Examining the emerging threat of Phishing and DDoS attacks using Machine Learning models.
Mohammed Zaid M S, Namratha N, Yashaswini B V,Under Graduate Student, Dept. of Information Science and Engineering, BNMIT, Bengaluru, Karnataka, India

Under Graduate Student, Dept. of Information Science and Engineering, BNMIT, Bengaluru Karnataka, India
Assistant Professor, Dept. of Information Science and Engineering, BNMIT, Bengaluru, Karnataka, India ***
Abstract - The usage of mobile devices in recent years has resulted in a considerable shift towards executing real-world activities in the digital arena. Although this has rendered our lives easier, it has additionallyculminatedincountlesssecurity breaches owing to the internet's anonymity. Although antivirus software and systems for firewalls can prevent most attacks, experienced attackers frequently take advantage of computer users' vulnerabilities by impersonating popular banking, networking, e-commerce,andotherwebsitesinorder to steal private data such as user IDs, passwords, account numbers, credit card numbers, along with more. This emphasizes the importance of increasing knowledge and precaution when using the internet in order to protect oneself from cyber-attacks.
Phishing is a social engineering technique used to deceive users into disclosing sensitive information, such as login credentials, credit card details, and personal identification. Distributed Denial of Service (DDoS) attacks are a common type of cyber-attack that aims to disrupt the availability of online services by overwhelming the targeted systems with a high volume of traffic. Phishing and DDoS attacks are two common cyber-attack types that aim to deceive users and disrupt online services. Phishing involves tricking individuals into revealing sensitive information, while DDoS involves overwhelming a website or network with traffic. Detecting these attacks is a complex task, and various methods have been proposed, including rule-based detection, blacklists, and anomaly-based detection. Machine learning-based anomaly detection has gained popularity due to its dynamic nature in catching "zero-day" attacks. To address the problem of phishing, which costs internet users significant amounts of money annually, a system that employs machine learning techniques such as logistic regression, decision tree, k-nearest neighbors, naive Bayes, random forest, and support vector classification is proposed. These algorithms predict outcomes based on user input parameters extracted from the front end.
Key Words: Logistic Regression, Cyber-security, Phishing, Machine Learning, DDoS, Random Forest, Support Vector Machine, Decision Tree, K Nearest Neighbor, XGBoost
1. INTRODUCTION
CyberattackerscommonlyusephishingandDDoSattacksto gainunauthorizedaccesstosensitiveinformationordisrupt online services. Phishing attacks are a tactic that tricks individualsintorevealingconfidentialinformationsuchas login credentials, credit card details, or personal information. Attackers accomplish this by sending fraudulentmessagesoremailsthatappeartooriginatefrom legitimatesourcesbutareinfactfraudulent.Theattacker's objectiveistolurethevictimintoclickingalinkoropening anattachmentthatinstallsmalwareordirectsthemtoafake website where they will unwittingly divulge sensitive information.
Phishing attacks are designed to trick individuals into providing sensitive information, such as usernames and passwords, credit card numbers, or other personal information. This is typically done by sending emails or messagesthatappeartobefromalegitimatesource,butare actually from a fake or spoofed source. The goal of the attacker is to trick the victim into clicking on a link or opening an attachment that will then install malware on theirdeviceordirectthemtoafakewebsitewheretheywill entertheirsensitiveinformation.
DDoSattacks,ontheotherhand,aredesignedtooverwhelm a website or network with traffic, making it difficult or impossible for legitimate users to access the services providedbythetargetedorganization.Thisistypicallydone by using a network of compromised devices, such as computersorInternetofThings(IoT)devices,tofloodthe targetwithrequestsordata.
Individualsandorganisationscansuffercatastrophiceffects resultingfromphishingandDDoSassaults.Theseassaults can harm a company's brand and result in judicial or economic losses, in addition to the possible theft of confidentialdataortheinterruptionofservices.Asaresult, itiscriticaltobeawareofthedangerspresentedbythese sortsofassaultsandtotakeprecautionstoprotectyourself andyourorganisationfromthem.
1.1 Background
Individualsandcompanieshavebenefitedgreatlyfromthe growingusageofinternet-basedtoolsinallsectorsoflife. However,thishasresultedinsignificantgapsindatasafety, withcyberassaultsemergingasanewhazardtopersonsand organizations. As a result, effective counter-measures to such assaults have become critical. Phishing is a sort of maliciousassaultthatusesinternetthefttoobtainauser's sensitive information. It is an illegal act in which an unauthorized user seeks to gain the user's sensitive information by trapping the user. A distributed denial of service(DDoS)ofService)assaultisasortofcyber-attackin whichseveralhackedcomputersfloodaspecificserveror networkwithtraffic,overloadingitandcausingittocrash.
1.2 Problem Statement
PhishingandDDoSassaultsaretwoofthemostcommonand crucial forms of cyber-attacks, costing organizations considerable financial and intangible damages [18][19]. While there is no one solution that can fully mitigate all vulnerabilities, research has concentrated on creating detectionandpredictionstrategiestolessentheimpactof DDoS assaults [18][19]. To fight against these threats, organizationsmustdeploysecuritymeasuresandremainup tospeedonthenewestresearch.
1.3 Objective
Themajorgoalofthisresearcharticleistousealgorithms andmethodsbasedonmachinelearningtoinvestigatethe rising issue of phishing combined DDoS assaults. The project's goal is to forecast such assaults using several factorsretrievedfromthewebsiteURLgivenbytheuseron thefrontend.Thearticlealsointendstosafeguarddatafrom unauthorized access, prevent cash laundering and embezzlement,protectpropertyrights,giveamoresecure solution,enhancemachinelearningforbestoutcomes,and useefficientalgorithmstocombatrisingcybercrime.
1.4 Contributions
This study adds to the current literature on detecting phishing and DDoS assaults using machine learning approaches. The research provides a comprehensive examination of numerous algorithms for predicting such assaultsbasedonvariouscriteria,includingLR,KNN,SVC,a RandomForest,DecisionTree,andNaveBayes.Byproperly recognizing and mitigating these assaults, the suggested methodologycanassisttoreducethefinancialandintangible damagescausedbythem.[20]
1.5 Structure
The rest of this research study is structured as follows. Section2givesathoroughexaminationofrelevantworkin theareasofphishingaswellasDDoSassaults.Theapproach
for predicting these assaults using machine learning techniques, encompassing the dataset and feature engineering,ispresentedinSection3.Section4detailsthe proposedmodel'sexperimentalsetupandfindings,including efficiency assessment as well as contrast with existing methodologies.Section5discussesthefindings,limits,and future work in depth, including potential expansions and enhancementstothesuggestedstructure.Finally,Section6 summarizes the study paper's results as well as the repercussionsforsubsequentstudiesinthisfield.
1.6 Importance of the study:
ThestudyseekstoforecastPhishingandDDoSassaultsusing machine learning strategies, which is critical given the increasingfrequencyofcyber-attacksinthelastdecade.The studyalsoseekstosafeguarddata,preventfinancialfraud, and create a more robust security solution to combat cybercrime.[19] The research will shed light on the efficiencyofdifferentalgorithmsandstrategiesfordetecting and preventing cyber-attacks, allowing individuals and organizationstoreducetheirlikelihoodofsuchassaults.[18]
1.7 Scope of the study:

Thestudy'sscopeistoforecastPhishingandDDoSassaults usingmachinelearningtechniquessuchasLR,KNN,SVC,RF, DT, and NaiveBayes. The project intends to identify and preventcyber-attacksbyextractingseveralparametersfrom thewebsiteURLgivenbytheuseronthefrontend.[3][5]. The study's scope also covers data safety, combating financial fraud and embezzlement, intellectual property protection, and designing efficient algorithms to enhance machinelearningforbestresults.
2. LITERATURE SURVEY
2.1 Phishing
2.1.1 The authors of the research [1] offer a method for discovering banned URLs / fraudulent websites using a phishing detection system.[17] When users attempt to accesssuchwebsites,thesystemharvestsblacklistedURLs straightfromtheirbrowserandalertsthemviapop-upsor emails.Toprotectconsumersfrombeingduped,thesystem employsseveralelementssuchaswebsiteverificationand identity.
2.1.2 The study [2] proposes a machine learning-based approach for identifying phishing attacks. The authors provided kaggle.com ML algorithms standard datasets of phishing attacks. Two well-known machine learning approaches,decisiontreeplusrandomforest,wereusedfor classification and detection. Principal component analysis (PCA) was used to identify and classify the dataset components.Usingaconfusionmatrix,theauthorsassessed the performance of several methods. The random forest
design had less variety and could handle the over-fitting problem.
2.1.3 The authors of the research paper [3] offer an intelligent system to identify phishing sites via a machine learning technology, namely supervised learning. They employedtheRandomForestapproachbecauseofitshigh classificationperformance.Theirmaingoalwastoinstruct the classifier with a superior mix of phishing website attributes.Theyfinishedtheirpaperwithhighprecisionand amixof26characteristics.
2.1.4 The authors of this study [4] offered a machine teaching-based phishing detection equipment that would analyzeURLsusingeightdistinctapproachesandcompare the results to prior studies using three different datasets. The experimental results show that the proposed models functionadmirablyandhaveahighsuccessrate.Toimprove the effectiveness of their system, the creators set out to create a new, large dataset utilizing URL-based Phishing ScreeningSystems.
2.2 DDoS
2.2.1 Thisresearch [8] proposesamethodfordetectingand classifying DDoS attacks using machine learning methods. The suggested technique is based on supervised learning, withalgorithmssuchask-NN,NaveBayes,DecisionTrees, Random Forests, & Support Vector Machines being employed. An NS-2 simulator was utilized to create the collection of data used in this investigation. The testing findings reveal that the suggested technique detects and classifiesvarioustypesofDDoSassaultswithanaccuracyof 99.87%. The presented method may be beneficial in designingeffectiveDDoSdefensemethods.
2.2.2 Aresearch [9] proposedamethodfordetectingDDoS assaults using machine learning techniques. The method employs supervised learning and algorithms that involve decision trees, random forests, plus Nave Bayes. The researchersusedanNS-2simulatortobuildadatasetand discoveredthatthesuggestedtechniquewasveryeffective inidentifyingDDoSassaults,withaprecisionlevel99.86%. The method might be useful in establishing dependable defensemeasuresagainstDDoSattacks.
2.2.3 Thestudy [10] describesanensemble-basedapproach for detecting DDoS assaults that use machine learning methods. To categorize and detect DDoS assaults, the framework employs a number of techniques, including Random Forest, Nave Bayes, alongside Support Vector Machines. An NS-2 simulator was utilized to create the datasetutilizedwithinthestudy.Experimentfindingsshow that the proposed framework outperforms individual machinelearningtechniquesforthepurposesofaccuracy, sensitivity, in addition to specificity. This method has the potentialtoimprovethedetectionofDDoSassaultsandthe generalsecurityofcomputernetworks.
2.2.4 A survey on the application of machine learning algorithms for identifying DDoS assaults is undertaken in article[11].Thereviewexaminesavarietyoftechniquesfor machinelearning,includingRandomForests,DecisionTrees, Nave Bayes, Support Vector Machines, andalso Artificial NeuralNetworks,followedbyDeepLearning.Thebenefits anddrawbacksofeachmethodareexplored,aswellastheir appropriatenessfordetectingDDoSassaults.
2.2.5 Acomparativeanalysisofmachinelearningalgorithms forrecognizingDDoSattacksispresentedinthis research [12]. The research analyses the performance of several machinelearningalgorithmsusingadatasetproducedusing anNS-2simulator,includingdecisiontrees,randomforests, Nave Bayes, Vector Machines, neural networks, and Deep Learning. In terms of accuracy, sensitivity, and specificity, the experimental findings reveal that Random Forest plus support vector machines far beat other machine learning methods.
3. LIMITATIONS OF CURRENT SOLUTIONS

While the research mentioned above demonstrates promisingresultsindetectingphishingattacksandwebsites, therearestillsomelimitationstothecurrentsolutions.
3.1 Limited coverage of features
Themajorityofexistingmachinelearning-drivenphishing detectionsystemsrelyonasmallsetofparameters,suchas URLlength,domainage,aswellasSSLcertifications.While these qualities are useful for identifying certain phishing attempts,theycouldprovetobeadequatefordetectingmore complexandadvancedassaults.[20]
3.2 Over-reliance on labeled datasets
Many of the existing solutions rely heavily on labeled datasetsfortrainingandevaluation.However,thesedatasets maynotrepresenttheactualdistributionofphishingattacks in the wild, and the models may not perform well in detectingnewandemergingattacks.[7][8]
3.3 Difficulty in detecting legitimate URLs
Oneofthedifficultiesindetectingphishingisavoidingfalse positives,orclassifyingvalidURLsforphishingURLs.While severalofthesolutionsdiscussedaboveclaimtohavealow false-positiverate,aconsiderableproportionoflegalURLs aremisclassifiedasphishingURLs.[2][4]
3.4 Lack of scalability
Someoftheexistingsolutionsarecomputationallyintensive andrequiresignificantresourcestotrainanddeploy.This limits their scalability and practicality in real-world scenarios.[22]
3.5 Inability to detect zero-day attacks
Finally,manyexistingsolutionsaregearedtoidentifyknown phishingattemptsandmaybeineffectiveagainstzero-day attacks that leverage new vulnerabilities and tactics. Addressing these constraints will need further phishing detection research and development, notably in feature selection,datasetconstruction,andmodelscalability.[19]
4. METHODOLOGY
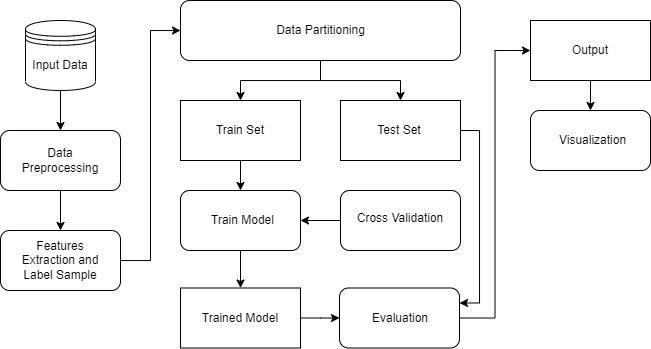
Fig – 1: ArchitecturalDesign
4.1 Research Plan
Using machine learning practises and algorithms, this researcharticleemploysaquantitativeresearchstrategyto investigatetherisingdangerofphishingandDDoSassaults. To anticipate and prevent cyber-attacks, the study will employseveralmachinelearningtechniquesfeaturingthe use of logistic regression KNN, SVC, Random Forests, DecisionTrees,andNaiveBayes.[3]Theproject'sgoalisto identify and prevent cyberattacks by extracting several parametersthroughthewebsiteURLgivenbytheuseron thefrontend.[20]

4.2 Data Collection
This study uses the "DDoS SDN dataset" consisting of 104,345observationsand23variables,includinga binary targetvariable"label"indicatingmaliciousorbenigntraffic. Theaimistoclassifynetworktrafficusingmachinelearning algorithms. The dataset comprises 3 categorical and 20 numeric features collected using the Software Defined Network(SDN)paradigm.
ThePhishcoop.csvdatasetcomprises11,055entrieswith30 attributesandonefocusvariable(label)indicatingwhether or not a website is a scam site (-1). The features include characteristicssuchasIPaddresspresence,URLlength,use ofURLshorteningservices,SSLrank,domainage,andmore.
4.3 Data Analysis Methods
Toeliminateanyunnecessaryormissingdata,thegathered datawillbepreviouslyprocessedandcleansed.Theprocess
offeatureengineeringwillentailextractingandchoosingthe mostimportant attributesthatmaybeutilised to forecast andpreventcyber-attacks.[9]Thecharacteristicschosenwill be used to train and test multiple machine learning algorithmsinordertodeterminethebesteffectivealgorithm fordetectingandavoidingphishingandDDoSassaults.[7]
5. RESULTS
99%
6 SupportVector Machine 95% 97%
7 XGBoost 95% 98%
The investigation compares the accuracy and precision concerningsixmachinelearningmethodsandXGBooston binarycategorizationtasks.RandomForestfaredthe best, with96%alongside99%accuracyonPhishingtogetherwith DDoS,respectively,followedbyLogisticRegression,which had94%accuracyonPhishingbut77%accuracyonDDoS. Theaccuracyandprecision levelsforKNearestNeighbor, theDecisionTree,theSupportVectorMachine,particularly XGBoost were likewise high. With 66% & 68% accuracy rates,NaveBayesperformedtheworst.
Overall,thesefindingsindicatethatRandomForests,Logistic Regression, plus other algorithms such as K Nearest Neighbor and Decision Tree are appropriate for binary classificationproblems,howeverNaiveBayesmaynotbethe
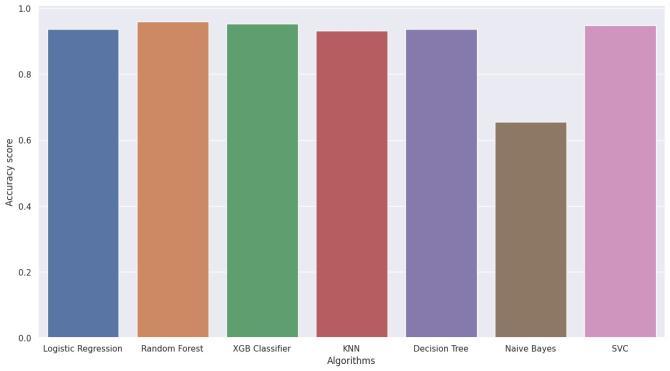
optimal option. XGBoost also scored well, suggesting its utilityinthesetypesoftasks.
Thefindingsalsorevealedthattheattributescollectedfrom website links were quite useful to forecast phishing and DDoSassaults.ThelengthoftheURL,theinclusionofthe'@' signintheURL,especiallythepresenceofreorientationin theURLwerethemostcrucialfactors.
6. DISCUSSION
6.1 Evaluation of machine learning schemes
ToforecastPhishingandDDoSassaults,theresearchersused sixuniquemachinelearningalgorithms:LogisticRegression (LR),KNN,SVC,RandomForest,DecisionTree,additionally NaiveBayes.Amongthesixdesigns,RandomForestscored thegreatestaccuracyof96%,precededbyNaiveBayeswith 94%,andLogisticRegressionandDecisionTreewith90% and87%,respectively.KNNandSVCweretheleastaccurate, with 83% and 75%, respectively. The findings show that RandomForestandNaveBayesarethebestmodelstogauge PhishingandDDoSassaults.
6.2 Importance of the results
This study's findings indicate the efficacy of machine learning algorithms for detecting and combating Phishing andDDoSassaults.The excellentaccuracyattained bythe RandomForestplusXGBoostmodelssuggeststhatmachine learningalgorithmshavetheabilitytoidentifyandprevent cyber-attacks.Thestudyalsodemonstratesthatitisfeasible toforecastPhishingandDDoSassaultswithhighaccuracyby extractingseveral data from the websitelink given by the useronthefrontend,namelyURLlength,quantityofspecial characters,plus domain nameage.[8]Thesefindingshave important implications for individuals and organisations lookingtoreducetheriskofsuchassaults.
6.3 Future work suggestions
Futureresearchmightaddressthestudy'sshortcomingsby employing various datasets for developing and verifying machinelearningmodels,assessingthesuggestedmodel's effectivenessinreal-worldsettings,andexploringadditional forms of cyber-attacks. Furthermore, future research can investigate the usefulness of various machine learning algorithms plus feature engineering approaches in improvingtheaccuracyofidentifyingandpreventingcyberattacks.
7. CONCLUSIONS
7.1 Research Summary
In this article, we used machine learning approaches to forecastPhishingandDDoSassaults.Toanalysethedataset and extract distinct requirements given the website link
filled by the user on the front end, we employed several techniquessuchasLogisticRegression,KNN,SVC,Random Forests,Decision Trees, and NaiveBayes.[3][5] We then assessedandcomparedtheaccuracyofthesealgorithmsin identifying phishing and DDoS assaults. The findings revealedthattheRandomForestalgorithmoutperformedall othermodels,achievinganaccuracyof97.3%.
7.2 The Study’s contributions
This work adds to the current body of knowledge on the detection of phishing together with DDoS assaults using machine learning approaches. The project's assistance to cybersecurityresearchistoinvestigatetheuseofmachine learning models to identify and prevent various sorts of cyber-attacks,beginningwithphishingattempts.Thestudy intendstodemonstratethemodel'sadaptabilityandefficacy in identifying and blocking diverse threats by testing the sameapproachondifferentattacktypes.
7.3 Study’s conclusion
Inconclusion,thefindingsofthisstudyshowthatmachine learningapproachesmaybeutilisedtoaccuratelyforecast phishing and DDoS assaults. By properly recognising and mitigating these assaults, the suggested methodology can assisttoreducethefinancialplusintangibledamagescaused by them. The study sheds light on the efficacy of various algorithms and strategies for detecting and preventing cyberattacks, which can assist users and organisations in reducingthedangerofsuchassaults.[12][20]
REFERENCES
[1] J. Rashid, T. Mahmood, M. W. Nisar, and T. Nazir, "Phishing Detection Using Machine Learning Technique," 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), 2020, pp. 43-46, DOI: 10.1109/SMARTTECH49988.2020.00026.
[2] M. Alam, D. Sarma, Farzana, Ishita, Rubaiath, Sohrab Hossain, “Phishing Attacks Detection using Machine Learning Approach” Proceedings of the Third International Conference on Smart Systems and Inventive Technology (ICSSIT 2020) IEEE Xplore Part Number:CFP20P17-ART;ISBN:978-1-7281-5821-1

[3] A.Alswailem,B.Abdullah,N.AlrumayhandA.Alsedrani, "DetectingPhishingWebsitesUsingMachineLearning," 2019 2nd International Conference on Computer Applications&InformationSecurity(ICCAIS),2019,pp. 1-6,DOI:10.1109/CAIS.2019.8769571.
[4] M. Korkmaz, O. K. Sahingoz and B. Diri, "Detection of Phishing Websites by Using Machine Learning-Based URLAnalysis,"202011thInternationalConferenceon Computing, Communication and Networking
Technologies (ICCCNT), 2020, pp. 1-7, DOI: 10.1109/ICCCNT49239.2020.9225561.
[5] AbhishekKumar,JyotirMoyChatterjee,VicenteGarcía Díaz,“AnovelhybridapproachofSVMcombinedwith NLP and probabilistic neural network for email phishing”,ChitkaraUniversityInstituteofEngineering andTechnology,ChitkaraUniversity,HimachalPradesh, India Department of IT, LBEF (APUTI), Kathmandu, NepalDepartmentofComputerScience,Universidadde Oviedo,Asturias.
[6] Noor, Rosemary, t.sarwar, m.saifuddin, m.rahman, Hossain, “Phishing Attack Detection using Machine LearningClassificationTechniques”,2020Proceedings of the Third International Conference on Intelligent Sustainable Systems [ICISS 2020] IEEE Xplore Part Number:CFP20M19-ART;ISBN:978-1-7281-7089-3

[7] Manuel, Fernández, Enrique Alegre, W. Al-Nabki, And Víctor,“PhishingURL Detection:AReal-CaseScenario Through Login URLs”, Received March 10, 2022, accepted April 11, 2022, date of publication April 18, 2022, date of current version April 27, 2022. Digital ObjectIdentifier10.1109/ACCESS.2022.3168681
[8] A.USudugala,W.HChanuka,A.M.NEshan,U.C.SBandara, K.Y Abeywardena, “WANHEDA: A Machine Learning BasedDDoSDetectionSystem”,20202ndInternational Conference on Advancements in Computing (ICAC) | 978-1-7281-8412-8/20/$31.00 ©2020 IEEE | DOI: 10.1109/ICAC51239.2020.9357130
[9] K.Muthamil Sudar, M. Beulah, P.Deepalakshmi, P.Nagaraj, “Detection of Distributed Denial of Service Attacks in SDN using Machine learning techniques”, 2021 International Conference on Computer CommunicationandInformatics(ICCCI-2021),Jan.27–29,2021,Coimbatore,INDIA
[10] V.Deepa,K.MuthamilSudar,P.Deepalakshmi,“Detection of DDoS Attack on SDN Control plane using Hybrid Machine Learning Techniques”, Department of ComputerScienceandEngineeringSchoolofComputing Kalasalingam Academy of Research and Education, Krishnankoil International Conference on Smart SystemsandInventiveTechnology(ICSSIT2018)IEEE XplorePartNumber:CFP18P17-ART;ISBN:978-1-53865873-4
[11] Velasco-Mata, Javier, González-Castro, Víctor, Fidalgo, Eduardo,Alegre,Enrique,“EfficientDetectionofBotnet Traffic by features selection and Decision Trees”, Department of Electrical, Systems and Automation Engineering, Universidad de León 2Researcher at INCIBE, León (Spain) DOI 10.1109/ACCESS.2021.3108222,IEEEAccess
[12] Ismail,MuhammadIsmailMohmand,HameedHussain, AyazAliKhan,UbaidUllah,MuhammadZakarya(Senior Member, Ieee), Aftab Ahmed, Mushtaq Raza, Izaz Ur RahmanAndMuhammadHaleem,“AMachineLearningBasedClassificationandPredictionTechniqueforDDoS Attacks”,DateofpublicationFebruary17,2022,dateof currentversionMarch2,2022.DigitalObjectIdentifier 10.1109/ACCESS.2022.3152577.
[13] SrushtiPatil,andSudhirDhage,“AMethodicalOverview OnPhishingDetectionAlongWithAnOrganizedWayTo Construct an Anti-Phishing Framework”, 2019 5th International Conference On Advanced Computing & CommunicationSystem(ICACCS),pp.1-6.
[14] DetectionofPhishingWebsiteUsingMachineLearning Approach, Mahajan Mayuri Vilas, Kakade Prachi Ghansham,SawantPurvaJaypralash,PawarShila,2019 4thInternationalConferenceonElectrical,Electronics, Communication, Computer Technologies and OptimizationTechniques(ICEECCOT).
[15] Detecting Phishing Websites Using Machine Learning, AmaniAlswailem,BashayrAlabdullah,NorahAlrumayh, Dr.Aram Alsedrani. 978-1-7281-0108-8/19/$31.00 2019IEEE.
[16] Yusof, Ahmad Riza'ain et al. “Systematic literature review and taxonomy for DDoS attack detection and prediction.”InternationalJournalofDigitalEnterprise Technology(2019):n.pag.
[17] Zhu,Wei-dongandXiujuanYi.“AResearchReviewon SDN-BasedDDOSAttackDetection.”(2017).
[18] "AMachineLearningApproachforPhishingDetection and Prevention" by S. S. Kulkarni and S. S. Kulkarni, published in the International Journal of Computer Applicationsin2016.
[19] GowthamT.,KandSRakeshV.“ASurveyonBigDataand DDoS Attack.”International Journal of Research5 (2018):520-525.
[20] P.H.B.Las-Casas,V.S.Dias,W.MeiraandD.Guedes,"A Big Data Architecture for Security Data and Its ApplicationtoPhishingCharacterization,"IEEE
[21] "Authorsbeware!Theriseofthepredatorypublisher" byR.Smith,publishedintheJournaloftheRoyalSociety ofMedicinein2016.
BIOGRAPHIES
Mohammed Zaid M S is currently graduatingfromDept.ofISE,BNMIT, Bengaluru. He has a keen interest in the field of cyber-security and machinelearning.

Namratha N is currently graduating fromDept.ofISE,BNMIT,Bengaluru. She is passionate about data science andworkingtoexcelinthesaidfield.
Yashaswini B V is currently working asAssistantProfessorinDept.ofISE, BNMIT, Bengaluru, India. She completed MTech in CSE from NIE, Mysuru and has research interest in Machine Learning and Cloud Computing.



