ANDROID & FIREBASE BASED ANTI THEFT MOBILE APPLICATION
Vedang Nikure1 , Pranay Ikhar2, Vaibhav Kharalkar3 , Jayant manapure4 , Sweta Choudhari5, Harshad Kubade61 Assistant Professor, Department of Information Technology, Priyadarshini College Of Engineering, Nagpur, Maharashtra, India.

2 UG Students, Department of Information Technology, Priyadarshini College Of Engineering, Nagpur, Maharashtra, India.
Abstract - This initiative uses various GPS locations to locate stolen or lost phones. After installation, the program will run in the background. The unique user id and password, SIM number, backup phone number, email address, WhatsApp number, and present location of the phone are all stored in this application. When a phone is lost or stolen, the user receives images taken by the front camera, a GPS location on a different phone number, and an email address. With the help of this information, we can quickly identify the phone and the person who has stolen it using the intruder selfie feature in the app
Key Words: Mobile theft catcher, firebase, alert system, android application, smart notification.
1.INTRODUCTION
Onsmartphones,sensitiveinfoisstoredinlargequantities. The combination of this knowledge and smartphones' expensive price makes them a desirable target to feed physical theft. It goes without saying that the device proprietor would choose to reclaim the device in this circumstance. The info must also be protected from unauthorizedaccess.Inthis research, wepresent the first anti-theft strategy that addresses these issues. Our recommendation is based on an innovative concept for a theft-deterrenthoneypotaccountthatprotectstheperson's datawhilepreventingacriminalfromscrubbingthedevice clean.
Today's cell phones cost anywhere from 50k to 1.5 lakh rupees.Besidestothecash loss,a phone canalsohave its confidentialdatalostorstolen.Accordingtoasurvey,there weremorethan3.1millionmissingsmartphonesin2016.A separate study found that victims would spend about Rs. 41,069.33 to get back all of their private data, including photographsandvideos.Inturn,informationleakagetothe criminalispreventedandthereisahighprobabilitythatthe trueownerofastoleninstrumentwillbeabletoretrieveit. The smartphone is a necessity for everyone. They significantly improve day-to-day living. Nowadays, people usecellphonesforawiderangeofactivities,suchastaking photos,viewingtheinternet,andconductingonlinebanking.
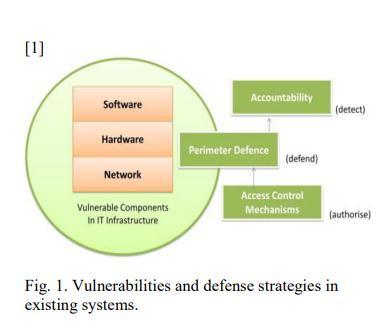
AsshowninFigure1.However,asmalwarebecomesmore sophisticatedandadvanced,ithasbeendiscoveredthatthe
perimeterdefencestrategy'sjointeffortsarebecomingless and less effective. Malware that is constantly changing appears to always find methods to completely avoid the perimeterdefence.Weprovideadetaileddescriptionofthe mostfrequentexploitationsatthehardware,software,and network levels of the current information system. The advantagesanddisadvantagesofthemostprevalentdefence strategiesemployedintheselevelsarethencovered
2. LITERATURE SURVEY
PriyadharshiniS.etal,[2]Machinelearningtechniques havebeenusedinthisstudytoidentifymaliciousAndroid applications.OpensourcedatasetsandKaggledatasetsare the ones who acquire the datasets. Here, data preparation and feature extraction methods are used to accelerate algorithmcomputation.Applyingdatapre processingtodata characteristics. In essence, it aids in normalizing the data within a certain region. Data pruning methods for feature extraction are employed. This document shows that data scienceisusedformalwaredetectionandaimstoexposethe use of machine learning (ML) methodologies for malware research.
IliyasuYahayaAdametal.,[3],theresearchdiscussessome securityissuesandpotentialbenefitsofmobilephonetracker
technologies, particularly for companies that buy and sell used mobile devices. Emerge in relation to the theft or disappearance of phones. Police may become involved in someoftheinstancesastheyconductdigitalinvestigationsto findtheoffenders.Somecomplainants'inabilitytoprovide information that will help the police conduct a successful investigationmayleadtothemistakenapprehendingofan innocent person or people as the perpetrator of a crime relatedto phone theft.In order to help phoneownersand prospectivebuyersandsellersofrefurbishedcellphoneswho want to safeguard their handsets from other GSM-related problems, the paper examines anti-theft and cellphone trackingtechnologies.
Abdulaziz Aldegheishem et al., [4], two innovative ETD modelsarecreatedinthisstudy.Inthefirstmodel,ahybrid samplingstrategyasyntheticminorityoversamplingmethod withaneditednearestneighborispresented.Additionally, dimensionality reduction and information extraction from data on energy consumption are done using AlexNet. A moderategradientboostingapproachisthenemployedfor categorization.Inthesecondmodel,theactualdistributionof thedataonelectricityusageiscapturedusingaconditional Wassersteingenerativestochasticnetworkwithagradient penalty.Tocreatemoreaccuratestatisticsfortheminority class, auxiliary provisional information is added to the formula. Additionally, GooLeNet architecture is used to minimizethedimensionalityofthedataset.
MichaelBecheretal.,[5],theworldispresentlytransitioning fromanInternet-basedtoamobilesociety,wherepreviously unremarkable phones are being used for an increasing amountofinformationaccess.Forinstance,between2016 and2023,theproportionofmobilephoneswithfull-fledged OS increased by almost 200%. Mobile protection is now necessaryratherthaninevitable.Thisreviewarticleoffersa succinctsummaryofmobilephonesecurity,attackvectors usingtheback-endsystemandthebrowseritself,aswellas thelayersofhardwareandtheuserasanattackenabler.We highlight the contrasts and parallels between "normal" security and security for smartphones, and we conclude futurestudydirections.
JulianJang-Jaccardetal.,[6],theoverwhelmingmajorityof businessesemployaperimeterdefencesecuritystrategyto shield their IT infrastructure from any potential outside intrusion. This approach places a strong emphasis on "layereddefence"or"defenseindepth"tactics,whichinvolve fortifyingandenclosingvitalinternalcomputerassets,such asserversorsensitivedata,toprotectthem.
SanjanaKuteetal.,[7],theresearchthatwillbedoneforthis thesiswillbeprimarilyfocusedondesigninganddeveloping an effective and convenient anti-theft device to address securityissuesthatwillhelptointerrelationship/stoptheft. The suggested system offers house protection and monitoring. Webcams with sensors installed assist in
identifying, notifying, and keeping users updated on trespassingevents.
ZhenyuChengetal.,[8],inthisarticle,wesuggesttheMobile Users'Informationdefendermodel,whicheffectivelydetects informationtheftbyusingconvolutionalneuralnetworksto analysetherelationshipbetweenusers'functioningpatterns and network flows. Most of the apps that steal collected information can't function correctly in reality due to Command-and-Control server invalidation,system version incompatibility,etc.
A. Shabtai et al., [9], in this article, we introduce a novel behavior-based anomaly identification method for the networkbehaviorofmobileapplications.Themainobjective of the suggested system is to safeguard users of mobile devices and providers of cellular infrastructure from fraudulentapplicationsbyfirstidentifyingmaliciousattacks orapplicationsthatposeaslegitimateonesthatareinstalled on a handheld device, and second identifying previously published,well-likedapplicationsthathavebeenrepackaged with malicious code. More specifically, wetry to identifya brand-newclassofmobileadwarethatcanupdateitselfthat wasjustdiscoveredonthemainGoogleAndroidmarket.
M.Contietal.,[10],thissystemwasfullyimplementedbythe authors,andwealsocarriedoutacomprehensivesetoftests thatdemonstratethatapproachcanachieveprecisionaswell asaccuracylevels higher than 92% for the majority of the actionstakenintoconsideration.Theauthorsofthisresearch evaluatedsolutionstothreecutting-edgealgorithms,andthe results showed that our solution outperforms all of these immediaterivals.

3. METHODOLOGY
3.1Problem Definition:
Personaldataisonamobilephone.Thereisachancethat thisinformationwillbemisusedifthephoneistaken.Any issues, whether they be personal or financial, could arise. Findingthestolenphoneisthereforeacrucialjob.Thereare someaccessibletechnologiesandmethods.Wecanidentify themissingphoneusingthat.Ifaphoneislostorstolenin India,theprocedureoffindingitbecomesextremelydifficult. Wemustfollowadrawn-outprocessandregisteracaseat the police station. To facilitate an easy and comfortable procedure we came up with the idea of anti-theft mobile application and its features are further elaborated in the belowsection.
3.2 Proposed Methodology:
activatingtheemergencywarning,TheftCatcher,alostphone finder,makessurethatanyonewhoobtainsyourphonegets intodifficulty.Eveniftheyswitchoffthedeviceoractivate airplanemode.Itwillcapturecovertpicturesoftheintruder andemailthemtoyou.Toassistinlocatingmissingphones,it additionally includes a cellphone tracker. False Shutdown, FakeAirplaneSetting,andIntruderDetectorarefeaturesof TheftCatcher.Alloftheseweredesignedtonotifyyourfamily totheirsafetyandtosendhelp.
Features of the Application

1. EmergencyContacts:
Hammer communicates live location updates, photos,andaudiofilestothoseclosesttoyouwhen itsensesanSOS.
2. FakeShutdown:
App Working:
Oncedeployed,itoperatesinthebackgroundsecretlytothe thief.
Whenatheftoccurs,theapplicationbeginstofunctionand provides a real-time Google Maps position of the stolen phone,aswellasanautomaticserverdatabackup.
Without the thief's knowledge, the application uses the front cameratocapturepicturesandvideosofhimorher and sends them along with their precise location to a registeredemailaddress.

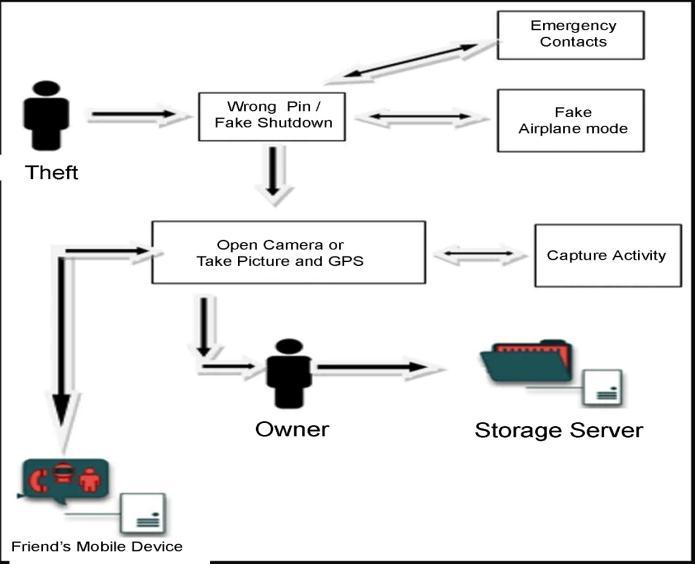
The application will pretend to Fake Shut Down while divertingtheuser'sfocus.
Regardless of whether the gadget has a mechanism for lockingornot,therearetwowaysthatitcanbestolen.Ifthe deviceisnotsecuredbyanunlockingmechanism,athiefwill haveinstantaccesstotheowner'sdataandmaymisuseuser data on the device such as credentials to cause the owner furtherdamage.Foraslongasthemechanismforunlocking is in position and the device is locked, it is useless to the burglar. Because of this, it will probably happen that the burglarwillcompletelyresetthedevice,whichwillresultin thelossofalluserdata.Nowadays,alotofimportantprivate data is stored on smartphones. Additionally, existing antitheft applications will also be removed from the device, greatlydecreasingthelikelihoodthatthedevice'susercan recoverit.[11]Thesetwopossibilitiesarenotsatisfactory. Therefore,a solutionisrequiredthatsafeguardsuserdata securitywhilepreventingunauthorizedfactoryresetsofthe device.Theauthorsofthisworkpresentthefirstmethodthat cansafeguardtheprivacyofadeviceowner'suserdatawhile prohibiting a thief from performing a factory reset and erasinganyanti theftsoftwarethathasbeenloaded.[11]By
Anytrackingapplicationintheuniverseisdisabled themomentyourphoneisturnedoff.Wemadethe decisiontoaddresstheunderlyingissueasaresult. Hammer will pretend that your phone is shutting down if someone attempts to do so, but it will actually send your Emergency Contacts a live location,pictures,andaudioinstead.
3. FakeAirplaneMode:
Hammer simulates an airplane mode state when someoneattemptstoactivateit,butinsteadsends livelocation,photos,andaudiostoyourcontactlist foremergencies.
4. IntruderSelfie:
Wewillsnapaphotoofyouandforwardittoyour registered email if someone repeatedly tries to unlockyourcelldevicewithoutsuccess.
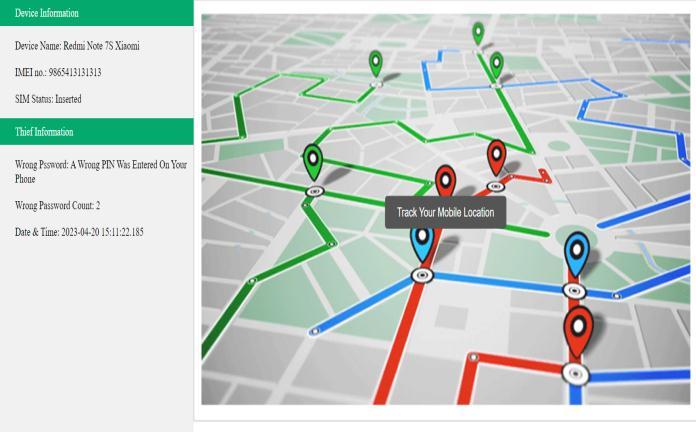
5. RESULT Splish
5. CONCLUSION
Our work on the Anti-Theft Mobile Application fulfils the needoftheuseroftheapplicationfortheprotectionoftheir contacts,bankinformation,andotherpersonalinformation fromthieves.Withthehelpoffirebasetechnology,wecan connect and send SMS to whoever we want, and with the user's legal permission, the phone's camera and contact access is taken to take action on the thief. The proposed applicationismadeusingjavatechnologyasitsbackendand XMLforfrontenddesigning.Thesuggestedideaisadaptable to different platforms and scenarios and is universal. Although this method is a crucial advancement in the creationofanti-theftmechanisms,ithasmorepotentialin thefuture.Potentialupgradesincludesafeguardingdifferent user data repositories, like the SIM card and device preferences.SincetheSIMcardisnolongerfrequentlyused tostorepersonaldataaswellasthedevicesettingsdonot holdhighlysensitiveinformation,thesestorageswerenot consideredinourapproach.Thedevelopmentofalternative methods that simulate the owner's account data from throughoutthehoneypotaccountisanotherareaoffuture work.[11]Theautomaticorsemi automaticgenerationof falsedataisoneofthesemethods.
6.REFERENCES
[1]S.N.JulianJang-Jaccard,"Asurveyofemergingthreatsin cybersecurity,,"JournalofComputerandSystemSciences,, Vols. Volume 80, ISSN 0022-0000,, no. Issue 5, https://doi.org/10.1016/j.jcss.2014.02.005.,pp.Pages973993,,2014,.

[2] S. P. a. S. Shanthi, "A Survey On Detecting Android Malware Using Machine Learning Technique," 7th International Conference on Advanced Computing and Communication Systems (ICACCS), no. doi: 10.1109/ICACCS51430.2021.9441712.,pp.pp.1621-1627,, Coimbatore,India,2021,
[3]C.V.A.V.IliyasuYahayaAdam,"ProblemsandProspects ofAnti-TheftandMobilePhoneTracking:AcaseinNigeria," 7th International Symposium on Digital Forensics and
Security (ISDFS), no. DOI:10.1109/ISDFS.2019.8757527, June2019.
[4] M. A. N. J. N. A. M. S. a. H. A. Abdulaziz Aldegheishem, "Towards Sustainable Energy Efficiency with Intelligent Electricity Theft Detection in Smart Grids Emphasising EnhancedNeural Networks,"IEEEAccess,vol.VOLUME9, no.DOI-10.1109/ACCESS.2021.30565664,2021.
[5] F. C. F. J. H. T. H. S. U. C. W. Michael Becher, "Mobile Security Catching Up? Revealing the Nuts and Bolts of the Security of Mobile Devices," IEEE Symposium on Security andPrivacy,vol.11,no.DOI10.1109/SP.2011.29,pp.10816011,2011.
[6]S.N.JulianJang-Jaccard,"Asurveyofemergingthreatsin cybersecurity," Journal of Computer and System Sciences, Vols. Volume 80, ISSN 0022-0000, no. Issue 5, doi.org/10.1016/j.jcss.2014.02.005., pp. Pages 973-993, 2014.
[7]R.P.V.M.M.G.SanjanaKute,"TheftDetectionSystem," Iconic Research and Engineering Journals, vol. Volume 4 Issue10,no.ISSN:2456-8880,April2021.

[8]X.C.Y.Z.S.L.a.J.X.ZhenyuCheng,"MUI-defender:CNNDriven,NetworkFlow-BasedInformationTheftDetectionfor MobileUsers,"LectureNotesoftheInstituteforComputer Sciences, Social Informatics and Telecommunications Engineering, Springer, vol. vol 268, no. doi.org/10.1007/978-3-030-12981-1_23.
[9]L.T.-C.D.M.L.R.B.S.Y.E.A.Shabtai,"Mobilemalware detection through analysis of deviations in application networkbehavior,"Computers&Security,vol.Volume43, no. ISSN 0167-4048, doi.org/10.1016/j.cose.2014.02.009, pp.Pages1-18,2014.
[10] L. V. M. R. S. a. N. V. V. M. Conti, "Analyzing Android EncryptedNetworkTraffictoIdentifyUserActions,"inIEEE TransactionsonInformationForensicsandSecurity,vol.vol. 11,no.doi:10.1109/TIFS.2015.2478741,pp.pp.114-125, Jan.2016.
[11] A. T. C. H. Sascha Groß, "ThiefTrap – An Anti-theft Framework for Android," Security and Privacy in Communication Networks, no. DOI:10.1007/978-3-31978813-5_9,pp.pp.167-184,January2018.
