International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
1,2,3,4 Department of B.Sc CS, Shivraj college of arts, commerce, and D. S. Kadam Science college Gadhinglaj. ***
Abstract - Every year newborn babies get abandoned by parents and to find those parents, a police investigation is also done but not 100 percent of all parents are found. Similarly, to find the criminals in rape cases and to identify the unknown dead bodies So with the help of bioinformatics and collecting Iris biometrics, footprints, fingerprint, and DNA sample we can find the culprit easily. Even when an accident occurs and if the patient goes under unconscious condition for that period due to this technology, we can find the medical history of that patient and we can proceed with his further treatment.
Key Words: Bioinformatics, Iris scanner, footprints, DNA sequencing, biological & genomic data.
Innovationintechnologyinthepastfewyearshasmadegreatadvancementsinprogressinheritablebasisof physicalcomposition.Bioinformaticshasbeenperceivedinbiologicalsciencewiththelatesttechnologyandadvancement, givingalargeamountofomicsinformation.Itisanintegrativefieldthatevolvesnewtechniquesandoperatingsystemtoolsto recognizethebiologicalinformationintheperiodwhenthedataarebigandcomposite.Itencompassesthebiologicalstudies thatusecomputerprogrammingforthe methodsandtechniques.Thefalcateandthis data which isavailableinthelocal databasemanagementareabigfacecomingchallengefortheexpertsfromthedifferentfields.Theuseofthistechnology coverstherecognitionofapplicantgenesandsinglenucleotidepolymorphism.TheuseofbioinformaticsTechnologyplaysan important role in forensic labs for the investigation of DNA samples and genomic data. Crime Investigation also helps to investigatethecriminalearlierandaccuratelywiththedatawhichisstoredinthedatabasesystem.Itsplaysandmainrolein theidentificationofthegenesandfibrinexpressionandregulation.Inbioinformatics,themaintaskistomakeuseofthe amountofdataandstructuralinformationandthechronologicaldatathathavebeenproducedatvariouslevelsofthebiotic system(Posner,2015).Inbioinformatics,theprogressofthetoolsisrequiredcomputerizedandstatisticalcapacityofassisting inknowingthemechanismwhichislyingunderthebioticqueriesintheresearch.Therefore,weconsiderthedifficultyof sciencethisisgreatlyreduced.Ittriestorecognizethebureaucraticprincipleswithinnucleicacidandproteinsuccession knownasproteomics.
Progressofcomprehensioninthefieldisessentialfortheinstinctivetechniqueforbioticresearcherstworapidlyand easilyrangeovertheexistinginformationtorecognizetheinformationsetandreporttherelevancetothefieldofattentiveness andtofindthemaindatawithinthosedatasets.Theadvantageandrequirementofrangeoverbasetechniquesworkedfora smallarrayofinformationonthemuchportablescaleoffewdatasets.Itcanberapidlycalculatedacrossthesequenceofmany datasetsthebioticprecisionisgreatlyreducedwhentakenoverdiversecircumstances.Thecongregateisbest-restricted beginning analytics of one data set. The most fundamental expression of assembling for the collection of any subset of conditions.SomeviewsobtainedquickrunningTimesbyrestrictingthetypesofbi-clustertheycanfindandtargetingspecific typesofinformationsuchastimecourses(Madeira&Oliveira,2005).Andanexpressionofassemblingfeatureselectionon technique approach may find a clamorous pattern among irrelevant states. It requires a lengthy computing period for a complete survey. To overcome all of these small problems we derived more ascendable circumstances of specific search methods.Toauthorizebiologyresearcherstorangeoververybigmicroarraycompilationinabiologicallymeaningfulmanner. Basedonthiscompendiumofdatawithdemonstratetheusefulnessofourthinkingforinformationexplorationandhypothesis formulation.
Assuming and signal processing let the removal of functional consequences from a big amount of Underdone information.Pasturegeneticshelpsinorderandglassgenomesandtheiridentifiedmutation.Bioinformaticsisderivedasthe useoftoolsofcomputationaldatatoviewthecaptureandinterpretationofbioticinformation.ItisafieldthattacklesPhysics Biologymathematicsandcomputerscience.Atamorecentralizationlevel,itassists,examines,andclassifiesthebiological trackwaysandnetworksthatarethemainpartofsystembiology,ithelpsincloningandmodelingRNA,DNAproteinacidsas wellasbiomolecularinterplay.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Figure:1

Previouslythemethodofbioinformaticsdoesn'tmeantoday'sTechnology.BenHesper&PaulienHogeweg derivedin1970tooveralllearntheprocessofthebiologysystemandtostudythedata.Thisdefinestheplacebioinformaticsas aparallelfieldtobiochemistry(Thestudyofchemicalprocessesinbiologicalsystems).InBioinformaticstheinformationis usedtocollectandorganizethedatachronologically.
Biometric technology is already changing the world in which we live. However, misconceptions and misinformationregardingprivacybreaches,accuracylevels,andsecurityrisksarehamperingthewidespreadadoptionof biometricsaroundtheworld.Inthisresearch,wearefocusingonthesecurestorageofbiometricdataandwearealsogoingto lookatsomeofthecommonmythsassociatedwiththesecurestorageofbiometricdata,theaccuracylevels,andthecostof adoptingbiometricauthenticationtechnology. InIndia,themostaccidentaldeathandcrimerateareincreasingdaybyday. Manyaccidentaldeathbodiesdeathcausesbynaturaldisastersrapecasesetc.Tofindthesuspectortoidentifytheparticular person’s medical history like allergies to the tablet allergies from the bond period or two identify the blood group. Bioinformaticsisusedtomatchthegenomicdataofthepersonforthemedicalrecordswhicharestoredinthedatabase.By testingandmatchingtheDNAofhairnailsoranyotherskinpartsitwillbeeasiertofindtheculpritrecordseasilybecausewe willStoreeachperson’suniqueidentificationdatainthedatabase.Thisdatabasewillbecreatedbyusingthegeneticcodeof theperson’sdata.Itwillbeeasiertomaintaintherecordsofthedata,thisdatacanbeaccessedthroughvariousgovernment hospitalsandarestoredincomputerizedonadigitalizedmannerthroughfingerprinteyescannerthumbprint,etc.itwillbe alsousedintheforensiclapseforthepost-mortemofthebody. InIndia,mostaccidentaldeathcasesareincreasingdaybyday. Accordingtothestatisticaldata,afederalstudyfoundthat22000babiesareleftinhospitalsbyparentsforcertainreasons,and everyday426dieinroadaccidents18perhour.RapeisthemostcommoncrimeinIndiaaccordingtothe2021annualreport ofNCRBinwhich31677rapecasestheregisterintheyear2019,2602deadbodieswerefoundamong278identified,25 murdercaseswerelaunchedandthecrimewasthesameinthenextyear.Toovercomethisproblemandtofindtheparticular person’shistoryandotherculpritidentificationthebioinformationwillhelptomatchthedataofthepersonwhichisstoredin thedatabase.Duetothis,wewillgettheaccuratedataofthepersonwhowillproceedwiththeworkmorepreciselyearly implementationofthisdatabasewillbedonethroughauniqueIDAadharcardtowhichthisdatabaseofDNAwillbeattached thiscanbedoneintwoways.
1)fornew-bornbabieswhichdaydonothavetheirAadharCarduniqueIDtheirdatawillbecollectedwhen they arebornin thehospitalsandwillbestoredintheparent’suniqueIDdatabasetilltheuniqueIDofnew-bornbabiesisnotcreated.
2)therestofthepopulationinIndiawillhavetoupdatetheAadharcardsforthisdatabaseattachment,incaseofacertaincase ofanaccidentarandomwillbehospitalizedinaprivatehospitalthentheyhavetotakethehealthofthegovernmenthospitals forthedatabase.
Thisideawillhelptomaintaintherecordsofthedataaccuratelyandweareresearchingimplementingthis datadigitallycomputerized.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072

IrisScanner: Itstudiestheirisandadmittancecardinonemachine.AnIrisscannerisatrustableidentityverification systemthatscanstheirisofanyperson’seyeitisthemostrapidandtrustablemodeofpersonverificationasitisthe requirementofrecollectingthepasswordsanduseridentificationname.irisscanandfingerprintdualisquiteabetter waytomakeconfirmthatnoonecancheatwiththesystem.Itisarapidwayofidentifyingsomeoneonthelocationif everneededanditisnoteasytofindanescapeclausetolikethiscastfingerprintsandusingbifocalsinceadaycanbe checkedsmoothlyandsometimesitisevencheckedbythesoftwarefullstopinIndiaAadharcardiscompulsoryto everycitizen.TheIrisscanner isonstandbyandI throughthe peoplelocation and irisitselfarefocusedon. The developmentisdigitallyclearedofvoiceandconvertedintoarectangularpatternaniriscode,containingdataabout theobject’suniquefeaturesandcharacteristicsinblackandwhite(likeaQRcode).Thenthiscodeiscomparedwith the database which is stored templates. At the same period, the expedite is very high, making it easy to use the databaseataverylargescale.Itisoneofthesafertechnologiesforpersonalidentificationwhichisindemandforthe capacity of the iris for use in contact lens scenario identification combined with a facial picture and a biometric identifier.SoifinfutureanycrimeoraccidentalcaseoccursandiftheeyesarefoundinCCTVthenwecanaccess Aadhardetailswhicharestoredinthedatabase.BydoingthiswecanmakeIndiaacrimelesscountry.
WorkingofIrisscanner:TheIrismethodmustbeverifiedtopasssuchabiometricscanning,allowingaverification responsetheIrisscanningisdoneintwostages.
Step1:Takingaclickshortofaneye.TheverificationsystemneedstorecognizeapersonwithaclickshortofhisIris.to proposethisscenarioeachindividualmustgothroughone-timeverificationoftheireyes.Inthisinstancethephotographing recognitionit'sdoneunderverystandardqualitylightninganddiscretecrimson.Thisinfraredlighthelpstoidentifytheunique methodofbrighteningeyesmorepreciselywhichismoredifficulttodoinnormallight.ThisIdidtocomputeranalysiswhich detachesinformationsuchaseyelashesandfocusesonabout240characteristicsintheIRISpattern.Afterthis,alldatawhichis found by the Iris scanner are converted into easy numeric data consisting of 512 digits (Iris code), which is stored in the computerwiththenameandotherinformationstoredinthedatabase.
Step2:verificationoftheauthenticityoftheeyeOncetheIrisimageisstoredinthedatabasetheverificationprocedurewillbe easytohandle.ThesystemrapidlyanalysestheresultingpicturematchingtheIriscodefromthedatabase.Thecomparing procedurewillstartfromhundreds,thousandsoflacks,ormillionsofIriscodesthatarepresentinthedatabasetheindividualis verifiedpositively.thisdataisstoredinthedatabasewheretheIrisscannercollectsapproximately240biometricfeatures,the combinationofwhichareuniquetoeveryIris.Thescannerwillcreateanautomatedrenditionofinformationfullstopthe numericradiationofdatatakenfromtheIrispicturewhichisstoredinthedatabase.
UIDAIrequiresonlytheverifieddevicesusedbyauthenticationecopartnerstofullystopthisdevicewiththe Aadharsystemforkeyencryptedmanagementwhichrectifiestheperson’sidentityandvalidatethisdevice.Everyphysical sensorhasuniqueverificationallowingdeviceverificationfromtraceability,fraud,etc.Eachrecordispassedwithinthesafe zoneeliminatingtransmissionofencryptedfingerprintsfromthesensortothehostdevice.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
In1900SirEdwardHenryofEnglandusefingerprintsforcriminalinvestigationwhichwascompared slowlybyhand.Thisprocessisunderdonefromthecrimescenarioandanotherbiometricfromthesuspectwhichiscompared underthemagnifyingscope.butbiometricfingerprintstakensometimeslookquitedifferentbecausesmudgingfingerprints fromthecrimescenetocompareandproofneedsmoreaccuracyandgreatskills.That'swhytheforensicresearcherproduced aneasysystemformatchingthebiometricswheretheylookbetween8and16distinctcharacteristics.

WorkingofaFingerprintscanner:
Therearethreemaintypesoffingerscanners,opticalscanners,capacitivescanners,andultrasonicScanner.
•Opticalscanner: Opticalfingerprintscannersareelderlywhocamebycapturingfingerprintsandcomparethem.Itis capturedinapictureandauniquealgorithmisusedtoverifypatternsonthefingerprintsurfacetomakeridgesandlines.These sensorsaredesignedforascannerthatapproximatelycapturesthedepthlessimage.Ithiresprogressopticalautomationto capturetheformatandridgesindriedandmoistfingersthroughSupremaRealscanG10portablescanner.
Step1:Whenthefingerprintsarecheckeddigitallytherewillbenopersonmatchingthefingerprintswithamagnifyingglass.It isdonepossiblybyregistrationandverificationofeachimageprintwhichisverifiedverypreciselycalledminutiae,wherethe linesinabiometricsplitin2.Thedistanceandanglesaremeasuredbythecomputerbetweencharacteristicslikedrawingaline andusinganalgorithm(mathematicalprocedure)toturnthedataintoanumericcode.Comparingbiometricsisasimplewayof comparingtheircodesiftheprincematchandthepersongainsaccess.
AlineofLEDscansdarklightontoaglassorplasticonwhichthefingerprintisplaten.theclassificationoftheimagewill changeaccordingtohowitisplatenhowcleanorGreasythefingersarefullstopreflectedlightcomesbackthroughtheplastic surfaceontoa CCDorCMOSpicturesensor.Thebrighterimageisvisibleinhowlongtheimageiscaptured.Iftheimageistoo brightthelinesofthefingerprintsincludingimportantinformationwillwashquicklyandifitistoothattheimagewilloccur blackandtheinformationwillnotbeabletoseefortheoppositecause.
Whethertheimageistoodarkorbrightitischeckedbythealgorithm,anaudiblebeeporindicationofLEDalertsthe user.Ifthepictureisroughlyvisibleoracceptablethenanothercheckthelevelofthedataalgorithmbycountingthenumberof elevationalternateoppositetoeachother.Byimagepassingthistosets,thescannerwillindicatethattheimageiscleartothe user(bybeeping).Itistoldinaflashmemorywhichisreadytotransfer(bywireless,Bluetooth,USB,oranyconnectivitywire)to hostadevicewhereitfurtherproceeds.Theimagesclickedbythewayare512*512pixelswithstandardimage2.5CM,500dots per inch, and 256 grey shades. The computer stores the image on a database or digitally match one or many fingerprint biometricstofindthematch.
•
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Thistechnologyassemblesmanysmallcapacitorcircuitswhicharemainlyfoundinthescannertocollect transforminginformationaboutfingerprints.capacitorreservethechargeandthey’reconductedtothemanagingplateonthe surfacetocrackthefingerprintinformation.ThechangesarelocatedusinganOP-ampnonsegregatedwhichislaterconverted usingananalogtodigitalconverter.Forhigher-qualityimages,morecapacitorsshouldbeconnected.Thisinformationcanbe savedforlatercomparisons.
This is the advanced technology that is used in fingerprint scanner full stop the hardware used in scannersconsistofanacceleratedcarrierandareceiver.Anultrasonicpulseistransmittedagainstthefingerplacedonthepanel scanner.Wheresomearesocupandrestreverberateback.Thisdependsontheridges,lines,pores,andothermarksfoundon thefinger.Thisisdifferentforeveryfinger. Theautomatedpressuremeasuredbyasensorisusedtocounttheintensityofthe reviewultrasonicpulse.Thishappensatdifferentlocationsonthescanner.Iftheperiodofexaminationislonger,thedepthof informationthatiscapturedismoreandauthorizeda3Drenderingofthesurface.
FootprintIdentificationTechnique(FIT)Withadvancedtechnology,fingerprintscannerhelpstoverify peopleontheiruniquefingerprints.Wherethefootprintscannerisveryusefulfortheidentificationofinfants.wecan'ttakea sampleofanewbornbaby’sfingerprintbecausetilltheageof12thefingerprintridgesvaryandthepalmhasalsoclosedthe baby,soitisnotpossibletotakeanaccuratepalmprintthroughthescanner.Sowearegoingtotakethefootprintstoidentify andverifytheabundantbabywiththeirparents.iftheyareleftorabandonedthenitisusefultomatchthisfootprintwhichis storedintheparent'sDatabasebecausethatbaby’sidisn'tavailable.Babies’footprintisuniqueandcomputerizedscanningof footprintscanbeusefultoverifythechildintheeventthereisanincident.Wearegoingtofootprintscannerassameas a fingerprintscanner.

ItistheadvancedtechnologyusedfortheDNAmatchoftheparent-child.Itistheprocessinwhichthe nucleicacidsequence(nucleotide)isinaDNAmolecule.ItisusedtostudythetypeofgeneticdatawhichiscarriedinDNA.In DNA sequence the four chemical basis always connect with the same pair of 'base pair'. Adenine (A) always pairs with Thymine(T);Guanine(G)alwayspairswithcytosine(C).TheDNAmoleculesarecopiedwhenthecellsgetseparatedinwhichthe humangenomeconsistsofthreebillionbasepairs.
ThisDNAsequenceisdonebyusingstarORF,first,theDNAsequenceistransferredintoRNAandthentranslatedintoall openingreadingframes(orf)encodedwithinevery6translationframes.Itincludestheorderof4bases;adenine,guanine, cytosine,andThymine.TheDNAsequencingdataisstoredinoldcomputingindualdigits(1s$0s).InDNAthedataiscollected andstoredinfournucleotidebaseswhichare(A,C,G,T)wheretheyarestoredandencodedthedata.Thegenomehastobe
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

sequencedsystematically,assembled,andannotated.Thedataisstoredin215petabytesinasinglegramofDNA,andthesystem storeseverybitofdatainthedatabase.
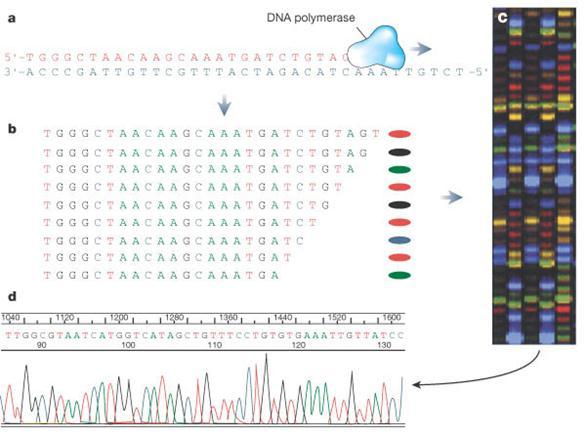
Figure5:DNASequencingsample
1. Itisusedingeneanalysis.
2. Itisusedinevolutionaryscrutinization.
3. Itisusedintheprophecyofproteinformation.
4. Itisusedfortherepository&reclamationofdata.
5. Tofindouttheperson’sevolutionaryhistory.
6. ItisusedfortheannotationofDNA&aminoacidsequences.
7. Itisusedfortheidentificationofcriminalsandforensics.
8. ItismakinguseofopenaccesstoForensicDNAdatabasessuchasthegenome/exomeAggregationDatabasesandExAC.
1. Itbringsanewchangeintheexistingprocess.
2. Ithashugedataprivacy.
3. Thedatacanbestoredandupdatedeasily.
4. ToreducethecrimerateinIndia.
5. Tomaintaintherecordsofbiologicaldataaccuratelyandtoimplementthisdatadigitallycomputerized.
1. Tofindthesuspectortoidentifytheparticularperson’smedicalhistory.
2. Tofindeasilytheparentsofabandonedbabies.
Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

3 Tofindthemedicalhistoryofaperson. 4. Toidentifybloodgroupseasily. 5. Toidentifyunknowndeadbodies. 6. Wecanaccessbiologicaldataandmedicalhistorythroughvariousgovernmenthospitals. 7. Toreducethelongprocessofthepoliceinvestigation. 8. Tofindcriminalsinrapecasesbyusingbioinformatics. 9. Tofindtheabandonedbaby’sparents’history. 10. Toidentifytheaccidentaldeadbodies.
8. Conclusion:
BioinformaticsisusefultoreducethecrimerateinIndia.Intoday'speriod,thepoliceinvestigationprocessrequiresa longtime,butwiththistechnology,wecaninvestigatethecasequickly.Also,theabandonedbabieswhoseparents’identification isdifficultbutduetobioinformatics,wecanfindtheirparents.Inforensiclabs,itisveryusefultostoreandmatchthedata.Ifany accidentcasehappensthenvarioustestshavetobedoneorifanydeadbodyisfoundthenidentifyingthatbodyisverydifficult butduetobioinformatics,allthemedicalhistoryoftheparticularpersonwillbestoredonly,soitwillbecomeeasytoidentify and to matchthedata.It isusedto matchthegenomic data of the person forthemedical recordswhicharestored in the database.Thisnewmethodologyislifelongandveryusefulinhospitals,policeinvestigations,forensiclabs,andvariousmedical fields.
Theauthorandco-authorswouldliketothanktheprofessor.PrasadTulsidasGoyalfortheadvice,guidance,mentalsupport andtechnicalsupportforthisresearch.(ComputerScienceDepartmentShivrajCollege,Gadhinglaj)

1.Marx,V.,(2013)Biology:thebigchallengesofbigdata.Nature,498,255-260.
2.InternationalHumanGenomeSequencingConsortium,(2001)Initialsequencingandanalysisofthehumangenome.Nature, 409,860-921.
3.Goodman,A.etal.,(2014)Tensimplerulesforthecareandfeedingofscientificdata.PLoSComp.Biol.,10(4):e1003542.
SourabhJTPatil
FounderofHelpingHandsYouth Circle(NGO).Maharashtra. MemberofAntiRagging CommitteeatDr.A.D.Shinde InstituteofTechnology.
MemberofPradnyaparisar prakalpforthefirsteverproject inIndiatoDevelopEmotional Friendlycampuses. Researchpaperpublished 1)3in1multi-utilityMaterial HandlingSystem.
2)PowderFertilizerDropper. 3)BlueEyeTechnology.
Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
YaminiUttamMore
Solardesigner. MemberofInternalComplaint CommitteeatDr.A.D.Shinde InstituteofTechnology Researchpaperpublished


1)BlueEyeTechnology
GiteshGirishKulkarni

CoordinatorofHelpingHands YouthCircle(NGO)Maharashta Researchpaperpublished
1)BlueEyeTechnology Researchpaperpublished
1)BlueEyeTechnology.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
