International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net

International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
e ISSN: 2395 0056
p ISSN: 2395 0072
1UG Student SRM Institute of Science and Technology, Ghaziabad, India
2UG Student SRM Institute of Science and Technology, Ghaziabad, India
3UG Student SRM Institute of Science and Technology, Ghaziabad, India
4UG Student SRM Institute of Science and Technology, Ghaziabad, India
5Asst. Professor, Dept. of Computer Science & Engg, SRM Institute of Science and Technology, Ghaziabad, India
Abstract User authentication is a vital step in protecting information, and facial bio metrics might assist in this regard. Face bio metrics seems to be more natural, simple to use, and less intrusive to humans. Unfortunately, emerging research has revealed that face bio metrics are extremely sensitive to spoofing assaults. A spoofing attackoccurswhenapersontries to masquerade as someone else by falsifying data and thereby gaining illegitimate access. Inspired by image quality assessment, characterization of printing artifacts, and differences in light reflection, we propose to approach the problem of spoofing detection from texture analysis point of view. This report discusses many types of assaults against visual spectrum facial recognition systems. We propose comprehensive data sets for assessing the susceptibility of recognition systems and the effectiveness ofcountermeasures. Finally, we give a brief overview of anti spoofingstrategiesfor visual spectrum face identification, as well as a viewpoint on difficulties that remain unresolved.
Key Words: Biometrics; Facial Recognition; Facial Anti Spoofing; Facial Presentation Attack Detection (PAD); RGB camera based anti spoofing methods; Computer Vision; Pattern Recognition
Biometricsisamultidisciplinaryfieldconcernedwith measuringandmappingspecificbiologicaltraits,such asfingerprints,faces,palmveins,andsoon,inorderto usethemasanindividualisedrecognitioncode[1]
Facerecognitionsystemsareutilisedinmanydomains, such as pattern recognition, computer vision, and imageprocessing,forvariouspurposes.
Biometric traits are divided into two categories: physical traits andbehavioural traits like signatures, voices,andkeystrokes.Biometricsiscriticalforawide rangeoftechnologies.
Therehasbeenwidespreadknowledgeforalongtime thatfacerecognitionsystemshaveweakresistanceto presentation attacks and are easily spoofed with photographs, videos, or 3D models of the enrolled person’sface.Thehumaneyeisquiteeffectiveatde tectingcounterfeits,butthisseemsnottoapplytoface verification systems. Therefore, face recognition systemsshouldbetreatedasafirstprioritybeforethey are implemented unsupervised as a replacement for usercredentials
Currently,biometricsystemsarebeingdeployedina varietyofenvironmentssuchasairports,laptops,and mobilephones,andthenumberofusersisbecoming more familiar with day to day life, so security is becoming increasingly important. As a result, this paper attempts to evaluate the various methods available in the various stages of this identification technique,aswellasthevariousclassificationmethods available.Thistechnologicaladvancementhasallowed biometricstobeusedinawiderangeofapplications, including forensics, access control, surveillance, and bordersecurity.
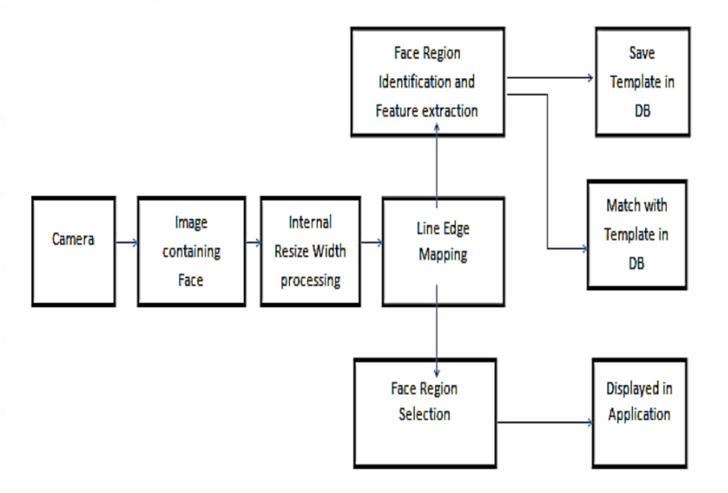
Recentadvancesinthefieldoffacialbiometricshave rekindledinterestinlivenessdetectionasasolutionto spoofingattackproblems.Thegoalofthispaperisto review recent research efforts and map them into a cohesive taxonomy based on liveness indicators, as wellastoprovideafurtherclassificationonfaceanti spoofing techniques. Various components of a face recognitionprocessareshowninFig.1[2].
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
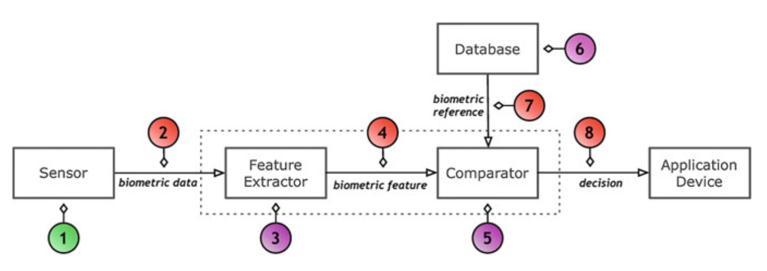
There are two types of biometric system attacks: indirectanddirect.[3]Figure2depictsaflowdiagram of a typical biometric recognition system, with numberedpointsindicatingpotentialattackpoints.
e ISSN: 2395 0056
p ISSN: 2395 0072
characteristicsinordertogainanunfairadvantage.As input sensors for face recognition systems, standard imagecamerasareused.Thesedevicescanbeusedto recordsingleormultiplephotosorvideosequencesof usersattemptingtogainaccesstoprotectedresources. Figure3depictsanidealstaticconfigurationforaface authentication system. In these cases, the camera is embeddedinalaptopthathasbeenpre programmed withafacerecognitionsystem.
Users position themselves so that the camera can capturetheirfacesforaslongasthesystemrequires. Theenvironmentalconditionsduringdataacquisition areanimportantconsiderationduringtherecognition process. It is a well known fact that poor lighting conditions,pose,andageing,amongotherfactors,can significantlyimpairone'sabilitytorecognisepeople[5]

Inamoremodernconfiguration,usersmayusea mobilephonetoaccessprotectedresourcesonthe phoneitself,orasaterminalforotherapplications. Mobiledevicescanalsobeusedtoidentifyother peopleinforensicsorsurveillanceapplications.The environmentalacquisitionconditionsinsuchcases canvarygreatly[6].
Fig. 2: Possibleattackpointsinagenericbiometric system
Indirect attacks are launched from within the recognition system, requiring intruders to first gain accesstothesystem'sinternals.Onceinside,indirect attackers can tamper with feature extractors or comparators, manipulate biometric references, or exploit potential flaws in communication channels. Indirect attacks can be mitigated by increasing the security of communication channels and restricting accesstotheinternalsofrecognitionsystemssothat cyber criminals do not exploit them. Direct, presentation,orspoofingattacksarecarriedoutatthe sensorlevel[4](shownasattacktype1inFig.2),which isbeyondthebiometricsystemmanufacturer'scontrol. Insuchcases,theattackerattemptstodirectlyfoolthe sensor, and thus no physical protection mechanisms are available. In a direct attack, also known as a presentationattack,apersonattemptstoimpersonate another person by falsifying their biometric
Inrecentyears,therehavebeennumerousstudiesin thesubjectofspoofingdetectionsystems.Thissection provides an overview of some of the techniques employed in this sector. The quantity of research articles,conferences,andjournalswithfreshideashas substantiallyincreasedinthelasttenyears,promoting spoofingbio metricsecurity.
Oneoftheearlystudiesonfacespoofdetection, accordingtoourknowledge,waspublishedin2004
Fig. 3. Examplesetupofafacerecognitionsystem
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
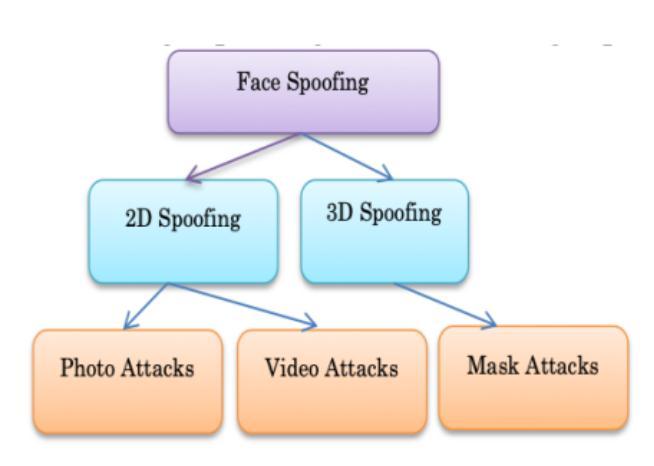
byLietal.[7]Facerecognitionforaccesscontrolhas growninprominenceinrecentyears,andthisarea hasgottenalotofattentionfromresearchersinthe lastfiveyears.Thegeneralclassificationofspoofing isshowninFigure4,whichcanbedividedintotwo categories:2D[8]imagespoofingand3Dimage spoofing[9].
e ISSN: 2395 0056
p ISSN: 2395 0072
Theclient’sfaceora3D[12]maskoftheclient’sfaceis used as a spoofing artefact in this attack. It is quite difficult to develop a defence against such mask attacks.Theface’s3Dstructureishidden,andtheface is mimicked here. Photo and video attacks can be mitigated with depth cues, whereas mask attacks requireonlymaskattacksclues.Althoughtheideaof fooling a biometric system by wearing a mask that imitates the face of another user has been floating aroundforawhile.

Theprimarypremiseofthisformoffraudulentac cess attempt is to offer a recognition system with a photographofalegitimateuser.Thephotographsare takenfromsocialnetworkingsitesoradigitalcamera by the attackers. The attacks might be on printed graphics on paper or images projected on a screen, suchasamobilephoneortablet.Photographicmasks are a more advanced sort of attack in the photograph[10].Thesearethemasksmadefromhigh qualityphoto cutmaterial.Duringattacks,animposter is placed behind the attacker so that specific facial expressions,suchaseyeblinks,canbereplicated.
Replayattacksarethenameforthesetypesofattacks. Thesearethemoreadvancedspoofsofthisshot.Inthis attack,insteadofusingstillphotos,theclient’svideo fromadigitaldeviceisutilised.Inthisattack,insteadof using still photos, the client’s video from a digital deviceisutilised.Somevideosfrommobilephonesand computersaretargeted,andtheyaremoredifficultto detectnotjustbecausetotheirtexture,butalsodueto theirdynamics[11].
2022, IRJET
Impact Factor value: 7.529
Kantetal.proposedamethodthatcombinedacamera andathermalsensor.Boththecameraandthethermal sensorcapturetheusersfordetection,andeachframe is compared to a thermal image from the thermal sensor,whichdistinguishesthefaceskinfromthe2 D surface.Usingthermalfacerecognition,theyachieveda 98percentaccuracy[13].
Jukkaetal.proposedamethodthatinvolvespassing theinputimagethroughafacedetectorandanupper body detector. After detecting the upper body, the imageissubjectedtoaspoofingmediumdetectorfor further classification of real and spoof faces. They obtainedanEERof6.8percentbycombiningtheCASIA andNUAAdatasets[14]
Facespoofingdetectionresearchhasbeengoingonfor over many years. Since then, several methods for detectingfacespoofinghavebeenproposed,including printattacks,replayattacks,and3Dmaskattacks.We provideabriefsummaryandanalysisofpublished2D facespoofdetectionmethodsbecauseourfocusison 2Dfacespoofattackdetection(onsmartphones).The methodsthathavebeenpublishedcanbedividedinto sixcategories:(i)facemotionanalysis,(ii)facetexture analysis,(iii)face3Ddepthanalysis,(iv)imagequality analysis,(v)frequencydomainanalysis,
ISO 9001:2008
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
Face motion analysis based spoofing detection methodsextractbehaviouralcharacteristicsoftheface, such as eye blinks and lip or head movement. To localisethefacialcomponents,thesemethodsrequire accurate face and landmark detection. In order to estimate the facialmotions,multiple framesmustbe used. Because these methods are designed to detect printattacks,theycannothandlevideoreplayattacks withfacialmotions.

Spoofing detection methods based on face texture analysiscapturetexturedifferences(duetodifferent reflection properties of the live face and spoof material)betweenfaceimagescapturedfromlivefaces and face images captured from different spoof mediums (e.g., paper and digital screen). These methodscandetectspoofsbasedonasinglefaceimage and thus have a relatively quick response time. However,whenusingsmalltrainingsetswithalimited numberofsubjectsandspoofingscenarios,facetexture analysis based methods may have poor generalizability.
Spoofing detection methods based on 3D depth analysis estimate a face's 3D depth to distinguish betweena3Dlivefaceanda2Dspoofface.Spooffaces presentedona2Dplanarmediumare2D,whereaslive faces are 3D objects. As a result, if the 3D depth informationofafacecanbereliablyestimated,these methods canbe quiteeffectiveinidentifying2Dface spoofattacks.Face3Ddepthanalysismethodstypically relyonmultipleframestoestimateaface'sdepthor3D shapeinformation.
Imagequalitydifferencesbetweenliveandspoofface imagesareusedbyspoofingdetectionmethodsbased onimagequalityanalysis.Becausespooffaceimages andvideosarecreatedbyrecapturinglivefaceimages andvideosinphotographsoronscreens,therewillbe colour,reflection,andblurrinessdegradationsinthe spooffaceimagescomparedtothelivefaceimagesand videos. These methods have been found to be very generalizable to a variety of scenarios. However, researchonfacespoofingdetectionusingimagequality analysisislimited.
Anti spoofing methods based on frequency domain analysenoisesignalsincapturedvideotodistinguish betweenliveandspooffaceaccess.Thereisadecrease inlowfrequencycomponentsandanincreaseinhigh
value:
e ISSN: 2395 0056
p ISSN: 2395 0072
frequencycomponentsduringtherecaptureofprinted photosorvideoreplays.
While many of the published methods in the five categories listed above produce positive results for intra database testing, their effectiveness in cross database testing scenarios has not been thoroughly evaluated.Thefewpublicationsthatdidconductcross databasetestinghavegenerallyreportedpoorresults. Consider fusion of multiple physiological or behavioural cues to improve the robustness of face spoof detection methods in cross database testing scenarios.
Thedatabasewascreatedusinganunspecifiedgeneric webcamthatrecordedphotoattacksandrealaccesses to 15 differentidentities[15]. As showninFig. 6, the database is divided into three sessions with varying lighting conditions. Because not all subjects participated in the three acquisition campaigns, the amountofdatacollectedacrosssessionsisunbalanced. Participantsinallsessionswereaskedtolookfrontally at thewebcamera,maintaininganeutral expression andavoidingeyeblinksorheadmovementsasmuchas possible. The webcam would then record for approximately 25 seconds at 20 frames per second, fromwhichasetofframeswouldbehand pickedfor the database. The database does not include the originalvideosequence.
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
TheReplay AttackDatabaseanditssubsets(thePrint Attack Database[16] and the Photo Attack Database[17])arefaceanti spoofingdatabasesmade up of short video recordings (about 10 seconds) of both real access and spoofing attacks on a face recognition system. This was the first database designedtoaidintheresearchofmotion basedanti spoofing techniques. This database was used in the CompetitiononCountermeasuresto2DFacialSpoofing Attacksin2011and2013.
Samples were taken from 50 different people. The entiredatabasecontainsspoofingattemptsfromthree majorcategoriesof themostobviousattacksonface recognitionsystems:
Printattacks:attackswithphotographsprinted onapaper
Photoattacks:digitalphotographsdisplayedon ascreenofanelectronicdevice
Videoattacks:videoclipsreplayedonascreen ofanelectronicdevice
TheCASIAFaceAnti spoofingDatabase(CASIA FASD) introducesfaceattacksofvaryingimagingquality.Itis adatabasethat,liketheNUAAPhoto,treatsspoofing detectionasabinaryclassificationtask.Incontrastto thelatter,thisdatabasecontainsvideofilesthatcanbe used to experiment with texture, motion, or fusion techniquesforanti spoofing[16].
The CASIA FASD data can be used in seven different anti spoofing protocols, which are divided into two subsets for training and testing spoofing classifiers. Thereisnodevelopmentsetavailableforfine tuning countermeasures. In total, 12 videos of about 10 secondseachareavailableforeachidentity:threereal accesses,threewarpedphotoattacks,threecutphoto attacks,andthreevideoattacksproducedusingeachof thepreviouslydescribeddeviceswithvariablequality.
Without ant spoofing measures, most cutting edge facial biometric systems are vulnerable to attacks, becausetheytrytomaximiseidentitydiscrimination rather thandeterminingwhetherthe presentedtrait
e ISSN: 2395 0056
p ISSN: 2395 0072
originates from a living legitimate client. Due to the pressingneedtoimprovethesecurityandrobustness of face biometrics, a number of spoofing detection schemeshavebeenproposedtoaddresstheproblemof presentationattacks.
A common anti spoofing countermeasure is liveness detection,whichdetectsphysiologicalsignsoflifesuch aseyeblinking,facialexpressionchanges,andmouth movements.Toprovidemoreevidenceoflife,Eulerian motionmagnification[18]wasusedtoenhancesubtle changesinthefaceregion[19]thatwouldotherwisego unnoticed without a closer inspection. Within the contextofthesecondcompetitionon2Dfacialspoofing countermeasures.However,thealgorithmneedstobe improvedinordertoperformbetterinmoredifficult andadversarialacquisitionconditions.
Othermotioncuescanbeusedforfaceantspoofingin additiontothefacialmotionusedinlivenessdetection. Itcanbeassumed,forexample,thatthemovementof planarobjects,suchasvideodisplaysandphotographs, differs significantly from that of real human faces, whicharecomplexnonrigid3Dobjects.Ifafacespoof isnottightlycroppedaroundthetargetedfaceorhas an incorporated background scene, scenic fake face, stationaryfacerecognitionsystemsshouldbeableto observeahighcorrelationbetweentheoverallmotion ofthefaceandthebackgroundregions.However,while being recognised, itcan become confused betweena fixedsupportphoto attackandamotionlessperson.
Face images captured from face spoofs may visually resemble images captured from live faces; thus, detecting face spoofing is difficult based on a single face image or a relatively short video sequence. Dependingonthe imagingandfake face quality,itis nearly impossible for humans like us to tell the differencebetweenagenuineandafakefacewithout any scene information or unnatural motion or facial texturepatterns.However,wecanimmediatelydetect anything suspicious in the view, such as someone holdingavideodisplayoraphotographinfrontofthe camera. Contextual information is a very important visualcueforfacespoofingdetection,accordingtothe
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3856
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
experiments conducted by the CASIA Face Anti spoofingDatabaseandtheNUAAPhotographImpostor Database.
FRR (False Rejection Rate), FAR (False Acceptance Rate,numberofzero effortimpostoraccessattempts wrongly accepted), and SFAR are the three most commonly used metrics for evaluating liveness detection metrics (Spoofing False Acceptance Rate, corresponding to the number of spoofing attacks wronglyaccepted).Thetruethreatposedbyaspoofing databasetoaspecificrecognitionsystemcanthusbe determined.
Spoofing (i.e., direct) attacks are among the tangible threats and vulnerabilities that current face recognitionsystemsface.Spoofingafacerecognition systemispossiblebypresentingaphotograph,avideo, or a three dimensional shaped mask of a targeted identitytotheinputcamera.Thisresearchproblemhas recentlyreceivedincreasedattention(i.e.,facespoofing attacks).Thisisevidencedbytheincreasingnumberof articlesandcompetitionsthathavebeguntoappearin majorbiometricforums.Inthischapter,werevealed thethreatsoffacespoofing,presentedtheevolutionof the available databases and protocols for evaluating face spoofing and anti spoofing based on visual information, and thoroughly discussed the various approachesproposedintheliteraturethusfar.
Most cutting edge facial biometric systems are vulnerable to spoofing attacks in the absence of
e ISSN: 2395 0056
p ISSN: 2395 0072
spoofing countermeasures, because they strive to maximise discriminability between identities regardless of whether the presented trait originates fromalivinglegitimateclientornot.Theproposedanti spoofing methods in the literature have shown very promising results on individual databases, but they may lack generalisation to the varying nature of spoofing attacks encountered in real world applications. This implies that a network of attack specificspoofingdetectorsmayberequiredtocombat various spoofing attacks. The existing databases for spoofing and anti spoofing analysis have been and continuetobeusefulforstudyingspoofingproblems, butitisimpossibletoanticipateandcoverallpossible attackscenariosindatabases.
1. Bledsoe, W. W. The model method in facial recognition,PanoramicResearchInc.,PaloAlto. CA,TechnicalReport,TechnicalReportPRI:15, 1964.
2. Dhawanpatil,T.,&Joglekar,B.,“FaceSpoofing DetectionusingMultiscaleLocalBinaryPattern Approach”,IEEE,InternationalConferenceon Computing, Communication, Control and Automation,2017,pp.1 5.
3. Ratha, N.K., Connell, J.H., Bolle, R.M.: An analysisofminutiaematchingstrength.In:Pro ceedings of the International Conference on Audio and Video Based Biometric Person Authentication (AVBPA), pp. 223 228. Springer Verlag(2001).
4. Jain,A.K.,Flynn,P.,Ross,A.A.(eds.):HandbookofBi ometrics.Springer Verlag(2008).
5. Li,S.Z.,Jain,A.K.(eds.):Hand book of Face Recognition.Springer Verlag(2011).
6. McCool C, Marcel S, Hadid,A., Pietikainen,M., MatejkaP,Cernocky,JPohN,Kittler J,Larcher, A., Levy, C., Matrouf, D., Bonastre, J.F. Tresadern, P Cootes T: Bi modal person recognition on a mobile phone: using mobile phone data. In: IEEE ICME Workshop on Hot TopicsinMobileMultimedia(2012).
7. Li, Jiangwei, Yunhong Wang, Tieniu Tan, and AnilK.Jain."Livefacedetectionbasedonthe analysis of fourier spectra." In Biometric Technology for Human Identification, vol. 5404, pp. 296 304. International Society for OpticsandPhotonics,2004.
8. de Freitas ereira, Tiago, Andre Anjos, Jose arioDe artino,andSe astien arcel. B
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page3857
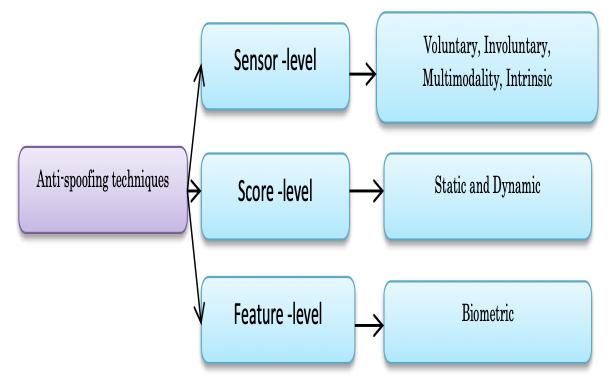
Figure 7: VariousAnti spoofingtechniquesInternational Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
TOP based countermeasure against face spoofing attacks." In Asian Conference on ComputerVision,pp.121 132.Springer,Berlin, Heidelberg,2012.
9. Wang, Tao, Jianwei Yang, Zhen Lei, Shengcai Liao, and Stan Z. Li. "Face liveness detection using 3D structure recovered from a single camera." In Biometrics (ICB), 2013 International Conference on, pp. 1 6. IEEE, 2013.
10. Ghorpade,Shruti,DhanashriGund,Swapnada Kadam, and Mr RA Jamadar. "Image Quality Assessment for Fake Biometric Detection: Application to Face and Fingerprint Recognition." International Journal of Emerging Technologies and Engineering (IJETE)Volume2.
11. Gal all , Javier, Se astien arcel, and Julian Fierrez. "Image quality assessment for fake biometric detection: Application to iris, fingerprint, and face recognition." IEEE transactions on image processing 23, no. 2 (2014):710 724.
12. Wang, Tao, Jianwei Yang, Zhen Lei, Shengcai Liao, and Stan Z. Li. "Face liveness detection using 3D structure recovered from a single camera." In Biometrics (ICB), 2013 International Conference on, pp. 1 6. IEEE, 2013.
13.Kant C and Sharma N 2013 Fake face recognitionusingfusionofthermalimageand skin elasticity International Journal for ComputerScienceandInformationSecurity
14. KomulainenJ,HadidAandPietikainenM2013 Context based face anti spoofing 6th International Conference on Biometrics: Theory,ApplicationsandSystems(BTAS)
15. X. Tan, Y. Li, J. Liu, L. Jiang, Face liveness detectionfromasingleimagewithsparselow rank bilinear discriminative model, in Proceedings of the European Conference on Computer Vision (ECCV), LNCS, vol. 6316, Heraklion,Crete,Greece,(Springer,2010),pp. 504 517
16. A. Anjos, M.M. Chakka and S. Marcel, Motion based counter measures to photo attacks in face recognition IET Biometrics, 3(3), 147 158 (2014)
17. M.M.Chakka,A.Anjos,S.Marcel,R.Tronci,B. Muntoni,G.Fadda,M.Pili,N.Sirena,G.Murgia, M. Ristri, F. Roli, J.Yan,D. Yi, Z. Lei, Z. Zhang, S.Z. Li, W.R. Schwartz, A. Rocha, H. Pedrini, J.
e ISSN: 2395 0056
p ISSN: 2395 0072
Lorenzo Navarro, M. Castrillon Santana, J. Maatta,A.Hadid,M.Pietikainen,Competition on countermeasures to 2 D facial spoofing attacks, in International Joint Confer ence on Biometrics (IJCB),Washington,DC.,USA,2011
18. Wu, H.Y., Rubinstein, M., Shih, E., Guttag, J., Durand, F., Freeman, W.T.: Eulerian video magnificationfor revealing subtle changes in the world. ACM Trans. Graph. (SIGGRAPH 2012)31(4)(2012).
19. Chingovska,I.,Anjos,A.,Marcel,S.:Anti spoofinginaction:jointoperationwithaverificati onsystem.In:ProceedingsofIEEEConference onComputerVisionandPatternRecognition, WorkshoponBiometrics(2013).
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008