:http://app.dimensions.ai(accessedon4January2021)
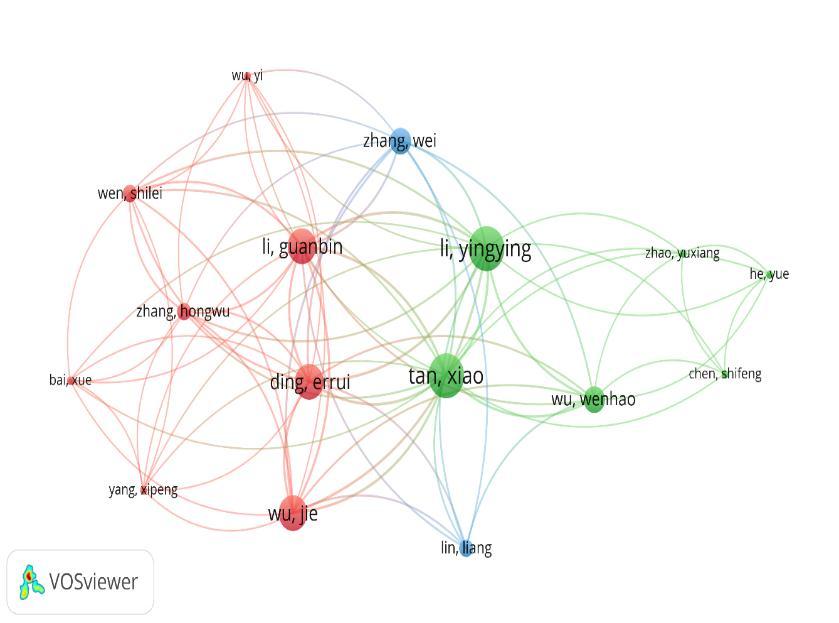
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Figure6showsthenetworkvisualizationofthecitationsreceivedbythedocuments.Thethresholdvaluewasset to1citationforeachdocument,and219documentsmetthethresholdoutof385documents.
Figure 6:Networkvisualizationofthecitationsreceivedbythedocument
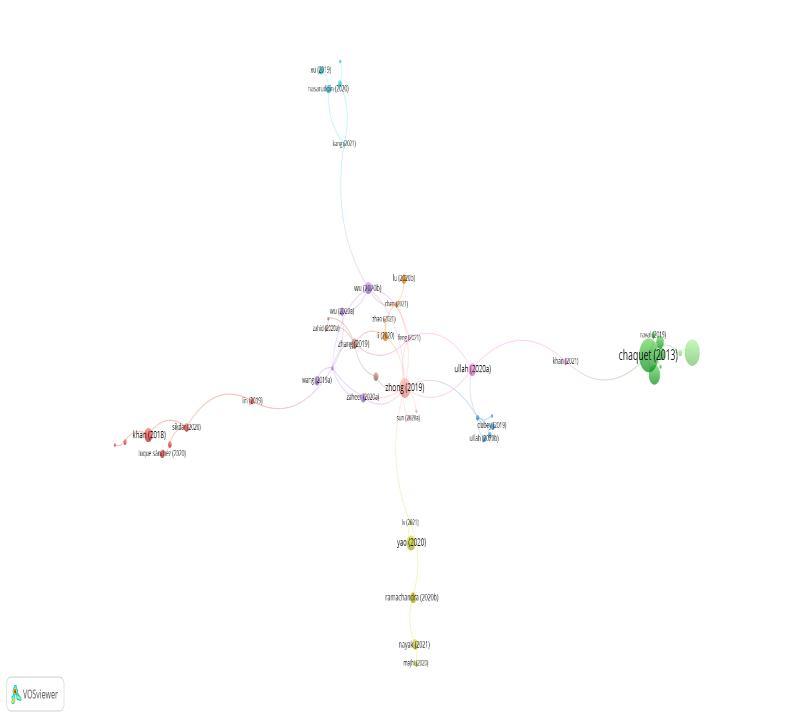
Source:http://app.dimensions.ai(accessedon4 January2021)
Figure 7 shows the citation based on different authors based on their published research works. This gives an insight on which author majorly contributed for the most cited research work. Most of the most cited authors in our subjectareMahmoodArif,ZaheerMuhammadZaigham,LeeSeung,Astrid Marcella,etc.
Figure 7:Networkvisualizationofthecitationsreceivedbytheauthorofthedocument
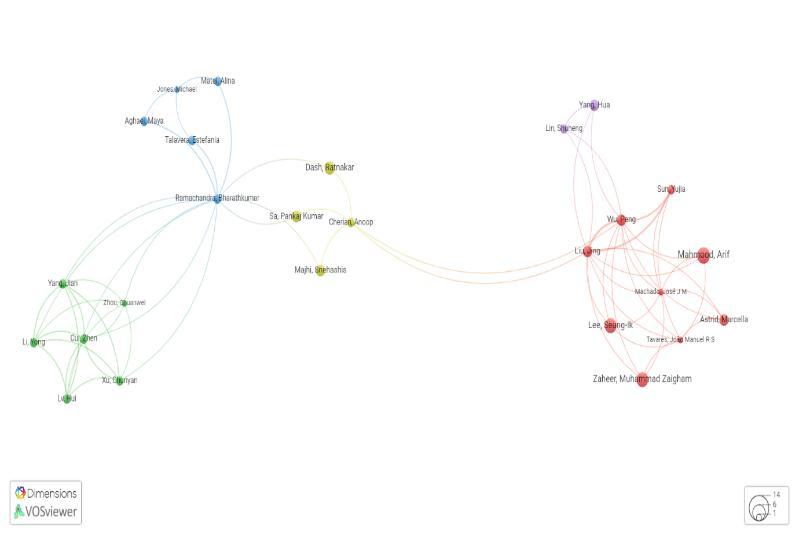
Source:http://app.dimensions.ai(accessedon4January 2021)
value:
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
Affiliation analysis shows the contribution of research work based on the universities and organisational affiliations of the authors of the documents. Table 2 shows the top ten authors along with their organizations or universities who have produced the most publications in the field of anomaly detection using UCF Crime Dataset. Here, Information Technology University, Pakistan shows the maximum contribution in the research field followed by Baidu, China.AuthorArifMahmoodfromPakistanhaspublishedthemostoftheworkrelatedtooursubjectfollowedbyXiaoTan fromChina.UniversitiesorOrganizationsfromvariouscountrieslikeSouthKorea,RussiaandIndiaalsohavecontributed well.
Table 2:ToptenAuthorsandtheirorganizationswiththemostpublicationsandtheircitationsrelatedto“Anomaly DetectionusingUCF CrimeDataset”
Source:http://app.dimensions.ai(accessedon4January2021)
Sr.No. NameoftheAuthorandtheirOrganization Publications Citations
1 ArifMahmood
InformationTechnologyUniversity,Pakistan 6 17
2 XiaoTan Baidu(China),China 5 11
3 Seung IkLee
Electronics and Telecommunications Research Institute, SouthKorea
4 MuhammadZaighamZaheer
Electronics and Telecommunications Research Institute, SouthKorea
5 17
5 17
5 SergeyVictorovichZhiganov 4 24
AminUllah SejongUniversity,SouthKorea 4 38
7 OlegSemenovichAmosov RussianAcademyofSciences,Russia
8 RatnakarDash
24
NationalInstituteofTechnologyRourkela,India 4 7
9 SungWookBaik SejongUniversity,SouthKorea 4 38
10 ErruiDing Baidu(China),China 4 10
Citation analysis is a method of determining the impact and importance of an author, article and publication by enumeratinghowmanytimesthatparticularauthor,articleandpublicationhasbeencited byotherresearchersfortheir work.Below,Table3showstheCitationdoneforAnomalyDetectiontechniques.ThetotalCitationis2,128ofanumberof publications,todate.Table4showsthelistofthetoptenpapersforanomalydetectionforUCFdatasetisshown.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Table 3:CitationsanalysisforpublicationsofanomalydetectionusingUCF CrimeDataset.
Year 2012 2013 2014 2015 2016 2017 2018 2019 2020 2021 Total No.ofCitations 5 21 53 79 88 119 147 262 474 880 2128
Source: http://app.dimensions.ai(accessedon4January2021)
Table 4:CitationanalysisofthetoptenpublicationofAnomalydetectionrelatedresearches.
PublicationTitle 2012 2013 2014 2015 2016 2017 2018 2019 2020 2021 Total Citation
Asurveyofvideodatasets forhumanactionand activityrecognition
ExplainableAI: Interpreting,Explaining andVisualizingDeep Learning
Areviewonvision techniquesappliedto HumanBehaviourAnalysis forAmbient AssistedLiving
0 9 32 24 36 39 38 37 21 36 272
0 0 0 0 0 0 0 3 59 103 165
1 8 13 24 15 23 10 14 20 10 138
Areviewonapplicationsof activityrecognitionsystems withregardtoperformance andevaluation
Graph Convolutional Label NoiseCleaner:TrainaPlug and play Action Classifier forAnomalyDetection
0 0 0 0 0 0 0 0 24 47 71
0 0 0 0 1 5 11 17 29 23 86 Multimedia Internet of Things: A Comprehensive Survey
0 1 8 27 18 17 71
Computer Vision ECCV 2016, 14th European Conference, Amsterdam, The Netherlands, October 11 14, 2016, Proceedings, PartI
11 8 10 4 5 63
1 8 27 18 17 71 Fuzzy human motion analysis:Areview
Crowd Scene UnderstandingfromVideo
4 12 18 34
11 12 13 44 Unsupervised Traffic Accident Detection in First PersonVideos
Source:http://app.dimensions.ai(accessedon4January2021)
| Impact Factor value: 7.529 |
9001:2008
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072
Table 5: Citationanalysisofthetoptenjournalsforanomalydetectiontechniques.
JournalTitle 2012 2013 2014 2015 2016 2017 2018 2019 2020 2021 Total Citations
Lecture notes in Computer Science
0 0 6 17 7 25 45 86 132 199 529
Computer Vision and Image Understanding 021 0
Expert Systems with Applications
9 32
36 39 38 37 21 36 272
0 8 13
15 23 10 17 28 21 160
IEEEAccess 0 0 0 0 0 0 1 5 42 84 132 International Journal of Distributed SensorNetworks
Advances in Intelligent Systems and Computing
0 0 0 0 1 5 11 17 29 23 86
0 0 0 0 0 2 9 11 20 23 80
Pattern Recognition 0 0 0 7 18 11 8 10 8 17 79 ACM Transactions on Multimedia Computing Communications
0 0 0 0 0 2 6 11 12 13 44
Information Fusion 0 0 0
Multimedia Tools and Applications
0 0 0
4 4 5 8 12 41
0 0 0 0 5 32 37
Source:http://app.dimensions.ai(accessedon4January2021)
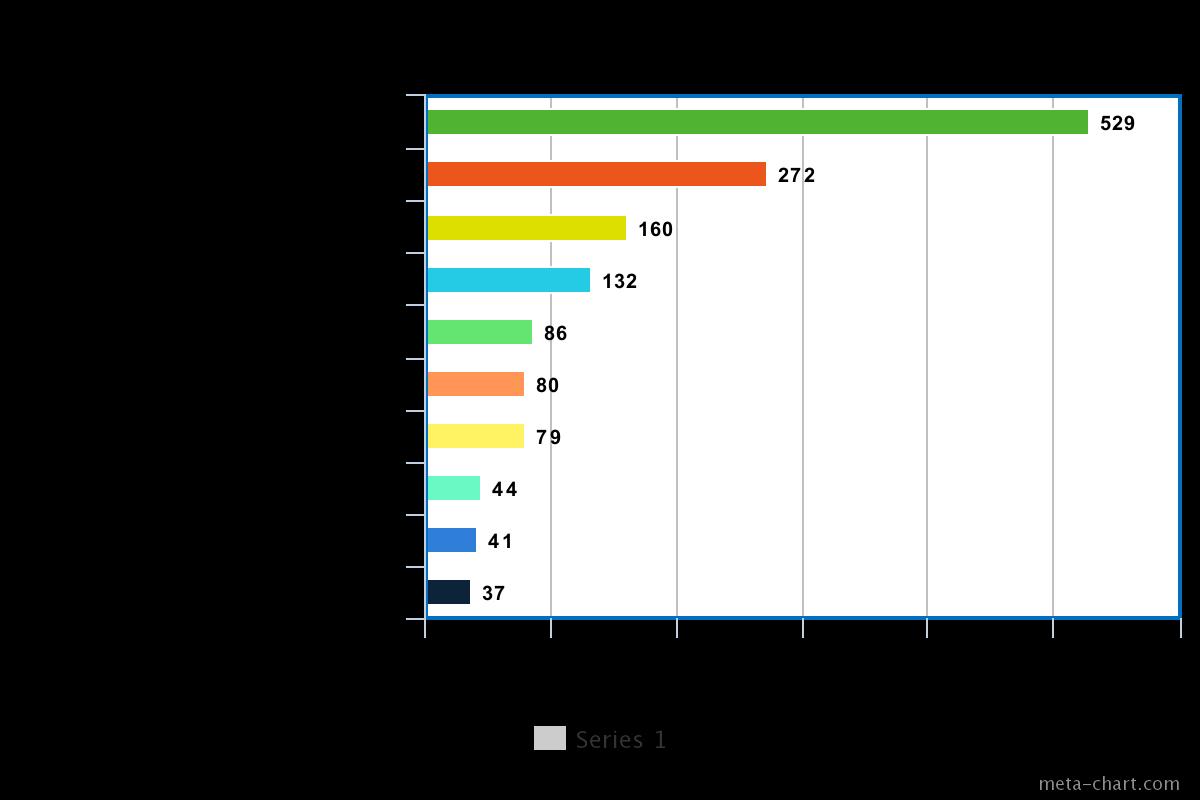
Figure 8 shows the statistical analysis of the top ten source titles based on the Citation for Anomaly detection. Fromthechart,itisobservedthatLectureNotesinComputerScienceJournalreceivethemaximumnumbersof Citation. InformationFusionandMultimediaToolsandApplicationjournalsreceivetheminimumnumberofcitations.
Factor value:
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
Figure 8: CitationAnalysisbasedonthetitleAnomalydetectionusingUCF Crimedatasetforthetoptenjournals.
Source:http://app.dimensions.ai(accessedon4January2021)
We conducted a survey related to work done in the field of smart CCTV i.e. automation of a surveillance system. The automated video surveillance system has risen as a significant research topic in the field of public security. Now a days each new place developed is being installed with a surveillance system for providing good level security to the individuals. Also the old places have installed new surveillance systems to increase their security. All these surveillance providing companies have developed new upgrades overtime and these upgrades have been provided useful for the people using them. New features like monitoring an area using an app on our phone or tablet remotely has also been introduced using IOT (Internet of Things). Artificial intelligence has also contributed a lot to these upgrades to reduce workloadandincreasetheefficiencyofsurveillance.
AtfirstwethoughttoaddaFaceDetectionSysteminthenormalsurveillancesystemtomakeitsmart.[1,3,4,6]So we looked up for the studies and work related to the same topic and we came across a lot of work which defined this systemhasalreadybeenstudiedthoroughlyandalsosomeofthesurveillanceprovidingcompanieshavealreadyappliedit intheirmainsurveillancesystem.Ithasbeentrainedtocapturevariousfeaturesofafacelikethestructureofthenose,the placement of the eyes, eye colour, shape of mouth, size of the forehead, etc. The face features of the user and the individuals which the user wants to keep in his known people directory are captured and stored in the surveillance system.Ifanunknown personentersthearea orin the vicinityoftheCCTV,theuserwill getinformedimmediately.The usercanalsousethisfeaturetoallowanindividualtoenteraplaceornotincludingthemintheknownpersons’list.Itisa veryusefulsystemforasmartsurveillancesystem.Butnow a daysduetoincreaseintheCovid 19pandemic,peopleare wearing masks everywhere they go. So, detecting their face is impossible as only the eyes and forehead are visible. To recognizeafaceaccuratelythewholefeaturesofthefaceshouldbevisibletothecamera.Alsotheuseoffacerecognition system is restricted to certain places like private homes and offices where only known people are allowed. It cannot be implementedonopenareas likemarkets,shoppingcentres,hotels,conferencehalls,etc. These days itis includedinthe SmartHomesystemwhichisapartofIOT.Alsoahigheraccuracyratewasachievedonthefacedetectionsystemwhichwe cametoknowthroughrelatedstudies.
So, to find an overall solution which could be applied in all areas closed or open we continued our survey. We came across another system related to AI to make the surveillance system smart which is the Object Detection System. [4,6]Wefoundoutalotofstudiesandworkrelatedtothissystemandwesawthatthisfieldisalsowellresearched.Inthis
Factor value:
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
systemvariousitemsorobjectphotosaretrainedandclassifiedintotheirspecificlabelslikebat,gun,suitcase,knife,etc. Mainlythephotosofharmfulobjectswereusedtotrainandclassifyintheobjectdetectionsystem.Whenevertheobjects labelled in the system are visible in the vicinity of the camera, the system marks the object and gives the label of the markedobject.Ifanyharmfulobjectisplacedorcarriedbyanindividualtheuserwillgetnotifiedthatwhichobjectisthat andthefurtheractioncanbetakenbytheuseritself.Thisobjectdetectionsystemisusefulin bothclosedandopenareas. Butitisnotanoverallsmartsolutionastheharmfulobjectdetectedcanalsobefakeoratoywhichwillmakefalsealarms Alsoalotmanyharmfulobjectscanbemadeandcanbeusedtocreateanyanomalywhicharenotknown tothesystem. Therefore,asmartsurveillancesystemcannotrelyonobjectdetectionsystemalone.
Thenwecameacross researchrelatedtocombinationoffacedetectionsystemandobjectdetectionsystemboth included in a smart surveillance system. [4] This combination system detects the face of known people, and also detects any harmful objects present in the vicinity of the camera. This surveillance system is very useful in closed areas like homes, societies, offices, etc as these are the places where user can keep a note of known people. If the face detection systemdoesn’tworkthentheobjectdetectionsystemcanbeusefultodetectmasksoranycoveroverthefaceandnotify theuser.Manycompanieshavealsoappliedthiscombinationsystemintheirsurveillancesystemtodevelopasmarthome. Alsosomestudiesshowedthatadetailedstudyisdonewiththissystem.Differentdeeplearningalgorithmsareappliedon facedetectionsystemandobjectdetectionsystemtogethighestaccuracyandtheresultispresented.Sowemovedfurther withoursurveyrelatedtoasmartsurveillancesystem.
We then found out a research related to Movement and Behaviour Detection system. [2,5] In this system the movementand behavioural patterns ofa person aretrainedand then classifiedinto differentlabelslikesitting, jumping, crying,running,etc.Wheneverapersonorgroupofpeoplearedetectedinthesurveillancecameraitcontinuouslyinforms the user about the behaviour and movement of that person or people. It just tells the user whether the person in the vicinity of the camera is doing what activity at that point of time in real time surveillance. This motion and behaviour detection system is limited only to the behavioural patterns of the person. For implementing this system in the surveillance system there is a need of a person continuously looking at the surveillance to detect a risky or suspicious behaviour by the people in the vicinity of the camera. This does not help in making the surveillance system automated whichisthemainaimofoursurvey.Sowethoughtthatthisresearchisincompleteinouraspecttomakethesurveillance systemsmart.
Thenwekeptsearchingfordifferentwaystomakeasmartsurveillancesystemthroughdeeplearning.Wefound outthatwhiletrainingthemovementandbehaviourdetectionsystemthevideosofpeopleperformingvariousactionslike sleeping,running,jumping,etcweretrainedandthenclassifiedintotheirrespectivelabels.Inthiswaywethoughtwecan train the behavioural patterns of the people performing different types of anomalies and then classify them into their respectiveanomalylabels.Intheseworldvarioustypesofanomalieshappenonadailybasis.Someofthemarecaptured oncamerawhilesomearenot.Thosewhicharecapturedoncameracanactasadatasetfortheanomalydetectionsystem. SowesearchedforworkrelatedtoAnomalyDetectionsystem.
WefoundresearchrelatedtoanomalydetectionsystembyWaqasSuhani,ChenChenandMubarakShahtomake a smart surveillance system.[7] In this system a negative bag was created which contained the videos of 12 different anomalies and a positive bag which had all the normal state videos. The positive bags would help the system to classify anomalous situations with normal situations. Then these two positive and negative bags are passed through 3D ConvolutionalNeuralNetworks(CNN)todetectthefeatures,behaviourpatterns,suddenmovementsinthedatasetvideos with good accuracy. The 12 different anomalies on which they worked on are Abuse, Burglar, Explosion, Shooting, Fighting,Shoplifting,RoadAccidents,Arson,Robbery,Stealing,AssaultandVandalism. Afterapplyingthe3DCNNmodelit wasclassifiedintoanomalyandnon anomaloussituationswhichisshownintheformoflabeltotheuser.Inthiswaythey carried outtheirversion of anomalyrecognitionsystem witha goodaccuracy.Ithink thiswasa benchmark foranomaly detectionsystemtobedescribedandimplementedusing3DCNNmodel. Thissystemlackshigheraccuracywhichcanbe achievedusingvariousimageprocessingtechniquesandtransferlearning.Alsothelabelofwhichanomalyistakingplace inrealtimeshouldappearfortheuser.
We also found research which was a further extension of the above mentioned research in which they used the UCF crime dataset which contained 12 different anomaly videos and normal videos.[8] The anomalies used here are as same as above. In this study they used image processing technique to focus only on the area where the anomaly takes placeandthentrainedthevideostoachieveagreateraccuracythenthepreviousone.Inthissystemalsotheyhaveused 3D CNN model to train the videos and then classify them into anomalous and non anomalous in the real time video
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
surveillance for theuser. Theaccuracyachievedafter theimplementationofthis researchwasupto 91% which isbetter thanabove,butitcanbeincreasedimplementingotherdeeplearningmethods.Alsothelabelsoftheanomalieshappening inrealtimesurveillanceshouldbevisibletotheuserandifthesituationisnormalitshouldbedisplayedasnormal.

Therefore, taking the research gaps of the mentioned anomaly detection systems we decided to conduct a bibliometric analysis on anomaly detection system related researches which will be useful to conduct future research to detecttheanomaloussituationsinrealtimeandmakeaSmartCCTV.

Itisobservedandanalysedthatthemajorityoftheresearchworkisrepresentedmostlybytheeditedbooksand thearticles.Itisobservedfromtheyearwisepublicationthatthoughtherewasinitiallysignificantlylessresearchwork in thisspecificfield,moreworkhasbeenrecentlycontributed.Ifthecountry wisepublicationisconsidered,Chinaranksthe highestincontributionsfollowedbyIndia.CountriesliketheUSA,SouthKorea andPakistanhavecontributedmajorlyin this field. From the subject area, it is observed that the research work is predominantly in the field of Information and Computer Science which consists of 385 publications and is our main data for bibliographic analysis. Statistical analysis based on affiliation/university and authors shows top 10 authors who contributed the most in the study of anomaly detection. Among all the authors Arif Mahmood from Information Technology University, Pakistan has contributed the mostinpublishingresearchworksrelatedtooursubject.Heisalsothemost citedauthorforreference byother authors forreferenceintheirstudyrelatedtoourtopic.Fromthecitationanalysis,outoftotal2,128citations,880citationsin the yearof2021reflectthemostsignificantinterestintheresearch.Intheanalysisoftoptenpublications,thetitle,“Asurvey of video datasets for human action and activity recognition” achieves maximum citation and is published in “Computer VisionandImageUnderstanding”journal.“LectureNotesinComputerScience”journalhasachievedthehighestcitations. AllthisinformationisobtainedthroughthebibliographicalanalysisthatweperformedontheDimensionsdata.
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 05 | May 2022 www.irjet.net
e ISSN:2395 0056
p ISSN:2395 0072
Throughtheliteraturesurveywegotthroughanumberofresearchworksofwhichregardingrealtimedetection of anomaly or any suspicious behaviour. We found out two studies related to anomaly detection. The first one was by Waqas Suhani which is the benchmark for anomaly detection for the UCF Crime dataset[11]. In this study the accuracy obtainedwasaround76%. Anotherstudywefoundwhichusedadifferentfeatureextractiontechniquetoachieveabetter accuracyof91%.
According to the bibliometric analysis, we can add documents from several other databases like Scopus, Google Scholar,WebofScience,etc.andcombinethemtocreateahugedataforbibliometricanalysis.Itwillgivenewinsightsinto the new types of documents and its overall analysis. We can use different graph generators and table generators techniquesforbettervisualeffects.
Accordingtotheliteraturesurvey,futureworkinthisresearchwouldbeintroducingalotof advancementsinthe surveillance system. We can introduce various other detection systems along with anomaly detection system like face recognition,objectrecognition,etc.WecanalsoembedhighqualityIOTsystemstohaveaverytightsurveillanceover an area.Butforthistohappenweneedtohaveaaccuracynearto100ornearly99percent.Weneedtomakethesystemto computefastanduselessresourcesaswell.Alsowecanincludeanumberofemerginganomaliesinthedataseteasilyand itshouldbetrainedaccuratelyforfutureresultsinthesystem.Wecandevelopanumberoffeatureextractiontechniques tosolvedifferentanomaliesforbetterresult.
Thecurrentstudyshowsthelimitationofthepaper,whereonlytheDimensionsdatabasehasbeenconsideredfor analysingtheliteratureworkdoneinpreviousyears.Ontheotherhand,anotherdatabaselikeGoogleScholar,Scopusand WebofSciencecanbeconsideredfortheliteraturework.Onlythedocumentsinthe“Informationand ComputingScience” field are used as a database. The document count can be increased by adding documents from other fields of study. The keywords used for this research work can be rearranged, and according to rearrangement, the outcome of documents changesdynamically.ThetoolssuchasGoogleSheet,VOSViewer,MicrosoftExcel,andMeta charthasbeenconsideredfor creating graphs, tables, charts, cluster diagram and figures. Apart from these, other tools such as Gephi and Leximancer canalsobeconsidered.Here,fortheresearchpurpose,thedatasetistakenwithinthelimitedspanofyearsfrom2012to 2021. Bigger datasets can give wide approach. A basic literature survey was done which can be increased by studying a large number of researched studies related to the subject which will provide deeper insights into anomaly detection models.Accordingtothecitedliteraturewecanseetheaccuracyofananomalydetectionsystemtorisefrom76%to91% which can be increased with future research [7,8]. There is a scopeto implement new feature extraction techniques and computationallyeasydeeplearningmodelstomaketheanomalydetectionsystemfasterandmoreaccurate.
The use of Artificial Intelligence along with normal surveillance systems will have a great advancement for automated monitoringsystems.Variousdetectionsystemscanbeincludedinanormalsurveillancesystemlikefacedetection,object detection,motiondetectionandanomalydetection,todevelopasmartCCTV.Amongthese, theanomalydetectionsystem is least researched topic and can be used for implementation by the surveillance companies. This system detects any potentialthreatorsuspiciousactivityinthevicinityofthesurveillancecamera.Itprovideswithmostoftheusecaseslike prediction, prevention, processing and customer experience for the surveillance companies. The Bibliometric study is carried outonanomalydetectionwiththeDimensionsdatabase.Theimportanceof anomalydetectionsystemsisshown by including 385 documents extracted from keywords such as anomaly detection, UCF Crime dataset, image processing, artificial intelligenceanddeepLearning.Thequantitativeanalysisinthepapershowsthatitisa recenttopicofresearch and also it is a trending topic mostly in the countries like China, India, United States of America (USA), South Korea and Pakistan.Thisbibliometricanalysiswillgiveagoodinsightandknowledgetothefutureresearchersabouttheworkdone in the previous decade. The area of anomaly detection in normal surveillance has a potential for opportunities in future research. Through our literature survey, a nice insight of anomaly detection model is obtained. It can be seen from this surveythatadoptingtheanomalydetectionsysteminthenormalsurveillancesystemhasawideapproachofautomation themonitoringsystemandthusdevelopasmartCCTVsysteminthefuturewithfurtherresearch.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 05 | May 2022 www.irjet.net p ISSN:2395 0072

1)Smart Surveillance System using Deep Learning Dayana R, Suganya M, Balaji P, Mohamed Thahir A, Arunkumar P , InternationalJournalofRecentTechnologyandEngineering(IJRTE) https://www.ijrte.org/wp content/uploads/papers/v9i1/A1464059120.pdf
2)DeepLearningbasedIntelligentSurveillanceSystem,(IJACSA)InternationalJournalofAdvancedComputerScienceand Applications https://thesai.org/Downloads/Volume11No4/Paper_79 Deep_Learning_Based_Intelligent_Surveillance_System.pdf
3)AIenabledsmartsurveillancesystemByTKeerthana,KKaviya,SDeepthiPriya,ASureshKumar
IOPPublishingLtdhttps://iopscience.iop.org/article/10.1088/1742 6596/1916/1/012034/pdf
4)VIDEOSURVEILLANCEUSINGDEEPLEARNINGBy,JosephGeorge,SreelakshmiRamchandran,NezmiKA,andShreya Nair,JOURNALOFCRITICALREVIEWShttp://www.jcreview.com/fulltext/197 1598784584.pdf
5) Smart Home Anti Theft System: A Novel Approach for Near Real Time Monitoring and Smart Home Security for WellnessProtocol,mdpi,https://www.mdpi.com/2571 5577/1/4/42/htm
6) A deep learning approach to building an intelligent video surveillance system, By ,Jie Xu, Springer https://link.springer.com/article/10.1007/s11042 020 09964 6#article info
7) Real world Anomaly Detection in Surveillance Videos Waqas Sultani Chen Chen , Mubarak Shah Department of ComputerScience,Pakistanand CenterforResearchinComputerVisionInformationTechnologyUniversity,Universityof CentralFlorida,Orlando,FL,USA,ComputerVisionFoundation(CVF) https://openaccess.thecvf.com/content_cvpr_2018/papers/Sultani_Real World_Anomaly_Detection_CVPR_2018_paper.pdf
8) Deep anomaly detection through visual attention in surveillance videos, Nassaruddin Nassarudin, Kahlil Muchtar, Afdhal Afdhal and Alvin Prayuda Juniartaa Dwiyantoro, Springer Open https://journalofbigdata.springeropen.com/articles/10.1186/s40537 020 00365 y
9)VOSviewerdownloadwebsite https://www.vosviewer.com/download
10)Dimensionsdatabase https://app.dimensions.ai
11)UCFCrimedataset https://www.kaggle.com/mission ai/crimeucfdataset