Emotet: A Sophisticated and Persistent Malware for Stealing Information, its Attack and Prevention Strategies
Deepak Reddy A R1, Dr. Chandra Mohan B21 Student at Vellore Institute of Technology, India

2School of Computer Science and Engineering, Vellore Institute of Technology, India ***
Abstract - Many people use internet every day for different activities like browsing, sending emails,banking,socialmedia, and downloading files and videos. EMOTET is an advanced type of virus that mainly focuses on financial systems and individuals to poach personal and financial information. It spreads by false emails to people and also by replicating on itself. It can download other types of malware that attack the system even more, and it can encrypt sensitive data, making it inaccessible to the user. The US-CERT has already warned people about this malware. According to a cybersecurity company called CrowdStrike, dealing with EMOTET can cost up to $1 million per incident.EMOTETusuallyspreadsthrough phishing emails, which can contain malicious links or attachments, like fake PDFs or Microsoft Worddocuments.It's crucial to be careful and not click on suspicious links or attachments to avoid falling victim tothismalware.Thisstudy intends to investigate the effects of Emotet on organizations and people as well as to find efficient preventative measures for this infection. The results of this paper provide valuable insights for businesses and individuals looking to protect themselves against the threat of Emotet and other sophisticated malwares.
Key Words: Emotet, Spider, Malware, Phishing, Cyber Security,Prevention,Banking.
1.INTRODUCTION
Emotet,alsoknownasGeodo,isatypeofmalwarethatfirst surfaced in early 2014 and poses a significant threat to computers and networks[13]. Since its discovery in June 2014, the Emotet malware has grown into a major threat distributor that distributes and drops additional banking TrojanslikeTrickbotandIceDiD.Thisoffersmalware-as-aservice.Itisdifficulttolocateandeliminatebecauseithas beenaroundforawhileandalteredovertime.Thevirusis knownasMUMMYSPIDERbyrenownedcybersecurityfirm CrowdStrike,anditfrequentlychangesitspayloadstoavoid discovery. Itsprimary goal istogainaccesstoaninfected device,collectdatafromthetarget,anddownloadadditional malware payloads to steal credentials. On the Windows operatingsystem,Emotetreplicatesitselfintofixedareas, makingitchallengingtofullyremove.It'sariskymalware thatcriminalsmightusetopropagatebankingTrojansand ransomwarelikeRyukandTrickbot.[12]Securityexpertsat GDATAfoundover33,000distinctEmotetversionsinjust the first half of 2019. Emotet Variant 1 is extremely
dangerousduetoitsmodularcapabilities,whichallowitto carryoutcoordinatedDDOSattacksandstealmoneystraight from the victim's bank account. These modules consist of spambot,banking,anddistributionmodules.
Itsmostrecentexamplescontainmodulesthatcansteala variety of data from the target, including email client credentials,contactlists,webbrowsercredentials,andemail contents. It can propagate through LAN using spam or through WAN using SMB vulnerabilities. Recent spam campaignsbyEmotethavebeenveryeffectiveatinfecting usersbymakingtheemailsappearmorelegitimatebyusing previouslystolenemailconversations.[5]
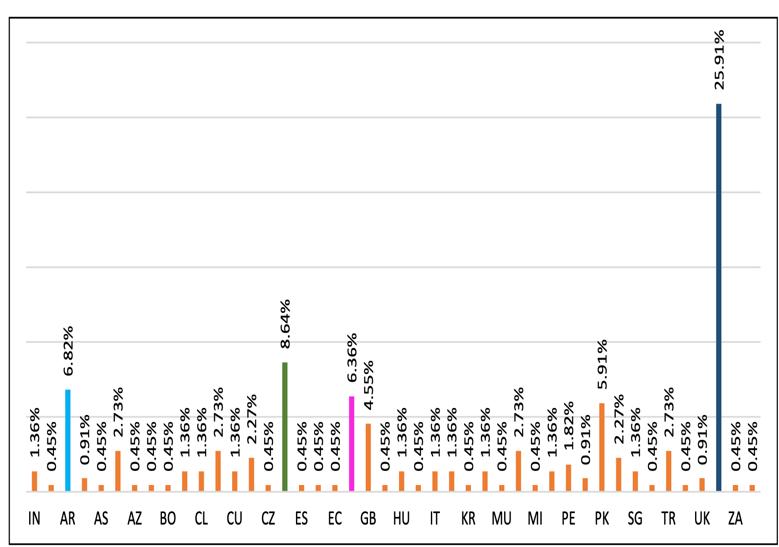
Itcanincreaserights,brute-forcelocalnetworkcredentials, harvestcontactsandrecentemailsfromOutlook,andproxy C2trafficfromotherinfecteddevices.Asitcollaborateswith othertypesofmalware,itspreadsrapidlyonceithasaccess toanetworkandexposesdevicestoawiderangeofthreats. Emotet samples have increased recently, with spam campaigns mainly focusing on users in Lithuania, Greece, and Japan.[9] The most recent Emotet campaign, which madeabigimpressioninmanynationsaroundtheglobe,is the subject of this report. The report examines the attack vector, maps the infrastructure used at different points in thecampaign,andanalysesEmotet'smaliciouspayloadsto determine their potential effect using a carefully crafted dataset
Emotet is among the priciest malware, with remediation expensesofupto$1millionperincident,accordingtoUSCERT. According to Sophos charts, Emotet regularly outperformed malware like GandCrab, HawkEye, Ursnif, Formbook,andAZORultinterms offrequencyofsighting.
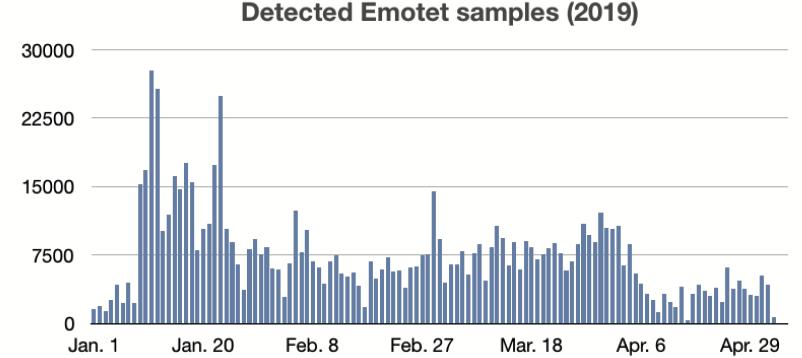
Every day, new Emotet spam campaigns and binaries are released, and countless spam emails are sent daily to guaranteewidespreadinfections.[8]
2. LITERATURE SURVEY
MalwarelikeEmotet,whichhasbeenaroundforawhileand is spread through junk emails, is common. Malicious software,links,ordocumentfileswithmacrocapabilityare the main entry points for it into a device.[1] In order to attract into clicking on dangerous URLs, the malware employs alluring wordinglike"yourinvoice" or"payment details." [4]. The virus was initially distributed through maliciousJSfiles,butasithasadvanced,italsomakesuseof documents with macro capability. Businesses and individuals have a difficult time analysing the malware becauseitishardtodetect.Additionallypolymorphic,ithas thecapacitytoalteritselfeachtimeitisdownloadedonto thecomputer,makingitdifficultforAVstosuccessfullyand pro-activelydetectit.Furthermore,thismalwarelacksany signalsandobtainsupdatesviaC&Cserversinawayakinto how a laptop's operating system updates itself. Financial Trojans are among the malware types that this malware facilitatestheinstallationof.Malwarecanalsorevealprivate informationlikeidentities,passwords,andemailaddresses thathavebeentaken.[4].
It is well known for its behavior, which involves surfing contactgroupsforemailidsinspecificandsendingitselfto the most important contacts. Since the mails are from genuine sources, they don't appear to be spam, and recipientsaremorelikelytoobtainthefilesbecausetheyare fromreliablesources.Thelikelihoodofthemalwaregetting to the financial servers is significant if a user uses it as "password." Through Eternal Blue flaws connected to WannaCryattacks,themalwaredistributes[8].
A Banking Credentials Malware called Emotet Avoiding suspiciousemails,accordingtotheStealerPekta&Acarman team, can also help to prevent the device from becoming infectedwithadware[6].ForusersoftheEmotetmalware, priorarticledidn’tofferanySSA.Thisarticlewillexamine the user awareness problem in depth and give readers a thoroughunderstandingoftheEmotetmalware'ssecurity situation. The purpose of this paper is to examine how similar, despite having different and largely unidentified origins,thisspecificgroupofmalware'sbehaviours[12].
To identify particular network congestion patterns, ML techniques are frequently employed. With a 99 percent discovery rate, SSH congestion is found using a ripper learner[6].Topreventmodelsthatdependonskewedport numbers that are given at random, they remove port nos. fromattributeset.Comparedspecificflowexportersusing MLtechniquestoenhancebotnetcongestionclassification. Themethodinvolvesusinga2-layerperceptionclassifierto detect randomised bot congestion, which is a common techniqueusedbybotstoevadedetection.Additionally,the
approach involves employing transient diligence to differentiatebetweenbenignandharmfulbotcongestion. The proposed work forms the basis for detecting and preventingtheinjectionoftheEmotetmoney-lendingTrojan andmalignantnetworkcongestion.

Thebehaviour-basedMLcategorizationmodelcanidentify someinstancesofEmotetinfectionwithoutexaminingthe PPCorIPaddressesoftheprogram.Overall,theapproach offers a robust and effective solution for detecting and preventing the Emotet money-lending Trojan and other formsofbotcongestion.
3. METHODOLOGY
Emotetisatypeofmalwarethatisprimarilyspreadthrough spammailsthatcontainmaliciousattachmentsorlinks to infectedwebsites.OnceEmotetinfectsasystem,itcancarry outavarietyofattacks.
3.1. Attack Methodology
Emotetisatypeofmalwarethatisprimarilyspreadthrough spammailsthatcontainmaliciousattachmentsorlinks to infectedwebsites.OnceEmotetinfectsasystem,itcancarry out a variety of attacks. Here is a stepwise elaboration of Emotet'sattackstepsandmethods:
1. An Emotet MS Word file is sent to the user as an emailattachment.
2. The user accepts the license agreement when opening the Microsoft Word document, thereby allowingEmotetmacrostorun.
3. Themacrorunsencodedcodeinsidethedocument usingtheterminal(cmd.exe)inthebackground.
4. Command Prompt launches to connect malicious Emotetsites.
5. Themalicioussitesdroppayloadsontothetarget’s machine.
6. ItinstallsTrojanmoduleslikeTrickbot,IceDiDon targetmachine,allowingittostealusers'financial andconfidentialinformation.
7. C2C(commandandcontrol)connectionisusedby Emotettosendstoleninformationtoattacker.
Initial infection: Emotetinfectsasystemthrougha spam email that contains a malicious attachment or a link to an infected website. The email is usually designed to look legitimateandconvincing,encouragingtheusertoclickon linkoropentheattachment.
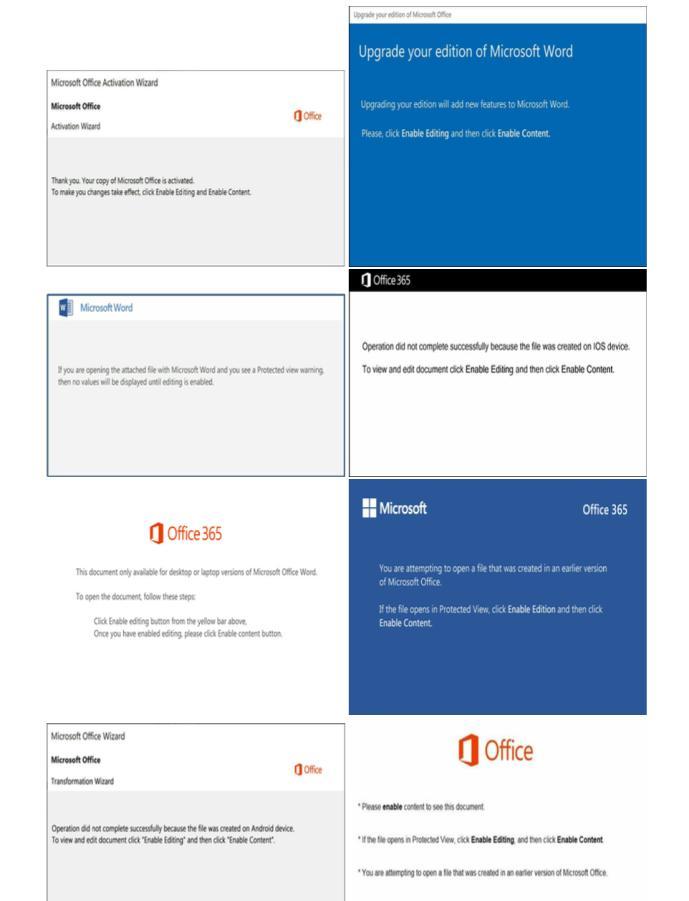
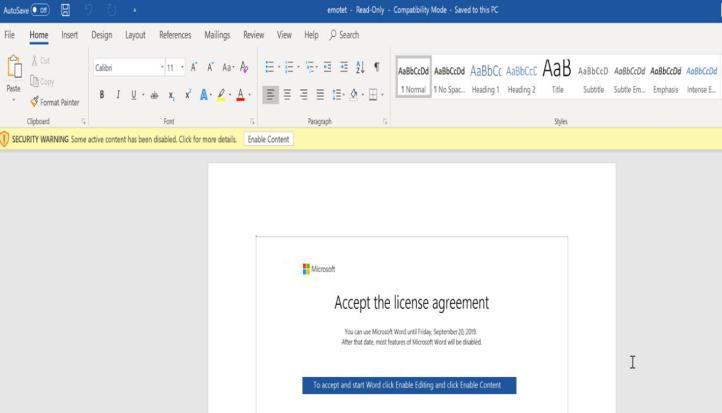
Malware installation: OnceEmotetisdownloadedontoa system,itstartstoinstallitselfandestablishpersistenceby modifyingthe registryandcreatingnewservicesortasks. Thismakesitdifficultforantivirus softwaretodetectand removemalware.
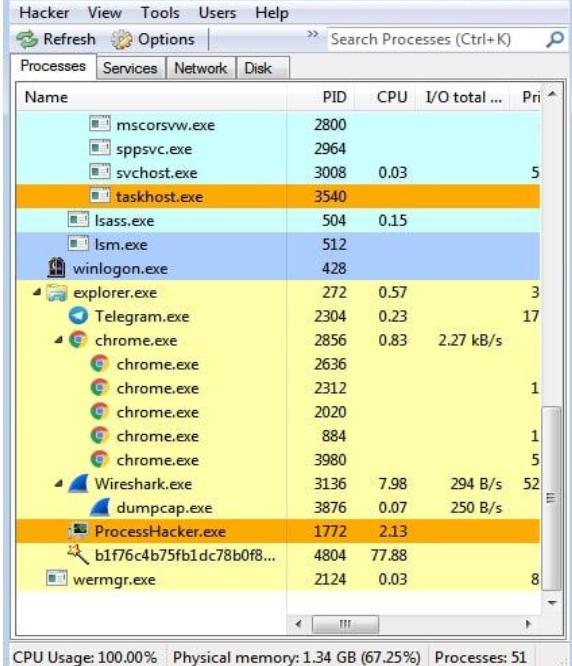
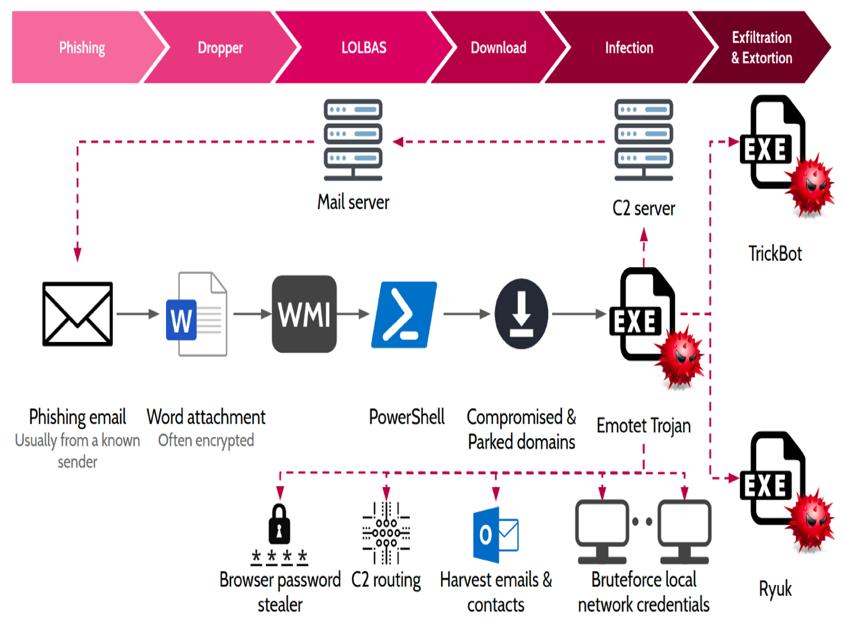

Network propagation: Emotetisdesignedtospreaditself toothersystemsonthesamenetworkbyusingavarietyof techniques such as brute-forcing passwords, exploiting vulnerabilities, and using stolen credentials. This allows Emotet to quickly infect multiple systems within an organization,makingitmoredifficulttocontain.
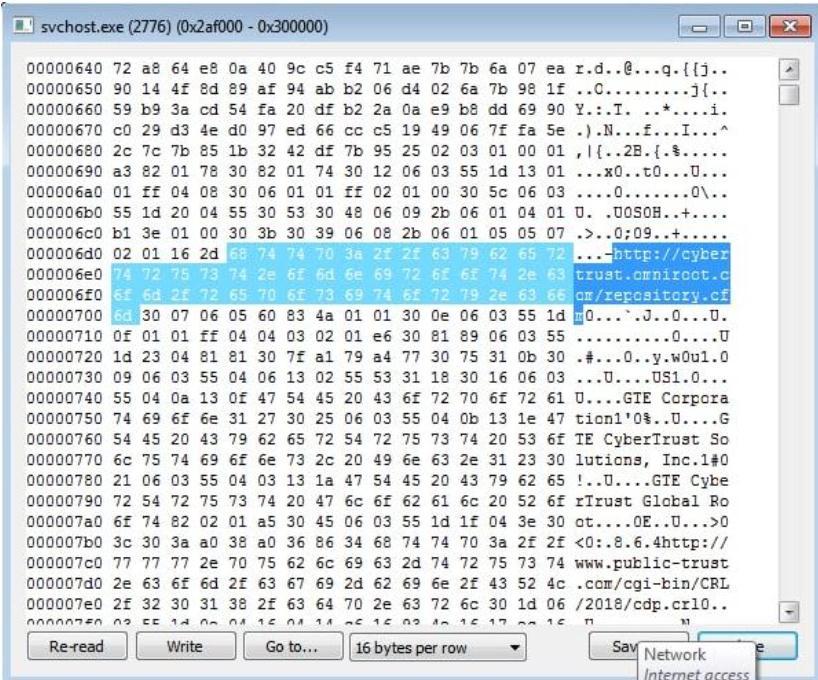
Information stealing: Emotetisprimarilydesignedtosteal sensitive information from infected systems. It uses keylogging and web injection techniques to capture and exfiltrate data such as email credentials, banking information, and other personal information. Emotet can also steal information by intercepting network traffic and searchingforsensitivedata.
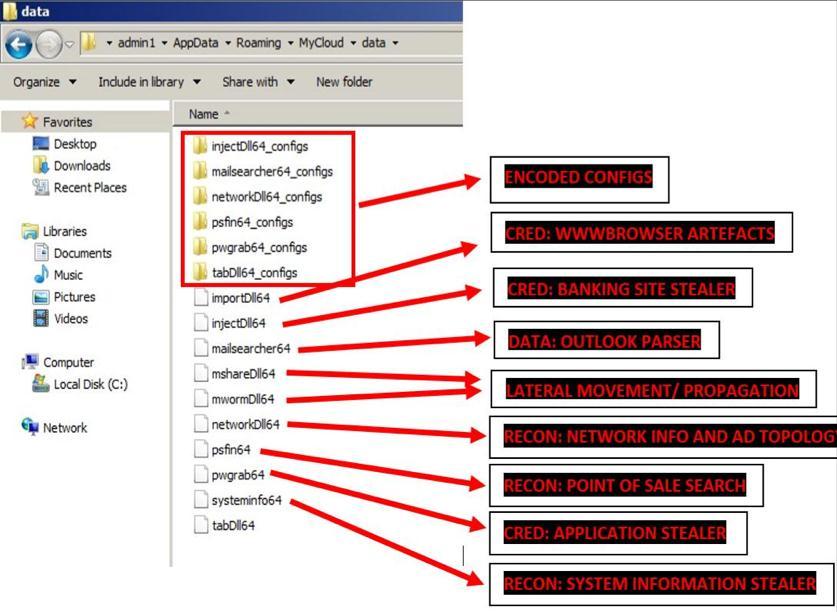
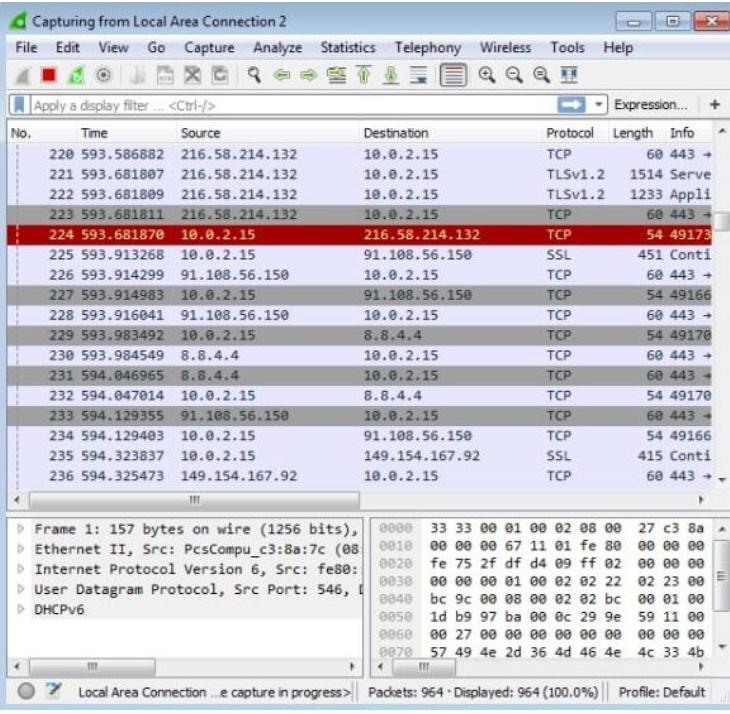

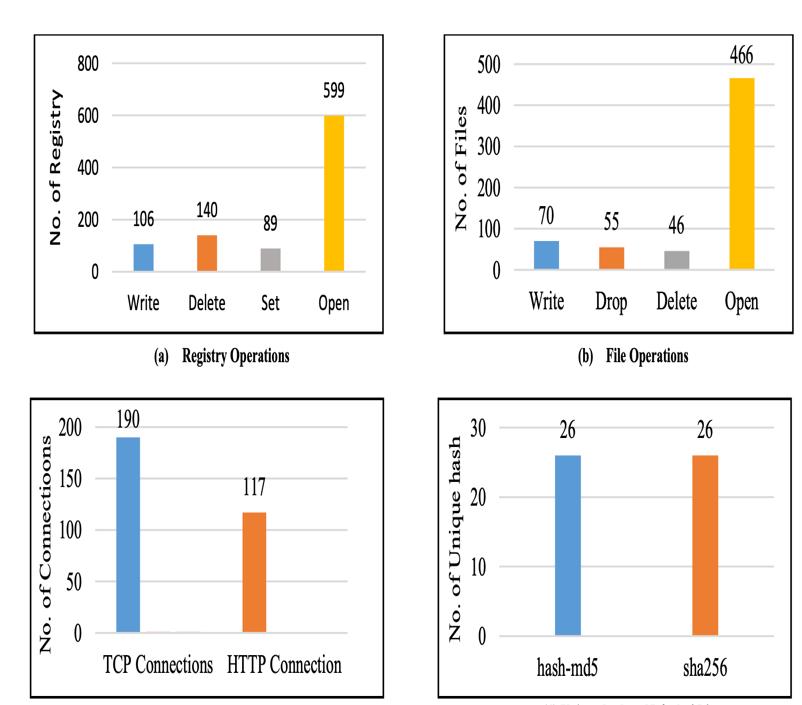
Fig-7:FilescreatedandmultipliedbyEmotet.
Command and control communication: Emotet communicateswithremotecommand-and-controlserversto receivecommandsandupdateitselfwithnewcapabilities. Thisallowsattackerstocontrolthemalwareandcarryout furtherattacksasneeded.
Delivery of other malware: OnceEmotethasestablisheda footholdonasystem,itcanbeusedtodeliverothertypesof malwaresuchasransomware or bankingTrojans.Emotet can also be used to distribute spam emails and phishing attacks,allowingattackerstospreadtheirreachandtarget morevictims.
Evasion techniques: Emotetisdesignedtoevadedetection andavoidremovalbyusingavarietyoftechniquessuchas obfuscation,anti-analysistechniques,andcodeinjection.
In conclusion, Emotet is a highly advanced and persistent piece of malware that employs a variety of techniques to infiltrate computer systems, steal information, and propagate to other devices. It poses a serious danger to computer systems and networks due to its capacity for continuousevolutionandcollaborationwithothermalware.
3.2. Prevention Strategies
ThemalwareknownasEmotetisverycunningandchanges allthetimetoattempttoevadethemeasurestakentostop it. As a result, there isn't a single method to stop it from contaminatingyourcomputeroryourcompany.Instead,you needtoattempttostopitinavarietyofways.
For instance, you can instruct users on how to spot suspicious emails,usevirus-checkingsoftware,frequently updatecomputerprograms,usefilterstoblockspamemails, restrict what users can do on their computers, regularly makebackupcopiesofcrucialfiles,andrequireuserstolog in with two different methods. All of these measures can lessenthelikelihoodthatEmotetwillinfectyourcompany, butsinceEmotetisconstantlyevolving,youmustcontinue toupdateandreviewthem.
ReframeitandresetLocalanddomaincredentials, changepasswordsforapps,andreviewandremove EmotetPhishemailsfromtheMailinbox.
Implement and modify email filter and block policies, and stay away from using the Local AdministratorandDomainAdministratoraccounts toaccessthecompromisedsystem.
TransfertheinfectedsystemtoadifferentVLANto eliminateallartifactswhilerepairingthesystem.
Educate employees on SSAs regarding Social EngineeringandPhishingattacks.
Warnstaffmembersnottofollowphishinglinksor open phishing attachments and not to share personalinformation,passwords,andusernames.
UseGPOsetuponWindowsfirewallrulestoprevent client systems from sending inbound SMB communications.
Implement a firewall and email policies to block, detect, and prevent malicious IP addresses and suspiciousemails.
Implement a least privilege policy that limits the amountofaccessthatemployeesneedtocompletea particulartask.
UseDMARCtoimprovevalidationandlessenspam emails.
Usedesignatedadministratorstorestricttheno.of employeeswhohaveaccesstoadmindetails.
Establish two-factor authentication (2FA) for systemsandappstopreventunauthorizedaccess.
Fig-9:Emotetdetectionflow
TostopthespreadofEmotetinfection:
Identify the infected system using Indicators of Compromise(IOCs)andisolateit.
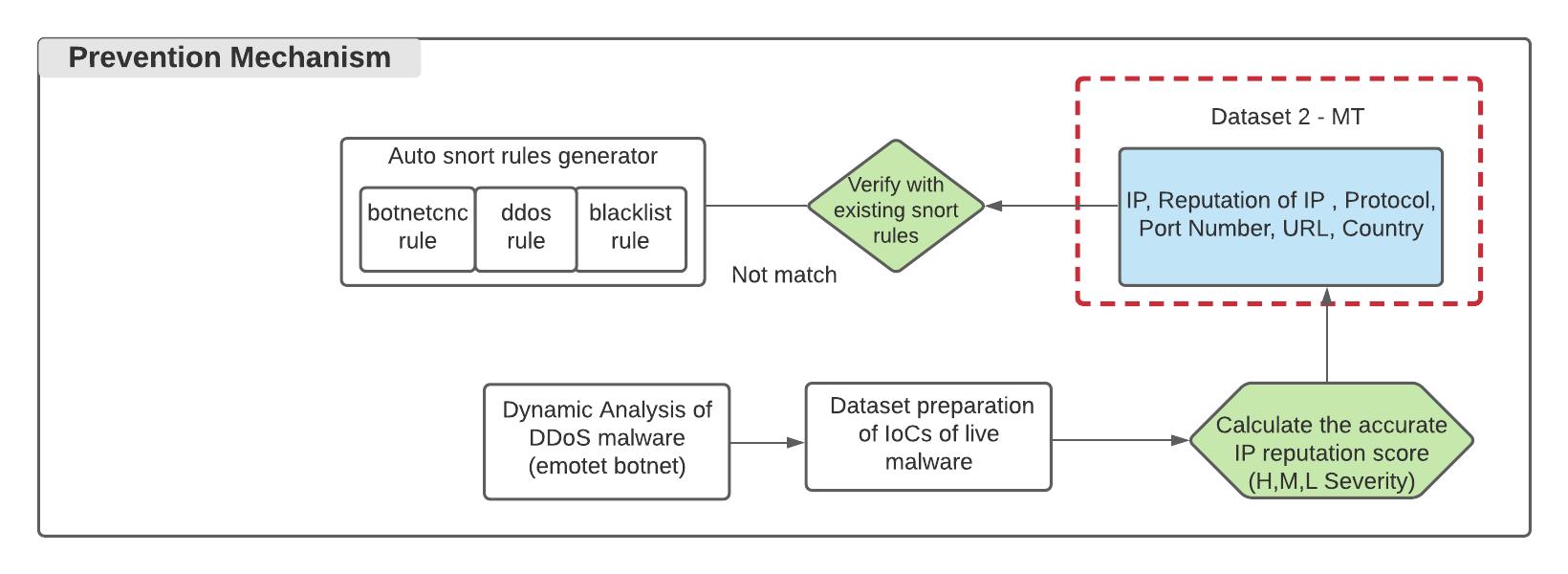

Identify the persistence of Emotet in Services, ScheduledTasks,andRegistryentries.
Block Server Message Block communications between infected and other computers in the network.
4. RESULTS
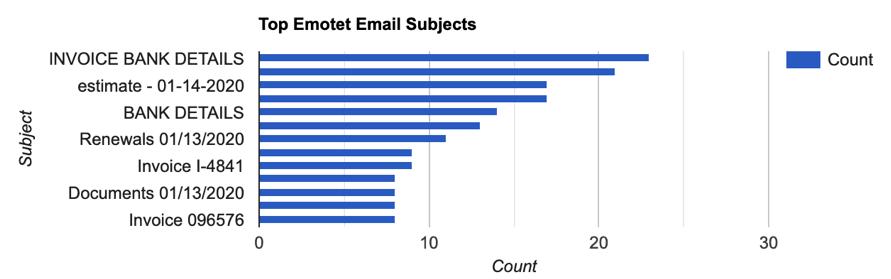
In order to penetrate computer systems, the Emotet malware uses social engineering strategies like spear phishing links and attachments. A phishing email that appears to be from a reliable source but may have been compromisediswhatbeginstheinfectionprocess.Emotet dropperisunknowinglydownloadedoncetherecipienttaps onthemaliciouslinkoropenstheattachment.TheEmotet executable is launched by the dropper's malicious macro, enablingittocreateaC2Clinkandextractdata.Usingthis method, spam emails can be sent from compromised accountsanddistantemailserviceproviders.
Implementinghost-basedintrusionprotectionsystemsand group policy settings that limit server message protocol (SMB) communications in a network are crucial for thwartingEmotetmalware.SMBisaprotocolthatfacilitates contact between devices and networks, but if Emotet is successfulinbreachingtheSMB,ithastheabilitytoinfect entiredomains,includingclientsandservers.
Accordingtodataresearch,Emotetmalwareisunfamiliarto most consumers. The job of identifying and preventing Emotetmalwareinfectionsfallstoorganizations,butdueto themalware'snumerousvariants,thiscanbedifficult.Itcan bechallengingtostopusersfromclickingonphishinglinks andfilesevenwithcybersecuritytraining.
To sum up, more study is required to create practical strategies for lowering the risk posed by Emotet malware andprotectingdevicesfromit.

5. CONCLUSIONS
Dueto its numerous variationsand difficultyindetection, the Emotet virus is posing issues for numerous users and businesses.Itbecomesmoredifficultforpeopletogetclear of it with each new version. The malware distributes to a person'sdevicesthemomenttheyclickonalinkoropenan attachment. People, organisations should avoid opening suspiciousemails,andstaffmembersshouldbeinstructed nottorelyonphishinglinksordocumentsinordertostop Emotetfrominfectingdevices.Inadditiontooutliningthe valueofSecuritySituationalAwareness(SSA),thedocument provides tips on preventing Emotet infections. One importantpieceofadviceistokeepaneyeoutforEmotet infections during SMB communications between client systemsandtolimitthesecommunicationsbyconfiguring Host-IPSorusinggrouppolicy.Thisdocumentoffersadvice on how to protect yourself from the Emotet malware in general.
REFERENCES
[1].Niu,W.,Li,T.,Zhang,X.,Hu,T.,Jiang,T.,&Wu,H.(2019). Using XGBoost to Discover Infected Hosts Based on HTTP Traffic. Security and Communication Networks, 2019
[2]. Ceschin, F., Botacin, M., Gomes, H. M., Oliveira . S. regio A. ovem er . Shallow security: n the
creationofadversarialvariantstoevademachinelearningbased malware detectors. In Proceedings of the 3rd ReversingandOffensive-orientedTrendsSymposium(pp.19).
[3]. Bhardwaj, A., & Goundar, S. (2019). A framework for effectivethreathunting.NetworkSecurity,2019(6),15-19. doi:10.1016/s13534858(19)30074-1.
[4]. Azab, A., Layton, R., Alazab, M., & Oliver, J. (2014). Miningmalwaretodetectvariants.2014FifthCybercrime and Trustworthy Computing Conference. doi:10.1109/ctc.2014.11.
[5]. ThreatAdvisory.(2019).TheevolutionofEmotet:From banking Trojan to threat distributor. https://www.symantec.com/blogs/threatintelligence/evolution-emotet-trojan-distributor.
[6]. ekta A.,&Acarman,T.(2018).Malwareclassification based on API calls and behavior analysis. IET Information Security,12(2),107-117.doi:10.1049/iet-ifs.2017.0430.

[7].Soomro,T.R.,&Hussain,M.(2019).SocialMedia-Related CybercrimesandTechniquesforTheirPrevention.Applied Computer Systems, 24(1), 9-17. [8]. Alert (TA18-201A) Emotet Malware. (July 20, 2018). Retrieved from https://www.us-cert.gov/ncas/alerts/TA18-201A
[9]. Emotet: Nastier Than WannaCry and Harder to Stop. (Feb 2010). A Sophos Whitepaper Retrieved from https://i.crn.com/sites/default/files/ckfinderimages/userfil es/images/crn/custom/2019/Sophos_LC_Q219_emotetnastier-than-wannacry-wp.PDF.
[10]. ittlefield May 3 . Three’s a crowd: ew Trickbot, Emotet & Ryuk Ransomware. Mediumhttps://littlefield.co/threes-a-crowd-new-trickbotemotet-ryuk-ransomware-16d1e25f72f4.
[11]. Alexey Shulmin (Apr 9, 2015). The Banking Trojan Emotet: Detailed Analysis. Secure list. https://securelist.com/the-banking-trojan-Emotet-detailedanalysis/69560.
[12]. Cybereason Nocturnus (Apr 2, 2019). Triple Threat: Emotet Deploys Trickbot to Steal Data & Spread RYUK. Cybereason. https://www.cybereason.com/blog/triplethreat-emotet-deploys-trickbot-to-steal-data-spread-ryukransomware.
[13]. ESETResearch(Nov9,2018).EmotetLaunchesMajor new Spam Campaign. Welivesecurity. https://www.welivesecurity.com/2018/11/09/emotetlaunches-major-new-spam-campaign/
[14]. ASEC Report. Emotet Returns to Prey on Banking Information(2017).
