Smart Surveillance System through Computer Vision
1Assistant Professor of Computer Science and Engineering, MIT College, Uttar Pradesh, India

2Student of Computer Science and Engineering, MIT College, Uttar Pradesh, India
3Student of Computer Science and Engineering, MIT College, Uttar Pradesh, India
4Student of Computer Science and Engineering, MIT College, Uttar Pradesh, India
5Student of Computer Science and Engineering, MIT College, Uttar Pradesh, India ***
Abstract -In safety and security lie at the heart of thewealth of nation. Every person wants to feel safe and secure from pitfalls. But today security is tough in allviewofourdailylives. This The usual surveillance system requires human interaction, to work more the number of cameras in home more human is required to monitor them. To deal with that problem, we suggest a smart surveillance system which is a python application made using high grew computer science field, which is “computer vision”. The computer vision is a branch of computer science in which we use digital data such as images, video, or real time data to extract beneficial information to deal with real time problems, for now in this paper we are mostly highlights the features of smart surveillance system that are object detection,facerecognition, object tracking, and alert system.
Key Words: Object Detection, Face Recognition, Object Tracking, Alert System
1. INTRODUCTION
Countless home and office security systems work on the same concept of security such as securing entry points of homeorofficessuchasdoors,windowsetc.forsecuritywe use,CCTVcameras,thatmightbeanissueusingthis,dueto countlessamount ofcamerasavailablein homeor offices, securityguardsseemstoalloverwatchingoverit,alsothe numberofexistingcamerasexceedsthenumberofsecurity guards to monitor them, that would be costly. By using computervisiontoolswithdeeplearningalgorithms,wecan detectweaponsandotherdangerousobjectsbyusingreal time footageaswell aspicturesandscenesfromvideo, to dealwiththethreat,sowecansaythatgrowthofcomputer visionisbeneficialforsociety.
Computer vision is fast growing especially in the realm of homesorofficessecuritytechnology.Itcontainsfeaturesthat cannotbeforgotten,faked,orlost,becausethroughcomputer vision,weareabletoscanCCTVinformationinrealtime,so that security teams are alert when someone breaches the security.
As we know that, face recognition is very good for authentication, because face is a physiological trait that is simplest to identify between two people, it is one of the forensics technologies that is always being research and developed.
ComputerVisionisafieldofartificialintelligence(AI)that enables computers to drive meaningful information from digital images, and other visual inputs. And act or make recommendations based onthat information. IfAI enables computers to think, computer vision enables them to see, observe,andunderstand.Computervisionworksmuchasthe humanvision,excepthumanshaveheadstart.Humansight hastheadvantageoflifetimeofcontexttotrainhowtotell objects apart, how far away they are, whether they are movingandwhetherthereissomethingwronginanimage. Computervisiontrainsmachinestoperformthesefunctions butithastodoitinmuchlesstimewithcameras,dataand algorithms rather than retinas, optics, nerves and a visual cortex.includingdetection,facerecognition,tracking,alert system, the project's objective is to develop a smart surveillance system that incorporates computer vision to facilitatesecurityinhomesandoffices.
Other research papers focused on constructing a security systemthatcanrecognizeaface,wherethisstudyscansfaces thathavebeenenteredintothedatabaseandthenmatches thephotosobtainedbythewebcam,iftheimageisnotmatch inthedatabase,analertisgeneratewithtrackingfeature.In thisproject,wecreatedasmartsurveillancesystem.Itaidsin theselectionofasuitableapproachfrommanyoptionsbased onourapplicationneeds,aswellastheresolutionofexisting difficultiesinreal-timeapplicationstosomeextent.Inrealtimescenarioswithmultiplevariablesandseamlesssettings, we obtain an accurate system. This technology may be described as an automated surveillance system. This techniqueisintendedtobeabletocombattheftinhomesthat arefrequentlyabandonedbytheirowners
Thisworkisexpectedtomakeasubstantialcontributiontoa new field of research on the use of face recognition, detection, tracking, and alert technology in surveillance systems.Asaresult,thepurposeofthisstudyistodevelopa smart surveillance system to enhancesecuritysystem and grammar.
2. REQUIREMENTS
As it is a software-based project. It must run on some hardware and operating system following are the requirementstorunthissoftware.
Windows/Linux/Macanyversionofpython3
PackagesinPython.
OpenCV.
NumPy.
FaceRecognition.
VisualStudioIDE.
IncaseofHardwarerequirements,youdon’tneedmuchbut stillsomeoftherequirementssuchas
WorkingPC.
Flashlight/LEDifusingthisatnight.
WebcamwithDriversInstalled.
3. METHODOLOGY
Inourprojectwehaveestablishedfeatures.Belowarethe different features which can be performed by using this project.
1. ObjectDetection
2. ObjectTracking.
3. FaceRecognition.
4. AlertSystem.
3.1 Object Detection
In this project our first task is to detect the instances of objectsofacertainclasswithinanimageorvideosandinreal time.Toperformobjectdetectioninrealtime,weuseobject detection techniques. Object detection technique is a computer technology related to computer vision, image processing,anddeeplearningthatdealswithdetectingthe instancesofobjectsinanimageorvideos.
Therearevarioustechniquesoralgorithmstoperformobject detection in real time such as R-CNN (Region- Based Convolutional Neural Networks), Fast R-CNN (Fast Region BasedConvolutionalNeuralNetworks),andYOLO(YouLook Only Once). In this project we use the YOLO algorithm to performobjectdetectioninrealtime
3.2 Object Detection

Afterdetectingtheinstancesofthevariousobjects,ournext task in our project is totrack the movement ofan objects. Object tracking usually involves the process of object detection.
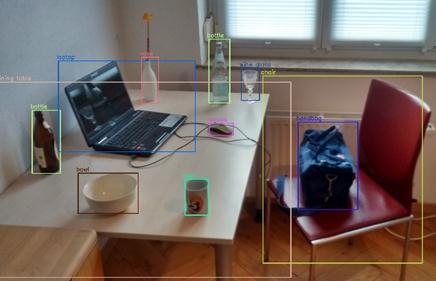
• Object detection, where the algorithm classifies and detectstheobjectbycreatingaboundingboxaroundit.
• Assigninguniqueidentificationforeachobject(ID).

• Trackingthedetectedobjectasitmovesthroughframes.
3.3 Face Recognition
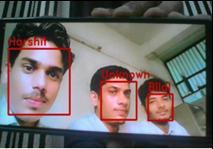
Afterdetectingtheinstancesofthevariousobjects,ourtaskis torecognizethefacesofthepersonappearinacamerarange. Toverifytheidentityoftheperson.Ifthefaceofthepersonis not match in the face recognition database, then alert is generatedbythesystemthroughSMS
3.4 Alert System
Ifanunknownpersonisdetectedbythesystem,thenalert willbegeneratedthroughtheSMSservice.Togeneratealert, weuse Twilio pythonlibrary which generates SMS. Twilio messagingAPIisbeingusedgloballytosendandreceiveSMS.
Theintelligencetrackingfeaturesenableusertocheckifthe messageisdeliveredornot.
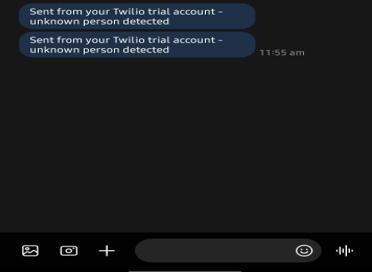
4.2 Flow Chart
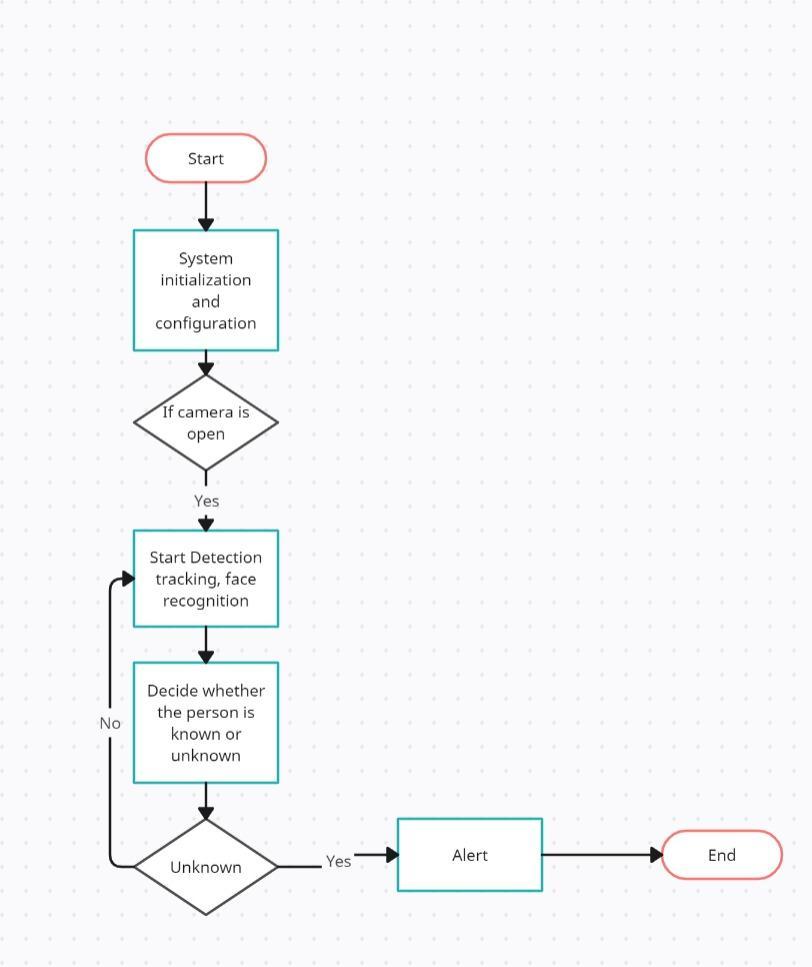
Forthe systemdesign,thedesigncanberepresentedusing theUse-CaseDiagramandflowchartDiagram.
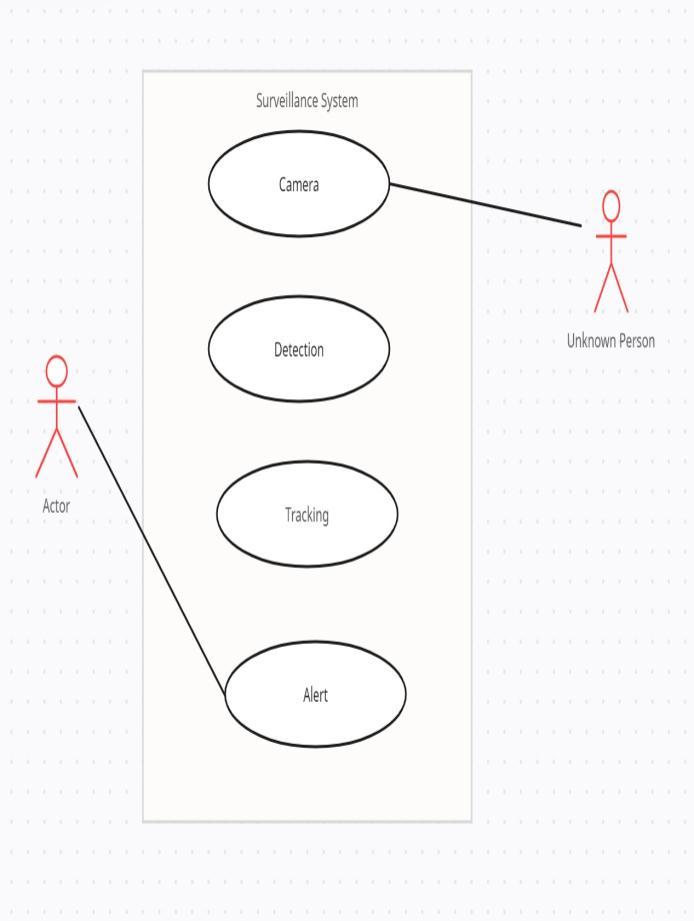
According to the use-case illustration above, when the unknownpersonisdetectedbythecamera throughobject detection, face recognition feature, a system generates the alertthroughSMStoinformsecuritysystem.

The smart surveillance system is initially initiated and configured, as shown in the flow chart diagram. After initializationandconfigurationofthesystemcameraofthe systemisinitiated,duetowhichdetection,tracking,andface recognitionoccurs,ifdetectingpersonisunknownthen,alert isgeneratedbythesystemthroughSMS.
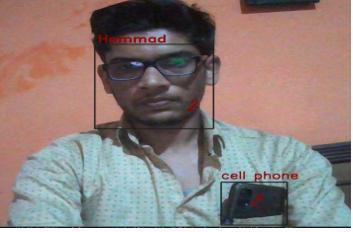
5. RESULTS

6. Future Scope
When smart surveillance systems (SSS) identifies when someoneoranythingtriestobreachasystemorresources. An alert is generated through SMS for detecting unknown person.However,withfuturedevelopment,adronecanbe used to track the unknown person’s location of unknown person by following the unknown person and provide the locationoftheunknownpersontothesecuritysystem.
7. CONCLUSIONS
Extensive research is going on in the field of computer vision.Inthisprojectwewillcompleteabitofworktocarry ontheproject.Themotiveistodetectinstancesofobjects,if persons detected then process the faces, and identify whetherthesefacesmatchinthefacerecognitiondatabase. If not match, then generate alert through SMS. Is still challengingtoenhancethesecurity,thesystemfailswhen thecameraisdamagedordoesnotworkproperly.

8. REFERENCES
[1] ArunHampapur,LisaBrown,JonathanConnell,Sharat Pankanti, Andrew Senior and Yingli Tian. Smart surveillance: - Applications, technologies and implications.ResearchGate.January2004.D.
[2] DayanaR,SuganyamM,BalajiP,MohammadThahirA, Arunkumar P. Smart surveillance system using Deep Learning. International journal of Recent Technology andEngineering.May2020
[3] PaulViola,MichaelJones.RapidObjectDetectionusing Boostedacascadeofsimplefeatures.Reserchgate.May 2004
[4] Kelvin salton do prado. Face Recognition on understandingLBPHAlgorithm.TowardsDatascience. Nov2017K.
