Big Data: Privacy and Security Aspects
the ever growing era of technology and commercialization, data has been a very important research topic for techno savvy people. 'Data' is something that is processed by one party and provided by another party. On a commercial level, companies and consumers are the two parties in which the exchange of data occurs as per the benefits and requirements of the company and the consumer. Hence, on different stages and scales, various transactions and exchanges of data lead to concern about the privacy and security of the data. At the company level, a lot of data having complex information, high variety, increased volume, and having high velocity is exchanged among multiple parties. This data is called 'Big Data '. Such huge and complex data makes the exchange to be complicated and the preservation of privacy and security of big data requires various mechanisms. This review paper puts light on the various concerns about the protection of privacy and security of big data. The infrastructure, the mechanisms of protection, and the cycle of big data are discussed inthis paper.
Key Words: Big data; Privacy; Security; Information Security:Mechanisms;SecurityProtection;Infrastructure; thecycleofbigdata;DataAnalysis;SocialApplications.
1. INTRODUCTION
In the last few years, data has become a prime significantfactorforbusinesses, companies,governments, themedicalsector,engineeringsectortonameafew.Data isanessentialassetforthesecompaniesandorganizations tocarryouttheirbusinessplans,marketingstrategiesand to make decisions. A single smartphone user generates approximately40Exabytesofdataeverymonth.Existence of this data is in the form of pictures, emails, music and songs, texts, videos, searches, etc. The number of users of smartphonesisinthemillions andthusdatageneratedis quitealotoftraditionalcomputingsystemstoprocessand analyzeit.Thiscollectionoflargeandcomplexsetsofdata is termed "Big Data". As we live in the era of big data, we needtogothroughalltheimportantaspectsofbigdata.So how do we classify a set of data as Big Data? This can be explained with velocity, volume, variety, value and veracity. Big data is super beneficial once it is processed andanalyzedproperly.
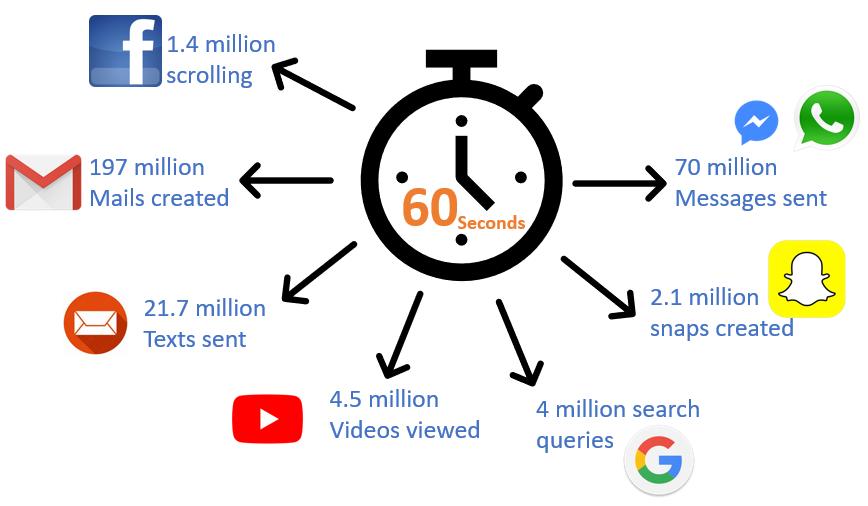

Froma privacyandsecurity perspective, a glance is to be taken on the fact that, for marketing purposes, making business strategies and research; many
companies use data collected from consumers but they maynotprovideafutureeconomicprofittoconsumerson a significant level. Instead this collected data may be misused to track the irrelative history of a consumer. Many businesses, companies and organizations use petabytes of data about their customers and company. These companies use technology to store and analyze data. Classification of this information (extracted from analyzeddata)becomesevenmorecritical.Theseissuesof big data are related not only to variety and volume but also to security and privacy. A balance between data privacyandinformationneedsistobemaintained.Hence, this review paper focuses on Big data privacy and securitysolutions.
LITERATURE REVIEW
Paper[1]writtenbyMr.Apparaoetal.proposeda method of data privacy and protection in transaction logs andthreatsinstealingtheusercredentials.Also,thepaper had proposed and explained some newer methodologies to prevent privacy in the transaction field. Big data is not structured and it is very big in volume that it is a tough process to store such a huge amount of data. So, one technology named Robust technology comes into the picture which helps to store data and gives tools which analyze it. To increase privacy in big data, especially in transaction logs, a mechanism called the auto tier mechanismisexplained.
Paper[2] i.e. journal written by S. K. Saravanan et al. explained the concept of the use of encryption and decryptiontechniquestopreventthesecurityandprivacy

aspectsofBigDatainformation.Sometechnologiesposea serious threat to one's information like Data mining. Encryptinganddecryptingthedatamakesitunreadableto third parties and the data is stored safely. But, to emphasize the security in big data, ‘SHA3’ algorithms of encryptionanddecryptionareused.
Inpaper[3],B.BGuptaetal.proposedsecurityand privacy issues regarding the information on an online platform, log in into apps, and cloud computing. Cyber threat is considered a major task today because the issue is being faced by all countries whether it is developed or developing. On multimedia, users share most of the memories of their life and the explosion and use of that information wrongly creates distrust among users regardingsocialmedia.So,itisaverychallengingtaskthat is taken into consideration because Big data is not only hugeinvolumebutalsoitisunstructured.
In paper[4], Julio Moreno et al. explained problems and challenges related to security issues in Big Data. The author further stated that security issues were much more significant when big data was introduced. Manyresearchers,therefore,focusedontheir researchon solutions for security and privacy issues. Moreover, the protection of the Hadoop system is of prime significance for researchers. If a proper framework on security in big dataiscarriedoutbythegovernment,therewillbearapid spreadofbigdatatechnology.BigDatatechnologywillbe usefulforthebasicdevelopmentofupcomingtechnology.
In Paper[5], Jose Moura et al. explained the infrastructuresecurityinbigdataconsideringtheassured modeledprocessingofdataandprovidedthemechanisms regardingsecurityfordatabasesthatarenotinthespecific storage pattern. The author stated about the aspects of dataanalysisthroughdatamining,granularaccesscontrol, granular audits, and data provenance. The author also proposed ‘cryptographic’ solutions regarding storing data in a secure and private manner. Various case studies in secure social apps are taken into account in the research paper.Alargecapacityandhighlydistributedarchitecture willberequired,exposedtoahostileenvironment.
The present state of the legal rules and regulations regarding the security and privacy of big data is proposed by Nils Gruschka et al. in their research paper[6] by analyzing various data conservation and privacy oriented mechanisms. In addition, for complying with the 'Data regulation laws', the author presented and analyzed two authentic research projects as case studies dealing with sensitive data and actions. The research paper proposed employed techniques under the legal requirements for protecting privacy, and the influence of thesetechniquesonthedataprocessingphase.Thispaper also explained how privacy preservation can be applied andinwhatmannerthedataprotectionlawsareimplied.
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
Nandhini. P, in her research paper[7], depicts the various security and privacy protection methodologies proposed by the various researchers and analyses the merits and demerits of those methodologies. The security and handling of big data are also considered with algorithms and techniques to do so. Challenges with the security and privacy of transaction data, stored data, and cloud computing are discussed with the help of surveys andotherresearchmaterial.Sheconcludedthatthereisa need to consider new technologies and modifications in the available technologies to make the data secure and to provideprivacy.
In paper [8], the author Venkata Narasimha Inukollu has discussed cloud computing, the Hadoop environment, and Big data. The author has conversed about security concerns about big data in cloud computing. The author broached the issues and provocations at various levels, namely: the network, validation, data, and generic level. The possible solutions for the issues and challenges allied with cloud computing security and Hadoop are also mentioned. The role played by cloud computing in sectors of data protection, its applications as well as the related infrastructure by assistance of policies, technologies, controls, and big data tools is also mooted. Measures and proposed approaches such as encryption of files and network, logging, software format and maintenance of node, authentication of node, honeypot nodes, acrid system testing of map reduce jobs, and framework for persuading cloud can be implemented toimprovisethesecurityissuesincloudcomputing.
Theauthor'KudakwasheZvarevashe'ofthepaper [9] has emphasized the subjects such as big data, MongoDB,Hadoop,Kerberos,NoSQL,andsocialnetworks. Thepaperpinpointsthelistofdirectionsofresearchfrom 2009 to 2014, which includes the topics such as security matters generated during the inventions of social networks, smart devices like smartphones, etc., and other technological advancements. The paper highlights the majorsecurityproblemslinkedwithBigData.Usingnodes like mapper nodes, reducer nodes. The use of encryption with Kerberos protocol makes the data more secure. However,securityandprivacyissuesarefacedindifferent forms such that Kerberos might not be enough to fully securethedata.
The paper written by Dongpo Zhang [10] tells us abouttheimpact,dependence,andimportanceofbigdata in the daily lives of human beings. It elaborates the need for strengthening the privacy and security of huge data transfers, to protect and secure the privacy. Big data is essential for ordinary people and very necessary in industrial, economical, and commercial sectors. This article states how to ensure the security of big data and the protection of privacy of lives. One of the most importantaspectmentioned inthis researchpaperisthat to ensure the authenticity and reliability of data.
2022, IRJET
ISSN:2395 0056
ISSN:2395 0072
According to author, the citizens of a country should also be made aware so that the privacy and security is protected.
Paper Id Related Work
Mechani sm/ Algorith m
Results Advanta ges Disadva ntages
Impact Factor value: 7.529
[1]
Cloud security alliance member ship and surveyed security practical oriented intervie wed by them to get a basic idea of high security issues
Autotie ring mechani sm propose d
Propose d more ways to secure data from hacking
Propose d new mechani sms and techniqu es
Autotie ring mechani smisnot explaine d in detail
[2]
Explaine d use of encrypti on and decrypti on to prevent security
SHA3 algorith m
Propose d encrypti on and decrypti on techniqu e
Data miningis explaine dinbrief
PPDM is not explaine dinbrief
[3]
Paper explains mainly on multime dia explosio n and difficulty in handling it
Cyber threat is consider ed a major issue faced by countrie s.
Explains well about cyber threat
Explanat ion is very basic
[4]
Explains how Hadoop techniqu e is big concern for research ers
Displays all possible problem s in Big data.
Explaine d well about threats and problem srelated to security issues related to Big data.
Doesnot provide solutions tothreat
[5]
The infrastru cture security in big
9001:2008
Case Study A high capacity and highly distribut
Cryptogr aphic solutions are propose
Impleme ntation of solutions is not
[6]
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p ISSN:2395 0072
data consideri ng the assured modeled processi ng of data.
ed architect ure will be necessar y when exposed to a hostile environ ment.
d. discusse d.
s, smart devices like smartph ones, and other technolo gical advance ments.
The present state of the legal regulatio ns regardin g big data security is propose d.
Data regulatio n
Data Regulati on Laws should be consider ed when dealing with security and privacy of big data.
Propose d employe d techniqu esunder the legal require ments for protectin g privacy.
Legal Actions on violation oflawsis not explaine d.
[10]
[7]
Study of various security and privacy methodo logies andtheir merits and demerits
Survey Study Modifica tions required in the available technolo gy
Challeng es with the security and privacy of transacti on data, stored data,and cloud computi ng are discusse d.
The holistic Framew ork is not explaine d in detail.
Theneed for strength eningthe privacy and security of huge data transfers , to protect and secure the privacy.
Awarene ss of common people
The citizens of a country should be made aware about data hacking along with other measure s.
Focus is on authenti city and reliabilit yofdata and common people.
Full supervisi on is propose d which may be violation of privacy itself.
[8]
Research about data storage on clouds, the Hadoop environ ment and the security issuesin cloud computi ng.
[9]
Security issues generate d during the inventio ns of social network
Cloud environ ments can be secured for complex business operatio ns by applicati ons of propose d approac hes.
Use of encrypti on with Kerberos protocol makes the data more secure.
Data Security and Privacy issuesat various levels are discusse d.
Third Party involvin g is not discusse d thorough ly.
3. CONCLUSION
Thisreviewpaperpresentedaviewaboutvarious paperswhichincludevarioussecurityandprivacyaspects. Not only big data in mobiles and multimedia but also in cloudstorageofdata.Also,thesecurityaspectsofmobiles andcloud baseddatatransfersaretakenintoaccount.Itis helpful in knowing about many open questions related to security.Thehugedatatransactionsandminingaswellas the significance of big data in the networks encourages researchers to look into various security and privacy problems that are essential to be resolved crucially by developing efficient and effective solutions. Massive work isessentialpriortothissolutiongettingquixoticallytaken on. We hope the papers dealt with in this review paper willbeagoodprovisiontothetrendsandissuescomingto the picture regarding the security and privacy of big data in transfers and computing. Modifications and research arestillrequiredtosetthesealonthesecurityandprivacy of big data. The current ways and mechanisms to protect data are insufficient to handle big data and will fail to protect it from misuse. Thus finding out the solutions to current problems and making big data transactions more secureandconfidentialisaneedoftechnology.
Concept of encrypti on is introduc ed to protect data hacking.
Kerberos may not be sufficient for fully securing thedata.
REFERENCES
[1] Mr. Yannam Apparao, Mrs. Kadiyala Laxminarayanamma. "Security Issue on “Secure DataStorageandTransactionLogs”InBigData".
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
Page 3200
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p ISSN:2395 0072
[2] SHASHANK PG Student II year MCA S.K.Saravanan, Assistant Professor (Sel.Gr) G.Rekha, Assistant Professor (Sen.Gr). "InformationSecurityinBigDatausingEncryption andDecryption".
[3] B. B. Gupta1 & Shingo Yamaguchi 2 & Dharma P. Agrawal 3."Advances in Security and Privacy of Multimedia Big Data in Mobile and Cloud Computing".
[4] Julio Moreno *, Manuel A. Serrano and Eduardo Fernández Medina. "Main Issues in Big Data Security".
[5] Jose Maura, Carlos Serrao. "Security and Privacy IssuesofBigData".
[6] Nils Gruschka† , Vasileios Mavroeidis† , Kamer Vishi† , Meiko Jensen∗ †Research Group of InformationandCyberSecurity,UniversityofOslo, Norway."PrivacyIssuesandDataProtectioninBig Data:ACaseStudyAnalysisunderGDPR".
[7] Nandhini. P. "A Research on Big Data Analytics Security and Privacy in Cloud, Data Mining, HadoopandMapReduce".
[8] Venkata Narasimha Inukollu1, Sailaja Arsi1, and Srinivasa Rao Ravuri3, "SECURITY ISSUES ASSOCIATED WITH BIG DATA IN CLOUD COMPUTING".
[9] Kudakwashe Zvarevashe1, Mainford Mutandavari2, Trust Gotora3, "A Survey of the Security Use Cases in Big Data" from International Journal of Innovative Research in Computer and Communication Engineering (An ISO 3297: 2007 CertifiedOrganization)Vol.2,Issue5,May2014.
[10] Dongpo Zhang, "Big Data Security and Privacy Protection" from Advances in Computer Science Research,volume77.
2022,
7.529
9001:2008
