UTILITY BILL PAYMENT BASED ON NETWORK SECURITY
1 AP, Department of Information Technology, Meenakshi College of Engineering, Chennai, Tamilnadu, India.
2-5Student, Department of Information Technology, Meenakshi College of Engineering, Chennai, Tamilnadu, India. ***

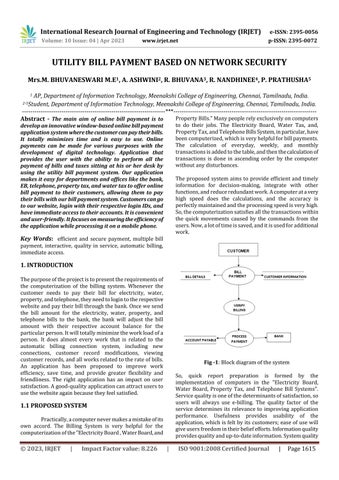
Abstract - The main aim of online bill payment is to develop an innovative window-based online bill payment application system wherethecustomercanpaytheirbills. It totally minimizes time and is easy to use. Online payments can be made for various purposes with the development of digital technology. Application that provides the user with the ability to perform all the payment of bills and taxes sitting at his or her desk by using the utility bill payment system. Our application makes it easy for departments and offices like the bank, EB, telephone, property tax, and water tax to offer online bill payment to their customers, allowing them to pay their bills with our bill paymentsystem.Customerscango to our website, login with their respective login IDs, and have immediate access to their accounts. It is convenient and user-friendly.Itfocusesonmeasuringtheefficiencyof the application while processing it on a mobile phone.
Key Words: efficient and secure payment, multiple bill payment, interactive, quality in service, automatic billing, immediateaccess.
1. INTRODUCTION
Thepurposeoftheprojectistopresenttherequirementsof the computerization of the billing system. Whenever the customer needs to pay their bill for electricity, water, property,andtelephone,theyneedtologintotherespective websiteandpaytheirbillthroughthebank.Oncewesend the bill amount for the electricity, water, property, and telephone bills to the bank, the bank will adjust the bill amount with their respective account balance for the particularperson.Itwilltotallyminimizetheworkloadofa person. It does almost every work that is related to the automatic billing connection system, including new connections, customer record modifications, viewing customerrecords,andallworksrelatedtotherateofbills. An application has been proposed to improve work efficiency, save time, and provide greater flexibility and friendliness. The right application has an impact on user satisfaction.Agood-qualityapplicationcanattractusersto usethewebsiteagainbecausetheyfeelsatisfied.
1.1 PROPOSED SYSTEM
Practically,acomputernevermakesamistakeofits own accord. The Billing System is very helpful for the computerizationofthe"ElectricityBoard,WaterBoard,and
PropertyBills."Manypeoplerelyexclusivelyoncomputers to do their jobs. The Electricity Board, Water Tax, and, PropertyTax,andTelephoneBillsSystem,inparticular,have beencomputerized,whichisveryhelpfulforbillpayments. The calculation of everyday, weekly, and monthly transactionsisaddedtothetable,andthenthecalculationof transactions is done in ascending order by the computer withoutanydisturbances.
The proposed system aims to provide efficient and timely information for decision-making, integrate with other functions,andreduceredundantwork.Acomputeratavery high speed does the calculations, and the accuracy is perfectlymaintainedandtheprocessingspeedisveryhigh. So,thecomputerizationsatisfiesallthetransactionswithin the quick movements caused by the commands from the users.Now,alotoftimeissaved,anditisusedforadditional work.
So, quick report preparation is formed by the implementation of computers in the "Electricity Board, Water Board, Property Tax, and Telephone Bill Systems". Servicequalityisoneofthedeterminantsofsatisfaction,so users will always use e-billing. The quality factor of the service determines its relevance to improving application performance. Usefulness provides usability of the application,whichisfeltbyitscustomers;easeofusewill giveusersfreedomintheirbeliefefforts.Informationquality providesqualityandup-to-dateinformation.Systemquality
can provide or add features according to usability, availability,reliability,adaptability,andresponsetime.
2. TECHNOLOGY AND TOOLS
THE.NET FRAMEWORK

The.NetFrameworkistheplumbingof.Net.TheFramework provides the services necessary to develop and deploy applicationsforthelooselycoupled,disconnectedInternet environment.Thetwomaincomponentsthatmakeupthe frameworkare:
•CommonLanguageRuntime(CLR)
•BaseClassLibraries(BCL)
TheCLRisthefoundationoftheframework.Thegoalsofthe CLRare
•Secureandrobustexecutionenvironment
•Simplifieddevelopmentprocess
•Multilingualsupport
•Simplifiedmanagementanddeployment
Visual Basic.NET (VB.NET) is a Microsoft object-oriented programminglanguagewhichwasevolvedfromVisualBasic 6usedtomeetanincreasingneedforeasywebdevelopment andservices.
Base Class Libraries (BCL)
TheBCLisdividedintonamespaces,whichdefineanaming schemeforclassessuchaswebclasses,dataclasses,window forms,XMLclasses,enterpriseservices,andsystemclasses.
ACTIVEX DATA OBJECTS
Microsoft’s ActiveX Data Objects (ADO) are a set of ComponentObjectModel(COM)objectsforaccessingdata sources.Itprovidesalayerbetweenprogramminglanguages andOLEDB(ameansofaccessingdatasources,whetherthey bedatabasesorotherwise,inauniformmanner).ADOallows a developer to write programs that access data without knowing how the database is implemented. You must be aware of your database for connection only. Some basic steps are required in order to be able to access and manipulatedatausingADO:
1.Createaconnectionobjecttoconnecttothedatabase.
2.Createarecordsetobjectinordertoreceivedata.
3.Opentheconnection.
4.PopulatetherecordsetbyopeningitandpassingtheSQL statement.
5.Doallthedesiredsearchingandprocessingonthefetched data.
6.CommitthechangesyoumadetothedatabyusingUpdate methods.
7.Closetherecorder.
8.Closetheconnection. Table -1
Telephone amount
status Int NotNull Current status
Microsoft SQL Server 2008
MicrosoftSQLServer2008offersavarietyofadministrative tools to ease the burdens of database development, maintenance,andadministration.Inthisarticle,we'llcover six of the more frequently used tools such as Enterprise Manager, Query Analyzer, SQL Profiler, Service Manager, DataTransformationServices,andBooksOnline.
Buffer Management
SQLServerbufferspagesinRAMtominimizediscI/O.Any8 KBpagecanbebufferedinmemory,andthesetofallpages currently buffered known as the buffer cache. Available memory in SQL Server decides how many pages will be cachedinmemory.SQLServerincludesacost-basedquery optimizer that tries to optimize based on the cost of the resourcesitwilltaketoexecutethequery.Finally,itdecides whether execute the query concurrently or not. While a concurrent execution is more costly in terms of total processortime,thefactthattheexecutionisactuallysplit among different processors might mean it will execute faster. Once a query plan is generated, it is temporarily cached.
Data Storage
The main unit of data storage is a database, which is a collection of tables with typed columns. A SQL Server databasecancontainotherobjects,includingviews,stored procedures, indexes, and constraints, in addition to tables andatransactionlog.ASQLServerdatabasecancontaina maximum of 231 objects. Storage space allocated to a databaseisdividedintosequentiallynumberedpages,each8 KBinsize.Atableissplitintomultiplepartitionsinorderto spreadadatabaseoveracluster.Rowsineachpartitionare storedineitheraB-treeorheapstructure.
The multiple payments protocol consist of six steps shown below:
Step1: CIN:M1={Tx,{Acc-c}SK(c-psp)j, h({Acc-c}SK(c-psp)j, SK(INC)j)}SK(IN-C)j
Customersend Tx andaccountnumberto PSP pass IN
TID
TransactionIdentifierofthepayments
IDx UniqueIdentifierofentityX

POMi MultiplePaymentOrder
PO PaymentOrder
BillnoMi billnumberforeachmerchant
PriceMi Priceofgoodsandservice
Tp Startingtimestampoftransactionprocessing
Acc-Mi Accountnumberofmerchanti
Acc-c Accountnumberofcustomer
Status SetofConfirmPaymenteachmerchanti
Statusc-Mi Approved/unapproved
{M}k EncryptionmessageMbykeyK
SK{X-Y}j
Chart -1:Multitransactions
3. DETAILED CONSTRUCTION
Themodelofmultipaymentisdesignedtohighlightfeatures ofrelatedworkthatintegratesthesetogetthebestprotocol formobilepaymentsthatcansupportnewlifestyles.
Thenewmodelhasfourparts,asfollows:
Customer(C):(client,purchaser,buyer)whoobtaingoods and services from a supplier for a monetary or other valuableconsideration.
Merchant (M): is a business person who trades in commoditiesproducedbyothers,inordertoearnaprofit. Intermediary(IN):isavirtualmechanismconnectedtoall partiesfordistributionofthemessage.
PaymentServiceProvider(PSP):Atrustedthirdpartythat suppliesmoneyforbusinessessuchas banksornonbanks.
Table-2
Considerascenarioof publicutilitypayment.ThepartyCis amemberofthepartyMiforcontactingthebusiness.Cand Mi are members of the same PSP, which have separate accountnumberssuchasAcc-candAcc-Mi.TheMipresents ahardcopybilltothecustomerforpayment.Thecustomer can make payments to multiple merchants via mobile applications that can select many bills payments per transaction.
Asessionkeythatsharesasecretkey between entity X and entity Y, in order to protectfromreplayattack sessionkeyused once.
h(m,K) Message Authentication Code(MAC) or HMACofamessagemandkeyK
TX PaymentTransaction={TID,Tp,PO}
Message (M1) was encrypted by session shared key between C and IN thatprovidedconfidentialityproperties. Peoplewhodonothavethesessionkeycannotaccessthe transaction.
Payment Distribution Process:
Step2:INMi:M2 = {Tx,h(Tx,SK(IN-Mi)j)}SK(IN-Mi)j IN receivedthemessagefrom C thendecryptedbyusing the session shared key and checked the destination to transfer anddistributetoallmerchantsviaprotecteddatausingthe encryptiontechnique.
Authorization request from MiIN to PSP:
Step3: MiIN: M3={StatusMi , Tx , {ACC-Mi , PriceMi}SK(Mi-PSP)j Mi checksthemessagetoascertainifthecondition matchesordoesnotmatch,thenupdatesmessage(approve or unapproved)ofstatus.Thencallbackto IN fortransferto PSP
Authorization Request/Response Between IN PSP
Step4: IN PSP: M4= {StatusMi , Tx ,{Acc-c}SK(C-PSP)j , {AAcc-Mi , PriceMi}SK(Mi-PSP)j , h({ACC-C}SK(Mi-PSP)j ,{Acc-Mi,PriceMi}sk(Mi-PSP)j ,SK(IN-PSP)j)}SK(INPSP)j
PSP checkedthestatusandupdatedauthorizationrequest suchasbalanceaccountofcustomerandmerchantthen respondsto C and Mipass In
step5 PSPIN:M5 = {Statusc-Mi , Tx, h(StatusMi , Tx , SK(INPSP)j)}SK(IN-PSP)j+1
PSP sendmessageto IN fortransferto C and Mi
IN dividedtheinformationanddistributedto C and Mi. The aforementioned six steps of the proposed protocol ensuresthesecurityproperties:CAIN.Allmessagesthatare transferredonnetworkbyusingacryptographictechnique that consists of symmetric key cryptography, hashing function,andMessageAuthenticationCode(MAC)
4.RESULTS
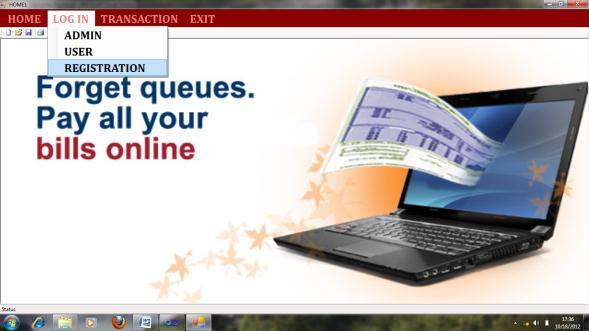
Figure2showstheloginform,whichhasadmin,user,and registrationforms.Intheregistrationform,theadminand usercanregistertheirdetails.Bothusersandadministrators areprovidedwithausernameandpasswordtologintothe page.
5.CONCLUSIONS
Wehavetriedtodevelopasystemthatcanbeagreathelp for the customer to pay their bills for electricity, water, property,andtelephonethroughthebank.Theapplicationis verywelltested,anderrorsareproperlydebugged.Wehave leftalltheoptionsopen.Ifthereisanyrequirementbythe userfortheenhancementofthesysteminfuture,thenitis possible to implement them. There is necessary of future enhancementinsystem,asthelimitationswillbeovercome bybetterfuturetechnologies.
6.FUTURE ENHANCEMENT
Figure3isthebillnumberregistrationform,whichallows the user to register their bill numbers provided to the specific department. We can provide the details of the electricitybill,waterbill,telephonebill,andwatertax.
Foranysystem,itisnecessaryvisualizethefuturescope. In thefuture,moresoftwarecompanieswillhirethisprogram becausenowadays,theneedforspeedinday-to-daylifehas become essential. As competition increases, companies developmoreefficientversionsforindividualsuccess.For example, in my project, records of the customer and their transactions are maintained, which will be helpful in the future as references prior to dealings as well as evidence. Also,limitationscanbeovercomebybettertechnologies,and systemscanbemademoreefficient.
REFERENCES
[1] YanjiaoChen,XuxianLi,JianZhang,HongliangBi(2022) “Multi-PartyPaymentChannelNetworkBasedonSmart Contract”.2(1),1-7.
[2] Barokati,N.,Wajdi,N.,&Barid,M.(2017).Application Design Library With the gamification concept. Jurnal Lentera: Kajian Keagamaan, Keilmuan dan Teknologi, 3(1),93-102.
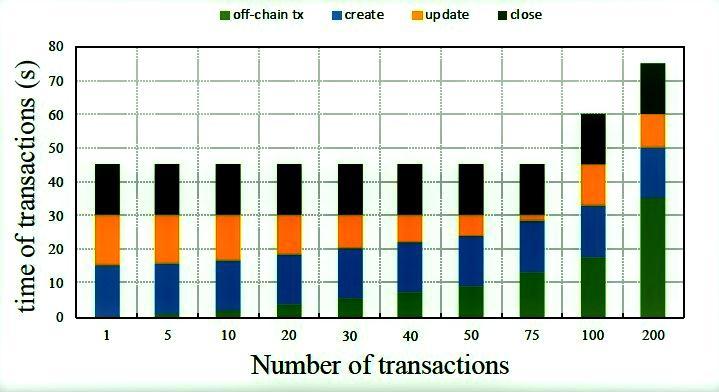
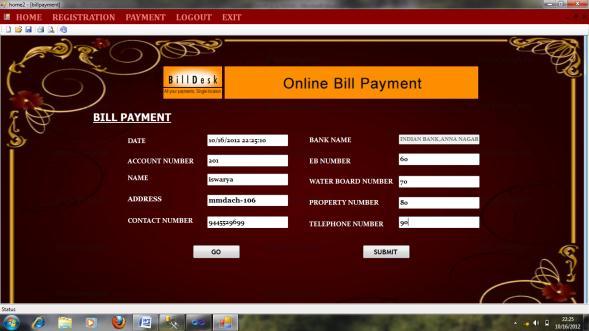
Figure4showstheadjustmentofbillsdoneintransaction form.Here,theuserreceivesthemulti-billsattheendofthe month from the bank and requests to pay the bills. This transactionformallowsyoutocombinethebillsintoasingle payment.Finally,theuserwillgettheconfirmationofpaid billdetailsthroughEmail.
[3] Kuzlu, M., Rahman, M. M., Pipattanasomporn, M., & Rahman, S. (2017). Internet-based communication platformforresidentialDRprogrammes.IETNetworks, 6(2),25-31.
[4] [15] Didyasarin, H., Vongurai, R., & Inthawadee, S. (2017). The factors impact attitude toward using and customer satisfaction with elderly health care mobile

applicationservices:acasestudyofpeopleinBangkok metropolitan,Thailand.AU-GSBe-JOURNAL,10(1),167.
[5] Nunkoo,R.,Teeroovengadum,V.,Thomas,P.,&Leonard, L.(2017).Integratingservicequalityasasecond-order factor in a customer satisfaction and loyalty model. International Journal of Contemporary Hospitality Management,29(12),2978-3005.
[6] Pensri Pukkasenung, Suphat Sukkasem (2016) An EfficientofSecureMobilePhoneApplicationforMultiple BillPayments978-1-5090-2461-2
[7] Pratama,R.D.(2014).PersepsiUserTerhadapDesain WebsiteEcommerce(StudiPadaPenggunaWebsiteJkm Store).JurnalAdministrasiBisnis,9(1).
[8] W., Stalling, “Cryptography and Network Security,” PrinciplesandPractice6thEdition.2013,PrenticeHall International,Inc.
[9] Daniel O. R. et al., “Adaptive Query Algorithm for LocationOrientedApplications”RoedunetInternational Conference(RoEduNet),2013th,Romania
[10] W., Qiongqiong, and M., Xin "Research on a secure mobile payment based on multi-agents," Wireless Communications,NetworkingandInformationSecurity (WCNIS),2010IEEEInternationalConferenceon.IEEE, 2010
[11] M. Carbonell, J. M. Sierra, and J. Lopez, “Secure multiparty paymentwith an intermediary entity,” computers&security,vol.28,no.5,pp.289–300,2009.
[12] M.,Carbonell,J.,Torres,D.,Suarez,J.,M.Sierra,“SecureePayment Protocol with New Involved Entities,” Collaborative Technologies and System, 2008 IEEE , 2008.CTS2008,InternationalSymposiumon,vol.,no., pp.103,111,19-23May2008

[13] T.S.Fun,L.Y.Beng,R.Roslan,andH.S.Habeeb,“Privacy in newmobile payment protocol”, World Academy of Science, Engineering and Technology. Vol:2, pp. 198202,2008.
[14] Moustakis,V.,Litos,C.,Dalivigas,A.,&Tsironis,L.(2004). Website Quality Assessment Criteria. IQ, 5, 59-73. S. Kungpisdan,B.Srinivasan,P.D.Le,“AsecureAccountbasedMobilePaymentprotocol”.