Cyber Attacks and Crimes in Cyber Security: A Comparative Analysis
Priti P. Tijare1, Monika S. Shirbhate2, Rupali Thakare3 1,2,3Assistant Professor, CSE Dept, Dr. Rajendra Gode Institute of Technology & Research, Amravati, Maharashtra, India
Abstract -In the cutting edge world that is run through of utilizing technological knowledge and network connections, it is fundamental to know what cyber security is and to be prepared to effectively utilize it. Frameworks, significant documents, information, and other significant virtual things are in risk assuming that there is no security to watch it. Security is most secure method of assurance from various sorts of dangers and most organizations participate in the difficulties of safety particularly digital assaults. The attacks are expanding day by day, the examination study imply that likenesses and dissimilarities in the perceived digital protection regardless of whether it is an IT firm. Attackers improved hacking procedures and go for the weak point in the organizations out there. This paper center around the basic comparative analysis on cyber security, crimes, attacks and awareness & non awareness about cyber security among people in various organizations. It also discusses about safety of private computing against cyber crime and analyze about problems of cyber crimes which is faced by the people. Digital protection is critical on the grounds that military, government, monetary, clinical and organization associations and different gadgets. A crucial quota of the data can be sensitive information, whether that is financial data, property, personal information, or other various sorts of data for which illegal access or could ensure negative concerns.
Key Words- Cyber Attack, Cyber Crime, Cyber Security, malwareawareness,protection
I. INTRODUCTION
The beyond couple of many years internet played significant role in worldwide communication and today it has almost about 3 billion users of internet, thus the internet has generated wide global network. We can't envision the existence without information technology exceeding half of the world population almost 58.8% used internet till 2019. Ratel Serbia reported 99.2% of people usescomputerwhichisagedbetween16and24yearsand 98.2 % people uses internet every day [6]. At present government, non-government organization is going through cyber space and most essential information carry to this space and consequently it may lead to the cyber threats, cyber-attacks and cyber-crimes. The cyber posed thesecuritytothegovernment,wecallitcybersecurity[9].
The cyber security originated in 1987. Cyber security is all aboutsecurityprotectionthroughwhichwecanprotectthe environment of user network, software application & also defendingthecomputernetworksystemwhichisconnected totheinternetandprovidingtheprotectiontosystemfrom unnecessary attack [11]. Cyber-attacks includes trojan horse, spyware, sniffer, denial of services, virus, cream which is shown in figure 1. The cyber threats aims to gain illegal access damage data over the computer network like malware. Malware is malicious software huge amount of viruses and malware spreading all over a global like the internet worms, email viruses and keystroke, we can enlarge our computer performance by detaching the spyware [8]. Ransomware software encodes our computer data and request to payment to decode for reinstate files, 80%ofourcomputersareinfectedbysuchkindofspyware [1]. Analyzing the need of security for the software application because there are threats in cyber- attacks they putshighriskinsoftwareforlossesthedataorinformation soitcanbedifficulttorecoverthedataorinformation[7].
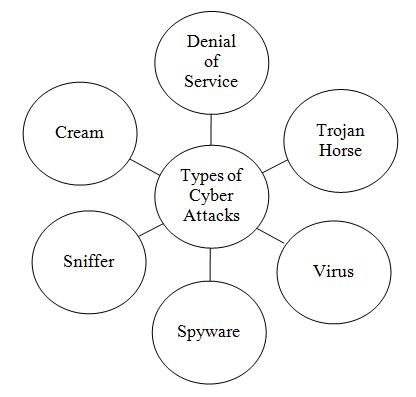
Fig 1:Typesofattacks
Although some user does not aware about the security risk they don't have any idea how to accomplish the cyber security even if they are aware about phishing attack, malware attack [6]. Cyber security is shared authority
internet and also everyone who make use of internet for any other reason which is private or the personal reason and the Internet corporation can also a make a contribute by using protection of their community and payment processes. The government should be aware and also instructtoenforceanticrimelaw[8].
II. LITERATURE REVIEW

Therehavebeenseveral papers which arehighlighting the useofcybersecurity, the attributes ofthreatsandalso the vulnerability in cyber safety are exceptional from information security. All safety is worried with variety of threatsfor resources[2].Theauthor [6]hassuggestedthe data which is having some quite proper facts about the cyberprotection,whicheverparticipanthasnolongertobe confident about cyber safety in the various institution and awareness and non awareness about protection of their non-publicdatafromunauthorized users
securitydepartment.
RTF files [Rich Text Format] is about secure structure to keep away from virus because the doc file can be hackedbyeasilywithoutanyproblembymicroviruses [1].
According to the researcher, from 2018 to 2021 cybercrime has expanded on the global degree the researcher haspointoutaverageofcyber-crimecasesintheworld.
The below figure 3 shows that cyber-crime is not only a national but international fact. The reliable growth has aims to multi responsible society along with the cyber safety infrastructure [5]. According to the author [10] therearethreemostimportantfeatureofcybersecurity.
For safety, the private computing can be carried out followinganticyber-crimepolicies.
Scan the executable archive downloaded at once as fromthenetbeforeusingit.

Document and spreadsheet can also include the spywaresoavoidit.
Virus also scan the electronic mails as well as attachmentsearlierthanopeningit.
Even if your personal computer is attacked by using any virus, malware, disconnect your pc immediately fromnetworkanddoawaywithitwiththehelpofIT
People: Every worker should aware about their role to preventcyberthreat.
Technology: From access manipulate to installing the antivirus,technologyutilizetodecreasecyberrisk.
Process: Documented approaches need to be clearly determining role, responsibility and procedures. The relevant researcher discussed about their rules and precautions for internet banking because there are high risk of cyber-crime in online transaction. User must be changedtheirpasswordineverythreemonths.Usepublic gadgets for internet banking as incredibly irresponsible. Bank should be force to their customers for changing the password and verify that there is no repetition as a final two passwords [8]. According to author [2], the cybercrimes are classified into three types like emails that troublesomeoneandspywaresoftwaretocrackanybody’s computer unlawfully and unauthorized access gain the personaldataandalsotheplagiarizingexclusiverecords.
III. PROBLEM ANALYSIS
In today’s world the cyber security is widely used in the worldwide because of the cyber-attack and cyber- crime increases day by day. The average people of the information technology not always have a technically educated and most likely no longer to be studied cyber securityinhis/herpasteducation.Peoplechoosemuchless secure password because problematic password has too hardtoremember,thisshowsimportantrealityofmajority of users are not aware about how to choose accurate and uniquepasswordthatcannotbeeasilyhackedbysomeone. In today’s generation all people have smart phones but only few people install antivirus into their phone. Others are used public wi-fi that becomes more problematic. The attacker can attack easily. Following are the problems to achievecybersecurityasmentionedbelow.
Non updates of software application to secure the system.
Notinstallingtheantivirustopreventfrommalicious software.
Use of less secure and easy password that unknown personmaycrackpasswordeasily.
Useof publicwifiornetwork.
Around 12.2% people are using the public wifi for online purchaseand6.1%foronline bankingandthe60.5%used for sending mails so it can easily attack by hackers and people do not even know about this [6]. This all problems mayaffectthecybersecurity.Thisallproblemsneedstobe fixedanditisimportantforoursecuritypurposesowecan aware and secure from the cyber-attack as well as cybercrime so the unknown person cannot get unauthorized accessandcannothack ourlegal information, wemaysafe formalltheunknownattacks.
IV. COMPARATIVE ANALYSIS
In this section, we analyze different methods, challenges, strength and weakness that other authors used for achievingthecybersecurityasfollow.
I] Paper title /author: Cyber Security at Software Development Time / Mark Bradley, Ansgar Fehnker, Ralf Huuck[3].
Methods: Gonna static analysis tool, tree-based pattern matchingtomodelchecking.
Challenges:Realsecurityissuedetection.
Strength: Highlighted importance of secure source code for developing for thesecuresystem andimprovingcyber security.
Weakness: Only on focuses the implementation phaseof softwaredoesnotcreatethesimpletaskforSDLC.
II] Paper title/ author: Analyzing and Evaluating Critical Cyber Security Challenges Faced by Vendor Organizations in Software Development: SLR Based Approach / Abdul wahid khan, shah zaib, faheemkhan, ilhan, tarimer jung taek seo, and jiho shin [2]. Method: Cyber-security challenge model (CSCM), Snow bowling technique,andthepattern-baseddetectionalgorithm.
Challenges: Critical cyber security challenge for companies.
Strength: Identification of security threats in the various organizationlikeasthePatternbaseddetectionalgorithm with assure continuous security observing. Weakness: Cost security issue that serious economicinvestment & financialissueinorganization.
III] Paper title/ author: Cyber Security: The State of the Practice in Public Sector Companies in India / T. R. Srinivas,G.Vivek[4].
Method:Byconductingthesurveythroughtheparticipant and did contribution to that work includingthe workshop inmay2014management.developmentprogram(MDP).
Challenges: Security issue, awareness about cyber security.
Strength: Motivated to the people improving the levelof cybersecuritythroughtheconductingsurvey.
Weakness: Does not conducting the training of the awareness of cyber risks and responding ratings of peopleswhodoesn’taware aboutfirewall protection 57% scanofmalware3.6%andthe10.7%isawarenessofcyber risk.
IV] Paper title/ author: A Bird's Eye View of Cyber Crimes and Free and Open Source Software’s to Detoxify Cyber Crime Attacks – an End User Perspective / M. K. JayanthiKannan[1].

Method: Providing the steps for the installation of spyware in system. Methods for deleting the spyware viruses&worms.Ex:softwareforantivirussecurity, email alertservicebox.
Challenges:Accessingthecybersecurity.
Strength: Protecting the personal laptop, desktop computer by installing antivirus security software will preventsfromspreadingofmalwarebyprovidingvarious steps.
Weakness:Thereisanomethodorstepsforupdatingthe antivirus or the software application. If the users already have a antivirus they does not aware about updating the antivirus.
V] Paper title/ author: Systematic Mapping Study on SecurityApproachesinSecureSoftwareEngineering
/ Rafiq Ahmad Khan, Siffat Ullah Khan, Habib UllahKhan, MuhammadIlyas[7].
Method: Stages-SMSprocess,SSEmethod.


Challenges: Systematicsoftwaresecurity.
Strength: Maintaining the security features like privacy, integrity, understanding secure software methods that can be leads with attacks, providing the concept about there are only 10.70% of peoples are aware about the cyber risk and 2% of training of awareness about cyber risk, 32.10% are responded that having appropriate softwaresecurity.
Weakness: It also needs to be combined with the powerfultoolsforimplementationplan.

According to the survey [4] anti-malware policy and practices. The following figure 4 and figure 5 shows the respondingratingsofawarenessofcyberriskandrelated training and responding ratings of malware protection and aware about scanning of malware. So the overall awareness levels and the necessary training are comparatively poor. In case of scanning for malware in network situation is pathetic as only 3.6% of the participants are aware. This is all about the comparative analyzeregardingthecybersecurity.
V. CONCLUSION
Everyone wants to be secure and safe while using internet buttimeshavecometomakethissureof cyber-attacksand cyber crimes. Based on this analysisof cyber security we identified thedifferent kind of cyber-attacks. We havegone through the comparative analysis on cyber security that includesthemethods,challenges,strength,weakness&also identify theresponding ratingsofawarenessofcyberrisk& malware protection. Day by day the cyber-crimes are increasingthatmayleadtothebiggestchallengeofsecuring theinformationfortheorganization.Thereforeanincreased awareness of cyber-attacks among individuals and organizationsisvitalsothatsolutionscanbefoundquickly. We also get surety about how many people are aware and non aware about the cyber security in various organizations. Future exploration focus needs to be on the development of a secure and secure internet terrain ofthe cominggeneration.
REFERENCES
[1]. M. K. Jayanthi Kannan, “A Bird's Eye View of Cyber Crimes and Free and Open Source Software’s to Detoxify Cyber Crime Attacks – an End User Perspective”, 2017 2nd International Conference on Anti Cyber Crimes (ICACC),©2017IEEE.
[2]. Khan, Abdul Wahid, Zaib, Shah, Khan, Faheem, Tarimer, Ilhan, Seo, Jung Taek, Shin, Jiho, “Analyzing and Evaluating Critical Cyber Security Challenges Faced by Vendor Organizations in Software Development: SLR BasedApproach”,IEEEAccess,vol.10,pp.65044-65054, 2022.
[3]. M. Bradley, A. Fehnker and R. Huuck, "Cyber security at software development time, Defence Science Research ConferenceandExpo(DSR),pp.1-4,September2011.
[4]. T. R. Srinivas and G. Vivek, "Cyber security: The state of the practice in public sector companies in India," International Conference on Computing and CommunicationTechnologies,2014,pp.1-5,March2015
[5]. Arti, Rani, Reena, “Cyber Security in Digital Society: Indian Perspective”, UGC CARE Group 1, ISSN: 22777067,vol.VII,Issue2(III),pp.44-48,2021-2022.
[6]. Kovacevic, Ana, Putnik, Nenad, Toskovic, Oliver, “FactorsRelatedtoCyberSecurityBehavior”,IEEEAccess, no.21693536,vol.8,pp.125140-125148,July8,2020.

[7]. Khan, Rafiq Ahmad, Khan, Siffat Ullah, Khan, Habib Ullah, Ilyas, Muhammad, “Systematic Mapping Study on Security Approaches in Secure Software Engineering”, IEEE Access, no. 21693536, vol. 9, pp. 19139- 19160, January18,2021.
[8]. Mallika, Vikas Deep, Purushottam Sharma, “Analysis and Impact of Cyber Security Threats in India using Mazarbot Case Study”, Proceedings of the International Conference on Computational Techniques, Electronics andMechanicalSystems(CTEMS-2018):21-23December 2018,Belagavi,India,pp.499-503,©2018IEEE.
[9]. Li, Yuchong, Liu, Qinghui, “A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments”, Energy Reports, no. 23524847,vol.7,pp.8176-8186,©2021.
[10]. Das, Ayan, Dawn Saju, Dr. Neha Gupta, “A Study of Cyber Security and Its Challenges”, International Journal of Engineering Applied Sciences and Technology, no. 2455-2143,vol.5,Issue1,pp.747-753,May2020.
[11].AdibaShaikh,ArshiyaA.Khan,SyedZebanaaz,Shazia Shaikh, Nazneen Akhter, “Exploring Recent Challenges In Cyber Security And Their Solutions”, International Journal of Creative Research Thoughts (IJCRT), ISSN: 2320- 2882, vol.9,no.12,pp.603-604, 2 December 2021.
