International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
Rutuja Patil, Adarsh Charak, Utkarsha Bhad, Sachin Deshmukh
Rutuja Patil Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
Sachin Deshmukh Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
Utkarsha Bhad Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033 Adarsh Charak Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
3Example: Prof. Vinodkumar Bhutanal, Dept. of Computer Engineering, JSPM’S RSCOE, Maharashtra, India ***
Abstract Safetyplaysamajorroleintoday’sworld.User authenticationcanbedefinedasaprocedureusedtoverifythe identityoftheuser,authenticationisanessentialterminthedigitalworldsoastoprotecttheclient’s/user’scritical data storedonlineoroffline.Variousmechanismsaregraduallyevolvingtoauthenticateusersinvariousscenarios.Atofficesand workplacesaswell,thisuserauthenticationisofutmostimportanceinordertoavoidanymal practicesifanyaswellasto maintainindividualworkprivacyintheorganization.Thisprojectaimsatdevelopingauserauthenticationsystemforoffices basedontheircompanygeneratedloginIDandpasswords,One Time Password(OTP)generationandfacerecognition.The systemalsohasfeaturessuchasauto savingdatatoserverandauto logout
Key Words: AutoSaved, Auto logout, Face recognition, Login ID and passwords credentials, One Time Password (OTP).
Asoftoday,computersareprotectedwithvarioussecuritysoftware,proxyservers,firewalls,stillthedatainsidethecomputer hasvulnerabilities.Weaiminproviding4stepsecuritysothatthedataisnotaccessedillegally.Thisapproachgivesmore securitybyrestrictingunauthorizedaccessandautologoutfeature.Wecanguarantee integrityandconfidentiality.Onestrong pillarthatisone timepasswordmakesitmoredifficulttogetillegalaccesstodata.
Theauthentication,confidentialityandprivacyofdataisneededintoday’sworld.IOTthatistheinternetofthingsisevolving widely.TheIoTarchitectureisjustmodifiedversionofsomeexistingdatacommunicationtools.Duetothevulnerabilitiesof the Internet, security and privacy issues should be considered and resolved before the IOT is globally deployed. Direct interactionofsmartdeviceswithintheimmediatelivingspaceofhumansintimidatesnewsecurityvulnerabilities.Research hasbeenledindevelopingcustomizedtoolsforcomputersecuritytoestablishconfidentiality,integrityandavailability.Incase ofanykindofsecurityfailure,oursystemprovidestheusersdatafullydatasecurityandassuranceofprivacy.Theaimisto preventionsystemthatisadaptiveandreceptivetonewthreatsandprovidesmorecontrolofowneronthedatastoredon systembyrestrictingtheaccesstoparticularuserforspecificfilewithlimitedrights.Theideabehindittocreatesoftwarethat willprotectthedatafromallkindsofattacksandmaintainentireconfidentialityofthedata.
1 Therehasbeenauseofthreetirearchitectureinpaper“EffectiveAuthenticationForRestricingUnauthorizedUser”,[1]for providingsecuritytothesystem.ThosetiersareFacialrecognition,FingerprintScanningandOTP.Allthesetiersgivea greatstrengthtosecurityofsystem.Incaseifthereisanattackonsystem,themeasuresareprovidedsoastonotleakthe importantdatafromthesystem.ByusingAES512allthedataisencryptedwhichcanonlybedecryptedbyaspecifickey.
2 Securityandprotectionofpersonaldataonline/offlineisverycriticalasdataisbecomingcriticalandsmartphonesare vulnerabletoillegalunauthorizedaccess.User authenticationallowslegitimatepersontoaskthedata.Mobilesaremade secured by using the methodology of biometric authentication using user’s physical traits. The survey provides an overview of the current state of the art approaches for continuous user authentication using behavioral biometrics captured by smartphones’ embedded sensors, including insights and open challenges for adoption, usability, and performance.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
3 BiometricUser authenticationofauserbyusingtheirownuniquetraitsis themosteasiestandcommonwaytoidentifya person. In [3], a multimodal biometric user verification system with similar twin shows the fingerprint, face and lip classificationmodelusingSupportVectorMachine.
4 Paper ‘Multi BiometricAuthenticationUsingDeepLearningClassifierforSecuringofHealthcaredata;[4]itanalysesthe resultsofusingbothfingerprintsaswellasonlinesignatures.Herethesignaturesareverifiedusingthedynamictime warpingmethodology.Theweightedsumruleisappliedfortheprocessofbiometricfusion(signaturesandfingerprints). Deeplearningclassifierisproposedinthisworkformulti biometricsauthentication.Whenabiometricauthentication requestissubmittedtoimprovetheauthenticationperformance,theproposeduser authenticationsystemusesdeep learningtoautomaticallyselectanaccuratematchingimage.
5 Now a dayswecanseetheconceptofcloudevolvinghavingbenefitslikehighperformance,accessibility,betterstoring capacityetc.Storagehasbecomeahugeissueforusershavinglargedata,cloudprovidesasolutionofunlimitedstorageto auser.Yetcloudhasvariousvulnerabilitiesandusersdonotwishtocompromisesecurity.Sotheaimistofigureoutand addressthesecurityissuesbyusingcrossvalidationstrategy.
6 User Authenticationisalwaysdoneatthestartoftheprogram,butinordertounderstandthegenuinenessoftheuserthe authenticationmustbecontinuouslygoingon.In[6],SuhailJavedQuraishiandSarabjeetSinghBediproposedtheusageof key strokeusedasbiometriccharacteristicforcontinuouslyauthenticatingtheuser.Authenticationusingbiometricuses basicallythreestagessuchastheenrollmentstage,theverificationstage,andtheidentificationstage.Identificationstage markstheuserasanauthenticateduseronlyiftheinputpatternismatchedwiththeprofilepatternorelsethesystemwill automaticallylogout.Thereisnorestrictiononinputdataduringenrolment,verification,andidentificationstage.The techniqueusedtoclassifytheauthenticateduser’sinputfromothersisUnsupervisedOne classSupportVector.ThisUser authentication system can be used in areas like in non proctored online examination, Intrusion and Fraud Detecting Systems,etc.
7 Paper“ARobuste Invigilation SystemEmployingMultimodalBiometricAuthentication”,presentsthedevelopmentof robust,flexible,transparentandcontinuousauthenticationmechanismfore assessments.Therehasbeenasignificant growthofstudents/usersusinge learningsande assessments.Themajorconcernisthattheymightcheatusingthese resourcesintheirexams.Soinordertoreducethechancesofcheatinginonlineexaminations,biometricsofthestudent can be used to check whether the legitimate student is attempting the exam the system gives a continuous user identification by using biometrics;: an eye tracker is used to record the student’s eye movement; and, the speech recognitionisusedtodetectcommunicationfromstudent’send.Thefocusof[7]particularlyisonthedevelopment3D Facial Authentication.Experimentshavealsobeenconductedinordertotestthesebiometricstoseewhetherthestudent ischeatingDuringtheexperiment,participants'biometric data,eye movement,andhead movementshavebeencollected usingasoftware.
8 Asoftoday,computersareprotectedwithvarioussecuritysoftware,proxyservers,firewalls,stillthedatainsidethe computerhasvulnerabilities.Weaiminproviding4stepsecuritysothatthedataisnotaccessedillegally.Thisapproach gives more security by restricting unauthorized access and auto logout feature. We can guarantee integrity and confidentiality.Onestrongpillarthatisone timepasswordmakesitmoredifficulttogetillegalaccesstodata.
9 Paper“EffectiveAuthenticationforAvoidingUnauthorizedUserAccess”,presentedaevolvedRoleBasedAccessControl modelbymodifyingpreviousrolebasedaccesscontrolinStructureQueryLanguage.Thismodelevaluates&executes security policies that contain access conditions against the dynamic nature of data. The goal is to create or use a mechanismfor forwardlooking,assertiveandflexiblesecurity featurestoregulateaccesstodatainthedatastorage.This iseasilyachievedbyintegratingroles&authenticatedaccessrulesandimplementedthrougheffectiveaudittrail.
10 Paper[10]presentedastateofartaboutbiometrichand,differenttechniquesused.Biometricisessentiallyusedtoavoid risksofpasswordeasytofindorStoll;withasslogansaveTimeandAttendance.Themeasurementandanalysisofunique physicalorbehavioralcharacteristics(suchasfingerprintorvoicepatterns)especiallyasameansofverifyingpersonal identity..Biometricsisrecognizingapersonbasedonhisphysicaluniquecharacteristicslikefingerprint,irisrecognition, facerecognitionetc.Thismethodologyprovidesusmoreuniquenessandsecurity.Asthesecharacteristicscannotbefaked, thechancesofthecomputersystemhavingbiometricsgettingaccessedillegallyarenegligible.Traditionallythebiometrics meantsignatures,keysandpasswords.Biometricsisdefinedas‘LifeMeasure’inGreekdictionary.Biometricsisavery usefulmethodwhichiswidelyusedincriminalidentificationandprisonsecurity.ThesecanbeusedtoprotecttheATMs, phones, systems, smartcards etc. Thus, Biometric is a widely evolving technology which is very efficient for user authenticationandsecurity.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
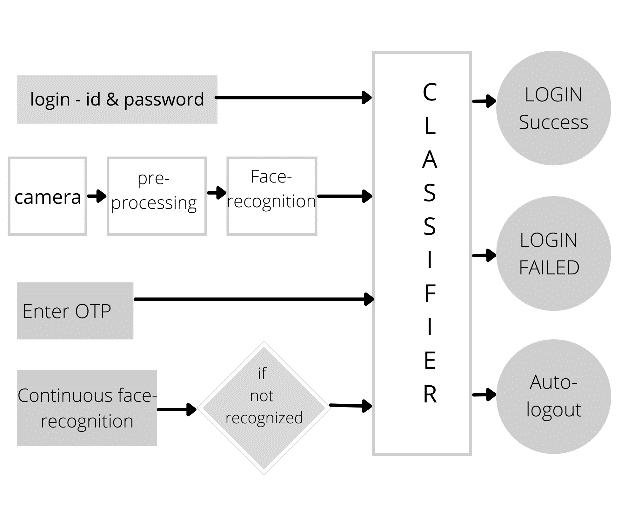
Afacerecognitionsystemisacomputerapplicationforautomaticallyidentifyingorverifyingapersonfromadigitalimageora video frame from a video source. For the enhancement of security of accounts and privacy of users features like face recognitionandOne TimePassword(OTP)areused.Facerecognitiontechnologyhelpsthemachinetoidentifyeachandevery useruniquely.Fig1illustratesthesystemarchitectureofproposedsystem.Itconsistsofathree stepsecureauthentication processforworkingemployeesintheirrespectiveorganizations.
As stated above, at first the user needs to enter the unique login Id and password combination provided to them by the company.Oncethatmatcheswiththedatabase,nextstepistogeneratetheOTPontheregisteredmobilenumber.Ifnot, furtheraccesstologinintothesystemwillbedenied.IfcorrectgeneratedOTPisenteredintothesystem,theusermoves secondstepaheadtogainaccesstothesystem.Oncethisisdone,nextcomesthefacerecognition.Withthehelpofwebcams presentwitheachandeverysystem,thefaceinfrontofcamisdetected.Intheprocessofcontinuous authentication,alive pictureoftheuseriscapturedthroughwebcamanditisthencomparedwiththeimageindatabase.Ifthisimagematches,user can get the access to operate that particular system. Haar Cascade Classifier is used to implement face recognition. An additionalfeatureofautosaveandauto logoutisalsoincludedinthissystem.Supposetheemployeehappenstoleavetheir deskduetosomereasons,thewebcamwillbecontinuouslydetectingandcapturingtheimagesifany.Incaseanunknownface image other than that system user, is captured by the webcam, the whole work/data will be automatically saved to the company’sserverandthesystemwillautomaticallylogout,sothat,theunknownusercannotmakeanymanipulationsinthe userswork
Theautosavefeaturehelpstheusertore continuetheworkformthepointhe/shehadleftit.Henceaveryefficient,safeand reliablesystemisdeveloped.
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
Fig.3.LoginPages
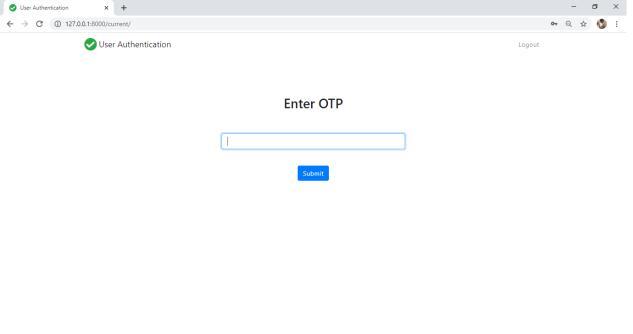
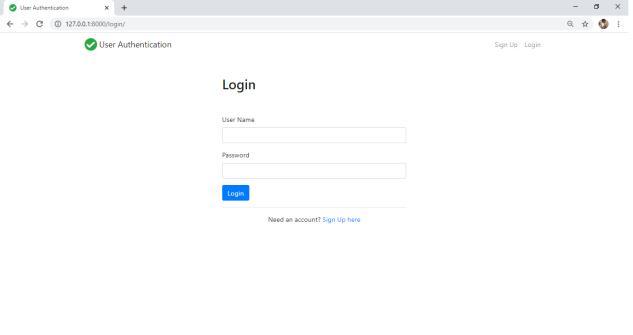
Fig.4Home
Fig.5.EnterOTP
Fig.6FINAL_PAGE
IRJET | Impact Factor value: 7.529 | ISO 9001:2008
e ISSN: 2395 0056
p ISSN: 2395 0072
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p ISSN: 2395 0072
Wehaveused4stepsforgivingtheaccuratesecurityandauthenticationpurpose.Thesesteps include 1.credentialsfor loggingin2.FacialrecognitionusingHAAR CASCADE3.OneTimePasswordand4.Auto Logout.Thesearethefourpillarsof oursystemwhichgiveproperauthenticationandsecurity..Thisapproachgivesmoresecuritybyrestrictingunauthorized accessandautologoutfeature.Wecanguarantee integrityandconfidentiality.Onestrongpillarthatisone timepassword makesitmoredifficulttogetillegalaccesstodata
1. Patil, A., Rana, D., Vichare, S., & Raut, C. (2018).Effective Authentication for Restricing Unauthorized User. 2018 InternationalConferenceonSmartCityandEmergingTechnology(ICSCET).doi:10.1109/icscet.2018.8537323
2. IEEEINTERNETOFTHINGSJOURNAL(IOTJ)21Sensor based;ContinuousAuthenticationofSmartphones’Users UsingBehavioralBiometrics:AContemporarySurveyMohammedAbuhamad,AhmedAbusnaina,DaeHunNyang,and DavidMohaisenarXiv:2001.08578v210onMay2020
3. Multimodal Biometric User Verification System with Similar Twin using SVM 2 B.Lakshmi priya, M.PushpaRani InternationalJournalofRecentTechnologyandEngineering(IJRTE)ISSN:2277 3878,Volume 8Issue 6,march2020
4. Multi BiometricUser AuthenticationTechniqueUsingDeepLearningClassifierforSecuringofHealthcareDataDr. GandhimathiAmirthalingam1,HarrinThangavel1Volume8,No.4,July August 2019
5. Cloud Security: To Prevent Unauthorized Access Using an Eeficient Key Management Authentication Algorithm S.NaveenKumar1,K.1Nirmala2InternationalJournalofEngineering&Technology,(IJET) ;7(1.1)2018
On the key strokes as Continuous User Biometric Authentication Mr.SuhailQuraishi, SarabjeetsinghBedi at InternationalJournalofEngineeringandAdvancedTechnologyIJEATISSN:2249 8958,,August 2019
IRJET

Impact Factor value: 7.529
ISO 9001:2008