A REVIEW ON NMAP AND ITS FEATURES
YASHVANT MAHADEV HANGE
Department of Mechanical Engineering, DIEMS College of Engineering, Aurangabad, Maharashtra, India. ***
Abstract - Network assaults have been common, resultinginthetheftofprivatedata.Informationgathering isthefirststepthathackersdobeforelaunchinganattack. Nmapisoneofthe mostoftenusedscanningprograms at thispointtogatherdatafromthetargethost.Tohelpwith the ensuing attack, the acquired data can be further examined. Hence, a reliable method of identifying Nmap scanning behavior must be developed. In Nmap we can scan all the 65535 ports in one go with the packet customizableoption,Theintrusiondetectionsystem(IDS) frequently employs the ET OPEN rule set to safeguard hosts against nefarious intrusion. With ET OPEN restrictions in place, the Nmap detection rate is 58.3%; however, when IDS evasion is present, it drops to 8.3%. We suggest the Comprehensive Nmap Detection Rules because of the low detection rate of ET OPEN (CNDR). Nmap scanning habits can be precisely and effectively detected by CNDR. The customizable fields in Nmap are gone, and rules for operating system scanning are added in the CNDR. With our specified dataset, CNDR achieves 100%detectionrateofregularNmapscanningand91.7% detection accuracy of Nmap with IDS evasion. The outcome demonstrates that CNDR is more resistant to customizedscanningandissuperiortoETOPEN.
Key Words: AReviewofNmapanditsfeatures,Network Mapper, Nmap tool, scanning the network, and Computer Networks
1. INTRODUCTION
Nowadays, everybody is connected to the world by the meansoftheInternet,theInternethaspenetratedmostof the world, and for connecting through the Internet we need to have devices that are capable of sending and receiving data packets. The devices are connected to each otherbydifferenttypesoftopologies.
Every device which is connected to the internet has its own IP and MAC address. Computer Networking is the practice of exchanging data between nodes in a shared medium. This type of data of computers is sensitive in nature as hackers might clone the data and sniff to the targetsystem.

There are several protocols available for the networks, andcomputersforthesmoothfunctioning oftheservices. On a normal computer system, there are a total of 65535 ports, from which 1-1024 are dedicated and others are dynamic ports, so it is difficult for system administrators
to track all the ports, which might result in possible vulnerability in the network, which can be exploited by hackersforextractingthedata.
ComputerNetworksecurityismainlyconcernedaboutthe computers that are connected to the internet, from the Network mapping tools we can gather information about the OS, open ports, versions of the system, and its vulnerabilities, The Nmap gives us a lot of features like gatheringinformationaboutOS,ports,etc.
Nmap is open-source platform, Nmap, which stands for Network Mapper,isa freeandopensource programused for port scanning, vulnerability analysis, and, obviously, network mapping. Nmap was developed in 1997, yet it continues to serve as the benchmark for all other comparable programs, whether they are open-source or commercial.
2. SCANNING TECHNIQUES
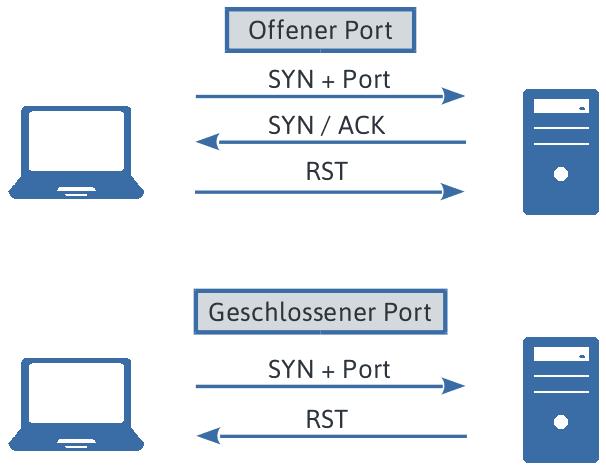
2.1 SYN scanning -Thisishownmapoperatesbydefault. SendingSYNpacketstotheintendedsystemandwatching for a response are involved. On the target machine, open portsarefoundusingthismethod.
Eachgenuineconnectionattemptbeginswiththisphaseof the TCP three-way handshake. Scan me completes the secondphasebysendingaresponsewiththeSYNandACK flagssincethetargetportisopen.Onatypicalconnection, Ereet's machine, krad, would send an ACK packet to acknowledge the SYN/ACK and finish the three-way handshake.TheSYN/ACKanswerhasinformedNmapthat the port is open, hence it is unnecessary for it to perform thisaction.
3. CONCLUSIONS
2.2 TCP Stealth Scanning –
Topreventportscans,TCPStealthisaproposedchangeto the Transmission Control Protocol (TCP) that would conceal open ports for certain TCP services from the public. It resembles the port-knocking method in certain ways.
What about the failed TCP Packets, though? Unable to inform the sender whether the port is "Open" or "Closed" for business, a "Stealth" port merely "drops" all incoming packets.
connectionless and lacks a handshake procedure, making itmoredifficulttodetectavailableports.
UDP scanning may be done using a variety of programs, including Nmap and hping. These programs send UDP packetstovariousportstodeterminewhichareopenand which are closed. Nevertheless, as compared to TCP scanning, UDP scanning has disadvantages since it does not provide stable connectivity and may not get answers from the target system, resulting in false positives and false negatives. Moreover, UDP scanning may set off networkalarmsandintrusiondetectionsystems,notifying system administrators and even banning the scanning source.
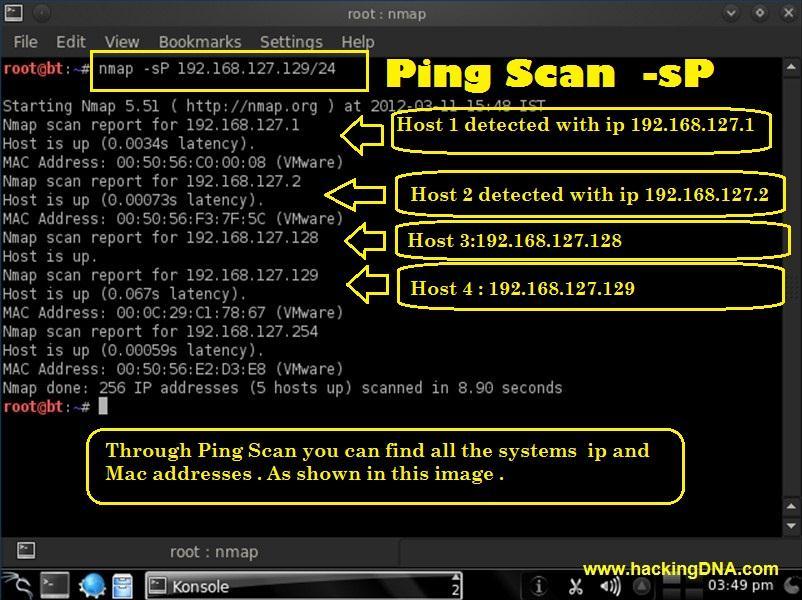
Generally, UDP scanning can give useful information on a targetsystem'sweaknessesandstrengths,butitshouldbe handled with caution and consideration for potential consequences.
3. FEATURES:
System administrators, security experts, and ethical hackers frequently utilize Nmap, a well-known network scanner, for tasks including network inventory, vulnerability scanning, and more. With the purpose of learning more about the target network, it employs several scanning techniques. Here are some of the methodsthatNmapemploys:
2.3 Idle Scanning: By delivering forged packets to the target system, this method operates. An inactive system, sometimes known as a "zombie," receives a SYN packet from Nmap. The destination machine may have an open portatthatIPaddressifthepacketisacknowledgedanda replyissent.
2.4 Fragment Scanning:
Fragment scanning is a computer security method that includesevaluatinganapplication'scodetofindandpatch vulnerabilities. This scanning procedure entails breaking down the application's code into smaller, more manageable chunks, scanning each fragment for potential vulnerabilities,andthenevaluatingtheresultstoestablish the application's overall security posture. Fragment scanning can assist firms in identifying and correcting securityproblemsearlyinthedevelopmentprocess,hence avoidingcostlyandharmfulsecuritybreacheslater.Itisa critical component of any complete security testing methodology.
2.5 UDP Scanning:
The technique of discovering open UDP ports on a target machine is known as UDP scanning. It is one of the most extensively used methods for network reconnaissance, and attackers frequently utilize it to uncover flaws in a target's network defenses. UDP, unlike TCP, is
3.1 Ping Scanning: To determine if the target IP addresses are up or not, Nmap sends ICMP Echo Queries to them. The term "ping sweep" is another name for this method.
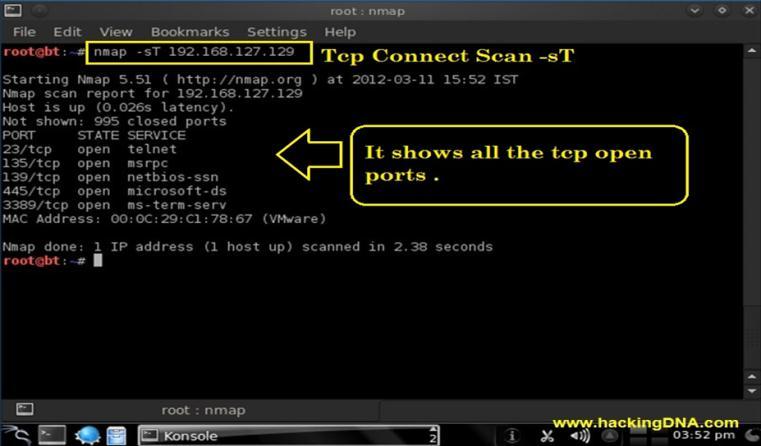
3.2 Port Scanning:
To find out which ports are open and which are closed, Nmap sends packets to the target IP addresses and

examinestheirresponses.Toaccomplishthis,itmakesuse of many types of scans, including TCP SYN scans, TCP Connectscans,andUDPscans.

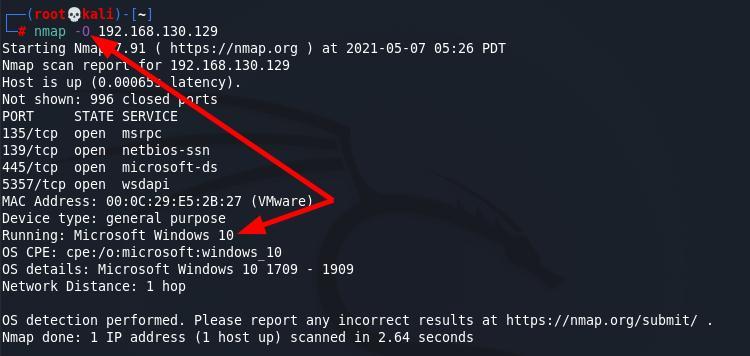
3.3 OS Detection:
By examining the replies to certain probes, Nmap may determinetheoperatingsystemofthetargetcomputer.
executionfeature.Thesescriptsmaybeusedtocarryouta number of operations, including network mapping, versiondetection,andvulnerabilityscreening.
Users of Nmap may execute both custom and pre-made scripts that can be downloaded from the Nmap Scripting Engine (NSE) database using the script execution feature. These scripts may be used to carry out a number of operations,includingnetworkmapping,versiondetection, andvulnerabilityscreening.
The vulnerability detection script and version detection scan will both be run by this command. Any known vulnerabilities will be looked for by the script, which will thennotifytheuser.
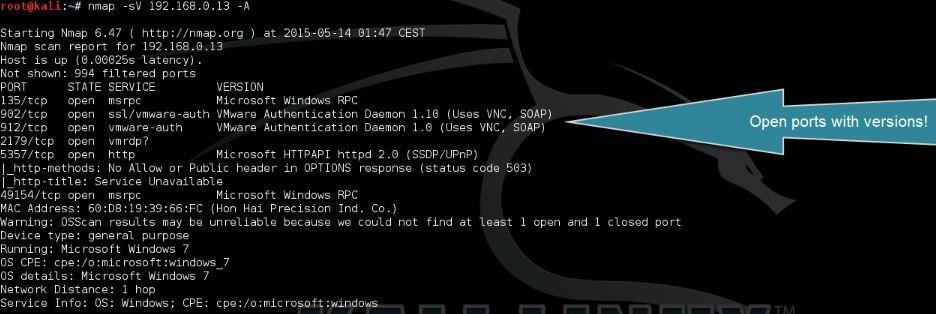
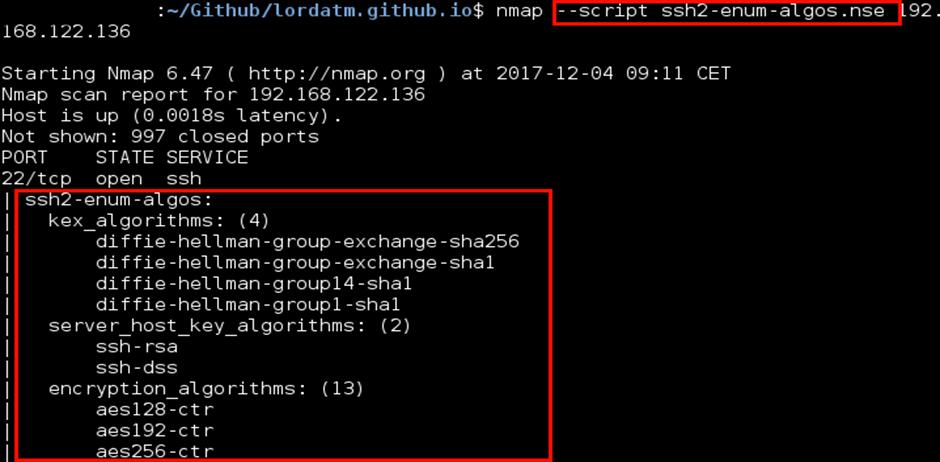
3.4 Version Detection:
By examining the responses to specific probes, Nmap can ascertaintheversionoftheservicesthatareactiveonthe targetmachine.
3.6 Flexible output formats:
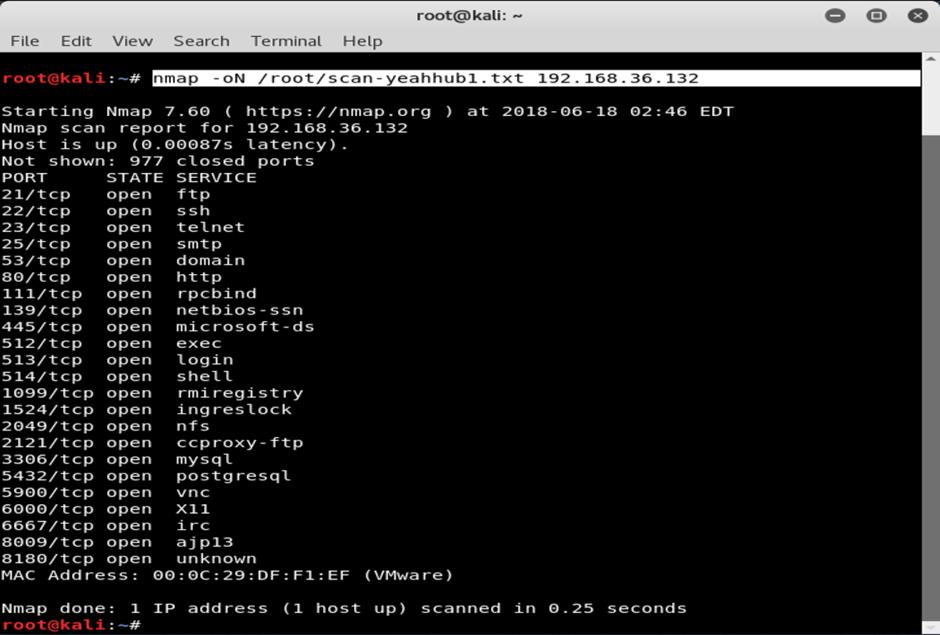
Nmapsupportsavarietyofoutputformats,includingXML, JSON,andGREP.
3.5 Script Execution:
Nmapoffersascriptingenginethatenablesuserstocreate originalscriptstocarryoutvariousactivities,likelearning more about the target computer and finding vulnerabilities. Users of Nmap may execute both custom and pre-made scripts that can be downloaded from the Nmap Scripting Engine (NSE) database using the script
3.7 Vulnerability assessment:
Nmap is a flexible tool for vulnerability assessment that maybeusedtofindpossiblevulnerabilitiesintargethosts and systems. It is vital to stress, however, that vulnerability assessment should be done ethically and withtheapprovalofthetargetsystemowner.
Nmap-vulners,Vulcan,andvulnarethecommonandmost popular CVE detection scripts in the Nmap search engine. Thesescriptsallowyoutodiscoverimportantinformation aboutsystemsecurityflaws.
3.8 NSE scripts:
A sophisticated feature of Nmap called NSE (Nmap Scripting Engine) enables the creation and execution of unique scripts during a scan. NSE scripts can automate processes that would otherwise require manual interventionandoffernewcapabilitiestoNmapscans.
Advantages:
1.Automating tasks:Automatingmanual processeslike banner capturing, service enumeration, and vulnerability assessmentispossiblewithNSEscripts.
2. Increased accuracy: By using vulnerabilities and finding hidden services, NSE scripts can produce more precisefindingsthanaregularscan.
3.Customization:NSEscriptsprovideuserstheability tomodifyscansbyaddingcertainparametersandflags.
4. Easeofuse:NSEscriptsareeasytouseandrequire minimalinputfromtheuser.
3.9 Stealth Scanning:
Nmap has a stealth scanning feature that makes scanning more concealable and challenging to find. By blocking reverse DNS lookups and using idle scanning methods, it canevadediscovery.Networkadministratorsandsecurity expertsemploythemethodofstealthscanningtoexamine a network covertly. Because it is intended to evade detectionbythesecuritymechanismsofthetargetsystem, itisknownas"stealth."
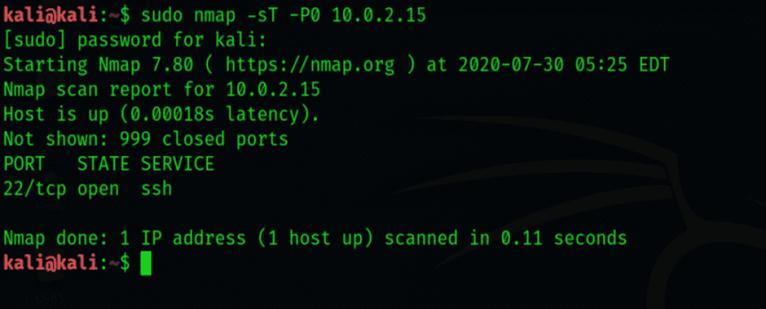
A number of settings for stealth scanning are available in the well-known network mapping program Nmap. Stealth scanning is often used to obtain data on a target system withouttheownerofthesystembeingawareofthescan.
4. NSE (Nmap Scripting Engine)
NSE(NmapScriptingEngine)isasophisticatedNmaptool feature that allows users to build and run custom scripts to automate a range of network-related operations. NSE scripts are written in the Lua programming language and are supplied by default with the Nmap installation. Below issomeinformationonNSEscripts.
NSE scripts are used to interact with network hosts in a morethoroughanddynamicmannerthantypicalnetwork scanningtoolsallow.Thescriptsmaybeadjustedtomatch unique requirements, and the output generated by NSE scripts can be used to uncover security weaknesses and potentialattackroutesthattypicalscanningmethodsmay notfind.
NSE also integrates well with other tools like Metasploit, allowing users to expedite their security testing process andquicklydetectandaddressvulnerabilities.Inaddition, the Nmap community routinely adds new NSE scripts, ensuring that the tool remains relevant and up to date in today'sever-changingcybersecurityscenario.
4.1 Purpose:
NSE's major goal is to automate network-related processes such as network scanning, host finding, vulnerabilitydetection,andexploittesting.NSEscriptscan be adjusted to fulfill specific needs, and users can also designtheirownscripts.
NSE offers a framework for users to develop and run customLuascriptstoautomateprocessesandenhancethe capabilitiesoftheNmaputility.
4.2 Pre-installed scripts:
Nmap has many pre-installed scripts that may be used to automate a variety of network-related operations. These scripts are classified based on their usefulness, making it simpleforuserstochoosethebestscriptforacertaintask. Below are some of the pre-installed script categories in Nmap:
1. Discovery scripts: These scripts are used to identify networkhostsanddeterminewhichservicesareactiveon eachhost.

2. Host scripts: These scripts are used to collect information on a given host, such as its operating system, openports,andservicesthatarerunning.
3. Vulnerability detection scripts: Thesescriptsareused to identify potential vulnerabilities on a host or network, such as weak passwords, open shares, or outdated softwareversions.
4. Exploit scripts: These scripts are used to test known exploits against specific hosts or services to determine if theyarevulnerabletoattack.
5. Intrusive scripts: These scripts are used to do more aggressive scans, which may disrupt services or network traffic.Thesescriptsshouldbeusedwithcautionandonly withthenecessarypermissions.
6. Brute force scripts: These programs are used to automatebruteforceassaultsandpasswordguessing.
7. Web scripts:
These scripts interact with web servers and web applications to perform tasks such as vulnerability scanning, web server fingerprinting, and testing for commonwebapplicationvulnerabilities.
8. Misc scripts:
These scripts carry out several tasks, including checking for default credentials, searching for open proxies, and identifyingSQLinjectionvulnerabilities.
You can use these pre-installed scripts in Nmap as-is or youcanmodifythemtosuityourneeds.Tofurtherexpand Nmap's capabilities, users can also create their own uniquescriptsusingtheLuaprogramminglanguage.
4.3 Custom scripts:
NSE scripts can be written by users themselves using the Lua programming language. Any task that can be automated through Nmap can be carried out using these scripts. Users with a fundamental understanding of programmingcanuseLuabecauseitisalightweight,userfriendlyprogramminglanguage.
HerearethestepstocreateacustomscriptinNmap:
1. Choose a task: Identifyingthe precisenetwork-related task you want to automate is the first step in writing a customscript.Forinstance,youmightwanttorunamore sophisticated network scan, gather more information aboutaparticularhost,orscanforaspecificvulnerability.
2. Write the script: Once you have determined the task, you can use the Lua programming language to create the script.Alightweight,adaptablelanguagemadespecifically
for scripting, Lua. For the scripting engine, Nmap offers thorough documentation as well as a ton of starter examples.
3. Test the script: Oncethe scriptiswritten,youcan run Nmaptotestitout.Toaccomplishthis,savethescripttoa file with the. nse extension and add it to your Nmap installation's scripts directory. The script can then be executed by either specifying its name on the command lineorbyusingthe scriptoptionandthescript'sname.
4. Share the script: If you have written a helpful custom script, you can contribute it to the official Nmap Scripting Engine repository and make it available to the Nmap community. This gives the chance for feedback and collaboration, as well as allowing other Nmap users to profitfromyourwork.
Nmap's custom scripts offer a potent method for automating particular network-related tasks and enhancing the program's functionality. You can build unique scripts that assist you in better comprehending and securing your network with a basic understanding of Luaprogrammingandalittleimagination.
4.4 Script execution:
TheNmapScriptingEngine(NSE)inNmapcanbeusedto run scripts. NSE offers a framework for executing scripts in a number of categories, such as web application scanning, vulnerability detection, and service enumeration. The steps to run scripts in Nmap are as follows:
1. Choose a script: Selecting a script that satisfies your unique requirements is the first step. Nmap comes with a sizablelibraryofpre-installedscriptsthatarecategorized according to their functionality. The Lua programming languagecanalsobeusedtowriteuniquescripts.
2. Specify the script: Once you have identified the script you want to execute, you can specify it on the command line using the script option followed by the name of the script. For example, to run the "http-title" script, you wouldusethefollowingcommand:
“nmap-p80 scripthttp-title<target>”.

3. Specify the script: Somescriptsneedextraarguments tofunctionproperly.Theseargumentscanbespecifiedby usingthe script-argsoptionanda listofkey-valuepairs. For instance, you would use the following command to specifytheuser-agentstringforthehttp-titlescript:
“ nmap -p 80 script http-title script-args http.useragent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110Safari/537.3"<target>.”
4. Run the scan: Once you have specified the script and any required arguments, you can run the scan by specifyingthetargethostornetwork.
5. View the results: Nmap will show the results of the scriptexecutionafterthescanisfinished.Detailslikeopen ports, active services, operating system information, and potential vulnerabilities might be included in the output. Usingthe-oNoptionandafilename,youcanalsosavethe resultstoafileforlateranalysis.
5. Conclusion:
Nmap is a versatile network exploration, administration, and security auditing tool. It includes functions such as host finding, port scanning, version detection, operating systemidentification,andvulnerabilityassessment.Nmap is adaptable and versatile, thanks to its command-line interface and extensive scripting features. Its user community is constantly building new modules and plugins. While it has significant limitations, such as the possibility of network interruption, system compatibility, and detection by intrusion detection systems, it is neverthelessanimportanttoolfornetworkadministrators and security experts. Overall, Nmap is an effective and dependable tool for assessing network security and administrationforbothnoviceandprofessionalusers.
REFERENCES
1. Fyodor. (n.d.). About Nmap. Retrieved from https://nmap.org/book/man-about-nmap.html
4.5 Integration with other tools:
Nmap can work together with other programs like Metasploit to automate the exploitation of vulnerabilities that it has identified. Users can streamline their security testingproceduresand quicklyfindand fixvulnerabilities thankstothisintegration.
4.6 Script output:
NSE scripts generate thorough output that can be used to examineanetworkscan'soutcomes.Informationlikeopen ports, active services, and discovered vulnerabilities are included in the output. By using this data, remediation effortscanbeprioritizedandoverallnetworksecuritycan beincreased.

4.7 Community contributions:
The Nmap community regularly contributes new NSE scripts,whichareopen-source.Becauseofthecommunitydriven approach, the Nmap tool is always current and useful in the rapidly changing cybersecurity environment oftoday.
In conclusion, the Nmap tool's NSE feature is a strong feature that enables users to automate a variety of network-related tasks. The tool includes a sizable library of pre-installed scripts, and the scripts can be altered to meet requirements. The comprehensive output generated by NSE scripts can be used to enhance overall network security,andNmapcanbeintegratedwithothertoolslike Metasploit.
Moore,D.,&Beale,J.(2006).NmapintheEnterprise:Your Guide to Network Scanning. United States: Syngress Publishing.
Smith, R. Parkinson, S. (2017). Nmap: Network Exploration and Security Auditing Cookbook. United States:PacketPublishing
