International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
Civil Engineer, 21, First Floor, Third Main Road, Vasanth Nagar, Bangalore – 560052, India ***
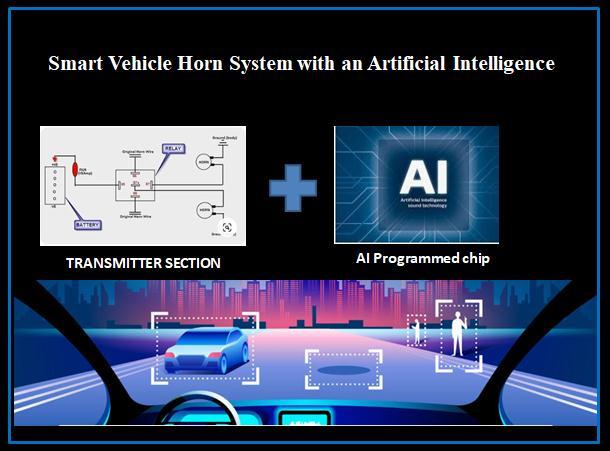
Abstract - The increasing levels of noise pollution pose a major threat to human health and the environment. Blaring unnecessarilyclose to neighbourhoods, schools signandclinics is for the most part impacted and unequivocally wanted. We propose a brand-new honking mechanism that would substantially reduce horn blowing noise. The current mechanism does not compromise the safety of individuals inside andaroundthe vehicle.The vehicle'sfixedhornsystemis used in our proposed mechanism. Using artificial intelligence, our horn system automatically adjusts the horn sound to the distance between people, the width of the road, and the size of the object. As a result, artificial intelligence will control the horn's sound.
Key Words - Intelligent Vehicle Horn System
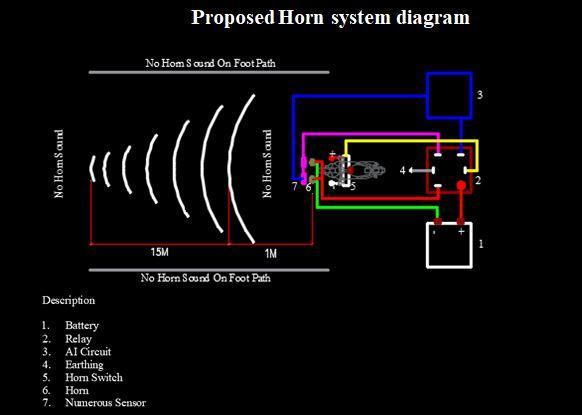
Hornsystemisfittedwithnumeroussensors;camerasand manual horn switch to generate massive amounts of environmentaldata.AlloftheseformtheDigitalSensorium, throughwhichtheindependentvehiclecanseeandfeelthe objects, roadinfrastructure,othervehiclesandeveryother objecton/neartheroad,justlikeahumandriverwouldpay attentiontotheroadwhiledriving.
This data is then processed with inbuilt chip and data communicationsystems.TheseareusedtoOnlypushtheon switch, and it will automatically return to its original position.
The horn switch will operate for a period of five seconds.
1.2 Mathematics:
D(x,y,σ)=(G(x,y,kσ)G(x,y,σ))*I(x,y) =L(x,y,kσ)L(x,y,σ)
Where *istheconvolutionoperator, G(x,y,σ)isavariablescaleGaussian, I(x,y)istheinputimageD(x,y,σ)
isDifferenceofGaussianswithscalektimes.[1]
2. HEADING
Wecan'tpresstheswitchformorethanasecondat atime.
Wecan'tchangethehornsystembecausedoingso woulddamagetheentiredevice.
The device won't function if people aren't on the roadorifanimalscrossorsleep.
Finally,thehornwillsoundbothhorizontallyand verticallydependingonthewidthoftheroad.
Thosewhoarewalkingalongsidethevehicle,onthe footpath, or inside the building cannot hear the horn.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056


Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
3.1 Scale-space Extreme Detection: The first stage of computation searches over all scales and image locations. It is implemented efficiently by using a difference-of-Gaussian function to identify potential interestpointsthatareinvarianttoscaleanddirection
3.2 Key point localization: At each object location, a detailedmodelisfittodeterminelocationandscale.Key pointsareselectedbasedonmeasuresoftheirstability.
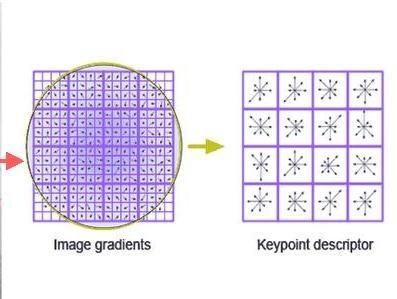
3.3 Orientation assignment: Oneormoreorientationis assigned to each key point to achieve invariance to image distance. A neighbourhood is taken around the key point location depending on the scale, and the gradientmagnitudeanddirectioniscalculatedinthat region.
3.4 Key point descriptor: Thelocal imagegradientsare measuredattheselectedscaleintheregionaroundeach keypoint.Thesearetransformedintoarepresentation thatallowsforsignificantlevelsoflocalshapedistortion and change in illumination. The first stage used difference-of-Gaussian (DOG) function to identify potentialinterestpoints,whichwereinvarianttoscale and orientation.DOGwasused insteadofGaussianto improvethecomputationspeed.
D(x,y,σ)=(G(x,y,kσ)G(x,y,σ))*I(x,y)
=L(x,y,kσ)L(x,y,σ)
Scale Invariant Feature Transform (SIFT) features are featuresextractedfromimagestohelpinreliablematching betweendifferentviewsofthesameordifferentobject.[6] Theextractedfeaturesareinvarianttoscaleandorientation, andarehighlydistinctiveoftheimage.Theyareextractedin four steps. The first step distance sensor the locations of potential interest points in the image by detecting the maximaandminimaofasetofDifferenceofGaussian(DoG) filters applied at different scales all over the image. Then, these locations are refined by discarding points of low contrast.Anorientationisthenassignedtoeachkeypoint based on local image features. Finally, a local feature descriptoriscomputedateachkeypoint.Thisdescriptoris basedonthelocalimagegradient,transformedaccordingto the distance of the key point to provide orientation invariance. Every feature is a vector of dimension 128 distinctively identifying the neighborhood around the key point.ThefollowingstepsareinvolvedinSIFTalgorithm:
Where *istheconvolutionoperator, G(x,y,σ)isavariablescaleGaussian, I(x,y) is the input image D(x,y, σ) is DifferenceofGaussianswithscalektimes.
Foranyobjectinanimage,interestingpointsontheobject can be extracted to provide a "feature description" of the object.Thisdescription,extractedfromatrainingimage,can thenbeusedtoidentifytheobjectwhenattemptingtolocate theobjectinatestimagecontainingmanyotherobjects.To performreliablerecognition,itisimportantthatthefeatures extracted [11] from the training image be detectable even underchangesinimagescale,noiseandillumination.Such pointsusuallylieonhigh-contrastregionsoftheimage,such asobjectedgesanddistance.
SIFT key points: [5]ofobjectsarefirstextractedfromaset of reference imagesand stored in a database. An object is recognizedinanewimagebyindividuallycomparingeach feature from the new image to this database and finding person/object matching features based onEuclidean distanceoftheirfeaturevectors.Fromthefullsetofmatches, subsetsofkeypointsthatagreeontheobjectanditslocation, scale,andorientationinthenewimageareidentifiedtofilter outgoodmatches.Thedeterminationofconsistentclustersis performed rapidlybyusinganefficient. Eachclusterof3or more features that agree on an object and its pose is then
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
subject to further detailed model verification and subsequentlyoutliersarediscarded.Finallytheprobability thataparticularsetoffeaturesindicatesthepresenceofan objectiscomputed,giventheaccuracyoffitandnumberof probable false matches. Object matches that pass all these testscanbeidentifiedascorrectwithhighconfidence.
3.5 Key point Matching: Keypoints between two images are matched by identifying their nearest neighbours.Butinsomecases,thesecondclosest-match maybeveryneartothefirst.Itmayhappenduetonoise orsomeotherreasons.
Anotherimportantcharacteristicofthesefeaturesisthatthe relative positions between them in the original scene shouldn'tchangefromoneimagetoanother.Forexample,if onlythefourcornersofa roadwereusedasfeatures,they wouldworkregardlessoftheobjectposition;butifpointsin the frame were also used, the recognition would fail ifthe road is long or closed. Similarly, features located in articulatedorflexibleobjectswouldtypicallynotworkifany change in their internal geometry happens between two imagesinthesetbeingprocessed.However,inpracticeSIFT detectsandusesamuchlargernumberoffeaturesfromthe images,whichreducesthecontributionoftheerrorscaused bytheselocal variationsintheaverageerrorofall feature matchingerrors.
SIFTcan robustly identify objects even among clutter and underpartialocclusion,becausetheSIFTfeaturedescriptor is invariant touniform scaling,distance, and partially invarianttoaffinedistortionandilluminationchanges.This sectionsummarizesLowe'sobjectrecognitionmethodand mentions a few competing techniques available for object recognitionunderclutterandpartialocclusion.
Inthekeypointlocalizationstep,theyarerejectedthelow contrastpointsandeliminated the edge response.Hessian matrix was used to compute the principal curvatures and eliminate the key points that have a ratio between the principal curvatures greater than the ratio. An orientation histogram was formed from the gradient orientations of samplepointswithinaregionaroundthekeypointinorder togetanorientationassignment.Accordingtoexperiments, thebestresultswereachievedwitha4x4arrayofhistograms with8orientationbinsineach.SothedescriptorofSIFTthat wasusedis4x4x8=128dimensions.
PCA-SIFT:PrincipalComponentAnalysis(PCA)isastandard techniquefordimensionalityreductionandhasbeenapplied to a broad class of computer vision problems, including feature selection. PCA-SIFT can be summarized in the followingsteps:
Pre-computeanEigenspacetoexpressthegradient imagesoflocalpatches
Givenapatch,computeitslocalimagegradient
Project the gradient image vector using the Eigen spacetoderiveacompactfeaturevector.
Theinputvectoriscreatedbyconcatenatingthehorizontal andverticalgradientmapsforthe41x41patchcenteredat the key point. Thus, the input vector has 2x39x39=3042 elements.Then normalizethisvectortounitmagnitudeto minimizetheimpactofvariationsinillumination.Projecting thegradientpatchontothelow-dimensionalspaceappearsto retain the identity related variation while discarding the distortionsinducedbyothereffects.Eigenspacecanbebuilt byrunningthefirstthreestagesoftheSIFTalgorithmona diverse collection of images and collected 21,000 patches. Each was processed as described above to create a 3042elementvector,andPCAwasappliedtothecovariancematrix of these vectors. The matrix consisting of the top n eigenvectorswasstoredondiskandusedastheprojection matrixforPCA-SIFT.TheimagesusedinbuildingtheEigen spacewerediscardedandnotusedinanyofthematching experiments[11].
AbasicsecondorderHessianmatrixapproximationisused for feature point detection. The approximation with box filtersispushedtotakeplaceofsecond-orderGaussianfilter. And a very low computational cost is obtained by using integral images. The Hessian-matrix approximation lends itself to the use of integral images, which is a very useful technique. Hence, computation time is reduced drastically [10]. In the construction of scale image pyramid in SURF algorithm,thescalespaceisdividedintooctaves,andthere are 4 scale levels in each octave. Each octave representsa series of filter response maps obtained by convolving the same input image with a filter of increasing size. And the minimum scale difference between subsequent scales dependsonthelengthofthepositiveornegativelobesofthe partialsecondorderderivativeinthedirectionofderivation.
Threshold is one of the widely methods used for image segmentation.Itisusefulindiscriminatingforegroundfrom thebackground.ByselectinganadequatethresholdvalueT, thegraylevelimagecanbeconvertedtobinaryimage.
International Journal of Scientific & Engineering Research Volume8,Issue5,May-2017
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
10strongestSURFfeaturesincludingscaleandorientation which was determined during the descriptor extraction process
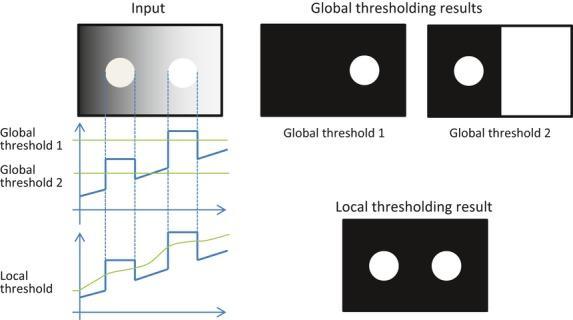
Thebinaryimageshouldcontainalloftheessential Informationaboutthepositionandshapeoftheobjectsof interest(foreground).
Ifg(x,y)isathresholdversionoff(x,y)atsomeglobal ThresholdTitcanbedefinedas[1], g(x,y)=1iff(x,y)≥T=0otherwise Thresholdingoperationisdefinedas: T=M[x,y,p(x,y),f(x,y)]
WhenTdependsonlyonf(x,y),onlyongray-levelvaluesand the value of T solely relates to the character of pixels, this thresholdingtechniqueiscalledglobalthresholding.
If threshold T depends on f(x, y) and p(x, y), this thresholding is called local thresholding. This method dividesanoriginalimageintoseveralsubregions[12],and choosesvariousthresholdsTforeachsubregion reasonably [13].

Figure,imshow(I);holdon; lot(valid_points.selectStrongest(10),’showOrientation’,true);
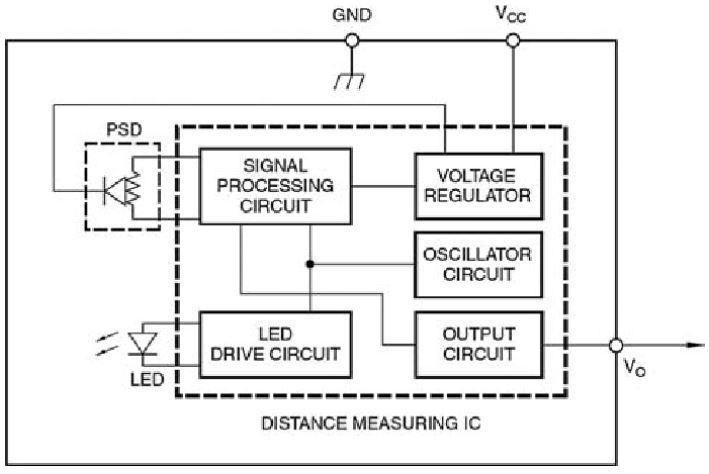
Fig -6: Block diagram showing the distance measuring from the range sensor.
Fig -7: Vehicle Image showing the distance measuring from the range sensor.

Read the two images. I1=imread('cameraman.tif');
Find the SURF features. Points=detectSURFFeatures(I); [features,valid_points]=extractFeatures(I,points);
Fig -8: Single-sensor-based chord offset synchronizing model
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
Thehornsystemincludesthefollowingterminology:
Impedance: Quantityimpedingorreducingflowofenergy. Canbeelectrical,mechanical,oracoustical.
Acoustical Impedance: The ratio of sound pressure to volumevelocityofair. Inahorn,theacoustical impedance willincreasewhenthecross-sectionofthehorndecreases,as a decrease in cross section will limit the flow of air at a certain pressure.
Volume Velocity: Flow of air through a surface in m3/s, equalsparticlevelocitytimesarea.

Throat: The small end of the horn, where the driver is attached.Mouth:Thefarendofthehorn,whichradiatesinto theair.
Driver: Loudspeakerunitusedfordrivingthehorn.
c:Thespeedofsound,344m/sat20°C.
7.1
Thehourlyflowofeachvehiclecategory(Veh/hr)andthe average speed of each category (km/hr) are used for calculationofLeqvalue.Thereforethismodelincorporated the volume speed correction that is applied for final Leq value.Thecorrectionisgivenas:
Avs=10Log(DOV/S)-25
Where,
V=Volumeforthecategory(Veh/hr)
S=Speed(km/hr)
DO=Referencedistance(m/s)
7.2 Distance correction:
Whencalculatingdistanceadjustmentthetypeofintervening ground cover between the highway and reception point is alsoconsidered.
AD=10Log10(DO/D)1+α]
Where,
DO=Referencedistancegivenas10meters
D=Distanceofmeasurementfromcenterofeach Lane
α=Groundcovercoefficient
ScaleInvariantFeatureTransformisusedtoextractfeatures from the ID. The implementation is done using MATLAB. Feature extractionenables you to derive a set of feature vectors, also called descriptors, from a set of detected features.ComputerVisionSystemToolboxofferscapabilities forfeaturedetectionandextraction.
SURF is used to detect blobs and regions. The SURF local featuredetectorfunctionisusedtofindthecorresponding pointsbetweendifferentimagesthatarenear/farandscaled withrespecttoeachother.
In accordance with another preferred embodiment of the invention, the positioning system further comprises supplementarysensors,suchasTacho/ABSsensorsorGyro sensors.
In accordance with another preferred embodiment of the invention, the alarm is an audio alarm and/or an optical alarm.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
According to the invention, at a location that honking is forbiddenorrestricted,thehornofavehicleisautomatically deactivatedorthesoundlevelislowered,and/orthedriver receives an alarm that the horn should not be used. Thus, hornnoisewillbeeffectivelycontrolledinspecifiedareas.In addition,atalocationthathonkingmustbeperformed,the hornofavehicleisautomaticallyoperatedtogeneratesound, and/orthedriverreceivesanalarmthatthehornshouldbe operated to generate sound. Thus, traffic safety can be improved.
The present invention in a second aspect provides an automatic vehicle horn control method comprising: a) acquiring information about horn operating regulation related with current or concerned location and driving directionofthevehicle;b)ifatcurrentorconcernedlocation andincurrentorconcerneddrivingdirectionitisnotallowed tooperatethehorntoproducesoundorthesoundlevelis notallowedtobehigherthanacertainlevel,thenahonking forbiddenorrestrictionmodeisinitiatedinwhichthehornis deactivatedorthesoundofthehorniscontrolledtobelower thanacertainlevel,and/oranalarmindicatingthehonking forbiddenorrestrictionrequirementisgenerated,
Using a distance parameter between a person and other objects,thisdevicecanmonitorandcontrolthesoundofthe vehiclehorn.
We can send these data to a faraway location around the worldtocreateasoundgraphreport.
Whenitismanufacturedinlargequantities,thisdevicewill berelativelyinexpensive.
Ifthesoundofthevehiclehorngoesawaywithinfiveyears, thiswillhaveagoodfutureandbeacompletesuccess.
DespitethefactthattheEarthhasprovideduswithallofthe necessaryresourcesforourexistence.Thenumerouslevels and domains of life, as well as the biosphere, lithosphere, atmosphere,andhydrosphere,areinperfectharmony.Asa resultofthiscoordinationandsynchronization,wemightbe abletolivealongandhealthylifehereonEarth.
Numerous factors, including increasing sound, vibration, heat,andclimatechange,aredepletingEarth'sresources.The depletionofourEarth'sresourcesisevidentinallofthese signs,anditistimetosaveourplanet:Theiceisgoingaway; woodlands are consuming; The fields are dry and empty; oceansareunsteady;Thewaterisimperfectandvibratesata higher frequency. We can help ourselves by reducing the earth'svibration

Fig -10: Only One Earth
[1] Priya M.S in honor of her Intelligence work on MultilevelImageThresholdingusingOTSU’sAlgorithm inImageSegmentationInternationalJournalofScientific &EngineeringResearchVolume8,Issue5,May-2017
[2] WinfriedOttoSchumanninhonorofhisseminalwork onglobalresonancesinmid-1950s
[3] IntelligentAutomotiveSolutions,Huawei
[4] MichaelCarlowicz EarthBook,NASA
[5] A.AnnisFathima,R.Karthik,V.Vaidehi,“ImageStitching withCombinedMomentInvariantsandSIFTFeatures”, ProcediaComputerScience19(2013)420–427.
[6] David G. Lowe. Distinctive image features from scaleinvariantkeypoints.Internationaljournalofcomputer vision,60,2004.
[7] Edouard Oyallon, Julien Rabin, "An Analysis and Implementation of the SURF Method, and its ComparisontoSIFT",ImageProcessingOnLine
[8] M.M. El-gayar, H. Soliman, N. meky, “A comparative studyofimagelowlevelfeatureextractionalgorithms”, EgyptianInformaticsJournal(2013)14,175–181.
[9] HerbertBay,TinneTuytelaars,andLucVanGool,“SURF: SpeededUpRobustFeatures”,ETHZurich,Katholieke UniversiteitLeuven
[10] SimranjeetKaur,GagandeepSinghSaini,SandeepKaur, “Performance Evaluation of Fuzzy Sift and Canny FeatureExtraction”,IJARCSSE,Vol5,Issue7,July2015.
[11] YanKe,RahulSukthankar, “PCA-SIFT: A More Distinctive Representation for Local Image Descriptors”, School of Computer Science, Carnegie Mellon University, Intel ResearchPittsburgh
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN: 2395-0072
[12] J.Gong,L.Li,andW. Chen,“Fastrecursivealgorithms for two-dimensional thresholding,” Pattern Recognition,vol. 31, no.3,pp.295–300,1998.
[13] J.S. Weszka: A Survey of Threshold Selection Techniques,ComputerGraphicsandImageProcessing, Vol.7,pp.259-265,1978.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
