International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
In today's culture, when everyone wants to keep their assets safe and secure, video surveillance for keeping an eye on a certain area, such as hospitals, institutions, public parks, and buildings, has become necessary. Crime has increased as a result of the growing urban population. Video surveillance has significantly impacted citizens. The most popular technology is closed-circuit television (CCTV), but it is more expensive, consumes more power, and requires more storage. We created a cutting-edge intelligent video surveillance system for settings with erratic human presence to address this problem. In such circumstances, it is not required to have cameras trained on the area. This uses up the electricity and the footage storage space that is needed. Machine Learning tool called It uses a software library to implement this system. The proposed system works by capturing video, processing it frame by frame, and starting to record when it recognizes human presence. If the cameras spot any movement, the security system will turn on. The proposed system collects information and keeps it in a local database. The video that was recorded and saved can be used to recognize the intruder and help track him down. It may be useful in locations with sporadic human presence, including homes and bank vaults
Keywords : Surveillance; Intruder; Open CV; Face Recognition
How computers might be employed to extract profound insights from digital photos or videos is one of the many topicscoveredbythetremendouslydiversescientificfield known as computer vision. The objective is to automate operations that the human visual system is capable of performing from an engineering standpoint. The study of computer vision involves techniques for capturing photographs, processing them, comprehending them as digitalimages,andextractinghigh-dimensionalinformation from the real world to create information that may be expressedasnumbersorsymbols,suchasjudgements.The primaryobjectiveofasetofprogrammingfunctionsknown as OpenCV is real-time computer vision (Open-source computer vision). It was initially created by Intel. The collectionismulti-platformandfreelyaccessibletoanyone. Traditional video security systems don't allow for quick interventionwhenacrimeisbeingcommitted.Asystemlike thisisalsoquiteexpensiveandcomplicatedtosetup.The
goalofthisprojectistocreateanintelligentopen-sourcetool thatcanhelppeople.individualsororganizationsinbuilding asecure,affordablesystemontheirownTheywilltherefore have total control over their technology, giving them the abilitytosecurethesettingsandmodifythemtosuittheir requirements.Inordertopreventsomecrimes,itisessential to secure our homes, places of employment, and other commercialareas.Typicalsurveillanceequipmentisunable toinformpropertyownersofanycriminalactivity.Theonly thingtransmittedandrecordedisthefeed.Asaresult,the ownersareunabletopreventabreak-inortheftrightaway.
Therearemanydifferenttechniquesforfacial recognition available today, but the majority of them have certain drawbacks.aprocessforimprovingfacedetectionaccuracy using the Euclidean distance technique. The model is equipped with the Euclidean algorithm to recognize faces fromavarietyofdistances.Butthismodel'sweaknessisthat itcanbefooledwithfacialphotos,andthedatasetutilized isn'tbigenoughtoincreasedetectionaccuracy.
Motiondetectioncanbeusedtostopspoofingthatemploys simply photographs. Article uses an infrared PIR (Passive Infrared Sensor) sensor to detect motion in the person, whichallowsittodeterminewhetherthepersonisgenuine oranimage.Butaddinganadditionalsensorincreasesthe ThereisnoneedforanadditionalsensorbecauseOpenCV3 provideslibrarieswithalgorithmstodetectmotioninvideo, whichlowersthecost.
AnotherstudymakesuseoftheLPBHalgorithmandmotion detection to identify faces and record their attendance. However, a person can mark his attendance by wearing anotherperson'smask.Thismodelisnotentirelyspoofproof becauseitcannotidentifyfacialfeatures.
The LPBH method is used in this paper to work with low resolution images. Although it makes advantage of lowresolution photos by manipulating pixels, this model still lacks the spoof-proof features required for security surveillance.
This device enhances a home's security features, transformingitintoasmarthome.[1]Theinternetofthings (IoT) and the raspberry pi are utilized to comply to all of thesetrends.This defensesystemalertsthesubjectto the problemandprovidesacleanphotographofwhat'sgoingon.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Whenthetemperatureinthelivingroomrises,thefireplace sensornoticesitandupdatesthereputationintheURLthat wasgiventothecustomer,activatingabuzzer.Thestrength ofthegasintheairistheonlyfactorusedbythefuelsensor toidentifyanygasleaks.Theautomaticdoorlockisturned onbyadcmotor.AllstatusesaresentacrosstheInternetof Thingsbetweenthesensorsandtheuser.Paper3:Raspberry PiandOpenCV-basedlow-costsmartsecuritycamerawith nightvisioncapability.
Context: With the help of a Raspberry Pi (RPI) and a PIR sensor, the system's goal was to develop and construct a low-cost smart security camera with night vision capabilities. It is capable of both individual detection and smokedetection,whichmayhelptopreventbothcrimesand fires.PIRsensor-equippedRaspberryPi(RPI)regulatesthe shifting body, supervises the alarm systems, and uses Bluetoothtosendtheacquiredphotographstotheperson's email address. As part of the alarm system, the speech "intruder"maybeheardwhenanoutsiderisdetected.This investigationlooksatasmartsurveillancemonitoringdevice builtmostlyontheraspberry.Videosurveillanceisessential forsafetyintoday'ssociety.Commercialspacesmusthave high-speed cameras, warehouses, hospitals, schools, and otherunfavorableindoorandoutdoorlocations.Duetothe expensiveRFIDsusedinmodernsolutions,moreresearchis requiredandthesecurityindustrybecomesmoreexpensive.
OpenCV,anopen-sourcecomputervisionlibrary,isusedto implementthesuggestedsystem.Itreducesboththeamount of power used and the amount of storage needed by only monitoringdatawhenahumanisdetected.
Mission'smethodologymodel
1. Thecameraisinitializedinstepone.
2. Thecamerabeginstoscanthesurroundingsurroundings.
3. Ifapersonisdiscoveredbythecamera,therecordingwill start.
4. If the motion is not detected for a few seconds, the recordingmaystop.
5.Therecordedvideosarekeptonalocaldrive.
Inadditiontoshowingtherelationships,constraints,and difficultiesthatexistbetweeneachpart,thearchitectural diagramalsoshowshowthesoftwaredevicelooksoverall.
1.Initializationofthecameraisdonefirst.
2.The camera'sevolutiontoviewthesurrounding area begins.
3.StartuptheHaarcascadeclassifier.
4.Producegrayscaleimagesfromthevideoframes.
5. The recording will begin once the digicam recognizes someone.
6. The recording may be halted if the guy or woman isn't alwaysspottedforafewseconds.
7.Aneighborhoodforcestoresthevideotapes.

In 1991, Turk and Pentland suggested a face recognition technique based on concepts from linear algebra and dimensionalityreduction.Thismethodwasusedinarange of applications at the time, including handwriting recognition,lipreading,medicalpictureanalysis,andothers. Itiscomputationallylessexpensiveandstraightforwardto implement. In 1901, Pearson proposed PCA (Principal ComponentAnalysis)asamethodforreducingthenumber ofdimensions.ItreducesdimensionalityusingEigenvalues andEigenVectors.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
The eigenfaces have been improved by fisher faces. This approachispredicatedonthenotionthatnoteveryfeature of the face is equally important or useful for facial recognition.Inordertoidentifysomeonewhenwelookat theirface,wesearchforthefeaturesthatdifferthemost.The Fisher faces technique has been shown to be 93 percent accuratewhenusedinconjunctionwiththePCAapproach duringthepre-processingstage.
Thefisherfacessetofruleshasbeenreportedtobe93% accurate when used with the PCA technique on the preprocessingstep.
Accordingtocurrentresults,thenonlineartrainingmachine has a bigger margin and better identification and classificationresults.
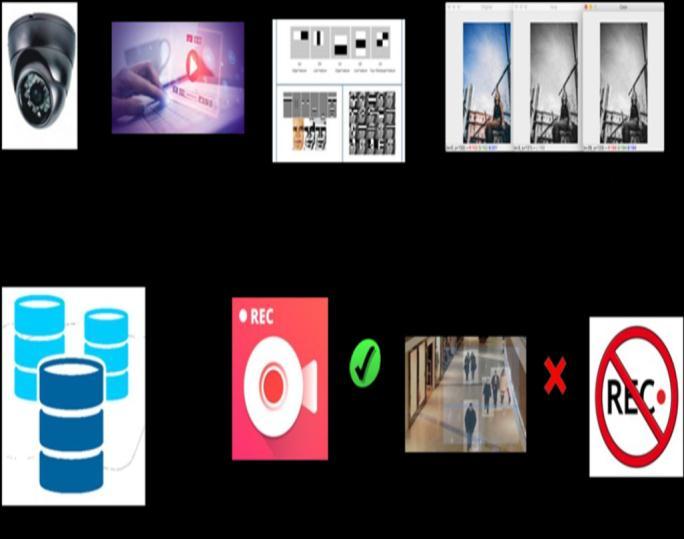
A technique for facial identification called LBPH (Local Binary Patterns Histograms) makes use of LBP. By thresholding each pixel's neighborhood and treating the result as a binary integer, the Local Binary Pattern (LBP) texturingoperatorassignslabelstoindividualpixelsinside animage.Additionally,itwasfoundthatcombiningLBPwith the histograms of oriented gradients (HOG) descriptor considerably improves detection performance on specific datasets. The facial images can be represented by a straightforward data vector. LBP may be used to identify facesbecauseitisavisualdescriptor.
1.Increasedprecision
2.Easytounderstand
Cons
1.Nevertheless,theremightbealossofrecognition.
2.Ittakesalongtimetoreceiveacknowledgement.
PCA (principal component analysis), when applied in the face recognition process, tries to reduce the amount of sourcedatawhilemaintainingthemostcrucialinformation. It generates a number of weighted eigenvectors, which in turngenerateeigenfaces,vastcollectionsofdifferentimages ofhumanfaces.Eachimageinthetrainingsetisrepresented byalinearcombinationofeigenfaces.Theseeigenvectorsare derivedusingPCAfromthecovariancematrixofaseriesof trainingimages.Themajor componentsofeachimageare calculated (from 5 to 200). The remaining components reveal subtle distinctions between noise and faces. The principal component of the unknown image is contrasted withthemajorcomponentsofallotherimagesaspartofthe recognitionprocess.
Support vector machine (SVM) is a machine learning technique that uses a two-group classification notion to distinguishbetween"faces"and"not-faces."Toclassifyfresh test data, a model employs a labelled training data set for each category. Researchers employ both linear and nonlinear. SVM training models for face recognition.

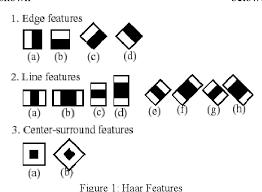
Intheir2001paper"rapiditempopularitywithaboosted cascade of easy features," Paul viola and Michael jones suggested an efficient object popularity strategy that was mostly based on the haar function based on cascade classifiers. It is a system-learning-based technique that investigatesacascadecharacteristicusingahugevarietyof fantasticanddreadfulimages.Thenitisappliedtoseveral snapshots so that objects may be located. We might concentrateonfacedetectionhere.Theapproachneedsboth positive (face-related) and negative (non-face-associated) imagestotraintheclassifier.Thenwe'lldecidewhatbenefits wecanderivefromit.Forthis,peoplewithattributeslike those listed below are hired. The picture below demonstratesthetypeoffeaturesincludingfourrectangle functions, line functions, and edge capabilities. When recognizingfaces,theseabilitiesareutilized
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Awindowshouldbediscardediftheinitialcheckfails.The finalcharacteristicsarenottakenintoaccount.
Haarcascadesareincrediblyquickwhencomputinghaarlikefunctionssincetheyusethenecessarypix(alsocalled summedlocationtables).TheAdaBoostsetofrulesmakes them fairly precise in their function selection. The most important role may be their ability to recognize faces in images,regardlessoftheirsizeorfunction.
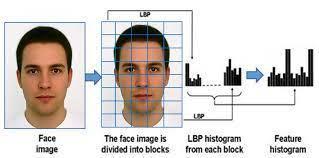
Themethodofgreyscalinginvolveschangingapicturefrom onecolourspacetoanother.Incontrasttoone-bitbi-tonal black-and-whiteimages,whichareblack-and-whiteimages inthecontextofcomputerimaging,grayscaleimageshave morethantwocolours.Therearenumerousshadesofgrey inbetweeningrayscalephotos.
1. Reducingthedimensionsofthephotos:Grayscale images are only one-dimensional and have no additionalparameterforcolourchannels,butRGB imageshavethreecolourchannelsandmakeupa three-dimensionalmatrix.
2. Due to dimension reduction, the information providedtoeachpixelisreduced.
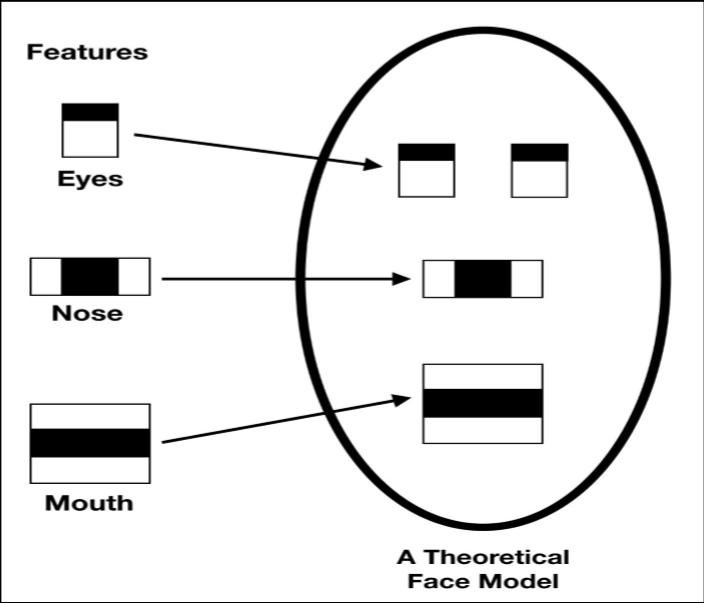
In a photograph, the non-face area is where most of the individualsare.Itisthereforepreferabletohaveaneasyway totellwhetherawindowisnotalwaysafacelocation.Ifit isn't,throwitawayimmediatelytoavoidhavingtoprocessit again.Instead,focusonlocationswhereafacemightappear. Thisenablesus toevaluate prospectiveface regions more thoroughly.
Theydevelopedtheideaofacascadeofclassifierstoachieve it.The6000capabilitiesmightbedividedupintostagesof classifiersandusedoneatatimeratherthanallatonce.
3. Reduces the complexity of the model: The neural network's input nodes will be significantly fewer whenlessinformationisprovidedtoeachpixelof theimage.Asa result,this makesa deeplearning modellessdifficult.

4. Colour photos are more challenging to visualise sincethesamealgorithmsorprocessesmaynotbe able to extract as much information from some images using grey scaling. The characteristics neededforextractionbecomemuchmoreapparent.
5. Tocomprehendimageprocessingbetter.
Fig6:BGRtoGrayConversion
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 12 | Dec 2022 www.irjet.net p-ISSN: 2395-0072
Thedevicemakesuseofahaarcascadeclassifiertolocate faces. It is easy to position into motion. This approach is particularly beneficial in conditions where humans are abnormal but the place should be monitored. It can significantly lessen storage use, power consumption, and maintenancecosts.Tofunctionproperly,thewholedevice best required the setup of OpenCV. It is by far a value effectiveerathatiseasytoputinforce.Thisapproachmay beusedbyeverybody,anditfacilitateslesseningtheamount ofstoragespaceimportantforthepictures.

[1]. A. Renjith and Aishwarya, “Enhanced home security UsingIoTandraspberrypi,"InternationalResearchJournal ofEngineeringandTechnology(IRJET),vol.4,2017.
[2]W. F. Abaya, J. Basa, M.Sy, A. C. Abad, and E.P. Dadios, "Low-costsmartsecuritycamerawithnightvisioncapability usingraspberrypiandOpenCV,"2014.
[3]M.Pervaiz,Y.Y.Ghadi,M.Gochoo,A.Jalal,S.Kamal,and D.-S.Kim,“Asmartsurveillancesystemforpeoplecounting and tracking using particle flow and modified som,” Sustainability,2021.
[4]M.Rashmika,“Motionsensorandfacerecognition-based surveillance system using raspberry pi,” International JournalofAdvancedResearchinComputer Science,vol.8, no.5,2017.
[5]A.CobParro,L.Gutierrez,Marron-Romera,GardelVicente, andBravo-Munoz,“Smartvideosurveillancesystembased onedgecomputing,”2021.
[6]T.Shivprasad,B.Shivani,A.P.Singh,andDeepak,“Survey paperonsmartsurveillancesystem,”InternationalResearch Journal of Engineering and Technology (IRJET), vol. 3, 2016.Fig6:BGRtoGrayConversion