Advanced Intelligent Video Surveillance System In Elevators By Using OpenCV
AKSHAY VANAPARTHI1 , ANUSHA RASAMSETTY2 , SIDHARTH REDDY CHAMAKURA3 , DHEERAJ SUNDARAGIRI41, 2, 3 B. Tech Scholars, Department of Computer Science and Engineering, SNIST, Hyderabad-501301, India
4 Assistant Professor, Department of Computer Science and Engineering, SNIST, Hyderabad-501301, India

Abstract - It takes a lot of time and effort to manually monitor unexpected occurrences that happen in an elevator cab and react in time. In this research, we createa smart video surveillance system and declare
Identification system for elevator cabs that allows for the estimation and security evaluation of information such as the condition of the cab door, human body behavior, and the number of occupants.
Our project called the Advanced Intelligent VideoSurveillance System uses OpenCV to detect motion in a certain region and only starts recording video when motion is found. The system further manages the functioning of an elevator in the same location, which only operates when motion is detected. The system uses a camera to record live video of the scene, which is then processed using OpenCV to look for motion. The device will begin capturing video and turn on the elevator when motion is detected. The device will cease capturing video and disable the elevator when motion is no longer being detected. The system may be applied to many different things, such as home, office, and building security systems. The project uses OpenCV, a well-known open-source computer vision library that offers a robust collection of capabilities for image processing and motion detection. The major goal of this project is to develop an intelligent surveillance system that improves the overall security of the area while conserving storage space by only recording when necessary and only operating the elevator when motion is detected.
Key Words: Surveillance,OpenCV,MotionDetection,Face Recognition,Storage
1. INTRODUCTION
Oneofthemanyissuesthatarestudiedintheextremely broadscientificdisciplineknownascomputervisionisthe potential application of computers to extract significant insightsfromdigitalimagesormovies.Thisisonlyoneofthe numerous topics that are discussed. From an engineering point of view, the goal is to develop automated processes thatareequivalenttothosethatthehumanvisualsystemis capable of completing. Computer vision is the study of strategies for acquiring photos, processing those photographs, interpreting those photographs as digital images,andextractinghigh-dimensionalinformationfrom
theactualenvironmenttogenerateinformationthatcanbe describedasnumbersorsymbols,suchasjudgments.These techniquesareallpartofthestudyofcomputervision.Realtime computer vision is the primary goal of a set of programmingfunctionsknownasOpenCV,whichstandsfor open-source computer vision. Intel was the company that came up with the idea first. The collection is available on several platforms and may be accessed by anybody at no cost.
Traditionalvideosurveillancesystemsdonotpermitfora prompt response in the event that a criminal act is in progress.Settingupasystemsimilartothisoneisnotonly fairlycostlybutalsoprettydifficult.Thisproject'sobjective istodevelopanintelligentopen-sourcetoolthatiscapable ofassistingindividualsinneed.peopleororganizationsin the process of independently constructing a reliable and cost-effective system They will,asa result,have complete controlovertheirtechnology,whichwillprovidethemthe opportunitytolockdowntheconfigurationsandadjustthem so that they are more suitable for their needs. It is imperativethatourhomes,placesofemployment,andany other business venues that we frequent be adequately protected from criminal activity. Standard surveillance technologyisunabletoalertpropertyownerstoanyillegal behaviourthatmaybetakingplaceontheirpremises.The feedisthesoleitemthatistransferredandcapturedinthis process. As a direct consequence of this, the owners are unable to take immediate action to prevent a break-in or theft.
Motiondetectionisacharacteristicthatcanbefoundin manycontemporaryelevatorsystems.Thishelpstoincrease both safety and the energy efficiency of the system. We propose in this project to use OpenCV and Haar cascade classifiers to identify motion in real-time video streams coming from security cameras that have been placed in elevators. These cameras will be located in different buildings.Thedevicewillcalltheelevatortoyourfloorand beginrecordingthevideoassoonasitsensesmotioninthe room.Afterthen,thevideothatwastakencanbeputtouse forpurposesofsecurityandsurveillance.TheHaarcascade classifier is used to a video stream in order to identify motionby monitoringvariationsinthepixel valuesof the stream.Itispossibletoexpandthecapabilitiesofthesystem
to incorporate more sophisticated functions like facial recognition,objecttracking,andreal-timewarnings.
2. LITERATURE SURVEY
In recent years, there has been a major uptick in interest regarding the utilization of intelligent video surveillance systemsforthedetectionofmotionandtheenhancementof safety.TheincorporationofOpenCV,apopularopen-source computervisionlibrary,haspavedthewayforthecreationof moresophisticatedsystemsthatarecapableofperforming image processing and motion detection in an effective manner.
Several research projects have investigated the use of OpenCV for motion detection in a variety of different environments.Forinstance,Pateletal.(2019)suggestedan elevator surveillance system that detected motion using OpenCVandtrackeditusingaRaspberryPi.Theirtechnology efficientlyrecognizedandtrackedpersonswhiletheywere inside the elevator, which made it possible for additional safetyprecautionstobetaken.

In addition, Yang et al. (2018) demonstrated a video surveillancesystemforelevatorsthatwasbuiltonOpenCV and incorporated face recognition technology for the purposes of identification. Their technology was able to detectpersonsastheyenteredandlefttheelevator,which contributedtotheenhancedsecuritymeasures.
Investigationshavebeenconducted,withinthecontextofthe surveillancesystem,notonlyintothedetectionofmotionbut alsointotheincorporationofelevatorcontrol.Anelevator surveillancesystemthatwasdevelopedbyWuetal.(2017) thatwasbasedonOpenCVandHadoopwasproposed.This system efficiently managed the functioning of the elevator basedonmotiondetection.Themechanismmadeitsuchthat theelevatorwouldonlyworkwhenitsensedmotion,which improvedboththeelevator'senergyefficiencyanditslevelof safety.
Theresultsoftheseresearchdemonstratethattheutilization ofOpenCVinvideosurveillancesystemstodetectmotionand implementadditionalsafetyprecautionsisbothfeasibleand beneficial.Thecapabilitiesofthesystemhavebeenfurther improvedbytheuseofcleveralgorithms,suchasthoseused forfacialrecognitionandelevatorcontrol.
Itisimportanttopointoutthatresearchanddevelopment activitiesarestillbeingconductedintheareaofintelligent video surveillance systems. There is a possibility that developmentsinmachinelearningandartificialintelligence algorithms will one day lead to improvements in the precision and effectiveness of motion detection and identification procedures.Inaddition, theincorporationof cloud-based storage solutions and capabilities for remote monitoring might provide further advantages to such systems.
Inconclusion,theresearchthathasbeendonelendscredence to the idea that an advanced intelligent video surveillance systemthatmakesuseofOpenCVformotiondetectionand image processing is both possible and practicable. The addition of an elevator control system that is based on motiondetectionprovidesanadditionallayerofsafetywhile alsoincreasingthebuilding'soverallefficiency.Theongoing research and technological breakthroughs in the sector continuetocontributetothecreationofvideosurveillance systemsthatarebothmoreadvancedandmoreeffective.
3. SYSTEM OVERVIEW
ThisprojectusesOpenCVaswellasHaarcascadesforthe purpose of object recognition and tracking. The major purpose of the system is to improve safety and offer continuousmonitoringofparticularentitiesoritemslocated withinaspecifiedregioninrealtime.
Acameraisusedinordertorecordlivevideofootagewhile thedeviceisinoperation.Afterthat,thevideoframesare analyzed with OpenCV, a sophisticated computer vision librarythatoffersabroadvarietyoftoolsandalgorithmsfor analyzing images and videos. This is done after the movie hasbeenplayed.
TheHaarcascadeclassifierisanimportantcomponentofthe systemasawhole.Haarcascadesareatypeofmethodthatis basedonmachinelearningandhasthecapabilityoflocating certainobjectsorcharacteristicsincludedinsideanimageor video frame. Object detection tasks, such as recognizing faces,pedestrians,orotherspecifieditems,areatypicaluse ofthistechnology'scapabilities.
Throughout the course of the study, Haar cascades are educatedtorecognizethemanythingsofinterest.Inorderto dothis,thecascadesneedtobetrainedusingbothpositive and negative examples so that they may learn the differentiatingcharacteristicsofthetargetitems.Afterthey havebeentrained,thecascadesmaythenbeappliedtothe videoframesinordertorecognizeandtracktheobjectsof interest.
The system is designed with a real-time monitoring component, which enables the detected items to be continuallymonitoredandthemotionofthoseobjectstobe studied. This makes it possible to detect immediately any activitythatarenotpermittedorthatseemsuspiciousinside themonitoredregion.When thesystemidentifiesa target object, it may proceed to perform a number of predeterminedactions.Thesemayincludesoundinganalert, sending notifications, or activating certain security measures.
Image preprocessing, feature extraction, and various approaches for image enhancement are some of the additional functionality that may be used in the system thankstoOpenCV'sprovisionoftheseadditionalcapabilities.
Thesefeaturescontributetoanimprovementintheobject identification and tracking system's accuracy and dependability.

Theoverall integrationof OpenCVand Haarcascadesinto thesystemarchitectureoftheprojectenableseffectiveand efficientobjectrecognitionandtracking,whichenhancesthe project'scapabilitiesintheareasofsecurityandmonitoring. Thesystemhasawiderangeofpotentialapplications,some ofwhichincludemonitoringinpublicareasandbuildingsas wellasapplicationsforpersonalsafetyandprotection.
Thefunctionalrequirementswillbevideorecording,video storage, video playback, video retrieval, live video monitoring, motion detection, camera positioning, remote access, alert notifications, integration with other systems andscalabilityusingOpenCVandthecameramodule
Theperformancerequirementswillbevideoquality,frame rate, storage capacity, video retrieval time, live video streaming, network bandwidth, motion detection speed, systemuptimeandcamerapositioningflexibility.
The software requirements will be an operating system, languageofcodingsuchaspython,toolsuchasvisualstudio toperformthisconcept.
Hardwarerequirementsfortheprojecttobeworkedwillbe a PC with atleast 4 gb of ram, enough disk space to store, 1.6GHzprocessorormore,acameramodule
4. SYSTEM ARCHITECTURE
Elevator Operation
Theelevatoroperationcomponentrepresentsthephysical architecture of the elevator system as well as the control mechanism.Itconsistsoftheelevatorcabinitself,aswellas thedoors,buttons,andthecontrolsystemthatliesunderthe surfaceandisresponsiblefordirectingthemovementand functioningoftheelevator.
Elevator Cameras
Thecameralocatedintheelevatoractsasthemajorsource of input for the video surveillance system. Typically, it is positionedontheinterioroftheelevatorcabinsothatitmay record live video footage of the outside environment. The program module is continually responsible for the processing and analysis of the video frames that are continuouslycapturedbythecamera.
Program Module
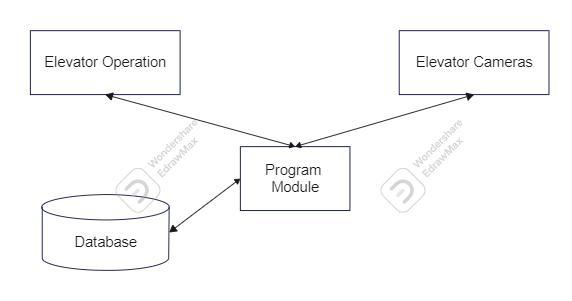
Thesoftwarecomponentofthesystemisreferredtoasthe program module, which represents this component. It incorporatesthenecessarylogic,algorithms,andcapability for motion detection, object recognition, and decisionmakingbasedonthevideoinputfromtheelevatorcamera. This information is obtained from the video. OpenCV is a computer vision library, and as such, it is an essential componentoftheprogrammodule.Itsuppliestheessential toolsandfunctionsforcarryingoutanalysisandprocessing ofimages.
The software module is responsible for carrying out a variety of activities, such as detecting motion by utilizing OpenCV'smotiondetectionalgorithms,recognizingobjects by utilizing Haar cascades or other machine learning approaches,andmakingdecisionsbasedontheeventsthat have been identified. The module could additionally incorporateotherfunctionalitysuchaseventlogging,alerts in real time, and interface with the control system for the elevator.
Database:
Fig -1:SystemArchitecture
Thearchitectureofthevideosurveillancesysteminstalledin elevatorsiscomprisedofnumerousessentialcomponents, including the elevator operation, the elevator camera, the programmodule,andthedatabaseasdepictedintheFig1. Theproperoperationandefficiencyofthesystemasawhole isdependentonthecontributionsmadebyeachcomponent individually.
Thedatabasecomponentofthevideosurveillancesystemis responsibleforstoringandmanagingtheinformationand datathathasbeengatheredfromthesystem.Itperformsthe functionofarepositoryforrecordedvideofootage,events thathavebeenidentified,timestamps,andothermetadata. Thedatabasemakesitpossibletoretrievedata,doanalysis onthatdata,andretrieveitagainforthepurposesoffuture reference,systemmonitoring,andauditing.
The elevator camera is responsible for capturing video footage, which is then processed by the program module with the help of OpenCV and any other applicable algorithms.Thisflowisfollowedbythesystemarchitecture. Themoduleisresponsiblefordetectingmotion,recognizing
objects,andinitiatingappropriateactionsdependingonthe rules that have been set. The database is used to save the datathathasbeengatheredandtheeventsthathavebeen identifiedsothattheymaybeanalyzedfurtherorretrieved.
Thecombinationofthesecomponentsresultsinanelevator videosurveillancesystem thatiscomprehensiveand very effective.Real-timemonitoring,motiondetection,andobject identificationareallmadepossiblebythedesign,which,in turn,ensuresanincreasedlevelofsecurityandsafetyinside theelevatorenvironment.
OpenCV
When it comes to computer vision and machine learning, many developersturntoOpenCV(OpenSourceComputer Vision Library). It's a potent instrument for many uses in image and video analysis because to its wide range of functionsandalgorithmsfordealingwithvisualdata.
OpenCVwascreatedbyIntelandisnowbackedbythelikes of Willow Garage and Itseez. Since it is built in C++ and providesbindingsforotherlanguages,likePython,itmaybe usedbyabroadvarietyofprogrammersandresearchers.
Imagefiltering,featureidentificationandextraction,object recognition,motionanalysis,andcameracalibrationarejust someofthemanyimageandvideoprocessingfeaturesmade availablebythispackage.Machinelearningtechniquesfor common applications like clustering, classification, and regressionarealsoincluded.
OpenCV'sabilitytoefficientlyandaccuratelyinterpretvisual input is thanks in large part to the library's sophisticated implementationofcomputervisionalgorithms.Itachieves good speed on many hardware systems thanks to streamlinedroutinesandparallelprocessingapproaches.

Edgedetection,picturesegmentation,objecttracking, and optical flow are just a few of the many computer vision techniques and algorithms that are a part of OpenCV. The mathematical models and formulae on which these algorithms are built make it possible to extract useful informationfromimages.
The following steps with formulas are used by OpenCV's implementationoftheCannyedgedetectiontechnique.
1.ApplyGaussiansmoothingto the input image usingthe formula:
smoothed_image=GaussianFilter(input_image,sigma)
2. Calculate the gradient magnitude and direction at each pixelusingtheformulas:
gradient_magnitude=sqrt((dx)^2+(dy)^2)
gradient_direction=atan2(dy,dx)
3. Apply non-maximum suppression to thin out the edges usingtheformula:
suppressed_edge_pixel=edge_pixelifgradient_magnitudeis maximumalongthegradientdirection,otherwisesetto0
4.Applyhysteresisthresholdingtodeterminethefinaledges usingtheformulas:
strong_edges=gradient_magnitude>=high_threshold
weak_edges=(gradient_magnitude>=low_threshold)and (gradient_magnitude<high_threshold)
final_edges = ApplyConnectedComponentAnalysis(strong_edges, weak_edges)
The edges in an image can be important for a variety of purposes,includingobjectboundaryrecognitionandfeature extraction,andthisapproachcanassistfindthem.
Based on Haar-like characteristics and machine learning methods, OpenCV's Haar cascade classifier is another popular tool. By training a classifier on a huge dataset of positiveandnegativesamples,theHaarcascadeclassifieris abletorecognisethingslikefacesoruniquepatterns.
Haar Cascade Classifier
TheHaarcascadeclassifieriswidelyusedincomputervision applicationsfordetectingobjects.Machinelearningisused inconjunctionwiththeideaofHaar-likecharacteristicsto identifyspecificobjectsinstillphotosandmovingvideo.
Trainingaclassifierwithbothpositiveandnegativepicture examplesiswhatmakestheHaarcascadeclassifiereffective. Imageswiththetargetiteminthemareconsideredpositive samples, whereas those without are considered negative samples.Inordertotrain,wefirstextractHaar-likefeatures from these data, and then we use a boosting technique to trainacascadeofclassifiers.
Theintensityfluctuationsinaparticularregionofanimage can be captured using Haar-like features, which are rectangularpatterns.Integralimages,whichprecomputethe sumsofpicturepixelsinsiderectangularsections,areused tocomputetheseattributesquickly.TocalculatetheHaarlikefeatures,wetakethedifferencebetweenthewhiteand blackintensitiesofeachpixelintherectangle.
Totrainthecascadeofclassifiers,theAdaBoostmethodis utilizedtopickthemosteffectiveHaar-likefeatures.Ituses an iterative process to choose characteristics that reliably distinguish between positive and negative data. The significance of the selected features in the final categorizationisreflectedbytheweightsassignedtothem. Each level of the cascade classifiers is made up of several relatively weak classifiers. Each weak classifier's output
decideswhetheraregioniseliminatedoradvancedtothe nextassessmentphase.
Theinputpictureismovedacrossthescreenatvarioussizes andlocationsasthetrainedHaarcascadeclassifierperforms its detection procedure. The classifier performs an evaluationoftheHaar-likecharacteristicsateachnodeand then applies a cascade of relatively weak classifiers. If a givenareasatisfiesallofthecascade'srequirements,thenit hassuccessfullydetectedthetarget.
TheHaarcascadeclassifieriswell-knownforitsusefulness in object identification applications. Face recognition, pedestriandetection,andobjectidentificationarejustsome oftheareaswhereithasbeenputtogooduse.Thetrained cascademaythenbeusedtosearchforthingsineitherlive videoorstillphotos.
UsingHaar-likecharacteristicsandtheAdaBoostalgorithm, the Haar cascade classifier is a machine learning-based approachtoobjectidentification.Itcanrecognizeitemsby passinganinputpicturethroughaseriesofclassifiers.The classifier'seffectivenessinawiderangeofcomputervision applicationsmakesitausefulresourcefordetectingobjects inimages.
5. EXPERIMENTAL METHODOLOGY

Eigenfaces (pca set of rules)
Turk and Pentland pioneeredfacial recognition withtheir 1991Eigenfacesmethod.It benchmarksfacial recognition systems using Principal Component Analysis (PCA). Key stepsofthealgorithm:

1. Training dataset: Grayscale face photographs are gathered. Multiple photographs of each person should capture lighting, emotion, and stance changes.
2. Normalizing size, rotation, and illumination: Face photos are preprocessed. Histogram equalization andfacelandmarkalignmentarecommonmethods forstandardizingillumination.
3. Eigenface Construction: The approach extracts eigenfaces from preprocessed face pictures using PCA. PCA creates face image dataset covariance matrix eigenvectors and eigenvalues. The eigenvectors show the dataset's highest variance, whiletheeigenvaluesreflectitsimportance.
4. EigenfaceSelection:Theeigenfaceswiththebiggest eigenvalues, which represent the most important facialtraits,arerecognized.Theseeigenfacescreate afaceimagespacebasisset.
5. Projection: Each dataset face picture is projected ontotheeigenfacespaceforareduced-dimensional representation.Calculatetheeigenfaceweightsor coefficients that best reconstruct the input face picture. Projection coefficients capture face features.
6. Recognition:Themethodprojectsaninputfaceinto the eigenfacespaceand determinesits projection coefficients.Thecoefficientsarethencomparedto known faces in the training dataset using a similaritymetriclikeEuclideandistanceorcosine similarity.Therecognizablefaceisnearer.
Turk and Pentland's Eigenfaces algorithm showed PCAbasedfacerecognition'spromise.Itsetthegroundforfuture advancesandisnowessentialtofacialrecognitionsystem development. The system was sensitive to lighting and position, but it established the groundwork for more advancedfacerecognitionmethods.
Fisher faces
Belhumeur, Hespanha, and Kriegman's 1997 Fisherfaces algorithm also known as Linear Discriminant Analysis (LDA) isaprominentfacerecognitionmethod.Itimproves Eigenfacesrecognitionbyaddingclassseparation.
Fisherfacesalgorithmoverview:
1. Data Collection: Like other facial recognition systems, face photos are gathered for training. Multiple samples of each person should capture lighting,emotion,andstancechanges.
2. Preprocessing: Size, rotation, and lighting are normalized in face photographs. Alignment, histogram equalization, and noise reduction improveimagequality.
3. FaceSpaceConstruction:Fisherfacesfindsalinear transformationthatmaximizesclassseparabilityin thefacepicturedataset.Itcalculatesthebetweenclass and within-class scatter matrices, which quantifyclassvariation.
4. Fisherface Extraction: The method then eigenanalysestheratioofthebetween-classscatter matrix to the within-class matrix. Fisherfaces, the ratiomatrix'sbiggesteigenvectors,aregenerated. Fisherfacesdistinguishfacialclasses.
5. DimensionalityReduction:Projectingfacepictures ontoFisherfacespacereducestheirdimensionality, likeEigenfaces.Thistransformationconvertseach facepictureintoaFisherfaces-spannedsubspace.
6. Recognition: The method projects a face into Fisherface space and generates projection coefficientstorecognizeit.Thecoefficientsarethen compared to known faces in the training dataset usingasimilaritymetriclikeEuclideandistanceor Mahalanobis distance. The recognizable face is nearer.
7. FisherfacesusesLDA'sdiscriminativecapabilitiesto improverecognitionaccuracyoverEigenfaces.The idealprojectionoptimizesfaceclassseparability.It works well in situations with lots of lighting and posturechanges.
In complicated real-world circumstances, the Fisherfaces algorithm's assumption of linearity and Gaussian distributionsmayrestrictitsperformance.However,ithas been widely investigated and implemented in face recognition research and is useful in computer vision and patternidentification.

approach known as PCA. It determines the principle components, a pair of orthogonal vectors that effectively encapsulatethedata'soverallvariance.Onewaytodescribe thealtereddataisasalinearcombinationoftheprincipal components.ThePCAformulaisexpressedasfollows:
X'=X*W
whereX'isthetransformeddata,Xistheoriginaldata,and Wrepresentsthematrixofprincipalcomponents.
An method for supervised learning used for classification and regression applications is called SVM. In a highdimensional space, it locates an ideal hyperplane that effectivelydividesvariousdataclasses.Inordertotransform theinputdataintoahigher-dimensionalfeaturespacewhere theclassesmaybelinearlyseparated,SVMrequiresakernel function.TheSVMformulalookslikethis:
f(x)=sign(sum(alpha_i*y_i*K(x_i,x))+b)
where f(x) represents the predicted class label for a new inputsamplex,alpha_iarethecoefficientsobtainedduring training,y_iarethecorrespondingclasslabels,K(x_i,x)isthe kernel function that measures the similarity between trainingsamplesandtheinputsample x,and b isthe bias term.
Kernel techniques, such as PCA and SVM, have been extensivelyusedinavarietyoffields,suchasbioinformatics, natural language processing, and image recognition. They provideversatilityinidentifyingnonlinearpatternsindata andcanhandleintricateinteractionsthatlinearapproaches might miss. These techniques have demonstrated their ability to successfully complete difficult classification and regressionproblems,makingthemimportantresourcesfor machinelearningresearchandapplications.

When compared to other face recognition algorithms like FisherfacesandEigenfaces,kernelapproacheslikePCAand SVMhaveanumberofadvantages.
Kernel Methods: PCA and SVM
Kernel methods are effective tools for nonlinear data analysisandclassificationinmachinelearningandpattern recognition. Principal Component Analysis (PCA) and SupportVectorMachines(SVM)aretwooftenutilizedkernel techniques.
Finding a lower-dimensional representation of highdimensional data while maintaining the most crucial information is the goal of the dimensionality reduction
1. Nonlinearity:Kernelapproacheshaveastrongtrack record with nonlinear data and are capable of capturingintricatepatternsandcorrelations.Kernel approaches, which can simulate complex fluctuationsinfacialcharacteristics,aremoresuited for face recognition applications using nonlinear data than Fisherfaces and Eigenfaces, which are linearmethods.
2. Themostdiscriminativefeaturesfromthedataare extracted using PCA and Eigenfaces. But they are only capable of linear modifications. In contrast, data may be projected onto a high-dimensional featurespaceusingkerneltechniques,particularly SVMwithkerneltrick,wherelinearseparabilityis attained.Askernelapproachescancaptureintricate
correlationsbetweenfacetraits,thisenablesmore preciseandreliablecategorization.
3. Robustness to Variations: When compared to FisherfacesandEigenfaces,kernelapproachesare moreresistanttochangesinposition,lighting,and facialemotions.Theycanimplicitlyaccommodate thesedifferencesandyetretainstrongclassification performance byapplyingkernel functions.Thisis especially crucial in real-world situations when facialfeaturesmightdiffergreatly.
4. Generalization: Kernel approaches can generalize moreeffectively.Bydeterminingthebestdecision limit,theymaysuccessfullymanageoverfittingand quicklyreacttonewdata.Thismakesitpossiblefor freshfacesthatweren'tpartofthetrainingsettobe recognizedmoreaccurately.

5. Flexibility: Kernel methods provide you the freedomtoselectseveralkernelfunctionsbasedon theissueathand.Toidentifycertainpatternsinthe data,otherkernelfunctionscanbeused,including sigmoid, polynomial, and gaussian. Kernel approachesareflexibleand usefulforavarietyof face recognition problems because to their versatility.
Fisherfaces and Eigenfaces are less accurate, robust, and flexiblethankernelapproaches,suchasPCAandSVM.They provide more precise recognition performance and improvedgeneralizationtounseenfaces,whichisespecially usefulwhenworkingwithcomplicatedandnonlinearface data.
Grey Scaling Images
Imagesarefrequentlygrayscaledinmotiondetectionand facial recognition systems to enhance and simplify image processing processes. The procedure entails turning the originalcolorphotosintograyscale,whichassignsasingle valuerangingfrom0(black)to255(white)toeachpixel's intensity.
Gray scaling aids in facial identification by reducing the impactofcolorchangesandconcentratingonthestructural andtexturaldetailsoftheface.Thealgorithmmayfocuson aspectsliketheshapeoftheface,thetextureoftheskin,and the patterns of facial landmarks like the eyes, nose, and mouth by converting the image to grayscale. This simplificationmakestheextractionandcomparisonofface featuresmorepreciseandeffective.
Grayscalabilityinpicturesisalsoadvantageousformotion detection systems. The emphasis is shifted from color changestovariationsinpixelintensitybymakingtheinput videoframesgrayscale.Thisreductionmakesspottingand followingmotioninascenesimpler.Movementisindicated
by changes in intensity, and algorithms may assess these fluctuations to pinpoint areas of interest where motion is takingplace.Additionally,grayscalinglessensthecomputing costofmotiondetectionmethods,increasingtheviabilityof real-timeprocessing.
Grayscalingoffersbenefitsintermsofcomputingsimplicity andeffectiveness.Grayscalephotosmaybeprocessedand analyzedmorequicklythanfull-coloronessincetheyneed lessmemoryandcomputerpower.Additionally,grayscale pictures are more robust and dependable for facial recognitionandmotiondetectiontasksbecausetheyareless susceptibletochangesinlightingandcolor.
Todeterminethegrayscalevalueforeachpixel,itnormally uses a straightforward formula or method. Taking the average of the red, green, and blue color channels in the originalpictureisonetypicaltechnique:
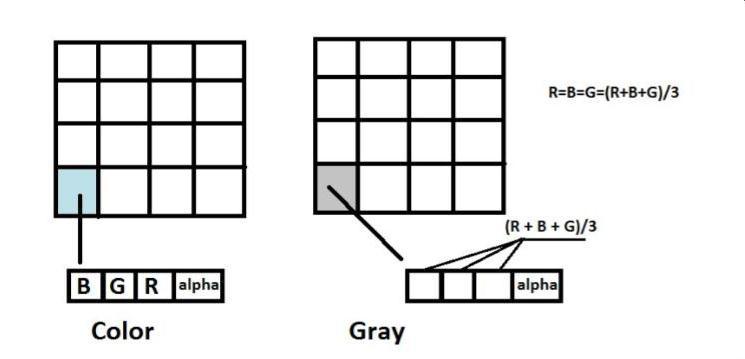
GrayscaleValue=(R+G+B)/3
WhereR,G,andBrepresentthered,green,andbluecolor channel values of the original image, respectively. This formulacalculatestheaverageintensityvalueandassignsit tothepixelinthegrayscaleimage.
Another approach is to use weighted averages that mimic the perceived luminance of different color channels. For example,theformulausedintheITU-RBT.601standardis:
GrayscaleValue=0.299*R+0.587*G+0.114*B
Each pixel's grayscale value is determined by these algorithms,producingagrayscalepicturewhereeachpixelis representedbyasingleintensityvalue.
While gray scaling photos does not require the use of complicated mathematical techniques, color photographs may be easily converted to grayscale using these easy averagingformulaeorweightedaverages.Itisappropriate for facial identification and motion detection applications since the emphasis is on obtaining structure and textural informationratherthanaccuratecolorrepresentations.
6. RESULTS
Firstoff,thetechnologyhasgreatlyimprovedsecurityinthe vicinityofitsdeployment.Itguaranteesthatanysuspicious behavior is swiftly identified and recorded thanks to its sophisticatedmotiondetectionfeatures,makingitauseful toolforspottingandanalyzingpossiblesecurityconcerns. Thebuilding'stenantsand occupantsnowfeel safeand at easeasaresultofthis.
Additionally,thesystem'sintegrationwithelevatorcontrol hassignificantlyincreasedtheelevators'generalefficiency andconvenience.Theoperationismorecost-effectiveand ecologicallybeneficialsinceexcessiveenergyconsumptionis reduced by only turning on the elevator when motion is detected.Thesecurityprecautionsarefurtherimprovedby therestrictedaccesstotheelevator,whichguaranteesthat onlyauthorizedpeoplemayuseit.
The system's capacity to conserve storage space by only capturing video when motion is detected is another important benefit. This not only lowers the amount of storage needed, but also makes it easier to evaluate the recordedvideo.Whensearchingandanalyzingtherecorded films, the intelligent motion detection tool removes extraneous information and concentrates on recording occurrencesofinterest.
Additionally, the project's use of OpenCV, a potent opensource computer vision toolkit, has made it possible to createasystemthatisincrediblyadaptiveandadjustable. This implies that, whether it's a large-scale commercial structureoraresidentialcomplex,thesurveillancesystem may be customized to match the unique demands and requirementsofvariouslocations.Thesystem'sadaptability allowsuserstocustomizeittomeettheirownsecurityand operationalrequirementswhileensuringthatitmaybeused inavarietyofsettings.
7. CONCLUSION
TheprogramusesaHaarCascadeClassifiertoanalyzethe data anddeterminetheidentitiesof people in the images. Afterinstallation,itmaybequicklyputtouse.Thistacticis ideal for when normal monitoring procedures must be maintainedinaplacewhereabnormalbehavioriscommon. Theamountofspaceneededforstorage,energyrequired, andupkeepcosts are all ableto be drasticallycutwithits help.TheinstallationofOpenCVwascrucialtotheoperation of the whole device. There is no more practical or economical time frame to put into use. This simple and accessible solution is useful for minimizing the amount of spaceneededtosavetheimages.
Inconclusion,theAdvanced IntelligentVideoSurveillance System implementing OpenCV has effectively attained its goals of motion detection, selective video recording, and elevator operation control. The project has shown to be
beneficial in boosting resource efficiency, supplying a dependablesurveillancesolution,andstrengtheningsecurity measures.
The system has demonstrated the capability of computer vision in motion detection and picture processing by utilizing OpenCV's capabilities. The effectiveness and efficiencyofthesystemhavebeenfurtherimprovedbythe useofsophisticatedalgorithmslikeHaarcascadesandfacial recognition. Due to the early detection and recording of possible threats and suspicious activity, security has increasedasaconsequence.
In addition to improving energy efficiency, the system's capacity to manage elevator operation based on motion detection offers an additional degree of protection. Unauthorized entry is reduced by only turning on the elevator when motion is sensed, protecting the building's tenants'privacyandsafety.
Additionally, the project's emphasis on motion-based selectiverecordinghasledtoeffectivestorageuse.Storage spaceismaximizedandtheprocessofevaluatingrecorded footage is expedited by only recording video when it is actuallyneeded.Thismakesitpossibletoanalyzepertinent occurrencesquicklyandprecisely,savingtimeandmoney fortheinquiry.
Thereareseveralpossibleusesfortheadvancedintelligent video surveillance system, including security systems in buildings,publicareas,andprivateresidences.Becauseofits versatilityandmodificationcapabilities,itmaybetailored byuserstofitavarietyofcontextsandrequirements.
Overall, the project has been effective in showcasing the advantagesandusefulnessofanOpenCV-basedintelligent video surveillance system. It has delivered improved resource management, increased security, and effective surveillancecapabilities.Thestudypavesthewayforfuture developmentsinintelligentsurveillancesystemsthatmake useofcomputervisiontobuildsettingsthataresaferand moresecure.
8. REFERENCES
[1]. A. Renjith and Aishwarya, “Enhanced home security UsingIoTandraspberrypi,"InternationalResearchJournal ofEngineeringandTechnology(IRJET),vol.4,2017.

[2]W. F. Abaya, J. Basa, M.Sy, A. C. Abad, and E.P. Dadios, "Low-costsmartsecuritycamerawithnightvisioncapability usingraspberrypiandOpenCV,"2014.
[3]M.Pervaiz,Y.Y.Ghadi,M.Gochoo,A.Jalal,S.Kamal,and D.-S.Kim,“Asmartsurveillancesystemforpeoplecounting and tracking using particle flow and modified som,” Sustainability,2021.
[4]M.Rashmika,“Motionsensorandfacerecognition-based surveillance system using raspberry pi,” International JournalofAdvancedResearchinComputerScience,vol.8, no.5,2017.
[5]A.CobParro,L.Gutierrez,Marron-Romera,GardelVicente, andBravo-Munoz,“Smartvideosurveillancesystembased onedgecomputing,”2021.
[6]T.Shivprasad,B.Shivani,A.P.Singh,andDeepak,“Survey paperonsmartsurveillancesystem,”InternationalResearch Journal of Engineering and Technology (IRJET), vol. 3, 2016.Fig6:BGRtoGrayConversion

