Women's Maltreatment Redressal System based on Machine Learning Techniques
Hemanth adhi sekhar obulasetty, Preetha Sivakumar, Shalini LStudent, Senior Assistant Professor, Vellore Institute of Technology, Vellore (Tamil Nadu), INDIA

Abstract - A significant and expanding concern on a global scale is violence against women. Various issues like difference in maintenance, proper maintenance of records in different countries, even parts of a country are present in the current system. Through our project, we shall be addressing these issues by development of a portal to register and assign complaints according to the classification based on ML program. The main focus on the portal would be ease the communication between the involved victim and government officials. In addition to which, new features like real –time communication through WEBRTC protocol, victim services and SOS alert are included. We have extensively analyzed and classified the case based on the selected algorithm having highest accuracy namely deep feed forward algorithm. The implemented algorithm is the simplestformofartificialneural network having no loops and carries the data only in a single direction. Known as the multiple layer perceptron, it inputs enter the layer and are multiplied by the weights in this model comprising of multiple hidden layers which are summed together to form a total. With the accurate and immediate classification of the cases, the efficiency and execution will be immensely improved through the use of our application.
Key Words: Web application, Deep Feed Forward, ML Algorithms, WebRTC, Deep learning
1. INTRODUCTION
Misuse or violent behaviour is as old as humanity, but it takes many forms and levels as time passes. Women's violence, in particular, is a major issue that must be addressed.Wediscoveredthatthereisnolinkbetweencases involving the same person in different regions, and that followingupondetailsandtheoverallprocessisdifficultfor policeauthoritiesduetothelackofinterconnectionbetween different regions and communication between involved officials. People of different cultures, background and educationlevelseventoilliteracylevelsrequiresomemode to register their complaint. With several cases being filed everyday,knowingtheprioritiesofthecasesisessential. Assigning the importance of the case was employed using machinelearningalgorithmsfromclassicalapproacheslike K-nearest neighbours, support vector machine, decision trees, random forest and gradient boosting algorithms to deepfeedforwardneuralnetwork,adeeplearningmethod. The model was intensively trained after data processing,
cleaning and feature selection to give the most accurate prediction. A centralized platform with all related information and services, as well as a forum for users, administrators, and government officials, is required. To addressthisissue,wedevelopedourproject.
1.1 Methodology:
Webapplicationsforcomplaintregisterandother services
Deeplearningbasedclassificationofcaserecords whichistoassignedtothegovernmentofficers
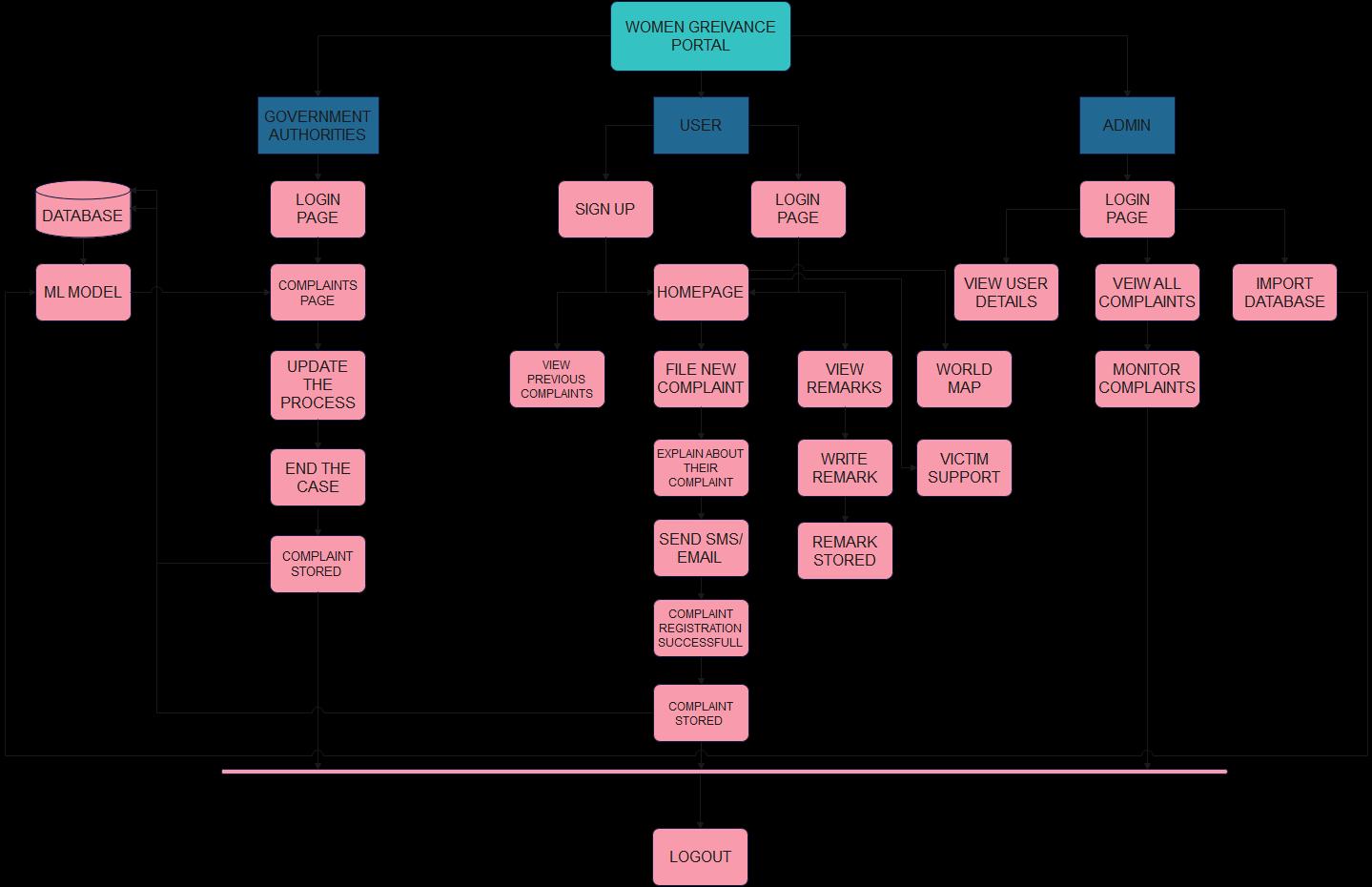
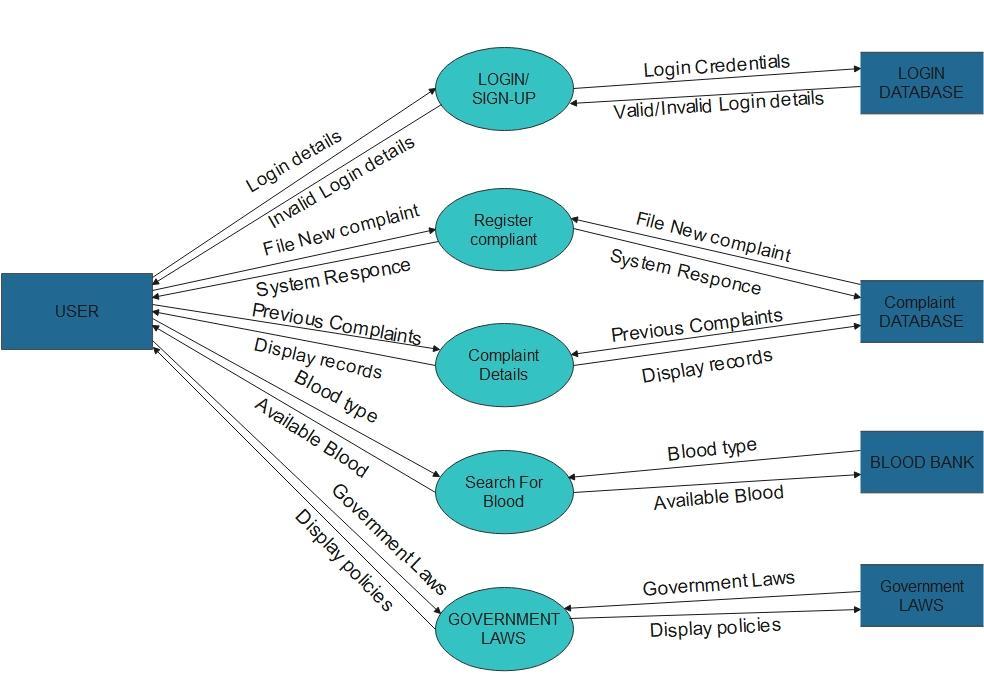
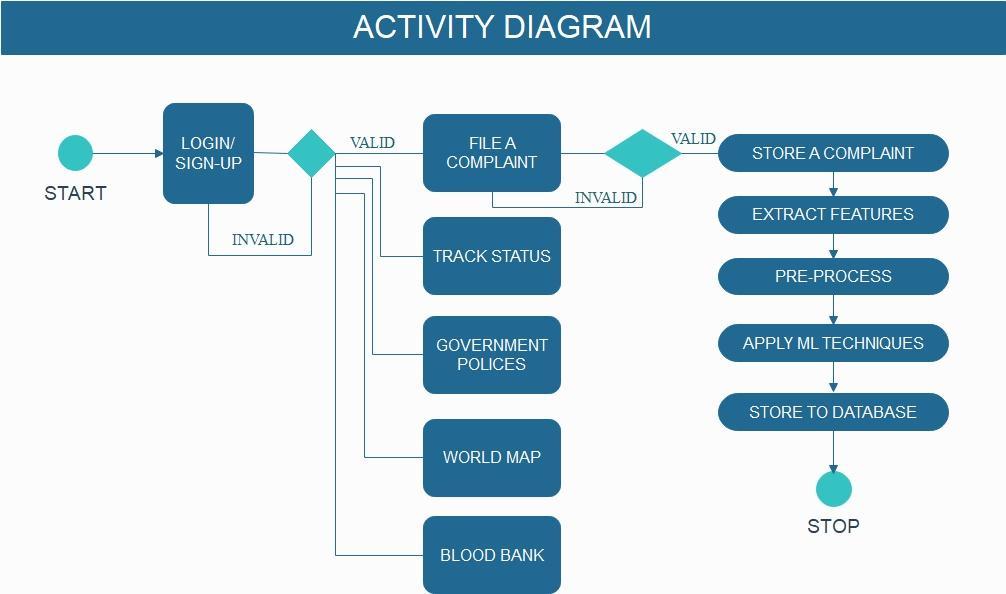
2. Overview of Application
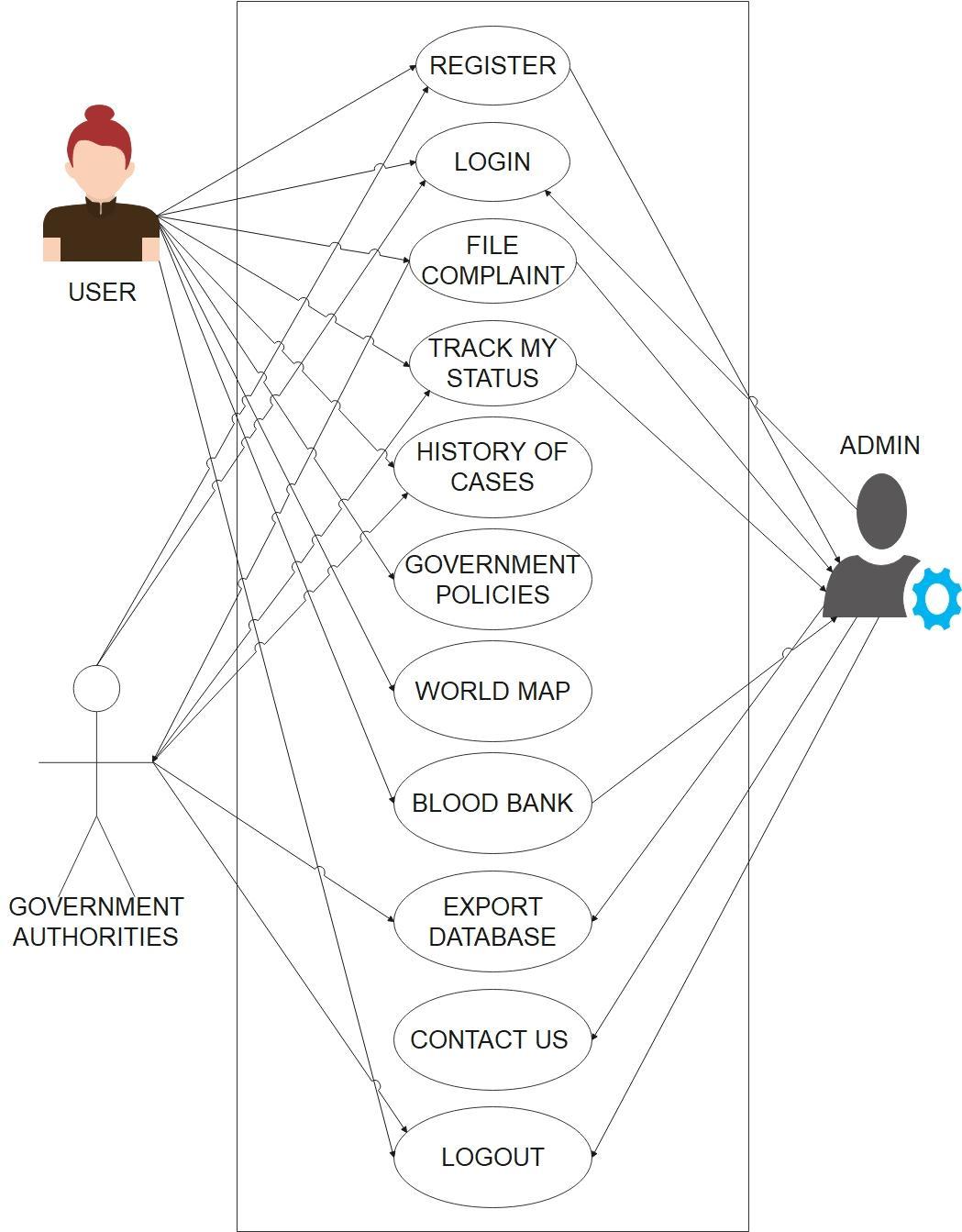
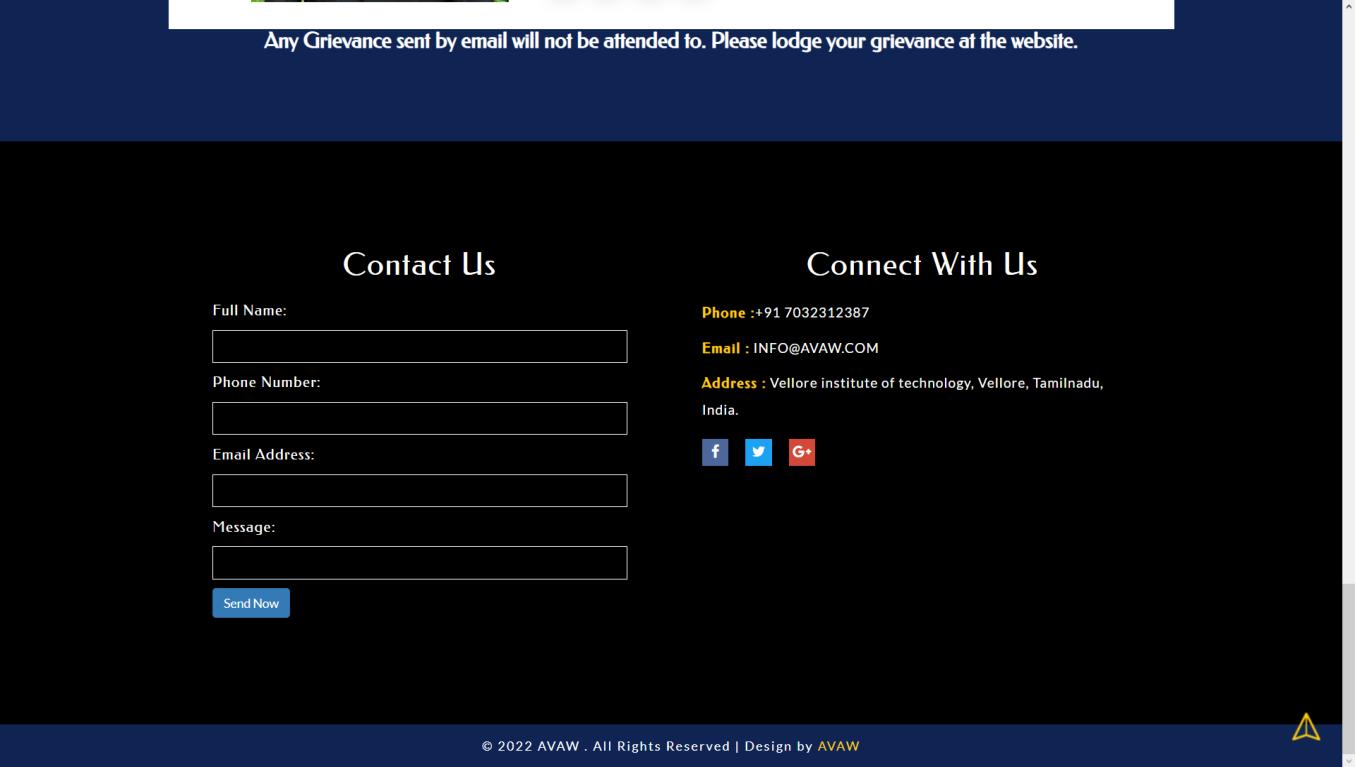
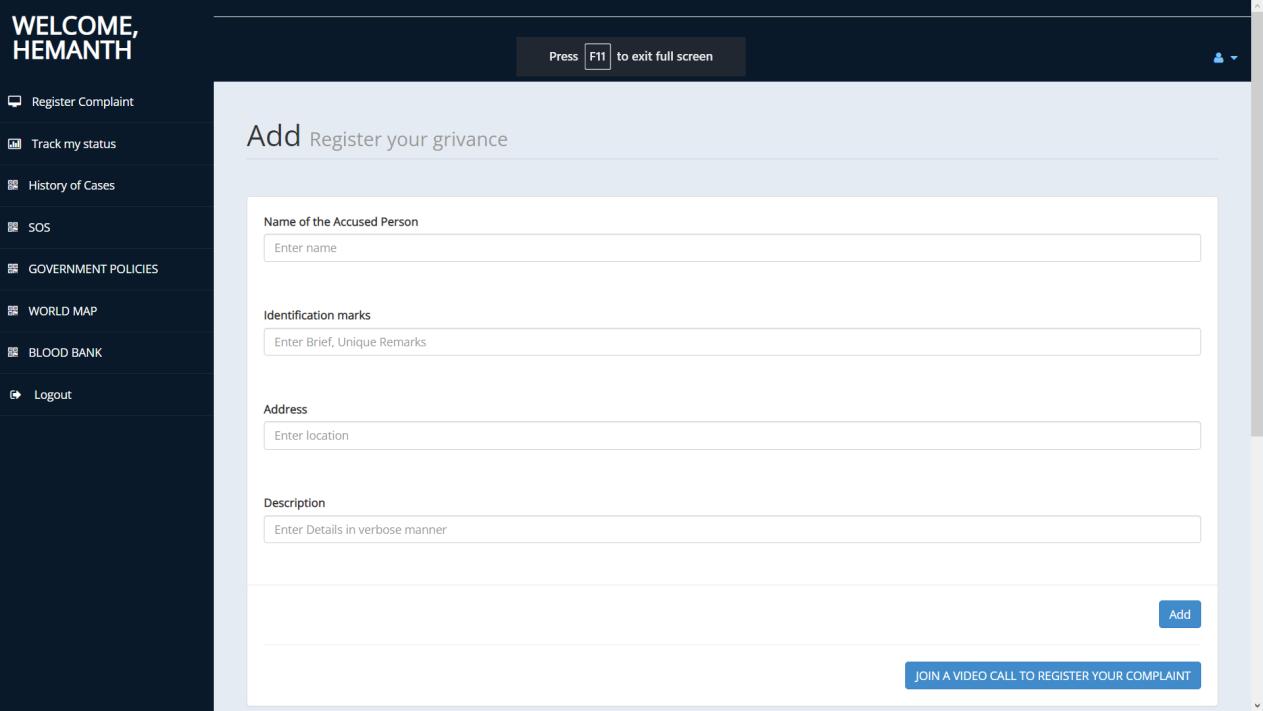
Theprojectintendstocreateauniversalportalasafriendly and convenient space for the victims to communicate and register their complaint and experiences officially. Upon proper authentication and sign up, the users would gain access to the resources like blood bank information, laws and policies up to date and global statistics in addition to SOS alert, tracking case and real-time communication through WebRTC. The main feature, registration, involves filing a form consisting of name of accuses, identification marks,detailsofincidentanditslocationwhichcanbeeither verbal orthroughvideocall.Dependingontheseverity of cases,itwillbeimmediatelyassignedtoapoliceofficerof the concerned rank. All information stored (using Mysql) andmaintainedissecuredandprivatetoensurenodatais erroneouslyusedandexploited.
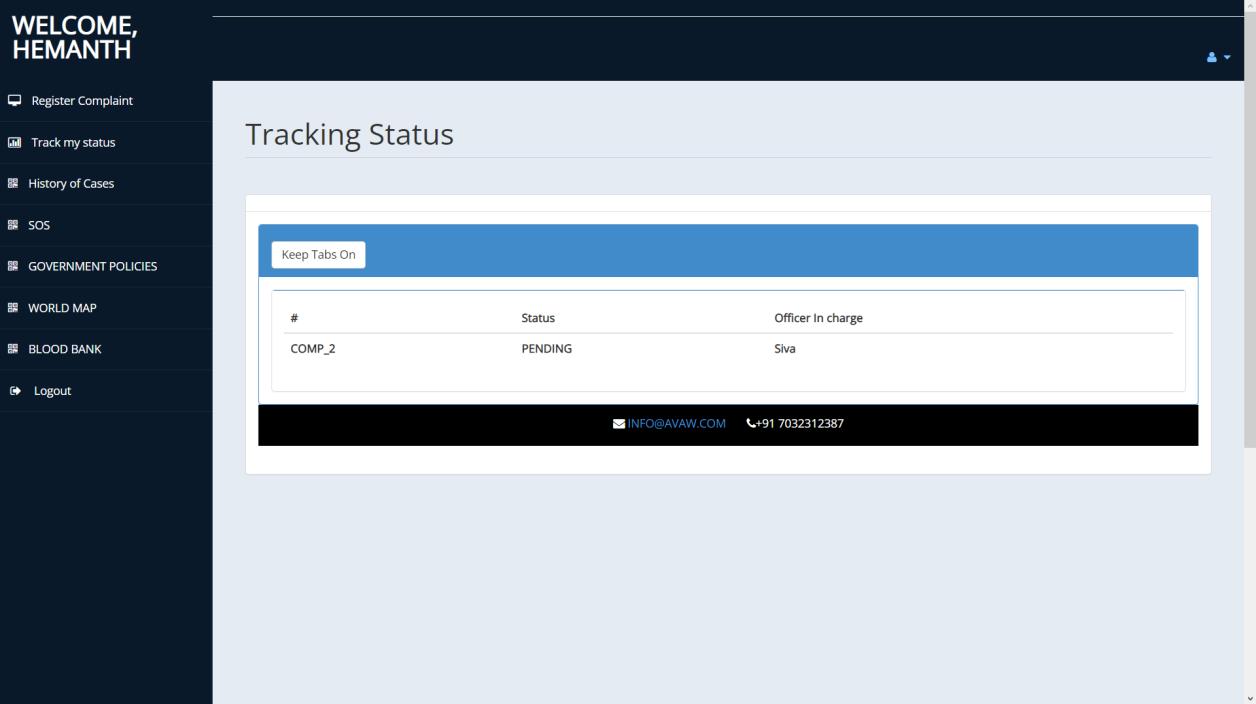
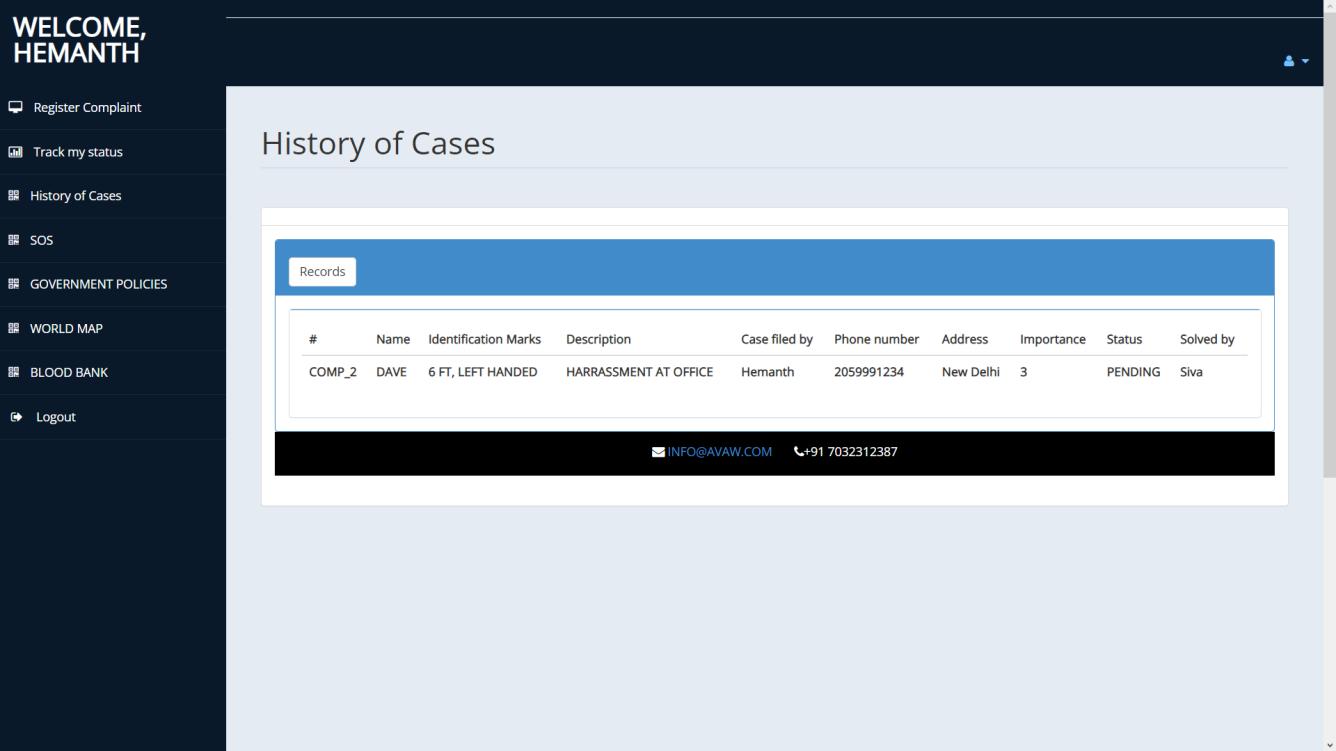
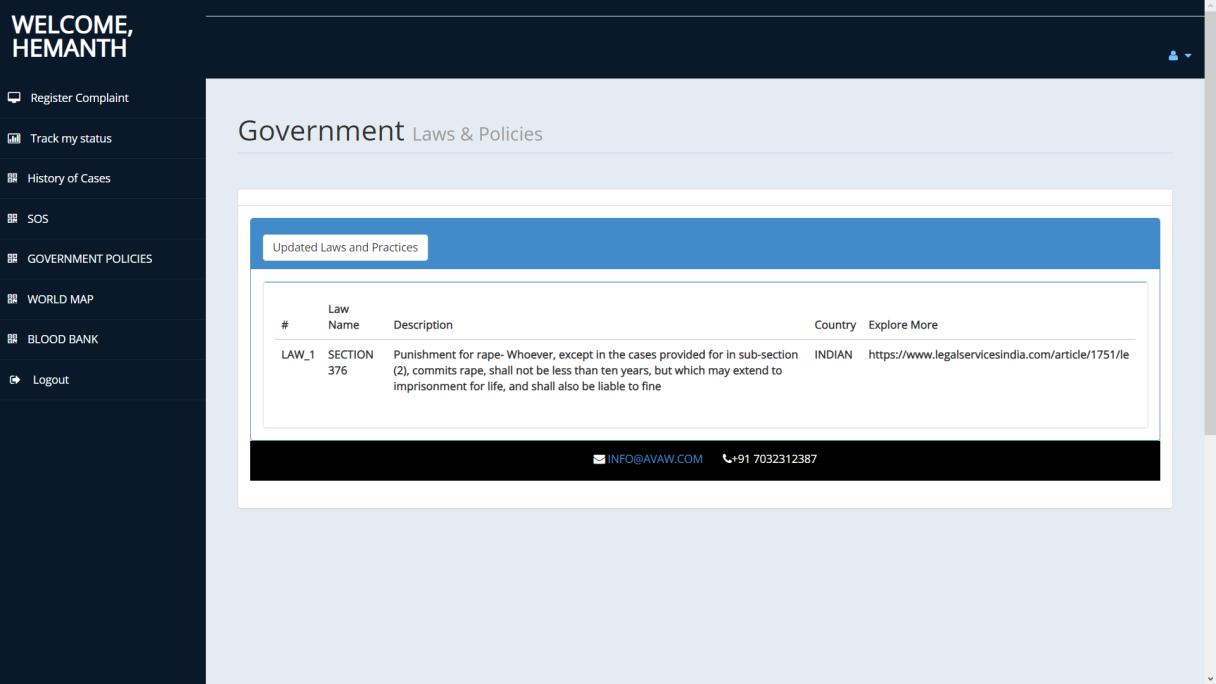
Governmentofficialshaveaseparatelogingatewayandwith authentication would be given access to the homepage containingallcaserecords.Theyalsohavetheoptiontoview victim’sdetailsandlawsandorderinformationandexport database of complaint records as a pdf. Their history of cases can also be seen inclusive of complaint, status and solvedby.Videocalloptionisgiventocommunicatetothose thatfeelmorecomfortableorunabletofillthedigitalformto fileanofficialcomplaint.
Theadmingainstoresponsibilitytostoreandmaintainthe databaseandportalwithaccurateinformationincludingthe staticrecordsofglobalstatistics,lawandpoliciesandblood bank.Theadmininsuresthecomplaintsarebeingaccurately classifiedandsolvedimmediately.Contactformswhichmay
be include feedback, issues or doubts regarding the applicationiscollectedandperformsthenecessarystepsin regardstotheuser’smessage.
2. Relevant Concepts

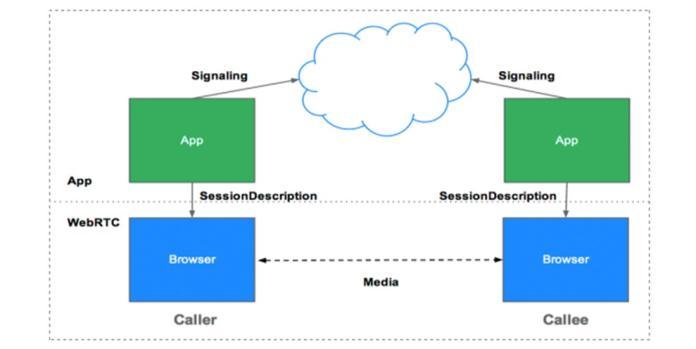
2.1 WebRTC
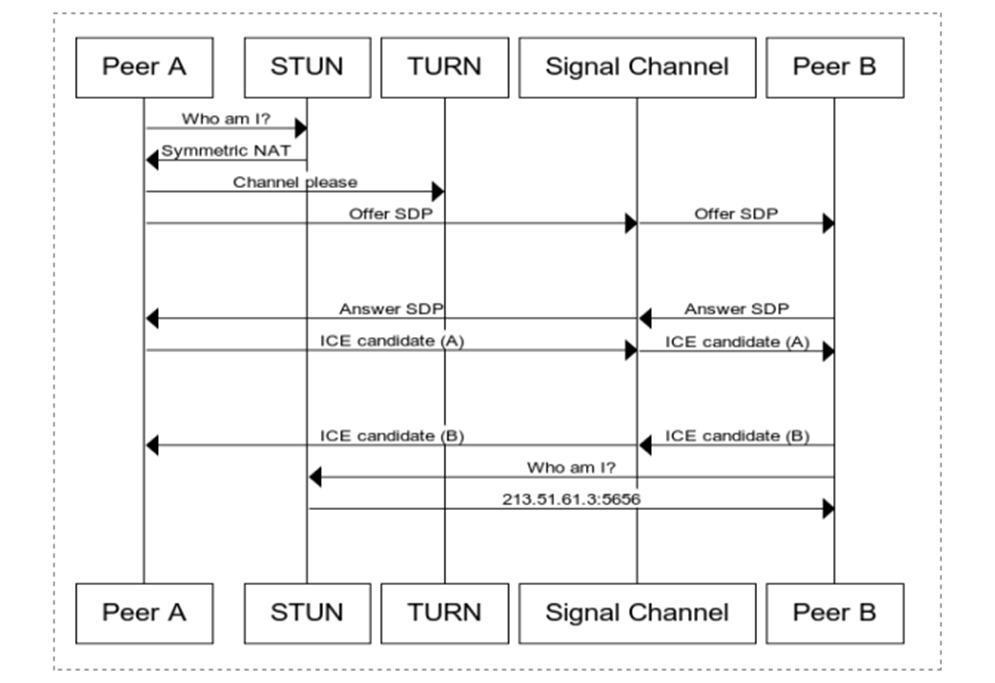
WebReal-TimeCommunication,isadevelopingstandardfor real-time browser communication. According to many IT experts,WebRTCwilleventuallyleadtoabreakthroughin communication technology. Because users do not need to install plugins such as Adobe Flash or use third-party software such as Skype, WebRTC's no-plugins strategy is advantageous and significantly reduces setup time. It enables real-time voice, video, and data transmission capabilitiesviawebbrowsers.WebRTCiswell-knownforits exceptional peer-to-peer communication features such as interoperability,security,andvideoquality.However,itis notwithoutflaws.Thedifficultiesencounteredwhenusing WebRTCarecausedbythediversityofaccessmethods,as their capacities and networks differ. The application is affected by the user's network bandwidth and latency. Screensizeisafactorbecauseresolutionsandqualityvary, makingitimpossibletobroadcastequalqualitytoallusers.
Outofthenumerousdeeplearningarchitectures,themost popularly used are feedforward neural networks, convolutional neural networks and recurrent neural network.
The deep learning technique utilized will fluctuate dependingonthekindofapplicationanddatasetused.The general workflow starts with an in-depth grasp of the problem specification and its viability. Following that, an appropriatedatasetisselected,andthesuitablealgorithm typeischosen.Goingtofollowthat,thedataispre-processed and cleaned to include the appropriate features and data formatfortraining.Themodel'sperformanceisevaluated afterachievinganoptimalaccuracyscorebyhyper-tuning
2.3 Data Visualization
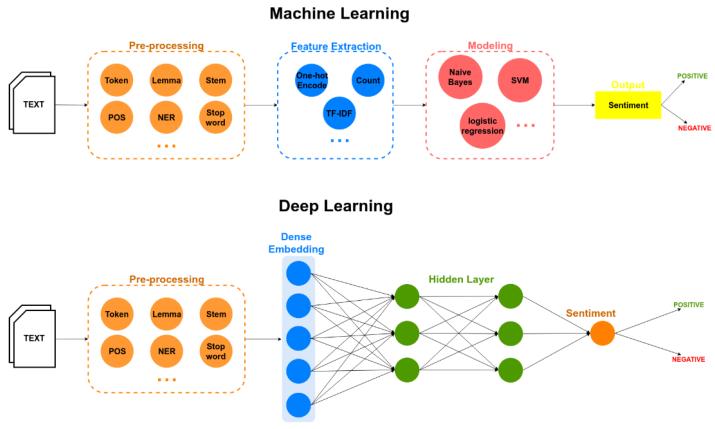
Machinelearningfocusesonthecreationofalgorithmsand mathematicalanalysisthatenablescomputerstolearnand make predictions or judgements without being explicitly programmed.Itentailstrainingalgorithmsonbigdatasetsto detect patterns and relationships, and then using these patterns to forecast or make choices about incoming data. Deeplearningisfragmentofmachinelearningthatevaluates complicatedpatternsandcorrelationsindatausingneural networkswithnumerouslayers.Likethecomplexstructure and functionality of the human brain, the deep learning algorithmsaretrainedtocomputebroadspectrumoftasks including as image identification, natural language processing, and speech recognition. The major limitation includesdatadependency,overfitting,lackofinterpretability, andcomputationallydemanding.
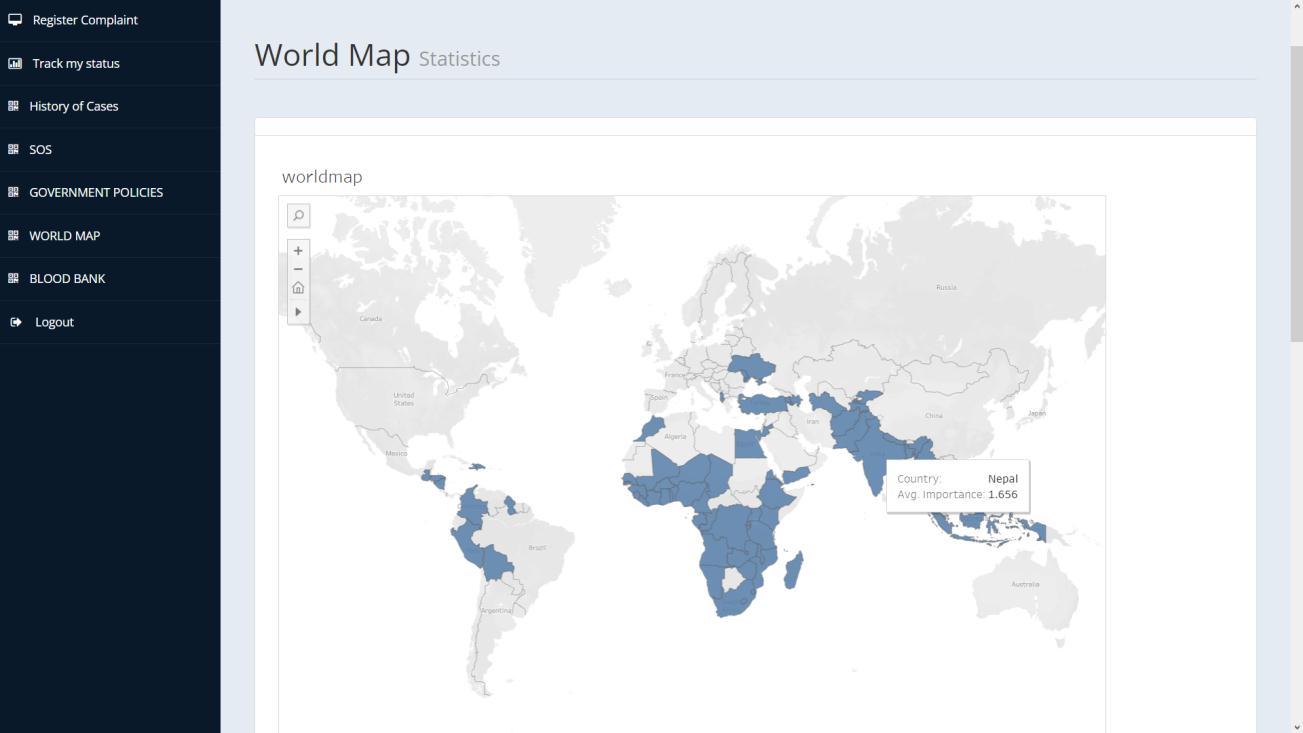
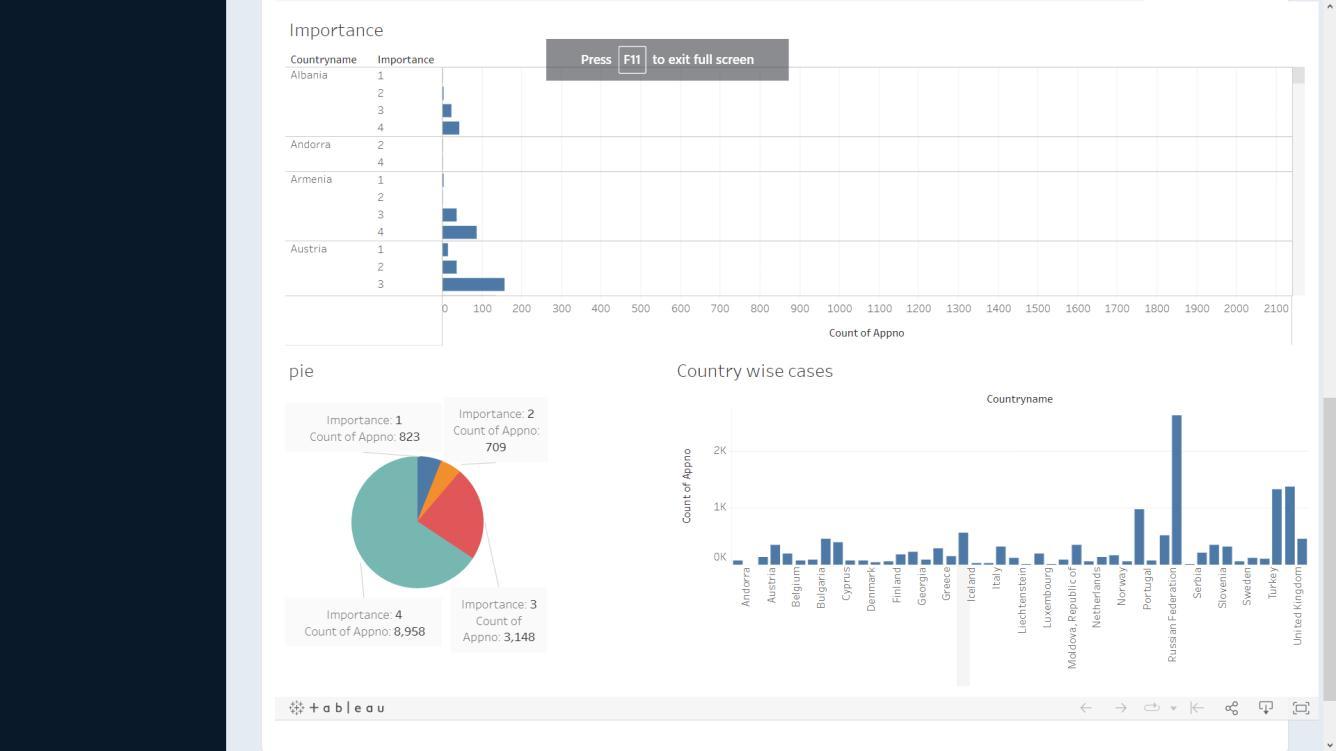
Datavisualizationistheconceptofconvertinginformation into a visual context via captions, maps, or graphs in a manner that allows the brain to easily comprehend and analyzedata.Itfacilitatestheprocessofidentifyingpatterns, trends,andoutliersinlargedatasetsbyusingadashboard thatcontainsinformaticsgraphics,visuals,andstatistics.Itis widely used in the data science process after data is collected, processed, and modelled. It is capable of identifying, locating, manipulating, formatting, and deliveringdatainthemostefficientmannerpossible.Users maydiversifyfromeducatorsusingittodisplaystudenttest results to computer scientists for advance artificial intelligence(AI)analyzes,andexecutivescanuseittoshare informationwithstakeholders.Theprominentsoftwareused forvisualizationtableauwhichisusedforourproject.
2.4 Gradient Boosting
Boostingisanensemblemodellingtechniquethatcreatesa strongclassifierfromasetofweakclassifiers.Amodelfrom trainingdataiscorrectedaftererrors,andmodelsareadded untileithertheentiretrainingdatasetiscorrectlypredicted or the maximum number of models are added. Gradient boosting was taken a step further, with each predictor
correctingtheerrorofitspredecessor.Itismainlyusedin classificationandregressionproblems.Givenitspracticality indealingwithmissingdata,outliers,andlargecardinality categoricalvaluesonyourfeaturesevenwithoutadjuvant, this technique is frequently utilised in many applications. The kind of input (numeric and categorical), managing missing information, and flexibility are all advantages. Overfitting, on the other hand, can occur and is computationally costly. The 4 types of gradient boosting includesgradientboostingmachine,xgboost,catboostand lightgbm.Allofwhichprovidehighaccuracy,butischosen dependingontheapplicationanddatachosengiven.
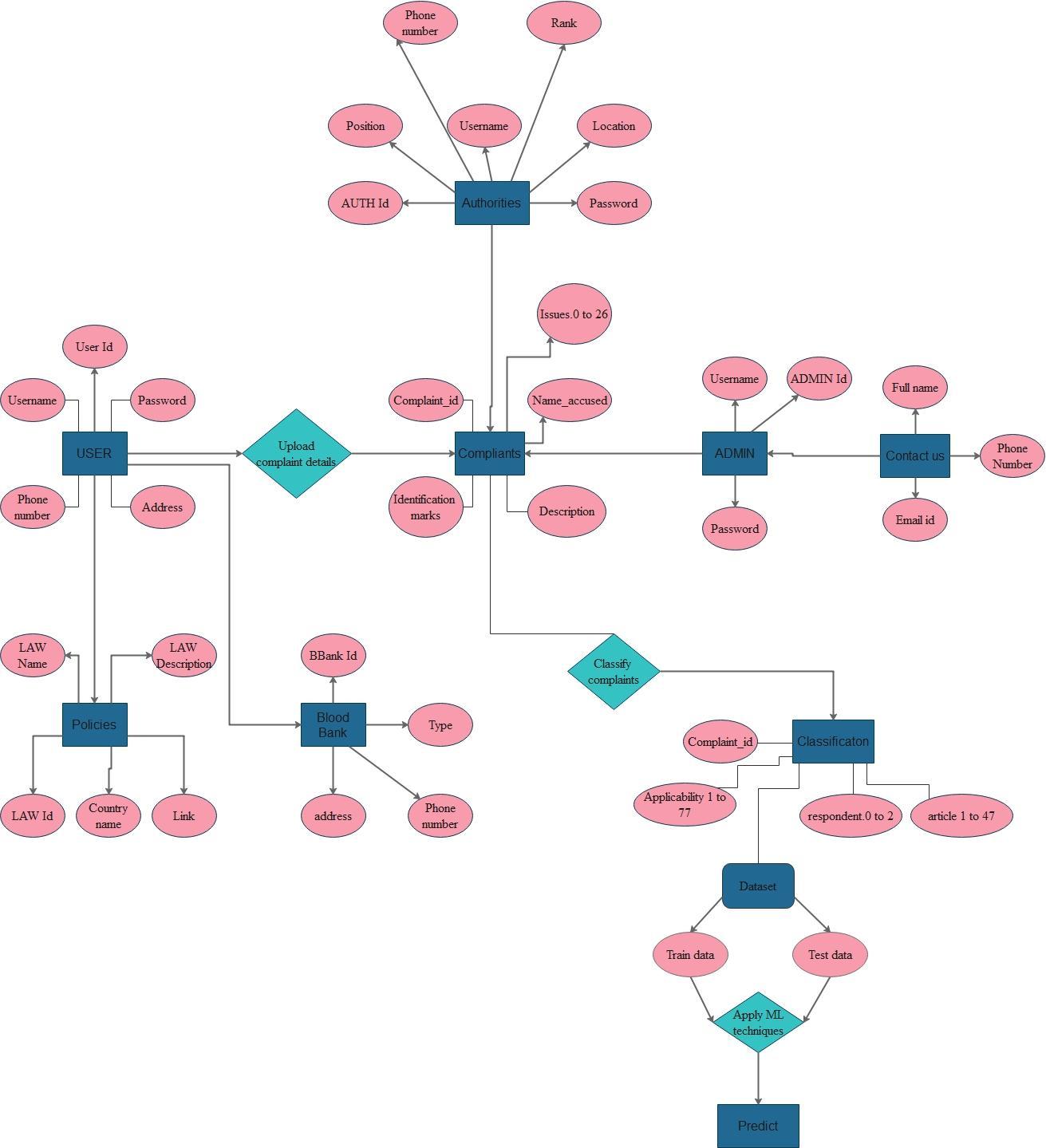
3. Dataset Features
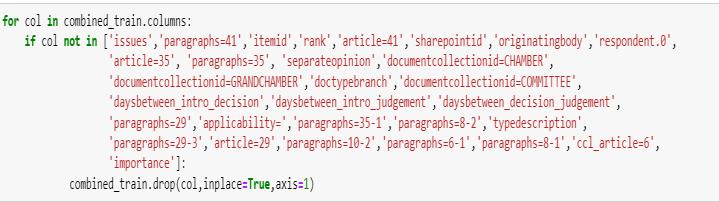
Our application is based on a Kaggle dataset of violent crimes against women in various countries comprising of trainingandtestingdata.Intotal,thedataconsistsof13638 recordsand329featureswhichareinconsistentwithtextual andnumericaldataandhasunprocessedinformation.The trainingdatahasgrievancedescriptionalongwiththerank where1indicatinglowurgencyand4implicatingimmediate attention. Datafeatureswerefilteredandselectedbasedon Extra Tree classifier to remove redundant material thus increasingtheaccuracy.
Feature
Issues
Paragraphs 41,Paragraphs_34, Paragraphs_35,Paragraphs_35-1, Paragraphs_8-2,Paragraphs_29-3, Paragraphs_10-2,Paragraphs_6-1, Paragraphs_8-1
Complaint_id
Rank
Description
Description of distinct issues present in dataset
Law id and description linked with a typeofissue.
Unique id of complaint
Level of importance of issue, ranging from1-4
Article 35, Article_41, ccl_article_6, Article_29 Name of law article applicable to thecase
Share point id
Encodedvalues
Incident_location Location were incident took place
Res_country
Name of country responding to the complaint incident
Separate opinion Binary values
Document_id_c
representing valid and invalid
The document istorespective of category chamber
Document_id_gc
The document istorespective of category grandchamber
Category Typeofissue
Document_id_comm

The document istorespective of category committee
Applicability
Types of relevancy linked with case
Type_description
Interval_intro_decision
Different types ofissuepresent
Time taken to give decision fromcomplaint registereddate
Time taken to passjudgement fromcomplaint registereddate Interval_decision_judgement Time take to passjudgement from decision date
Interval_intro_judgement
4. Data Pre-processing
Datapre-processingisatechniquefortransformingdatainto amoreaccessibleandefficientformat.Inreal-time,mostraw data contains null values, superfluous values, duplicate values,andnoisewithnoorderortrend,whichcanhavea significant impact on the model's performance. This preprocessingapproachcleans,consistencies,andorganisesthe datainordertoadequatelytrainthedatasetforanefficient model. There are numerous methods for initialising this technique, including filling NA or NULL values, deleting duplicatevalues,dealingwithoutliers,normalisingthedata to make it scale free, and smoothing to deal with noise, among others. Because our dataset is somewhat huge, we usedavarietyofdatapre-processingtechniques,including thefollowing:
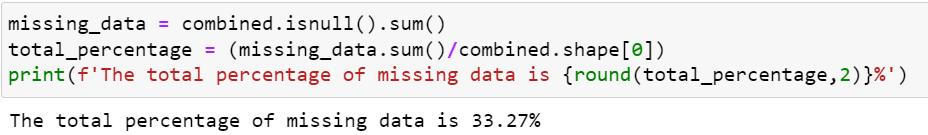
4.1 Amount of Missing Data
Missing_data=combined.isnull().sum()createsanew DataFrame missing_data that contains the count of
missingvaluesforeachcolumnofthetraindataset.The isnull() function examines for missing values in the train datasetandreturnsmissingdataofthesamestructurewith Trueformissingvaluesand Falseotherwise.Additionally, sum()functionisusedtocalculatethefrequencyofmissing valuesineachcolumn.
4.4 Featurize Columns
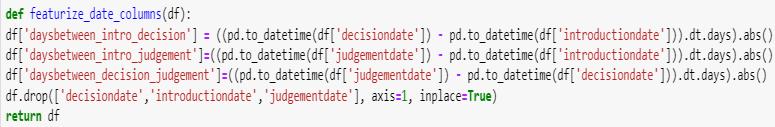
Thisfunctionformulatesnewattributesbycomputingthe absolute number of days between the combinatinons of 'decisiondate'and'introductiondate','judgementdate'and 'introductiondate',and'judgementdate'and'decisiondate' usingthedt.daysattributeandtheabs()method.
4. 2 Combining Issues
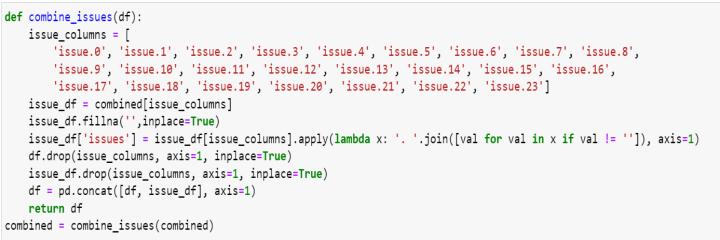
Thisfunctioncombinesmultiplecolumnscontainingissue informationinatraindataset,thefunctionfirstdefinesalist issue_columns containing the names of the columns that contain issue information. It results in a new DataFrame issue_dfthatcontainsonlythesecolumnsfromtheoriginal DataFrame df. The fillna() method is used to replace any missing values in the issue_df DataFrame with an empty string. The resulting string is assigned to the new 'issues' column.Thiscodeeffectivelycombinesalltheissuecolumns intraindatasetintoasinglecolumncalled'issues'.
4.5
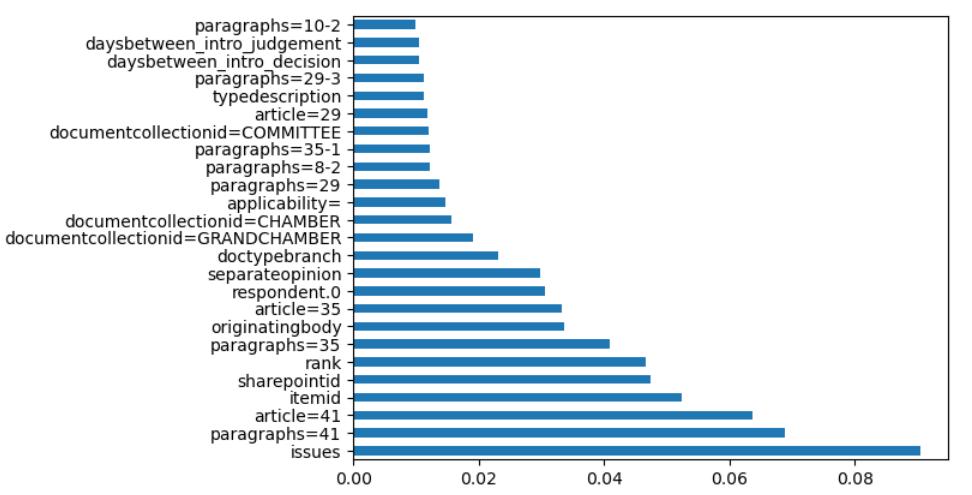
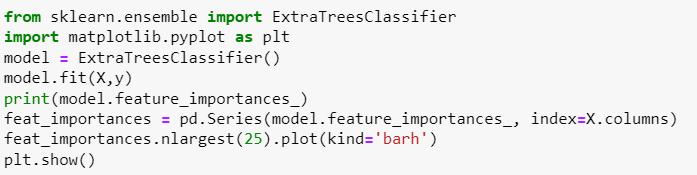
UsingtheExtraTreesClassifier,identifyingthetop25 featureswiththelargestfeatureimportancesandusing thenlargest()methodtoplotthemusingahorizontal barplotforbetterunderstanding.

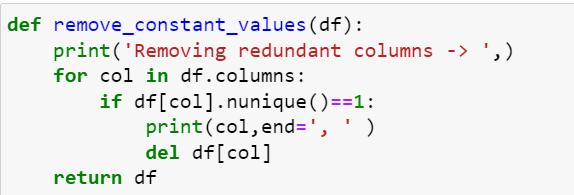
4.3 Discard Superfluous Features
Removesfromatrainingdatasetcolumnsthatonlyhavea singleuniquevalue.Thesecolumnsaredeemedunnecessary sincetheyprovidenovaluableinformation.
Thisfunctiondeletestheotherfeaturescolumnsapartfrom top 25, to train a simpler model with fewer features and moreaccuracy.
4.7 Features Scaling
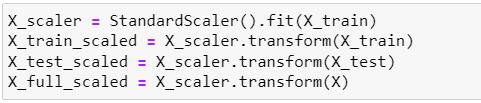
This function transforms the training set using the transform() method of the StandardScaler object to standardize the features by subtracting the mean and dividing by the standard deviation. Feature scaling is a commonpre-processingstepinmachinelearningthathelps to improve the performance of many model which is especially useful when working with features that have different scales or units. By scaling the features, we can ensurethattheyareallonasimilarscale,whichcanhelpthe model converge faster and make the results more interpretable.
optima.SomeapplicationsofSVMmaybeappliedtobinary andmulti-classclassificationissues,forecastingthedistance between the test point and the hyperplane in regression issues.SVMcanbeinfluencedbythekernelfunctionusedto translate data into a higher dimensional space. One drawback ofSVMisthatitscomputationallycostlyforbig datasetsandmighttakealongtimetotrain.
5.1.2 KNN
K-Nearest Neighbours is a fundamental classification algorithm in Machine Learning, which comes under supervisedlearningalgorithmthatiswidelyusedinpattern recognition,datamining,andintrusiondetection.Itiswidely applicable in real-world scenarios, because it is nonparametric, which means it makes no underlying assumptions about data distribution. When dealing with largedatasets,therobust,simplealgorithmcomesinhandy, butitcan bedifficultto determine Kvalueandhasa high consumptioncost.Theapproachispredicatedonthenotion that data points in the feature map that are close to each otherbelongtothesameclass.KNNisalazylearner,which meansitmemorisesthetrainingdataandutilisesitattest time rather than learning a model from it. The time complexityandauxiliaryspaceforthespecifiedalgorithm areO(N*logN)andO(N*logN),respectivelyO(1).
5.1.3 DECISION TREE
5. Machine Learning
Theuser'scomplaintservesasinputtothemachinelearning system, which classifies the urgency of the case before assigningittotheappropriatepoliceofficer.Theinstances areprioritized and processed out instantly based on the output rank. The model utilizedfilters outunnecessary or duplicatedforms,boostingtheapplication'sefficiency.The maintenanceandarrangementofcasesaremethodicaland effortless with suitable organization, resulting in further studiessuchaspredominantcasetype, locationof events, andsocialbehavior.Wemaytrainandevaluatedataforthat model before deploying it. After making the necessary adjustments,thecomplaintswillbesavedinthedatabase.
5.1 Classical ML Techniques
5.1.1 SVM
SVMisaprominentmachinelearningmethodthatisusedfor classification and regression problems. SVM works by locatingthehyperplanebydatapointsarecloseaspossible throughwhichitdividesthedataintodistinctgroups.This approachcanhandlelargedatasetswithmanydimensions, efficiently working with tiny datasets unaffected by local
Decision trees, which recursively divide the data into subgroups based on the value of a feature, are another categorizationapproach.In ordertooptimiseinformation gain or reduce impurity in the subsets, the partitions are chosen.Bothqualitativeandnumericaldatacanbehandled by the straightforward and clear DT algorithm. Even with limited datasets, DT performs well and is unaffected by outliers serving as its highlights. This approach is mainly usedforclassificationproblems(binaryandmulti-class)and regressionbycalculatingtargetvariable'smeanormedian for each leaf node. Factors like splitting criterion and the depthofthetreemayinfluenceitsperformanceandresultin overfitting if the tree is too deep or if the training data is noisy.
5.1.4 RANDOM FOREST
Random Forest is a commonly used algorithm for classification and regression problems using supervised learning.Itisbasedonensemblelearning,whichmeansthat multipleclassifiersassistinsolvingandenhancethemodel's performance.Themodelforecastsitsfinaloutputusingthe majorityvotesofpredictionsfromeachtree,whichwould showadirectproportionalitybetweenthefrequencyoftrees andaccuracyrate.Thekeybenefitistheaccuracyevenwith enormous datasets and relatively short training time. The modelmightnotbeappropriateforsomeregressiontasks

andcanbecomputationallyintensiveforlargedatasetsand canrequiresignificanttrainingtime.
5.1.5 CATBOOST
This updated ensembler can handle categorical features utilising sorted target statistics rather than one-hot encoding.Thegreedytechniquetakestheaimforacategory group andaveragesit. One advantageous characteristic of thismethodisitssuccessfulusewithdefaultparametersand decisiontree,whichreducesthetimerequiredforprediction and parameter adjustment. Nevertheless, target leakage occurs because the target value is utilised to construct a representation for the categorical variables, which is then usedforprediction.Basedonthedata,CBcanautomatically choosetheidealnumberoftreesandmanagemissingvalues. Althoughtherearevariousbuilt-inmethodsfortuningthe hyperparameters,itcanbesensitivetotheselectionofthe parameters. Its applications include ranking, recommendation systems, forecasting, and even personal assistants.
4.1.6 LIGHTGBM
Toaddresstheconstraintsofhistogram-basedtechniques, whicharetypicallyutilisedinallrelevantframeworks,Light GradientBoostingMachineutilisesGradient-basedOneSide Sampling and Exclusive Feature Bundling (EFB). The fundamental distinction in decision trees' construction is that the tree is divided leaf-wise, with the leaf with the largest delta loss being chosen to grow. To handle categorical characteristics, LightGBM employs a unique technique that combines one-hot encoding with the gradient-basedapproach.Thecapacitytomanage missing values, reduce memory use and training time by of the histogram-basedfeaturebinningandautomaticallychoose theidealnumberoftreesdependingonthedataarejusta fewofthisgradientboostingmethod.
4.1.7 XGBOOST
In eXtreme Gradient Boosting, weights are allocated to all individualisticvariables and then supplied into a decision treethatforecastsresults.Thosepredictedinaccuratelyby thetreeareraised,andthesefactorsarethensentintothe second decision tree. Individual classifiers/predictors are thenused.Theseindividualclassifiers/predictorsarethen amalgamatedtocreateamorepowerfulandprecisemodel. Regularization and handling of missing data are done bygenerallycharacterisedthemashyperparametersinthe objective function. Weighted quantile sketch is a new additionthatspeedsupthealgorithm'strainingprocessand useslessmemory.Duetoitsrobustandaccuratenature,its application vary including problems involving regression, classification,ranking,anduser-definedprediction.

5.2 Proposed Model
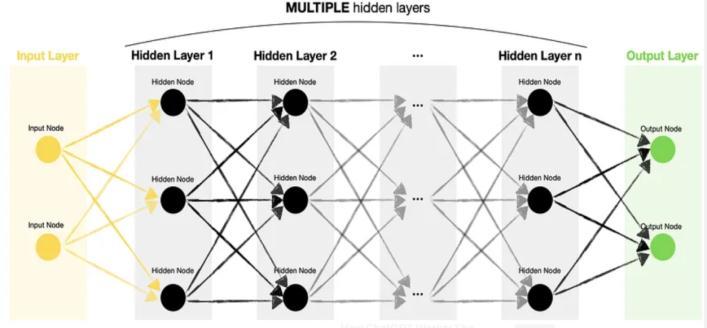
Ourapplicationusesdeepfeedforward,atypeofartificial neuralnetwork.Thealgorithmisbasedontheprinciplethat inputs labelled with weights are passed through multiple hidden layers before being computed together and compared to the threshold value. Back-propagation is a processinwhichtheweightsofthedatasetarealteredusing thedeltarulebasedontheoutput.Thegeneralarchitecture layersaremadeupofneurons,activationfunctions,sigmoid, tanh,andrectifiedlinearunits,aswellasinput,output,and hiddenlayers.
Theneural network operatesina singledirectionwith no cycles, with each layer of neurons performing a nonlinear transformationontheinput andfeedingthe outputtothe nextlayer.Commencingwiththeinputlayer,itfunctionsasa neuralbridgetothehiddenlayercomposedof neuronsthat applyaweightedsumoftheinputstoanonlinearactivation function. Itresults in the neuron's output, which is then adjustedthroughbackpropagation.Theactivationfunction employed depends on the issue; for example, the sigmoid function is widely used in binary classification issues, whereas the softmax function is utilised in multiclass classification problems. For regression issues, the output layer is typically built around one neuron with a linear function. Imagecategorization,naturallanguageprocessing, andspeechrecognitionarejustafewoftheapplicationsfor theDFFmodel.Nevertheless,ifthenetworkistoovastorthe trainingdataisnoisy,theymaysufferfromoverfittingwhich canbepreventedthroughregularizationtechniqueslikeas dropoutorweightdecay.
Thealgorithmdatasetwaschosenfromkaggleasatraining set with 8,878 records and 328 features and a testing set with 4,760 records and 328 features for our application. Bothof whichare pre-processedto exclude inappropriate andnulldataandadjustfeaturesandrecordstoensurethe performance efficiency of the algorithm. After conversion and universalization of content, removal of redundant constantfeatures,thedesiredfeaturesareselectedbasedon univariateselectionandfeatureimportance.Theformeruses SelectKBestclass,providedbyscikit-learnlibrary,tofindthe topfeatureswithstrongestlinktotheoutputandthelatter
usesExtraTreeclassifiertoscoreitsrelevancetowardthe output. After which, the dataset is split into training and testing batches where train size comprises of 80% data. UsingthescalerobjectcreatedbyStandardScaler,thedata are scaled and reshaped according to the input type. DFF (deepfeedforward)modelisinitiatedwithinputlayerof25 selectedfeatures.Followingwhichare5hiddenlayerseach with a specified dense layer of varied neurons frequency, activation of rectified linear units and HeNormal kernel initializer.Tocounteractover-fittingthetrainingdataset,a dropoutrateof0.4isemployedtodiscard40%ofthenodes' material. The output dense layer uses softmax activation consistsof5neurons,becauseofthepresenceof4levelsof urgency.
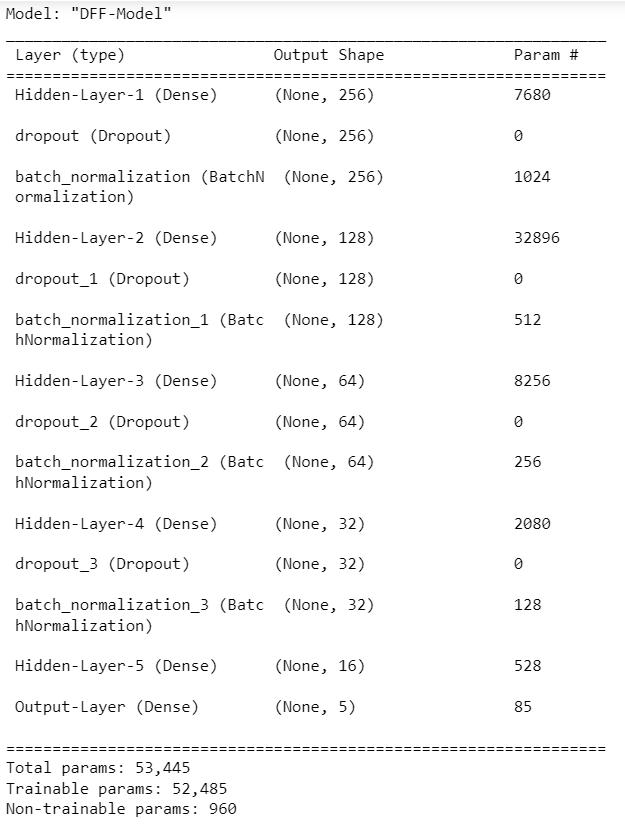
6. Results (comparison)
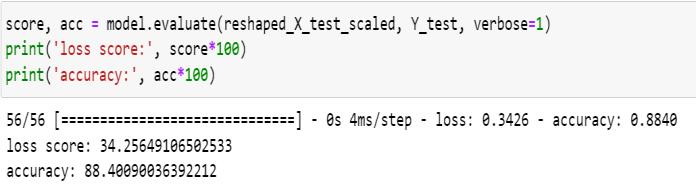
Using the Deep Feed Forward model, the dataset of was trained of 13,638 records and 329 features to ultimately rankeachinstancefrom1to4.Thesequentialmodelusing theoutputdenselayerthroughsoftmaxactivationgivesthe outputaccuracy.Themodelhasatotalof53,445paramsin which52,485aretrainableandtherestare non-trainable. The DFF model uses the adam optimizer to compile its accuracy. Through 300 epoch with batch size of 128, the model was evaluated to have a loss score of 34.26% and accuracyof88.40%.
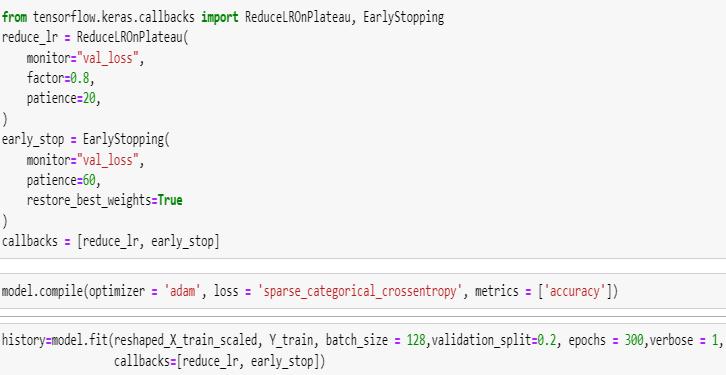

These callbacks in Keras used for monitoring the training process and preventing overfitting, learning rate will be reduced if the validation loss does not improve for 20 epochs, and the training process will be stopped if the validationlossdoesnotimprovefor60epochs.Theweights of the best-performing model during training will be restored
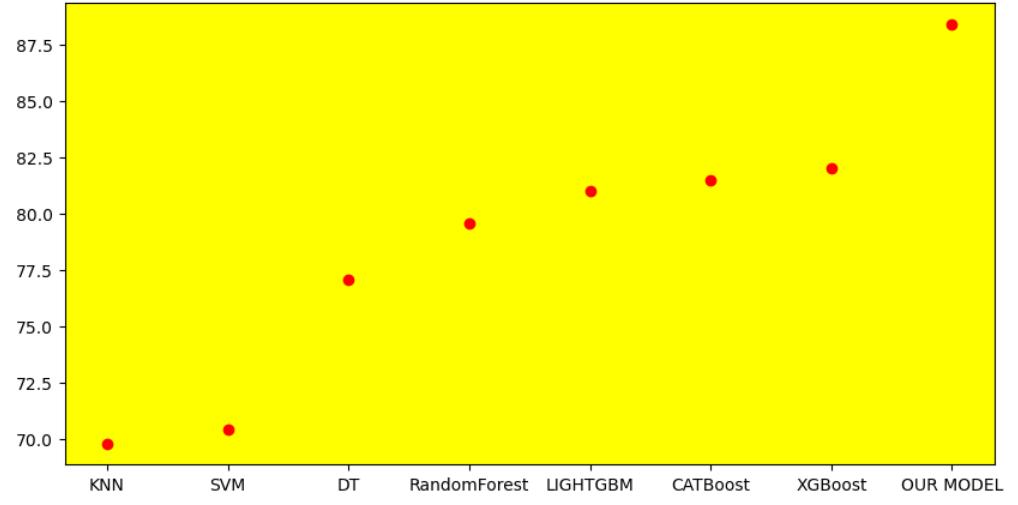
Incomparisonwiththeothermachinelearningtechniques,it isobservedthatDFFhasthehighestaccuracyrate.

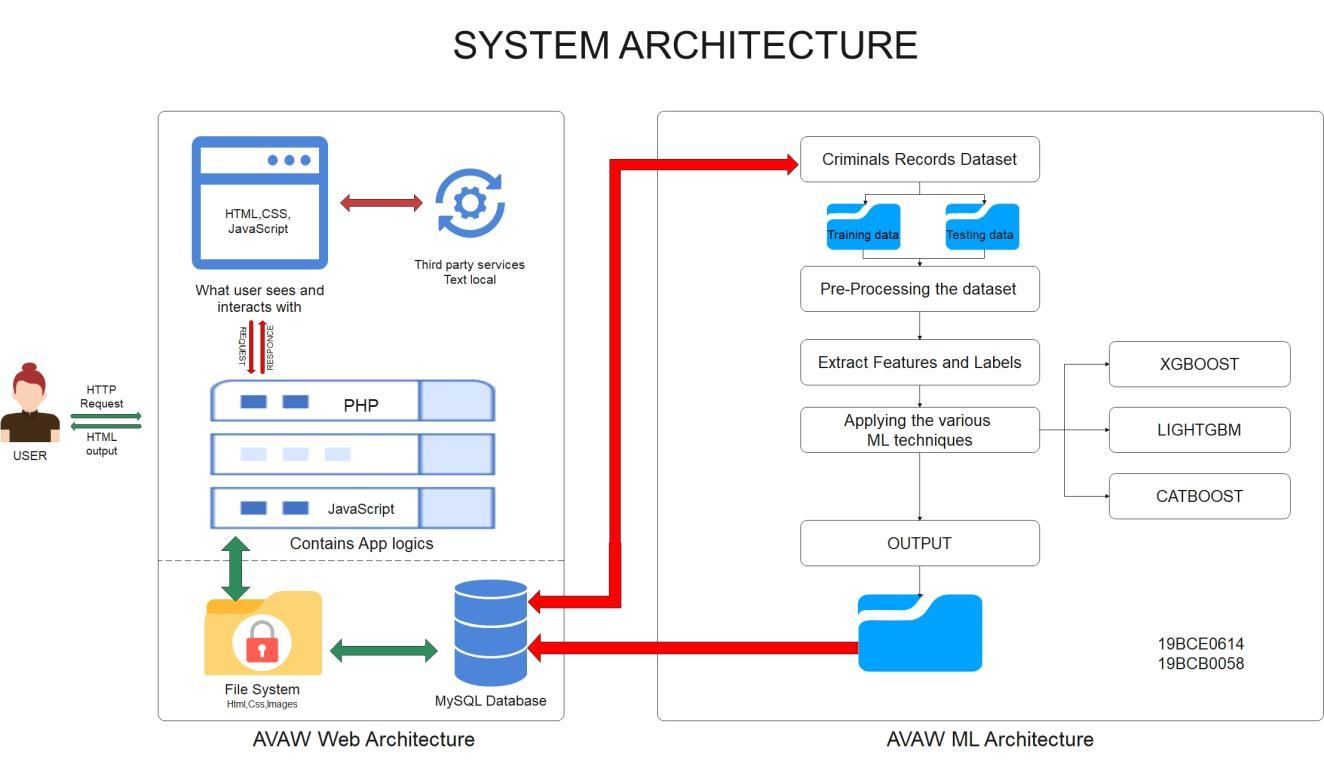











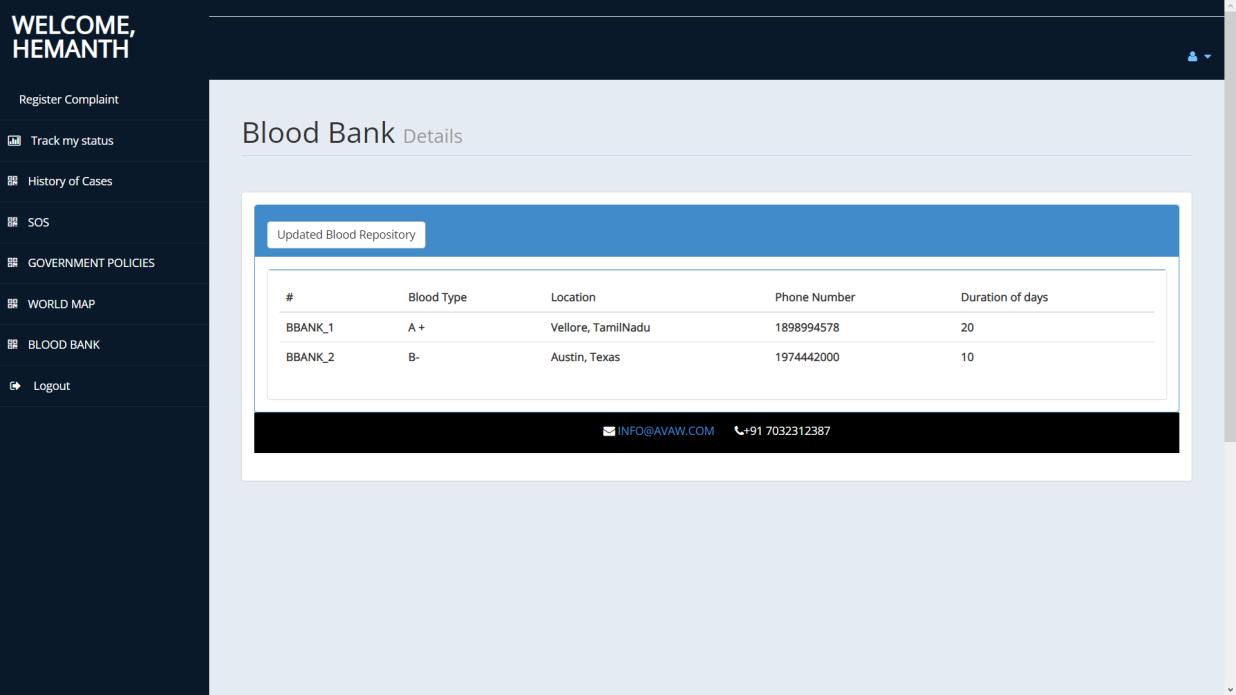

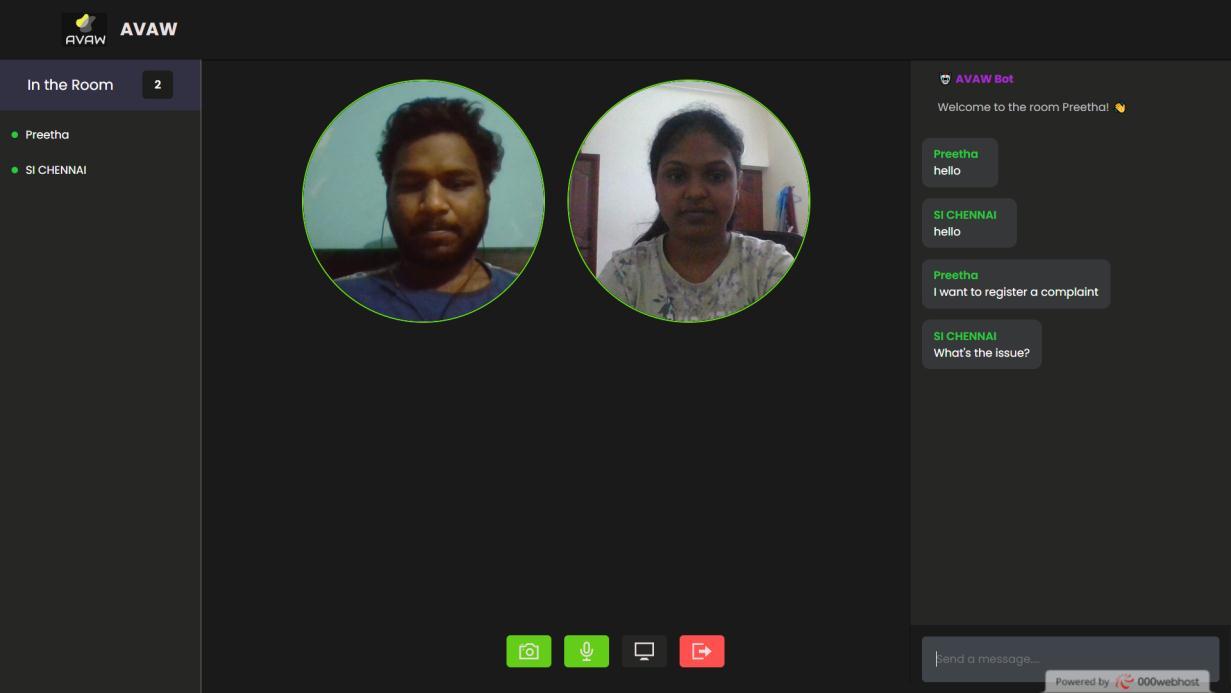
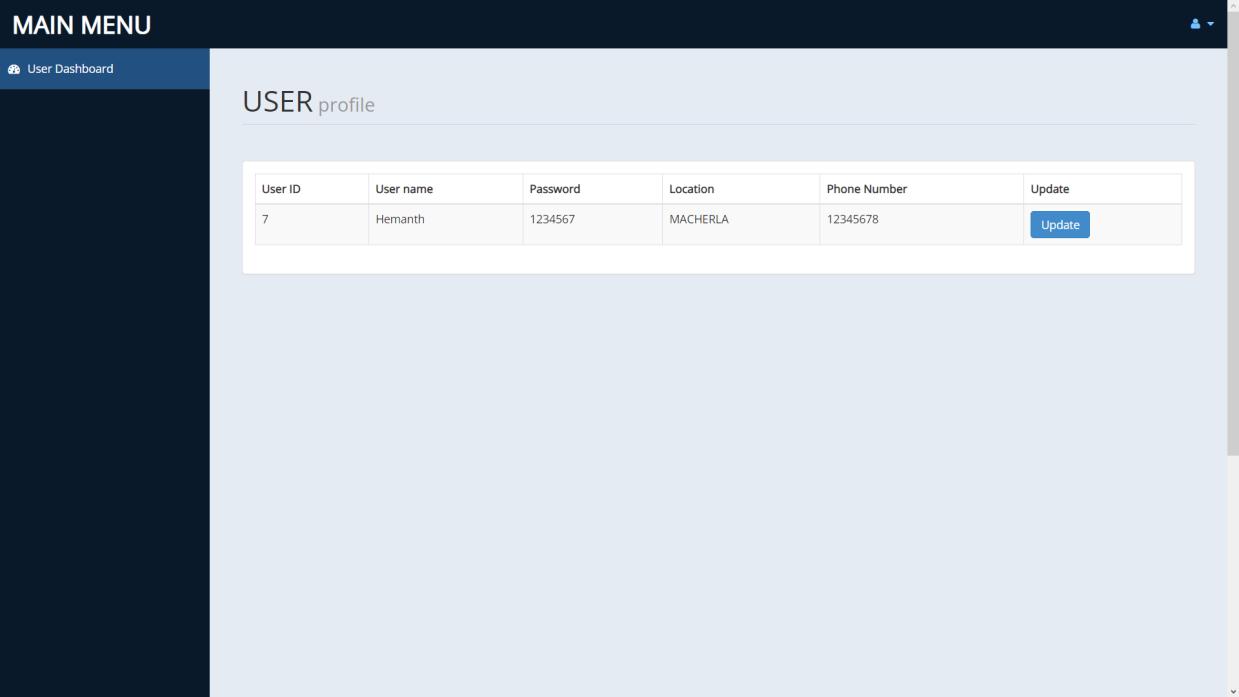
AUTHORITY MODULE:
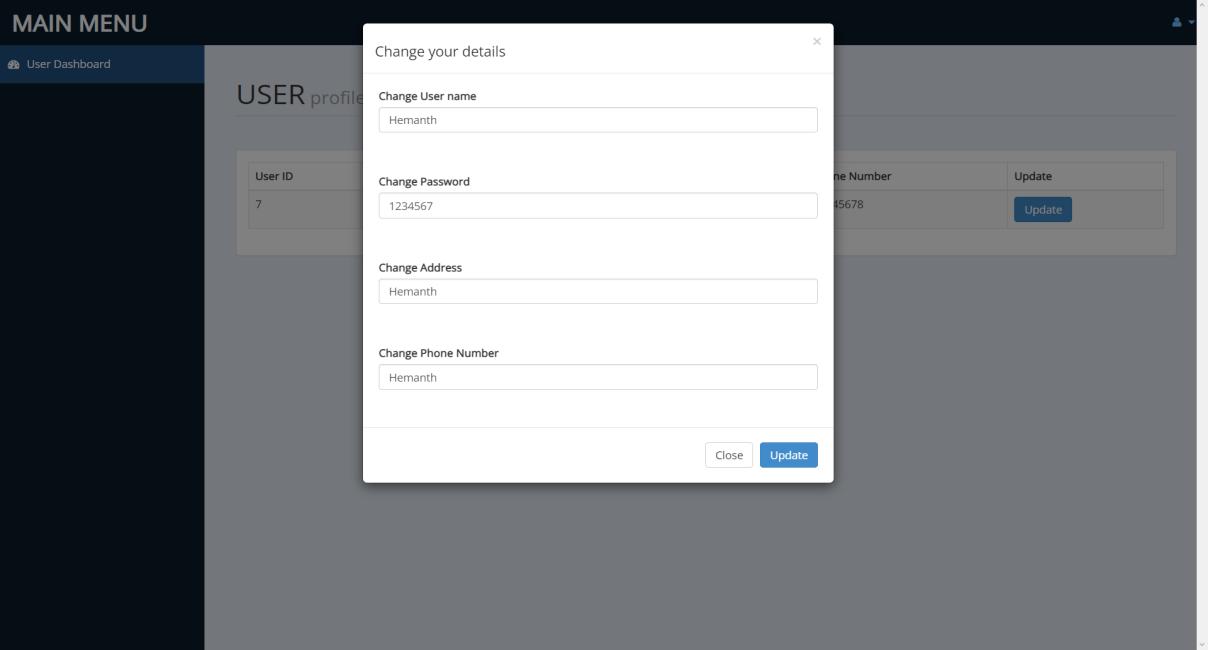
Authoritiesarethegovernmentofficialsandtheywillhaveaccesstothefunctionsaccordinglyaftersignupandloginprocess. Theywouldberequiredtofillinlegitinformationliketheirfullname,phonenumber,locationandpositionofauthority.The systemwillredirectthemtothelandingpageinwhichfeatureslikecasesrecords,historyofcasehandledbythem,status tracking,databaseexportingandlawandorderdatabaseareavailable.Sinceuserscanvideocalltothenearbypolicestationto communicatetoaconstable,policeofficerscanjointheroomaccordingandmakearecordoftheircaseasanofficialcomplaint. Theirprofilecanbeedited.

CASE RECORD PAGE
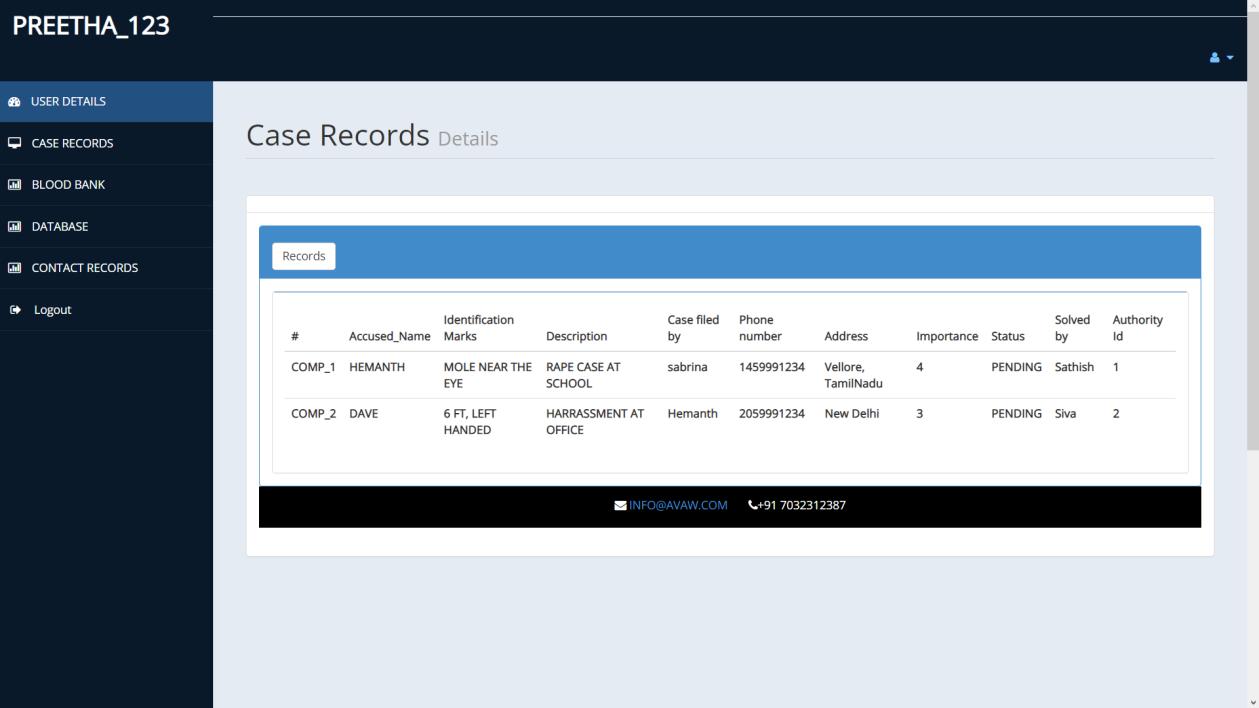

ADMIN MODULE:
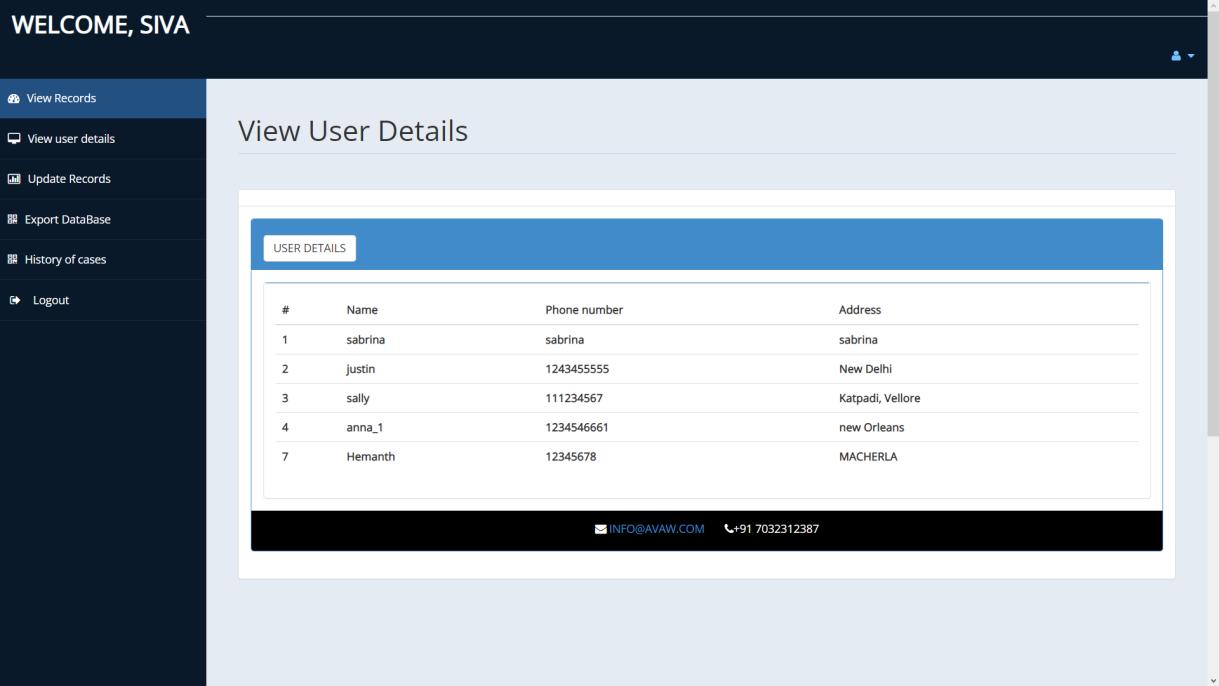
Adminisresponsibleformonitoringandmanagingalldatastorageandoverallsystem.Withproperauthentication,adminhas accesstothelandingpagecontainingallfeaturesfromviewingcaserecordsanduserdetailstomanagementofdatabaseandits exportation.Theadminneedstofilteroutunnecessaryorinappropriateinformationenteredbyeitheroftheotherusersofthe system.


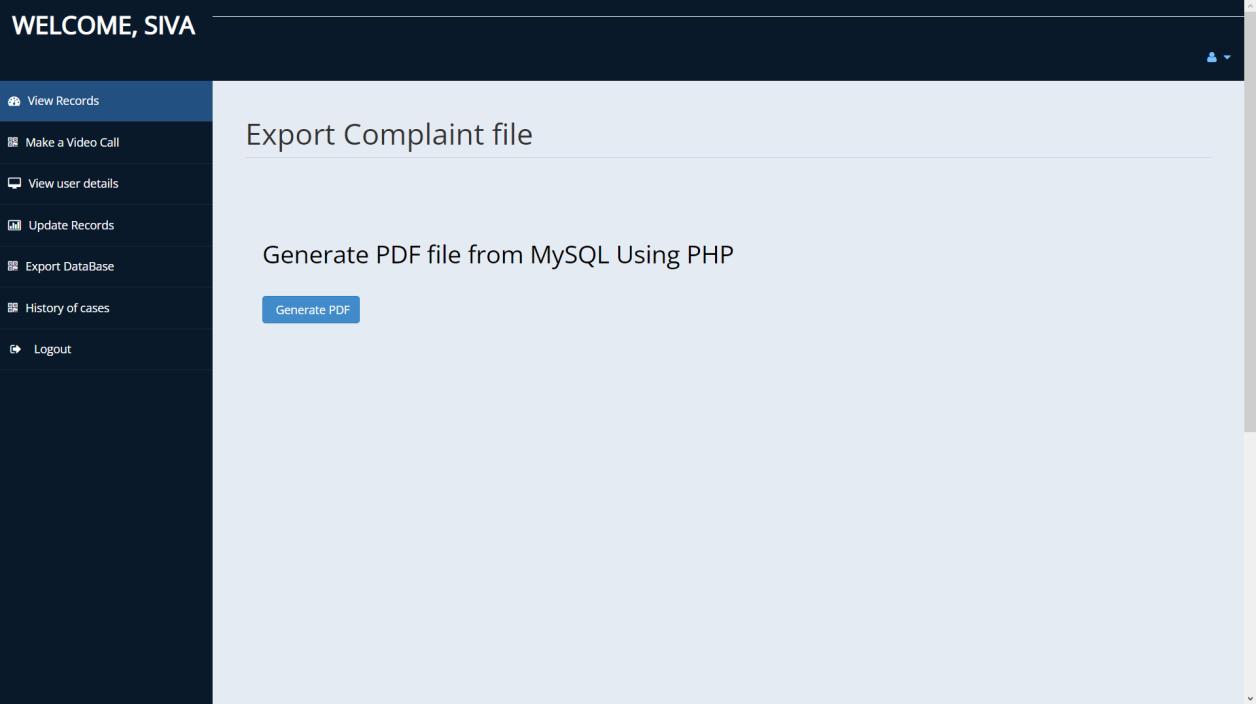
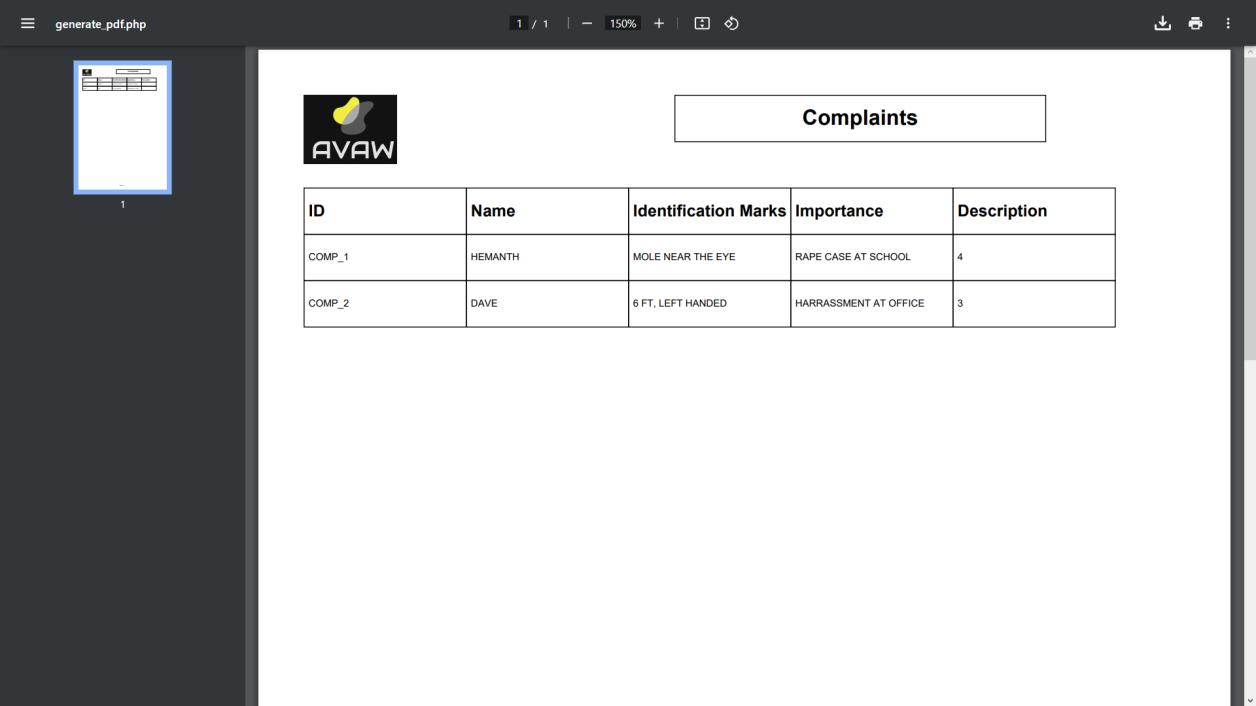

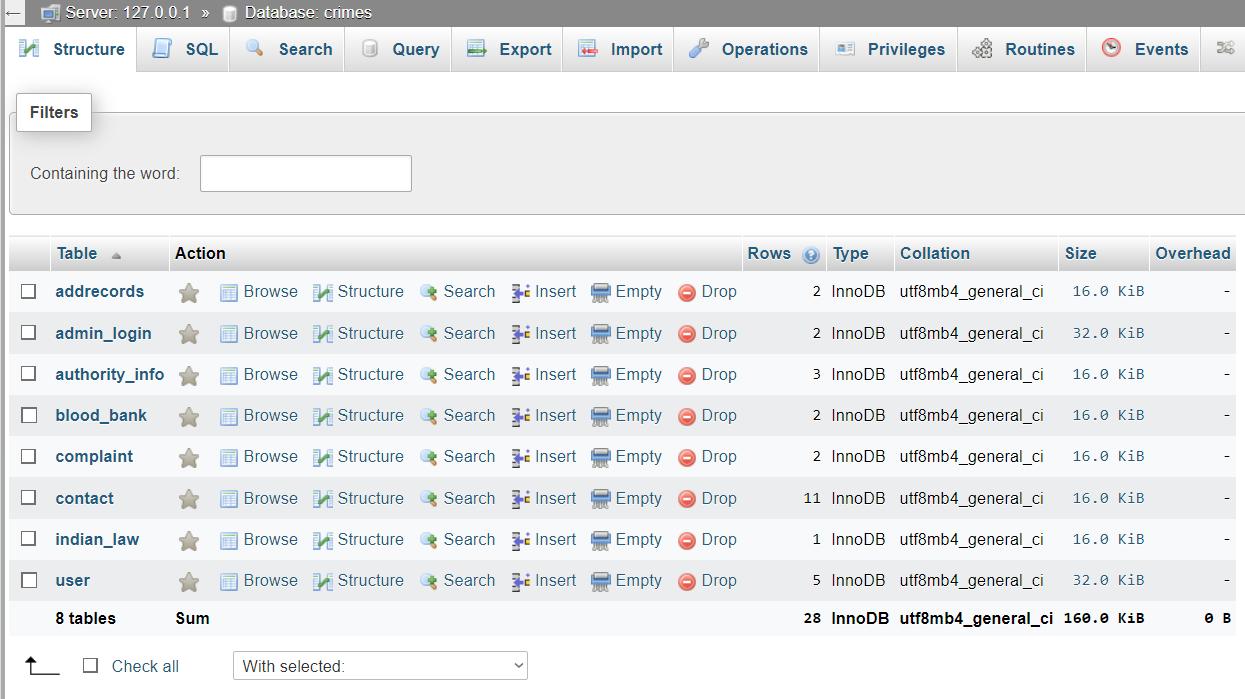
CONCLUSION
Lawenforcementdepartmentsarefacingnewchallengesascrimeratescontinuetorise.Theymustkeeptheirforcesonthe lookoutforanysignsofcriminalactivity,especiallyinvolvingwomen.Thegoalofthisapplicationistoanalyzeandpredict varioustypesofcrimes.Thefinishedproductwouldbeawebapplicationwiththepreviouslymentionedelementssuchasa userforum,aworldmapdashboard,services,andagovernmentpolicypage.Inthefuture,theapplicationcanbefurthered developed by adding an illustration of the accused person in the complaint which can be sorted and analyzed by image recognition.InadditiontotheWebRTC,wecanaddoptionsforvoicetranslatingservicesandspeechtotextconversionfor users.
REFERENCES
[1] Mishra,Shivani&Kumar,Suraj.(2019).“AcomparativestudyofcrimesagainstwomenbasedonMachineLearningusing BigDatatechniques”Conference:InternationalConferenceonDistributedComputingandInternetTechnology
[2] Vineet Pande, Viraj Samant, Sindhu Nair, 2016, Crime Detection using Data Mining, INTERNATIONAL JOURNAL OF ENGINEERING RESEARCH & TECHNOLOGY (IJERT) Volume 05, Issue 01 (January 2016), http://dx.doi.org/10.17577/IJERTV5IS010610
[3] P.DasandA.K.Das,"Crimeanalysisagainstwomenfromonlinenewspaperreportsandanapproachtoapplyitindynamic environment,"2017InternationalConferenceonBigDataAnalyticsandComputationalIntelligence(ICBDAC),Chirala, AndhraPradesh,India,2017,pp.312-317,doi:10.1109/ICBDACI.2017.8070855.
[4] VinayNarayanBhat,VSanthoshKumar,Prof.SaravananC,”AnalysisandPredictionofCrimeagainstwomeninIndiausing machinelearningalgorithms.",InternationalJournalofEmergingTechnologiesandInnovativeResearch(www.jetir.org), ISSN:2349-5162,Vol.8,Issue6,pageno.a752-a758,June-2021,Available:http://www.jetir.org/papers/JETIR2106104.pdf

[5] M.R.Reza,F.M.B.Mannan,D.Barua,S.Islam,N.I.KhanandS.R.Mahmud,"DevelopingaMachineLearningBasedSupport System forMitigatingthe SuppressionAgainst WomenandChildren," 2021 5th International Conference on Electrical Engineering and Information Communication Technology (ICEEICT), Dhaka, Bangladesh, 2021, pp. 1-6, doi: 10.1109/ICEEICT53905.2021.9667924.
[6] Yang,M.,Wong,S.C.P.,&Coid,J.(2010).Theefficacyofviolenceprediction:Ameta-analyticcomparisonofninerisk assessmenttools.PsychologicalBulletin,136(5),740–767.https://doi.org/10.1037/a0020473
[7] P.TamilarasiandR.U.Rani,"Diagnosis ofCrimeRateagainstWomenusingk-foldCross ValidationthroughMachine Learning,"2020FourthInternationalConferenceonComputingMethodologiesandCommunication(ICCMC),Erode,India, 2020,pp.1034-1038,doi:10.1109/ICCMC48092.2020.ICCMC-000193.
[8] A.Adhikary,S.A.Murad,M.S.MunirandC.S.Hong,"EdgeAssistedCrimePredictionandEvaluationFramework for MachineLearningAlgorithms,"2022InternationalConferenceonInformationNetworking(ICOIN),Jeju-si,Korea,Republic of,2022,pp.417-422,doi:10.1109/ICOIN53446.2022.9687156.
[9] Aziz,R.M.,Sharma,P.&Hussain,A.MachineLearningAlgorithmsforCrimePredictionunderIndianPenalCode.Ann.Data. Sci.(2022).https://doi.org/10.1007/s40745-022-00424-6
[10] J.AzeezandD.J.Aravindhar,"Hybridapproachtocrimepredictionusingdeeplearning," 2015InternationalConferenceon Advances in Computing, Communications and Informatics (ICACCI), Kochi, India, 2015, pp. 1701-1710, doi: 10.1109/ICACCI.2015.7275858.
[11] https://www.who.int/news-room/fact-sheets/detail/violence-against-women
[12] https://plan4womenssafety.dss.gov.au/resources/what-is-violence-against-women/
[13] https://www.clearias.com/violence-against-women/#:~:text=In%20respect%20of%20India,According%20to%20the&text=Most%20of%20the%20cases%20of,and%20rape%20(7.4%20percent).
[14] https://www.bbc.com/news/world-asia-india-62830634
[15] https://evaw-global-database.unwomen.org/en/countries/asia/india

