Digital Image Sham Detection Using Deep Learning
Divya SrivathsaAbstract“Digital Image Sham Detection Using Deep Learning”, Capturing images day by day as been increasing since there are availability of variety of cameras. Images as become a part in our daily lives because they contain an lot of information and sometimes it is also required to capture extra images to find additional information. This increases the grievousness and recurrence of fake image, which is now a major source of concern. A lot of customary techniques have been come into being over time to detect image falsification. In recent years, convolutional neural networks (CNNs) have come across much intentness, and CNN has also supremacy the field of image forgery detection. Even so, most image falsification techniques based on CNN that survive in the literature are limited to detecting a distinct type of sham . As a result, a technique capable of logically and well aimed detecting the presence of out of sight forgeries in an image is required.
Key Words: Image, Detection, CNN
1.INTRODUCTION
Now-a-days a handful of software are accessible that are usedtoexploitimagesothattheimageisalookalikeofthe unedited.Imagesarecast-offassubstantiategalleyforany offenceandiftheseimagedoesnotremainveritablethenit will causean issue. Inthisscientific era a large number of peoplehavebecomecasualtyofimagefalsification.
A large number of people operate technology to modify images and use it as verification to mislead the court. Image manipulation is any type of operation that is accomplishedondigitalimagesbyutilizinganysoftware,it isalsomentionedasimagepolish.So,toendtothis,allthe images that are allocated through social media should be designatedasoriginalorfrauderrorless.
Social media is a huge party line to mingle, split andwidenknowledgebutifheedfulnessisnotemployed,it can misguide people and even cause devastation due to unwitting false advocacy. Image tampering is a type of image falsification which return some content of an image with up to date content. If the up to date content is emulatedfromthesameimageitselfthenitiscalledcopymove tampering and if the up to date content is emulated
from non-identical image then it is known as image splicing.
1.1 Overview
Numerous methods have been uplifted in the literature to compact with image falsification. The large numberofconventionalmethodologyarebasedonspecific artefact left by image falsification, whereas fresh techniques based on CNNs and deep learning were established, which are brought up below. First, we will mention the various orthodox techniques and then progressontodeeplearningbasedtechniques.Itprovides twolevelinspectionfortheimage.Atfirstlevel,it examine the image metadata. Image metadata is not that much authentic since it can be changed using effortless programs. But most of the images we come across will have nonchanged metadata which helps to figure out the changes.
1.2 Problem Statement
Since the innovation of photography, individuals and company have often look for paths to modify and manipulateimagesinordertodefraudtheviewer.Existing systemshaveworkedonthecontrastofimagefalsification identification methods, these are frequently narrowed in spanandonlyweighupalternateoftheidenticalalgorithm on images that are expressly fabricate for that type of routine. There are also shamed images which cannot be identifiedbytheexistingapplications.
2. EXISTING SYSTEM
In existing forgery image detection system, it can be use to detect only limited type of image forgery like splicing and copy-move and not able to detect all types of forgery images.
Using new technologies any images can be forged with help of variety of tools available in the internet which makes impossible for humans to differentiate whether an imageisforgedornot.
Even withthehelp ofcomplexneural network itis nearly impossibletodetermineforgedornot.

3.PROPOSED SYSTEM
In this proposed system the application is able to detect whether an image is forged or not for all types of forged images like copy-move, splicing, tampering, morphingetc.,heretheapplicationusesVGG16andVGG19 algorithm and with the help of learning rate 0.0001 the VGG16andVGG19algorithmgives100%accuracyandfor comparison purpose this system also uses error detection analysesalso. Theprocesshowapplicationworksare
-First it will train the model using the provided datasets.

-Then in testing the user can choose one analyses type out of three and as to put an image for the test then theresultispublishedintheformofPieChart.
The main advantage of this system is the user can clearly compare with each algorithm to check the image originalityandthendecidewhattodowiththatimage.
4. SYSTEM ARCHITECTURE
Maintaining Authenticity: Most of the images are often usedasevidenceinlegalandinvestigativecontextsaswell asinjournalisticanddocumentarycontexts.
Preventing misinformation: In today’s generation any imagecanbeforgedaccordingtotheneedsandcanspread false information for the society which is very dangerous. Withthehelpofdetectionsystemthiscanbeprevented.
ProtectingIntellectualProperty:Imageforgerycanalsobe used to steal intellectual property of an artist. Detecting imageforgerycanhelpprotecttherightsofthecreator.
Overall, image forgery detection is essential for maintain the integrity of images and ensuring that they are used appropriatelyandaccuratelyinavarietyofcontexts.
6. IMAGE FORGERY TYPES
The image may be forged either by adding, removing or replacing some regions in the original image with only one thing in mind that it leaves no visually detectabletrace.Theimagecanbeforgedbyusingseveral methods,thesemethodsarecommonlycategorized

Fig-1 Architecture of Image Forgery
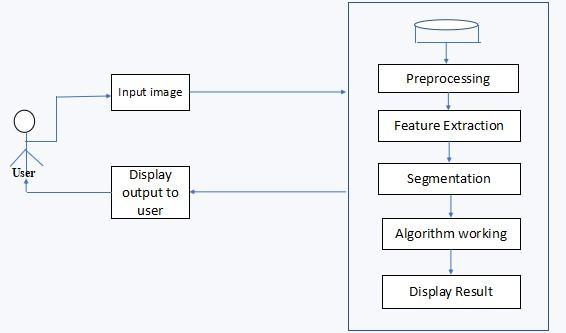
The system architecture defines the way how the system is designed. It also defines the relationship with other components and other aspects of software and reflects how it interacts with other systems and outside world. The architecture above describes the proposed system. It describes the way this system is developed and how it is connected to other components and the working flowofit.
5. Need of Digital Image Forgery Detection
The image forgery detection is very important nowadays because of rapid growth in the technology field there are many tools using which any one can tamper the original image and it will be very harmful if they use it in a bad way. So, it is very important to distinguish between authenticate image and the fake image which human cannot do it with their eyes. Image forgery detection is importantinmanyaspectssuchas,
Fig-2 Types of Image Forgery
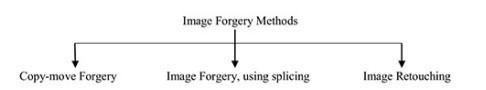
6.1 Copy Mover Forgery
Copy-Move Forgery means duplicating some part oftheimageandreplacinginotherpartofthesameimage asshowninbelowfigure.Theintentionofthisistoconceal some part of the image information. It is the most usually utilized methods to forge an image. As the forged part of the image remains in the same image itself. Therefore, its detectionisusuallytough.
6.2 Image Forgery, using retouching
It is the process of combining more than one image.Theimagesarecombinedtomakeanalteredimage. It uses cut/copy paste operations. A bit of one image is taken and pasted onto some other image. In order to completely connect the cut/copied part of an image into another image as shown in the above figure, it need some additional postprocessing operations. The pasted portion alters the pattern of the image. Thus, analysis of image patternhelpsindetectionofimageforgery.
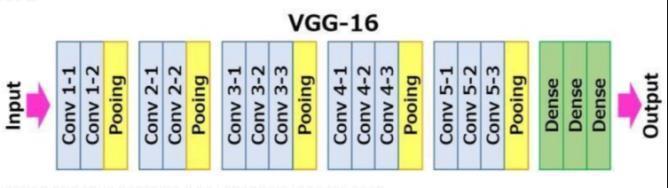
7. ALGORITHM
Fig-4 Convolution layers of VGG-16 Algorithm
Step 1:
InputImage:Animagefromthetrainingdatasetsistaken.
Step 2:
ImageProcessing:Scaledowntheimage pixelandconvert themintonumpy.
1. Filtering: Suppress the high frequency and smoothentheimage.
2. Padding: To have zero padding so that the output doesnotdifferfromtheinputimage.
Step 3:
Data preprocessed: Flipping the images vertically and horizontally.
1. 2D/3D convolution: To perform element wise multiplication.
2. Pooling: (Ih-f+1) / S*Ic (Ih- Image height, IwImage width, Ic- Number of channels in feature, f-filter, sStridelength)
Step 4:
Activationfunction:Basedonthetestcasesitactivatesthe modelalongwithbackgroundverification.
Step 5:
Output: Predicts the image score whether the image is originalimageorforged.
Step 6: End
8. MODULE
DESCRIPTION

i. Tensor Flow
A free and comprehensive open-source software library for artificial intelligence and machine learning is called TensorFlow.Thecreationandtrainingofmachinelearning modelsuseit.
ii. Keras

The Keras high-level Python library runs on top of the TensorFlow framework and is small, simple to learn and effective. It is made with an emphasis on comprehending deeplearningmethodologies.
iii. pyQt
It is a python binding for Qt, a collection of libraries and development tools that offer abstractions for graphical userinterfacesregardlessofplatform.
iv. Pillow [Pi]
All the fundamental image processing capabilities are available in the pillow library. It supports a wide range of picturefiletypesforopening,editingandsaving.
v. Epoch
Theentirenumberofinteractionsofallthetrainingdatain one cycle for training the machine learning model is referred to as all the training data and is utilized all at once.
10. EXPERIMENTAL RESULTS

In this project we are majorly using VGG-16 and VGG-19 algorithm. The reason behind using these algorithms is that the accuracy of these two algorithms is toohighincomparisontoothers.Also,thisprojectdelivers 98.8% accuracy to all the datasets provided. The results areshownasbelow.
Snapshot Results of the Experiment
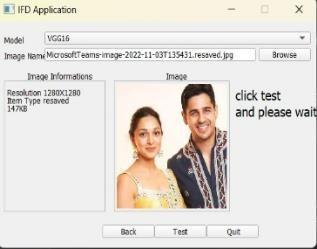
(a) WindowofImageForgerydetection.
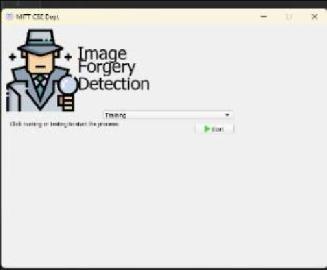
(b) Epochfortrainingdatasets.
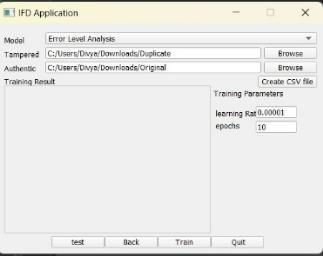
(c) Resultoftrainingdata.
(d) Epochfortestingdatasets.
(e) Resultoftestingdatasets.
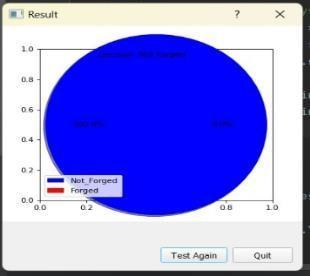
11. CONCLUSIONS
In this study, multiple passive picture forgery detection methods were sketched out. A thorough examination of several forgery detection methods is also provided. In addition, this publication offers a variety of data sets that may be used with various forgery detection strategies. Theprimaryshortcoming ofcurrentlyavailable forgery detection methods is that they require human intervention in order to be detected. The failure of the procedures up to this point to distinguish between malicious and lawful tampering is another significant flaw in their design. Additionally, the discussed methods are only designed to detect the forgery type for which they were developed. Therefore, a comprehensive, reliable method to spot any kind of image forgery is required A potential solution for digital picture forensics is proposed with the development of powerful artificial intelligence algorithms. Although deep-learning-based methods show promise, theylack the powerto perform well ina number of digital image forensics applications. All of these parametersstillrequirealotofworktobedone.
ACKNOWLEDGEMENT
We would like to give Prof. Hemanth.C, our project leader, our heartfelt appreciation for leading us through this project, for sharing his invaluable insights and recommendations with us, thus helping us better it beyond our wildest expectations. Secondly, we would like to express our gratitude to our project coordinators, Dr. Ranjit K. N. and Dr. HK Chethan, who continuously encouraged us and assisted us in completing this project within the allotted timeframe. We also want to extend our sincere gratitude to our department's head, Dr. Ranjit KN, for giving us a venue to work on
projects and show how our academic curriculum isput touseinthe real world. We would like to thankDr. Y TKrishne Gowda, our principal, for giving usthe chance to complete this amazing project on the topicof"Digital ImageShamDetection."Thisprojecthas also assisted us in conducting extensive research and learninghowtoputitintopractice.
REFERENCES
[1]Mukesh M.Goswami and Zankhana J. Barad, [2020] "ImageForgeryDetectionUsingDeepLearning",
[2] P. Lavanya, B. Jagruti, M. Srinidhi, and P. Mallesh,"ImageForgeryDetection",[2022]

[3] A review of "A review on Digital Image Forgery Detection" by Jahnavi Ega, Deepak Sri Sai Krishna, and V.M. Manikandan was published in [2021].
[4] Kshitij Swapnil Jain, Udit Amit Patel, and Rushab Kheni, "Handwritten signatures forgery detection",[2021]
[5] Francesco Marra, "A Full-Image resolution End-toEnd Trainable CNN Framework for Image ForgeryDetection"[2020]
[6] "Detection of Image Forgery" [2020] by ShubhamSharmaandSudeekshaVerma
[7] S Prayla Shyry, Mahitha Moganti, and Saranya Meka, "Digital Image Forgery Detection" [2019].
[8] "Copy-Move Forgery Classification via UnsupervisedDomainAdaptation"byAkashKumarand ArnavBhavsarwaspublishedin2019.
