OPTIMIZED ROUTING AND DENIAL OF SERVICE FOR ROBUST TRANSMISSION IN WIRELESS NETWORKS
Tamilnadu,
Abstract Projects based on the cloud domains are increased in the recent years even though there are some security threats on the networks and data. One of the cyber attacks is Distributed Denial of Service attack, it is considered as the second most predominant attack in the information theft. These attacks can exhaust the power, bandwidth and all cloud resources. It causes end to end delay and connectivity problem in the network and affects the Quality of Service (QoS). Prevention and detection ofDDoS attacks are vital roles in cloud domains. In this paper we are introducing a classifier system for detection of DDoS flood attacks which is named as CS_DDoS. It offers a solution to secure data by classifying packets as malicious packets and normal packets. It makes decisions based on the classification results. And the packets which are noted as an malicious will be blocked from the network and IP will be blacklisted. And to prevent a data and information we are performing efficient and quality routing technique with the use of Hybrid Optimization System (HOS). This will increase the lifetime of the network and leads the users to effective and energy efficient communication.
Key Words: DDoS, CS_DDoS, , Detection phase, Flood attacks, QoS, Genuine flow and Malicious flow.
1. INTRODUCTION
Backgroundoftheproject:Middle Boxdetectiontechnique: Middleboxisoneofthedetectiontechniqueswhichisused todetectDDoSattacksinconventionalsystembutitrequires customized hardware and software, So itfailstomaintain globalintelligenceinnetworks.
Differentiate between flow: Detecting the DDoS is hard withoutaffectingtheresources.Ithastheneedtofindout thatincomingflowismaliciousfloworgenuineflow.
Routing:Detectionoftheattackisthepartoftheprocess,we havetousetheroutingtechniquetotransferthedatafrom one node to another node. Basically data are transfer in staticpath,ItmakeseasyfortheattackerstomakeanDDoS attacksandtoaccesstheirsystems.Anditmakesthesystem slowwhentheattackisoccurredordetectedanditwilllead toinefficientcommunication.
1.1 STATEMENT OF PROBLEM:
InthetimeofstudyfortheprojectwenotedthattheDDoS attackdetectiontechniquehassomeofthedrawbackslike not identifying difference between genuine flow and malicious flow. Multiple ports connected on the single switch, which is also called as dump switch is one of the reasons. And also having the low ternary content addressable memory (TCAM) slow down the searching of contents. DDoS attack affects the performance of the integrated network’s throughput, delay and delivery ratio which is evaluated in terms of Data Packet Delivery Ratio (DPDR), Control Packet Overhead (CPO) which scales the total number of control packets from the total number of packetswithinthenetwork. InData PacketDeliveryRatio (DPDR), the ratio is calculated by the total number of effectively transmittedpacketstothetotalnumberofdata packets transferred from the source to the destination. It alsodecreasesthecapacityofloadbalancingofthesystem.It resultsinthepacketdrop,whichmeansthatistheratioof unsuccessfullytransmittedpacketssentfromthesources.
1.2 AIM AND OBJECTIVES OF THE PROJECT:
ThemainaimoftheprojectistodetecttheDDoSattackin theveryefficientmannerandalsopreventthedatabythe routing techniques, and it also important that the routing technique has to be efficient and it have to save our time thantheothertechniques,wehavetofindtheshortestpath tofindthenearbynodestotransferthedatabetweenthem. The process has to repeat when the attacker attacks the redirectednode.Sothatwearecreatingthemultiplepaths tomaketheprocessoffindingpathtougher.
Themainobjectivesoftheprojectare:
•TodesignaneffectiveDetectionandRoutingtechniquefor identifyingthefake flows(maliciousflow)andtotransfer thedatainotherpathwithoutaffectingtimeandcontent.
•TheobjectiveoftheRoutingandDetectiontechniqueisto removaloffaketrafficandthedelayinnetworksandtofind theduplicatedata.
• And to perform cost effective routing technique which takes less time to transfer the data from source to the destinationwithoutlosingdata.

2. RELATED WORK:
Thissectionpresentspreviousworkrelatedtoourproposed
Wehavehighlightedsomeofthemtoidentify thesignificantattributesofthesesystems.
TolgaNumanogluetal[1]alinthispaperhestudiesabout the coordinated and also non coordinated MAC protocols andtheperformancewithrespecttotheresultofchannel noise.DuetothecontroltrafficdependenceandBERlevel the performance loss and the vulnerability in the coordinatedMACprotocolishigherwhenit’scomparedto noncoordinatedMACprotocols.
BulentTavliandWendiB.Heinzelmanetal[2]Inthispaper hedescribesaboutthesuperframesandalsoneeproposed MH TRACE,superframeisaframewhichconsistofmultiple timeframes,totransmitthepacketsclusterhavetochoose theanyframe.Anywayallthenodesarereceivethetargeted packetsintherangeaccordingtotheformedclusters.This paperresultsintheeachnodescreateclusterstoreceivethe packetsitwantsandthenitdeclaredthatthethroughputof carriersenseMACprotocolsarelowerthentheMHTRACE protocol.
Mikkokohvakkaetal[3]Thispaperismorelybasedonthe peer to peer topology which focuses on the energy consumption in the network. There are several models describedinthisstudylikeMultipleaccesscontrolandthe CSMA CAmechanismandalsoZigBee.Theneedofthepaper is to analyze the power and throughput of the network which are checked by the WISENES. It results that the minimumpowerutilizedis73µWandthebeaconintervalis 3.93s.
Sung HwaHongetal[4]Heproposedthemechanismcalled as an duty cycling which is used to achieve the energy efficiencyinthewirelesssensornetworks,intheprevious projectstheexchangebetweenthelatencyandtheenergy efficiency is the only remained issue. So In this paper he proposedtheExpressMACwhichstronglyimposestheneed ofendtoendlatencywhensavingtheenergy.Itcanalsoable toaccesstheapplicationsin themultihopwiththeuseof cross layer application program interface. It is an proven methodthatEXMACisabletoEnsurelatencyandwakeup time.
JunGuoetal[5]HebrieflystudiedabouttheTDMAmodel's waiting time and the density distribution with the state dependent service. The solidity of the interval with the combination of beta allows efficient recursive scheme. Queuingmethodisusedtoexpressthewaitingtimeandhe also proposed the methodology which treats the special issuesinthepreviouspapers.
KazemSohrabyetal[6]Inthispaperwestudiedsomeofthe uniquefeaturesinthewirelesssensornetworks.Thispaper
briefly presents review about the transport protocols and someofthechallengesandbasicdesignsinit.Andalsothe writerdiscussedaboutsomeoftheopenresearchproblems.
JingZhuetal[7]Authoranticipatedthatwhataresomeof the specifications needed to modify the multi hop connectivity, so he provides the overview about the dedicated short range communication (DSRC) and their requirements. And also provides the variety of QoS and highlightssomeoftheissues.

Stavros Toumpis et al [8] This paper analysis about the CSMA that is carrier Sense multiple access and compares with the powercontrol MACandtheCA protocol.And it’s resultthattheroutingprotocolsareperformsbetterthenthe Carriersensemultipleaccessprotocolandthepowercontrol MAC.InthetermsofanenergyefficiencyPOBAisbetterthan theothertwoprotocols.
BoraKaraogluetal[9]Thispaperexplainsaboutthemobile ad hoc network and it success which fulfill the specific requirements of the networks and the better use of the channelresources.Thedimensionsofthistechniqueisthat when the space increases the power of processing also increases.Headdressedtherelationshipbetweentheoverall performanceandtheparametersoftheprotocols.Thispaper presents the model for the effective parameters by increasingthenumberofframesandalsowantstopredicts theconditions.
3. PROPOSED WORK:
Inourmodifiedproposedsystemwearefocusingonfactors mainly efficient reliability and the maximum time of the networkinthead hocnetwork(wireless).Weareproviding theenergyknowledgeroutingalgorithmcalledasconsistent orreliableminimumenergycostroutingthatisRMECRand it is used to find the consistent route which is energy efficientthatusedtomaximizethedurationandlifetimeof the network communication, we are using an deep and detailedanalyticalmodelfortheenergyexpenditureofthe nodes.Ithasthepropertyofhopbyhop(HBH)whichused in link layer consistency and the E2E retransmission reliability.ThehopbyhopisacceptablebytheMAClayerto increasereliabilityofthelinks.SomeoftheMACprotocols arenotacceptablebytheHBHretransmissioninthiskindof E2Eretransmissioncouldbeusedtoensurereliabilityofthe network. Load distribution (non uniform) and the spatial reuse which is very strongly linked to the bandwidth efficiency are the main obstacle when using the MAC protocol. When we use the Spatial reuse will drastically increasetheefficiencyofbandwidth,ontheothersidethe trafficloadismostlynonuniformwhichisthecriticalpart that the protocol be able to handle traffic efficiently, this happens due to the dynamic behavior in the mobile networks.TheseUnco operativeprotocolsareincorporated withthespatialreuseandtomakeitselfreadytohandlethe
International Research Journal of Engineering and Technology (IRJET)

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net
loaddistributionthroughthecarriermechanism.Thecareful designoftheMAClayerwillmakewaytothechangesinthe traffic distribution. As like the cellular system and the combinedmobilenetworkandtheMACprotocolneedssome ofthechannelmechanismthatisborrowingmechanismthat noticedthecharacteristicsofthemobilenetworktoprovide theadvantageslikeincreasingthebandwidthandtheirUn assembled counterparts. MANET are having some of the dynamic nature the network load is not uniformly distributed.Wehavetocopethenon uniformeddistribution thatisloaddistributioninthemobile networkssoweare proposingthealgorithmsnamelythelessweightdistribution allocation(Dynamicchannel)andbasedontheavailabilityof the resource nodes are need to select the channel access providers, so the alloy called coordinative load balancing algorithmareused.
Fig.1.Systemarchitecturediagramforproposedsystem
MH Traceframeworkmanagestheloaddistribution,butit don’t provide any of the support to change the conditions andtheformationsoftheload.Toughweusethisalgorithm for creating the new protocols with the CDCA and CMH trace.When the MH TRACE are enables the dynamic assignment and also the scalable assignment the CDMA TRACEareusedtomaintainthesameenergylevelandthe efficiency.Italsokeepsthetracksofthenearbyclustersto utilizethespectrumsensingfeaturemakessuresthecellular networksmaketheCDCAIsmoresuitablefortheMANET.
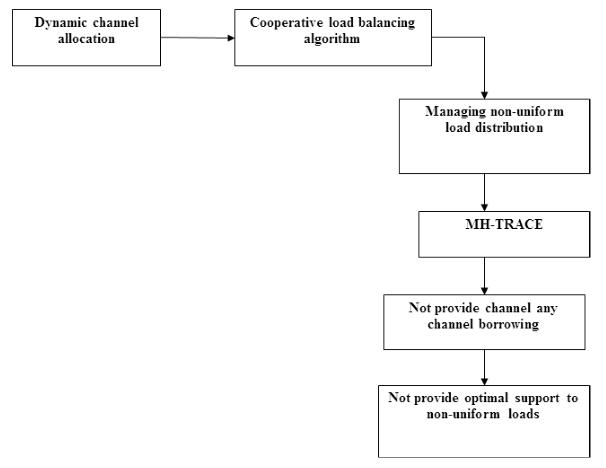
IntheMACprotocolsunderthenonuniformload,itismore critical to flexible enough to let the bandwidth which are unusedintothecontrollersofthehighlyloadedregions.The mechanismofthedynamicchannelallocationissimilarto thecellularsystemwhichisalreadyexistsandperformthe channelallocationbetweenthecelltowers.Byadoptingthis utilizesthespectrumsensingandthemessagearecosttoo muchforamobilenetwork.
The person who is controlling the channel has to monitor power and the availability asses in the channels by contrasting with the threshold levels. When the threshold level increases over capacity it motivates the coordinator.
ISSN: 2395 0056
ISSN: 2395 0072
Then he has to increase the power level of that channel whichsafeguardthemtoaccessthesamechannel.
In this algorithm maximizing the bandwidth seeks the attentionofthechannelcoordinators.Itiseffectiveinterms of providing the support and the response by the coordinatorwillincreaseentireinterference.
From the perspective of channel coordinators the DCA Algorithm approaches the problem of non uniform load distribution.Thesameproblemcanalsobeapproachedfrom the perspective of ordinary nodes. Without the need of coordinator side the cooperative behaviour clears non uniformitiesintheloaddistribution.Tomonitorthechannel usageandtheactivenodesloadbalancingalgorithmisused anditswitchtheheavyloadfromcoordinatoranddepleted theirchannelload.Thisincreasesthroughputandthetotal noofnodesthataccessthechannel
Mesh routers has the minimal number of mobility and no constrains, so the routing protocols in there are expected with some of the changes like change in size when it’s comparedtothead hocnetworks,routingfortheclientsare moreeasywiththeuseofinfrastructurebuildin.
Fig.2.DataFlowdiagramforproposedsystem
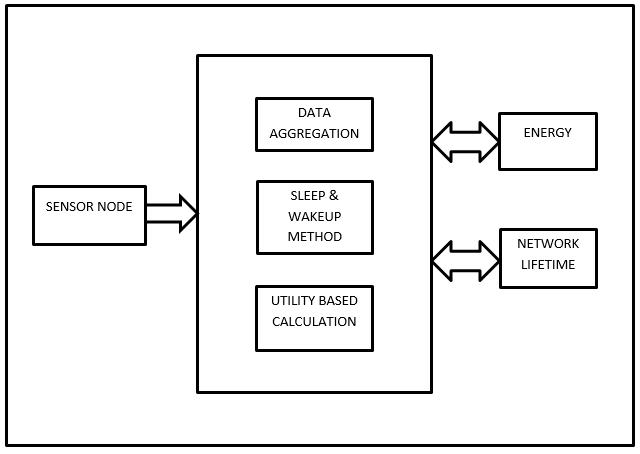
Theperformancelevelofprotocolhasthelegitimateimpact in the LQSR that is link quality source routing. There are some of the performance levels in the LQSR they are the expected transmission count, per hop packet pair and the per hot RTT. This performance will be calculated and comparedwiththeleastandtheminimumhopcountcodes toachievethebetterperformance.Thiswillberesultinthe linkqualitymetricsandit’snotenoughfortheWMNwhere themobilityisconsidered.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008
4. METHODOLOGY:
DDoS is an attack is process of creating the fake network trafficwiththeuseofmalicioussoftwarewhicharespreadin theclouddomainstoaffectthedata,allthebotnetsperform the same kind of malicious function. They are performing this attack by the fake IP address to make themselves untraceable.Therearesomeofthereasonstoperformthis attacklikecloudbasedcompetitionoranyrevengeandalso forfun.DDoSattack pointstheweaknessofthecloudand attack precisely. This attack in the cloud may be either internalorexternal
In this paper we are using the new scheme called as the Hybrid Optimization System for performing effective and efficientconnectionsthroughroutingtechniques.ThisHOS system consists of some of the advantages like dynamic routingandmultipathschedulingandstrongtransmission toovercometheattacksinthenetwork.Italsominimizethe faultsinthenodelevelstoincreaseendtoendconnectivity and to balance the load to maintain the stable and static transfer between source and destination. It also performs wellintermsofpacketdeliveryratio,averagedelaytimeand alsointhroughput.

4.1 DDoS Attack Detection
When we do the data transfer in the software defined networkthereisathreatinthreeplanesofthatnetwork.All the three planes of SDN architecture namely Controller plane, Application plane and Data plane has some of the threatsfortheattackslikespaceconstraintinthedataplane causesthebuffersaturation,thisisduetothepresenceof multiple ports interconnection. So in this work we are building the efficient and effective Intrusion Detection System(IDS)thisproposedworkleadstheuserforthehigh speedandthesecurecommunication.Inoursystemweare featuring the use of anomaly detection and the Network FunctionVirtualizationtechnique,thelightweightanomaly detectionbasedonthesinglefeatureisbestforthesoftware definednetworkswearealsousingtheopenvirtualswitches inthedetectionsystemtovirtualizethe path,moreover it helpstotracktheabnormaltraffic,whichcanbeappliedin manyareas.
Eachofthenodessendtheirrouterequesttotheneighbour nodestoknowifitisthedestinationifnotthatsecondnode sendstherequesttotheirneighbournode,thisprocesswill continueuntilthedestinationisidentified,afterfindingthe destination,itwillsendtherouteresponsetothesourceand the system will scan the path for if any of the malicious nodesare containing.Thesystemcalculatesthe threshold energy with the use of anomaly detection and TCAM memory,whenthresholdlevelincreasesabovethelimitit will report as an attack and our routing technique takes place.Ifnonodesaregivingtheresponseitwillbeaddressed asrouteerrororbrokenlinks.
4.2 Routing
This is the process after we detect the attack, we have to redirect the static path into the other if not it leads to the data loss so we have to perform routing. For that we are using routing algorithm for performing the routing in the efficientmanner.
Adhocondemanddistancevectorroutingtechniqueisused in this process it is mostly used in the mobile ad hoc networksandalsoitiscapabletoperformbothunicasting and also multicasting. This algorithm builds the routes betweenthesourceanddestinationnodes.Italsoformsthe treeswhicharecomposedofsomenumbersandtoensure thenodesdoesn'tgetaffected.Italsocapableforloopingand selfformationforthelargenumberofmobilenodes.Then OpenshortestPathAlgorithmisusedtofindthepathwhich has the minimum distance to reach the destination. The design is based on wireless sensor networks which can changedynamically,itlooksasdeployedininitialcondition but when the process finished it consist only of the disconnected parts
Fig.3.flowdiagramforroutingprocess
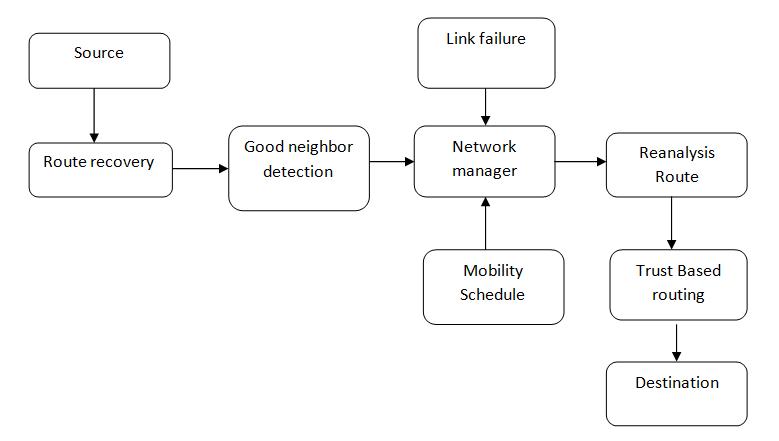
Hardware and software components
Thefollowingsectionisusedtodescribeaboutthe componentsusedinthissystem
5.
A. Hardware Requirements: We are using the intel processor Pentium IV series with 2.4 GHz and our systemhastheharddiskof40GbintheMonitorwhich has15VGAColour,MouseandRamof512Mb.
B. SoftwareRequirements:OperatingSystem:Thisproject canbedoneintheWindowsXP/7/10/LINUX,andthis is implemented in NS2 in the Version of 2.28. In the Front End we are using OTCL (Object Oriented Tool
International Research Journal of Engineering and Technology (IRJET)

2395
2395
Command Language), Tool: Cygwin (To Simulate in Windows
C. NS2: NS2 is an open source event driven simulator designed specifically for research in computer communicationnetworks.Sinceitsinceptionin1989, NS2hascontinuouslygainedtremendousinterestfrom industry, academia, and government. Having been under constant investigation and enhancement for years, NS2 now contains modules for numerous networkcomponentssuchasrouting,transportlayer protocol, application, etc. To investigate network performance, researchers can simply use an easy to use scripting language to configure a network, and observeresultsgeneratedbyNS2.
D. OperatingSystem:Ubuntu10.04(LINUX):Ubuntuisa Linux distribution based on Debian and composed mostly of free and open source software. Many additional software packages are accessible from Ubuntu software as well as any other APT based package management tools. Ubuntu is officially releasedinthreeeditions:Desktops,ServerandCore forIOTdevicesandrobots.Alltheeditionscanrunon thecomputeraloneorinavirtualmachine.
E. WorkStationTool:VMWareWorkstationPro12.1 VM Ware workstation supports bridging existing host networkadaptersandsharingphysicaldiskdrivesand USB devices with a virtual machine. VM ware WorkstationProcansavethestateofavirtualmachine (a“snapshot”)atanyinstant.Itcansimulatediskdrives an ISO image file can be mounted as a virtual optical disc drives and virtual hard disk drives are implemented as dot vmdk files. These snapshots can later be restored effectively returning the virtual machinetothesavedstateasitwasandfreefromany postdamagetotheVM.
F. DesigningLanguage:TCL(ToolCommandLanguage): TCL is a scripting language for controlling and extending software applications. You can run TCL consolewindowswiththeTCLScriptscommandonthe tool menu or tasks in the Task windows A .TCL file contains a TCL script which is composed of TCL functionandcanalsoincludeQuartusprimeapplication programming interface (API) functions used as commands.
G. ProtocolDesign:C++isaprogramminglanguagewhich allowstheprogrammertoinstructacomputertouse system resources and memory. C++ is adaptable to multipleplatforms.
6. EXPERIMENT AND RESULT:
In this experiment, results of our implemented system as wellastherelevantdetails.Thisoutputcanbedividedinto fiveconsecutivepartswhichworktogether:
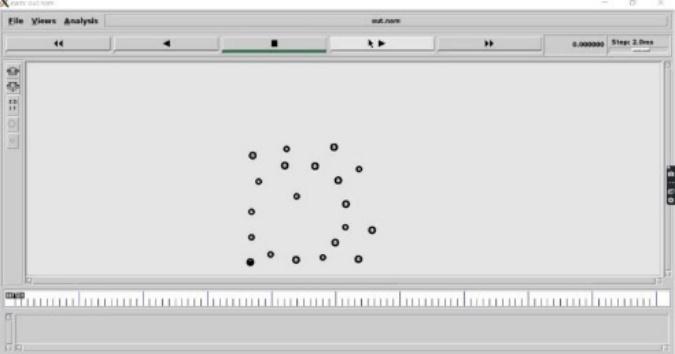
A)Creatingmultiplenodes
B)EAACKprocess
C)DataTransferfromsourcetodestination
D)EAACK Ackprocess
E)DynamicSourceRouting
A. Creatingmultiplenodes:
Betweenthesourceandthedestinationnodeswehaveto createintermediatenodesusingthenetworkvirtualization functionandtheopenswitch.Multipleintermediatenodes are created for the routing if the attack takes place the intermediate nodes. All the intermediate nodes are virtualizedwithinthestaticpath.Thedestinationalsonot initialized between the nodes, it will be identified by requestingneighbournodesuntilitfindsthedestination.
Fig.4Creatingmultiplenodes
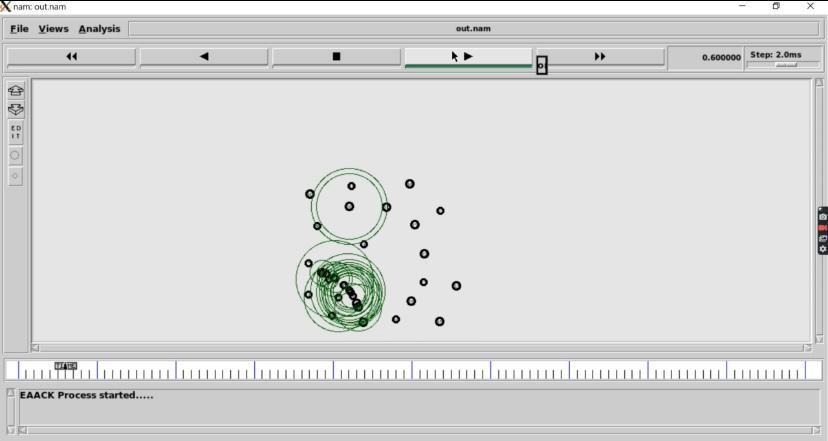
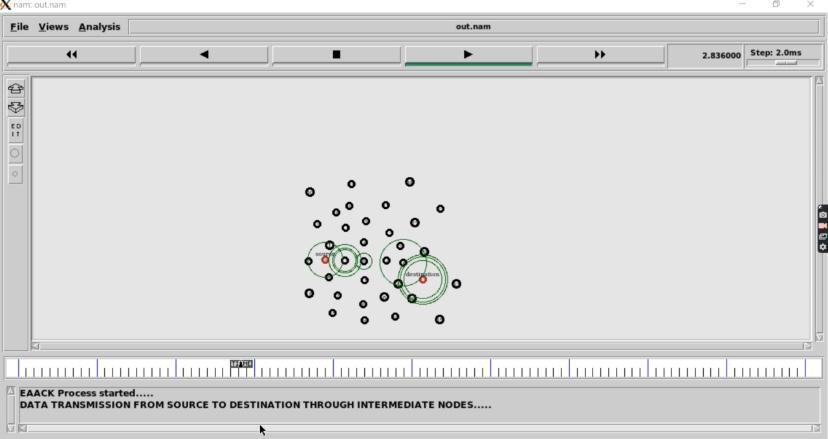
B. EAACKProcess:
Enhanced AdaptiveAcknowledgment (EAACK)it isusedto performthedefensemechanismforthepacketattack.Itisthe intrusiondetectionsystemdetectingtheneighbournodesto findthedestinationnodeandalsocheckingthenodesthatif containsanymaliciousnodesornot.
Fig.5.EAACKProcess
C. DataTransmissionfromsourcetoDestination
Previous process is used identify the
Inthisprocess
nodessearchesforthe
notit continuesthestatictransmission
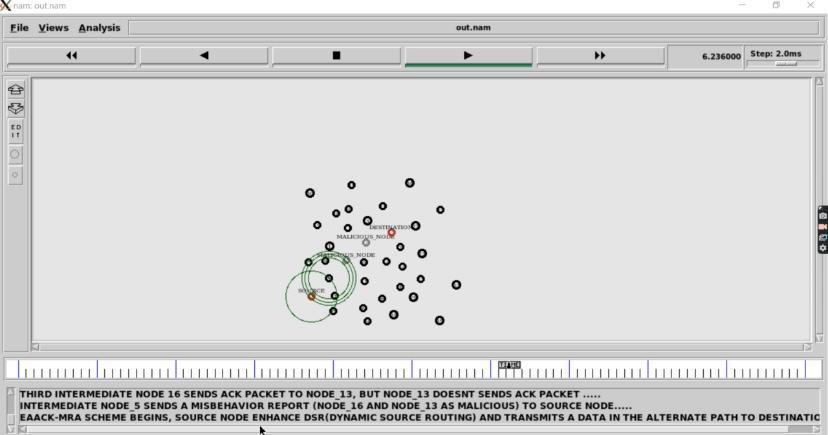
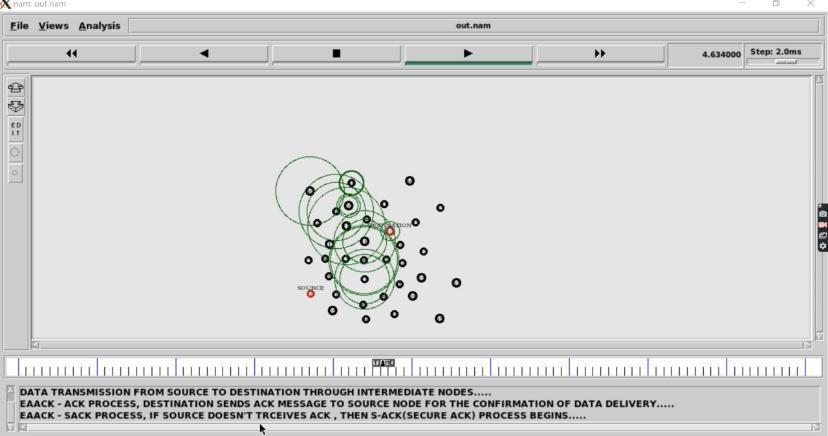
system.
nodesthatiftheycontain
notitacknowledges
Fig.
D. EAACK ACK
After analysing the neighbour nodes there is a need to acknowledgethesystemthatthereisnomaliciousnodeorif any malicious nodes are identified it also mandatory to acknowledgetoprocesstheroutingtechnique.Theintrusion detectionsystemhastheacknowledgmentpartwhichtakes placeafteranalysingthenodes.
E. Dynamic Source Routing
Whentheacknowledgementcamethatthepathcontainsthe maliciousnodesdynamicroutingwillbeprocessedwiththe mentioned algorithm of Ad hoc on demand Distance algorithm and with the use of the open shortest path algorithm.
This algorithm finds the shortest way to reach the destinationnodeandthenitanalyzethenewlyfoundedpath that to verify that there is no malicious nodes is the new path.
If any nodes are identified it will alternate the path till system finds the path without any malicious flow. After findingthesecurepathstaticdatatransmissionisused,each of the nodes only have the info about the previous and the next nodes so it makes tough for the attackers to find the path.
7. CONCLUSION:
Thisprojectresultsintheeffectontheroutinglayerweare notinvestigatedtheeffectsandwefocusedontheMAClayer about that capability and service like broadcasting in the local level. Packet has the significant impact based on the loaddistribution.
Networkfloodingisusingthelocallinkbroadcastingalong withthenetworkcoding.Asconclusionjointoptimizationof theMACandtheroutinglayerscanmakethebettersolution. Andtheeffectoftheroutingisleftasthefuturework.
8. REFERENCES:
Fig.7.EAACK ACK
If the malicious nodes are identified the nodes are highlighted and the next process of routing will be takes place.
[1] LifeiHuangandTen HwangLai.Onthescalabilityofad hocnetworks.InProceedingsofthe3rdACMinternational symposiumonMobileadhocnetworking&computing,
ISBN:1581135017
DOI:10.1145/513800

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p ISSN: 2395 0072
[2] Xin Ming Zhang, Yue Zhang, Fan Yan, and Athanasios V.Vasilakos. “Interference Based Topology Control AlgorithmforDelay ConstrainedMobileAdHocNetworks”, IEEETRANSACTIONSONMOBILECOMPUTING.
ISBN: 14965390
DOI: 10.1109/TMC.2014.2331966
[3] R. G. Li and A. Eryilmaz, “Scheduling for end to end deadlineconstrainedtrafficwithreliabilityrequirementsin multihopnetworks”.
ISBN: 13039045
DOI: 10.1109/TNET.2012.2186978
[4] M.F. Neuts, Jun Guo, M. Zukerman, and Hai Le Vu. The waiting time distribution for a TDMA model with a finite bufferandstate dependentservice.
ISBN :8584479
DOI: 10.1109/TCOMM.2005.855014
[5]MikkoKohvakka,MauriKuorilehto,MarkoH¨annik¨ainen, and Timo D. H¨am¨al¨ainen. Performance analysis of and zigbeeforlargescalewirelesssensornetworkapplications. InProceedingsofthe3rdACMinternational workshop on Performance evaluation of wireless ad hoc, sensor and ubiquitousnetworks.
ISBN:1595934871
DOI: 10.1145/1163610
[6] B. Tavli and W. B. Heinzelman. MH TRACE: Multi hop timereservationusingadaptivecontrolforenergyefficiency. IEEEJournalonSelectedAreasofCommunications
ISBN:8111623
DOI: 10.1109/JSAC.2004.826932
[7]P.Li,C.Zhang,andY.Fang,“Capacityanddelayofhybrid wirelessbroadbandaccessnetworks”
ISBN:10469657
DOI: 10.1109/JSAC.2009.090203
[8]ChonggangWang,K.Sohraby,BoLi,M.Daneshmand,and Yueming Hu. A survey of transport protocols for wireless sensornetworks
ISBN:8944364
DOI: 10.1109/MNET.2006.1637930
[9] Bianchi. Performance analysis of the distributed coordinationfunction.SelectedAreasinCommunications
ISBN:6584745
DOI: 10.1109/49.840210
© 2022, IRJET
[10]SangkyuBaekandBongDaeChoi.Performanceanalysis of power save mode infrastructure WLAN In Telecommunications
ISBN:10364438
DOI: 10.1109/ICTEL.2008.4652710
Impact Factor value: 7.529 | ISO 9001:2008
