Automated Invigilation System for Detection of Suspicious Activities During Examination
1, Assistant Professor, Department of Computer Science and Engineering, Jnana Vikas Institute of Technology, Karnataka, India

2,3,4,5 Undergraduate student, Department of Computer Science and Engineering, Jnana Vikas Institute of Technology, Karnataka, India ***
Abstract –Automated invigilation systems are software programs that monitor examinations and look for suspect activity using a variety of methods, including facial recognition, eye tracking, and screen recording. These systems have the power to completely alter the way exams are administered, enabling a more effective and efficient methodofcombatingcheating.However,usingsuchsystems raises privacy and ethical issues, so the choice to do so should be carefully weighed against any potential advantages and disadvantages. To guarantee that such systems are used morally and with regard for students' privacy rights, it is essential to establish them with transparency and explicit standards. In the end, other strategies for guaranteeing academic integrity, such bettering instruction, should be balanced with the use of automatedinvigilationtechnologies.
Education institutions resolve student strength and weakness through the examinations. Academic dishonesty has been constantly been worrying factors for the institutes in education system. Cheating and abnormal activities which includes like whispering, impersonation or hand contact these are widely involved in the exams around the globe, this research purpose is to examine and identify the abnormal/malpractices undertaking during the period of exams which results in inequality or unfair examination system. Automated video surveillance which roots image and video processing which is an optimal solution for monitoring the students activities during the offline examination. The proposed system automatically alerts the management when there is any suspicious activities are identified. The proposed system walk through various process- pre-processing, segmentation, classification, feature extraction and related works in sequential manner. The proposed model is effective, efficient and relatively less processingpower.
Key Words: Video surveillance, impersonation, segmentation,featureextraction,suspicious
1. INTRODUCTION
In recent years, automated invigilation systems have drawn increased interest as a potential means of combating exam cheating. When suspect activity is
observed during exams, these systems use cutting-edge technologies like facial recognition, eye tracking, and screen recording to alert human examiners for additional investigation. The process of invigilation will be made moreeffectiveandefficient,andacademicintegritywillbe improved.
In recent years, automated invigilation systems have drawn increased interest as a potential means of combating exam cheating. When suspect activity is observed during exams, these systems use cutting-edge technologies like facial recognition, eye tracking, and screen recording to alert human examiners for additional investigation. The process of invigilation will be made moreeffectiveandefficient,andacademicintegritywillbe improved.
The traditional method of invigilation/examinations, involves in human invigilators to present in examination hall to monitoring the students. The more number of studentsrequiresmorenumberofinvigilatorstobringthe quality in education and for the fair conduction of examination. A invigilation system is required to prevent cheatingandtoavoidanymalpracticesinexaminationsas itdirectlyimpactsthestudentsmorality.
A system based on computer artificial intelligence is proposedforthedetectionofcheatingbythemovementof head and neck movements through the surveillance camera.Thesystemismorebetterandmoreeffectivethan the traditional invigilation system hence it does not requiresmuchlabor,energy,effortandtime.
Automated invigilation systems offer several benefits, such as reducing the likelihood of cheating, improving examsecurityandensuring fairnessforall students.They can also save time and resources for educational institutions as fewer human invigilators are needed to monitor the exams. There are also potential downsides including concerns about privacy, accuracy, and the potentialforthetechnologytobemisused.
Theproposedsystemdetectsthesuspicious activitiesand cheating works done by the students during the examination. Detection of the cheating activities in the
classroom is implemented by the system using the YOLO (you Only Look Once ) algorithm. The proposed model will be able to process the real time automated videos using the existing dataset of the student and various activities will analyzed which is happening in the examination.
Examination malpractice or cheating is any form of unlawful activity in an examination center. It is most dangerous practice, which must be avoided since this should not be a reason which impacts negative effect on the society. In this paper, proposed a system that detects and recognized the cheating done by the students in the examination hall. Despite these concerns, automated invigilation systems are still being investigated as a potential means of enhancing academic integrity in educational institutions. The effectiveness, constraints, and ethical ramifications of automated invigilation systems will all be covered in this essay. The paper will also go over the necessity for a well-rounded approach to academic integrity, which includes enhancing teaching methods,supportingstudents,andtakingintoaccountthe applicationofvarioustechnologiestoimproveinvigilation procedures.
2. LITRATURE REVIEW
Automatedinvigilationsystemisacomputerbasedsystem that is used to monitor the students and detect the suspicious activities during examination among the students.Itisdesignedtoreducetheincidenceofacademic dishonestyandfairconductionoftheexamsbymonitoring thestudentsactionsinreal-timeusingacombinedversions of computer vision and machine learning algorithms. The purposeofthisliteraturereviewistoexaminetheexisting researchonautomatedinvigilationsystemfordetectionof suspiciousactivitiesduringtheexamination.
1.
MonitoringandAssessment of
The authors developed an automated invigilation system that uses computer vision and machine learningalgorithmstomonitorthestudentactions during the examinations. It presents multimedia analyticssystemforonlineproctoring,whichaims to maintain academic integrity in e-learning. User verification, text decoration, speech detection, active window detection, gaze estimation and phone detection, these are the features acquired from the analysis and then used for the cheat detection. The capability of the system, nearly 87%segmentbaseddetectionrateacrossalltypes ofcheatingbehaviorsatafixedFARof2%.
2. “Detection of Cheating Behaviors in Online Exams Using an Automated Invigilation System”

Cheating detection and prevention methods are needed to combat forbidden actions. Detection methods without applying prevention methods could not be affective. As cheating detection and prevention methods are evolved, new cheating types and technologies emerge as well. The HAR that employs a deep learning model based on MobileNetV2 architecture. The data was derived fromavideoclipofapersontakinganonlineexam using a webcam capture. When employing hyperparameters such as max epoch of 20, a learning rateof0.0001,abatchsizeof16,andadenselayer offive,thedeeplearningmodelwithMobileNetV2 architecture achieved optimal performances. The evolution findings have an F1-score of 84.52% .The primary objective of, after creation of the optimal model was identified is thecreation ofan Indonesian-language web based application. This is unquestionably a tool that may be used to advanceeducationaltechnologyinIndonesia.
RCNN is a deep learning model implemented for object detection and classification. It gives the accurate results and better accuracy as compared tootherCNNmodelsforinvigilatingpurposes.The proposed model implemented as a binary classifier to classify students activities into two categories : cheating; and No cheating. The no cheating label is considered for the students who are doing their paper as obedient in a perfection manner and the cheating label is considered to those students who are continuously looking left, right and peeking to other student papers for cheating.
Invigilation dataset with training accuracy of 99.5 and a test accuracy of the model 98.5. student identificationandrecognitionarewithanaccuracy 95&. The results of the both the faster runner classifier and face recognition module are combines and students status reports are generated.
The existing invigilator-exam assignment system in the university under consideration has some
problems like time and man power needed for constructingtheassignment.
A user-friendly decision support system based on a multi-objective mixed-integer programming model is introduced for invigilator-exam assignment problem with an eye to practical use. The system has a appropriate facilities for providing help to the users to implement an assignmentschedule.

Comparing with the current invigilator-exam assignments for 2004-2005 spring midterm and final exam terms, it is seen that the required time fortheassignmentsisdroppedofffromafewdays toseconds.AIASreachesoptimumresultsinafew seconds.
Automated invigilation system are an effective way to reduce academic dishonesty during exams. The systems use computer vision and machine learning algorithms to monitorthestudentactionsanddetectsuspiciousactivities such as copying pasting switching between windows, and using unauthorized access devices. The existing research on automated invigilation system that these systems are effectiveinreducingacademicdishonesty.
Table -1: Summaryofresearchwork
Themaincontributionsmadetothisstudyareasfollows:
A novel system has been developed that can identify and recognize students cheating in the examination.Theyolov3architecturewaschanged by replacing the parameters and backbone architecture.
Generated the local dataset of invigilation of studentsintheexamination.
3. METHODOLOGY
3.1 Data Preparation
Data preparation is a crucial step in developing an automated invigilation system. some of the key considerationsfordatapreparation
The systemshould collect data fromvarious sources,such as cameras, microphones, and sensors. The data should includeimages,videos,andotherrelevantinformationthat canbeusedtoanalyzestudentbehaviorduringexamsthen the collected data may contain noise or irrelevant information, which can affect the accuracy of the system. Therefore, it is essential to clean and preprocess the data beforeusingitforanalysis.
Thecollecteddatashouldbelabeledwithappropriatetags to indicate different activities, such as reading, writing, or lookingatanotherscreen.Thislabelingisessentialtotrain the machine learning models to recognize and detect suspiciousactivitiesaccurately.
Data augmentation involves creating additional training data fromexistingdata toimprovetheperformanceofthe machine learning models. For example, the system can artificially increase the number of students in an image to create a more diverse dataset. The system should use different sampling techniques to balance the data distribution. For example, if cheating activities occur less frequently, oversampling techniques can be used to increase the representation of these activities in the dataset.Thecollecteddatashouldbevalidatedtoensureits accuracy and completeness. Validation includes checking the quality of the data and ensuring that it represents the activitiesthatoccurduringexams.
3.2 Image acquisition
In data acquisition, a camera is utilized to record video of the students, which is afterwards turned into various frames (or images) that can be used to detect and recognizethestudents.
Researchersall across the world had done solid work, but there were certain accuracy flaws that could be fixed, whichtheproposedstudyaimstodo.
For the detection of suspicious activity and face recognition, distinct datasets have been gathered. For the aim of tracking head orientation, training and testing
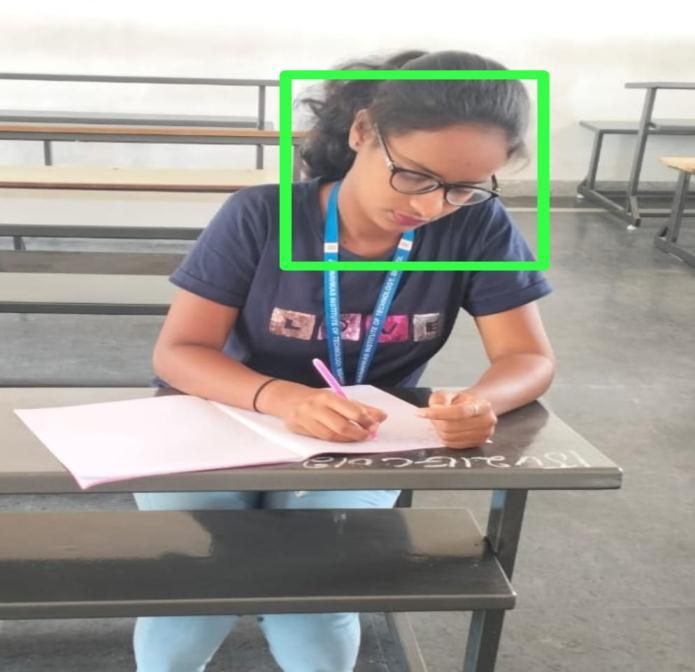
datasets are created for students moving their heads forward,backward,left,andright. Label imagesoftwareis thenusedtomanuallygeneratethelabels"Normalactivity" and"Suspiciousactivity"onthesephotos.
To get a clean shot of every student and their desks, the cameras in the exam room should be carefully placed. In order to reduce shadows and produce high-quality photographs, the positioning of the camera should also take into account the lighting and angle of the scene. In order to ensure that the photos recorded are of good quality and provide sufficient detail to identify any potential cheating behaviors, the camera's quality is crucial. In automated invigilation systems, high-resolution cameras with good low-light sensitivity are often used. To guarantee that the images recorded are precise and reliable, the cameras must be calibrated. To produce consistent, high-quality photographs, this entails tweaking the camera's settings for brightness, contrast, and white balance. To find any potential cheating behaviors, it is necessarytoprocesstheimagesthatthecamerascaptured. This entails analyzing the photos to find any suspicious activity using algorithms like object detection, facial recognition, and posture detection. To protect the privacy and confidentiality of the exam data, the photos that were taken must be maintained securely. Additionally, the system needs to have safeguards against unauthorized accessanddatatampering.
The collection includes 5000 photos, of which 1000 are singlephotographsand4000depictvariousclasseswhere students are engaging in cheating and non-cheating activities. 80% of the dataset is utilized for training, while 20% is used for testing. After training, a live feed from an automatedsecuritycamerainanexamroomisusedtotest themodel.Onalabeleddatasetthatwashead-oriented,we trainedourfasterRCNNmodel.Aftertraining,themodelis tested using real-time footage from anautomatedsecurity camerainanexamroom.Duringimplementation,thevideo isfirstbrokenupintoframes,andeachframeisexamined forheadmovementbeforebeingcategorizedascheatingor not.Forthepurposeofidentifyingstudentfaces,aseparate database of recognized faces has been developed. The dataset includes 1000 photos of students, each of which hasthefront,left,andrightanglesoftheirfacescaptured.
The dataset produced locally for the current work. Six classes worth of physical exams were recorded using a camera with a 640 x 480 resolution and a 25 frames per second frame rate. The footage showed both the students' regular and questionable behavior. From the captured videos,30,000framesweretakenout.UsedaPythonscript withtheOpenCVlibrarytoextractmorethan5000frames. Preprocessing of the collected frames involved manually deletingblurredframesfromthefolder.
The proposed model was trained on a dataset of headoriented student data, where student head movements to
the left, right, and up were classified as either cheating or not,itislimitedinthatitonlyconsidersthestudents'head orientation when determining whether or not there was any cheating. The suggested invigilation system can be improvedfurtherbytrainingafasterinvigilationsystemto detecthandmotionsandhandcontactwhilepassingsheets by extending the existing dataset to include the classes of student hand gesture photos and student hand contact images. The suggested invigilation system can be further improvedbytrainingonanexpandeddatasetthatincludes the classes of student hand gesture photos and student handcontactimages.Thesuggestedinvigilationsystemcan be further improved by training a faster RCNN system to detect hand motions and hand contact during passing sheets by extending the existing dataset to include the classes of student hand gesture photos and student hand contact images. It can also be used to identify any type of dangerousinstruments,suchascalculatorsandphones,to lessen the risk of cheating in offline exams. Several Deep Learning models, including YOLOv4, RCNN, and Mask RCNN,PCA,canbeusedtodetectcheatingbehavior.

3.3 Face Recognition
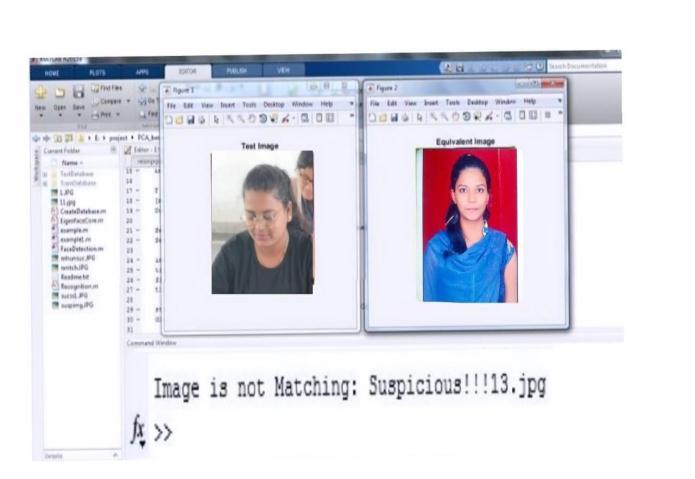
Face Recognition with Open-CV is used for student identification.Toidentifythestudents,theirfacesarefirst identified. Face detection is performed using MTCNN. Students' facial traits are extracted using face embedding models. For the purpose of recognizing and identifying a student, a vector called face embedding that represents the student's facial features is employed. For the purpose of identifying students, a different database is developed. Each student's face is embedded in the system. Each student's face embedding in a live video stream has been calculated, and the results have been compared to the known face embedding that is already present in the dataset.
By matching the student faces to the pictures kept in the database, the system can confirm their identities. This reducesthepossibilityofimpersonationandhelpsensure thattheappropriatestudentistakingtheexam.
Usingcameras,thesystemcancontinuouslywatchthetest space and identify any changes in the students' facial expressions or posture. This can assist in identifying any students who might be switching positions or attempting tocheatbytalkingtoanotherstudent.
The invigilators can be instantly alerted if the system notices any questionable activity, giving them the informationtheyneedtorespondappropriately.
To assist invigilators in reviewing and analyzing exam data, including seeing trends of suspicious behavior or suspectedcheating,thesystemcanalsoofferanalyticsand reporting functions. It is significant to note that privacy and security issues are raised by the use of facial
recognition technology in automated invigilation systems. The system should be built with adequate safeguards to allay these worries, including making sure that data is collectedandstoredsecurelyandthatthesystemcomplies with relevant privacy laws and regulations. The system should also clearly explain to students their rights and how their data will be used, as well as be honest about howitmakesuseoffacialrecognitiontechnology.
4. IMPLEMENTATION
The architecture and design of an automated invigilation system may vary depending on the specific features and functionalitiesitoffers.However,ingeneral,anautomated invigilationsystemconsistsofthefollowingcomponents:
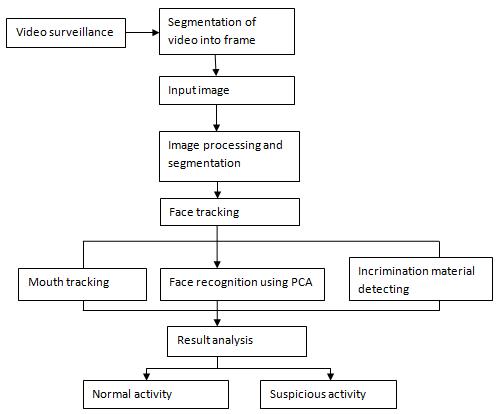
1. Camerasandsensors
2. Datastorageandprocessing
3. Algorithmsandmachinelearningmodels
4. Alertingandreporting

5. Userinterface
Thesystemisdesignedforthemonitoringisonlyengaged during the test period, the system should be built to recognizeandidentifytheexamroom.
To guarantee that they capture all required areas of the exam room while minimizing any potential privacy violations, the placement of cameras and sensors should be carefully designed. Data must be gathered and processed by the system in a secure and trustworthy manner. Additionally, it ought to offer a means of storing andretrievingdataforpossiblelaterreviewandanalysis.
Machine learning models that have been trained to accurately detect dishonest behavior should be used by the system along with trustworthy and efficient algorithms. When suspicious activity is discovered, the system must to have an alerting feature that notifies the invigilator. Additionally, to produce reports containing thorough details about the activities found during the examination.Theprivacyandmoralramificationsofusing the system should be taken into account throughout design. It should make sure that the system is utilized morally and that data is only used for the intended purpose. It should also respect students' privacy rights. The technology should have a user-friendly interface that enables the invigilator to efficiently monitor the exam room. Tomakeitsimplerto spotsuspicious activities,the interfaceshouldpresentthedatainastraightforwardand intelligiblemanner.
To guarantee a seamless experience for the user, the system should be built to interface with other systems, suchaslearningmanagementsystems.
Toensureitseffectiveness, dependability,and ethical use, anautomatedinvigilationsystemshouldtakeintoaccount a variety of components and elements throughout design. Thesystemcanbethoughtfullydesignedtoassistprevent examcheatingwhileupholdingstudents'righttoprivacy.
The technology uses cameras and sensors to record the exam room and keep an eye on the students' behaviors. These cameras and sensors might have features include screen recording, eye-tracking, and facial recognition. The systemgathersinformationfromthecamerasandsensors, analysesit,andsavesitinasafedatabase.Images,movies, andotherpertinentinformationcouldbeincludedwiththe data. The system analyses the data and looks for any unusual activity using algorithms and machine learning models. These models learn to recognize patterns of dishonestbehaviorthroughtrainingonasizabledatasetof labeled samples. If the system notices any suspicious activity, it notifies human invigilators so they can review the video and respond appropriately. Additionally, the system produces reports that give thorough details about the activities found during the examination. The system mighthaveauserinterfacethatenableshumanexaminers to keep an eye on the examroom in real-time and see the images the cameras and sensors are taking. The design of anautomatedinvigilationsystemmusttakeintoaccounta number of criteria, including ease of use, security, and privacy.Itmustmakesurethatthesystem'sdatacollection is retained securely and used only for that reason. The systemshouldalsoensurethatstudents'privacyrightsare maintainedandsetclearinstructionsonhowthedata will
be utilized. Additionally, for invigilators to effectively watchtheexamroom,theuserinterfacemustbesimpleto useandprovidealltheinformationtheyneed.
6. ALGORITHMS
Are speaking or whispering, which may indicate that they are collaborating or using outside resources to cheat. Computer vision and machine learning algorithms are frequently combined in automated invigilation systems to detectsuspectactivityduringtests.Someofthealgorithms thatmightbeappliedinthesesystemsarelistedbelow:
You Only Look Once (YOLO) or Faster R-CNN (Regionbased Convolution Neural Networks) object detection algorithmscanbeusedtofindprohibiteditemsintheexam room, such as electronic devices, books, notes, and other materials.
Algorithms for posture detection can be used to spot changes in a student's behavior or posture that can be a signofcheating.Thesealgorithms,forinstance,areableto recognize when a student bends over towards their desk, whichcould indicatethat they arelookingata device ora cheatsheet.
The ability to recognize specific students in the test room canbeachievedusingfacialrecognitionsoftwarelikeOpen Face or Face Net. To prevent students from switching places or using someone else's identity to cheat, these algorithmscanrecognizeandtrackfacetraits.


Algorithms for anomaly detectioncan be used to spot odd ortroublingexambehavior.Withtheuseofhistoricaldata, these algorithms may recognize patterns that are inconsistentwithregularbehavior,suchasabruptshiftsin astudent'sbehaviororunexpectedmotions.
Convolution neural networks and recurrent neural networks are two examples of deep learning algorithms that can automatically identify suspicious activity by learningfromthedatagatheredduringtests.Theaccuracy andperformanceofthesealgorithmscanbeimprovedover timebytrainingthemonvastdatasetsoflabeleddata.
Algorithms forspeech recognition can be used to examine the audio from the examination room. These algorithms areabletoidentifywhenstudents
To identify suspect behavior during exams, automated invigilation systems may combine object detection, facial recognition, posture detection, speech recognition, anomaly detection, and deep learning algorithms. Together,thesealgorithmsareintendedtoofferacomplete solution for overseeing exams and preserving academic integrity.

6. CONCLUSIONS
Automated invigilation systems have the ability to completely change how exams are administered by enabling a more effective and efficient method of combating cheating. The technologies identify suspect activities and mark them for additional inspection by






humaninvigilatorsusingavarietyoftechniques,including facial recognition, eye tracking, and screen recording. Although it has been demonstrated that automated invigilation systems are successful at catching cheating, there are worries about the privacy and moral ramifications of deploying such systems. Some contend thattheapplicationofthesesystemsmayviolatestudents' right to privacy and faster a stressful environment that impairstheirperformance
Automated invigilation systems are becoming more and more popular for spotting irregularities during inspections. These systems employ AI to track and examine the student actions throughout exams, including theirheadmovements,eyemovements,and keystrokesin order to find signs of cheating or other irregularities. The educational institutions can monitor the students during academic offline and online examinations, reducing the burdenontheexamadministrations.Theinstitutionscurb incidents of examination malpractice, surveillance and monitoring system can be a reliable and adequate in providing a conductive and safer environment for the studentsandthestaffattheexaminationhall.
Theproposedsystemfordetectionofsuspiciousactivities during the examination is based on various computer vision algorithms such as Viola Jones and related-Like Feature and AdaBoost algorithms. The head movement and hand contact are based on color and grid manipulation and face tracking using the trained dataset. Theproposed model helps educational institutions,which will be useful in detecting and recognizing cheating activitiesintheexamhall.
Although AI-based systems are becoming more sophisticated, there is still space for the improvement for their accuracy. Future research and development could help to reduce false positives and ensure for the fair conductionofexaminationsandexamintegrity.Astheuse of artificial Intelligence in educational settings become more prevalent, it is important to ensure that privacy concerns are adequately addressed. The further work could more focus on developing more robust privacy protections that are built into the Automated Invigilation System. Future work could explore expanding scope of thesystemtootherareasofeducation,suchasmonitoring student engagement or detecting plagiarisms in assignments and mitigate potential biases in the system and ensure that it does not discourage certain group of students.
Ultimately, the choice to utilize automated invigilation systems should be carefully considered, taking into account the special conditions and requirements of the educational institution and its students, as well as the potentialadvantagesanddisadvantages.Toguaranteethat such systems are used morally and with regard for
students' privacy rights, it is essential to establish them withtransparencyandexplicitstandards.
The model of deep learning, the faster RCNN is implemented as a classifier with a training accuracy of 99.5 on the Invigilation dataset and a testing accuracy of 98.5. With a 95% accuracy rate, the faces Recognition moduleisusedtoidentifyandrecognizestudents.Student status reports are generated. The proposed model out performs the current model since it can track more than 100 students at once and requires less computing time to get the required result than previous models. The development of a quicker invigilation system can further enhancethesuggestedinvigilationsystem.
REFERENCES
[1] Zhang, Xiangyu, Xinyu Zhou, Mengxiao Lin, and Jian Sun. “Shufflenet: An extremely efficient convolutional neural network for mobile devices.” In Proceedings of the IEEE conference on computer vision and pattern recognition,pp.6848-6856.2018.

[2]Ahmad SalihuBen-Musa,Sanjay Kumar Singh, Prateek Agrawal, “Suspicious Human Activity Recognition for Video Surveillance System”, International Conference on Control, Instrumentation, Communication and ComputationalTechnologies,Researchgate,2015.
[3] B. C. Amanze, C. C. Ononiwu, B. C. Nwoke, I. A. Amaefule,“VideoSurveillanceAndMonitoringSystemFor Examination Malpractice In Tertiary Institutions”, International Journal Of Engineering And Computer Science,Vol.5,January2016,pp.15560-15571
[4] X. Wang, M. Xia, H. Cai, Y. Gao, C. Cattani, “HiddenMarkovModels-Based Dynamic Hand Gesture Recognition”, Mathematical Problems in Engineering, pp. 1-10,2012.
[5] R. Lockton, A.W. Fitzgibbon, “Real-Time Gesture Recognition Using Deterministic Boosting”, Proc. British MachineVisionConference,pp.817-826,Sept.2002.
[6] Paul Viola, Michael J. Jones , “Robust Real time Face Detection, International Journal of Computer Vision”, Vol 57,issue2,pages:137-154,2004
[7] Richard Szeliski, “Computer Vision: Algorithms and Applications”,FirstEdition,Springer,2010.
[8] Teddy Co, “A Survey on Behavior Analysis in Video Surveillance for Homeland Security Applications”, IEEE Conference on Applied Imagery Pattern Recognition Workshop(AIPR),Pages:1–8,2008.
[9]Ren,Shaoqing,KaimingHe,RossGirshick,andJianSun. “Faster r-cnn: Towards real-time object detection with region proposal networks.” arXiv preprint arXiv:1506.01497(2015).
[10] N. Rajesh, H. Saroja Devi, “Emerging trends in video surveillance Applications”, International Conference on SoftwareandComputerApplications,vol.9,2011.
[11] Neil Robertson, Ian Reid, “A General Method for Human Activity Recognition in Video”, Journal of Computer Vision and Image Understanding, Vol. 104, No. 2,pp.232-248,2006
[12]Arun,M.,E.Baraneetharan,A.Kanchana,andS.Prabu. "Detection and monitoring of the asymptotic COVID-19 patients using IoT devices and sensors." International Journal of Pervasive Computing and Communications (2020)
BIBILOGRAPHY
NOOR SUMAIYA

Assistant Professor, Dept of Computer Science and Engineering, MS, Pursuing PhD fromRevaUniversity




NAVYA S K
B.E Student, Department of Computer Science and Engineering
ANJALI R
B.E Student, Department of Computer Science and Engineering
PRIYA N
B.E Student, Department of Computer Science and Engineering
NANDAN A





B.E Student, Department of Computer Science and Engineering

