A detailed review on Video Steganography
Tarak Bharambe, Mrs. Pradnya Kasture, Jui Thule, Abhishek Chaudar, Sejal Raotole1B.Tech student, Computer Science, RMD Sinhgad School Of Engineering ,Pune, India.
2 Professor, Dept. of Computer Engineering, RMD Sinhgad School of Engineering, Pune, India
3 B.Tech student, Computer Science, RMD Sinhgad School Of Engineering ,Pune, India.
4 B.Tech student, Computer Science, RMD Sinhgad School Of Engineering ,Pune, India.
5 B.Tech student, Computer Science, RMD Sinhgad School Of Engineering ,Pune, India. ***

Abstract - When transmitting sensitive details, it's indeed essential to have adequate confidentiality. Cryptography and Steganography are indeed the ways by whichdatamaybesecuredinamannerthatisbothreliable aswellasdiscreet.Theconfidentialinformationischanged into cryptographic information during the process of cryptography,howeverduringtheprocessofsteganography, this same confidential information is kept intact but is concealedinsideaseparatetypeoffiles.Theprotectionof sensitivedatafromunauthorizedaccessbycybercriminalsis adifficultprobleminmodernenvironmentbecauseofthe prevalence ofsophisticated communicationstechnologies. Steganography is a method of concealing the presence of information and protecting sensitive data from being accessedbyunauthorizedparties.Asaresult,thereexistsa pressing requirement for an efficient method that can be usedfortheobjectiveofgeneratingthevideosteganography, whichisademandinthepresentdayandage.Throughthe examinationofagreatnumberofresearchprojectswhich have been carried out on this subject, it has become clear that the application of a method called Least Significant Bytes,orLSBforshort,isessentialtotheachievementofa successful video steganography methodology. This has resulted in the completion of our system for video steganography, which makes use of Frame Extraction, a Genetic Algorithm for Frame Identification, LSB Labeling, andAES basedSteganography.This method will get more developmentinsubsequentversionsofthestudyarticlethat areplanned.
Key Words: Frame Extraction, Genetic Algorithm, LSB Labeling, AES Encryption, Steganography
1.INTRODUCTION
The Internet plays an essential role in the lives of peoplelivinginthemodernage.Thefastexpansionofthe World Wide Web helps make it simpler for people to go abouttheireverydaylives.Thefollowingareafewusesof theonlineplatformthatserveasrepresentations:onlinebill payments, online recharge, e - ticketing reservation, electronic financial transactions, online reservation scheduling,e-shopping,etc.Thesocialnetworkingwebsites such as WhatsApp, Instagram, Twitter, and Facebook, amongst others, are the other component of the
infrastructure that has the largest impact on human life. People are able to communicate critically significant data andpaperstooneanotherbecausetothisfeature.Asaresult of the World Wide Web, individuals freely divulge their personal information to other individuals. If you send confidentialinformationovertheinternet,youruntherisk of being targeted by cybercriminals. Consequently, maintainingahighlevelofdataprotectionthroughoutthe processoftransmittinginformationacrosstheinternetmust be of the highest significance. The use of encryption and steganographyisgoingtobenecessaryinordertosolvethis challenge.
Inlightofthedramaticincreaseinindividualdevices and information development, as well as the significant increaseintheconsumptionofcommunicationchannelsin the downlink and uplink of information and data, the preservation of electronic media that is stored on the website has developed into a concern that is of critical importance. As a result, the studies focus their efforts on developingtechniquestosafeguardtheessential data and render it a little more confidential, with the goal of preventingcybercriminalsandotherunwantedvisitorsfrom gaining exposureto it.Cryptographyisa methodwhich is employedtosafeguardimportantdatabyencryptingitina certain manner that no one other than the trustworthy person whopossessestheuniquecodecanunderstand or accessit.Thisisaccomplishedbyemployingthetechniqueof encryption.Itispossibletoencodeanddecryptinformation usinganyoneofanumberofdifferentways;but,following theinventionoftheInternet,alloftheseapproachesturned useless,resultinginitbecomingessentialtolookformore meansofdataobfuscation.
As a direct consequence of this, the idea of steganography came into being. The practice of steganographyreferstothescienceofinformationhidingor the communication between the transmitter and the recipientofconfidentialinformationbyemployingthehost mediumasaveil,forinstance(video,audio,images,ortext). Thedifferenceforbothcryptographyandsteganographythe fact that the former term refers to the process of reconfiguringthecontentsofthemessageinsuchamanner suchthatonlytheintendedreceiverofthetextcanrecognize it,whereasthelattertermreferstotheprocessofconcealing
datainsideofshieldwithoutchangingthestructureofthe datainanymanner.
First, the confidential information is encrypted and afterwards,onceithasbeenencrypted,itisconcealedinside thevideo'sindividualframes.Cryptographyisamethodthat usescryptographictechniquestoscrambleprivatedata to preventitfrombeingdecipheredbyunauthorizedparties. Theprocessofconcealingtheinformationbehindavideois identical to the process of concealing data underneath a picture. In the approach that has been presented, video is employed as cover material. In order to conceal the confidential material, the video is cut up into individual framesorpictures.Finally,theconfidentialdatacouldcome in the format of text, or it might be hidden in a document thatisdisguisedasvideo.
In this article that analyzes literature, chapter 2 is brokenupintoanassessmentofpreviousresearchthatis presented in the manner of a reviewed literature, and the thirdchapterconcludeswithsomesuggestionsforhowmore researchshouldbeconducted.

2. RELATED WORKS
Intending to minimize the effect of steganography on neural network-automated tasks, Yang et al. [1] provide a binary attention mechanism-based solution to picture steganography.Theimagetexturecomplexity(ITC)modelis the initial attention mechanism and it helps find the positionsofthepixelsandtheirtoleranceforchangewithout being noticed by the human visual system. The second mechanism,theminimizingfeaturedistortion(MFD)model, mitigatestheeffectofembeddingbyreconstructingfeature maps.Thisresearchalsosuggestsmuchattentiontofusion andfinetunewaystoenhancetheprecisionofsecurityand covertinformationextraction.Inthisresearch,thesuggested methodsuccessfullydemonstratestheinvisibilityofsecret informationbydemonstratingthatembeddedpicturesmay evadedetectionbyavarietyofsteganographytechniques.
VideosteganographyisproposedbyXianfengetal. [2] as a defense against the widespread practice of transcoding videos before uploading them to social networkingsites.Tobegin,PCA-basedadaptiveselectionis utilizedtochooseareasoptimalforrobustembedding.To synchronize the embedding and extraction zones, a dualchannel joint embedding depending on the Y and U components is implemented. Thirdly, a video preparation procedureiscarriedouttoproducecoverfilmsthatmimic TCM.ErrorbitsarefinallywipedoutthankstoBCHcoding. Extensivestudiesareconductedonlocalmimickedchannels, YouTube,andVimeotoensuretheconsistencyandviability of the proposed approach. The experimental evidence demonstrates the robustness of the suggested technique againstvideotranscoding.It'sasaferandmoredependable waytodocovertcommunicationviaplatformslikeYouTube andVimeothanotheralternatives.
Inthehistoryofvideosteganography,VStegNETisa pioneering effort of its sort. Islam et al. [3] have demonstratedandcomparedtheperformanceofVStegNET and models that depend on 2D-CNN. Using a variety of industry-standard methods, they have shown that their model not only performs well quantitatively but is also resistanttosteganography.Theproposedmodellendsitself toseveralnaturalextensionsandimprovements,suchasthe embedding of more data in the covers, the embedding of othermediatypes(images,text,audio,etc.),andtheaddition ofadversariallossforincreasedresistancetosteganalysis. Anadvancedinnovationtheauthorsaimtoworkonisthe recurrent storage of secret information in the container's cover in both spatial and temporal locations to prevent problems caused by container misuse such as the introductionofnoise,compression,orcroppingofvideo,etc.
VideoswereproposedbyRajkumaretal.[4]when combined with encryption, steganography adds an extra layer of protection to a system. The suggested system's resultisembeddingtheencrypteddatawithinthevideofiles themselves.Thereare3bitsofinformationhiddenineach frame.Asfortheplannedvideo,videoandconfidentialdata of varying sizes are utilized to test steganography. The proposed method proves that the encrypted video is not significantlydegradedinquality.Thatqualityiscomparable totheoriginalvideo.Therecipientofthestegovideoisthe oneinpossessionofthedecryptionkey.Itisimpossibleto ascertain whether or not hidden knowledge exists. Therefore,theinformationcanbesenttoitsfinal location without worry. The Data Encryption Standard (DES) algorithm is the most basic and straightforward data encryption method currently in use. Although it is straightforward and employs widely-used methods, it providesaquickandsecuremeansofdatatransfer.
A unique encoder-decoder architecture for image steganography waspresented byRehman etal.,[5] which was built on convolutional neural networks (CNNs). The proposedmethodologycombinesapairofencoder-decoder networkstoembedagivenimageaspayloadandrobustly retrieveitfromagivencoverimage,incontrasttoprevious techniqueswhichsimplyutilizedabinaryrepresentationas payload.Extensivetrialshavedemonstratedtheefficacyof theproposedsuggestedtechnique,withsubstantialpayload capacityresultinginoutstandingoutcomesacrossavariety ofwild-imagedatasets.
A. U. Islam et al. [6] describe an MSB-based techniqueofimagesteganography.Thismethodreliesonthe fact that the cover picture is encoded with the difference betweentwo-pixelbits.Thefifthandsixthbitsofapixelare the ones that will be embedded. The entering secret information bit determines the value of the difference between bits 5 and 6. Bit 5 can be left unchanged if the differencebetweenbits5and6isidenticaltotheincoming
secretbit.Ifbit5'sdifferencefrombit6doesnotmatchthe incomingbit,bit5isinvertedtomakethemequal.Sincethe LSB is typically the focus of steganographic systems, switchingtotheMSBstrengthensthesecurityofthesystem. Inaddition,theproposedmethodhasahigherPSNRthanthe competing methods, demonstrating the scheme's efficacy through comparison. The suggested method can conceal more information in a single cover image, and its payload capacityisalsosuperiortoexistingmethods.

Thedata-hidingstrategy,presentedbyS.Shakeela etal.,isbotheffectiveandsecure.Thetwofoldcodingsystem employed in this approach makes the steganography extremely secure, making deciphering the hidden informationadifficulttask.Thesteganographicmoviemay beplayedwithlittlequalitylossduetocompressionwhena transformdomainmethodisused.However,thesuggested strategystillmanagestosaveasubstantialamountofhidden data from such compression assaults, which is surprising given that it is common knowledge that compression eliminatesredundantinformationfromthemedium.Ifthe hiddenmaterialinquestionissoundandit'sretrievedfrom avideo,itwon'tsoundexactlylikethemusicorsoundeffects thatwereoriginallyplacedinthevideo[7].Duetopossible distortion introduced by rounding, processing stages, and compression techniques, further processing of the audio data is required to achieve a near-identical listening experience.Therefore,thisstrategyhasbroadpotentialfor theadvancementofscienceandtechnology.Improvements toexistingmethodsandtheidentificationofvulnerabilities insecretandsecurecommunicationrequiremorework.
A3-3-2LSBsteganographicapproachisproposed byP.A.Shofroetal.[8]whichusestheCaesarandVigenere cyphersandincorporatesbitwiseandoroperationsintothe insertion process. The suggested approach has been evaluated using a variety of images and three different message sizes, with an average PSNR of over 40 dB being achieved.Theresultssuggestthattheapproachiseffective. However, the image quality is compromised by a larger payload size. A PSNR of less than 40dB was seen when encodinga2.67bppmessage,however,itwasstillgreater than30dB. Therefore, itissuggestedthata biggerpicture sizebeutilizedtopreserveimagequality.Youshouldencode apayloadof1.33bpptopreservestealth.
To conceal information, S. Kumar et al. [9] developedamethodthatwouldselectivelyfeedthepixels. Theresultingnoisebaseisunremarkableanddoesnotraise anyredflags.IncomparisontothecommonLSBmethod,the stegopicture'shistogramrevealsonlyminordeviationsfrom the original cover image, confirming its superior visual quality.Whenthesecretdataisembeddedintoapicture,it causeslittledistortion,asmeasuredbythepeaksignal-tonoise ratio (PSNR), which outperforms the standard LSB substitution approach. In terms of how it behaves, this incorporateddistortionfactorwouldnaturallymatchwhat
theimagegainsfromthetransmissionchannel.Therefore, thetransmissionchannelnoisemakesitmoreprobablethat the picture abnormality, however little, discovered by the steganalysis method would be missed. In addition to the predeterminedselectivitycriteriaofthealgorithm,justone bit-per-pixel is changed, therefore the overall size of the imageislittleaffected.
S.Chavanetal.[10]proposedamethodologythat makes use of the DES algorithm and a shifting algorithm based on steganography, with the aid of a visual cryptographic technique. Steganographic and visual cryptography can be used to achieve the same level of success as regular image security. Therefore, it becomes difficult to attempt decrypting the prearranged legitimate information. Using the least significant bit treatment throughout and including the shifting algorithm greatly optimizes the security properties of steganographic techniques.Theplannedsystempermitsthebestgreyscale output, which makes it more resourceful in the real-life applicationandisalsoresistanttoRSattack.
An affine transformation encryption scheme was presentedbyH.Mathuretal.tosecureatestpicture.They simulatedtheproposedworkinMATLABISImRa2009and implemented it there. The suggested work has been simulated, and the results have been presented and compared to prior work in terms of PSNR, SSIM, entropy, andcomputationaltime.Thesuggestedworkhasalsobeen given a histogram [11]. The simulations and real-world applicationsoftheproposedworkdemonstrateitssuperior securityandexceptionalperformance.Whenthetimecomes, they may use peppy text assaults to gauge how well the suggestedapproachprotectssensitivedata.Toimprovethe affine transformation's decorrelating capabilities, several tweaksarenecessary.Thesuggestedaffinetransformation forimagedecompositionencodinganddecodingmight be replacedwithanothertransformwithgreaterdecorrelating capabilitiesandlowcomputationalcost.
Younusetal.[12]establishedanovelstrategyfor video steganography that takes use of a suggested key functiontechniquetoencryptaconcealedinformation.This strategy was designed with the intention of making the systemmoresecure.Therecommendedmethodmakesuse of a major feature for encryption that consists of a configurationofrandomvaluesandallowsforthevaluesto bechangedwitheachtransaction.Thishelpstoincreasethe method'seffectivenessaswellasitsrobustness.Inrelation, the knight tour is used to enhance the Lsb method for embedding process inside the video sequence. This is accomplishedbyselectingtheembeddingpixelsatirregular intervals rather than in a sequential sort of manner, as is accomplished with the regular LSB. This prevents cybercriminals from determining out where the pixels constitutethesensitivedocumentsbymakingitimpossible for them to determine which pixel value constitute the
confidentialinfo.Inperspectiveofpeaksignal-to-noiseratio, meansquarederror,andimprovedsecurity,theresultsof the investigation indicate that the proposed technique is superiortothetechnologycurrentlyinuse.
3. METHODOLOGY
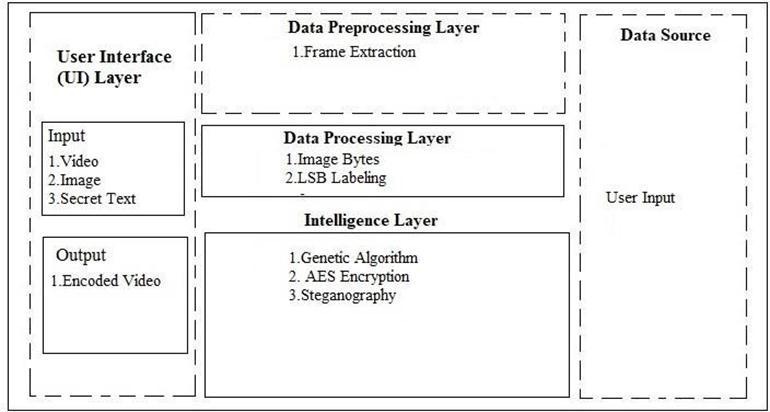
Shortvideosteganographyforimageandtextusing deepgeneticalgorithmandLSBisatechniqueusedtohide information in a video. This technique has many applications,includingsecurecommunication,datahiding, and watermarking. LSB embedding involves replacing the leastsignificantbitsofthecovervideo'spixelvalueswiththe bitsofthehiddeninformation.Thedeepgeneticalgorithmis used to optimize the embedding pattern to reduce the distortion caused by the hidden information while maximizingthecapacityofthehiddendata.
To ensure the confidentiality of the hidden information, encryptionisusedtoscramblethedatabeforeembedding. Theencryptionkeymustbeprovidedtothereceiverofthe steganographic video to decrypt and extract the hidden information.
Short video steganography for image and text using deep genetic algorithm and LSB is a secure way to hide information in a video. It can be used for various applications,includingsecurecommunication,datahiding, andwatermarking,toprovideanadditionallayerofsecurity andprivacy.
4. CONCLUSIONS
Inthis dayandageofmodernization, there isa wide rangeoftechnologicaladvancementsavailable,andanybody maysimplymakeuseoftheseadvancementstoimprovein theperformanceoftheiroperations.Ontheotherhand,as technologicalprogresscontinues,sodoesthesophistication ofcriminal activity.Specificallywithregardto the theft of dataandthepiratingofcontentbymaliciousactors.Theuse ofsteganographyitselfismethodamongseveral thatmay safeguard the transfer of data and so reduce the risk of fraudulent activity and infringement. Steganography is a
methodthatconcealsinformationindigitalpicturessothat it could be recognized by unauthorized individuals. This protectstheconfidentialityofthedatabeingcommunicated. Theprocedureofobtainingsteganographyonavideowas amongthemostcutting-edgeanddifficultundertakingsthat have been completed in past few years. Steganography is usedtohideinformationon videos.Therefore,inorder to accomplish video steganography, the suggested method utilizes AES Encryption, Frame Extraction, and a Genetic Algorithm for Frame Identification, and Least Significant BytesLabeling.Themethodologywillbeelaboratedoutin moredetailinsubsequentversionsofthisstudy.
5. ACKNOWLEGEMENT
We wouldliketo thank our Principal Dr.V.V.Dixit, Headofdepartment,ProfVinaM.Lomte,ourco-ordinator Asst. Prof. Sonal S. Fatangare and my guide Asst Prof.PradnyaKasturefortheirvaluableadviceandtechinal assistance.
REFERENCES
[1]Wu,Pin&Chang, Xuting &Yang,Yang&Li,Xiaoqiang. (2020). BASN Learning Steganography with a Binary Attention Mechanism. Future Internet. 12. 43. 10.3390/fi12030043.
[2] Fan, Pingan & Zhang, Hong & Zhao, Xianfeng. (2022). Robustvideosteganographyforsocialmediasharingbased on principal component analysis. EURASIP Journal on InformationSecurity.2022.10.1186/s13635-022-00130-z.
[3]Islam,Saiful&Nigam,Aditya&Mishra,Aayush&Kumar, Suraj. (2019). VStegNET: Video Steganography Network usingSpatio-TemporalfeaturesandMicro-Bottleneck.
[4] Rajkumar, Gat & Malemath, Virendra. (2017). Video Steganography:SecureDataHidingTechnique.International JournalofComputerNetworkandInformationSecurity.9. 38-45 10.5815/ijcnis.2017.09.05.
[5]Rehman,Atique&Rahim,Rafia&Nadeem,Muhammad& Hussain, Sibt. (2017). End-to-end Trained CNN EncodeDecoderNetworksforImageSteganography.
[6] A. U. Islam et al., "An improved image steganography techniquebasedonMSBusingbitdifferencing,"2016Sixth International Conference on Innovative Computing Technology (INTECH), 2016, pp. 265-269, DOI: 10.1109/INTECH.2016.7845020.
[7]S.Shakeela,P.Arulmozhivarman,R.Chudiwal,andS.Pal, "Doublecodingmechanismforrobustaudiodatahidingin videos," 2016 IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), 2016, pp. 997-1001, DOI: 10.1109/RTEICT.2016.7807979.

[8] P. A. Shofro, K. Widia, D. D. A. P. Astuti, E. H. Rachmawanto,D.R.I.M.Setiadi,andC.A.Sari,"Improved MessagePayloadandSecurityofImageSteganographyusing 3-3-2LSBandDualEncryption,"2018InternationalSeminar on Research of Information Technology and Intelligent Systems (ISRITI), 2018, pp. 158-162, DOI: 10.1109/ISRITI.2018.8864285.
[9]S.Kumar,N.K.Singh,A.Majumder,andS.Changder,"A Novel ApproachtoHideTextData inColourImage,"2018 7th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), 2018, pp. 577-581, DOI: 10.1109/ICRITO.2018.8748390.

[10] S. Chavan and Y. B. Gurav, "Lossless Tagged Visual Cryptography Scheme Using Bit Plane Slicing for Image Processing," 2018 International Conference on Inventive Research in Computing Applications (ICIRCA), 2018, pp. 1168-1172,DOI:10.1109/ICIRCA.2018.8596778.
[11]H.MathurandS.Veenadhari,"BlendedVectorMatrixon Different Channels of Image Encryption with Multi-Level DistinctFrequencyBasedChaoticApproachtoPreventCyber Crimes by Using Affine Transformation," 2018 Second InternationalConferenceonInventiveCommunicationand Computational Technologies (ICICCT), 2018, pp. 650-656, DOI:10.1109/ICICCT.2018.8473235.
[12] Younus, Zeyad Safaa and Younus, Ghada Thanoon. "VideoSteganographyUsingKnightTourAlgorithmandLSB MethodforEncryptedData"JournalofIntelligentSystems, vol. 29, no. 1, 2020, pp. 1216-1225. https://doi.org/10.1515/jisys-2018-0225
