International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
MACHINE LEARNING BASED SECURITY SYSTEM FOR OFFICE PREMISES
Rutuja Patil, Adarsh Charak, Utkarsha Bhad, Sachin Deshmukh
Rutuja Patil Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
Sachin Deshmukh Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
Utkarsha Bhad Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
Adarsh Charak Undergraduate Student JSPM’s RSCOE, Maharashtra, INDIA Pune 411033
3Example: Prof. Vinodkumar Bhutanal, Dept. of Computer Engineering, JSPM’S RSCOE, Maharashtra, India
***
Abstract -
Safetyplaysamajorroleintoday’sworld.User authenticationcanbedefinedasaprocedureusedtoverifytheidentityofthe user,authenticationisanessentialtermInthedigitalworldsoastoprotecttheclient’s/user’scriticaldatastoredonlineor offline.Variousmechanismsaregraduallyevolvingtoauthenticateusersinvariousscenarios.Atofficesandworkplacesas well, this user authentication is of utmost importance in order to avoid any mal practices if any as well as to maintain individualworkprivacyintheorganization.Thisprojectaimsatdevelopingauserauthenticationsystemforofficesbasedon theircompanygeneratedloginIDandpasswords,One Time Password(OTP)generationandfacerecognition.Thesystemalso hasfeaturessuchasauto savingdatatoserverandauto logout
Key Words: AutoSaved, Auto logout, Face recognition, Login ID and passwords credentials, One Time Password (OTP).
1. INTRODUCTION
Now a dayswehavevarioustoolsforprotectingsystemfrommaliciousactivitysuchasproxyservers,firewalls,security software,andsoon.Stillthedataprivacycannotbeassured,andhencewehavetocomeupwithasoftwareoratoolwhichhas negligible chances of getting attacked. We aim in providing 4 step security so that the data is not accessed illegally. This approachgivesmoresecuritybyrestrictingunauthorizedaccessandautologoutfeature.Wecanguarantee integrityand confidentiality.Onestrongpillarthatisone timepasswordmakesitmoredifficulttogetillegalaccesstodata.
Theauthentication,confidentialityandprivacyofdataisneededintoday’sworld.IOTthatistheinternetofthingsisevolving widely.TheIoTarchitectureisjustmodifiedversionofsomeexistingdatacommunicationtools.Duetothevulnerabilitiesof the Internet, security and privacy issues should be considered and resolved before the IOT is globally deployed. Direct interactionofsmartdeviceswithintheimmediatelivingspaceofhumansintimidatesnewsecurityvulnerabilities.Research hasbeenledindevelopingcustomizedtoolsforcomputersecuritytoestablishconfidentiality,integrityandavailability.Incase ofanykindofsecurityfailure,oursystemprovidestheusersdatafullydatasecurityandassuranceofprivacy.Theaimisto preventionsystemthatisadaptiveandreceptivetonewthreatsandprovidesmorecontrolofowneronthedatastoredon systembyrestrictingtheaccesstoparticularuserforspecificfilewithlimitedrights.Theideabehindittocreatesoftwarethat willprotectthedatafromallkindsofattacksandmaintainentireconfidentialityofthedata.
2. LITERATURE REVIEW
Therehasbeenauseofthreetirearchitectureinpaper“EffectiveAuthenticationForRestricingUnauthorizedUser”,[1]for providingsecuritytothesystem.ThosetiersareFacialrecognition,FingerprintScanningandOTP.Allthesetiersgiveagreat strengthtosecurityofsystem.Incaseifthereisanattackonsystem,themeasuresareprovidedsoastonotleaktheimportant datafromthesystem.ByusingAES512allthedataisencryptedwhichcanonlybedecryptedbyaspecifickey.
Security and protection of personal data online/offline is very critical as data is becoming critical and smartphones are vulnerabletoillegalunauthorizedaccess.User authenticationallowslegitimatepersontoaskthedata.Mobilesaremade securedbyusingthemethodologyofbiometricauthenticationusinguser’sphysicaltraits.Thesurveyprovidesanoverviewof the current state of the art approaches for continuous user authentication using behavioral biometrics captured by smartphones’embeddedsensors,includinginsightsandopenchallengesforadoption,usability,andperformance.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
BiometricUser authenticationofauserbyusingtheirownuniquetraitsis themosteasiestandcommonwaytoidentifya person. In [3], a multimodal biometric user verification system with similar twin shows the fingerprint, face and lip classificationmodelusingSupportVectorMachine.
Paper ‘Multi BiometricAuthenticationUsingDeepLearningClassifierforSecuringofHealthcaredata;
[4]itanalysestheresultsofusingbothfingerprintsaswellasonlinesignatures.Herethesignaturesareverifiedusingthe dynamictimewarpingmethodology.Theweightedsumruleisappliedfortheprocessofbiometricfusion(signaturesand fingerprints). Deep learning classifier is proposed in this work for multi biometrics authentication. When a biometric authenticationrequestissubmittedtoimprovetheauthenticationperformance,theproposeduser authenticationsystemuses deep learningtoautomaticallyselectanaccuratematchingimage.
Now a days we can see the concept of cloud evolving having benefits like high performance, accessibility, better storing capacityetc.Storagehasbecomeahugeissueforusershavinglargedata,cloudprovidesasolutionofunlimitedstoragetoa user.Yetcloudhasvariousvulnerabilitiesandusersdonotwishtocompromisesecurity.Sotheaimistofigureoutandaddress thesecurityissuesbyusingcrossvalidationstrategy.
User Authenticationisalwaysdoneatthestartoftheprogram,butinordertounderstandthegenuinenessoftheuserthe authenticationmustbecontinuouslygoingon.In[6],SuhailJavedQuraishiandSarabjeetSinghBediproposedtheusageofkey strokeusedasbiometriccharacteristicforcontinuouslyauthenticatingtheuser.Authenticationusingbiometricusesbasically threestagessuchastheenrollmentstage,theverificationstage,andtheidentificationstage.Identificationstage marksthe userasanauthenticateduseronlyiftheinputpatternismatchedwiththeprofilepatternorelsethesystemwillautomatically logout.Thereisnorestrictiononinputdataduringenrolment,verification,andidentificationstage.Thetechniqueusedto classifytheauthenticateduser’sinputfromothersisUnsupervisedOne classSupportVector.ThisUser authenticationsystem canbeusedinareaslikeinnon proctoredonline examination,IntrusionandFraudDetectingSystems,etc.
Paper“ARobuste Invigilation SystemEmployingMultimodalBiometricAuthentication”,presentsthedevelopmentofrobust, flexible,transparentandcontinuousauthenticationmechanismfore assessments.Therehasbeenasignificantgrowthof students/usersusinge learningsande assessments.Themajorconcernisthattheymightcheatusingtheseresourcesintheir exams.Soinordertoreducethechancesofcheatinginonlineexaminations,biometricsofthestudentcanbeusedtocheck whetherthelegitimatestudentisattemptingtheexamthesystemgivesacontinuoususer identificationbyusingbiometrics;: aneyetrackerisusedtorecordthestudent’seyemovement;and,thespeech recognitionisusedtodetectcommunication fromstudent’send.Thefocusof[7]particularlyisonthedevelopment3DFacial Authentication.Experimentshavealsobeen conducted in order to test these biometrics to see whether the student is cheating During the experiment, participants' biometric data,eye movement,andhead movementshavebeencollectedusingasoftware.
Asoftoday,computersareprotectedwithvarioussecuritysoftware,proxyservers,firewalls,stillthedatainsidethecomputer hasvulnerabilities.Weaiminproviding4stepsecuritysothatthedataisnotaccessedillegally.Thisapproachgivesmore securitybyrestrictingunauthorizedaccessandautologoutfeature.Wecanguarantee integrityandconfidentiality.Onestrong pillarthatisone timepasswordmakesitmoredifficulttogetillegalaccesstodata.
Paper“EffectiveAuthenticationforAvoidingUnauthorizedUserAccess”,presentedaevolvedRoleBasedAccessControlmodel bymodifyingpreviousrolebasedaccesscontrolinStructureQueryLanguage.Thismodelevaluates&executessecuritypolicies that contain access conditions against the dynamic nature of data. The goal is to create or use a mechanism for forward looking, assertive and flexible security features to regulate access to data in the data storage. This is easily achieved by integratingroles&authenticatedaccessrulesandimplementedthrougheffectiveaudittrail.
Paper[10]presentedastateofartaboutbiometrichand,differenttechniquesused.Biometricisessentiallyusedtoavoidrisks ofpasswordeasytofindorStoll;withasslogansaveTimeandAttendance.Themeasurementandanalysisofuniquephysical or behavioral characteristics (such as fingerprint or voice patterns) especially as a means of verifying personal identity.. Biometrics is recognizing a person based on his physical unique characteristics like fingerprint, iris recognition, face recognitionetc.Thismethodologyprovidesusmoreuniquenessandsecurity.Asthesecharacteristicscannotbefaked,the chancesofthecomputersystemhavingbiometricsgettingaccessedillegallyarenegligible.Traditionallythebiometricsmeant signatures,keysandpasswords.Biometricsisdefinedas‘LifeMeasure’inGreekdictionary.Biometricsisaveryusefulmethod whichiswidelyusedincriminalidentificationandprisonsecurity.ThesecanbeusedtoprotecttheATMs,phones,systems, smartcardsetc.Thus,Biometricisawidelyevolvingtechnologywhichisveryefficientforuserauthenticationandsecurity.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
Objectives:
1.EffectiveAuthenticationforAvoidingUnauthorizedUserAccess.
2.EffectiveAuthenticationforRestrictingUnauthorizedUser.
3. Evaluationof3Dfacialconfirmation.
3. RELATED WORK
Module1 ProposedFramework
e ISSN: 2395 0056
p ISSN: 2395 0072
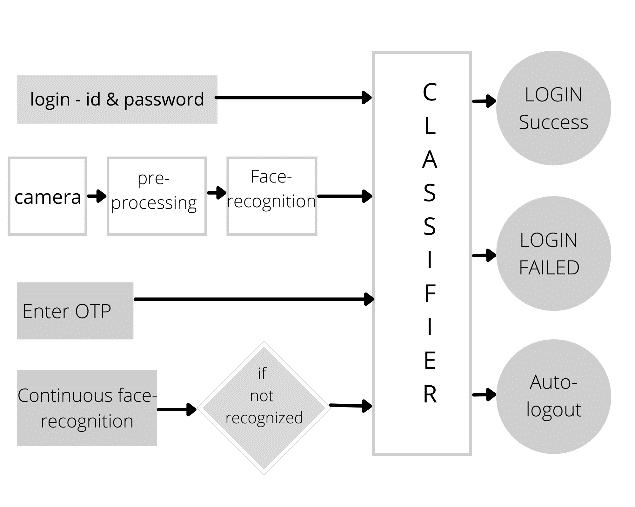
AfaceacknowledgmentframeworkisaPCapplicationfornaturallyrecognizingorcheckinganindividualfromanadvanced pictureoravideooutlinefromavideosource.HighlightslikefaceacknowledgmentandOne TimePassword(OTP)areutilized fortheimprovementofsafetyofrecordsandprotectionofclients.Faceacknowledgmentinnovationassiststhemachinewith recognizingeverysingleclientparticularly.Proposedframeworkcomprisesofafour venturesecureverificationprocessfor workingrepresentativesintheirseparateassociations.
Module2 Login
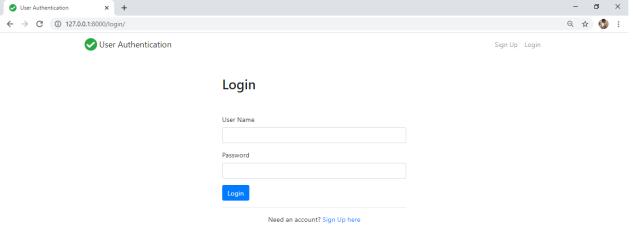
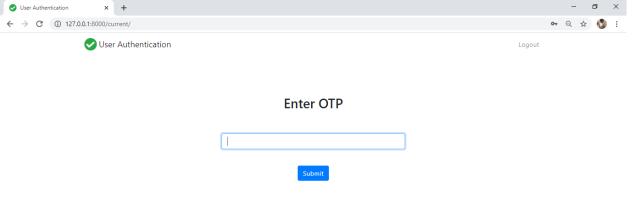
Firstly,theclient/userneedstoentertheloginIdandsecretkeywhichareuniqueprovidedbytheorganization.Whenthat coordinateswiththedataset,thenextphaseistocreatetheOTPontheenlistedphonenumber.Iftheuserisfailedtoprovide theOTP,furtheraccesstothesystemisdenied.IftheOTPisaccurate,theuserisdirectedtothenextphase.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
Module3 OTPandFaceRecognition
e ISSN: 2395 0056
p ISSN: 2395 0072
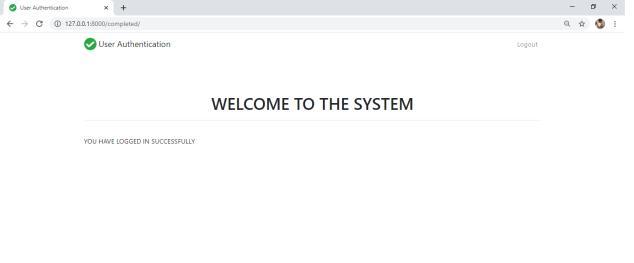
Wheneverthisisdone,nextcomesthefacerecognitionandacknowledgment.Withtheassistanceofwebcamspresentwith everysinglesystem,thefacebeforecamisdistinguished.Alivepictureiscaughtconsequentlythroughawebcamintroduced onthegadget,whichiscontrastedandthepictureputawayinthedataset.Assumingthispicturematches,clientcangetthe admittancetoworkthatspecificframework.HaarCascadeClassifierisutilizedtoexecutefaceacknowledgment.Anextra component of autosave and auto logout is likewise remembered for this framework. Assume the representative ends up passing around their work area because of certain reasons, the webcam will be ceaselessly recognizing and catching the picturesifany.
Incaseanobscurefacepictureotherthanthatframeworkclient,iscaughtbythewebcam,theentirework/informationwillbe consequentlysavedtotheorganization'sserverandtheframeworkwillnaturallylogout,sothat,theobscureclientcan'tmake anycontrolsintheclient’swork.Theautosavehighlightassiststheclienttore proceedwiththeworkwithframingthepoint he/shehadleftit.Thus,anextremelyeffective,protectedanddependableframeworkiscreated.
Module4 Algorithms
Haar CascadeAlgorithm
2. MakingIntegralPictures
Adaboostcoachingandcascading
4. RESEARCH GAP ANALYSIS
Byreferringseveralrelatedworks,thefollowingchallengesassociatedwiththeexistingframework
1. HaarCascadeAlgorithmmayfailtorecognizethefaceifthefaceismanipulatedbywearingsunglassesortiltinghead towardsanyside.
2. Fortrainingthemodel,manualinterventionisrequired.
3. TheexistingsystemworksonlyonWindowsOS.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p ISSN: 2395 0072
5. CONCLUSIONS
Wehaveused4stepsforgivingtheaccuratesecurityandauthenticationpurpose.Thesesteps include 1.credentialsfor loggingin2.FacialrecognitionusingHAAR CASCADE3.OneTimePasswordand4.Auto Logout.Thesearethefourpillarsof oursystemwhichgiveproperauthenticationandsecurity..Thisapproachgivesmoresecuritybyrestrictingunauthorized accessandautologoutfeature.Wecanguarantee integrityandconfidentiality.Onestrongpillarthatisone timepassword makesitmoredifficulttogetillegalaccesstodata
REFERENCES
1. Patil, A., Rana, D., Vichare, S., & Raut, C. (2018).Effective Authentication for Restricing Unauthorized User. 2018 InternationalConferenceonSmartCityandEmergingTechnology(ICSCET).doi:10.1109/icscet.2018.8537323
2. IEEEINTERNETOFTHINGSJOURNAL(IOTJ)21Sensor based;ContinuousAuthenticationofSmartphones’Users UsingBehavioralBiometrics:AContemporarySurveyMohammedAbuhamad,AhmedAbusnaina,DaeHunNyang,and DavidMohaisenarXiv:2001.08578v210onMay2020
3. Multimodal Biometric User Verification System with Similar Twin using SVM 2 B.Lakshmi priya, M.PushpaRani InternationalJournalofRecentTechnologyandEngineering(IJRTE)ISSN:2277 3878,Volume 8Issue 6,march2020
4. Multi BiometricUser AuthenticationTechniqueUsingDeepLearningClassifierforSecuringofHealthcareDataDr. GandhimathiAmirthalingam1,HarrinThangavel1Volume8,No.4,July August 2019
5. Cloud Security: To Prevent Unauthorized Access Using an Eeficient Key Management Authentication Algorithm S.NaveenKumar1,K.1Nirmala2InternationalJournalofEngineering&Technology,(IJET) ;7(1.1)2018
On the key strokes as Continuous User Biometric Authentication Mr.SuhailQuraishi, SarabjeetsinghBedi at InternationalJournalofEngineeringandAdvancedTechnologyIJEATISSN:2249 8958,,August 2019
IRJET

Impact Factor value: 7.529
ISO 9001:2008
