International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072
1Dept. Of Computer Science, Karnataka State Akkamahadevi Women’s University, Vijayapur. 2PG Scholar, Karnataka State Akkamahadevi Women’s University, Vijayapur ***
Abstract:-
The phrase "ransomware" or "malevolent computing" refers to unique or unfortunate programming. Malware can be arranged by its motivation into various classes. PC infections, deliver product, Some of the most wellknown forms of malware include espionage, grubs, bloatware, and misrepresentations. Antivirus can be used to disrupt computer operations, gather sensitive data, or access a private computer device. In secrecy mode for malware intended to take data about PC users or spies have been doing so for a long time despite customers knowledge. Keyloggers programme development is fundamentally distinct from other evil initiatives that involve ransomware and perhaps other types of computer viruses everywhere. Order is additionally fundamental for the turn of events and execution of the fitting programming patch to close the weakness of the program. We advise measuring the inspection at how software is typically disturbed and recommending the differentiating substantiation of URL contamination in light of the handle of common language The Internet URL is comparable to one of the prose messages which may be sorted using standard phonological awareness. The organisation channel for ransomwareonURListhenrecognisedusingthen-gram technique. The next step is to choose the computer categorizationperspectivebasedonthemarkovChain,a computational vulnerability assessment process. The paper discusses extensive field writings and demonstrates why Nicely is a reliable and successful method for classifying and identifying transformational infections.

Keywords: Malware location, Malware review, NLP Method,designcoordinating
The rise of new correspondence advancements has shown a huge impact on corporate improvement just as advancement which has filled in different applications like internet banking, online business, and informal communication. In all actuality, having an operational existence is practically basic for running a fruitful endeavor at the present age. Subsequently, the meaning of the World The Rest Of The internet keeps creating. Ironically, improvement is caused by new, sophisticated methods for avoiding hazards and deceiving others
These occurrences incorporate dissident locales selling imitationitems,as
money related blackmail, perhaps cash or unmistakable verificationoftheft,
or on the other hand presenting malware on client's contraption by constraining clients to uncover tricky data.
Computerized attacks similarly as Ransom ware ransomware attacks are incredibly common in today's technologically advanced environment, and distinguishing these unlawful activities has now turned into a huge test in the computerized crime location examination field. High level contraptions are significantly disposed to malware attacks and the quick Web rapidly enables their feast. Computer virus is the hazardous software designed to intentionally harm computers,cellularphones,orsocialnetworks.Different programs can gain passwords from either the host computer and transfer it back to the attackers outside theirconsent.
Malware assaults are between the most limit types of digital assaults on organizations, organizations or people. Contamination with malware can make broad harm and annihilation the information put away in PC frameworks. The various types of viruses include invasions, software, Ransom Braid, keyloggers, code name, exit stream merchandise, trojan horses, worms, and Key Woodsman. According to GDATA Platform's measured analysis from 2017, a viruses and worms instanceissuppliedevery4.2milliseconds.
InexcessIntheopeningquartierof2018alone,AV-Test, a renowned testing group for anti-malware products, discovered 20 million new malware tests. ten years, in accordance with the Atrioventricular assessment. Ransomware localisation and prevention having emerged as valuable data assurance scientific disciplines. Malware analysis is done to discover fresh ransomware marks and their behaviour in order to prevent contamination and data breaches. In this study, wediscussandexplorevariousexplorationprojectsthat use the Hidden Markov Model in the heuristic space examinationandnoxiousprogrammingarrangement.
Typical language elements are evaluated at various levelsoflinguisticstudy in a processknownasfrequent
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page690
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072
machine translation (NLP). lexical, physical properties, industrial,cultural,intellectual,phonology,andspeaking characteristicsof phrase. Then,at thatpoint itturnsout tobemoreunpredictableanddifficulttolessen theNLP handling stock. The exploration space of the NLP has been significant in the advancement of frameworks. A significant number of the submissions in various fields depend on NLP tools that consider massive amounts of content and discourse preparation of data. Operations that involve acquiring It takes time and money to use NLPapproachesin theseenvironmentsto enhancedata, correct mistakes, and make judgments using that information.
EngineersarealsoendorsingNLPtechniquestoevaluate andgatherdatafromnumeroussources.Themajorityof NLPfeaturesaretypicallyusedinlargeframeworksand submissions, such as estimation analysis, speech recognition, information mining, and word preparing. Consequently, in the time of web administrations, NLP stages offer a decent wide scope of fundamental and progressed NLP includes that provisions the user interface design interface (API) for online submission. The connection among administrations and outer constructions is made simpler by covering the interior idea of such APIs. Designers can in any case utilize innovation to make a NLP program, as opposed to makingtheentiretyofthesubmissioncapacities.
The Internet streamer specification is intended to receive relevant information through the N:gram age section.Todothis,theN:grammaturitylevelsubsystem converts each oncoming language set (obtained via a streamer split) into an N-gram aggregation. As illustrationsoftranslatingwordmixturesofsourcesinto N:gram components. The furthest left segment is the underlyingwordsuccession,addressingastreamineach column.Asequenceamongthesetermstotals1gramme. The centre and farthest right portions of each connection's generating word set are known as n-gram repeated units. If N is equal to 2, the topmost layer communicationsthe progressionof 2 grammes,andif N seems to be 3, the farthest top portion expresses the combinationof3grammes.
To give you an idea, the broadcast 1 meta description reads "apikey air pushapp id60563coordinate system 0," and its 1-gram placement is identical to the foundational excellent selection, but its 2-gram progression is "(apikey airpush)(air pushappid)(appid 60563)..." and its 3-gram adjustment is "(apikeyairpushappid)(airpushappid 60563)." The N:gram integrates analytical information to obtain significant term groupings. For particular, we can infer thatthereisn'tobviouslinkseenbetweenconceptsfrom the 1 gramme "apikey" or "airpush" configurations of course of its existence in addition to understanding the significance of a single word as presented It is most
likely visible from either the entire sample period "(apikeyairpush)" 2-gram configurations that such existence of "airpush" is influenced by "apikey." The principleofkeywordintroductionintheHTTPstreamer top corner is addressed, making measurement of the N senseofworthoftheutmostimportance
Creative utilizations of AI have stayed seen in network safetylately[1]-[3].Theytendedtootherdigitaldangers, and gave no consideration to identifying malevolent URLs. For instance,[3] presents an examination on the utilizationofAIwithinformationdiggingframeworksfor the identification of network protection interruption. Overviews use AI to noxiously recognize URLs however are restricted to a rundown or area. For instance, in 2007 [4] a trial investigation of different AI techniques for recognizing malignant URL was played out, the usefulness or AI In speaking, no prototypes with this subject were investigated. [5], [6] provided a detailed explanation of online fraud and related problems but omitted to include components announcements or engagement computations. [7] Its fundamental spotlight isonmalignantURLlocationwithincludedetermination.
The acknowledgment of dangerous URLs is solidly associated with various solicitations, for instance, spam ID. 8] In 2012, Various types of spammer (substance junk mail, enlistment malicious code, timeliness and redirectedinappropriatecontent,andbombard)andthe tactics employed to combat them were described in a competent audit that was completed. They are also referred to as spammy area related buzz (performing corresponding data from a variety URLs), composition predicated spammer revelations approaches (to use syllable bundles as well as specific linguistic handling approaches), and development of methods. Spam acknowledgment relies upon the use of ordinary language taking care of for planning text and examination in an emailIf certain methods aren't employed to depict the Urls as that stands, it won't be evident that hacking is being revealed. Spam disclosure methodologiesthatusageintermittent based features to conclude poisonous URLs will undoubtedly qualify, despiteafewcoveringbetweenspamrecognizableproof and techniques used for malevolent URL affirmation. Certainnewexaminationsetupinvestigationsregarding spam disclosure integrate [ 9]-[11], a critical number of whichcenteraroundonlinespam.
In publications containing a location containing a comparablesubclassofpathogen,expressingsimilarities are utilized to investigate equivalency. Certain portions of this book are appropriate for the situation at hand, especially when lead isn't taken into account. Clustered the ransomware is an idea put out by Lee and others. The problem of determining frequency integration
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072
various ransomware in this method is quite significant forinstrumentinteractions Insubsequentstudy(Spiegel et al., 2010), Pharma et al adopted the quicker nearest neighbours analysis, applying careful hashing for relationship evaluation statistics with swiftly constructed straightforward profiling (works with used data legitimate strategies to screen device call). The different evened out gathering estimation is used reliably for lead analyzes. The expected benefits in precision and memory are 0.98 and 0.93, respectively, based on the connection between groups and true infected bunches. The plan strategy utilised by Rieck et al.(2008)wasusedbySVMs(Riecketal.,2008)tosetup innovativemaliciousfamilymembersthatdidn'tinvolve theaccumulationofvirusesandwormsexperienceswith households. This antivirus model was constructed throughout the arrangements and that it will ultimately beutilisedtocollectantivirusaccusations
The assessments for such inspection are closely monitored, comprising 33000 summaries and then a careful review of system performance. F-scores for variousMaleharperformancebuncheswerearound0.95 and 0.97. Their prior work often discusses ransomware collection svm classification computers, and leadership breaches in friendlier monitoring were looked at to handle influence the company Additionally, creators provide a different illustration for something like the controlling dissemination of virus (Trininus and others, 2010). This essay is excellent for incorporating data mining and cognitive computing to useful tasks. Vazner andco.(Wazeretal.,2008)proposeacomplexindicative procedure wherein they are used to assess likenesses during the time spent change of the plan of couples and to manhandle the distances of Hai linger. We also demonstrate how the work piece material is supported by phylogenetically. Spiegel et al. (2009) made an effort at another obscure regulation that was used to the generation of this kind of ransomware. The 3-gram report substances or a roughly similar component employed on the Distance measure are generally maintainedinongoingeffortsorsummarisedexpansions tree branches In order to quantify the resemblance of commitments from NFS continues for limit structures, Neeraja et al. (Yadwadkar et al., 2010) applied the PHMMtotheinstructiongroupsoftheNFSaccompanies. They also observe comparatively few planning developments, which is acceptable for showcasing and foraspecifickindofaccountability.Geeprofile,awidely accessible contaminant unit, was used for the x86 apocode new advancements of parametric pathogen couplings developed with another work (Attalouri and others, 2009). However, due to problems with code transmission and procedure modification, they discover thatall thisapproachonlyperformsfora select number ofexceptionalhouseholds
Man-made intelligence Strategies try to survey a URL anditsassociatedlocalesorsitepages,trytobereadyas a model for malignant and chivalrous URL planning by encouraging the productive included depictions and getting ready of URLs. Two property structures fixed features, and dynamic properties. Humans perform browser analysis in a predetermined analysis while interpretingtheURL(forexample,invokingJavaScriptor other code). Output signals combine the Website list, contain data and occasionally language from Encoding and Actionscript contents. Such theories are preferable to functional components since they do not require processing. The key presumption is that the above phrases are delivered unusually as contrasting to dangerous and liberal URLs, which is something that cannot be avoided. This migration knowledge has the potential to create a phased rollout that anticipates incomingURLs.
By spread over man-made intelligence systems, stable expressive procedures have been extensively dissected, in light of the fact that they have an overall safe environment for getting significant information and a large number of risks (not just the standard strategies perceived by an imprint). In this examination, it is an immense achievement to focus in fundamentally on the static assessment systems used inside power-driven erudition. Interactive assessment strategies monitor the actions of probable reversal interconnections and investigate any lingering situations. That incorporate monitored machines call conditions for outstanding direct, and it is a mine Broadband internet log knowledge for dubious activities. Interactive evaluation techniques have quite a history of failure, and they are challengingtoimplementandnormalise
Recognizing evidence virus is a straightforward and commonapproachtodetectharmfulURLsthatroutinely fails to include the potentially threat URLs. Right when one more URL is gotten to, a chase of the informational collectionwillbemade. Awarningmightevenbeissued if a URL is on the firewall displayed because it is perceived as hazardous; otherwise, it would be considered low - risk. Since new URLs can be made consistently, considering the way that blackies can't see new risks, blacklists involvement the evil impacts of the inability to manage a full summary of each and every poisonous Url. While creating new computations for URLs, the aggressors will stay away from all blacklists. Due to their simplicity and adaptability, they may be among the most often used techniques in today's anticontamination programmes despite the substantial
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072
environmental difficulties. There is no quarantine, yet therearemanymalwaretypes.URLstatistics
input: The source text document yield: The encoded stream
inputstring=readsourcetextrecord include=numberofgramsintheinputstringwhile���������� ≥5do
Get the first five grammes of the inputstring with st5; detectwithdocumentation(st5,fivegrammedict) if����������≥0then,atthatpoint
power four gram compression(st4) outputstring += compress(index, 5) erase initial five grams of the inputstringtally−=5
endelse
Inthisanalysis,welookatstate-of-the-artcomputational machinelearning that are employed and documented in physicalcopytoidentifymaliciousURLs.Wespecifically concentrate about donations generated locally for the developmentofproductandtheknowledgeestimations. For this task, we intentionally request different brand name depictions used to fabricate planning data and portray a couple of learning computations which can be usedtoacquirecapabilitywitha fairassumptionmodel. We settled requests of transparency, and we perceived streetsforfutureassessment.Additionally,wediscussed a diverse variety of statistical and artificial intelligencebased techniques using for group harmful URLs in the remaining surveyed mailing lists. In this evaluation, we examine state-of-the-art computational intellectual abilitytechniquesthatweredeployedandmaintainedin printed version to recognise malicious URLs. We base unequivocallyongiftsmadearoundhereforthecreation oftheapplicationandthelearningcomputation.Forthis endeavor, we purposely bunch different brand name depictionsusedtoconstructplanningdataandrequesta couple of learning estimations which can be used to get to know a respectable assumption model. We answered inquiries for availability, then we identified neighborhoods for further research. Additionally, we discussedavarietyofstatisticalandartificialapplication domainswasusingtoarrangeharmful URLsthroughout theremainingframeworkregistries
AoriginaltextdocumentwasprocessedusinganN:gram extractor, which was then used to separate it into newline-based paragraphs and obtain the number of grammesconnectedtothepressurizedunitsyielding.
st4+=getfirstgramoftheinputstringerasefirstgramof theinputstringcheck−=1 assuming number of grams of st4 = 4, four gram compression(st4) end if����������>0then,atthatpoint end end fourgramcompression(inputstring) end
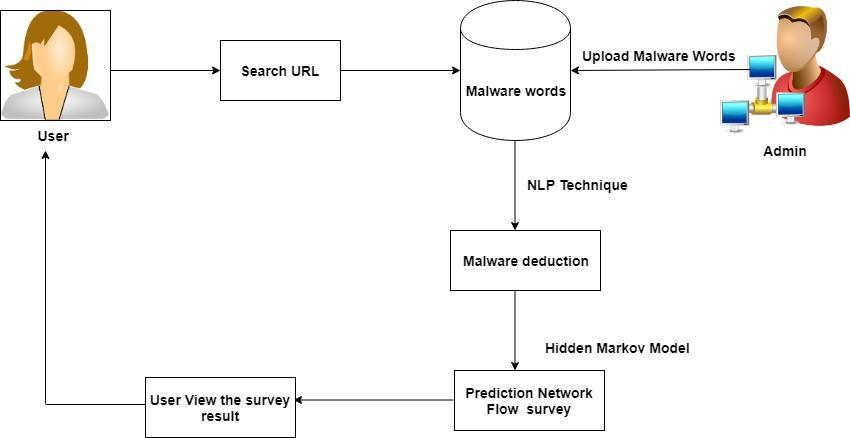
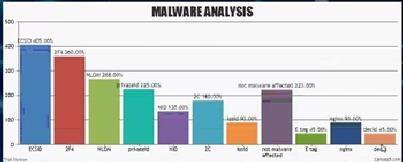
Thenameofafewmalwareisdistinguishedthroughthe url.ThenameofMalwared isorderedandthevolumeof trafficstreaminthatspecificmalwareexists.Weneedto utilizetheNLPphilosophy.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 10 | Oct 2022 www.irjet.net p-ISSN: 2395-0072
Numerous computations were used in the assessment method. We need to assess in which calculation the outcomeMalwaretechnologyhasimproved.Inaddition, the NLP Algorithm is provided the proper accuracy for malwareanalysis.
Communication Engineering, vol. 2, no. 11, pp. 4349–4355,2013.
[2] S.DuaandX.Du,DataminingandAIinnetwork safety.CRCpress,2016.
[3] A. L. Buczak and E. Guven, "A review of information mining and AI strategies for network protection interruption identification," IEEE CommunicationsSurveysandTutorials,vol.18,no.2,pp. 1153–1176,2016.
[4] "A correlation of AI techniques for phishing location," in Proceedings of the anti phishing working sessions, by S. Abu-Nimeh, D. Nappa, X. Wang, and S. Nair.secondyearlyeCrimescientistshighestpoint.ACM, 2007,pp.60–69.
[5] D. R. Patil and J. Patil, "Review on pernicious website pages identification procedures," International Journal of u-and e-Service, Science and Technology, vol. 8,no.5,pp.195–206,2015.



In various computerized submissions, harmful URL affirmationexpectsahugepart,andartificialintelligence measures give off an impression of being a respectable look. In this piece we used artificial intelligence strategies to play out a cautious and purposeful outline on harmful URL ID. We especially displayed hazardous URLconfirmationasarequiresgoodfromtheviewpoint of intelligent machines, researched emerging judgements for hazardous URL reassurance, especially new types of characterisation establishment, and made neweducationroughestimatesfordeleteriousdefensive strategy Website address public acknowledgement processes..Most of all, in this outline, we requested existing works recorded as a hard copy for dangerous URL recognizing verification and perceived the fundamental guidelines and troubles expected to encourage malignant URL distinguishing proof as a help for Certifiable Digital Submissions Based mostly on keyloggers evaluation, we really like to predict URL keyloggers in Upcoming years Upgrades, and we desire toperformthethoroughinspectionaswell
[1] J. Singh and M. J. Nene, "A study on AI methods for interruption location frameworks," International Journal of Advanced Research in Computer and
[6] M. Khonji, Y. Iraqi, and A. Jones, "Phishing identification: a writing review," IEEE Communications Surveys and Tutorials, vol. 15, no. 4, pp. 2091–2121, 2013.
[7] H. Zuhair, A. Selamat, and M. Salleh, "Highlight determination for phishing recognition: an audit of exploration,"InternationalJournalofIntelligentSystems Technologies and Applications, vol. 15, no. 2, pp. 147–162,2016.
[8] W. Enck et al., “TaintDroid: An information-flow tracking system for realtime privacy monitoring on smartphones,”ACMTrans.Comput.Syst.,vol.32,no.2,p. 5,Jun.2014.
[9] M. Egele, T. Scholte, E. Kirda, and C. Kruegel, “A survey on automated dynamic malware-analysis techniquesandtools,”ACM Comput.Surv.,vol.44, no.2, pp.1–42,2012.
[10] S. Hong, R. Baykov, L. Xu, S. Nadimpalli, and G. Gu, “TowardsSDN-definedprogrammableBYOD(bringyour owndevice)security,”inProc.Netw.Distrib.Syst.Secur. Symp.(NDSS),2016,pp.1–15