CrAlSim: A Cryptography Algorithm Simulator
Avinash Singh1 , Swapnil Mane2 , Mihir Bist3 , Samuel Jacob4
1B.E. Information Technology, Dept. of Information Technology, Vidyalankar Institute of Technology, Maharashtra, India

2 B.E. Information Technology, Dept. of Information Technology, Vidyalankar Institute of Technology, Maharashtra,India
3B.E. Information Technology, Dept. of Information Technology, Vidyalankar Institute of Technology, Maharashtra, India
4Professor, Dept. of InformationTechnology, Vidyalankar Institute of Technology, Maharashtra, India ***
Abstract- Encryption algorithms are an essential part of Information Security, as they safeguard the messages sent between users, and also protect the integrity and confidentiality of the system. For students to understand the internal working of complex algorithms, it’s requisite that they don’t mug up the steps happening in the cipher, but rather will learn better if it happens to be a graphical visualization of everyevent happening inthe algorithm. This paper describes working of cryptographic algorithm simulation system. CrAlSim is based on matrix formation, stepwise color-based value change in code of the crypto algorithms, highlighted by each function showing the calculationright fromthe first tolast step ofencryption. The system created highlights how based on user inputs for a plain message or a key wherever required, how the actual inside conversions happen in an algorithm which led to the encryptions, be it a simple monoalphabetic cipher like Affine or blockcipher like AES (Advance EncryptionStandard). The encryption functions adjusted with the simulations are programmed in JavaScript, and simply HTML and CSS are used to display the web elements and styling, so understanding the source code even for creating of other algorithm visualization systems is comprehensible and apprehensible for a normal user. This paper elaborates the mechanism of CrAlSim and discusses the results obtained usingit.
Key Words: Simulator; Encryption; Decryption; AES; Affine; RSA; Peer to peer message confidentiality; Algorithm simulation.
1. INTRODUCTION
Nowadays, students often face the dilemma of choosing whether to take up security as one of their core domains. Since most students seem to face the problem in understanding various ciphers, they never chose to look further on how security works more than just simple cipher exchanging acknowledgement requests in SSL of presentationlayer[1].So,everyITstudentneedsaneasier guide to comprehend ciphers, be it of various types in an easy format. Since a picture is worth a thousand words, a step visualization simulation for demonstrating a cipher
working with all the components running over every input character is much better than 500 pages of algorithm in theory mode of a published author. As most students face this issue after reaching their second year in IT or Computer branch, they are the target audience of this website. Encryption algorithms are very essential to be learnt in the current era, asmalicious users most often are lookingforunsecureddatastreamsovertheinternet.Ifany attacks are launched, it can prove to be hazardous if sensitive data is revealed, and Government information, data related to financial sectors and other critical data can be leaked to foreign parties if it isn’t encrypted properly. Hence these encryption algorithms need to be studied, and canbebetterstudied bytraineeengineersorITstudentsif they learn it via a visualization tool which will enhance their perception of all stages happening in the code of certain algorithms [9]. Such a tool is CrAlSim which providesasimulatorforessentialcryptographicalgorithms.
1.1 Simulation Process
Visualization of algorithms is done using simple functions which target over the events which can be made graphical as so students or any user perceives those events in motion picturesorcolorhighlightsandhencebetterrepresentationof various operational fields of code can be shown. First step is selectionofcipherasinwhichcategoryofthealgorithmneeds to be visualized. For a single word string, monoalphabetic ciphers such as Affine are useful as their encryption can be based on just a certain length and for a block of letters; AES (Advanced Encryption Standard) cipher can be chosen. User thenneedstoinputthe proper type of the plain textmessage, as certain criteriais setfor certain ciphers based on length of string,orit’sstandardlanguageused.Thenthekeyisselected, orgenerated asperconditions,asRSAneedsveryhigh values forpropersecurity.Encryptionanddecryptionbuttonsshould be used to generate cipher text or decipher plain message. Note must be made of the special instructions in the process, explaining as in which kind of key to select, or what conversions are happening. Then controlling the flow of simulationusingthestart,play,pauseorresetbuttons.
2. LITERATURE SURVEY

Throughthissection,wesummarizesomeoftheexisting research work on either encryption or general simulation systems.
In January 2017, U. Arom-oon had proposed an AES cryptosystemfora small-scale network [2] Forlowpower sensor devices, the scale of the network based on wireless communication is quite small. To protect electronic data, FIPS 197 standard [12] encryption is used. Say a UAVs wireless communication network has microcontroller which works on real time operating system, so the main basisofsecurityischosenfromthecodebookwhichisone mode of AES method. In real time scenarios, scheduler decideswhichroletogetthenodbasedontheeventhaving the top priority. Hence no clash of system calls happen in the system. The basis of the accomplishment is decidedby the quality of security in communication of UAVs which consist of control and telemetry commands. The target hardwareisimplementedonthearmcortex-M4.
In December 2020,C.R.Martin proposeda systemofA New Simulation Algorithm for PDEVS (Discrete Event Systems Specification) Models [5]. The algorithm deals with the timing of code executions, as functions can’t be controlled in their flow of system calls just to wait for an animation packet to be displayed. In case of simulations, the user deals with the working of only general models and the corresponding DEVS simulations occur when the scheduled events are triggered. When system call occurs simultaneously inside a function for different events, processing happens with event A being executed firstly and later only event B is executed. But if animation call asks for the inputs simultaneously for different events, it may lead to incorrect and non-requisite results for simulation. So, in this paper, proposal of a new algorithm is laid out which makes sure that the model is such that output section of result is sent only on the condition that it’s given to a corresponding event at the appropriate simulationtimereceivedbythemodel.
In November 2021, A. Kabulov and M. Berdimurodov proposedasystemofoptimalrepresentationintheformof logical functions of microinstructions of cryptographic algorithms (RSA, El-Gamal) [6] According to the present study, the algorithms can be described by a set of microinstructions consisting of a sequence of operators. Based on an analysis of graphs, logic, algebraic, and matrix representationsofalgorithms,animplementationminimal logical representation for hard-drive implementation is constructed.
In September 2020, RahmaIsnaini Masya; Rizal Fathoni Aji; Setiadi Yazid proposed the Comparison of Vigenere Cipher and Affine Cipher in Three-pass Protocol for Securing Image [7] The aim of this study was to utilize Vigenere Cipher and Affine Cipher in Three-pass Protocol andcomparetheirencryptionresultsandexecutiontimeat
each stage of the protocol. The findings indicate that Affine Cipher outperforms Vigenere Cipher in terms of encryption results within the Three-pass Protocol. Different types of files, such as text, binary encoding for images, audio, and video, are frequently exchanged through the internet. The study focuses on securing images using classical cryptographyalgorithms.VigenereCipherandAffineCipher are implemented in Three-pass Protocol to eliminate the need for key exchange. The key is kept secure by each sender and recipient, making it impossible for attackers to obtainit.But,theexecutiontimeforAffineCipherinThreepassProtocolislongerthanthatofVigenereCipher.
InAugust2014,Y.Li,H.Zhang,H.JuandX.Jiangproposed a Visual Simulation Technique of Decision Making of Interactive Stand Management Methods [10] To adapt to intensive forest management, a technique platform was createdthat employs multiple visual simulation techniques. Thirteen stand management-related activities were customized and presented graphically using the WF technique. A flow model for decision-making during interactive stand management was developed based on human-computer interaction. The GDI+ drawing technique was used to simulate statistics of stand structure and state in2D,whiletheMOGREtechniquewasusedtosimulatethe stand scene in 3D. The effectiveness of the method was demonstrated by carrying out a case study of accretion cutting in a Chinese fir plantation, which showed that the methodwasflexible,visibleandoperable,andcouldbeused to create stand management flow models., The aforementioned approach has the ability to replicate the decision-making process involved in selecting the most suitable method from a set of techniques based on the decision-making criteria. It can be effectively implemented in stand management practices and can optimize the method selection by taking into account the specific stand management objectives, ultimately enhancing the overall scientificmanagementproficiency.
3. PROPOSED SYSTEM
Witha viewto simulatevarious cryptographic algorithms, therearisesthefeelingofobligationtocreatefunctionsbased onstepwisehandlingofthemessagedata.Thisoccurswhen various functions are written as per the flow of the code, synchronized with each cipher generation, setting color divisions, creating loops for multiple steps and conditions. After simulation is complete, final result is shown by displaying the resultant string, by rather selecting the comparisonoftheplaintext,orindifferentformatbasedon userselectedcipher.Thesimulator[11]parsesallthevalues of calculations in a table which show the inside configurations happening in each step, be it alphabets or numbers fed into a formula, or passing through rounds of a code.
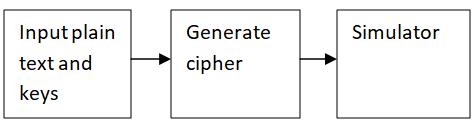
Detailed explanation about modules in Fig 3.1 is given below-
1. Inputplaintextandkeysmodule:Inmoduleone,oncethe userselectsthetypeofcipherheneeds,hemustinputhisplain text message, which can be either in standard format, or can includebasicpunctuationinconjunctionwithnumbers.Thekey orkeystobeselectedarementionedinthenote,forthecriteria needstobesatisfiedoverwhichtypesofkeyscanbeselected, e.g.,forAffineciphertwokeysaretobeselectedandtheyshould beco-prime,inAESblockcipher,akeycanbe128,192,or256 bits.Forourprojectpermissiblevaluechosenis128bitsonly, i.e.,16characters.
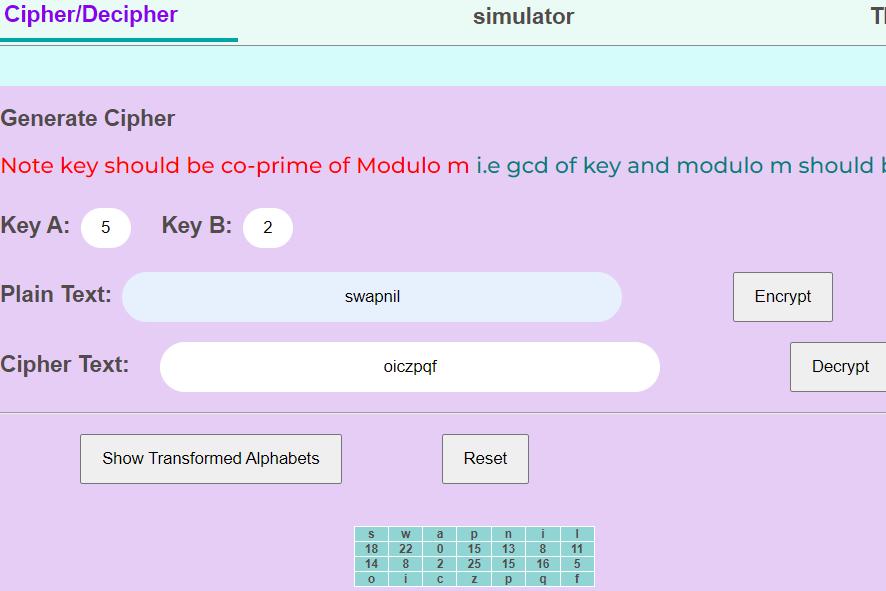
2. Generateciphermodule:Inmoduletwo,wechoosethe encryptionoption.Bygivinginproperinputsforplaintext messageandkeys,wecangenerateacipherbyclickingon the encrypt button. Following output is also shown on a general scale as in for Affine cipher, transformation of all alphabets is shown, hence user can tally how the change happenedinoriginalmessageandencryptedkeyword.
3. Simulator: It consists of a JS code which checks all the necessary conditions for encryption to begin, and then creates the graphical representation of the working of the code, based on each step, value is fetched into matrices or tables, each new alphabet or number currently under operationishighlightedbyacolororstylewhichindicates the current step in progression, final transformations are duly saved in a all calculated values table so user can go through all the formula and numeric changes happened overeachsteporround.
4. IMPLEMENTATION AND RESULTS

4.1 Implementation
As process is initiated in the first module, encryption processoccurs.Usergoestohomepageofourwebsiteand selects the cryptographic algorithm he wants to work upon,beitaffinecipherofmonoalphabetictype,AESofthe category included in block cipher or RSA [13] a part of asymmetric cipher. Then the user enters his plain text message, can be in alphabetical form of characters, punctuationmarksornumbers,thenanappropriatekeyis selected.Foraffinecipher,keyAandBshouldbeco-prime ofmodulo mi.e.,GCD ofkey andmodulo mshould be 1 as other combination result in two alphabets having same characterasacipher,sotheinverseconditionfails. Finally when all the clauses are satisfied, user can click on encryptionbuttonandgeneratethecipher.
In the second module, a graphical user interface (GUI) is rendered, as this is a tab where simulator works on the simulation [4], or graphical visualization of internal working of the algorithms. In correspondence to the highlighting of changes occurring in the code with respect toplaintext message, internal ciphercodefunctionrunsin synchronizedmanner.Basedonthat,valuetransformations happenwhichare exhibited via tables,matrices, or moving ofobjectvalues.Eachroundofthefunctionisdemonstrated for each block of code or a single character, and to control the narrative over whether to watch all the steps or just comprehend one of the transformations and then skip to the final output, set controls are provided such as play, pause, skip and start buttons. Internal working of all calculationsisshowninatable,orasinAESsimulation,All Value button functionality is provided where all XOR, multiplication operations are accounted for each round. Final output value is converted back into a string, as calculations inside the function happen for hexadecimal values.So,theresultantcipherisreturnedbacktothe user inmoduleone[15]
FlowchartforCrAlSimsystemisshownbelow:
Fig 4.1: Flow chart for working of CrAlSim
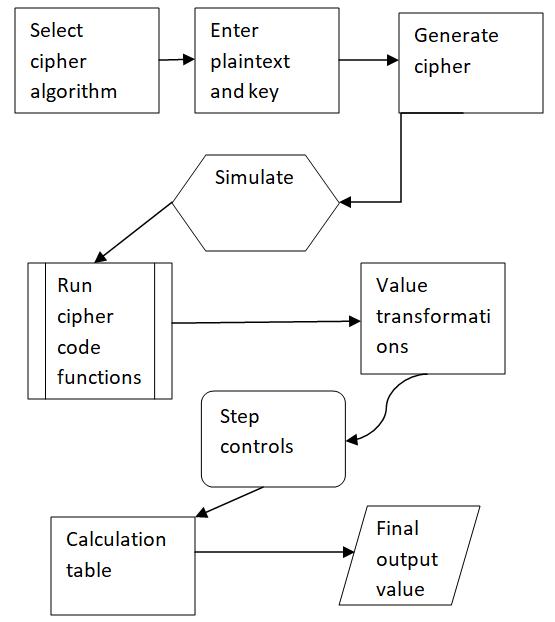
AsshowninFig4.1,CrAlSimcomprisesoftwomodules,one displaying the basic encryption and other the actual simulation of internal working of algorithm.
4.2 Results
Examples when checked through the system showed accurate visualization graphics as intended and suited for thecryptographicalgorithms.
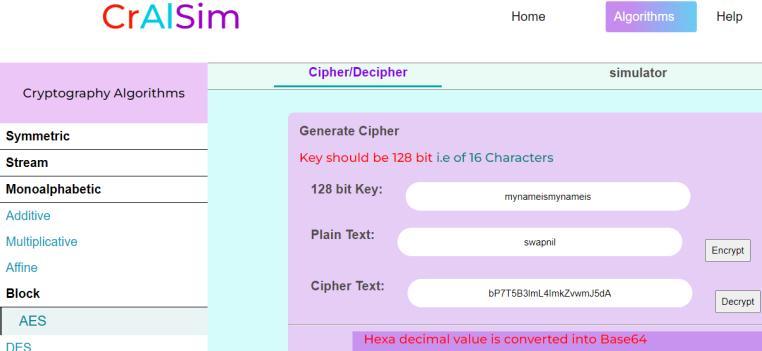
For plain text ‘swapnil’ and using 128 bits key ‘mynameismynameis’, cipher text generated after encryptionwas‘bP7T5B3lmL4ImkZvwmJ5dA’.
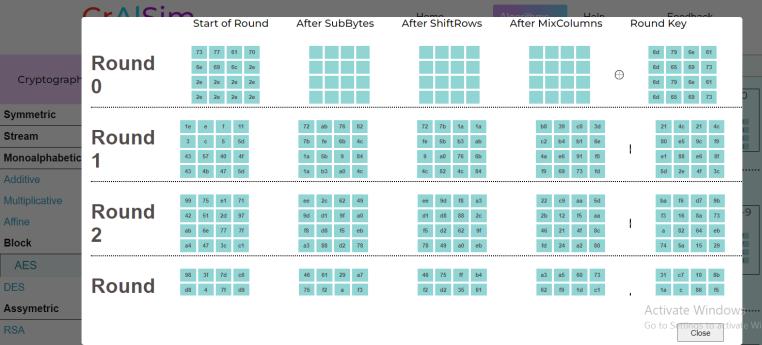
The initial round array meets various events, and undergoes transformations. SubBytes implements substitution using a lookup table also called the S-box, in next event, rows of the incoming 4*4 array are shifted certain times to left, MixColumns event does matrix multiplication and in final event Add Round Keys the resultant output of the previous stage is XOR-ed with the correspondingroundkey.
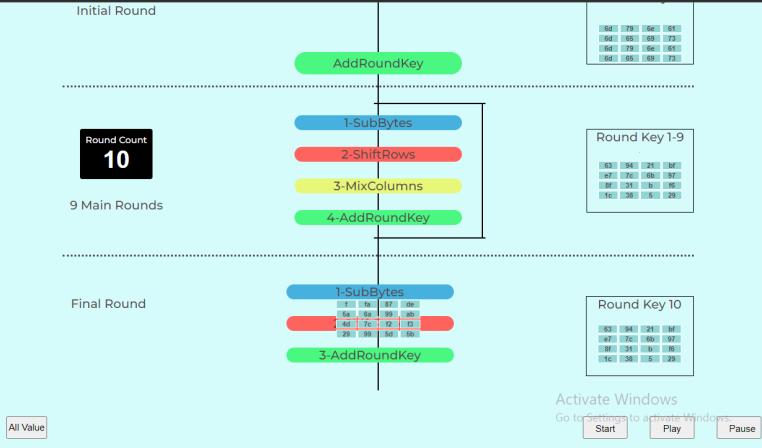
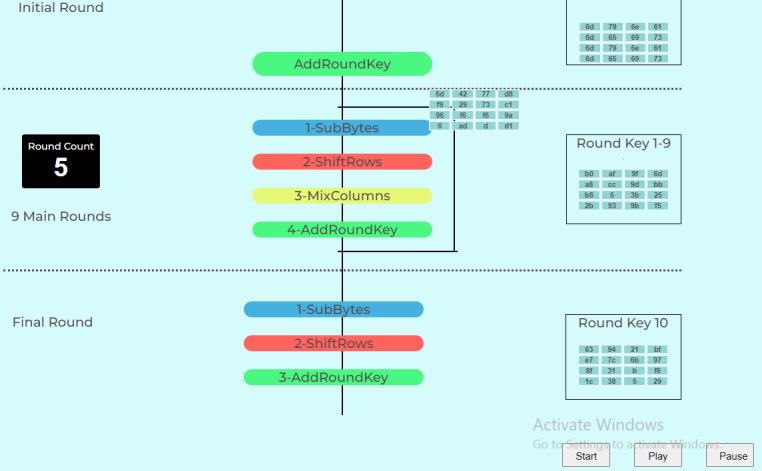
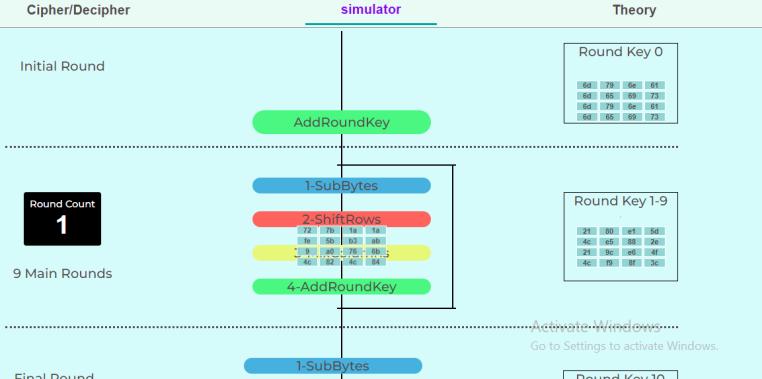
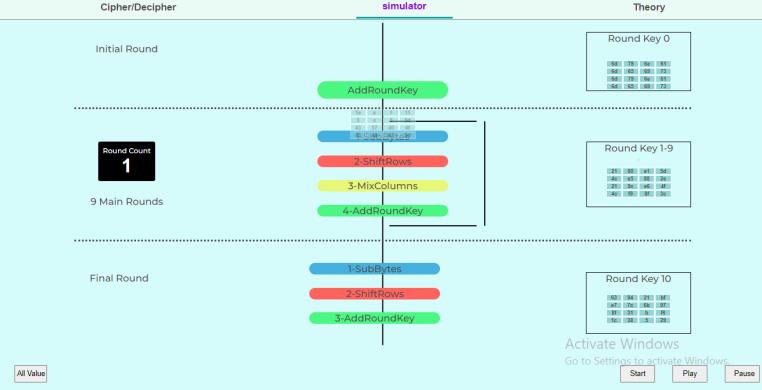
In initial round only XOR operation is performed between plain text converted into hexadecimal format put in a 4*4 array,(justlikeamatrixiscreatedinhillcipherwhereeach letter is represented by a number modulo 26) [8] along with the event round key word [0..3], and the output is calculated to the repetitive steps later in round 1.
All theabove events are repeated again ina cyclic loop 9 times,theoutputphotoshowshowthearrayofaddround keyeventwentbackasinputtoSubBytes.Acounterisset
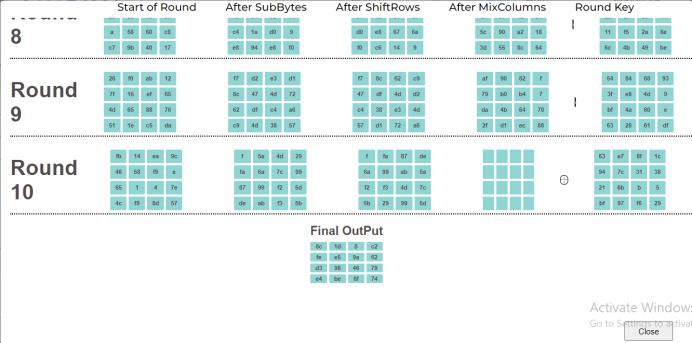
After all the in between process changes, final round outputisgeneratedandtheoutputshowshowthearrayis flowing through the process, with no MixColumns event.

All intermediary calculations of events in each round are shown in the All-Value page. Each XOR result, along with mathematicaloperationsofleftshifts,matrixmultiplication andsubstitutionscanbeseenindepth.
Key A is 5 and key B is given 2 as input, they satisfy the condition of being co-prime. Plain text is provided, and cipher is generated, and all transformed alphabets are represented in correspondence to their numeric values withletter‘a’startingfrom0.
Final output value is generated in a 4*4 array of hexadecimal value, which was converted back to base64 andshowninaproperstringtouserastheencryptedvalue in module one. As the output size remains same for an encrypted data, it can be compared to hashing which is irreversible, and helps in preventing possible issues of two encrypted strings having same input [16].
Affine:

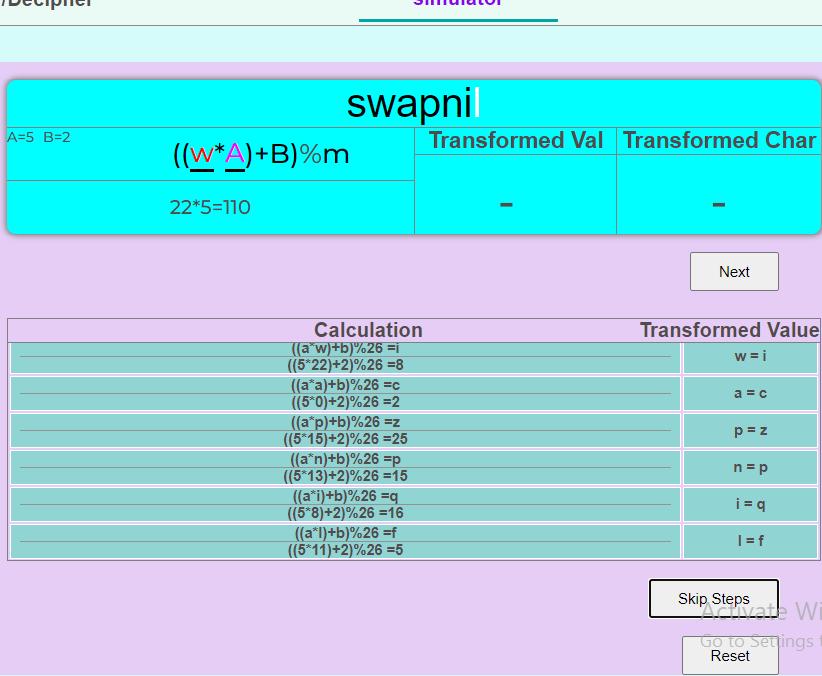
For plain text ‘swapnil’, each letter [19] is fed into the formula(ax+b)%m,andsubsequentcalculationsare
shown each time Next button is clicked. Calculation for letter‘s’isdone,soit’shighlightedinblack,currentletter underprocessis‘w’asitisseenincolorwhiteandyetto converted characters in gray. Every derivation and its resultant value are shown in transformation table with theircalculationsandchangesimplied.
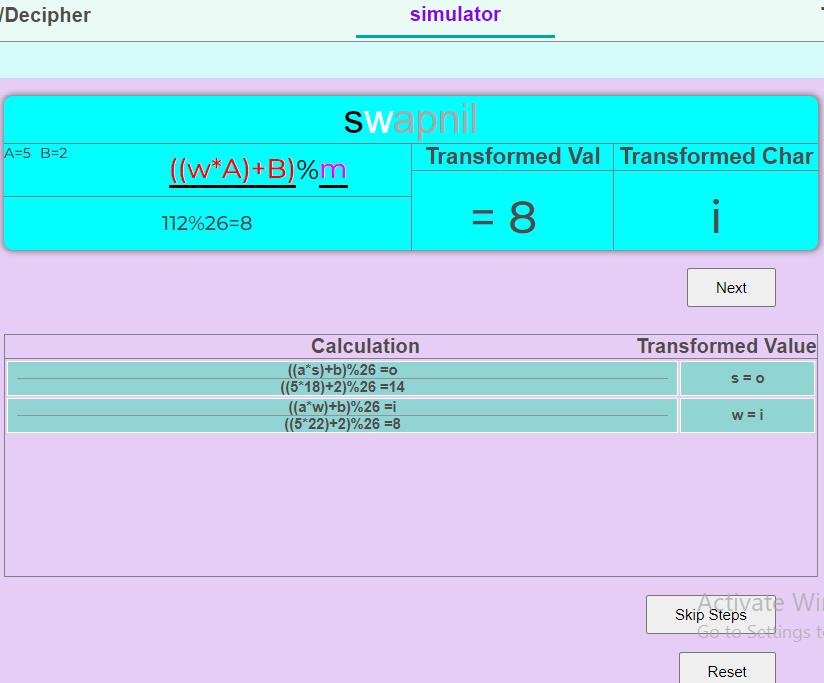
If the process is comprehended for one letter, going through each letter transformation can be tedious, hence skip steps leads us to eventual values and the output is completely generated with affine cipher.
5. CONCLUSIONS
This paper focused on the proposed visualization tool for cryptographic algorithms, and elaborately exhibited the graphical viewoftheinternal workingofa fewtypes. There are several encryption tools available over the internet, but not many visualization tools for these algorithms. No relationaldatabaseisusedtostorethesimulationsteps.The factor which makes CrAlSim advantageous is that the algorithmscoveredarethe primaryonesintheircategories, likeAffineinmonoalphabeticcipherandAESinblockcipher, simpledemonstrationis also madeforRSA [3],andthatthe complexcalculationsliketheinitialroundwithnoeventand 8roundsof4distinguishedeventsinaloopfor128bitskey in AES all can be visualized and understood rather than students mugging up theory of each step. The existing simulator on further upgrade can be imbibed with more enhancements like adding more in-depth simulations of the multipleroundsand events,addinga videobasedfeatureto download a mp4 file of an instance simulation, adding comparison factors to two similar inputs but different ciphers generated as output, and also more highlighting of certain events in color scheme as what to visualize is differentfromtheperceptionofeachuser.
REFERENCES
[1] L. Ogiela, M. R. Ogiela and U. Ogiela, "Cognitive information systems in secure information management and personalized cryptography," The city of Kitakyushu hosted the 2014 Joint 7th International Conference on Soft Computing and Intelligent Systems (SCIS) and the 15th International Symposium on Advanced Intelligent Systems (ISIS), Japan, 2014, pp. 1152-1157, doi: 10.1109/SCISISIS.2014.7044798
[2] U. Arom-oon, "An AES cryptosystem for small scale network," 2017 Third Asian Conference on Defence Technology (ACDT), Phuket, Thailand, 2017, pp. 4953,doi:10.1109/ACDT.2017.7886156.
[3] P. M. Aiswarya, A. Raj, D. John, L. Martin and G. Sreenu, "Binary RSA encryption algorithm," 2016 International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT), Kumaracoil, India, 2016, pp. 178-181,doi:10.1109/ICCICCT.2016.7987940.
[4] N. Buckley, A. Nagar and S. Arumugam, "Evolution of Visual Cryptography Basis Matrices with Binary Chromosomes," 2013 8th EUROSIM Congress on
ModellingandSimulation,Cardiff,UK,2013,pp.7-12, doi:10.1109/EUROSIM.2013.12.
[5] C. R. Martin, G. G. Trabes and G. A. Wainer, "A New Simulation Algorithm for PDEVS Models with Time Advance Zero," 2020 Winter Simulation Conference (WSC), Orlando, FL, USA, 2020, pp. 2208-2220, doi: 10.1109/WSC48552.2020.9384028.
[6] A. Kabulov and M. Berdimurodov, "Optimal representation in the form of logical functions of microinstructions of cryptographic algorithms (RSA, El-Gamal)," 2021 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 2021, pp.1-4,doi:10.1109/ICISCT52966.2021.9670149.
[7] R. I. Masya, R. F. Aji and S. Yazid, "Comparison of Vigenere Cipher and Affine Cipher in Three-pass Protocol for Securing Image," 2020 6th International Conference on Science and Technology (ICST), Yogyakarta, Indonesia, 2020, pp. 1-5, doi: 10.1109/ICST50505.2020.9732873.

[8] R.MahendranandK.Mani,"GenerationofKeyMatrix for Hill Cipher Encryption Using Classical Cipher," 2017 World Congress on Computing and Communication Technologies (WCCCT), Tiruchirappalli, India, 2017, pp. 51-54, doi: 10.1109/WCCCT.2016.22.
[9] M. Kocheta, N. Sujatha, K. Sivakanya, R. Srikanth, S. Shetty and P. V. Ananda Mohan, "A review of some recentstreamciphers,"2013Internationalconference on Circuits, Controls and Communications (CCUBE), Bengaluru, India, 2013, pp. 1-6, doi: 10.1109/CCUBE.2013.6718558.
[10] Y. Li, H. Zhang, H. Ju and X. Jiang, "Visual Simulation Technique of Decision Making of Interactive Stand Management Methods," 2014 International Conference on Virtual Reality and Visualization, Shenyang, China, 2014, pp. 459-466, doi: 10.1109/ICVRV.2014.37.
[11] Bloom, Yuval & Fields, Ilai & Maslennikov, Alona & Rozenman, Georgi. (2022). Quantum Cryptography A Simplified Undergraduate Experiment and Simulation. Physics. 4. 104-123. 10.3390/physics4010009.
[12] Walter Tuchman (1997). "A brief history of the data encryption standard". Internet besieged: countering cyberspace scofflaws. ACM Press/Addison-Wesley PublishingCo.NewYork,NY,USA.pp.275–280.
[13] Gurpreet K. and Vishal A., (2013), “An Efficient Implementation of RSA Algorithm using FPGA and BigPrime Digit”, International Journal of Computer & Communication Engineering Research (IJCCER), Volume1-Issue4.

[14] Alemami, Yahia & Mohamed, Mohamad A & Atiewi, Saleh. (2023). Advanced approach for encryption usingadvancedencryptionstandardwithchaoticmap. International Journal of Electrical and Computer Engineering (IJECE). 13. 10.11591/ijece.v13i2.pp1708-1723.
[15] A. Singh, “Comparatively analysis of AES, DES and SDES algorithms [9]” In 2014, the International Journal of Computer Science and Technology published a research paper titled "Comparative analysis of encryption algorithms for various types of data files for data security," authored by K. P. Karule andN.V.Nagrale.Thepaperwaspublishedinvolume 8491,issue3,andspannedpages200-202.
[16] M. M. Bachtiar,T. H.Ditanaya,S. Wasista,and R. R. K. Perdana, “Security enhancement of AES based encryption using dynamic salt algorithm,” in Proceedings of the 2018 International Conference on Applied Engineering, ICAE 2018, 2018, pp.1–6, doi:10.1109/INCAE.2018.8579381.
[17] M. I. Reddy, “A modified advanced encryption standard algorithm,” Journal of Mechanics of Continua and Mathematical Sciences, no. 1, pp. 112–117, 2020, doi: 10.26782/jmcms.spl.5/2020.01.00027.
[18] A. Hafsa, A. Sghaier, M. Zeghid, J. Malek, and M. Machhout, “An improved co-designed AES-ECC cryptosystem for secure data transmission,” in International Journal of Information and Computer Security, 2020, vol. 13, no. 1, pp. 118–140, doi: 10.1504/IJICS.2020.108145.
[19] Arroyo, Jan Carlo & Delima, Allemar Jhone. (2020). A Keystream-Based Affine Cipher for Dynamic Encryption.InternationalJournalofEmergingTrends in Engineering Research. 8. 2919-2922. 10.30534/ijeter/2020/06872020.
