An in-depth review on Contactless Fingerprint Identification using Deep Learning
1B.Tech student, Computer Science, RMD Sinhgad School of Engineering, Pune, India.,

2 B.Tech student, Computer Science, RMD Sinhgad School of Engineering, Pune, India,
3 B.Tech student, Computer Science, RMD Sinhgad School ofEngineering ,Pune, India,
4 B.Tech student, Computer Science, RMD Sinhgad School of Engineering ,Pune, India.***
Abstract
Biometric authentication has been one of the leading techniquesfortheverificationofanindividual intherecent electronics paradigm. There have been increase in the numberofSmartphonesandotherelectronicgadgetssuchas laptopsthatcomeequippedwithafingerprintsensorforthe purpose of authentication of the rightful user. There has been increased instances of utilization of such biometric techniques as it is one of the most accurate and full proof solution for the purposeof authenticatingauser.Butinthe recentyearstherehasbeenincreasedskepticisminutilizing public biometric authentication scanner devices due to thosedevicesbeingcoveredindirtandorviruses.Therefore toimprovetheparadigmoffingerprintidentificationthereis the need for effective and useful contact-less fingerprint identification system. This re-search paper identifies the current techniques for contactlessfingerprint in which are used for an effective analysis or re- view that has been useful in developing are methodology forthis topic which willbeelaboratedinthefutureeditionsofthisarticle.
Key Words: Biometric Verification, Contactless Fingerprint identification, Image processing, Convolutional Neural Networks.
Introduction
In a contemporary world where innovation is emerging at a fast rate, safe verification and recognition of individualsis necessary. Although solutions such as Card information, OTP,andSecuritycodesavailable,typicallydoesn’tfulfill all compliancerequirementsandaresusceptibletoexploitation. Biometric verification is more resilient and provides more reliable verification and identification. In biometric verification, authorization is granted or the user is authenticatedbasedontheirphysicaltraits.
A person may be recognized by key structural and psychological characteristics, or by a mixture of these two types of characteristics. Individuality and identity are comprised of these behavioral characteristics, which encompass a per-son’s ideas, behaviors, speech, posture,
sentiments, etc. In contrast, individuals are conceived with physical characteristics such as handprint, DNA sequence, fingerprints, iris structure and coloration, appearance, etc. Biometric Validation refers to the classification of a person using the above- mentioned characteristics. Human physiological or morphological characteristics, which are unique to each individual,are most frequently utilized for authenticationandprivacyapplications.
Biometric solutions have the ability to address a wide variety of authentication needs for the computerized and rapididentificationofhumanbeings.Fromthemanybiometric in- formation used for e- governance, e-business, and a variety of law- enforcement operations, fingerprinting is perhaps the most commonly used. In addition to capillary arrangement, handprint, face, and iris, other biometric markers also including hand print, face, and retina have showntheirutilizationinavarietyofscenarios.Theselection ofbiometricfeaturesisdependentuponthecharacteristicsof the application requirements, comprising effectiveness, precision,andmostsignificantly,userfriendliness.
Numerousobstacleshavesurfacedwiththeintroductionof fingerprint biometric identification systems. It is wellestablished that fingerprint recognition performance degrades owing to recurrent scarring, dampness, residual debris,skindeflections, or perspiration,and that a considerableproportionofphysicalworkersandtheagingpopulation alsohavefingerprintsofinsufficientintegrityforrecognition. Different scholars and solution providers have developed a variety of consumer and law enforcement solutions employing proof of identity based on physiological properties of the individual anatomy. In the biometrics area, a number of biological and physiological characteristics have been evaluated for their usefulness in actual privacy and crime investigation. Notwithstanding expanding uses in analytics and enforcement agencies, the contactless fingerprintiscurrently one of the widely explored biometric traits, and new techniques are still being devised to fully exploititscapability.
Related Works
Cheng,KevinH.M.,[1]investigatestheconstructionofa 3D handknuckledetectionmethodandintroduces,forthequite firstinstanceinthepublishedliterature,a 3Dhand knuckle picture repository for future exploration. It can-not be anticipatedthatanypracticalimplementationofcur-rent3D features extracted, such as those created for 3D palm print as well as 3D fingerprint recognition, can retrieve the majority of appropriate feature using 3D finger knuckle designs.Inordertoreachthepeakperformanceof3Dfinger knuckle biometric authentication, it is necessary to construct individual feature characteristics. Another of the key concerns associated with each new biometric imaging modalitiespertainstoitsdistinctivenessoridentitythathas never previously been examined in the biometrics community. This work attempts to solve this issue by constructing an individualized concept for 3D finger knuckle patterning utilizingthemosteffectivefeatureidentifier.
Ramya T.N [2] offers a strong and reliable verification system with an exceptionally significant proportion of dynamical correctness. Using key set values, the approach gives distinct layouts based on the same personal data. The benefit of the suggested solution is that even though the blueprintishacked,nopersonaldataabouttheuser’sfingerprint is released. With the worldwide COVID epidemic, the touch - free 3D fingerprint could serve as a means to a safe and sanitary authentication method. In the coming years, 3D-to-2D projection will employ a non-parametric unraveling approach. Utilization of additional fingerprint factors, suchassweatpores,ridgestructure,etc.,forfingerprint-ing production. Integration of 3D fingerprint with additional modalities,suchasear,retina,andface.
HanzhuoTan[3]offersaquickandpreciserecurrentconvolutionalnetwork-basedarchitectureforenhancingthecooperation amongst contactless fingerprint scanner and traditional contact-based fingerprint scanner. The suggested granularityperceptionnetwork,togetherwiththeequivalent proximity loss, may handle picture creation discrepancies andprocurementabnormalitiesdirectly.Theempiricalfindings reported in the past segment on two accessible to the public collections demonstrate that the effectiveness of the priorapproachesandenterpriseapplicationsismuchworse. These encouraging findings greatly enhance the compatibility between contactless and contact- based fingerprints, whichmayassisttothe establishmentofcontactlessfingerprintsystems.
Ajay Kumar [4] created a novel method for contactless fingerprint granularity recognition with a deep neural networkwhichcontainsatrousspatialpyramidpooling.Therepeatable empirical findings provided in this research show thatthesuggesteddesignwillyieldinasubstantialincrease
in quality. This research also includes the cross-database contactless fingerprinting assessment system, which trains thenetworksthroughusingphotosgatheredthroughoutthis research and evaluates the network’s functionality by using two additional publicly available datasets even without finetuning. These cross-database appropriate performance findings given in this research also serve that will further evaluatetheframework’sefficacyandresilience.

Metodi P. Yankov [5] evaluates the fingerprint pictures’ similarity measurement and volatility. It was proved that texture-based neural network models provide calculation of entropy every pixel regardless of main sensor. Consequently, the entropy was proven to rely exclusively on the quantity of active region included in the biometric specimen. Consequently, the biometric effectiveness of complexityunrestricted fingerprint identification algorithms is simplya consequence of the region of intersection between boththe sensorandcomparisonspecimens.UsingtheMImatch-ing a probeandstandardfornumerouspublicdatasets,thefeasible biometric authentication technique efficiencies were then determined.
Methodology
Requirement Gathering and Analysis: In this stage, we determine the many needs for our project, such as software, hardware, databases, and interfaces. System Design: During thesystemdesignphase,wecreateasystemthatissimpleto understand for the end user, i.e., user-friendly. We cre- ate several UML diagrams and data flow diagrams to bet- ter understand the system low, system module, and execu- tion sequence.Implementation: During the implementationphase of our project, we implemented several modules that were necessary to effectively achieve the intended results at various module levels. The system is first built in tiny programs called modules, with input from system design,and thencombinedinthefollowingstepasmentionedinFig-ure 1. Testing: The various test cases are carried out to see whethertheprojectmoduleisproducingtherequiredresults within the time frame specified. After each unit has been tested,alloftheunits builtduringtheimplementationphase are merged into a system. Following integration, the complete system is tested for flaws and failures. Deployment of System: Following the completion of functional and nonfunctional testing, the product is deployedin the client environmentorlaunchedtothemarket.Maintenance:Therearea few difficulties that arise in the client environment. Patches have been provided to address these problems. In order to improve the product, newer versions are published. All of thesephasesareconnectedinsuchawaythatdevelopmentis perceived as owing progressively downhill like a water fall through thephases. Thenextphaseis initiatedonly oncethe previously defined set of goals for the previous phase have
been met and signed off on, hence the term ”Waterfall Model.”
The contactless fingerprint recognization system goes throughthefollowingprocedures:-

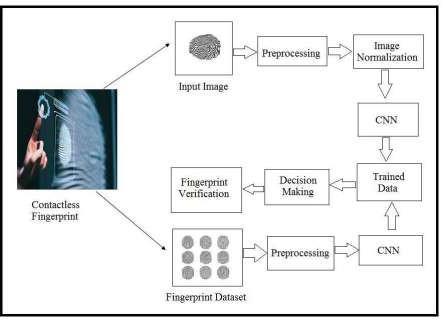
1. Preprocessing-Aftercertainimagesaretakenasinput it goes through preprocessing technique. The input images are cleaned by going through certain process like transforming, cleaning and integrating of data in order to make it ready for further process. It mainly focuses on improving the quality of the data and to make it more suitable for the specific data mining task. This step also involves techniques like combining data from multiple sources,suchasdatabases, spreadsheetsetc.Italsoinvolves stepssuchasconvertingthedata into a format that is more suitableforfurtherprocess. Itcanbenormalizingnumerical data, creating dummy variables, and encoding categorical data. The dataset may require to preprocess to ensure a suitableformatfortrainingCNN.
2. Image Normalization- Image normalization is a technique that changes the range of pixel intensity values ofa particular image.This datasetmayinclude photographs withpoorcontrast.Inthisstepwewillperformatechnique thatproducesanormalizationofaninputimagegrayscaleor RGB.
ofa particularsystem. Ithelpsingainingdetailedknowledge about overall system. It helps in defining and organizing functional requirements in a system. They helps in identifying actors along with their interactions with system. There are certain components used in building use case diagrams.Inthebelowprovidedusecasediagramthereisonly oneActor.
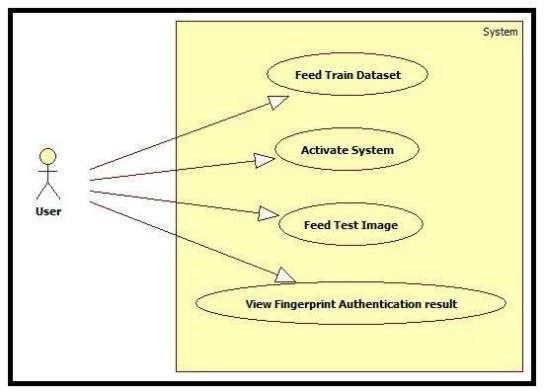
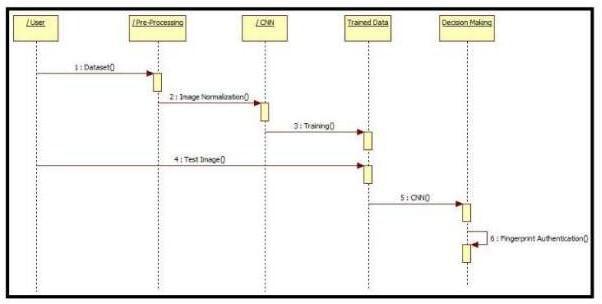
2. Sequence Diagram: Theusecasediagramofcontact-less fingerprint recognisation is given below Use case diagrams are useful to refresent the eternal functionality of a particular system. It helps in gaining detailed knowledge about overall system. It helps in defining and organizing functional requirements in a system. They helps in identifying actors along with their interactions with system. There are certain components used in building usecase diagrams.Inthebelowprovidedusecasediagramthereisonly oneActor.
Figure1:SystemDesign
3. CNN- is a important part for image processing. These algorithmsarecurrentlythe bestalgorithms wecanuse for for image processing Images mainly include data of RGB combination. The computer can’t see an image, all it can only consider is an array of numbers. Color images are mainlystoredin3-dimensionalarrays.
UML Diagrams
1. Use Case Diagram : The use case diagram of contactless fingerprint recognisation is given below Use case diagrams are useful to refresent the eternal functionality
3. State Transition Diagram : State-transition diagrams describethestatesthatanobjectmighthave,theeventsunderwhichobjectscanchangeitsstateortransitionandthe activitiesundertakenduringthewholelifecycleofanobject State-transitiondiagramsareveryusefulfordescribingthe behaviorofeachandeveryobjectspresentinthesystemThe mainfocusofstatetransitionsystemistovisualizethestate changesoreventsoccuringthroughouttheprocedure.
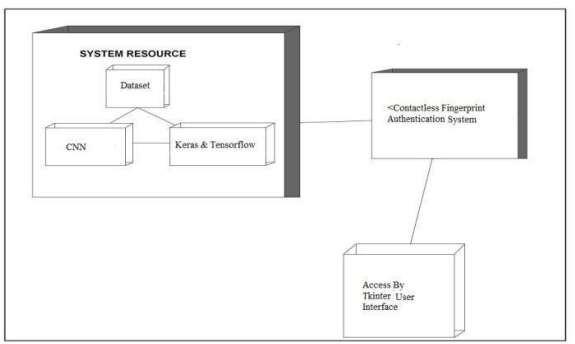
Deployment diagram : A deployment diagram is a UML diagram that represents the execution architecture of a particular system, which includes nodes such as hard- ware or software execution environments, and the middle- ware connecting them. These diagrams are mainly used to visualize the physical hardware and software of a system. It helps in understanding how the system will be physically deployed on the hardware environments. Deployment diagramdescribes the purpose of overall system. There are certain notations that are used to build deployment diagrams. A component diagram verifies that a system’s
required functionality is acceptable or not. These diagrams mainly helps in communication purpose between the developer and stake- holders of the system. Programmers and developers are the most benefited one’s from this diagram. They can use thesediagrams as a roadmap for the implementation,allowingforbetterdecision-makingpurpos. Component diagram focuses on physical aspects of object oriented classes. Component diagrams are normally class digramsthatfocusesoncomponentsofsystem.
pathogens. Consequently, a practical and usable con-tact list fingerprint identification system must be developed to advance the fingerprint identification methodology. This research study outlines the current approaches for contactless fingerprint examination or assessment that have been essential in the development of our technique for this issue, whichwillbedevelopedinfutureversionsofthispublication.
Acknowledgments
WewouldliketothankourPrincipalDr.V.V.Dixit,Headofthe Department, Prof.VinaM.Lomte,ourco-ordinatorAsst.Prof. Sonal S.FatangareandmyguideAsst.ProfNitha KPfortheir valuableadviceandtechnicalassistance.
Reference
[1] A. Kumar, ”Contactless Finger Knuckle Authentication under Severe Pose Deformations,” 2020 8th Inter-national WorkshoponBiometricsandForensics(IWBF), 2020, pp. 16,doi:10.1109/IWBF49977.2020.9107951.
[2]R. Kapoor, D. Kumar, Harshit, A. Garg and A. Sharma, ”Completely Contactless Finger-Knuckle Recognition us- ing Gabor Initialized Siamese Network,” 2020 Interna- tional Conference on Electronics and Sustainable Com-munication Systems (ICESC), 2020, pp. 867-872, doi: 10.1109/ICESC48915.2020.9155554
[3] K. H. M. Cheng and A. Kumar, ”Contactless Biometric IdentificationUs-ing 3D Finger Knuckle Patterns,” in IEEE Transactionson Pattern Analysis and Machine Intelligence, vol. 42, no. 8, pp. 1868-1883, 1 Aug. 2020, doi: 10.1109/TPAMI.2019.2904232.
[4]R. T. N and V. M B, ”AnalysisofPolynomialCo-Efficient Based Authentication for 3D Fingerprints,” 2020 IEEE International Conference for In- novation in Technology (INOCON), 2020, pp. 1-6, doi: 10.1109/INOCON50539.2020.9298341.

Conclusion
User authentication is one of the most crucial and highly essential aspects of providing security and privacy to the consumers.Withouttheauthenticationprinciplesincurrent placetherewouldbealotofleakageofdatainformationand thecollapseofprivacyofindividuals.Asitrepresentsoneof thebestcomprehensiveandfoolproofmethodsforverifying a user, the adoption of biometric techniques has expanded. In recent years, however, there has recently beenasurgein mistrust over the usage of public biometric identification scanners, since these devices are often coated in filth and/or
[5]H. Tan and A.Kumar, ”Minutiae Attention Network With Reciprocal Dis-tance Loss for Contactless to Contact-Based Fingerprint Identification,” in IEEE Transactions on InformationForen-sics and Security, vol. 16, pp. 3299-3311, 2021,doi:10.1109/TIFS.2021.3076307.
[6]H. Tan and A. Kumar, ”To- wards More Accurate Contactless Fingerprint Minutiae Ex- traction and PoseInvariant Matching,” in IEEE Transac- tions on Information Forensics and Security, vol. 15, pp. 3924-3937, 2020, doi:10.1109/TIFS.2020.3001732.
[7]M.P. Yankov, M. A. Olsen, M. B. Stegmann, S. S. Christensen and S. Forchhammer, ”Fingerprint Entropy and Identification Capacity Estimation Based on Pixel-Level Generative Modelling,” in IEEE Transactions on Information Forensics and Security, vol. 15, pp. 56-65, 2020, doi: 10.1109/TIFS.2019.2916406.
[8]A. Krishnan, G. R. Nayar, T. Thomas and N. A. Nystrom, ”FEBA - An Anatomy Based Finger Vein Classification,” 2020 IEEE Interna- tional Joint Conference on Biometrics (IJCB), 2020,pp.1-9,doi:10.1109/IJCB48548.2020.9304889.
[9]. Toygar, F.O. Babalola and Y. Bitirim, ”FYO: A Novel Multimodal Vein Database With Palmar, Dorsal and Wrist Biomet-rics,” in IEEE Access, vol. 8, pp. 82461-82470, 2020, doi:10.1109/ACCESS.2020.2991475.
[10]R.S.Kuzu,E.Pici-ucco,E.MaioranaandP.Campisi,”Onthe-Fly Finger- Vein-Based Biometric Recognition Using Deep Neural Networks,” in IEEE Transactions on InformationForen-sicsandSecurity,vol.15,pp.2641-2654, 2020,doi:10.1109/TIFS.2020.2971144.
[11]Harivanto, S. A. Sudiro, T. M. Kusuma, S. Madenda and L.M.R.Rere, ”Detec-tionofFingerprintAuthenticityBased on Deep Learning Using Image Pixel Value,” 2020 Fifth International Con- ference on Informatics and Computing (ICIC), 2020, pp. 1-6, doi: 10.1109/ICIC50835.2020.9288589.
[12]Y. Zhang,C.Gao,S.Pan, Z.Li,Y.XuandH.Qiu,”AScoreLevel Fusion of Fingerprint Matching With Fingerprint Liveness Detection,” in IEEE Access, vol. 8, pp. 183391183400,2020,doi:10.1109/ACCESS.2020.3027846.
[13]K. Han and X. Li, ”Application of Partial Differential Equation Methodin Fingerprint Image Enhancement,” 2021 IEEE/ACIS 19th International Conference on Software Engineering Research, Management and Applications (SERA), 2021, pp. 33-38, doi: 10.1109/SERA51205.2021.9509273.

[14]M.Yang, ”Fingerprint Recognition System based on Big Data and Multi-feature Fusion,” 2020 International ConferenceonCulture-orientedScienceTechnology(ICCST), 2020,pp.473-475,doi:10.1109/ICCST50977.2020.00097.
[15]P.Poonia, O. G. Deshmukh and P. K. Ajmera, ”Adaptive Quality Enhancement Fingerprint Analysis,” 20203rd International Conference on Emerging Technologies in ComputerEngineering:MachineLearning and In-ternetof Things (ICETCE), 2020, pp. 149-153, doi: 10.1109/ICETCE48199.2020.9091760.
