Online Voting System Using Fingerprint sensor and Blockchain
1Student, Maharaja Agrasen Institute of Technology
2Student, Maharaja Agrasen Institute of Technology
3Student, Maharaja Agrasen Institute of Technology
4Asst. Professor, Maharaja Agrasen Institute of Technology ***

Abstract - An online voting system also referred to as an online pollingsystemor e-votingsystem is anemergingtoolto maintain integrity and rightfulness to one's fundamental rights while casting their preference in the elections. Digitalization has been proven to be a helping hand to mankind with emergingtechnologies like blockchain,whichis widely adopted worldwide to ensure end-to-end authentication, encryption, and verification advantages we have used Aadhar Id and fingerprint sensor in this project research to increase the integrity and security factors. Here it serves as a secure method to carry out election processes. We tend to carry out this sensitive process in the decentralized distributive system without any outer alterations to the data storedin blocks andhashes thus helpingtheuserstocastvotes remotely in a hassle-free, time-saving and paperless manner, thus reducing insufficiency andmalpractices that havewidely been seen ina traditional ballot or Electronic Voting Machine (EVM) systems.
Key Words: Blockchain, Digitalization, Decentralized, Encryption, integrity, Authentication, Aadhar id, Electronic Voting Machine
1. INTRODUCTION
Votingisoneoftheoldestmethodstoelectasupremehead in any institution, committee, or political body. In most democratic countries like India, voting has been widely adoptedovertheyearstocreateanatmosphereofintegrity and rightfulness where people have the right to choose a representativewhocanservetheirdemands[3].Themost adaptedtraditionalwayofelectingaleaderovertheyears has been casting votes where people gather physically at pollingboothsandelectamember.
1.1 Problem with existing system
Themajorproblemwhichismostlyseeninthistraditional method where people cast votes using Electronic Voting Machines (EVMs) is the usage of malpractices influencing peopleandgettingvotes,forcefullythreateningpeople,lack of privacy, security, compliance issues, and unbothered citizens[2].
1.2 Online Voting as a solution
Blockchainisanefficientemergingtechnologythatworkson end-to-endencryption.Duetoitsintrinsicabilitytopreserve anonymity,maintainadecentralizedandpubliclydistributed ledgeroftransactionsacrossallnodes,andplayasignificant roleinthefieldofelectronicvoting,bystoringdatainblocks that cannot be altered until the data gets delivered as the informationthusmaintainingsecurity,integrity,andprivacy ofusersinsuchsensitiveprocesses.Withvotesbeingcast remotely from any place, without any biased interference saves time, maintains fundamental rights, and motivates peopletotakepartintheprocess.
1.3 Scope
Forverification,theperson’sFingerprintwillbescannedon theclient-sideandmatchedone-to-oneattheserverswith the data extracted from the local database. We used Fingerprints for authentication because processing Fingerprintsisfasterandbetterthanotherbiometricdata. Moreover, by using Fingerprints it is ensured such fake entriesareblockedrightattheverybeginning[8].Thus,the online voting system is an approach to bring anonymity, integrity,productivity,andlibertytoanindividualensuring security and accessibility to the people to take part in electionsandvotefreelywiththeirowndecision.
2. LITERATURE SURVEY:
Block chain was first introduced by Satoshi Nakamoto (a pseudonym),whoproposedapeerto-peerpaymentsystem thatallowscashtransactionsthroughtheinternetwithout relyingontrustortheneedforafinancialinstitution Block chainissecurebydesign,andanillustrationofasystemwith a highintricatefailureforbearance.E-votingis animplicit result to the lack of interest in advancing amongst the youthfultechsmartpopulation.Fore-votingtocomemore open, transparent, and singly auditable, an implicit result would be base it on blockchain technology. Blockchain technology has a lot of pledge; still, in its current state it mightnotreachitsfulleventuality.
GabyG.Dagger,MateoMilinkovic,andJordanMahler(2018) deal with Voting as a fundamental part of democratic systems,itgivesindividualsinacommunitythefacultyto voice their opinion In recent times, name turnout has
loweredwhileenterprisesregardingintegrity,security,and availability of current voting systems have escalated. EVotingwasintroducedtoaddressthoseconcerns;however, itisnotcost-effectiveandstillrequiresfullsupervisionbya central authority. The Blockchain is an emerging, decentralized,anddistributedtechnologythatpromisesto enhancedifferentaspectsofmanyindustries.
Many organizations such as [1] have created their own pollingwebsitewheretheycancastvotesamongtheirown selectedgroupofveteransandmilitaryfamilymembersto electthe next generationof poll workers. Thereare many such websites that allow organizations and people to cast votesatlowlevels.
Past studies show that an online voting system was suggested. It was primarily built using python and other programming languages. It allowed users to cast votes by simply logging into their accounts with their user ids and casting votes. But this doesn't ensure much privacy and authenticitytoone’sidentity[9].
Pashine, naive and kelapure [4] proposed an android platformforonlinevotingsystem.Thisapplicationprovides diversionoflongprocessalsoprovidesecuritytothevoter and its voter comfort system voter no need to go polling bootheasilyvoteforcandidateinhometownitself.Andalso providetheoptionofgesturerecognitionbutauthentication istheproblemofandroidplatform.Inthisapplicationwhich is partitioned into three panels Admin Panel, Candidate PanelandVoterPanel.
Khasawneh[5]ProposedAnE-VotingSystemforBiometric SecurityIsProvidingATwoSidedSolutionSuchAsServer And User Side. After casting the vote system will induce hardcopy for voter and also induce unique number. This uniquenumberandvoternameandidentificationnumberis secured. All content is stored in special box. This box is securedbox.Thisinformationishabituatedforvindicating thevoteBeforeStoredinFinalDatabase Thissidecopyis printed with unique barcode that can be easily readable automaticallyandscannedthenrandomlychooseonecop, then this copy is tested. This two-sided process providing verificationandcorrectnessforthesystem.
FiresI.Hazzan,SeifeddineKadar(6)thispaperdealswiththe designanddevelopmentofaweb-groundedvotingpointin ordertogiveahighperformancewithhighsecuritytothe voting system also we use web technology to make the votingsystemmorepractical.Thenewdesignisproposedan election for a university for selecting the president of the university. The proposed EVS allows the choosers to overlooktheirpoint,whichisalsomatchedwithanformerly savedimagewithinadatabase.DevelopedWeb-grounded Voting System using Fingerprint Recognition. This system hashandedaneffectivewaytocastvotes,freeoffraud,and make the system more responsible, profitable and fast.
We've used Minutiae- grounded point identification and matchingwithhighdelicacy.

Anotherresearchusedfacialdetectiontoincreasesecurity measuresbutitdoesn'tcompletelyjustifyone'sidentityand anonymity while electing a leader. It doesn't ensure fair means and may cause ambiguity issues. Earlier it wasn't muchvalidatedwhichcouldensuretheusertocheckiftheir votehasbeensuccessfullydoneorwhethertheyareeligible ornot,thusleavingmanyimportantfactorsunnoticed.
Astechnologyadvances,manycountrieshavenowoptedfor electronic voting systems. Any voting system must follow principles of translucency and equity in order to achieve fairness.Theblockchainmechanismemploysadistributed architecture and all these researches somewhat lack the anonymity,authenticityandrealnessofuserwhichcanbe overcomeusingcombinationofdifferentfeatureslikeusing Aadhar id, confidential details and most importantly fingerprintsensorwhichensuresintegrityandrealnessof theuser.
3. METHODOLOGY:
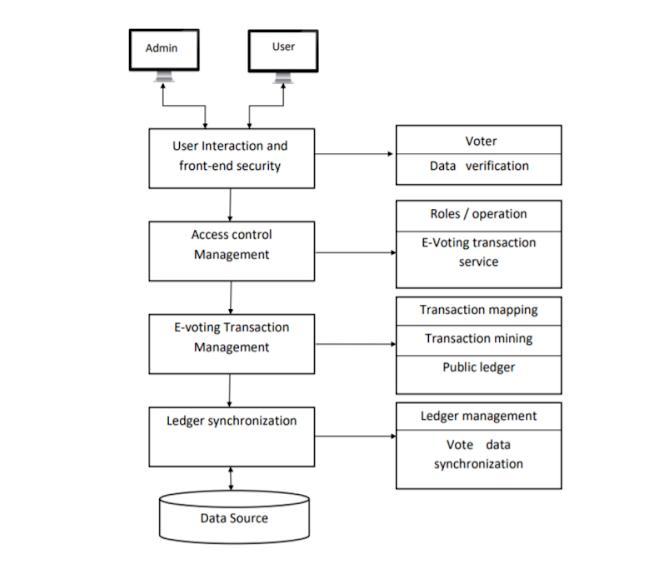
This digital voting system is a platform that enables only authentic and eligible users to cast their votes in the elections.Theuserisprovidedtologinfirsttothewindow withtherightcredentials.Hewouldregisterwiththephone numberorAadharcardidorvoteridissuedtohim.Oncethe userisfoundauthenticandeligible,thatis,thesystemholds his data, he meets the age criteria, and citizenship of the region or nation he is casting votes for, he is moved to further process. It is being worked to implement the fingerprint sensor so as to increase the authenticity and securityofthe system.Wehaveconsidered2mainmodules whichareasfollows:
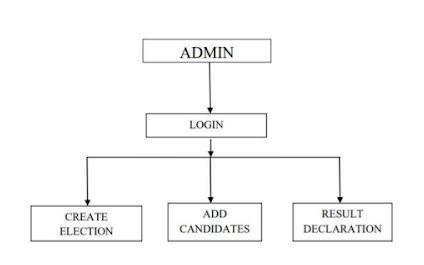
A. Admin- The admin module is divided into 5 components-
1. Dashboard-It will contain various charts to display informationsuchasnumberofparties,no.ofvotersetc.
2. Add seeker- In this point of admin, he can add campaignerswhoarestandingintheelection.Afterseekeris addedit'llbedisplayedonthestonerside.
3.CreateElection-Thisfeatureofadminwillallowhimto create election. A user can cast his vote only after the electioniscreatedbyadmin.Ausercancastvotebetween thestartdateandenddate.
4.ElectionDetails-Inthissectionadmincanupdateelection detailssuchasstartdate,enddateetc.
5.CandidateDetails-Incandidatedetailsallthecandidates addedbyadminwillbedisplayed.Admincanmodernizethe seekerdetailsifincaseawrongentryisdone.
B. User- The user module is divided into 4 components-
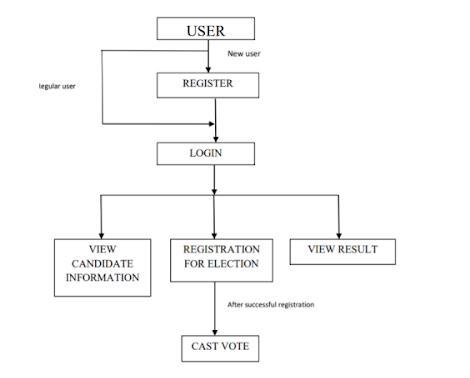
1. Dashboard- The user dashboard contains information about parties and their candidates. A user can see all the informationaboutcandidate.
2. Voter Register- In this section first user will have to registerhimselfonlythenhewillbeabletocasthisvote.
3.VotingArea-Afteruserisregistered,thenonlyhewillbe directedtothispageandthenhecancasthisvote.
4.Results-Inthiscomponenttheuserwillbeabletoseethe resultsoftheelection.
3.1 Algorithms:
Minutiae Based Algorithm
Inthisweusetwoalgorithms:minutiae-extractionalgorithm (fingerprint detection) and minutiae-matching (matching fingerprint i.e. input fingerprint and database fingerprint) algorithm.
a. Minutiae Extraction
Fingerprint authentication is based on minutiae patterns matching.Minutiaeextractionconsistingthreecomponents:
i.Orientationfieldestimation
ii.Ridgeextraction

iii.Minutiaeextractionandpostprocessing
b. Minutiae Matching
We can match fingerprint by different strategies, such as pointpatternmatching,image-basedmatching,ridgepattern matching, graph-based scheme, etc. The point pattern matching is the minutiae matching. a minutia matching is decomposedintotwostages:
i.Alignmentstage
ii.Matchingstage
Theprocesscanfurtherproceedinanothersection where the user can cast vote according to his choice using the MetaMaskwallet.Oncethevoteiscast,theuserreceivesa notificationofthesameorcanseetheprogressinthestatus sectionofthesystem.
Oncethevoteiscastwithoneid/number/ Aadharid,the votergetsineligibletocastvoteagainforthesameprocess. Thismaintainshomogeneityandanonymity.
Thesystemcanbeusedbyseveralothermemberswhomay befromthesamefamily,team,orgroupbutwiththeirown IDs and Aadhar IDs which makes the system distributive whilemaintainingprivacy.
Theuserdoesn’tneedtovisitanypoolingboothswhichwill save a lot of time, reduce workload, and can prevent any possibleinterferencewhichcouldleadtobiaseddecisions thus preserving one’s fundamental rights and integrity to personalinformation
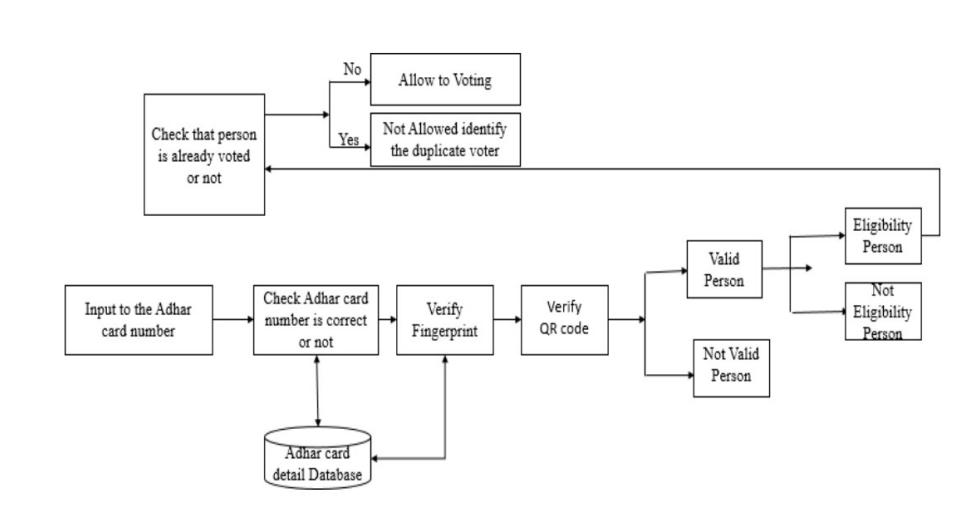
3.2 Fingerprint Verification:
A person must have a valid UID number in order to be authenticated.Thelocaldatabaserecordswillbeexamined firstbeforethenumberisused.Thecentralrepositorywill besearchedifitcannotbelocated.Aone-to-manymatchis involved.Naturally,thepersonwon'tbeabletoparticipate inthevotingprocedureiftheirnumbercannotbelocatedin the main database. This record is taken out of the local database and forwarded to the servers that handle authentication for further processing. For verification, the client-sidefingerprintscanoftheuserwillbecomparedoneto-one at the servers with the information taken from the local database. The local database is less stressed by this approach, and data throughput is increased. Because processingfingerprintsisquickerandmoreaccuratethan processingotherbiometricdata,weemployfingerprintsfor authentication. Aadhar information would also be insufficienttoproveaperson'sgenuineidentitybecauseitis simpletospoofthem,bututilizingfingerprintsensuresthat bogusentriesarestoppedatthesource[9].

3.3 Technologies Used:
The whole system is blockchain-based and is run on Ethereum (an open-source platform to create blockchain applications).Wehavealsousedsmartcontactswhichhold thetermsandconditionsforcertainapplicationstobebuilt. Thesearetheprogramsstoredontheblockchainprogram whichareallowedtorunwhencertainconditionsaremet. Solidity is the high-level language on which the whole projectisbuilt.Weknowthatanyprocessthatundergoesin a blockchain is considered a transaction and to carry out eachstepoftheprocesswhichisreferredtoasatransaction here is achieved using the MetaMask wallet. It generates passwords enabling only one current user to access the systemwhichmakesitasecureplatformwhileundergoing such sensitive processes. Since the transactions require actualmoney,GanacheisusedasalocalRPCwhichprovides 10accountstocheck ortest thetransaction. Truffleisthe framework suitethatisusedinEthereumtointeractwith compiled smart contacts in an easier and more effective manner.
4. FUTURE SCOPE:
OnlineVotingtechniquescanbegreatlyadaptedinnearby futureforbigdecisionmakingslikeelectionsinanycountry, which will allow citizens to live a balanced social and personallife.ItcanreplacethecurrentEVMsandwiththe fingerprint sensor, this model can become more reliable, thus ensuring only authentic and eligible users cast their votes. Some of the important features that can be implementedare:
1) Improved security measures: You could focus on developingadvancedsecuritymeasures,suchasencryption, biometricauthentication,andothertechnologies,toprotect againstcybersecurityattacksandensuretheintegrityofthe votingprocess.
2)Enhancedaccessibility:Youcoulddesignyourapptobe moreaccessibleforpeoplewithdisabilities,forexampleby offering features such as text-to-speech or visual aids for peoplewithvisionimpairments.
3)Improvedconvenience:Youcouldofferfeaturessuchas automaticballotscanningortheabilitytocastvotesfrom multiple devices to make the voting process more convenientforusers.
4)Integrationwithothersystems:Youcouldintegrateyour appwithothersystems,suchasvoterregistrationdatabases orcandidateinformationportals,toprovideamoreseamless andconvenientvotingexperience.
5) Additional language support: You could translate your app into multiple languages to make it more accessible to non-Englishspeakers.
6) Verification and auditability: You could incorporate features such as voter verification and ballot tracking to enhance the transparency and auditability of the voting process.
7)Improveduserinterface:Youcouldfocusondesigninga moreuser-friendlyinterfacetomakeiteasierforpeopleto navigateanduseyourapp.
8) Advanced analytics: You could equip your app with advancedanalyticscapabilitiestohelpelectoralauthorities betterunderstandvoterbehaviorandpreferences.
It'salsoimportanttoconductmarketresearchtounderstand theneedsandpreferencesofpotentialusers,aswellasto identifyanygapsinthecurrentofferingsthatyourappcould fill.
5. CONCLUSION:
DigitalisationandBlockchaintogetherinasingleframework isfoundanefficientwaytomaintainanonymity,integrity, privacy,andbasicfundamentalrightsofanyuserorcitizen ofanynationwhilecarryingouttheprocessofvotingwhich isgenerallycompromisedincurrenttraditionalmethodsof ballots and EVMs. By using different configuration techniqueslikeincludingAAdharIdandfingerprintsensors whilecastingvotes,itensuresauthenticityandintegrity.The status of votes on one's own system ensures privacy and reliability to be a productive and responsible citizen. An online voting system would lower the cost of elections conductedonpaperandboostvoterturnout.Byusingthis technology,additionalvotescanbecast,andtheresultsof those votes are accurately, permanently, securely, and publiclyrecorded.
REFERENCES:
[1]Himanshu Agarwal and G.N. Pandey “Online Voting System for India Based on AADHAAR ID” 2013 Eleventh International Conference on ICT and Knowledge Engineering

[2]SmitaB.Khaimar,P.SanyasiNaidu,ReenaKharat“Secure AuthenticationforOnlineVotingSystem”
[3]Shivendra Katiyar, Kullai Reddy Meka, Ferdous A. Barbhuiya,SukumarNandi“OnlineVotingSystemPowered By Biometric Security” 2011 Second International Conference on Emerging Applications of Information Technology
[4] F. Hai, M. N. Kreeger, B. Randell, D. Clarke, S. F. Shahandashti,andP.H.-J.Lee.Everyvotecounts:Ensuring integrityinlarge-scaleelectronicvoting.USENIXJournalof ElectionTechnology&Systems,2(3):1-25,2014.
[5] Feng Hai and Peter Y A Ryan (Ends).Real-world ElectronicVoting:Design,AnalysisandDeployment,Series inSecurity,PrivacyandTrust.CRCPress,2016.
[6]DivyaGNair,Binu.V.P,G.SanthoshKumar,”AnImproved E-votingschemeusingSecretSharing basedSecureMultiparty Computation”, arXiv: 1502.07469v1 [cs.CR] 26 Feb 2015
[7] Roberts, C. Biometric attack vectors and defences. Comput. Secur. 2007, 26, 14–25. [Google Scholar] [CrossRef][Green Version]
[8]Páez,R.;Pérez,M.;Ramírez,G.;Montes,J.;Bouvarel,L.An Architecture for Biometric Electronic Identification Document System Based on Blockchain. Future Internet 2020, 12,10.[Google Scholar][CrossRef][GreenVersion]
[9] Nimje, R.; Bhalerao, D. Blockchain Based Electronic Voting System Using Biometric. In Proceedings of the International Conference on Sustainable Communication NetworksandApplication,Erode,India,30–31July2019;pp. 746–754.[Google Scholar]
[10] Pawade, D.; Sakhapara, A.; Badgujar, A.; Adepu, D.; Andrade,M.SecureOnlineVotingSystemUsingBiometric and Blockchain. In Data Management, Analytics and Innovation;Springer:Berlin/Heidelberg,Germany,2020;pp. 93–110.[Google Scholar]
[11]Odelu,V.IMBUA:IdentityManagementonBlockchain forBiometrics-BasedUserAuthentication.InProceedingsof theInternationalCongressonBlockchainandApplications, Ávila,Spain,26–28June2019;pp.1–10.[Google Scholar]
[12] Makhdoom, I.; Abolhasan, M.; Abbas, H.; Ni, W. Blockchain’s adoption in IoT: The challenges, and a way forward. J. Netw. Comput. Appl. 2019, 125,251–279.[Google Scholar][CrossRef]
[13] Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; 2008; Available online: https://bitcoin.org/bitcoin.pdf (accessedon1June2020).
[14] Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where is current research on blockchain technology? A systematicreview. PLoS ONE 2016, 11,e0163477.[Google Scholar][CrossRef][PubMed]
[15] Multichain (2017) Open platform for Blockchain applications. Available at: www.multichain.com last accessed:December2017.
[16] McCorry, P., Shahandashti, S. F. and Hao. F. (2017) A smartcontractforboardroomvotingwithmaximumvoter privacyintheproceedingsofFC2017.
[17]Kraft,D.(2015)DifficultyControlforBlockchainBased Consensus System, Peer-to-Peer Networking and ApplicationsbySpringer,March2015
[18]Kadam,M.,Jha,P. Jaiswal,S.(2015)DoubleSpending Prevention in Bitcoins Network, International Journal of ComputerEngineeringandApplications,August2015
[19] Rosenfeld. M. (2017). Analysis of hashrate-based double-spending.[Online].
[20] Umut Can Çabuk1, Eylül Adıgüzel2, Enis Karaarslan2 (2018);ASurveyonFeasibilityandSuitabilityofBlockchain TechniquesfortheE-VotingSystems;InternationalJournal of Advanced Research in Computer and Communication Engineering.[Online].
[21] Aayushi Gupta1, Jyotirmay Patel2, Mansi Gupta1, Harshit Gupta1 (2017); Issues and Effectiveness of Blockchain Technology on Digital Voting; International Journal of Engineering and Manufacturing Science. ISSN 2249-3115Vol.7,No.1(2017).[Online].
[22]PavelTarasovandHiteshTewari(2017);theFutureof E-Voting;IADISInternationalJournalonComputerScience and Information Systems Vol.12, No. 2, pp. 148- 165 I. [Online].

