A SECURED AUDITING PROTOCOL FOR TRANSFERRING DATA AND PROTECTED DISTRIBUTED STORAGE WITH SOCIAL MEDIA
, S. Aswath Naraayanan43&4 UG Scholar, Department of Computer Science and Engineering
1&2 Assistant Professor, Department of Computer Science and Engineering

1234 Prince Dr. K. Vasudevan College of Engineering and Technology, Chennai, TamilNadu, India
***
Abstract – There are numerous ways to handle a company'sdata.Everythingofthecompany'sdata,including itstransactions,history,andauditingprocedures,mustbe handled correctly. To manage these things effectively, a differentdatabaseneedstobebuilt.Toaccessthedatabase information for that database, we require distinct connectivityandaccessibilitytools.Also,thedatabaseneeds tokeepeachperson'sdataseparately.
Key Words: Cloud, Database, Data, Big data, Transactions, Managing and Auditingdata, Social Media
1.INTRODUCTION
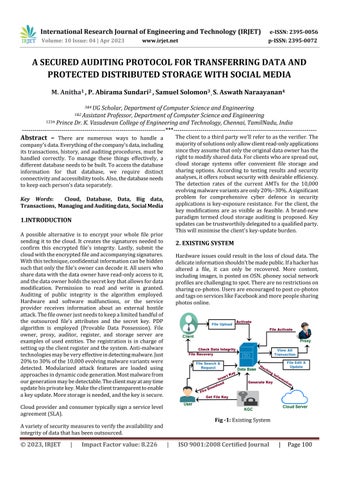
A possible alternative is to encrypt your whole file prior sendingittothecloud.Itcreatesthesignaturesneededto confirm this encrypted file's integrity. Lastly, submit the cloudwiththeencryptedfileandaccompanyingsignatures. Withthistechnique,confidentialinformationcanbehidden suchthatonlythefile'sownercandecodeit.Alluserswho sharedatawiththedataownerhaveread-onlyaccesstoit, andthedataownerholdsthesecretkeythatallowsfordata modification. Permission to read and write is granted. Auditing of public integrity is the algorithm employed. Hardware and software malfunctions, or the service provider receives information about an external hostile attack.Thefileownerjustneedstokeepalimitedhandfulof the outsourced file's attributes and the secret key. PDP algorithm is employed (Provable Data Possession). File owner, proxy, auditor, register, and storage server are examples of used entities. The registration is in charge of settinguptheclientregisterandthesystem.Anti-malware technologiesmaybeveryeffectiveindetectingmalware.Just 20%to30%ofthe10,000evolvingmalwarevariantswere detected. Modularized attack features are loaded using approachesindynamiccodegeneration.Mostmalwarefrom ourgenerationmaybedetectable.Theclientmayatanytime updatehisprivatekey.Maketheclienttransparenttoenable akeyupdate.Morestorageisneeded,andthekeyissecure.
Cloudproviderandconsumertypicallysignaservicelevel agreement(SLA).
Avarietyofsecuritymeasurestoverifytheavailabilityand integrityofdatathathasbeenoutsourced.
Theclienttoathirdpartywe'llrefertoastheverifier.The majorityofsolutionsonlyallowclientread-onlyapplications sincetheyassumethatonlytheoriginaldataownerhasthe righttomodifyshareddata.Forclientswhoarespreadout, cloud storage systems offer convenient file storage and sharing options. According to testing results and security analyses,itoffersrobustsecuritywithdesirableefficiency. The detection rates of the current AMTs for the 10,000 evolvingmalwarevariantsareonly20%–30%.Asignificant problem for comprehensive cyber defence in security applicationsiskey-exposureresistance.Fortheclient,the key modifications are as visible as feasible. A brand-new paradigm termed cloud storage auditing is proposed. Key updatescanbetrustworthilydelegatedtoaqualifiedparty. Thiswillminimisetheclient'skey-updateburden.
2. EXISTING SYSTEM
Hardwareissuescouldresultinthelossofclouddata.The delicateinformationshouldn'tbemadepublic.Ifahackerhas altered a file, it can only be recovered. More content, includingimages,ispostedonOSN.phoneysocialnetwork profilesarechallengingtospot.Therearenorestrictionson sharingco-photos.Usersareencouragedtopostco-photos andtagsonserviceslikeFacebookandmorepeoplesharing photosonline.
3. DISADVANTAGES OF EXISTING SYSTEM
Posting a coworker's photo without consent is a privacy infringement.Co-ownersneedsomedegreeofcontrolover shared photos. Both the shared users and the cloud are unreliable.Usersmustshoulderasignificantburdentokeep thedatalocallyduetothedata'srapidincrease.Thesharing of data cannot be supported by remote data integrity auditing techniques. It is incompatible with multi-user modification.Processcanonlybereadbyusers.Itwasstill able to upload the corrupted file. Access is simple for hackers.Whensignalsarehacked,theusercannotreceive them. Because there is no security, a hacker can quickly access the data. It cannot be kept in the file and shared anonymously. It offers high computational expense. Using malwaresamplesfromtheGENOMEcollectionofAndroid malware, a malware meta-model for modularizing typical attack activities in brief strategies for evasion in reusable features. Minimal time complexity, stateless verification, unrestricted query use, and data retrievability are some further drawbacks. entrusted data to store financial informationandstoragespaceforbackupprocedures.
4. PROPOSED SYSTEM
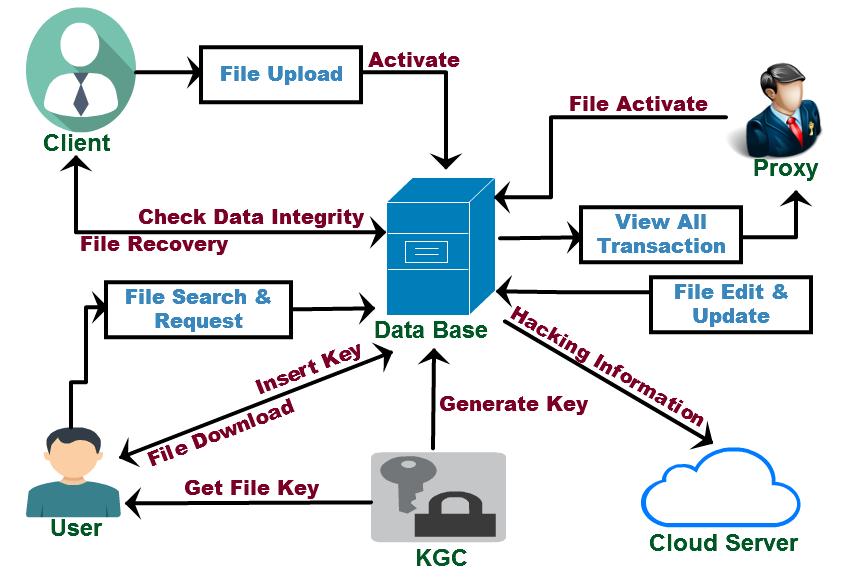
Inthefuture,remotedataintegrityauditingwillbeused to ensure data integrity. Some popular cloud storage solutionshavecloudfileswithsensitivedatainthem.Find outhowtosharedatawhilemaskingsensitiveinformation. Every user record kept in the database is verified by the administrator.Userscanmatchtheirprofilesandlearnabout theirmatches'likesanddislikesbeforesubmittingrequests. Beforejoining,usershavetheoptiontoacceptorrejectthe groupbeforeitisformed.Detectsafalseprofilebylookingat theactivityofthepostings.Beforepostinganypictures,get theuser'sapproval.Ourplanenablessharinganduseofthe cloud-based file as a result. It is necessary to use the commercialpubliccloudasareliablebackenddatacenterin ordertomanagetheexponentialgrowthofimagesinvolved insocialdiscovery.
We provide a safe and effective indexing structure to facilitatequickandscalablesimilaritysearchoverhundreds ofthousandsofencryptedphotos.
ConSecIdx–containssecretkeyandimageprofilesetto securetheprofile.
PrimaryInsert-contains profile identifier and user metadata.
RandomProbe-contains profile identifier,user metadata andrandomproberange.
The suggested model can correctly predict more than 80% of friends under the strongest social tie strength, accordingtotheresults.
The proposed approach is effective in terms of privacy preservation,communicationcost,flexibility,andscalability, according to performance analysis and evaluation. This algorithmcanmoreaccuratelyidentifyinfluentialusers.
ENROLLMENT
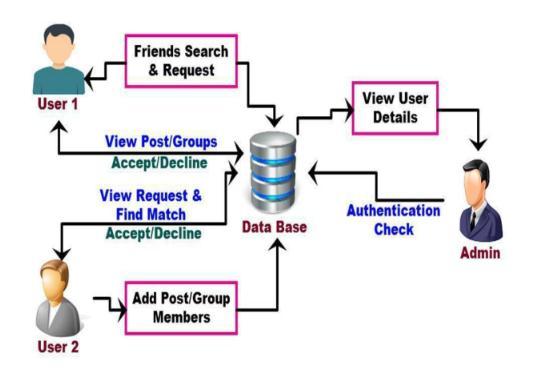
After enrolling,theuserhas toentera validusername, email address, and password in order to access their account.
Ifcredentialsarevalid,thesystemwillallowaccesstothe websites; otherwise, it will generate a user name or user accountalert.

REFORM THE ACCOUNT
The user's profile must be updated after logging in becauseitservesasthefoundationforallsubsequentsystem functions.
Userscanaddmoreinformationthroughouttheupdating process,includingtheirinterests,educationalbackground, thenameoftheircollege,andsoforth.
When you select your profile picture and then click Update,theserverwillbeupdated.
ITINEARY ADD
Peoplepublishcontenttoexpresstheiremotionstoothers (i.e.,shareamongfriends).
You will be notified of any posts that contain your own profile'staggingifthishappens.
Beforetheuseracceptsorrejectsthepost,noonewillsee it.
COMPANION APPEAL
Theusertypescertainstringsintothesearchbarandthen requeststheserverusingthosestrings.
When a user submits this kind of a request, the server automaticallyexaminesthelikelihoodofaresponsebefore respondingtotheuser.
Responsesonlygivethenamesoftheindividualsandno furtherdetails.
Theusercansubmitafriendrequesttoanyindividualon thelistiftheydesiretobefriends.
CONTOUR PAIRED
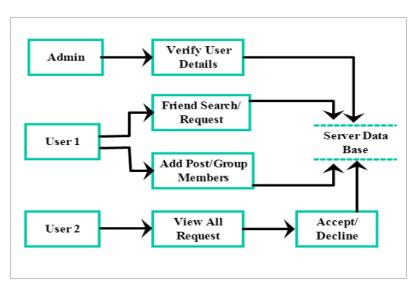
When a user submits a request, the server runs this module.
The server first retrieves the other user's name and profileinformationfromthedatabasebeforecollectingthe requesteduser'sprofileinformation.
Serverusesa profile matchingalgorithm tomatch both profilesusingthefiveparametersthataregiven.
Usersthatreceiverequestsviewtherequestinformation usingasinglevaluegeneratedbasedonthematchingoffive parameters,andtheymaythenchoosewhethertoacceptor rejecttherequest.
PROTECTED CONTOUR
Users have the option of uploading images to serve as their profile pictures, which are visible to the public and allowforfriend-to-friendcommunication.
When a profile image is updated by another user, the originaluserisnotified.
Images can only be viewed with the user's consent; otherwise,theadministratormaybantheuser.
ASSOCIATION OPERATIONS
Users have the option of creating groups to share informationwithcertainusers.
Youwereaddedbythegroupadministratorwiththeconsent ofeachperson.
Each person will receive informed of that group's participation.
Iftheuseragreestotherequest,theycanjointhatgroup.
6. RESULTS AND DISCUSSIONS
7. CONCLUSIONS
The
to
conduct the distant information honestyexaminationisstillpresent.
Theproposedplot'ssecurityevidenceshowsthatsecurity andproductivityareachieved.Theproposedsystemreduced thecomplicationsofimplementingtheolderdatabasedesign toaccessthedata.Thus,thenewerdesignprovidesflexibility ofaccessingsocialmediainaneffectivemanner.
8. FUTURE ENHANCEMENT
Byaddingaproxycomponenttoverifyforintegrity,thiscan beaccomplished.
The fact that the data owner does not need to remain for integrityverificationisanextrabenefit.

Facedetectionisbasedonthetrainingofaclassifierutilising alargenumberofnegativephotosthatindicatefeaturesor itemsthatshouldnotbedetectedaswellasabignumberof positiveimagesthatrepresenttheobjecttoberecognised.
Toassessthefacefeature,theregionoftheimagewiththe highestlikelihoodofthefeatureisregionalized.
Asiteliminatesfalsepositives,whichdecreasestheareathat needstobechecked,thespeedofdetectionisboosted.
REFERENCES
[1] I. Altman. Privacy regulation: Culturally universal or culturally Specific Journal of Social Issues, 33(3):66–84, 1977.
[2] A. Besmer and H. Richter Lipford. Moving beyond untagging:photoprivacyinataggedworld.InProceedings oftheSIGCHIConferenceonHumanFactorsin Computing Systems, CHI ’10, pages 1563–1572, New York, NY, USA, 2010.ACM.
[3] S. Boyd, N. Parikh, E. Chu, B. Peleato, and J. Eckstein. Distributed optimization and statistical learning via the alternatingdirectionmethodofmultipliers.Found.Trends Mach.Learn.,3(1):1–122,Jan.2011.
[4]B.Carminati,E.Ferrari,andA.Perego.Rule-basedaccess controlforsocialnetworks.InR.Meersman,Z.Tari,andP. Herrero, editors, On the Move to Meaningful Internet Systems 2006: OTM 2006 Workshops, volume 4278 of Lecture Notes in Computer Science, pages 1734–1744. SpringerBerlinHeidelberg,2006.
[5] J. Y. Choi, W. De Neve, K. Plataniotis, and Y.-M. Ro. Collaborativefacerecognitionforimprovedfaceannotation in personal photo collections shared on online social networks.Multimedia,IEEETransactionson,13(1):14–28, 2011.
[6] K. Choi, H. Byun, and K.-A. Toh. A collaborative face recognition framework on a social network platform. In AutomaticFaceGestureRecognition,2008.FG’08.8thIEEE InternationalConferenceon,pages1–6,2008.
[7]Z.Stone,T.Zickler,andT.Darrell.Towardlarge-scaleface recognitionusingsocialnetworkcontext.Proceedingsofthe IEEE,98(8):1408–1415.
[8]Z.Stone,T.Zickler,andT.Darrell.Autotaggingfacebook: Social network context improves photo annotation. In ComputerVisionandPatternRecognitionWorkshops,2008. CVPRW’08.IEEEComputerSocietyConferenceon,pages1–8.IEEE,2008
[9]K.Ren,C.Wang,andQ.Wang,“Securitychallengesforthe publiccloud,”IEEEInternetComputing,vol.16,no.1,pp.69–73,Jan2012.
[10]G.Ateniese,R.Burns,R.Curtmola,J.Herring,L.Kissner, Z. Peterson, and D. Song, “Provable data possession at untrusted stores,” in Proceedings of the 14th ACM ConferenceonComputerandCommunicationsSecurity,ser. CCS’07,2007,pp.598–609.
[11]A.JuelsandB.S.Kaliski,“Pors:Proofsofretrievability forlargefiles,”inProceedingsofthe14thACMConference on Computer and Communications Security, ser. CCS ’07, 2007,pp.584–597.
[12] H. Shacham and B. Waters, “Compact proofs of retrievability,”J.Cryptology,vol.26,no.3,pp.442–483,Jul. 2013.
[13] C. Wang, S. S. M. Chow, Q. Wang, K. Ren, and W. Lou, “Privacy-preserving public auditing for secure cloud storage,”IEEETransactionsonComputers,vol.62,no.2,pp. 362–375,2013.
[14]S.G.Worku,C.Xu,J.Zhao,andX.He,“Secureandefficient privacy-preserving public auditing scheme for cloud storage,”Comput.Electr.Eng.,vol.40,no.5,pp.1703–1713, Jul.2014.
[15] C. Guan, K. Ren, F. Zhang, F. Kerschbaum, and J. Yu, “Symmetric-key based proofs of retrievability supporting publicverification,”inComputerSecurity–ESORICS2015. Cham:SpringerInternationalPublishing,2015,pp.203–223.
[16]W.Shen,J.Yu,H.Xia,H.Zhang,X.Lu,andR.Hao,“Lightweight and privacy- preserving secure cloud auditing schemeforgroupusersviathethirdpartymedium,”Journal ofNetworkandComputerApplications,vol.82,pp.56–64, 2017.
[17] J. Sun and Y. Fang, “Cross-domain data sharing in distributed electronic health record systems,” IEEE TransactionsonParallelandDistributedSystems,vol.21,no. 6,pp.754–764,June2010.
[18] G. Ateniese, R. D. Pietro, L. V. Mancini, and G. Tsudik, “Scalable and efficient provable data possession,” in Proceedingsofthe4thinternationalconferenceonSecurity andprivacyincommunicationnetowrks,2008,pp.1–10.