International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072


Devang Barot1 , Saket Swarndeep2
1Student of Master of Engineering, Ahmedabad, Dept. of Computer Engineering, L.J University, Gujarat, India. 2Assisstant Professor, Dept. of Computer Engineering and Technology, L.J University, Ahmedabad, Gujarat, India ***
Abstract - There are many Credit Card Fraud Detection Systemintwodays world.Thispaperisgoingto discussabout the various techniques used in Credit Card Fraud Detection andalsohowthedatasetsarechosenorpre-processedtobuild the Machine Learning, Deep Learning, Neural Network models.We willbegoingto discussvarious models like neural networks, decision tree, logistic regression, Random Forest, ParallelGranularNeuralNetworks,Multivariatecontrolchart ,GaussianKernel,Meta-Learning,ComputationalIntelligence, Convolutional Neural Networks, NeuralNetwork onthe basis of Mining System, Self-Organizing Maps, Generative AdversarialNetworks,Pipeling,EnsembleLearning,AdaBoost, Majority Voting, Deep Convolution Neural Network Model, Adversarial Learning, Fuzzy Clustering, Optimized Light Gradient Boosting, anti-k nearest neighbour, Calibrated Probabilities, bidirectional Long short-term memory (BiLSTM),bidirectionalGatedrecurrentunit(BiGRU),Genetic Algorithm, Class Balancing Techniques, Auto-Encoder, Restricted Boltzmann Machine, Cat Boost, Light Gradient Boosting Machine
Key Words: Credit Card Fraud Detection, Credit Card Frauds, Machine Learning, Deep Learning, Detection Methods, Classifiers
So, to overcome these frauds there are many frauds detection system has been created by the use of Python, Machine Learning, Deep Learning. Credit Card Fraud DetectionSystemisasystemoranalgorithmorcombination ofmultiplealgorithmswhichpreventthefraudtransactions tobehappeningandiffraudtransitionhappenitwillinform theuseraboutthefraudtransactionisdetected.
Fig - 1: CreditCardFraudDetectionSystem[16]
CreditCardhadmadedailylifemucheasier.Dailypayments canbedoneinnotimebuteverycoinhas2sidesallthings allprosandcons.CreditcardhasCreditcardfraudsasthe most important con. Credit card frauds can be virtual or physical.Creditcardfraudisagrowingmenacethesedays.It isaprocessinwhichthirdpartydothemoneytransaction withoutpermissionorunderobservationofthecardholder.
Fig - 2: CreditCardFrauds[15]
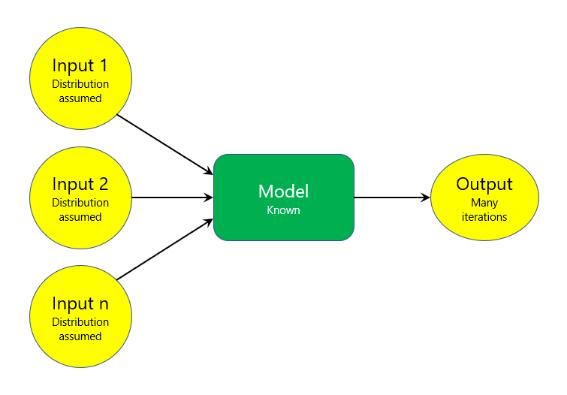
Machine Learning:ItisabranchofComputerSciencewhich takesthepreviousdataandlearnfromitandbuiltamodel on the bases of which we give the future predictions. Machine learning is taking over all the other techniques todayworldisusing.Machinelearninghavevariousamount ofalgorithmwhichcanhelpusinpredictions.
Fig - 3: BasicModelofMachineLearning[17]
Factor value: 7.529 | ISO 9001:2008 Certified Journal
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
MachineLearninghas3maintechniquestheyare:
1. Unsupervised Learning: - UnsupervisedLearning is a technique which uses unlabelled data and learningdonottakeplaceundersupervisor.Output isnotknowntouser
2. Supervised Learning:Supervised Learning is a technique which uses labelled datasets and learning takes placed under supervisor. Outputisknowntouser.
3. Reinforcement Learning:In this process negative and positive reward are given onthe basisof theactionanddecisionthey take.Machineobservestherewardsactaccordingly.
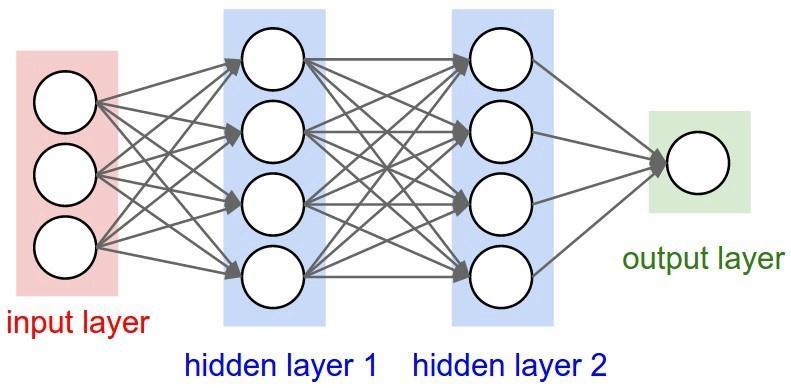
Deep Learning: WE can say that the deep learning is the extended version of the machine learning or a part of machine learning where artificial neural network is used where extraction of high features takes place from the datasetswheremultiplelayersofprocessesisused.
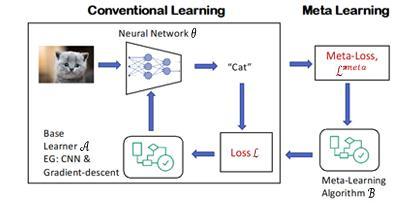
Metalearninggivesyouhowtolearnandcombinationand integration of numbers of separated learned classifiers or models.MultipleU.Sbankscontributeddataforthisfraud detectionsimulation.Thedatabasecontains500000records andeachrecordwerehaving30fields.Thedatawhichwas provided by the banks where labelled as the fraud transaction and non-fraud transaction. Data between January and October was taken as training data and validation in meta data was done in month of November. December’s data was taken as testing data. They consider 42000 data randomly for training purpose and 4000 data fromtheNovembermonthforthemetalearningvalidation. to test the data, they had taken 4000 records for testing purpose.TheyhaveuseID3andCART.Thelearningprocess ofboththealgorithmsarebasedonthedecisiontrees.The process of getting base classifier for meta learning to use class-combiner.Experimentwascariedouttwiceand1600 times each combination was processed. The Data was distributedinthepercentageof50-50fraud/non-fraud.The truepositiverategeneratedwas80%andfalsepositivewas lessthan16%andthisdistributiongeneratedamaximum frauddetectionrateandminimumamountofalarmrate.For thefutureaspectstheygonebeusingslidingwindowforthe selectionoftrainingdatafromthepreviousmonths.
Fig - 4: BasicModelofDeepLearning[18]
In [1], they talked about how to use meta learning for detectionoffraud.thesystemtheybuildinghas2important components which are Local Fraud Detection Agents and MetaLearningAgent.LocalFraudDetectionAgentsdetect theintrusionbylearningpreviousfraudsinasinglesystem. A generated new classifier agent is made up of 2 or more classifiersbymetalearningagents.
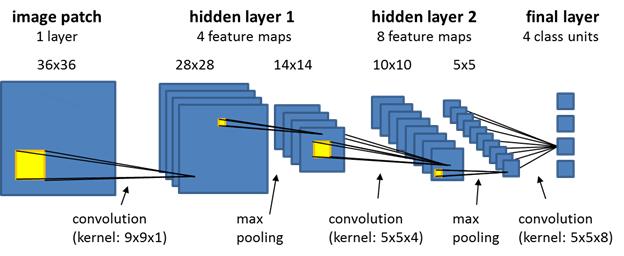
Neural Networks [2] had also played an important role in Creditcardfrauddetection.Wearegoingtodiscussabout conversation neural network and how it going to help in creditcardfrauddetection.FeatureMatrixhasbeenusedfor theabandonedtransactionsdata.Atfirst,theyhavegiventhe small description about CNN-based fraud detection framework after getting idea about fraud detection Frameworksecondly,theywhointroducedustothenovel trading features and third step will be solving problem of creditcardfrauddetectionthefirsttwoinitialstepisthatthe trainingpartwillbedoneofflineandthepredictionpartwill beonline.Whenthetransactionwillarrive,thesystemwill judge whether the following transaction is legitimate or fraudulentinno time.Following threeinitial steps will be takenandthatisafeatureselectionfeaturetransformation andclassificationmodule.CNNhadbeenusedbecauseitis veryconvenientforthelargesizeofdataandalsoitisvery helpfulforavoidingtheoverfittingofthemodel.Thereare manyapplicationsofconvolutionneuralnetworkandtwoof themareimageclassificationandspeechsignalprocessing. Fromtheoriginalattributesoftransactionwhichgeneratea one dimensional which are then transformed into feature matrices
Fig - 5: BasicModelofMetaLearning[19]
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
Werandomlyselectthesampleswhichcanbefraudulentor legitimateinordertogenerateheatmaps.Inthemodelthere aresixmeanplayers.Firstlayercontentconvolutionlayer whichisthenfollowedbysamplinglayerthirdlayerisalso called convolution layer and the last three contain all the connectivitywhichisnamedasafullyconnectionlayerthe dataistakenfromthetraditionalcommercialbanksandthe datasetcontainsto260milliontransactionrecordsinwhich rest of the data is legitimate transaction and only 4000 transactionswerefraudulent.DidtothedatafromJanuaryto December as a training data and the records of 11 word takenforthetestingpurpose.TheresultsofCNNmodelwere comparedwiththeotheralgorithmsanditisresultedthat CNN model on various samples achieve the best performance from all of the other algorithms After the algorithmisprocessF1scoreisdecidedonthebasisofF1 scoreperformanceisevaluatedofthemodel.
Thispaper[3]talksabouthowthedataminingsystemcan helpincreditcardfrauddetection.Thebasictargetbehind this idea is to extract implicitly interesting and unknown knowledgefromthedatabase.Theapproximatenumbersays thataVisacardandMasterCardusers’lossapproximately 700millioninUSasafraudcreditcardcharge.Singin the present tense feedforward network architecture are implemented in the CARDWATCH the cardboard system consists of five main models which are global constant module GCM Core Graphical User Interface Module GUIM DatabaseInterfaceModuleDBIMLearningAlgorithmLibrary
LALLearningAlgorithmInterfaceModuleLAIM.Cardwatch isafraudulentdetectionsystem.Andtalkinginthepresent times only feed forward network architecture are implemented in garbage they have used 3-layer neural networkfunctioningpurpose.Autoassociativenetworkhas been used for the training purpose in order to reproduce legal patent which is fresh and new but they cannot reproducefraudpatternsthemajordrawbackofthesystem wastheyuseone network forcustomerrestrictions. They createdafakecardholderinordertogeneratethisuserthey haveused3transactiongeneratorinputsstartingpointof transactionconsistofsetor323transactionswithnumberof threedifferentpurchasecategorieswhichhaveperiodof365 days costly 264 transaction work given for the training purposehencetheyhave3purchasecategoriessotheinputs were given in the unit of 7-7-7 in architecture of network RMSC was used to determine whether the transaction is legalorfraudulentafterthissystemwastesteditgenerate 85% of fraud detection rate and hundred percent of legal transactionidentificationratethissystemhasaGUIinterface veryfriendly.Forthefuturepurposethecardwatchwillbe extended for the use of general purpose of anomaly detection
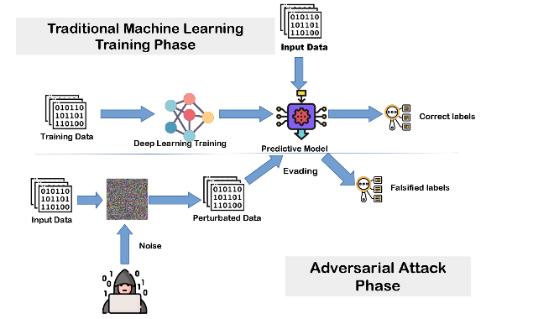
Whenthereisattackonmachinelearningalgorithmsandthe waywearegoingtotacklethatattack'sthistypeoflearning is called that was adversarial learning. In [4] adversarial learningisusedfordetectingthefraud.Togenerateamodel offraudsterbeststrategytheyhaveusedgametheoretical adversarial learning approach. For the classification of fraudulentandnon-fraudulenttransactiontheyhaveused Logisticregression.Testresultsshowsthatstatisticmodel does not perform well while adversary aware classifier is betterthanstaticmodel.Adversaryaclassifierhasincrease under the curve score. They are using SMOTE in order to balancetheclassratiobygenerationofsyntheticinstancesof fraudulenttransactionsintheversionofversionsampling. Theprocessislikeokchoicebetweenstrategiesaregiven opportunity is given to the classifier that it can utilize the sameclassafireorRetrain theclassifier.ROCcurvewith adversarial learninghadshown growthanarea underthe curveiswentupto0.78to0.84.Itisalsonoticedthatasthe roundproceedsperformanceofclassifier.
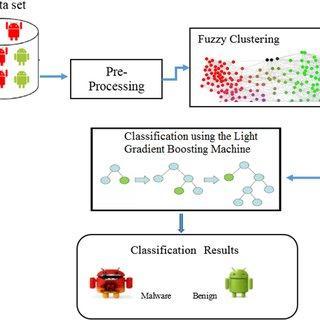
This research paper [5] has use the hybrid approach in whichdayhaveusetwomethodswhicharefuzzyclustering andneuralnetwork.Clusteringwheredatapointbelongsto one or more clusters is known as fuzzy clustering. Neural network consists of input layer hidden layer and output layer and also consists of nodes. Neural network act as a human brain. Because of overlapping nature of cluster boundaries, the usage of hard clustering is limited in
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
physicalworldapplication.Duetounavailabilityofreal-life creditsetthedatasethasbeendevelopedbyPanigrahi.The synthetic transaction is generated by use of Gaussian distribution that shows the behaviour of Genuine user as wellandfraudulentusertheSimulatorreflectsthereal-life scenario those are usually seen in credit card transaction processing system. MATLAB- 2014 is used in the implementation of fraudulent detection system fuzzy c meansalgorithmmoduleisprovidedinputvectorsasinput. Suspicionscoreiscalculatedforeachandeverydatapoint thereintheclusterbythehelpofEuclidiandistance.They have determined to threshold value which are lower thresholdandupperthreshold.Theupperthresholdvalueis saidto0.72andlowerthresholdvalueissetto0.28.Ifthe goingontransactionhasasuspicionscorevaluemorethan threshold value then it is as discarded from the cluster. Suspicion table contain values whose suspicion score lie between upper threshold and lower threshold. Learning takesplacewhenthesuspiciontablearefedtothemachine learning layer where SGC back propagation algorithm processes it. 5 hidden layer is used to train the network. Results keep getting better when the number of hidden layersisincreasesbutasaconsequencecomputationtime alsoincreases.Thedatasheetisdividedinto3categoriesit consistsof15%ofvalidation70%oftrainingfaceand15% oftesting.Whenthealgorithmisprocessedtheresults,we getourare93.9arecorrectclassificationtransactionsand 6.1%areincorrectlyclassifiedtransactions.Forthefuture purposetheywillbeexperimentingdifferentalgorithmsto.
transactionrecordsarecontainedbyfirstdatasitewhichis owned in September 2013 in Europe. UCSD-FICO data miningcontest2009datasetisourseconddatasetwhich contains e commerce transaction. Fivefold procedure was conductedusingtoRealworlddata.Crossvalidationprocess wasemployedtogetthereliablecomparison.Thissystem achievesAUC90.94%indataset1and92.9%indataset2. Thevalueofrecallscorewentupto40.5%indataset1and 28.3%indataset2.Butthisresultsitcanbeensuredthat fraud detection rate went up to 40%. AUC score of RF algorithmstandson2ndpositionbyachieving90.9it%and 92.8%. SVM algorithm stands on the last position as it achievesthelowestareaunderthecurvescoreof47.8%and 70.90%forthedataset1anddataset2.
In [6] order to integrate the parameters of light gradient boosting basin system hyperparameter optimization algorithm is used. This experiment was performed by the helpof2realworldpubliccreditcardtransactiondataset. This system discriminates between legitimate and fraudulent credit card transactions. The utilization to optimize parameter of light gradient boosting is the main contributionofthisresearch.IntelCorei7Processorisbeen used with 8GB RAM in this experiment techniques of machine learning are also used. 284807 credit card
-
This paper [7] gives the information about how anti knearestneighbouralgorithmcanbeusedforthedetectionof thefraud.Traditionaltechniqueandmoderntechniquesare 2commonformsofcreditcardfraud.Applicationfraud is typeoftraditionaltechniquesandinterceptfraudisatypeof moderntechnique.Thisparticularsystemusestrimoutliner detectionbasedonreversedk-nearestalgorithm.Thereare two main procedures of this algorithm which are stream managerandthequerymanager.Theincomingdatastream objectisreceivedbytheformerprocedureandthecurrent windowefficientlyupdateit.Weneedtoupdateknnlistand rknnlisttomaintaincurrentwindowperfectly.Randomdata setsizeischosenwhichincludes10,000multidimensional spacepointsdatawhichisuniformlydistributedondifferent dimensions. The pros of this proposed model were the recordoflostandstolencarfeaturesmakesithandytostop fraudulent transaction. Error detection in sequence of numbershandsdetectinvalidnumbereasilybuycreditcard validationchecks.Concludingthispaperbylettingallknow thatthenumberofscansisbeenreducedbythisalgorithmis onlyone.Theproposedmethodisefficientandeffectiveon bothsyntheticandrealdataset.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
In [8] order to experiment contacts of credit card fraud detection2differentmethodsofcalibratingprobabilityare used which aims to find the model that lessens the RealWorld loss of credit card transactions. The first method includesofadjustmentofprobabilitiesontheparametersof differenceinbadrateamongthetrainingandtestingdata sets and for the second method calibrated property are taken after the modification of receiver operating characteristic curve.BigEuropeancompanyhadprovided datasetwiththetransactionbetweenJanuary2012toJune 2013. State-of-the-art fraud system is implementing the currentversionofthesystem.Probabilityofrandomforest algorithmisusedbytheBMRbadeuseofUndersampleand training data set RF algorithm is train by doing this observationofvariouspositivebaseratesispossible.Scikit learn is implemented in order to use RF algorithm. Parameters of RF is tune in order to get good range of possibilitiesofestimates.Fortheconstructionpurposewith BMR logistic integration and decision trees also used. In ordertogetbetterresults,wefoundthatBMRmodelisused. It is observed that when BMR model is used the fraud detection rate increased as well as precision was also maintained.Savingsleadsto41.7%.LR-u-calROCCH-BMRis consideredtobebestmodelsofar.Finally,5820eurosrise inthemodel.49.26%savingagaintheoptionofcontactin everyclient.Paperisendedbysayingthatitonlybyuseof raw possibilities bayes minimum risk are performed outperformed.
Machinelearninganddeeplearningisarisingtechnologies intoday'sworld.So,thispaper[9]talksabouthowmachine learning and deep learning can be implemented in the detection of fraud transactions. The data set for this experimentwasprovidedbyKaggle.ThemodelDeusedin thisexperimentBiLSTM-MaxPooling-BiGRU-MaxPoolingis basically based on bi directional the memory and bidirectional Gate recurrent unit. Not only this day also applied some machine learning classifiers like naive base, voting, ada-boosting, random forest, decision tree and Logisticregression.Oneofthebiggestproblemstobuilda creditcardfrauddetectionsystemislackofgooddatasets. Thedatasetsarehighlyinbalanceandcontainsnotknown fields that's why data pre-processing is needed. Some evaluationmeasuresusedinthisexperimentwerecatching rate, false alarm rate Matthew’s correlation Coefficient balance classification. Best of performance is achieved by decisiontreewhichisbasedonbaggingclassifierandresults alsoshowsthatT2donotperformbetterthanOCVM.OCVM givetheaccuracyof96.6%andit's FPRis8.5%alsoitsFscore is 100%. A data set contains 569875 labelled as legitimatetransactionsontheotherhandthereare20663 transactions are fraudulent transactions. As we have a balancedatathreetechniqueshavebeenusedtoresolvethis problemSMOTEtechniquerandomoversampling,random undersampling.Bydoinghardvotingwiththehelpofunder andoversamplingtheareaunderthecurvethatweachieve is 80% and 81%. Max pooling is applied to both the
algorithms bidirectional Long short-term memory and bidirectional Gated Recurrent Units. By use of under sampling,randomoversamplingandSMOTEwasnotvery promising. Thus, it is observed that better results are achieved by using deep learning rather than machine learningmodels.Areaunderthecurvewas80%and81%by the use of hard voting when we use machine learning classifiersbyapplyingunderSamplingandoversampling.In fact our model achieves the better results than machine learningmodelwhichachievestheareaunderthecurveis equalto91.37%
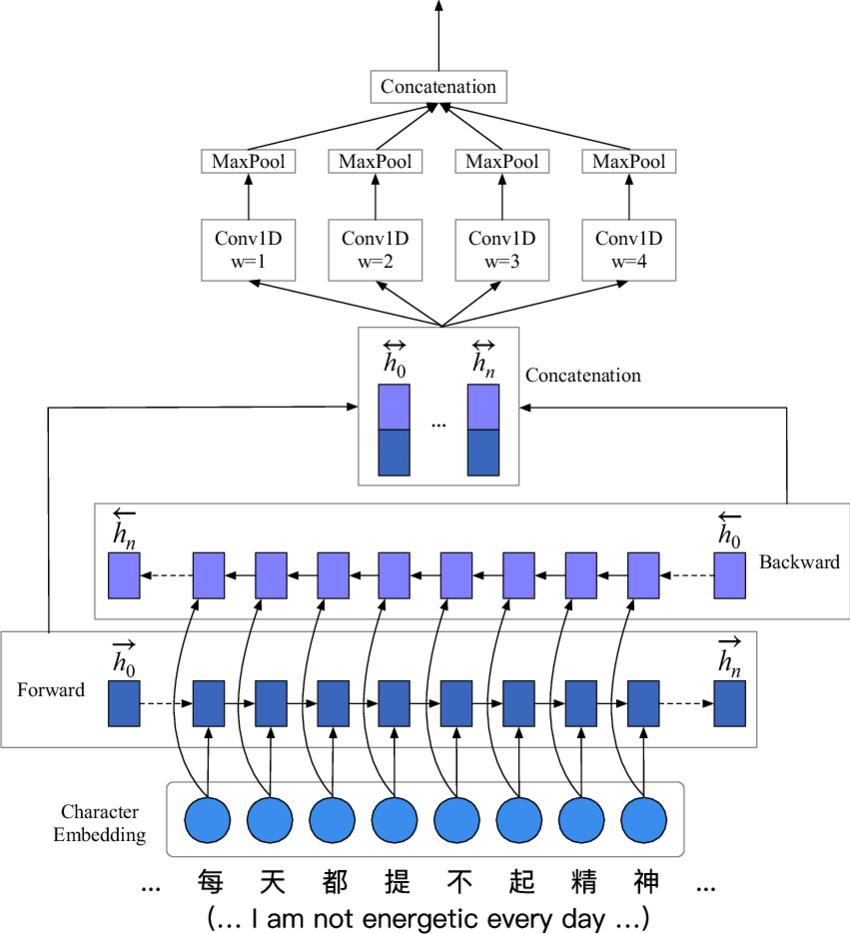
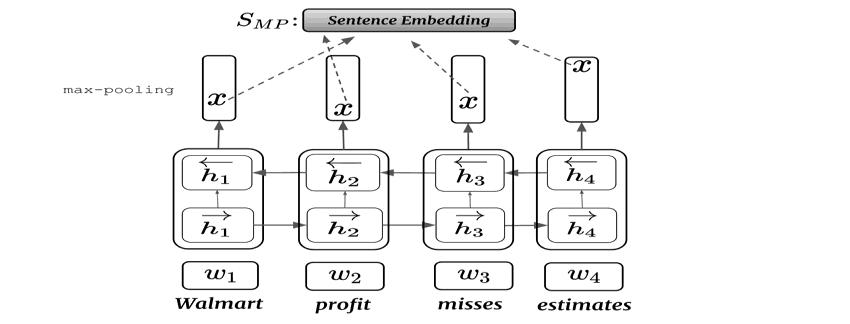
Fig - 11: BiLSTM–MaxPooling[25]
Fig - 12: BiGRU–MaxPooling[26]
AstheratioofRAWtonormaltransactionisverylesssowe should take care of the highly skewed nature of data. By doingthisexperiment[10] wecametoknowthatrandom forest gives the more accurate result to find the normal transaction while neural network is good for detecting fraudulent transactions. One 12th of one percent transactions can be identified in today’s fraud detection system.Therearetwomajorwaystofightagainstcreditcard fraudstheyarefrauddetectionandfraudprevention.Direct severalfraudpreventiontechniquesnowadaysoneofthem isOTP,bankingwebsitesprovidesecurityquestions.Inthis experimenttheyhaveuseddatawhichispubliclyaccessible. Thisdatasetcontainnumericalrecords.Inthisexperiment
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
wearegoingtokeepbestofboththealgorithmssowecan predicthighaccuracy.Nowtrainingdataconsistsof60%of normaltransactionin60%offraudulenttransactionforthe cross validation the data is divided into 20% normal transaction and 20% fraudulent transaction while for the testingpurposeforthedataisdividedinto20%ofnormal transactionand20%offraudulenttransaction.Thenforthe training of the model we will first train the feedforward neural network on the entire training data. Then we will train another feed forward neural network of 60% it of fraudulenttransactionand60%ofnormaltransactionson undersamplingtrainingdata.Thenagain,theyhavetrained same number of fraudulent transaction while half of the normaltransaction.Thenextstepwillbetrainingdatawill be trained by the random forest which consist of 300 decision trees. Same processor will be repeat again but random forest will have 400 decision trees. Then crossvalidationwillbeappliedinordertogettuningparameterof three models. The output received from the majority of classifierisusedtotestthetestingdata.Themainaimofthis experiment was to minimize be misclassification of fraudulenttransactions.
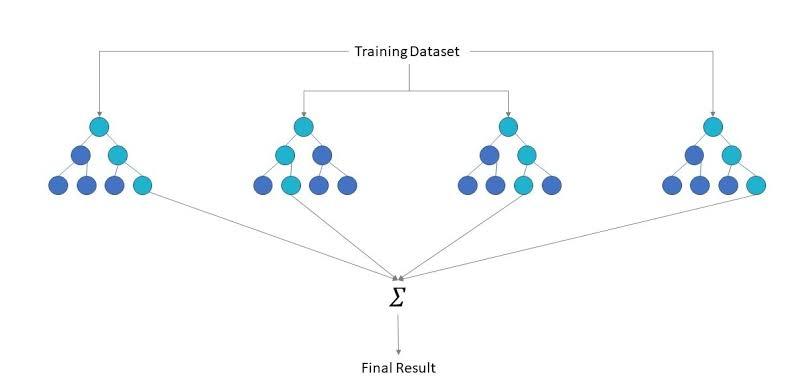
Thispaper[12]showshowclassbalancingtechniqueshelps increditcardfrauddetection.threemostpopularsolutionR data level algorithmlevel andensemblesolutions.For the purpose of balancing of majority and minority classes samplingmethodslikeoversamplingundersamplingisbeen implemented.Imbalancelearningproblemisthemajorissue which is to be solved first. Because of imbalance learning problem the ratio of finding fraudulent transaction to legitimate transaction will be very low. The system will followthisprocessfirstlyrawdataiscollectedthenthatdata ispre-process.Oncethepre-processingiscompletedthen datasetisgeneratedfromthatdata.Thedataisgiventothe over Sampling and under sampling method. On the over samplingpartSMOTE,SMOTEENN,SMOTETL,SafeSMOTE, ROS is applied on the data. On the other hand, on under samplingRUS,CNN,CNNTL,TLisapplied.Thenallthedata is combined and given to the cost-sensitive methods and ensemblemethods.On thecostsensitive methodside,the supportvectormachineandC4.5decisiontreeisappliedon thedatawhileontheensemblemethodsideAdaBoosting andbaggingisappliedondata.Theprocessdatanowgoesto the performance meter where you get the value of area under the R the ROC the curve, sensitivity, specificity, GMean.FromalloftheoversamplingmethodsSMOTEENN performance was better and also bagging use the better resultfromalltheclassifiers.Inthefollowingexperimentit is observed that sampling take lesser time then under samplingwhenapplyto the samemodel. The final results saysthatforoversamplingSMOTEENNperformbestand fortheunder-samplingTLperformbest.
Fig - 13: BasicIdeaforRandomForest[27]
Geneticalgorithmisanewtechnologynowadaysit'sameans toobtainedbettersolutionandeliminatefraudtransactions. In [11], it is discussed that how genetic algorithm can be used in purpose of fraud detection. Video Aar system is designedinawaythatfraudulentrulesetsaregiventothe systemthenruleengineisappliedinwhichdatasetsisgiven fromthatstepthenwemovetothenextstepwherefieldand priority are given then the process data is given to the geneticalgorithm.Thisspecificsystemisbuiltintheapplet vieweruserinterfacemodule.
Intoday'sworldmakingonlinefraudtransactionisbecame very easy. In order to stop them this paper [13] has implementeddeeplearningmethodologieswhichareautoencoder and restricted Boltzmann machine. Fraudster continuouslychangetheirfraudpatternsinordertonotget detected.Sowehavetochangethemediumfromofflineto online fraud transaction detection using unsupervised learning.AE, RBM, H2O is used from the Google by deep learning. Three data sets were used which were from Germany, Australia, and Europe. For the calculation of nearest point KNN was used. Autoencoder is used for the detectionoffraud.Inordertoencodeanddecodetheoutput and input they have used the hyperbolic function. After doing all the calculations the auto-encoder give the area under the curve up to 0.9603 on the European data set whichissuitableforlargedatasetsontheotherhandwhen auto-encoderandBoltzmannwasappliedonAustralianand Germandatasetstheresultswerenotasexpectedsowecan concludethatworkonbigdatasetswellandfineanddonot workwellonsmalldatasets.
Fig -
Thispaper[14]tellsusabouthowCatboostingandLight GradientBoostingMachine (LGBM)canbeusedforcredit cardfrauddetection.Theyhadcomparedtheperformanceof Auto-Encoder(AE),K-meansclustering,LogisticRegression andNeuralNetwork(NN)vsCatboostingandLightGradient
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072
BoostingMachine(LGBM).Incatboostingparametertuning isnotneededanditcanberunonthedefault’sparameters. It does not require the conversion of categorical data to numericaldata.basicbenefitofusinggradientboostingisit increase the accuracy and minimize the overfitting rate. LGBMisbasedondecisiontreesandclassificationofmodel maximized also reduce the usage of memory. Synthetic MinorityOverSampling(SMOTE),LogisticRegressionand AEallhavelowamountofrecallscoresandlessamountof robustness as it takes more time to compute and its inappropriatefortheimbalancedata.Afterimplementation itisobservedthatCatBoostisbestforintermofaccuracy and in case of large datasets LGBM is better suits. LGBM performbestamongallofthemandachievedtheaccuracy score of 99% while NN, Logistic Regression, AE, K-Means clustering,CatBoostscores96%,77%,96%,93%,98%
Asperthereferenceofthe[6]and[15],Ourproposemodel use Light Gradient Boosting Machine Learning (LGBM) as per the [6] and [15] perform far better than the other algorithms.OursystemcomparestheXGBoosting,SMOTE, Light Gradient Boosting and finds the transactions are legitimateorfraudulentasshowninfigure.
Step 3: Providing training data to XGBOOSTING, SMOTE, LGBMtobuiltamodel.
Step 4: Comparingusingtestingdatawhichperformbetter.
Technology growth is directly proposal to the growth of CreditCardFrauds.Asforthefutureworkwecanapplydeep learningtechniquesfordetectingfraudulenttransactionsas deeplearningiscapableofmakingmorepowerfulmodelas comparetomachinelearning.
[1] Stolfo,S.,Fan,D.W.,Lee,W.,Prodromidis,A.,&Chan,P. (1997, July). Credit card fraud detection using metalearning:Issuesandinitialresults.In AAAI-97Workshop onFraudDetectionandRiskManagement (pp.83-90).M. Young, The Technical Writer’s Handbook. Mill Valley, CA:UniversityScience,1989.
[2] Fu, K., Cheng, D., Tu, Y., & Zhang, L. (2016, October). Creditcardfrauddetectionusingconvolutionalneural networks. In International conference on neural informationprocessing (pp.483-490).Springer,Cham.K. Elissa,“Titleofpaperifknown,”unpublished.
[3] Aleskerov, E., Freisleben, B., & Rao, B. (1997, March). Cardwatch: A neural network based database mining systemforcreditcardfrauddetection.In Proceedingsof the IEEE/IAFE 1997 computational intelligence for financial engineering (CIFEr) (pp.220-226).IEEE.
[4] Zeager,M.F.,Sridhar,A.,Fogal,N.,Adams,S.,Brown,D. E.,&Beling,P.A.(2017,April).Adversariallearningin credit card fraud detection. In 2017 Systems and Information Engineering Design Symposium (SIEDS) (pp.112-116).IEEE.
[5] Behera, T. K., & Panigrahi, S. (2015, May). Credit card fraud detection: a hybrid approach using fuzzy clustering & neural network. In 2015 second internationalconferenceonadvancesincomputingand communicationengineering(pp.494-499).IEEE.
[6] Taha, A. A., & Malebary, S. J. (2020). An intelligent approach to credit card fraud detection using an optimizedlightgradientboostingmachine.IEEEAccess, 8,25579-25587.
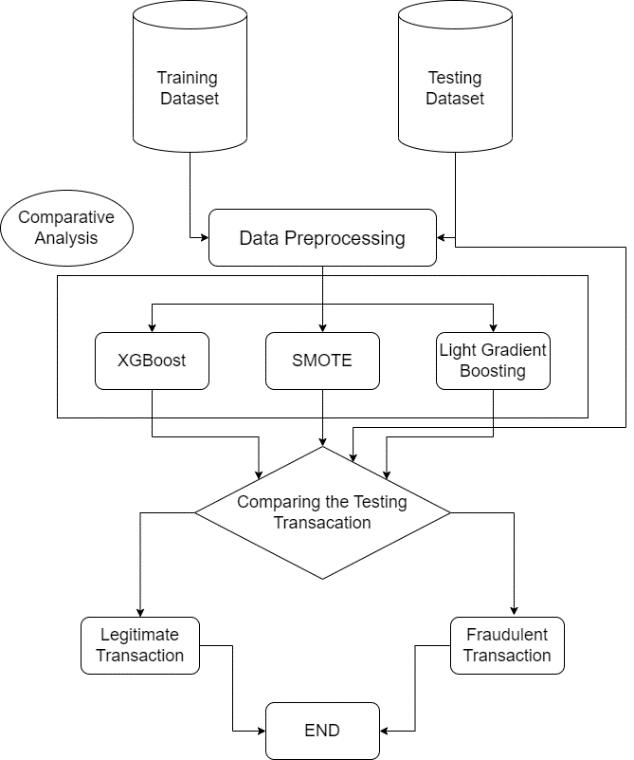
Step 1: TakingtheDatasets anddivideitintothetraining andtestingsets.
Step 2: Thendataispre-processedinordertogetrequired features.
[7] Ganji,V.R.,&Mannem,S.N.P.(2012).Creditcardfraud detection using anti-k nearest neighbor algorithm. InternationalJournalonComputerScienceand Engineering, 4(6),1035-1039.
[8] Bahnsen,A.C.,Stojanovic,A.,Aouada,D.,&Ottersten,B. (2014, April). Improving credit card fraud detection withcalibratedprobabilities.In Proceedingsofthe2014
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

SIAM international conference on data mining (pp.677685).SocietyforIndustrialandAppliedMathematics.
[9] Najadat,H.,Altiti,O.,Aqouleh,A.A.,&Younes,M.(2020, April).Creditcardfrauddetectionbasedonmachineand deeplearning.In 2020 11th InternationalConference on Information and Communication Systems (ICICS) (pp. 204-208).IEEE
[10] Sohony, I., Pratap, R., & Nambiar, U. (2018, January). Ensemble learning for credit card fraud detection. In Proceedings of the ACM India Joint International ConferenceonDataScienceandManagementofData (pp. 289-294).
[11] RamaKalyani,K.,&UmaDevi,D.(2012).Frauddetection of credit card payment system by genetic algorithm. International Journal of Scientific & Engineering Research, 3(7),1-6.
[12] Sisodia, D. S., Reddy, N. K., & Bhandari, S. (2017, September).Performanceevaluationofclassbalancing techniquesforcreditcardfrauddetection.In 2017IEEE International Conference on Power, Control, Signals and Instrumentation Engineering (ICPCSI) (pp.2747-2752). IEEE.
[13] Pumsirirat, A., & Liu, Y. (2018). Credit card fraud detection using deep learning based on auto-encoder andrestrictedboltzmannmachine. InternationalJournal of advanced computer science and applications, 9(1).
[14] A.A.TahaandS.J.Malebary,"AnIntelligentApproachto CreditCardFraudDetectionUsinganOptimizedLight GradientBoostingMachine,"inIEEEAccess,vol.8,pp. 25579-25587,2020.
[15] AI Journey https://ai-journey.com/wpcontent/uploads/2019/06/fraud-EMV-chip-creditcard.jpg
[16] Data Aspirant https://dataaspirant.com/wpcontent/uploads/2020/09/1-Credit-card-frauddetection-with-classification-algorithms.png
[17] Vortarus https://vortarus.com/wpcontent/uploads/2018/12/simulation-diagram.png
[18] Malicksarr https://www.malicksarr.com/wpcontent/uploads/2021/06/Deep-LearningDefinition.png.jpg
[19] Code Ground https://cdn.codeground.org/nsr/images/img/blogthumb23.jpg
[20] Ecognition https://docs.ecognition.com/Resources/Images/ECogU sr/UG_CNN_scheme.png
Volume: 09 Issue: 11 | Nov 2022 www.irjet.net p-ISSN:2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page781
[21] Medium https://miro.medium.com/proxy/1*8FhisenG1AsVvMxRpVYZg.png
[22] Digital Transformation Pro https://digitaltransformationpro.com/wpcontent/uploads/2017/06/Datamining-1024x576.png
[23] Els-cdnhttps://ars.els-cdn.com/content/image/1-s2.0S0010482505000417-gr4.jpg
[24] Research Gate https://www.researchgate.net/publication/345040132 /figure/fig1/AS:952564933750788@1604120586852/ The-proposed-approach-for-Android-malwareclassification_Q320.jpg
[25] Research Gate https://www.researchgate.net/publication/330008974 /figure/fig4/AS:709745916776451@1546228021348/ BiLSTM-max-pooling-The-network-performs-a-pollingoperation-on-top-of-each-word-hidden.ppm
[26] Research Gate https://www.researchgate.net/profile/WenpengLu/publication/331459358/figure/fig3/AS:850162641 534980@1579705977589/Network-architecture-ofBiGRU-CNN.png
[27] IBMhttps://1.cms.s81c.com/sites/default/files/202012-07/Random%20Forest%20Diagram.jpg
[28] edu CDA https://cdn.educba.com/academy/wpcontent/uploads/2019/09/What-is-GeneticAlgorithm.png