International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
 Ashish Dibouliya
Ashish Dibouliya
Principal Architect – Data, Connecticut, USA ***
Abstract - Attacks against Internet of Things (IoT) devices have increased dramatically in recent years. Attacks on vital internetinfrastructuresystemshavebeencarriedoutbycyber thieves using hacked IoT devices. Information security researchers are under increasing pressure to provide new tacticsandsolutionstoprotectsusceptibledevicesatalllevels following recent assaults. When it comes to home networks, malevolentactors don't care aboutthesmart devicesthat are part of them. National and global governments are placing a highvalue onsecuringcriticalIoTnetworksliketheelectrical grid and water distribution systems. Many different technologies are being applied to the problem of Internet of Things security. These include blockchain, AI, and edge/fog computing (IoT). Authentication and authorization are two legs of the CIA's crucial triad of components. However, due to the scaleofIoT networks and the limitedresources ofdevices, standard authentication and authorization mechanisms are unsuitable for handling security. We employ blockchain technology as a lightweight and straightforward authentication solution for IoT devices. The use of artificial intelligence (AI) to aid in decision-making and carry out predictive analytics in a wide variety of contexts is gaining popularity. In recent years, blockchain (a peer-to-peer distributed system) has also been used to enable AI applications,suchassecuredatasharing(formodeltraining), data privacy, trustworthy AI decision making, and decentralized AI. The purpose of this effort is to create a hybrid authentication technique based on Blockchain authentication and AI for user and device authentication in a fully interconnected IOT setting.
Keywords: IOT (Internet of Things), WSN (Wireless Sensor Networks), Blockchain Authentication, Artificial Intelligence, Hybrid Authentication
TheconceptoftheInternetofThings(IoT)israpidly growingandgainingpopularity.Manyofourregulartasks and routines would be impossible without the Internet of Things. New IoT applications in areas including smart homes,smarthealthcare,smartcities,industry4.0,wireless sensor networks (WSN), and smart farming have the potentialtointroduceandadvancetheconceptofasmart world. Security measuresat several layers,along withthe capacitytoanalyzeandregulatealldataandinformation,are
essential for the platforms, networks, devices1, and applications that make up the Internet of Things (IoT) ecosystem.Thedevicescanbeeasilycompromised,leaving usersopentoidentitytheftandmeddlingwiththeirdata.
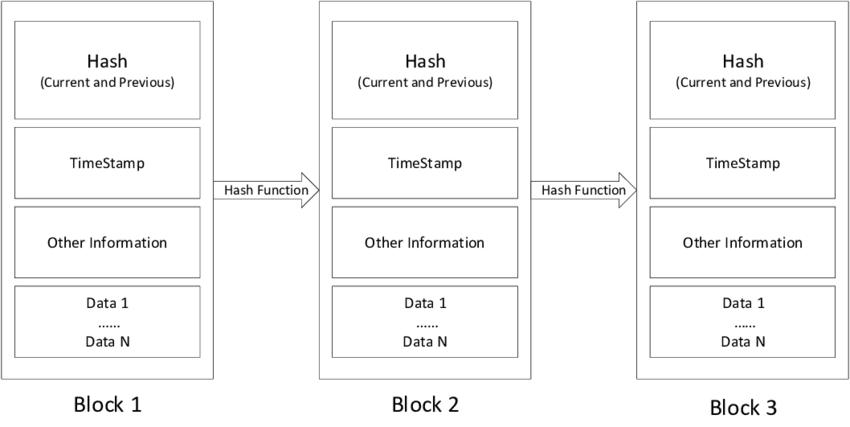
Theledgermustbegeneratedandmaintainedbyeachnode in the blockchain ecosystem. To participate, a participant mustbeabletoreadandwritetransactions.Therearetwo categoriesofparticipants:read-onlyandread-write.Toput itanotherway,minerscanaddtransactionstothechainas uniquenodes.Anestablishedtechnology,blockchainholdsa lotofpromise.Itisregardedasafundamentalapproachina decentralizednetworkenvironmentsinceitisdistributed, decentralized,andunchanging.Fortheblockchainnetwork's peerstoacceptablock,minersmustcompleteproofofwork (PoW).Figure1depictstheblockchain'sbasicstructure.For securingtheInternetofThings(IoT),Blockchainhasbeen hailed as an ideal option. To ensure the safety of the IoT ecosystem,wehavealsobenefitedfromthistechnology.Itis ourprimarypurposeinthisresearchprojecttoprovidean authenticationsystembasedontheEthereumBlockchain, whichisa publicblockchainandprovidesdistributedand decentralized security for IoT devices. Using this method, users and their gadgets may communicate in a secure environment. There are three sections in which the documentisbrokendown:1stsectionincludesintroduction partofthepaper.Second,thereisasectioncalledRelated Work that provides an overview of the blockchain and includes work done by other authors to secure IoT with blockchain.ThirdistheProposedTechnique,whichincludes the results and discussion of the proposed method, and finallySectionVistheConclusion.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
IoTisnowarealitythatpervadesmanyaspectsof ourlife,anditisonlygoingtobecomingmoreprevalentin the future.Although IoTwas formerlyviewedas a science fiction concept, it has now become a reality thanks to the work of several researchers who see it as one of the most significanttechnicalshiftsofthetwenty-firstcentury.Asingle linkedthingperpersonwasachievedin2008,andcurrent estimatesplacethenumberatroughly26smartobjectsper personby2020.Therearestillmanychallengesthatneedto beovercomebeforetheInternetofThingscanbeusedtoits fullpotential.Thesechallengesincludebutarenotlimitedto computingconstraintsimposedbyInternetofThings(IoT) devices; heterogeneity; identification; power supply; data storage/processing;amongotherthings.Securityandprivacy are two of the most pressing issues, considering the widespreaduseofsmartdevicesineverydaylife.IoTsecurity solutions aren't applicable in general because of the restrictions of IoT components, which have minimal capabilitiesinbothenergyandprocessingresources.
As a result, they cannot implement elaborate schemes supporting security. Unfortunately, this makes thingsevenmoredifficult.MostprevalentIoTexploits,and vulnerabilities have been documented by the OWASP InternetofThingsProject.
Most devices that participate on the internet of things are autonomous and have modest power requirements.Thesenodescancollectdata,actbasedonthat data, and communicate with one another and with other entitiesthankstotheuseofsensors,actuators,andeventhe Cloud.Whenthecomplexity ofthealgorithmsbecametoo difficult to manage, attention turned from artificial intelligence(AI)tomachinelearning(ML).Machinelearning methods are used in numerous modern contexts, from statistical analysis and prediction to practical tasks like speech recognition and fraud detection. Algorithms and methodsusedinmachinelearninghavebeenimpactedby many disciplines, including mathematics, neuroscience, statistics, and computer science. To test an algorithm's ability to learn from data, it is common to split the developmentofthealgorithmintotwodistinctphases:the training phase and the verification phase. Most today's machine learning algorithms fall under the categories of unsupervised,supervised,andreinforcementlearning.For thefirst-classtrainingphasetobesuccessful,alabelleddata set is required so that the studied relationships can be represented.Incontrasttothefirsttype,theinput/output pairings for the unsupervised learning techniques are not provided.Theprimaryfocusofthisactivityisonlocatingthe linksbetweenthevariousdatapoints.Thethirdtype,online learning, describes situations in which an agent acquires
knowledge about how to behave by engaging in trial-anderrorinteractionswithaninteractiveenvironment.
Design and development of an authentication techniquewhichemployeeshybridalgorithms/techniques suchasBlockchainAuthenticationandArtificialIntelligence, forseamlessuseraswellasdeviceauthenticationinanIOT network.
Achraf Fayad et. All (2019) Numerousstudieshavebeen donetoproposenovelmethodsandsystemsforensuringthe authenticationofIoTdevices.Manyexistingeffortsdonot meet all of the IoT's objectives, such as permitting the mobility of nodes or guaranteeing scalability through decentralisedtechniquesormakingiteasytointegratenew devices and services. The authors of this paper put up a simple way of authentication in this situation. Using a blockchain,whichisentirelydecentralised,isattheheartof our answer to this problem. As a result, it fulfils all of the previously described conditions. Real-world implementations of our method were used to test the validityofourfindings.Itwasevidentfromtheresultsthatit waslowinweight.[1]
Aissam Outchkoucht et. All (2017) Even as the mechanisms for actuation, communication, and control improveandbecomemorewidespread,theriskstheypose tousertrustandtheInternetofThingsasawhole,whennot adequatelyaddressed,arealsoincreasinginsophistication and pervasiveness. This investigation has centered on the IoT(InternetofThings).Itproposedaframeworkwiththe intentionoffixingtwoissues:Ithosethatarisefromusinga centralized design, and (ii) the need to transmit the administrationofaccesscontrolfromacentralbodytothe nodes of the network. Indeed, the limited devices of the InternetofThingsdonothavethecomputationalresources or data storage space required to support a decentralized accesscontrolsystem.Thesheernumberofconnectedsmart devices can be overwhelming in an IoT setting, posing a number of regulatory issues related to regulating user access. As a result, security officers and managers often resorttoenforcing"staticpolicies,"inwhichallsecurityand accesscontrolrulesarewrittenbyasingleperson.[2]
Soumyashree S. Panda et. All (2019) The Internet of Things(IoT)anditsmanyuseshavebecomeanintegralpart of our everyday lives. Without the need for human intervention, a number of smart devices can interact with one other. To participate in an autonomous system, only genuine entities should be able to participate. As a result, thisstudyproposesanIoTsystemauthenticationscheme. Blockchainisthedecentralisedledgertechnologythatwould beusedintheproposedsystem,notacentralauthority.[3]
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Khadija Fazal et. All (2020) Authenticatedusersmustbe abletoaccessandretrievedatafromeachdevice.Accessto thesegadgetsandthecommunicationstheyprovideshould besafeinmostinstances.IoTsecurityisakeyroadblockto widespreadadoptionandimplementationofthetechnology, foravarietyofreasons,includingthefactthatitisextremely vulnerable to cyberattacks. Authors present a blockchainbasedEthereumauthenticationsystemforconstructingsafe zonesintheinternetofthings.VariousIoTsettings,services, and situations can benefit from the authors' proposed strategy.Wecanbeconfidentinthesecurityofoursystem becauseweareusingapublicformofBlockchain.Totestthe suggestedapproach, wewantto writea smartcontract in solidityusingtheRemixIDEandanalyseitsperformancein termsofcostandtime.[4]
Dr. Sakthi Kumaresh et. All (2021) In this article, a Decentralized Artificial Intelligence-enabled Blockchain network is implemented using the confluence of AI and Blockchain technology (DAIBCN). The proposed DAIBC methodusesadecisiontreemodeltoautomaticallyidentify minernodes.Thereislessrequirementforminernodesto performcomplexhashfunctionsinordertobeeligiblefor reward. The testing findings reveal that the suggested AIenabledapproachsavesasignificantamountofenergyand also reduces the time it takes to complete a transaction becausethenodeselectionisdoneautomatically.[5]
Praveen Kumar Kollu et. All (2021) Blockhain development has spurred continuing study in a variety of theoreticalandfunctionalareas.Decentralization,identity, and trust are three of today's most pressing technological issues, and the blockchain is widely seen as a promising answer even as it is still in its infancy. When it comes to finding the best way to store and access cloud data, the groundbreakingblockchainisaninvaluableresource.This article examines the potential ofblockchaintechnology to defend cloud computing. A cloud computing data security mechanismisalsopresentedinthispaper.Thisapplication uses smart contracts and permission lists to secure data security.[6]
Shanshan Zhao et. All (2019) Dataisgenerated,collected, processed,sent,andstored byseveral organisations in an IIoT ecosystem. Blockchaining both IIoT entities and businessprocessesishighlysoughtafterbythesectors.The Internet of Things (IIoT) is predicted to be widely implemented in sectors as a result of fast technological advancements and new business models. In this article, we've looked at blockchain and IIoT integration from an industrial standpoint. Introduced is a blockchain-enabled architecture for the Internet of Things (IoT). The most importantapplicationsandissuesarecovered.BlockchainenabledIIoTresearchissuesandpotentialtrendswerealso examinedbytheauthors.[7]
Muhammad Tahir et. All (2020) Authentication,privacy, chaos,mining,andadministrationarejustafewoftheissues thatthegrowingIoTmarketandtheBlockchainecosystem are creating. In IoT applications, mutual authentication is essentialbecauseitgivessecuritytousersandassuresthe validity of data and protects their privacy. The mutual authentication of IoT devices has been separated into distinctclassesbasedontheauthenticationandassessment methodologies. A innovative approach for mutual authenticationandauthorisationispresentedinthiswork bytheauthors.Distributedjointconditionalprobabilityand the selection of random numbers are used to establish robustness in the proposed framework. The performance assessment and results analysis reveal that the suggested framework achieves better security strength, fewer communicationoverheadcosts,andconsumeslesstimein processingdatatogetherwithincreasedsecurity.[8]
Dr Mohd Javaid et. All (2021) Inadditiontoensuringthe safety of all communications between the many interconnectedsmartdevices,the blockchainalsokeepsa permanent record of every single message ever sent. Individuals'identitiescouldalsobeprotectedviablockchain technology. Due to its deceptive nature, this technology enablesitsuserstoestablishasafeanddependableonline persona.ABlockchainidentitymightbeusedforanything fromasingleclicktoaccessingawholesuiteofapplications andservicesorevenforgingdigitalsignatures.Blockchain couldbeusefulforSMEsandsuppliersasitoffersasecure, high-qualitytransactionaldatasource.Furthermore,ashop mustguaranteethatallofitsproductsareofuniformquality. [9]
Bhabendu K. Mohanta et. All (2019) The Internet of Things (or IoT) is a relatively new concept. Smart homes, smart cities, smart transportation, and smart healthcare systems are just a few examples of how IoT is enhancing human well-being in a variety of contexts. Real-time monitoringandcontrolareavailableinallcircumstances.To test the efficacy of the DecAuth (Decentralized Authentication)system,thispaperproposesaBlockchainbased ethereum platform implementation. An IoT device maybeauthenticatedinadecentralisedmanner,according totheexperimentalresults.Also,accordingtothestudy,the suggestedsystemisimpenetrable bythecurrentlyknown assaults.[10]
Jesse Yli-Huumo et. All (2016) TheBitcoincryptocurrency ispoweredbyblockchaintechnology.Anopenledgerofall transactionsismaintainedinadecentralizedsettingthatis accessibletoeveryone.Blockchainaimstogiveitsuserswith complete anonymity, safety, privacy, and transparency. However, these characteristics pose several technological issuesandconstraintsthatmustbeaddressed.Authorsused thesystematicmappingstudyapproachtomapallrelevant studiesonBlockchaintechnologytobettergraspthepresent stateofthefield.Thestudy'smainobjectivewastomapout
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
the existing state and future directions of blockchain technology.Asidefromthetechnical viewpoint,writers in this study did not offer viewpoints on economics, law, business, or regulation. From scientific databases, 41 primary publicationswereretrievedand examinedbythe authors.[11]
The proposed system is aimed for seamless authenticationofUser(s)&Device(s)inIOT-WSNNetwork’s, the system employs a block – chain of user/device authentication entries, which is used to train a Function Fitting Neural Network, which is used to ascertain the authenticity of new block - chain entry for user/device authentication,informofatransactionauthenticityscore.
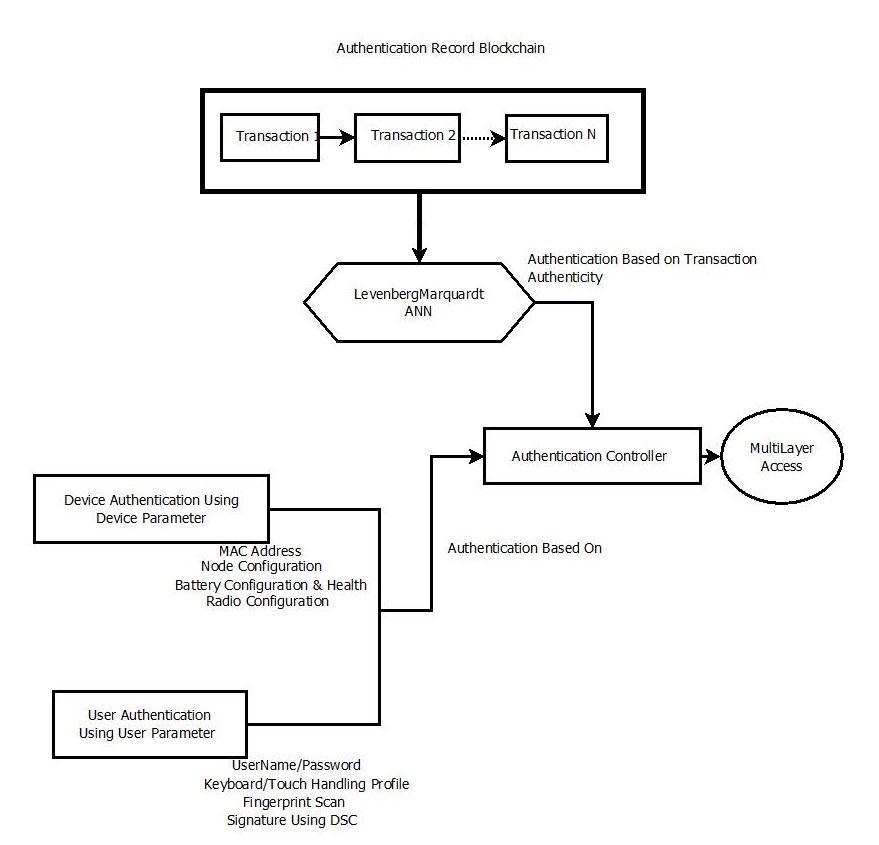
Apart from block - chain based login access; secondaryauthenticationisprovidedbasedUserandDevice parameters listed below. The user/device parameters are used to train another pattern matching neural network, whichisusedtoprovideUser/DeviceAuthenticationScore.
Block-Chain based authentication score is combined with User/Device authentication score using custom machine intelligencetogeneratefinalauthenticationscore,whichis usedtoprovidemulti-layeraccesstovariousservicesand resourceshostedbytheIOT–WSNNetwork.
Tocalculatethe minimum ofa function (linearor nonlinear) over a space of parameters, the well-known Levenberg-Marquardtalgorithm(LMA)isoftenemployed.A function,suchasaquadratic,isusedinternallytomimica reliableportionofthegoalfunction.Onceagoodmatchis established, the trusted area grows to include the new addition. The Levenberg-Marquardt methodology is sensitivetotheinitialbeginningparameters,asisthecase withmanynumericalalgorithms.Thisarticledescribesthe training and testing phases of the Levenberg-Marquardt algorithmforlearningartificialneuralnetworks.
The created LM-ANN model is more sensitive for predictionoftheinflowswhenthestatisticsofthelong-term andseasonal-termoutputsarecompared.Further,thespeed andreliabilityoftheLM-ANNtechniquemakeitapplicableto themodellingofawiderangeofhydrologicalfactors.Fora givencollectionoftrainingdata,theLevenbergMarquardt (LM)trainingfunctionachievedthebestperformance(the smallestMSE).LevenbergMarquardtisfoundtobethemost effectivepredictivealgorithmthroughextensivetesting.
1. TheLMalgorithmismorerobustandhasmorestable convergencethantheeGNalgorithm
2. This algorithm is mostly used for training small and mediumsizedproblemsinANN.
3. Theadvantageoftheapproachisthat,oncethenetwork is trained, it allows instantaneous evaluation of solutions at any desired number of points; thus, spendinglittlecomputingtime.
4. Levenberg-Marquardtalgorithmgivesthebestresults withhighperformance.
5. The Levenberg-Marquardt (LM) gradient descent algorithmisusedextensivelyforthetrainingofArtificial NeuralNetworks(ANN).
6. The Levenberg–Marquardt algorithm provides a numerical solution to the problem of minimizing a (generallynonlinear)function.
7. TheLEVENBERG-MARQUARDTmethodisasingle-shot method which attempts to find the local fit-statistic minimumnearesttothestartingpoint.
In the proposed work Levenberg–Marquardt algorithm Used for train artificial neural network and processsomefunctionsthansomemathematicalcalculation
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
will be perform then train function, then plot error and performance plot and calculated estimated distance with respect or transmit power. if any node tries to establish connectioninournetwork,ifthisisinourrangethenour accesscontrollerprovidedtruekeyforestablishconnection withsomeleniencyotherwiseifthisisinoutsidetherange thenaccesscontrollerprovidedfakerandomkeyforprivacy.
S.No Parameter Name Narration
1. User Name/Password PrimaryAccessControl&User Identification
2. Keyboard/Touch HandlingProfile 2nd FactorAuthenticatorUsing ComparisonofKeyboard/Touch HandlingWithPreviously KnownHistory
3. FingerprintScan 2nd FactorAuthenticatorUsing Biometric–FingerprintScan UsingMinutiaeExtraction &EuclidianDistance Computation
4. Signature Using DSC 2nd FactorAuthenticationUsing DigitalSignatureCertificate ProvidedByTrustedAuthority SuchAsCCAInIndia
Table: 3.1 UserParameters
S.No Parameter Name Narration
1. MACAddress PrimaryDeviceIdentifier,Using UniqueMachineAddressUsed ForDirectNodeAddressUsage orReferencedUsageSuchAsIP AddressBasedRedirection
2. Node Configuration 2ndFactorAuthenticatorUsing ComputingConfigurationofThe DeviceSuchAsProcessorSpeed, NumberofCores,RAM,Flash ROM,ArchitectureEtc
3. Battery Configuration& Health
4. Radio Configuration
2ndFactorAuthenticatorUsing BatteryConfiguration,Voltage, mAh,Technology,No.ofBanks EtcAlongWithBatteryHealth Monitoring
2ndFactorAuthenticatorUsing Wireless/RadioConfigurationof TheNode/DeviceSuchAs Transmitpower,Receive Sensitivity,NoiseFloorEtc
Table: 3.2 DeviceParameters
Factor value:
Figure: 3.2 TrustedNodeRFRangingBased Location/Distance
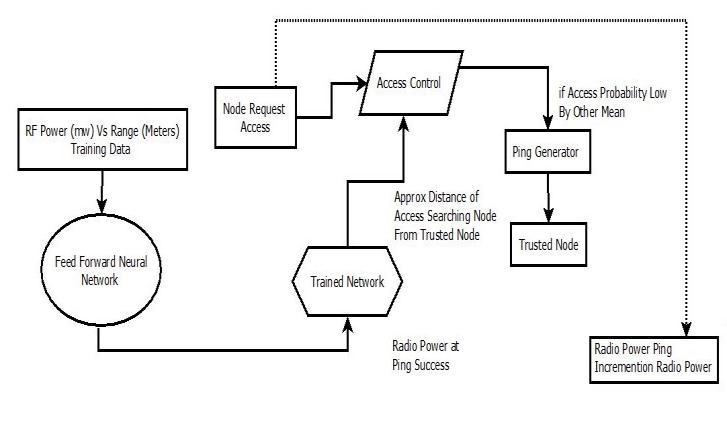
Apartfromtheauthenticationpathdescribedabove, another method of improving authentication score is provided, for User/Device denied access by marginal difference in authentication score, by verification of their physical/geographicproximitytothetrusted/centralnode using a novel technique developed using Artificial Intelligence & slowly increasing Transmit Distance by varying theRadioPowerusingTransmitPowerEstimation ANN, until ping is replied by the User/Device requesting access. After each ping, the pin generator increases the power by a certain amount until a node connects. Once a node does connect, the trained network calculates its distancefromanaccesscontrollerandprovidesakeyand someleniencyinaccess.Theaccesscontrollerwillprovidea false (fake) key if the neural networks calculated range is greaterthanthecoveragerange.Thisishowwe'llverifythe authenticity.
International Research Journal of Engineering
Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
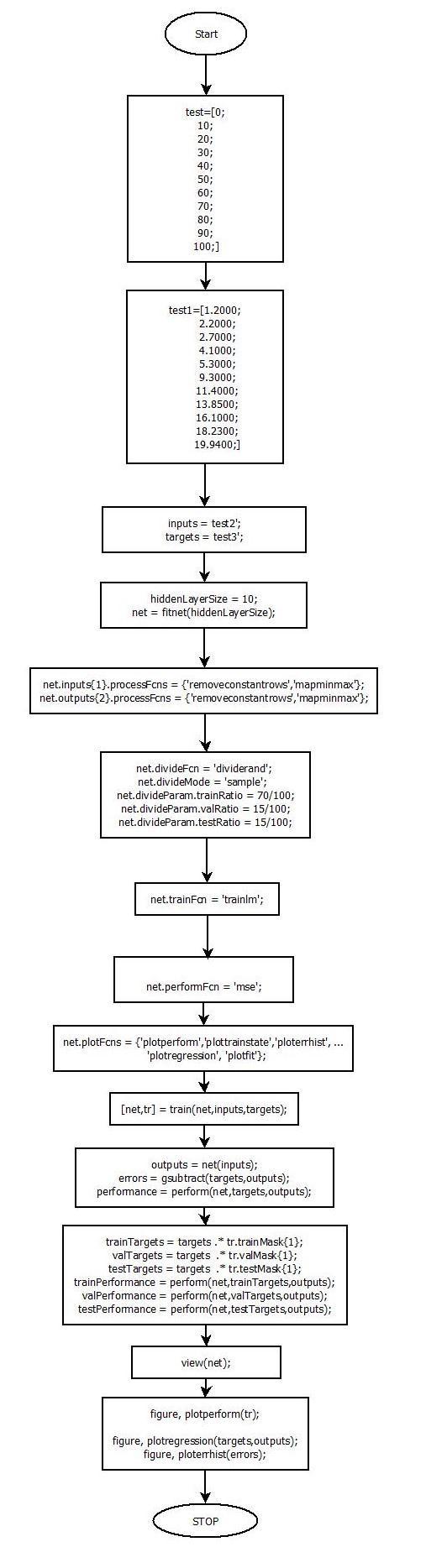
Neuralnetworksareself-learningadaptivesystems thatuseinterconnectednodes(sometimescalledneurons)in amulti-tieredarchitecturelikethehumanbrain(alsoknown as artificial neural networks). By being fed enough information,aneuralnetworkcanlearntoidentifypatterns, organizeinformationintocategories,andmakepredictions about the future. The input is broken down into levels of abstractionbyaneuralnetwork.Itmaybetaughttodetect patterns in speech or images, for example, using many samples, just like a human brain. A system's behavior is determinedbythewayitscomponentsarelinkedtogether and the weights attached to those links. To achieve the required job, these weights are automatically modified duringtrainingbasedonapredeterminedlearningrule.In thisflowchartwecansee1stourANNcodeisstartthancall totestvaluestheninputandtargetstestvaluesthenhidden layeroperationperformthenprocesssomefunctionsthan some mathematical calculation will be perform then train function, then plot error and performance plot after that codewillbestop.
Figure: 3.3 ArtificialNeuralNetworkFlowChart
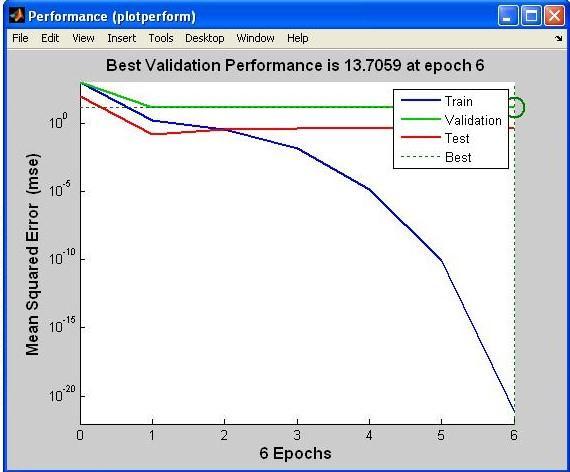
The accompanying diagram depicts the Artificial NeuralNetwork'sbestvalidationperformanceplot.Thebest, validation, test, and railway lines are all displayed here. Errortypicallyreduceswithadditionaltrainingepochsbut mayincreaseonthevalidationdatasetifthenetworkbegins to overfit the training data. Epochs with low validation errorsgetthegreatestresultswiththedefaultconfiguration afteraseriesofsixconsecutiveincreasesinvalidationerror.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
power estimated is 3 mw and ping is success after 100 seconds.Atthedistanceof101meterandpowerestimated on this distance is 20 mw ping is success. This distance is outsidetherangeofcoverageareasothereisriskinprivacy if connection is established so access controller sent fake randomkeythatisintheformofzeroforprovidesecurityto network.
S. NO. Time Distance Power
1 0Sec. 0meter 3mw
2 10Sec. 10meters 2mw
3 20Sec. 20meters 3mw
4 30Sec. 30meters 4mw
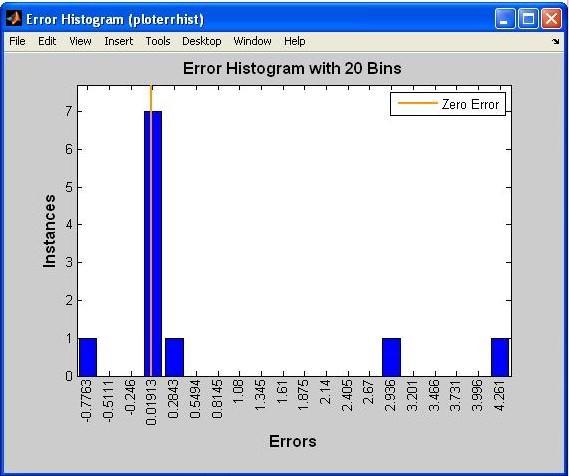
The error histogram plot produced by our neural networksimulationisdisplayedabove.Anerrorhistogramis a histogram of the deviations from the desired value, or forecast,thatoccurredaftertrainingafeedforwardneural network.Becausetheyindicatehowfartheprojectedvalues deviatefromthedesiredones,theseerrornumberscanbe negative.Thenumberofdiscretecategories(or"bins")ina barchart.Thehistogramisaformofbarchartthatdisplays numerical data by organizing it into discrete buckets. The error bars in the preceding graph range from a high of 0.01913at7instancestoalowof0.2843.
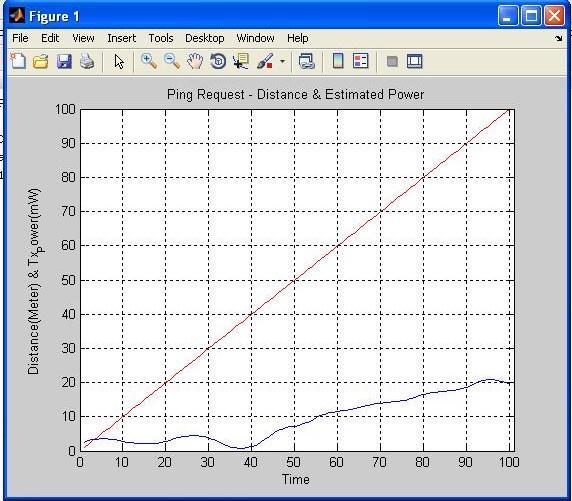
Theaboveresultisforpowerestimationbasedon distance,accesscontrollerstartssendingpingrequestatthe 0second,andcontinuouslysentpinwithtimeintervalof10 seconds with increment of some power after each 10 seconds of time interval. At the 0 (zero) meter transmit
5 40Sec. 40meters 2mw
6 50Sec. 50meters 8mw
7 60Sec. 60meters 11mw
8 70Sec. 70meters 14mw
9 80Sec. 80meters 17mw
10 90Sec. 90meters 19mw
11 100Sec. 101meters 20mw
Table: 4.1 PingRequest-Distance&EstimatedPower
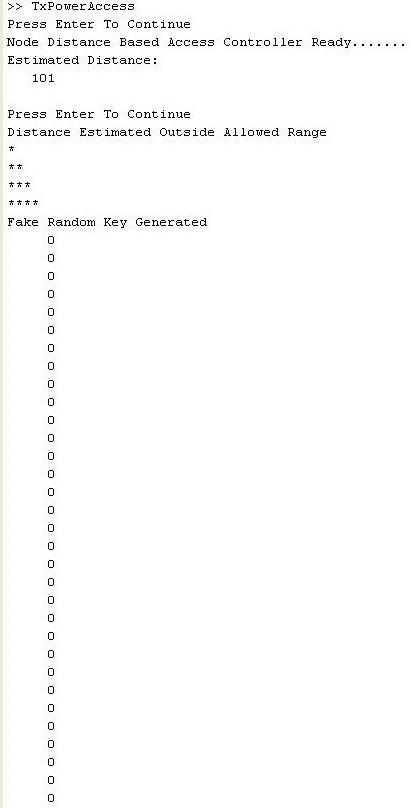
Figure: 4.4 FakeRandomKeyGenerated
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
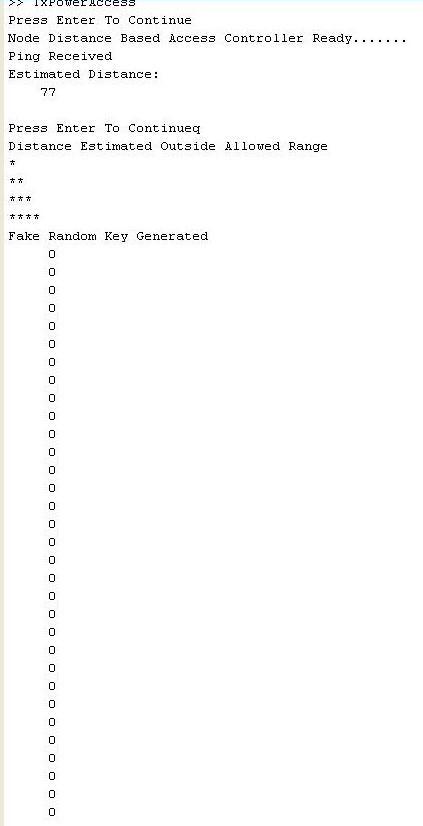
Inthisabovefigurewecanseepingreceivedatthe distanceof101meterandatthisdistancetransmitpoweris 20 mw, this range of distance estimated is outside of the allowedrange,soaccesscontrollergeneratesfakerandom keys in the form of zeros and provide to node for authenticationandprivacyofnetwork.
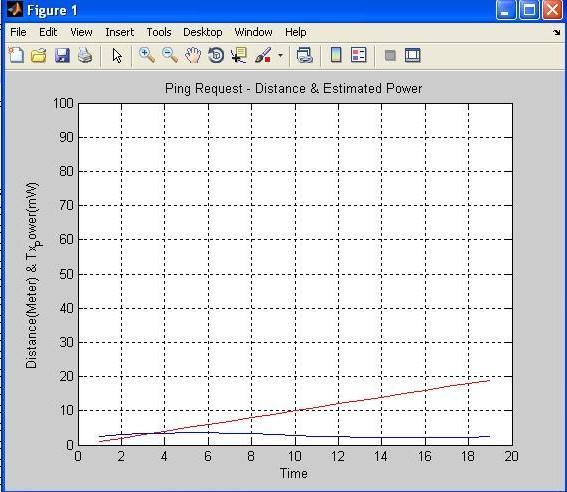
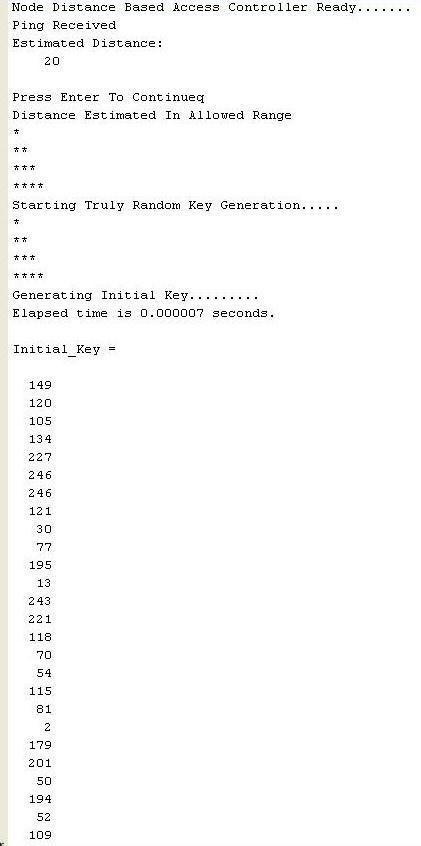
Abovefigureshowsdistanceestimationwithpower, access controller starts sending ping request with 2mw power,atthispowerdistanceestimatedbytrainednetwork is1meterat1second. Accesscontrollersentping request continuously with increment of some power, after 19 secondswith2mwpowerestimateddistancecalculatedby trained network is 19 meters at this point ping is success because this range in converge area so access controller provide initial key for establish connection with some leniencyinaccess.
S. NO. Time Distance Power
1 1Sec. 1meter 2mw
2 2Sec. 2meters 2.5mw
3 4Sec. 4meters 3mw
4 6Sec. 7meters 3mw
5 8Sec. 8meters 2.5mw
6 10Sec. 10meters 2mw
7 12Sec. 12meters 2mw
8 14Sec. 14meters 2mw
9 16Sec. 17meters 1mw
10 18Sec. 18meters 1mw
11 19Sec. 19meters 2mw
Table: 4.2 PingRequest–Distance&EstimatedPower
Inthisabovefigurewecanseeestimateddistance and initialize key. Above figure shows that node is in convergerange,sonodedistance-basedaccesscontrolleris ready for establish connection between node and access controller,becausepingisreceivedatdistanceof19meter. So,accesscontrollerprovedinitialkey,generatedinitialkey wecanalsoseeinabovefigure.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
controllersentpingrequestcontinuouslywithincrementof somepowerwiththetimeintervalof10 seconds,after78 secondswith15mwpowerestimateddistancecalculatedby trainednetworkis77metersatthispointpingisaccept.But thisdistanceisnotinconvergerange,soaccesscontroller providesfakekeyforprivacyofnetwork.
S. NO. Time Distance Power
1 0Sec. 0meter 3mw
2 10Sec. 10meters 2mw
3 20Sec. 20meters 2mw
4 30Sec. 30meters 4mw
5 40Sec. 40meters 1mw
6 50Sec. 50meters 8mw
7 60Sec. 60meters 12mw
8 70Sec. 70meters 14mw
9 78Sec. 77meters 15mw
Table: 4.3 PingRequest-Distance&EstimatedPower
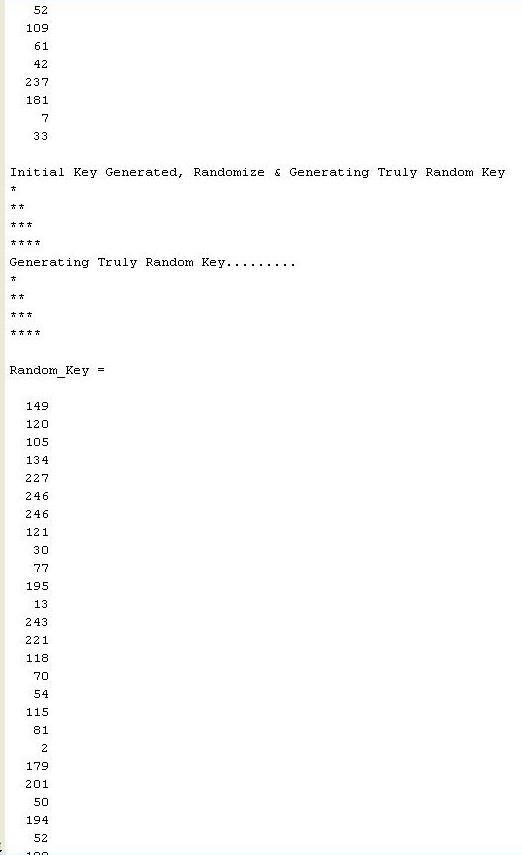
Inthisabovefigurewecanseegeneratedtrulyrandomkey.
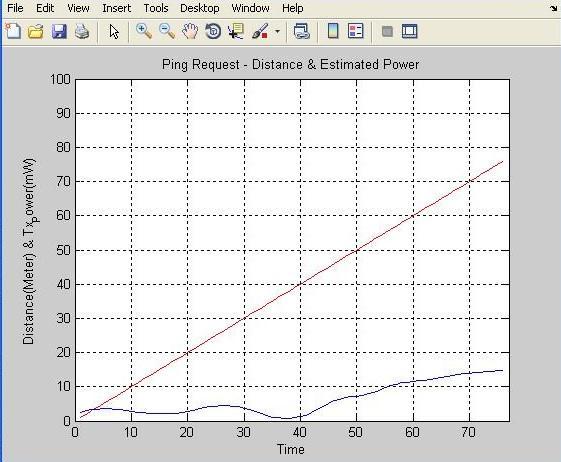
The above figure shows distance estimation with power,accesscontrollerstartssendingpingrequestwith0 mw power, at this power distance estimated by trained network is 0 meter at when time is 0 second. Access
value:
Figure: 4.9 FakeRandomKeyGenerated
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Inthisabovefigurewecanseepingreceivedatthe distanceof77meterandtheirtransmitpoweris15mw,this rangeofdistanceestimatedisoutsideoftheallowedrange, soaccesscontrollergeneratesfakerandomkeysintheform ofzerosandprovidetonodeforauthenticationandprivacy ofnetwork.
Blockchain technology is used in the suggested system.Blockchain-basedsecuritymechanismsmayalsobe implemented in the real world. The same blockchain architectureallowsplayerstoidentifyeachdevice.Thedata putintothesystemisunquestionableandmaybeused to identify the device that supplied it. IoT applications will benefitgreatlyfromblockchain'sabilitytoprovidesecure, distributedauthenticationandauthorizationofIoTdevices. Smartcontractscanconfirmdevicemessageexchangeson the blockchain, making it possible to secure device communication.
IoT protocols can be more secure with the aid of blockchain technology. In the Blockchain, messages sent between devices may be seen as transactions, and smart contractscanbeusedtoverifythem.IoTprotocolscanbe moresecurewiththeaidofblockchaintechnology.Thegoal proposed work is provided privacy in network based on distanceandpowerestimation,ifanynodetriestoestablish connectioninournetwork,ifthisisinourrangethenour accesscontrollerprovidedtruekeyforestablishconnection withsomeleniencyotherwiseifthisisinoutsidetherange thenaccesscontrollerprovidedfakerandomkeyforprivacy. Severalfactors,includingPathlossisthedecreaseinpower density of a radio signal over a long distance. Path loss is morelikelyduetothegradualattenuationofradiosignals overtheirextendedjourney.
The so-called inverse square law states that the radio wave power density increases as the square of the distance decreases. The sensitivity of the receiver is the secondmostessentialfactorinestablishingarange.Fading margin and environmental circumstances are two other variables that must be accounted for in any computation. There is also a potential height effect on the measuring range,sobemindfulofthatwhilesettingupyourantenna. Theaccompanyinggraphdepictsnonlinearitythatiscaused bythenonlineareffectsofseveraldifferentvariablesinthe RFspectrum.
Biometric identifiers, fingerprints, voice samples, retina or iris information, and other forms of biometric identificationallcanbedoneforimprovementintermsof security.Akey'sdependabilitymayalsobeestimatedusing trustmetricsbuiltontopofthedatarecordsthatmakeup
blockchain. There will be a lot of testing of Io Chain’s performance and sturdiness through the development of various apps on top of it. Also, the private Ethereum blockchainnetworkhastobeupdatedsothatthePoS-based versionoftheledgermaybeutilized,whenitispublishedby Ethereumdevelopers.Toexpandthisworkintohealthcare, hospitality,pharmaceuticalandeducationispossibleinthe future.
[1] Achraf Fayad, Badis Hammi, Rida Khatoun “A Blockchain-basedLightweightAuthenticationSolution forIoT”CyberSecurityinNetworkingConference2019.
[2] Aissam Outchkoucht, Hamza, Jean Philippe Leroy “Dynamic Access Control Policy based on Blockchain and Machine Learning for the Internet of Things” InternationalJournalofAdvancedComputerScienceand Applications2017.
[3] SoumyashreeS.Panda,UtkalikaSatapathy,BhabenduK. Mohanta “A Blockchain Based Decentralized Authentication Framework for Resource Constrained IOTdevices”IEEE2019.
[4] Khadija Fazal1, Adeel M.Syed “Blockchain Authentication Mechanism for Securing Internet of Things”PakJET2020.
[5] Dr.SakthiKumaresh,Dr.KBPriyaIyer“Decentralised Artificial Intelligence Enabled Blockchain Network Model”TurkishJournalofComputerandMathematics Education2021.
[6] Praveen Kumar Kollu, Monika Saxena, Khongdet Phasinam“BlockchainTechniquesforSecureStorageof Data in Cloud Environment” Turkish Journal of ComputerandMathematicsEducation2021.
[7] Shanshan Zhao, Shancang Li “Blockchain Enabled IndustrialInternetofThingsTechnology”IEEE2019.
[8] Muhammad Tahir, Muhammad Sardaraz , Shakoor Muhammad “A Lightweight Authentication and AuthorizationFramework forBlockchain-EnabledIoT NetworkinHealth-Informatics”Sustainability2020.
[9] DrMohdJavaid,Prof.AbidHaleem,DrRaviPratapSingh “BlockchaintechnologyapplicationsforIndustry4.0:A literaturebasedreview”JournalPre-proof2021.
[10] BhabenduK.Mohanta,AnishaSahoo,ShibasisPatel “DecAuth:DecentralizedAuthenticationSchemeforIoT DeviceUsingEthereumBlockchain”IEEE2019.
[11] JesseYli-Huumo,DeokyoonKo,SujinCho“WhereIs Current Research on Blockchain Technology? A SystematicReview”PLOSONE2016.