VOICE BASED EMAIL SYSTEM
Nivila A1 , Parameswari S2,Pavya R3, Gnanaparakash V41Student, Information Technology, Bannari amman institute of technology, Tamilnadu, India

2Student, Information Technology, Bannari amman institute of technology, Tamilnadu, India
3Student, Information Technology, Bannari amman institute of technology, Tamilnadu, India
4Professor, Electronics and communication engineering, Bannari amman institute of technology, Tamilnadu, India ***
Abstract - Today, a significant portion of people depend on freely accessible email or messages sent by strangers. Because anyone can send an email or leave a message, spammers have a golden chance to write messages about our various interests. Numerous absurd emails from spam clutter up mailboxes. Degrade. Today, having access to the internet is a necessity for daily life. Internet access is extensively used by all people to access knowledge and information. However, blind people have trouble accessing these text resources and using any online tool. The development of computer-based accessible tools has greatly expanded the opportunities available to the blind and visually impairedworldwide. The screenreaders and other audio feedback-basedvirtual environments have greatly aided blind people in using internet apps. We outline the voicemail system architecture that a blind individual can use to quickly and easily access emails. Additionally, locating these spammers and the spam content can be difficult and a hot research subject. Spam email is the practice of sending numerous communications via postal mail. Spam is essentially postage due advertising because the recipient bears the majority of the cost. Because email can be a very cost-effective medium for senders, spam email is a type of commercial advertising that is commercially feasible. Using the Bayes theorem, the Naive Bayes Classifier, and the IP address of the sender, the proposed model can determine whether a given communication is spam or not.
Key Words: RF, NB, DT, KNN algorithms
1. INTRODUCTION
As we have seen, the advent of the Internet has transformedmanyindustries.Today'spopulationhaseasy accesstoanyknowledgetheydesirethankstotheinternet. One of the major areas that the Internet has significantly changediscommunication.Forsendingandreceivingsome crucial information over the Internet, emails are the most dependablemethodofcommunication.However,thereisa requirementthatyoubeabletoseeinorderforhumansto reach the Internet. However, there are also people with variousabilitiesinoursocietywholackyourtalents.Some blind or visually impaired individuals are unable to see anything, including the computer screen and keyboard. There are more than 240 million visually impaired individuals in the world, according to a survey. In other words,about240millionindividualsdon'tknowhowtouse
theInternetoremail.Thissystemseekstocreateanemail system that will enable even someone who is blind to communicateusingtheserviceswithoutpriortraining.
The system is entirely based on interactive voice reaction,makingitsimpletouseandeffective.Theprojectas awholeisbuiltonvoiceinteraction,orspeechsynthesisand recognition. Nowadays, technology is an essential componentofdailyliving.Theuseoftheinternetisgrowing rapidly,andalongwithit,theuseofemailtocommunicate and exchange information has grown as well; for the majority of people, it is now second nature. Even though everyone needs emails, they also contain unwanted, pointless mass mails known as spam mails. Spam is accessibletoanyonewithanonlineconnectionandadevice. Most spam emails aim to draw recipients' attention away from legitimate and essential emails and toward negative circumstances.Spamemailshavetheabilitytosignificantly slowdowninternetperformancebycloggingupinboxesand storagespace.Theseemailshavethepowertotakevaluable informationandconinindividuals,ortheycancorruptone's system by introducing viruses into it. The process of identifying spam emails can be very time-consuming and irritating at times. Although spam detection can be done directly,itcanbetime-consumingandinefficienttofilterout alotofspamemails.Asaresult,spammonitoringsoftwareis nowabsolutelynecessary.Differentspamdetectionmethods are now used to address this issue. The use of the Naive Bayesian approach and feature sets that determine the presenceofspamkeywordsisthemostwidelyusedmethod forspamdetection.
Problem Definition
Thefactthatusingthemneedsvisualperceptionmakes using this technology very challenging for those who are visuallyimpaired.However,noteveryonehasaccesstothe internet.Thisisbecauseyouwouldneedtounderstandwhat wasdisplayedonthescreeninordertoaccesstheinternet.It servesnopurposeifthatisnotapparent.Becauseofthis,the internetisanentirelyuselesstoolforthosewhoareblindor illiterate.
Existing Algorithm
Upuntil2014,4.1billionemailaccountswereestablished in total. By the end of 2018, it is predicted that 5.2 billion
accounts will have been created. Emails are therefore the most common method of communication. People who are visuallyimpairedcannotusethemostcommonmailsystems thatweuse on a dailybasis. Thisisduetothelack ofany facilitiesthatwouldallowtheindividualinfronttohearthe content of the screen. They are unable to perform the necessary actions because they are unable to see what is alreadyonthescreenorwheretoselect.Althoughitisuserfriendly,usingacomputerforthefirsttimeisnotaseasyfor someonewhoisblindasitisforanormaluser.
Disadvantage of Existing Algorithm
Becausetheyareinwrittenformatorcontainany typeofattachedinformationandthereisnoread-outchoice tohearthemailthatisdeliveredtotheirmailaddresses,the current mail services do not offer simple access to the visuallyimpaired.Anapplicationthatcouldassisttheuser sendandreceiveemailsinEnglishwasdevelopedasaresult of one of the studies. At the time of this study, it was discoveredthattheproposedarchitectureperformedbetter than the existing architecture. Techniques for converting speechtotextandtexttospeechwereusedinthatprojectto giveblindpersonssimpleaccess.
Proposed System
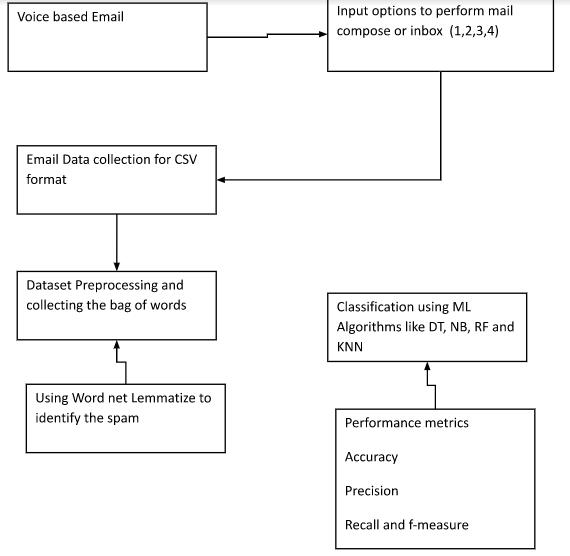
Thevoice-basedapplicationcreatedforthevoicebased email system initiative makes it simple for blind people to use email. The suggested system focuses on offeringthefundamentalcapabilities,includingvoice-based interaction and the ability to compose, read, send, and receive emails. This makes it easier to use all of the aforementioned features and the option to submit emails usingbothvoiceandtext.Thesuggestedmethodmakesit simpleforblindpeopletouseemail.
Users can simply provide input by speaking the messagebecausethesystemdoesnotrequireakeyboardor mouse. As a result, the structure we are creating is completelydifferentfromthosealreadyinplace.Oursystem also focuses on individuals who are visually challenged, unlike other systems that only target a specific group of people.Thesystemwillbeabletoreceiveinstructionsfrom the user, which it will then carry out. Additionally, the systemwillprompttheusertotakeparticularstepsinorder tousetheappropriateservices.
Advantages Over Existing System
Welcometousers(asBlindpeoplecaneasilyusevoice basedapplications).
Data storage is simple, it is more effective, and it takeslesstimeandeffort.
Thesystem wearecreating iscompletelydistinct fromtheonesthatarealreadyinplace.Oursystem also focuses on individuals who are visually challenged,unlikeothersystemsthatonlytargeta specificgroupofpeople.
Italsobenefitsthedisabledandtheilliterate.
Literature survey
1. A. Dixit and A. Agarwal [1] The author used group learning rather than focusing on one method. The averageaccuracyscorefoundwas85%,whichis15% moreaccuratethantheaccuracyoftheKNNmodelwith the worst performance. Even with the dataset and valuesprovided,thewritersonlyusedasmallportionof the data. The remaining information was insufficient anddidnotprovideanyadditionalmarkersthatcould be used to differentiate between false and real news.
2. Abdullah,N.A.,andAhmed,A.A.[2]Phishingwebsites canbedistinguishedfromlegitimatewebsitesbytheir URLs.Thesuggestedtechniquemightbeabletoidentify authenticandfakewebsitesbyexaminingtheUniform ResourceLocators(URLs)ofsuspectwebpages.(URLs). To recognize phishing sites, a number of traits are

lookedforinURLs.Tostopsuchincidents,theidentified attacksaresubmittedtotherelevantauthorities.
3. S.S.Birunda,R.K.Devi,andothers[3]Forthepurpose offindingFNfromvarioussources,anovelscore-based structurehas been created. The most prominent false and actual characteristics were extracted from news stories using the TF-IDF method. Using the site url attributesthatthesourcegave,thesources'Credibility Scores were calculated. The retrieved text-based characteristics and the multi-source Credibility Score weremergedtodeterminehowreliablethenewswas. The effectiveness and applicability of the proposed framework are evaluated and contrasted with other classifiers.
4. W. Cheng and others, [5] In order to weight MSSE (Minimum Sum of Squared Errors) models for integrated forecasting, this paper combines ARIMA (AutoregressiveIntegratedMovingAverage)time-series modelswithBP(BackPropagation)neuralnetworks.
Objectives
The study's goal is to develop a voice-based messaging program for visually impaired people. The program allows Gmail login, inbox reading, and email composition.Thereisnolimittohowmanypeoplecanuse thisprogram.Thereisnoneedtouseacomputerbecause theentiresystemwilloperateviamouse.Thismethodcanbe usedbyawiderangeofusersandwasdesignedwithpeople whoareblindinmind.
Methodology
This system places a greater emphasis on user friendliness for all kinds of people, including sighted and non-sightedpeople.Interactivevoiceresponse,orIVR,isthe foundationoftheentiresystem.Inthesuggestedsystem,the user is free to click anywhere on the screen; the IVR will specifywhichtypeofclickswillcarryoutwhichfunctions. WiththeIVRfeature,theycanfollowthepromptsgivenby thesystemandtaketheappropriateaction

Development
Top-down strategies place a strong emphasis on preparationandathoroughcomprehensionofthesystem.It isinherentthatnocodingcanstartbeforethedesignofat least a portion of the system has been developed to a sufficientdegreeofdetail.Becausewritingsoftwarecode,or programming,isonlyonecomponentoftheprocess,people prefer to be referred to as developers rather than just programmers.
The foundation of conventional procedural languages is top-down programming, which starts with defining complicated tasks and then breaking them down into individual modules. The software is written once the componentsaredetailedenoughtobecoded.Thewaterfall model is a sequential design process that's frequently appliedtosoftwaredevelopmentprocesses.Inthismethod, progress is viewed as steadily gushing downward (like a waterfall)throughthestagesofInitiation,Analysis,Design, Code, Testing, Production/Implementation, and Maintenance.
Advantages of waterfall model:
In terms of complexity and practicality, it is the simplestsoftwareprocessparadigm.
Thismodelisusedatdifferentprojectmanagement levelsbecauseitisverysimpletounderstand.
It uses a methodical approach to project creation anddelivery.Therefore,theWaterfallparadigmis usedtocreatethissystem.
Code Design:
The architecture of the code should allow us to accomplish more goals with less coding. If there is less writing, the system will operate more quickly. The coding determines whether the data in the system is useful and readablebythesystem.Theproject'scodingisdoneinaway that ensures the correct entry validations are carried out. Errorentriesarenotpermitted.Additionally,careistakento ensurethatthedatabase'sreferentialanddatasecurityare notcompromised.Additionally,codingiscreatedina way thatmakesperfectuseofrestricteduseraccesstothetable andconcurrencyavoidancewhenaccessingthedatabase.
Statements and Current Flow
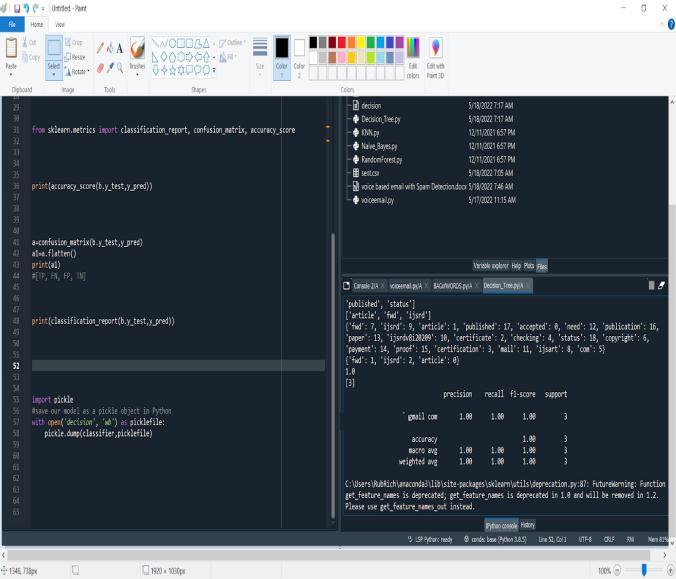
The assignment statement (the equals symbol, or token "="). This works differently from how conventional imperativeprogramminglanguageswork,anditshedslight on many other aspects of the language, including the way variables work in Python. When written in C, assignment readsas"typedvariablenamexreceivesacopyofnumeric value2,"forexample,x=2.The(left-hand)variablename serves as the symbolic address for the allocated storage placewherethe(right-hand)valueiscopied.Thevariable has been allotted memory that is sufficient for the stated type and may even be quite large. x = 2 means "(generic) name x receives a reference to a separate, dynamically allocated object of numeric (int) type of value 2" in the simplestcaseofaPythonassignment.
Bindingthenametotheitemiswhatthisisknownas.Itis incorrecttorefertothename'sstoragelocationasavariable because it lacks the specified value. Names may later be rebound to objects of incredibly diverse types, such as strings, procedures, sophisticated objects with data and methods,etc.,atanymoment.Whenacommonnumberis successivelyassignedtomultiplenames,aswhenx=2,y=2, andz=2,storageisallocatedto(atmost)threenamesand onenumericalobject,towhichallthreenamesarebound.It is inappropriate to link a fixed data type with a name because it serves as a general reference point. Dynamic typing,ontheotherhand,referstothebindingofnamesto specificobjectsthathavetypesatspecifictimes.
Alongwithelseandelif,theifstatementrunsablock ofcodeonlyifcertainconditionsaremet.(acontractionof else-if). The attached block can use the for statement to iterateoveraniterableobjectandstoreeachpieceinalocal variable. While a condition is true, a block of code is executed by the while expression. The try statement guaranteesthatcleanupcodeinafinallyblockwillalwaysbe executed regardless of how the block exits by allowing exceptionsraisedinitsattachedcodeblocktobecaughtand handledbyexceptclauses.Inobject-orientedprogramming, theclassstatementisusedtorunablockofcodeandattach its local namespace to a class. A function or procedure is definedbythedefstatement.
TheResourceAcquisitionIsInitialization(RAII)-like behaviorismadepossiblebythewithstatement(introduced inPython2.5),whichenclosesacodeblockwithinacontext manager(forinstance,acquiringalockbeforetheblockof codeisexecutedandreleasingthelockafterwardoropening afileandthenclosingit).Thepassdeclaration,whichactsas aNOP.Anemptycodesectionmustbecreatedforsyntactic reasons.Duringdebugging,theassertstatementisusedto lookforcircumstancesthatshouldexist.theyieldstatement, whichcausesageneratorfunctiontodeliveravalue.Since Python2.5,yieldhasbeena separatefunction.Coroutines areimplementedusingthisstructure.
Using the import statement, modules whose functionsorvariablescanbeusedbythepresentprogram are imported. Import can be done in four different ways: importmodulename>,import*frommodulename>,import numpyasnp,andimportnumpyimportpiasPie.Python3 replacedtheprintlinewiththeprint()function.
According to Guido van Rossum, Python does not currently allow tail call optimization or first-class continuations. But Python 2.5 offers greater support for coroutine-like functionality by extending its generators. Before version 2.5, generators were slack iterators that passedinformationoutinasingleway.Informationcanbe passedbackintoageneratorfunctionstartingwithPython 2.5,andstartingwithPython3.3,itcanbepassedthrough numerousstacklevels.
Feasibility study
Thisstageinvolvesanalyzingtheproject'sviability andpresentingabusinesspropositionthatincludesavery basicprojectplanandsomecostprojections.Theviability studyforthesuggestedsystemmustbecompletedduring systemanalysis.Thisisdonetomakesurethesystemisn'ta financial strain for the business. Understanding the main criteriaforthesystemiscrucialforfeasibilityanalysis.
The problem and the stakeholders' information requirementsareexaminedinthefeasibilitystudy.Itaimsto ascertaintheresourcesnecessarytoprovideaninformation systems solution, the price and advantages of such a solution,aswellastheviabilityofsuchasolution.Themost common techniques used by the analyst performing the studytogatherinformationare:
Conducting user, employee, manager, and client interviews.
Creating and distributing surveys to interested parties, such as prospective information system users.
Observingortrackingusersofthepresentsystemto learn about their requirements and gauge their satisfactionordissatisfactionwithit.

Gathering, looking over, and analyzing all paperwork related to the present system's operations,includingreports,layouts,instructions, andmanuals.
The purpose of the feasibilitystudyis to examine different information system solutions, determine how feasibletheyare,andthenrecommendthesolutionthatis best for the company. A suggested solution's viability is assessedintermsofitsconstituentparts.
Implementation activities

Usethesingle-entry,single-exitmethod
Standardbuildindentationshouldbeused.
Useastraightforwardcodingapproach.
To parameterize procedures, use symbolic variables.
providefinancialmargins
Offerstandardizedpaperwork
Observetheconventionsforprivatecommenting
Yousaid:4
Importantmailsselected
Chooseandspeak out the option number forthe task you want to perform. Say 1 to send a mail. Say 2 to get your mailboxstatus.Say3tosearchamail.Say4togetthelast3 mails.
Yousaid:1
MentionthegmailIDofthepersonstowhomyouwantto sendamail.EmailIDsshouldbeseparatedwiththe word, AND.
Yousaid:Shivaattherategmail.com
The mail will be send to Shiva@gmail.com. Confirm by sayingYESorNO.
Yousaid:yes
Sayyourmessage
Yousaid:hiwelcomehowareyoutoday
Yousaid hiwelcomehowareyoutoday.Confirmbysaying YESorNO.
Yousaid:yes
Messagesent
CONCLUSION
Chooseandspeak out the option number forthe task you want to perform. Say 1 to send a mail. Say 2 to get your mailboxstatus.Say3tosearchamail.Say4togetthelast3 mails.
Yousaid:4
Choose the folder name to get the latest mails. Say 1 for Inbox. Say 2 for Sent Mailbox. Say 3 for Drafts. Say 4 for importantmails.Say5forSpam.Say6forStarredMails.Say 7forBin.
Itisdeterminedthatthesystemwillfunctionwellandthus satisfytheneedsoftheendusers.Errorsarepreciselyfixed after the system has been tested. This program will be accessed from one or more systems, so it is tested with multipleloginattempts.Itentailscreatingandimplementing a real-time email engagement system for people who are blind.Weintendtocreateasystemthatwillmakeiteasier for people with vision impairments to use email services effectively. Our software can assist in solving some of the shortcomingsofthecurrentemailinfrastructure.Theuseof a keyboard has been entirely eliminated in this system, which lessens the cognitive burden associated with memorizingkeyboardshortcutsandthelocationsofthekeys onakeyboard.Toconductthedesiredactions,theuseronly needs to respond appropriately to the voice commands issuedbythesystem.Inorderforthesystemtoconductthe necessaryoperations,theusermustspeaktheoperationin theemailapplication.Whennecessary,thesystemwillask theusertoenterinformationusingvoicecommands,andthe user'sdetailswillbeauthenticated.Additionally,itbenefits thedisabledandilliterate.
REFERNCES
[1]Agarwal,A.,&Dixit,A.(2020).FakeNewsDetection:An Ensemble Learning Approach. 2020 4th International ConferenceonIntelligentComputingand Control Systems (ICICCS).doi:10.1109/iciccs48265.2020.9121

[2] Ahmed, A. A., & Abdullah, N. A. (2016).Real-time detection of phishing websites. 2016 IEEE 7th Annual Information Technology, Electronics and Mobile CommunicationConference (IEMCON).doi:10.1109/iemcon.2016.7746247
[3]Birunda,S.S.,&Devi,R.K.(2021).ANovelScore-Based Multi-SourceFakeNewsDetectionusingGradientBoosting Algorithm. 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS).doi:10.1109/icais50930.2021.93958
[4] Bhutani, B., Rastogi, N., Sehgal, P., & Purwar, A. (2019).FakeNewsDetectionUsingSentimentAnalysis.2019 Twelfth International Conference on Contemporary Computing(IC3).doi:10.1109/ic3.2019.8844880
