CREATING CCTV CAMERA SYSTEM USING ARTIFICIAL INTELLIGENCE, IMAGE PROCESSING, AND CYBERSECURITY TOOL
Md Arham Siddiqui1 , Kunal Agarwal21BTech student, Dept. of Computer Science and Engineering, Vellore Institute of Technology, Vellore, India

2BTech student, Dept. of Computer Science and Engineering, Vellore Institute of Technology, Vellore, India ***
ABSTRACT - The first CCTV camera was known to be installed in Germany in 1942. Since then, we have made a lot of progress, added a lot of features and now there are an estimated more than 750 million CCTV cameras installed all around the globe. But even with all the features already existing in current CCTV technologies, most CCTV cameras all around the world have too many loopholes, which makes them easy to exploit and ultimately leads hackers to attack andgain control of the cameras. In our project, we will be aiming to reduce these loopholes to a minimum by implementing various innovative and new features like specific human gestures detection such as the suspicious hand gestures that humans make while committing different crimes like holding a knife, hand movements while fighting with someone, etc. using deep learning including Artificial Intelligence. As there are a lot of thefts regarding vehicles like cars and bikes. So our next module will be focused on License Plate realization or recognition. Our module will be connected to the database which will be regularly updated with all the vehicles which are complained as missing or theft so that our camera can automatically detect using techniques like Image Processing and recognize the number plates for all the vehicles that pass from its vision. Our next module will be focused on Face mask detection using IP methods as per our government rules that a mask is mandatory for all the citizens due to the Covid-19 times. This will help reduce the load on all the officers working hard so the next variant after Omicron can’t spread like the previous Covid waves, as warned by scientists. Our final module will solely be focused on securing the CCTV using various cybersecurity methods which aren't supported and implemented in real- time. But even when a CCTV camera is equipped with all these features, its purpose will be defeated if even for once it's under attack by a hacker. So we'll be further implementing cybersecurity protection by preventing DDoS, SQL, and other attacks. Image Processing and Cyber Security that are available in our framework will be easier to use by the public and a worthy step forward in the security sector. Therefore, an assistive app can be used that allows the users to traverse freely without worrying about their surveillance security and it also becomes a crucial requirement in their daily life. Therefore, our all-in-one application is implemented to make the life of the local businesses, small scale and largescale businesses at check by proper surveillance of the same.
Key Words: Artificial Intelligence, Image Processing, Cybersecurity, Deep Learning, Security Sector.
1. INTRODUCTION
With the CCTV cameras numbers rapidly increasing, it’s predictedto cross the1 billion marks withinthe next few years.Withthebasicmindset,[7]themainbenefitsofthe usageofCCTVcamerasaresecurity,safety,surveillance,and preventionofcrime.Asourtechnologyisadvancingmany upgradesarebeingimplementedinCCTVcameras,suchas humandetectionusingAI,real-timesurveillanceusingIoT, theseincludedetectingthehumanpresenceinfrontofthe cameraoraparticularmarkedareathatthecameracovers initsviewandalertingthe[8]sametothelivemonitoring device,smartphoneintegration,usingvoicecontroltoturn onandmanagethecontrolsofcameras,usingsolar-powered cameraswithenergystoragesotheycanwork24×7inany environment,andfeatureslikenightvisionhavebeeninuse atpresent.
WeplantoputupwiththeefficiencyoftheCCTVsystem,to include new [6] features, like detecting criminals within vehicles, facemask, during violent activities, along with securingthethreatsthatmostoftheCCTVsystemspossess andpreventconfidentiality,integrityandavailabilityofthe datastoredwithinthesame[9]
Objectivesoftheproposedwork:Firstly,we’llbereducing loopholestoaminimumbyimplementingvariousinnovative andnewfeatureslikespecifichumangesturesdetectionsuch as the suspicious hand gestures that humans make while committing different crimes like holding a knife, hand movementswhile[5]fightingwithsomeone,etc.usingdeep learningincludingArtificialIntelligence.Astherearealotof thefts regarding vehicles like cars and bikes. So our next module will be focused on License Plate realization or recognition.Ourmodulewillbeconnectedtothedatabase whichwillberegularlyupdatedwithallthevehicleswhich arecomplainedasmissingortheftsothatourcameracan automaticallydetectusingImageProcessingandrecognize thenumberplatesforallthevehiclesthat[10]passfromits vision. Our next module will be focused on Face mask detection using image processing methods as per our government rules that a mask is mandatory for all the citizensduetotheCovid-19times.Thiswillhelpreducethe loadonalltheofficersworkinghardsothenextvariantafter Omicron can’t spread like the previous Covid waves, as warned by scientists. [11] Our final module will solely be focusedonsecuringtheCCTVusingvariouscybersecurity
methodswhicharen'tsupportedandimplementedinrealtime. But even when a CCTV camera is equipped with all thesefeatures,itspurposewillbedefeatedifevenforonce it's under attack by a hacker. So, we'll be further implementingcybersecurityprotectionbypreventingDDoS, SQL,andotherattacks.ImageProcessingandCyberSecurity thatareavailableinourframeworkwillbe[12]easiertouse by the public and a worthy step forward in the security sector.
2. LITERATURE SURVEY

Various models have been come across while we were conductingtheliteraturesurvey.
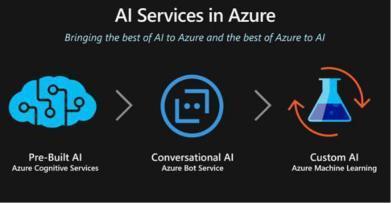
FirstpaperproposesaframeworkforCriminalDetection and Recognition of CCTV Data Using Cloud and Machine Learning.ItisfinishedinvolvingMicrosoftAzureCognitive ServicesandCloudframeworkwiththeendgoalofexecution oftheproposedframework.[13]Theframeworkcanlikewise beutilizedtofindmissingyoungstersandindividualsfrom theCCTVfilmthatisaccessiblefromthesite.Usingvarious methodologies,theauthorshavedescribedtheaccuracyand costing of each method along with the sensors used and ultimate result that can be obtained by using these technologieswithintegrationtotheCCTVsystem.
onarrangementsthatrelatetorelocatingAI-basedderivation towardstheedgeand[14]brilliantclientgadgets,aswellas differentstrategiesforDDoS(DistributedDenialofService) cannyidentification,whereDDoSassaultisperceivedasone of the essential worries in network safety, strategies to preventsuchattacksaredevelopedwithinthesame.
The next research article is regarding the newly considered evaluations on the crime prevention effects on CCTV.Itshowsthat,thatCCTVisassociatedwithasignificant decreaseincrime.Thelargestandthemostconsistenteffects of CCTV were observed in car parks. The results of this analysiscanalsodemonstrateevidenceofsignificantcrime reductionswithinothersettings,[15]particularlyresidential areas. CCTV schemes incorporating active monitoring that aregeneratedbylargereffectsizesthandidpassivesystems. Schemes deploying multiple interventions alongside CCTV generated larger effect sizes that did schemes deploying single or no other interventions besides CCTV. As CCTV surveillanceincreasesday-by-day,highendandhigh-quality evaluationsofoutcomesandimplementationsisofutmost importance,onlythenthecrimeratecanbekeptrelatively low.
Particularly, in the next paper authors have really emphasizedonhowthedetectionofcrimeinCCTVvideos canbedoneusingdeeplearning.Intheirproposedmodel, they represent what things are important for this whole methodology to work. Firstly, a crime dataset needs to be analyzed and studied, followed by the neural network training,whichfiltersseverallayerstofigureoutwhatexactly the activity is about. If the respective activity detected is matched with the [16] one in the dataset, then it needs to sendsomesortofalarmingsystemthatcanmaketheowner protecthisorherpropertyormaybecallforhelpandlocal police. With good amount of accuracy, the details of the technicalfindingscanbedistinguishedbyreadingthrough thepaper.
Theauthorstrytoefficientlymanagethetrafficaccidents andthedeathsthattakeplaceduetoitinthesecondpaper, considering lack of helmet usage being one of the biggest reasons for it. To perfectly manage the traffic, and its rule breakers,an intelligent [4]automatedsystem is proposed, whereinmaximumnumberoftwo-wheelerswillbedetected viathevideoandthosedisregardingthetraffic,theirnumber plate will be noted and corresponding fine or charges are imposedviatheelectronicfinemanagementsystem.
Inthethirdone,whichischapter,weobservedthatcyberattacks like the DDoS and other attacks which lowers the CCTV security are something that needs to be detected automatically rather than putting manual efforts into detection which can too much time consuming. Creators attempt to investigate the conceivable outcomes to give better security to video reconnaissance frameworks and correspondenceorganizations.Afterappropriatelychecking
Thereasoningofpapernumbersixportraysastudyusing aquasi-experimentaldesigntodeterminetheactualimpact ofanintegratedCCTVprogramonallofcrimeinDetroit,USA. Themethodologyusedbytheauthorswasalsounmatched, thedataonthefirst87businessesintheProjectnamedGreen LightDetroitwascollected,alongwithamatchedcomparison groupof201otherbusinesses.ABayesian[17] hierarchical lineargrowthcurvedmodelwasdeployedtodeterminethe overall effect of CCTV camera surveillance at Green Light businesses over the span of 2 years. On proper finding, it indicated that Green Light businesses experienced an immediate,buttransientincreaseinpropertycrimereports, as well as more consistent proactive police activity postintervene.Theoutcome,thatcanbeconcluded[18]through isthatintegratedCCTVprogramsmayincreasethereporting ofminorcrimeswhichmayhavenotbeenreportedbefore. However, these programs may not likely impact violent crimes.Inaddition,tyingalltheproactiveresponseandto
patrolthepatroltheparticipatingbusinessesplaceshigher manpowercostsondepartments.
TheauthorstakeupNameddatanetworking(NDN)asan essentialinformationtransmissionrecreationtechnique.It focusesonproficientsubstanceconveyanceanddiminishing theovertrepetitivenessofinformationtransmission.InNDN, oneofthesignificantissuesishowtousethemisgenerally reserveditemstodecreasetheclient'sreactiontodelayand work on the usage of the genuine [1] store assets. In this paper,acleversubstancedisclosureframeworkisutilizedto completely use the store assets, called DENA, is proposed, whichenvelopstheprofoundoutstandingreservedeclaration andreserveenergy-basedreservesubstitutioncalculations. DENAgivestheeasiestroutewaystointrigueparcelstogetto designated information bundles under directions of a declared table built by a shift accuracy-based reserved content declaration calculation with low correspondence upward.Meanwhile,astoresubstitutioncalculationtohelp thereservedeclarationislikewiseproposed.Thetechnique utilizes a [19] purported reserve energy list to teach the substitutionofstoredcontent.Therecreationresultsshow thattheframeworkworksontheusageofstoreassetsand the organization limit while keeping the organization's controltrafficatagenerallylowlevel.
Eighth paper again depicts the philosophy for weapon discoveryinobservationrecordingsutilizingprofoundbrain organizations. Creators attempt to work on the normal accuracyoffirearm[2]discoveryatvariousscales,lastly,they figure out how to increase to however much 18% more accuracythanthepastandexistingarmsrecognitiondraws near.
Likemostofthepaperswecameacross,authorsofthis paper too are talking about weapon detection and how to control and minimize crime rate in crowded as well as suspicious lonely areas. So, authors try to implement an automatic weapon detection, particularly guns, using CNN (Convolutional Neural Network) based SSD (single shot detection),alongwithfasterRCNN(regionCNN).Afterusing 2typesofdatasetspre-labelledimageandmanuallylabelled accuracyofapplicationistabulated.Further,SSDandFaster RCNN algorithms are simulated for pre labelled and selfcreatedimagedatasetforgundetection.Boththealgorithms are efficient and give good results, but their application progressivelydependsonthe[3]tradebetweenspeedand precision.Asfarasspeed,SSDcalculationgivesbetterspeed with0.736secondsperoutline.ThoughFasterRCNNgivesa speed of 1.606 seconds per outline, which is poorly contrasted with SSD. As for precision, Faster RCNN gives betterexactnessof84.6%.ThoughSSDgivesanexactnessof 73.8%, which is poorlycontrastedwithquicker RCNN.SSD gaveconstantlocationbecauseofquickerspeedyetFaster RCNNgaveunrivaledprecision.Intermsoffutureworks,the authors relate thathigh-endGPUs andDSPs(digital signal processors) large datasets can be used to train for more accuratealgorithm.
Inthetenthpaperauthorstrytoproveanddescribethe developmentandimplementationofanearlywarningsystem thatrecognizespeopleautomaticallyinasurveillancecamera environment and then use data from various sources to identifythesepeopleandbuildtheirprofileandnetworkthe authors extracted feature vectors of all face images from camerafeedandgalleryimages.WeutilizedOpenFacemodel and our prepared model to gather two separate element vectorsforeachpicturetolookatwhichhighlightextraction model worksbetterinanobservationclimate.Afterwhich theycomparedtheaccuracyofrecognitionintwodifferent settings, one with only one face of a person in the gallery (neutral face) compared to when having two faces in the gallery for every person (neutral and smiling face). After settingupthedatabasegallery,oneoftheauthorsrantests oneachportalandsequencewiththethreedifferentcameras availableandthenfinallyshowingaccuracyresultsofusing thedifferentrecognitionmodelstoclassifypeoplepassing, usingthreetables.Further,theyaimtoimproveaccuracyand reduceruntimebyexperimentingdifferenttechniquesother thanthosealreadyusedin.
Theworkthusthispaperiscenteredaroundgivingasafe spot involving a CCTV film as the principal source to distinguish hurtful weapons by applying open-source profoundlearningalgorithms.Theyhavecarriedoutpaired order expecting gun as the reference class and pertinent disarrayobjectsincorporationideaisacquaintedwithlessen misleadingup-sidesandbogusnegatives.Withthehelpofa series of experiments, we concluded that object detection algorithmswithROI(RegionofInterest)performbetterthan algorithms without ROI. The authors have tested many models but among all of them, the state-of-the-art Yolov4, trained new database, gave very few false positive and negativevalues,henceitachievedthemostsuccessfulresults. Itgave91.73%meanaverageprecision(mAP)andaF1-score of 91% with almost 99% confidence score on all types of imagesandvideos,hencedevelopinganautomaticrealtime weapondetector.Reductionoffalsepositivescanbeseenas in future works to make it more accurate according to authorsinthiseleventhpaper.
Whileanalyzingthecostandaccuracyofusingcloudand machinelearningfordetectionofviolence,bothfactorsdon’t go hand-in-hand along with proper CCTV system management.Theaccuracywedealwithhereiswaylessthan 90%.
Also, there is no domain within any one of the papers which is improving accuracy and integrating Image processing, Artificial Intelligence andCybersecurity,under one CCTV website system [20], which can be used as a number one domain to login and use the most high-tech systemforsurveillanceinthecountry.
Aswecameacrossmoreandmorepaperswithinthespan ofpast3years,wealwaysendedupnegotiatingthesecurity or data of the CCTV systemof a particular organizationor

government.Whichturnsouttobeeasilyhackable,especially inIndianstates.Thereby,acoremoduleofcybersecurityis ardentlyneeded,securingmajorityofattacks,andtriggering warningifsystemisabouttogetcompromised.Mostofthe top technology and algorithms among the CCTV system business revolves within different governments trying to securetheirindividualbagofsurveillance.Insimplewords, privatesectorcompaniesandothersmallbusinessowners are excluded from reaping benefits of such technologies. Therefore, all the above modules under one website providing CCTV security services is something that can be found almost nowhere, and needs to be taken charge of creatingdevelopingassoonaspossible.
3 OVERVIEW OF PROPOSED SYSTEM
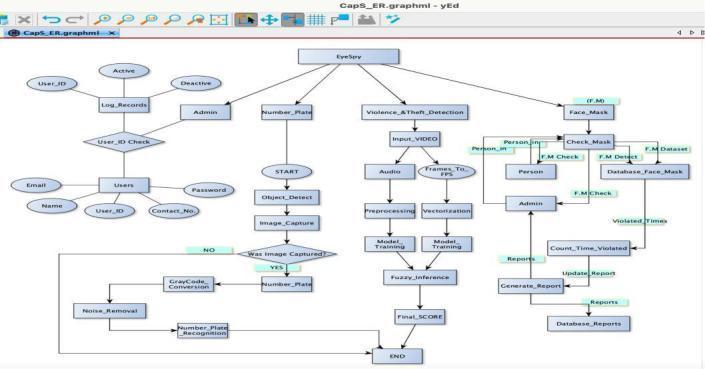
Summarizing the complete project, inculcating all the modulesunderonename,‘EyeSpy’.
Thusly,itisridiculoustotryandexpectandrepelthatsort of kind of individual in light of the fact that the traffic individualmightnothavethechoicetorecuperatethevehicle numberfromthemovingvehiclebeforethecamerabecause ofthespeedofthevehicle.
Furthermore,althoughViolencerateshavebeenbrought downaround57%duringtherangeofrecentmanyyearsyet it doesn't impact the way that the exhibition of brutality occurs,concealedbythelaw.Brutalitycanbemasscontrolled in some cases by higher specialists, anyway, to keep everything in line one must "Microgovern" over every development happening in each street of each square. So, modulesandcalculationslikeHAARCASCADEareutilizedfor picturerecognition.Additionally,[22]toaddressthebutterfly impactsswayinoursetting,wemadeanexceptionalmodel andahypothesizedframeworktodealwiththeissueusing profoundlearning.Themodeltakesthecontributionofthe CCTVvideotakescareandlaterdrawssurmisingperceives assuming[21]aviciousdevelopmentisgoingon.Likewise, wecreatedtheAutomaticNumberPlateRecognition(ANPR) frameworkasoneoftheanswerstotheseissues.
Finally,weintegrateallthecombinedmodulesandfigureout thecriminalsbyverifyingthosedetectedonCCTVwiththatof thedatabase.
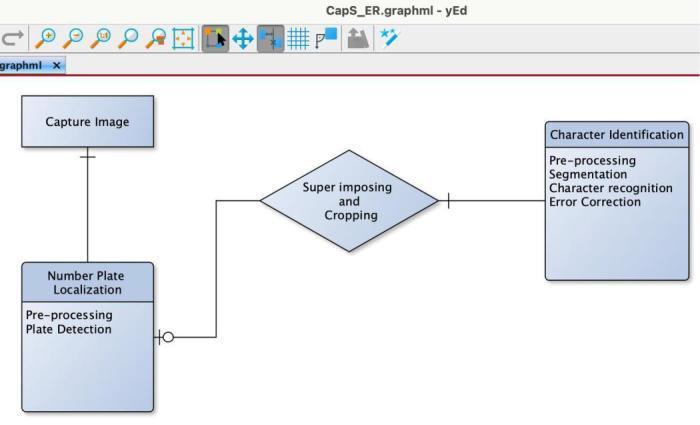
3.2 MODELING AND ANALYSIS
3.1 METHODOLOGY
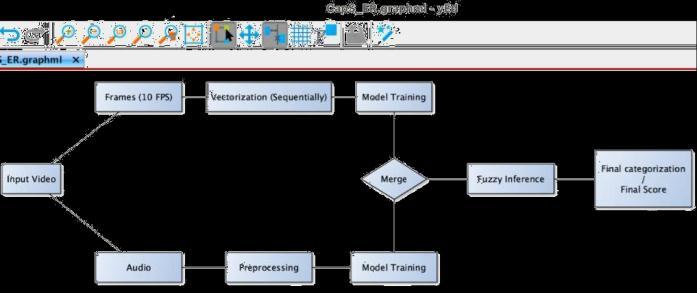
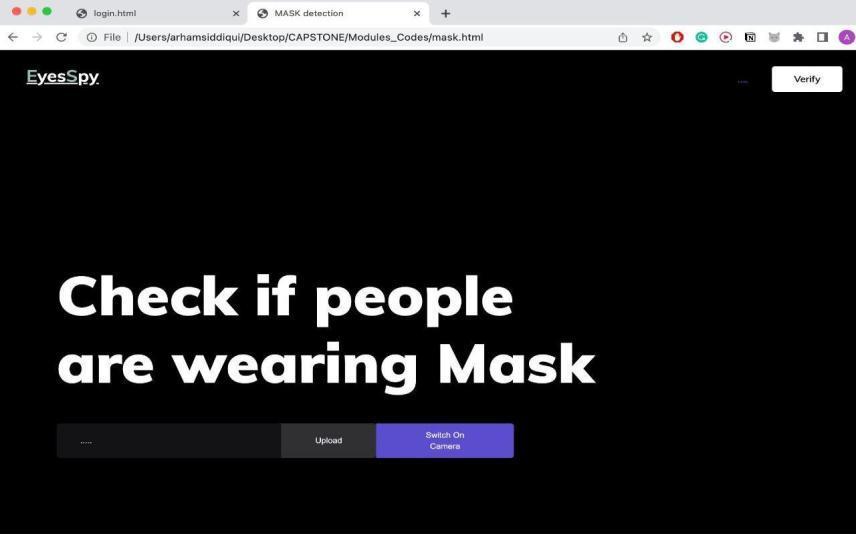
Worldwide pandemic COVID-19 conditions arose in a scourgeofhazardousinfectionfromonesideoftheplanetto theother.Wearingafacialcoveringwillhelpwiththwarting thespreadofdefilementandholdtheindividualbackfrom getting any airborne overpowering organisms. Using our module of Face Mask Detection System, one can screen assumingthatpeoplearewearingcoversortheotherhand not. Another ordinary issue is Traffic control and vehicle ownerIDhasbecomemajorineverycountry.
Occasionally it becomes testing to perceive a vehicle owner who for the most part mishandles traffic rules and drivesunreasonablyrapidly.
Fig.3NumberPlateDetection
This application is implemented using ReactJs for the front-endandPHP,sql,MongoDBfortheback-end.InReactJS applicationanimageisacceptedasinputfromtheuserwhich willbesavedinourlocaldirectory.Thatimageisreadinthe back-endapplicationusingtheOpenCVmodule.
Theimagereadispre-processedandfirstthediameterof the circular shaped objects present in our image is determined.

Afterloggingin,theuserselectsthe'NumberPlate’option onthemenubartocheckiftheimageofthenumberplateof thevehiclethatheorshetookorhasisastolenvehicleor not.So,aHaarCascadeclassifierisbeingusedheretodetect the numbers on the number plate. This classifier gives an element-basedobjectdiscoveryprocedure,whichmatches very nearly 18000 highlights in a picture to recognize an objectiveitem.Utilizing'objectidentification'wedistinguish an article situated inside the picture. In the beginning advance,itneedsbunchesofpositivepicturesforexample number plate pictures, and negative pictures for example pictures that don't contain a number plate, to prepare the calculation.
All things considered, we have utilized a pre-prepared numberplaterecognizerutilizingHaarCascadetodistinguish anumberplateinagivenpicture
anarticle[23]situatedinsidethepicture.Inthebeginning advance,itneedsbunchesofpositivepicturesforexample number plate pictures, and negative pictures for example pictures that don't contain a number plate, to prepare the calculation.
All things considered, we have utilized a pre-prepared numberplaterecognizerutilizingHaarCascadetodistinguish anumberplateinagivenpicture.
Fig.4FaceMaskDetection
This application is implemented using ReactJs for the front-endandPHP,sql,MongoDBfortheback-end.InReactJS applicationanimageisacceptedasinputfromtheuserwhich willbesavedinourlocaldirectory.Thatimageisreadinthe back-endapplicationusingtheOpenCVmodule.
Theimagereadispre-processedandfirstthediameterof the circular shaped objects present in our image is determined.

Afterloggingin,theuserselectsthe'NumberPlate’option onthemenubartocheckiftheimageofthenumberplateof thevehiclethatheorshetookorhasisastolenvehicleor not.So,aHaarCascadeclassifierisbeingusedheretodetect the numbers on the number plate. This classifier gives an element-basedobjectdiscoveryprocedure,whichmatches very nearly 18000 highlights in a picture to recognize an objectiveitem.Utilizing'objectidentification'wedistinguish
Fig.5Detectionofviolence,crimedetectionbyAIhuman actionsofcrimefrom(dataset)
Further,thethirdoptionwithinthemenubarcanbeseen is'TheftandViolence',usingthisoption,clickingtheusercan check if the live video of the CCTV camera the user is one involvingviolence,theft,ornot.Thefollowingarchitecture canbeseenbelow.
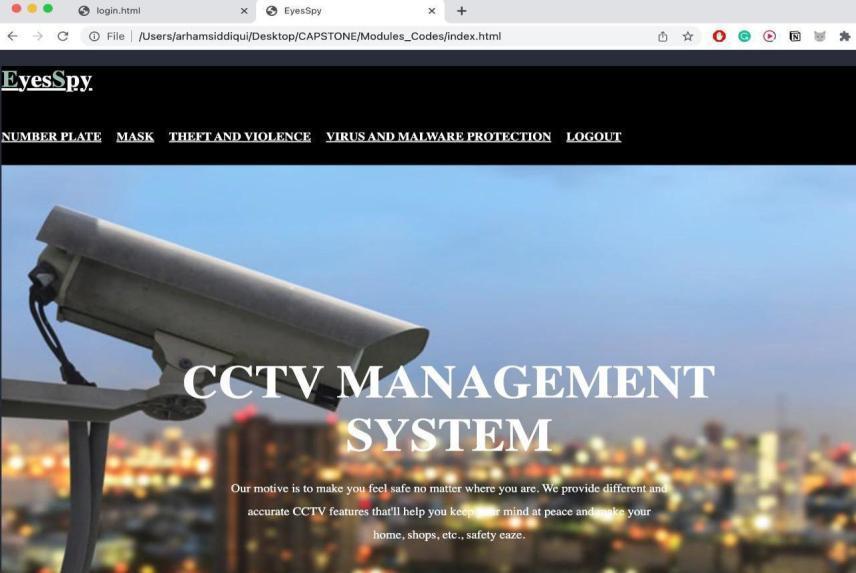
Further,enhancingcybersecurityoftheCCTVsystemby automating the vulnerability scan and alerting the host systemwhenathreatisdetected.
Thisparticularmoduleinvolvesalotofbrainstormingand formulationofarchitecturebeforeputtingitoutonline,the developmentofthismoduleisdonebyusing‘HackerTarget’ vulnerabilityscanner,whichisanopen-sourcevulnerability scanner which runs frequent scans against our website. Wherein,wewillbeinteractingwiththeHackerTargetAPI throughourwebsite.
4. RESULTS AND DISCUSSION
Login Logging into
FMM-1 Normal people with face mask.
FMM-2 People without mask
Uploading an image of a coupleposing atthecamera withmasks.
Uploading an image of peopleposing atthecamera without masks
Green box with mask detected and percentage.
Red boxwith no mask detected and percentage.
PASS
FMM-3 A crowd ofpeople.
Uploading an image of people walkingdown the street with and withoutmask.
Red and green boxes with people without and with masks respectively.
PASS
NPDM1 License plate and face of a person
Uploading an imageofacar withaperson sittinginside.
PASS
NPDM2 In extreme condition s
TVDM1 Violent Video
TVDM2 Nonviolent video
TVDM3 With animals as a reference
Inputting an imageofacar with extreme unclesr image.
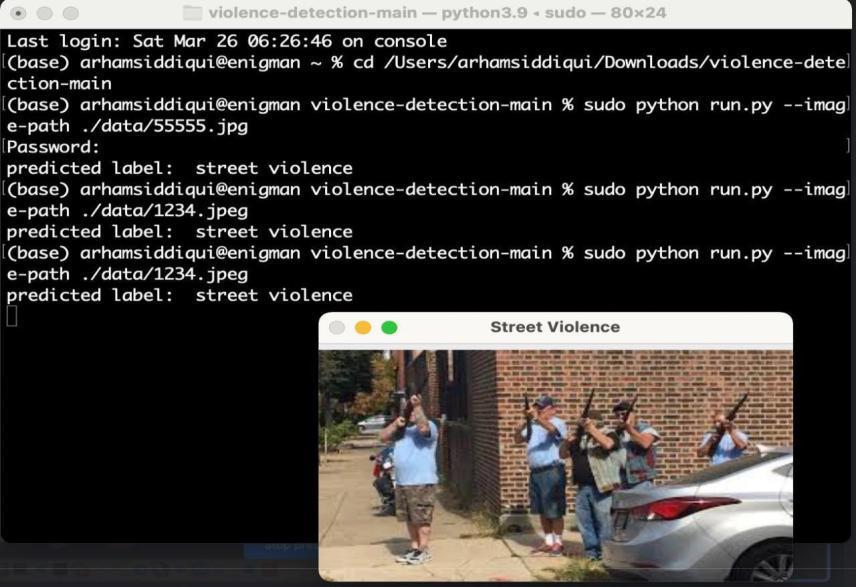
Uploading a violentvideo
Uploading a violentvideo
The vehicle number and image of the person extractedand matched.
Matching the person and thecar.
Itisa violent video with percentage confidence.
It is a nonviolent video with percentage confidence.
PASS
PASS
PASS
PASS
Uploadingthe video
5. PERFORMANCE METRICS
Itisa violent ornon-violent video with percentage confidence.

PASS
Consideringtheoverallefficiencywehavebeensuccessful inachievingmorethan95%accuracyonourtrialdatasets.
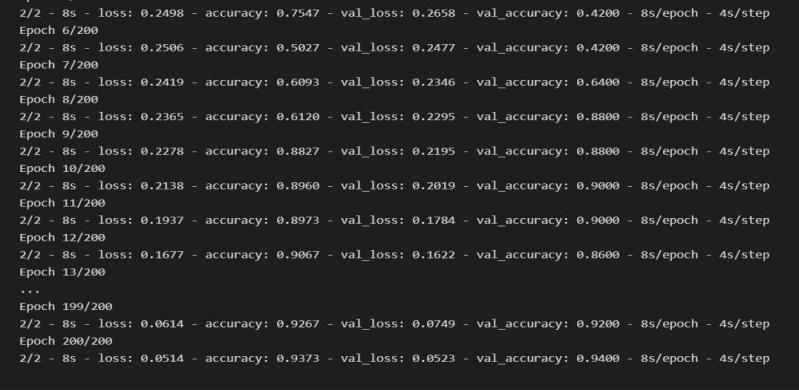
Theprocesscalledhyper-tuninghasbeenusedsolelyonthe ‘hockeydataset’.Thehyperparametertuningisappliedfor eachdatasetwithin,usingonly20epochsandearlystopping of5insteadof15asweapplyinthefinaloptimalnetwork training,wealsouseaclassic80-20splitfortrain-testdata. Thedropoutof50%improvedthemodelperformanceand resultedin98.5%accuracy.
13GraphofTESTvsTRAIN

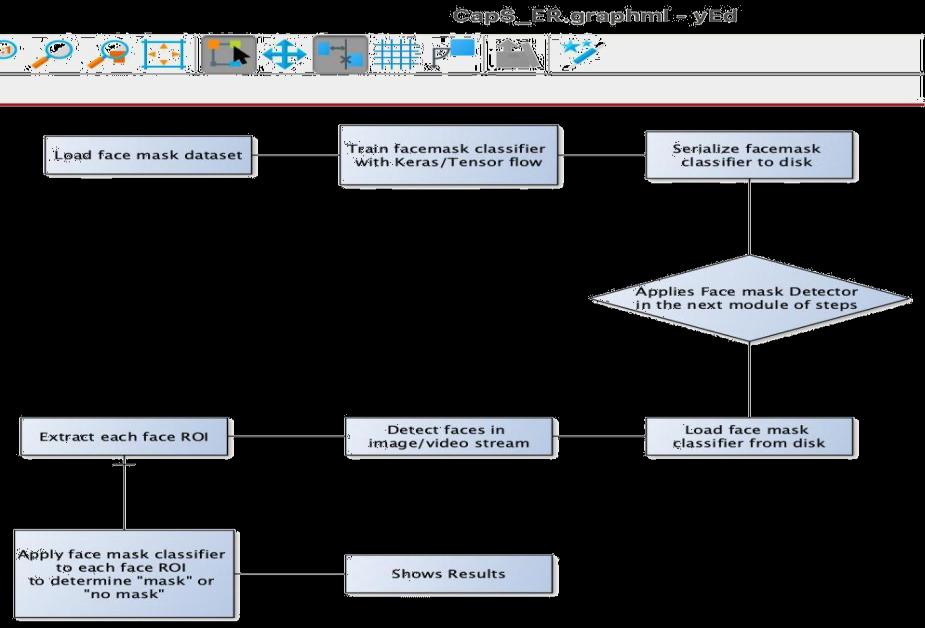
Each of the models was tried with various dataset pictures, recordings, and continuous video transfers. The exactnessofthismodelisfundamentallyaccomplishedand thestreamliningofthismodelisessentiallyapersistentcycle we are intending to fabricate an exceptionally precise arrangement by tuning the hyperparameters. This specific model[24]canlikewisebeutilizedasautilizationbestcase for edge examination. Besides, the proposed strategy accomplishesthebestoutcomesonapublicfacialcovering dataset.Withtheimprovementoffacialcoveringlocation,we canrecognizeontheoffchancethattheindividualiswearing afacialcovering,andpermittingtheirentrancewouldbeof incredibleassistancetosociety.
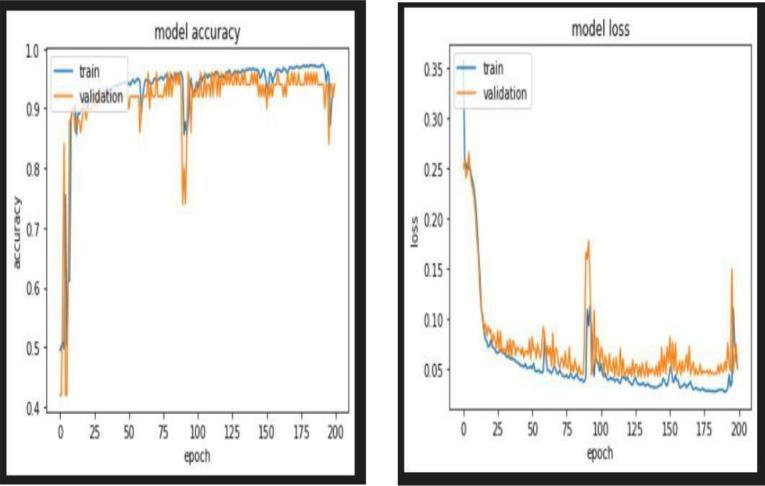
Ourmodelgave98%accuracywithtensorflowgpu.
With the Epochs, we were able to have an accuracy of 93% which can be grown till 98% Considering the 'mask detection module’, we used OpenCV, tensor flow, Keras, Pytorch,andCNNtodetectwhetherpeoplewerewearingthe facemasksornot.Wehaveused‘Withmask’and‘Without mask’datasets.
Our accuracy almost touched the asymptote from the beginning.Thetotallosscameoutas1.4andtheefficiency was98%
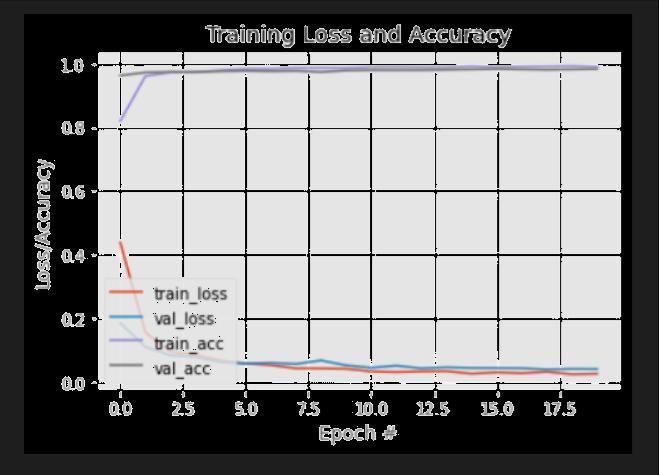
14AccuracyofFaceMask
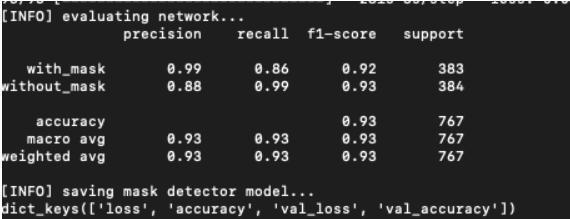
Consideringthe'numberplatedetectionmodule’,thisproject wassuccessfulinperformingmainlyfourtasks.Theventure was effectively planned with the goal that we can comprehend the innovation utilized in these days' programmedtagframeworksandOCRframeworksutilized in most evolved nations like Germany, France, Singapore, Japan,andsoon.Itisseenthatsecuritypowersallaroundthe worlddealwithissuesfindingorenrollingvehiclenumbers tofollowanyguiltyparty.Itisalsoseenthattechnologycan greatly help us in this situation by solving it [25]. After manually testing it, the results and efficiency came about 94%.
6. CONCLUSIONS
CommunicationwithuserandaccountholderoftheCCTV system they run, during the time of security breach and crime detected, is very important. Thus, providing IoT feature and alerts for a range of users of CCTV system is attained in this project. Failure to converse alerts and improve accuracy of detecting criminals through AI and imageprocessing,canleadtomajorlossesasanindividual and as a particular company as well. For this general populationcanbeaninconveniencetoall-inclusivesecurity of vital information and feelings of freedom for legitimate observation. In this paper, with the abilities and the inspiration,wecreatedsomethingforthesmallandmedium sizedbusinessessothattheykeeptrackoftheirprocesses througharesponsivesurveillance,wemadethisapplication which will help individuals who are figuring out how to discuss better with their CCTV framework. Our visionary applicationvisionisanapplicationthatleadsa discussion throughImageProcessing.Evenwithallthesefeaturessome featurescouldnotbeimplementedbecauseofGPUissues ForexampletheliveCCTVfacemaskdetectioncouldnotbe implemented as well as the live footage of car number detection. For future use we will be happy to work with bettersystemswhohasabetterGPUsowecanimplement ourlivefootagefromCCTVfacemaskdetectionandnumber platedetection.
We also did our best to increase our accuracy by using differenttechniquesasmuchaspossibleliketheyprevious atbestaccuracywasabout91%andwetookitto95%which isthecurrentaccuracyforfuturewewillbeusingdifferent variationsanddifferenttechniqueslikeConvoLSTM+CNN so wecan increase our accuracy even more and take it to 98%oreven99%.
REFERENCES
[1] S.Shirsat,A.Naik,D.Tamse,J.Yadav,P.Shetgaonkarand S.Aswale,"ProposedSystemforCriminalDetectionand Recognition on CCTV Data Using Cloud and Machine Learning," 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), 2019, pp. 1-6, doi: 10.1109/ViTECoN.2019.8899441.L. Eschenauer, V. D. GligorandJ.Bara,‘OnTrustEstablishmentinMobileAd HocNetworks’,SecurityProtocolsSpringer,(2004),pp. 47-66.
[2] Roopa,Y.M.,Popuri,S.H.,Sankar,G.G.S.,&Kuppili,T.C. (2020, July). Convolutional Neural Network-based Automatic Extraction and Fine Generation. In 2020 SecondInternationalConferenceonInventiveResearch inComputingApplications(ICIRCA)(pp.230-234).IEEE. doi:10.1109/ICIRCA48905.2020.9182844.
[3] Gavrovska, A. and Samčović, A., 2020. Intelligent Automation Using Machine and Deep Learning in
Cybersecurity of Industrial IoT. Cyber Security of Industrial Control Systems in the Future Internet Environment, pp.156-174, doi: 10.4018/978-1-79982910-2.ch008.

[4] Piza,EL,Welsh,BC,Farrington,DP,Thomas,AL.CCTV Surveillanceforcrimeprevention:A40-yearsystematic reviewwithmeta-analysis.Criminology&PublicPolicy. 2019; 18: 135– 159. https://doi.org/10.1111/17459133.12419
[5] Morales G., Salazar-Reque I., Telles J., Díaz D. (2019) DetectingViolentRobberiesinCCTVVideosUsingDeep Learning. In: MacIntyre J., Maglogiannis I., Iliadis L., Pimenidis E. (eds) Artificial Intelligence Applications and Innovations. AIAI 2019. IFIP Advances in InformationandCommunicationTechnology,vol559. Springer, Cham. https://doi.org/10.1007/978-3-03019823-7_23
[6] Circo, G., McGarrell, E. Estimating the impact of an integratedCCTVprogramoncrime.JExpCriminol17, 129–150(2021).https://doi.org/10.1007/s11292-01909404-y
[7] L. J. Halawa, A. Wibowo and F. Ernawan, "Face Recognition Using Faster R- CNN with Inception-V2 ArchitectureforCCTVCamera,"20193rdInternational ConferenceonInformaticsandComputationalSciences (ICICoS), 2019, pp. 1-6, doi: 10.1109/ICICoS48119.2019.8982383.
[8] J.Lim,M.I.AlJobayer,V.M.Baskaran,J.M.Lim,K.Wong andJ.See,"GunDetectioninSurveillanceVideosusing Deep Neural Networks," 2019 Asia-Pacific Signal and InformationProcessingAssociationAnnualSummitand Conference (APSIPA ASC), 2019, pp. 1998-2002, doi: 10.1109/APSIPAASC47483.2019.9023182.
[9] H. Jain, A. Vikram, Mohana, A. Kashyap and A. Jain, "WeaponDetectionusingArtificialIntelligenceandDeep LearningforSecurityApplications,"2020International Conference on Electronics and Sustainable Communication Systems (ICESC), 2020, pp. 193-198, doi:10.1109/ICESC48915.2020.9155832.
[10] SalimAfra,RedaAlhajj,Earlywarningsystem:Fromface recognition by surveillance cameras to social media analysis to detecting suspicious people, Physica A: StatisticalMechanicsanditsApplications,Volume540, 2020, 123151, ISSN 0378-4371, https://doi.org/10.1016/j.physa.2019.123151.
[11] M. T. Bhatti, M. G. Khan, M. Aslam and M. J. Fiaz, "Weapon Detection in Real-Time CCTV Videos Using DeepLearning,"inIEEEAccess,vol.9,pp.34366-34382, 2021,doi:10.1109/ACCESS.2021.3059170.
[12] Donath P., Grega M., Guzik P., Król J., Matiolański A., Rusek K. (2020) Dangerous Tool Detection for CCTV Systems. In: Dziech A., Mees W., Czyżewski A. (eds) Multimedia Communications, Services and Security. MCSS 2020. Communications in Computer and Information Science, vol 1284. Springer, Cham. https://doi.org/10.1007/978-3-030-59000-0_18
[13] R. Kakadiya, R. Lemos, S. Mangalan, M. Pillai and S. Nikam,"AIBasedAutomaticRobbery/TheftDetection using Smart Surveillance in Banks," 2019 3rd InternationalconferenceonElectronics,Communication andAerospaceTechnology(ICECA),2019,pp.201-204, doi:10.1109/ICECA.2019.8822186.
[14] Sung, CS., Park, J.Y. Design of an intelligent video surveillancesystemforcrimeprevention:applyingdeep learningtechnology.Multimed ToolsAppl 80,34297–34309 (2021). https://doi.org/10.1007/s11042-02110809-z
[15] MinhT.Nguyen,LinhH.Truong,TrangT.Tran,Chen-Fu Chien, Artificial intelligence based data processing algorithmforvideosurveillanceto empowerindustry 3.5,Computers & Industrial Engineering,Volume 148, 2020, 106671, ISSN 0360-8352, https://doi.org/10.1016/j.cie.2020.106671.
[16] Kim,J.,Lee,D.&Park,N.CCTV-RFIDenabledmultifactor authenticationmodelforsecuredifferentiallevelvideo accesscontrol.MultimedToolsAppl79,23461–23481 (2020).https://doi.org/10.1007/s11042-020-09016-z
[17] Sanjana, S., Sanjana, S., Shriya, V.R. et al. A review on various methodologies used for vehicle classification, helmet detection and number plate recognition. Evol. Intel. 14, 979–987 (2021). https://doi.org/10.1007/s12065-020-00493-7
[18] Che-Yen Wen, Shih-Hsuan Chiu, Jiun-Jian Liaw and Chuan-PinLu,"Thesafetyhelmet detection for ATM's surveillancesystemviathemodifiedHoughtransform," IEEE 37th Annual 2003 International Carnahan ConferenceonSecurityTechnology,2003.Proceedings., 2003,pp.364-369,doi:10.1109/CCST.2003.1297588.
[19] N. Boonsirisumpun, W. Puarungroj and P. Wairotchanaphuttha, "Automatic Detector for Bikers with no Helmet using Deep Learning," 2018 22nd International Computer Science and Engineering Conference (ICSEC), 2018, pp. 1-4, doi: 10.1109/ICSEC.2018.8712778.
[20] Gavrovska, A. and Samčović, A., 2020. Intelligent Automation Using Machine and Deep Learning in Cybersecurity of Industrial IoT. Cyber Security of Industrial Control Systems in the Future Internet

Environment, pp.156-174, doi: https://doi.org/10.3390/su13031210
[21] Shakya,Subarna."Analysisofartificialintelligencebased imageclassificationtechniques."JournalofInnovative ImageProcessing(JIIP)2.01(2020):44-54.
[22] C. T. Kong and S. M. Yiu, "Hacking CCTV by changing time," 2021 International Conference on Electrical, Communication,andComputerEngineering(ICECCE), 2021, pp. 1-8, doi: 10.1109/ICECCE52056.2021.9514241.
[23] Thirumagal E., Saruladha K. (2021) Design of LSTM–CNNwithFeatureMapMergeforCrimeSceneDetection inCCTVFootage.In:BhatejaV.,SatapathyS.C.,TraviesoGonzálezC.M.,Aradhya V.N.M.(eds) Data Engineering and Intelligent Computing. Advances in Intelligent SystemsandComputing,vol1407.Springer,Singapore. https://doi.org/10.1007/978-981-16-0171-2_2
[24] R.Ke,Y.Zhuang,Z.PuandY.Wang,"ASmart,Efficient, and Reliable Parking Surveillance System With Edge Artificial Intelligence on IoT Devices," in IEEE TransactionsonIntelligentTransportationSystems,vol. 22, no. 8, pp. 4962-4974, Aug. 2021, doi: 10.1109/TITS.2020.2984197.
[25] Chavda, J. Dsouza, S. Badgujar and A. Damani, "MultiStageCNNArchitectureforFaceMaskDetection,"2021 6th International Conference for Convergence in Technology (I2CT), 2021, pp. 1-8, doi: 10.1109/I2CT51068.2021.9418207.
