International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
Sandeepkumar Chauhan1 , Sanjeev Kumar Mandal2 , Santanu Jha3, Prashant Koparde4
1,2,3Students, Department of Computer Science & Engineering, T John Institute of Technology, Bengaluru, India 4Asst. Professor, Department of Computer Science & Engineering, T John Institute of Technology, Bengaluru, India ***
Abstract - Voting is a complex process with a lot depending on it. Building an e-voting system that can guarantee anonymity, verifiability, and transparency together is a challenging task. Continuous efforts are being made to improve the voting system to achieve these properties. Recently, blockchain has hit the technology space with many promises, especially to make verifiable and transparent decentralizedsystems.However,amajorchallengefacedwith blockchain-based e-voting systems is to achieve the users’ anonymity while ensuring only authorized voters should be able to vote, and that too only once. To address these issues, this paper proposes a blockchain-based e-voting system with secret contracts. We have used Enigma (a secure multiparty computation platform) to design secret contracts. The proposed system meets most of the features required to conduct free and fair voting electronically.
Key Words: Online Voting System Using Blockchain technology, Decentralized Voting System, Blockchain Technology Based Project, A Secured Balloting Voting System Using Blockchain Technology.
Indiaisademocraticcountryandhasademocratic country. As now all Indian citizen become a part of the growingdigitalIndiawithadigitalIDthatisAadhaarcard Votingschemeshaveevolvedfromcountinghandsinearly days to systems that include paper, punch card and electronicvotingmachine.
Theideabehindane-votingsystembasedonblockchainis similartodigitalwallets.Thesystemorauthoritycanissuea digitalwallettoeachparticipantafterverifyingitsidentity. The wallet issued mustcontaintheuser credentialsand a singlecoinrepresentingasinglechancetovoteWhenauser selectsacandidateandcastsitsvote,thecoinintheuser’s walletistransferredtocandidate’saccountorwallet.Atthe end the number of coins in each candidate’s wallet representsthenumberofvotescasttohim.Electronicand onlinevotingsystemcanprovidemoresecurityandintegrity than EVM. It also provides privacy to the users; as the eligiblevoterscancasttheirvotesusingtheircomputersor even smartphones, thus maintaining anonymity. It also buildstrustonthesystemasitisonlineandcompletelyan opensystem.Itcanalsoincreasethenumberofparticipants’ involvement.
Our motivation here is to provide a platform for peoplewheretheyareabletocompletelytrustthesystem, carry out the transactions and not be worried about miscounting of their votes, their choice and their decision remainsunalteredandthuscannotbemanipulatedinany way. The platform that we are going to provide can be accessedfromanydevicerunningtheblockchainnodesuch as computers, servers, embedded systems or even mobile devicesinthenearfuture.
Our aim is to design and develop a software platforms online voting system based on blockchain technology which helps to securely conduct votes and elections.Asa digital platform, they eliminatethe need to cast the votes using paper or having to gather in person. Theyalso protect the integrityof your vote bypreventing votersfrombeingabletovotemultipletimes.E-votinghas fundamental benefits over paper based systems such as increased efficiency and reduced errors. The electronic voting system tends to maximize user participation, by allowingthemtovotefromanywhereandfromanydevice that has an internet connection. The blockchain is an emerging, decentralized, and distributed technology with strongcryptographicfoundationsthatpromisestoimprove differentaspectsofmanyindustries.Expandinge-votinginto blockchaintechnologycouldbethesolutiontoalleviatethe presentconcernsine-voting.Hereweproposeablockchainbased voting system that will limit the voting fraud and makethevotingprocesssimple,secureandefficient.
Currentlyincreasingdigitaltechnologyhelpedmany people lives. In contrast to the electoral system, there are manyconventionalusesofpaperinitsimplementation.The aspect of security and transparency is a threat from still widespread election with the conventional system .Block chaintechnologyisoneofsolutions,becauseitembracesa decentralizedsystemandtheentiredatabaseareownedby manyusers.Thereisnodoubtthattherevolutionaryconcept oftheblockchain,whichistheunderlyingtechnologybehind the famous crypto currency Bit coin and its successors, is triggering the start of a new era in the Internet and the online services. In this work, we have implemented and testedasamplee-votingapplicationasasmartcontractfor
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
theEthereumnetworkusingtheEthereumwalletsandthe Solidity language. Block chain was first introduced by SatoshiNakamoto(apseudonym),whoproposedapeertopeerpaymentsystemthatallowscashtransactionsthrough the Internet without relying on trust or the need for a financialinstitution.Blockchainissecurebydesign,andan exampleofasystemwithahighbyzantinefailuretolerance. E-voting is a potential solution to the lack of interest in voting amongst the young tech savvy population. For evoting to become more open, transparent, and independentlyauditable,apotentialsolutionwouldbebase itonblockchaintechnology.Blockchaintechnologyhasalot ofpromise;however,initscurrentstateitmightnotreach itsfullpotential.Electronicvotinghasbeenusedinvarying forms since 1970s with fundamental benefits. over paper based systems such as increased efficiency and reduced errors. With the extraordinary growth in the use of block chaintechnologies,anumberofinitiativeshavebeenmade to explore the feasibility of using block chain to aid an effective solution to e-voting. It presented one such effort which leverages benefits of block chain such as cryptographicfoundationsandtransparencytoachievean effective solution to e-voting. The proposed approach has beenimplementedwithMultichainandin-depthevaluation of approach highlights its effectiveness with respect to achievingfundamentalrequirementsforane-votingscheme. Recent major technical challenges relating to e-voting systemsembrace,howevernot restrictedtosecuredigital identitymanagement.
Ethereum [3][6] is an open-source, blockchainbasedplatform thathelpsbuilddecentralizedapplications (Dapps).Itfeaturesscriptingfunctionalities.Thesescripting features-calledsmartcontracts[3]-arelogicthatoperates on the network of computers in the blockchain and is responsiblefortheinteractionofDappwithblockchainin theformoftransactions.Bydefinition,Blockchainisapublic ledger, so achieving data privacy using blockchain in its currentformisnotpossible.Dataprivacy,however,iscrucial foranyapplicationlookingtogainitsuser’strust,andhence the full potential of blockchain and, in extension, decentralizationcouldnotbeharnessed.Thatwasthecase untilGuyZyskind(nowCEOofENIGMA)introducedtheidea of the off-chain storage in [7] and then extended it to offchain computation in Enigma protocol [8] and quickly becamethefoundationstoneforallfurthertalkonthetopic ofdecentralizationand privacy.Enigmais a decentralized computation platform with guaranteed privacy. It aims to enable end-to-end decentralized applications to be built without any need for a trusted third party. In [7], tasks functions are divided into two types, off chain, handling privatedataandcomputations,andon-chainforconsensus (validation).
Enigma is designed to work over an existing blockchainbyaddinganoff-chainnetworkofmultiplenodes called secret nodes where private computations/storage on/of data is offloaded. Each node must have in-built support for TEE (Trusted Execution environments); otherwise,nodeswon’tbeallowedtobecomeapartofthe network. TEE technology (enigma relies on intel’s SGX) is secure hardware that decrypts sensitive data inside a definedprivateregionofmemorycalledenclavesandwhose contentsareprotectedandcannotbereadoraccessedby any program or entity outside the enclave, including processeswithhigherprivilegelevelsandeventheownerof the hardware. These TEE-compatible nodes, along with multi-partycomputation(MPC),helpinprivacypreserving computations.EnigmausesMPCasitscomputationmodel. Thresholdcryptosystemsarenormallyusedhere,withthe generalonebeingShamir’ssecretsharing.Secretsharingis whereasecretissharedamongnusers,andt+1isrequired toreconstructthesecret.Anysubsetoftandnothingcanbe learned about the secret. The Enigma network cryptographically guarantees privacy by encrypting data before it leaves the user’s premises. When any data input into the network, it is encrypted client-side. The data is decryptedinsidetheenclave,whichdoesnotrevealanything outside, preserving secrecy. Finally, results are encrypted too.Enigmaalsoextendsthefunctionalityofsmartcontracts byintroducingsecretcontracts.Thebiggestbenefitofthis wasthesecretstate,thatis,inputsandoutputs,butnowthe state can also be secretly maintained, and thus it is not accessible to network participants. This helps provide at least the same functionality as Ethereum smart contracts, probablymuchmore.Secretcontractsinenigmaarewritten inRustandcompiledintoWebAssembly(WASM)bytecode. Rust is an excellent programming language that simultaneouslyoptimizesforbothsafetyandperformance. Also,rustmakesiteasytousemachinelearningcomponents andperformothercomplexcalculationsincontracts.Secret contracts are interoperable with Ethereum, which means EthereumdeveloperscancontinuetobuildonEthereumand usetheEnigmanetwork forsecretcomputations.Asecret contractisbrokendownbyaninterpreter,wheretheparts dealing with private data are sent to the enigma network, and the parts dealing with public data are sent to the blockchain network. Enigma working can be explained as below: When a user enters a task to be computed by the enigma network, a randomly-selected node picks up the inputs and propagates the encrypted inputs to a group of secretnodesworkingonthatparticularsecretcontract.The selected secret nodes can decrypt the inputs inside their enclaves,computeonthedata,andreachasimpleconsensus on the result. Once this consensus is reached, the secret contract’sstateisupdated, andEthereumsmartcontracts may be called if required. The key management module ensures that a random secret node can compute an encryptedinputsentby the user.Thisis enabledbyusing
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
the Diffie Hellman scheme, where keys are exchanged betweentheuserclientandworkersinthenetwork.Along withtheabove,enigmaintroducesscalability.Inatraditional blockchain, every node executes the same code and maintains the same public state, causing quite a lot of redundancyandalsodelaywhenacceptinganewblockto the chain. However, in an enigma, the computation is efficiently distributedacrossthesubsetofsecretnodesthat computesandgivesbackresults.Asonlyasubsetofnodes takespartinaparticularcomputation,thenetworkismore scalable.
In [9], the Author proposed an improvisation on FOO voting scheme [10] using smart contracts and hyper ledgerfabric-basedblockchainnetwork byaddressingthe limitation or weakness in existing FOO voting system like thirdpartyinvolvementbeingreplacedwithsmartcontracts andothers.Theauthorsof[11]proposedablockchain-based framework where verification is done through a central party.Toguaranteeanonymitytothevoters,thesystemuses NIZKP for wallet generation, but there is no clear specificationofhowexactlyNIZKPwillbeintegrated.They also ask that the voters trust the third party for authentication/verificationandwalletgeneration,whichisa deal-breaker. In [12], the Author proposed a secure and reliable e voting system based on smart contracts and an Ethereum-based private blockchain network. This system enables all users to view the voting data, and there is no involvement of any third party. The proposed system maintains the required properties like voter’s anonymity, prevents re-voting, etc. In [13], the Authors proposed a secureend-to-endverifiableInternet-votingsystembased onanidentity-basedblindsignatureschemeusingcertain features bio-metric features and voter’s unique identification. However, the authors used elliptic curve discrete logarithm to achieve privacy of the proposed system.Thesystemenablesuserstoverifythevoter’scast vote,andeveneachvotercanverifythecountingprocessof recorded ballots correctly. The author showed that the proposed system takes the least machine cycles while comparing with some other works. In [4], the authors proposed an e-voting system based on blockchain as it is considered a robust consensus mechanism and provides immutability,transparency.Inadditiontothat, theAuthors incorporatedhomomorphicencryptionschemestoprotect theprivacyofthevoters.CastedVoteswillbestored onto the blockchain in the encrypted form by performing homomorphicencryptionsothatthereisnoneedtoperform decryptiontocountthevotes.Inadditiontotheproperties provided by the blockchain, the Authors designed a selftallying e-voting system in paper [14] where anyone can verifytheballot’svalidityandtallytheballotswithoutany central authorities and any third parties. It is achieved by generating and distributing the random numbers for the ballotsecurity.Theserandomnumbersallowcountingthe
ballots as these numbers will be cancelled out when multiplying all ballots. This scheme’s limitation is that all votershavetocasttheirvotes;otherwise,thesystemwould not work. In [15], the authors suggest using a private blockchain instead of a public blockchain. The private blockchainwouldthenhavetomaintainasizablenumberof peersinthesystemtoachievetransparency.Thesystemalso uses a Central authority for identity verification. In this paper,avoterwouldsendadigitalcommitmentofhisvote to the central authority along with his public key after applyingablindingfunction.Theyproposethattheblinding functionwillhideaperson’s.votefrompartiesinvolved.Still, theissuepersistsasacentralauthoritycanlinkaperson’s identitytohis/herpublickey.
The protocol is designed while keeping decentralizationinmindastheprimarygoal.Besidesthat, we give high consideration to maintaining the voters’ anonymity, votes even during the tallying phase, and verifiabilityofthetally.Earlierworksuseacentralauthority as a trusted third party to maintain the secrecy of voters’ identitieswhilstallowingonlyeligiblevoterstoparticipate. On the other hand, our proposal transfers this role of the centralauthoritytoasecretcontract sothatthesystemis more under the control of peers rather than one single organization. Before providing a high-level description of our proposed solution, we first describe some protocol terms.
A. Roles and Entities Wallet: Represents a digital wallet andisreferencedbyauniqueaddressontheblockchain.
Vote:Avoteisrepresentedbyatokeninthesystem.Avote castingtoacandidatetransfersthetokenfromthevoter’s wallettothecandidate’swallet.
Voter: Voter is a user who wants to cast a vote. Until and unless mentioned otherwise, a voter refers to an eligible voter only. Voters can be identified by the system in two ways. Using secret contracts, voters interact using encryptionofhisgovernment-issuedID,whereas,withsmart contracts, they can only interact using their blockchain addresses.
Election Authority: An authority which holds the responsibilityofdeployingcontracts,registeringcandidates, starting elections, and ending it. Every action of this authority is now under public scrutiny. Candidate: the contestantofelectionregisteredbyelectionauthority.They havealreadybeenvettedofflinebydueprocess.
We divide the process into four phases, each of which is detailedbelow
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
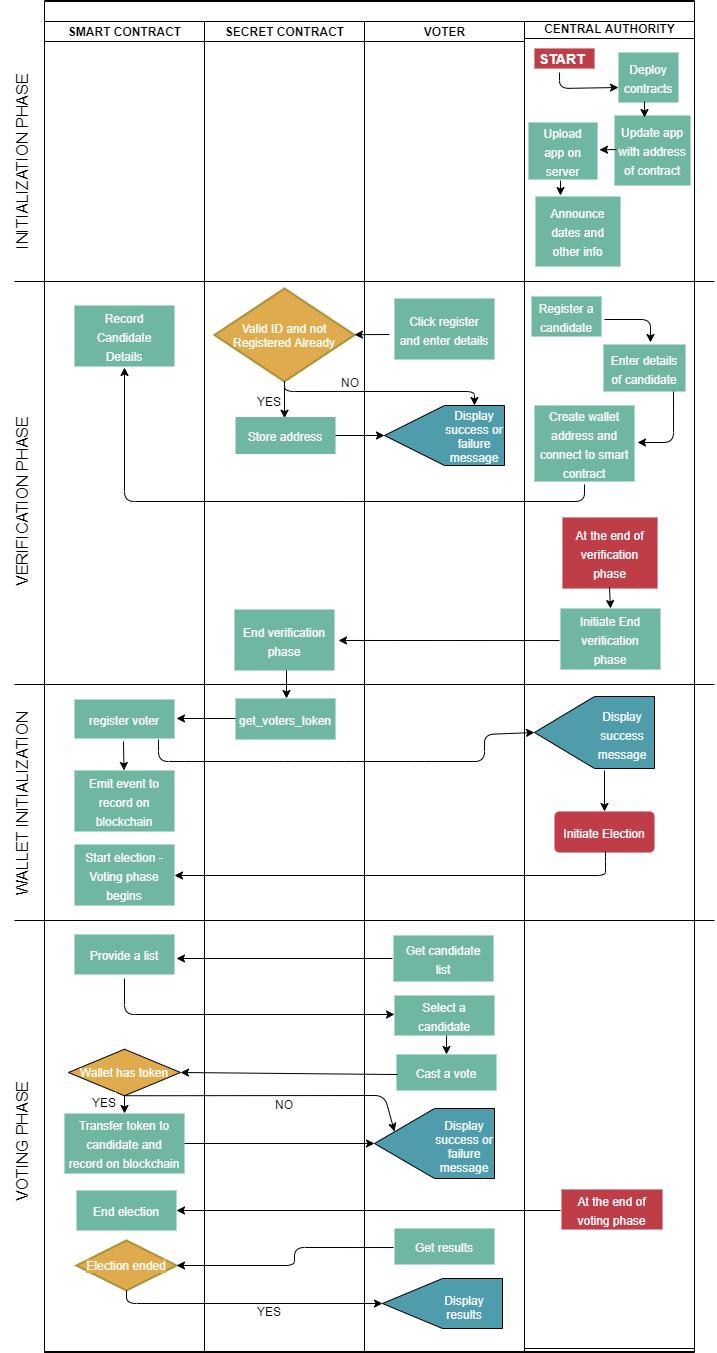
1) Initialization phase:Inthisphase,electionauthorities deploybothsmartcontractandsecretcontract,separately announceanelectionstartdateandenddate,andhost an updatedandroidapplication.Avotercaninteractwiththe system only through this updated application as this containshenewcontractaddresses.Secretcontractsarean enhanced version of smart contracts and are designed specificallyforprivacybecausetheydonotrevealtheinput datatheyinteractwith.Inthisphase,theelectionauthority alsouploadsalistofvalidcandidates’government-issuedID numbersalongwithappropriateverificationcredentials.We assume that the credentials have been shared with the votersbefore.Thislistisapartofthesecretcontractstate andisonlyaccessiblebysecretcontractnodeswithintheir enclaves.Thesecret
asmorepowerisaddedtosecretcontracts,amorerobust verificationprotocolcanbeintroduced.
Secret contractstores onlythe wallet addresses of voters, whichhavebeenverifiedtobeusedinthenextphase.These walletaddressesshouldbestoredinalistseparatefromthe governmentID’slist.Thusthereisnowaytoestablishalink betweenthetwo.Also,fromtimetotime,wecanrandomize thelisttomaintainsecrecy.
Thisphasehasone additional task.Theelection authority registersvalidcandidatesthroughasmartcontractthrough anappwemadeseparatelyforelectionauthority.Internally thismeanscreatinga walletaddresscorrespondingtothe candidateandstoringitcorrespondingtothecandidateIDin asmartcontract.
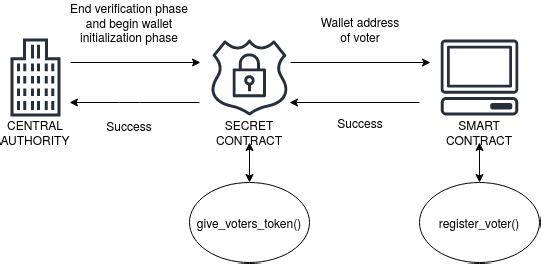
3) Wallet Initialization Phase: Thisphasebeginsafterthe previousphaseisoveraccordingtothetimelinesetbythe electionauthorities.Whentheelectionauthorityindicates the secret contract that the verification phase is over, as showninfigure2,ittriggersacalltothesmartcontract to passthelistofstoredwalletIDs.Thisfunctioncontactsthe smart contract’s“registerVoter”functionwithverified
contractsusethislisttoverifytheidentityofvotersduring theverificationphase.StoringIDsinasecretstatemakesthe secretcontractself-reliantasitdoesnotneedtocontactany other third party DB after this step. For scalability, we suggestaseparatesetofcontractsforeachdistrict,butwe intendtodiscussandoutlineoursystemwithrespecttoone district,andthesameprocess canbefollowedforanyother. We also assume that each voter has an Ethereum account neededtointeractwiththesystem.Ethereumaccountsare required only because we are basing this project on the Ethereum blockchain. If any other blockchainwasused, it accordinglycouldbeintegrated.
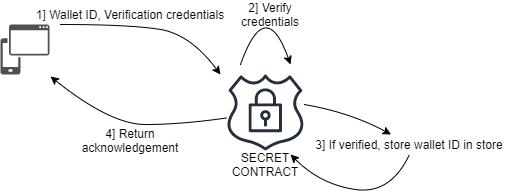
2) Verification Phase: This phase begins as soon as the initializationphaseisover.Inthisphase,weexpecteligible voters to download the app and register themselves. Internally the application flow is as follows: voters put a registration request through an app on their device using their ID numbers and verification credentials (maybe fingerprintorsomeothersecretquestionasnecessitatedby thesystem).Asshowninfigure1,arequestispassedtothe secretcontractwiththeaboveinformationandthevoter’s blockchain wallet address, which is to be created by the voter beforehand. The ID and other personal information helpsecretcontractsvalidatethevoterwhowillverifythe voter. For the time being, this verification is a simple matchingofIDnumbersinthesecretcontractenclaves,but
voters’addresses,whichwerestoredinthepreviousphase. Inthisfunctionofthesmartcontract,thewalletrepresented byeachaddresswillbecreditedwithonetoken.Eachtoken will represent onevotein oursystem. Wehave separated thisphasefromtheVerificationphasetoensureatimeline cannotbebuiltbetweenvoterregistrationandtransaction withthesmartcontract.
4) Voting Phase: Thisisthefinalphaseofthesystemandis performed on the Ethereum blockchain. The start of this phaseisindicatedbytheelectionauthoritycallingafunction “setstartelection”ofasmartcontractthroughtheirapp.
Oncetheelectionhasstarted,registeredvoterscanvoteby transactingtheirtokenstotheirchosencandidate’swallet. As per Ethereum flow, the transaction will generate a transactionIDthatthevoterscanusetoensurethattheir voteshavebeencorrectlycast.Thusprovidingverifiability.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
At the end of the voting cycle, each candidate’s wallet balancecanbechecked,andthecandidatewiththehighest tally wins. Results can be verified easily as all transaction detailsarestoredinthepublicblockchain.Applicationflow isasfollows:Eachvoterusinghiswalletwilltransactatoken toacandidate’swallet(theinterfacewillbehandledbyapp automatically).Thetransactionofatokenrepresentscasting ofavote.AvoterwillgetatransactionIDwhichcanbeused to verify that his vote has been correctly casted. After the votingphase,thecandidate’swalletbalance will showthe final tally. Tallyofall candidatescan now be compared to decideandsetthewinner.
Inthefollowing,weexplainhoweachrequiredpropertyis achievedbytheproposedprotocol.
1) Eligibility:Whiledeployingasecretcontract,theelection authority initializes it with a list of encrypted ID’s of only eligiblevoters.Sowhileexecutingasecretcontractwillnot verifyanypersonwhoseIDcouldnotbeverifiedwithalist.
2) No multiple voting fraud:Secretcontractmaintains a statevariablewhichstoresifanIDwaspreviouslyverified.If so, it means some address has already been stored corresponding to it. Thus only one address at max can be thereforoneID.Also,Whenthewalletinitializationphase beginssmartcontractensuresthatonlyonetokenisgranted to an address. Thus a voter can have only one token resulting in him only being able to vote once. Also, blockchainitselfmakessure thatdoublespendinghasnot beendone.
3) Anonymous voting:Asstatesofthesecretcontractare privateandalsoincomingandoutgoingdataisencrypted. Thisperfectlyhelpsusachievenoidentifiablelinkbetweena personandhiswalletandthuswithhisvote.
4) Verification: Smart contracts store a state of which address voted to which candidate using that a voter can easily verify his vote. The voter has a transaction number storedbyaneventontheblockchain,whichcanbequeried togetdata fromtheblockchainandverify.Also,following thetrailoftransactionsfromthetimesincethevotingphase began,onecaneasilyverifythetallyindependentlyonhis own. Also, the design of the blockchain itself makes the systemtamper-proof.
5) Decentralization: Blockchain being the center of the whole application clearly achieves decentralization to the system.
6) Consensus: The final result is the consensus of all the voters.
The system activity diagram, which shows the interactionamongphasesmentionedintheprevioussection, canbeseeninfigure3.WeareusingaRopstonEthereum,a testnetversion ofEthereum-basedblockchain.It provides thesameenvironmentasthemainnetofblockchain;onlyit doesnotcostmoney.Itisapublicblockchain,anditusesthe ProofofWork(PoW)Algorithm.Accesstothistestnetcanbe achievedthroughRemixonlineIDE,whichisusedtocreate, compile,deploy,andinteractwithsmartcontracts.Itneedsa wallet like meta mask to support transactions with smart contracts.WehavetestedoursmartcontractusingthisIDE withtheRopstenTestnetandtestether.Thesecretcontract ideaistosetupalocalenigmanetworkwhichcomeswithits ownlocalblockchain.Asecretcontractwritteninrustanda smartcontractaredeployedonthisnetwork,andandroid applicationsareusedtointeractwith thesecontracts.The secret contract is intended to perform the following functions
•RegisteraVoter-Verifyuniquenessandidentityofavoter. • Start wallet initialization when the end of this phase is marked.
Procedureverifyidusinglist(encryptedIDproofs) Result:Trueifvalidelsefalse returnlist[encryptedIDproofs] Procedureregisteravoter(walletaddress, encryptedIDproofs) require(verificationphaseend==false) res=verifyidusinglist();//thiscanbereplacedbya moresophisticatedlater ifres==truethen addaddresstoeligiblevoterslist; else ; end
Algorithm2:WalletInitalization
Proceduregivevoterstoken() require(verificationphaseend==true) foraddressineligiblevoterlist registervoter(address,1);//registervoterisa smart contractfunction Procedureendverificationphase() require(msg.sender==owner) require(verificationphaseend==false) verificationphaseend==true givevoterstoken();
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
Also the Smart contract provides the following functionality to support different phases of the election process.
•RegisteraCandidate(Thecalltothiscanonlygothrough ownerofcontract)
• Transfer of token to voter (The call to this can only go throughsecretcontract)
• Start election (only owner of contract - election commissioninthiscase-cancallthis)
• Vote Casting (As a transfer of token to a registered candidateonly)
•Endelection(onlyownerofcontract–electioncommission inthiscase-cancallthis)
•ShowresultsandverifyVote
Algorithm 3, 4, and 5 provide pseudo-code for Candidate registration, token transfer to voter and vote casting respectively.
ProcedureRegistercandidate(address,name); require(msg.sender==owner) foraddressineligiblevoterlist require(electionstart=falseandelectionend=false) addcandidatedetailstostatevariableandalsoset correspondingbalance=0//balancedictates votecount
Procedureregistervoter(address,tokens); require(msg.sender==secretcontract) require(electionstart=falseandelectionend=false) require(tokens==1)
balance[owner]=balance[owner]-1 balance[address]=balance[address]+1 emittransferevent//torecorddataonblockchain
Procedurecastavote(name,addressofcandidate, tokens); require(electionstart=trueandelectionend=false) require(tokens==1)
balance[msg.sender]=balance[msg.sender]–1 balance[addressofcandidate]=balance[address]+1 emittransferevent//torecorddataonblockchain
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 10 Issue: 01 | Jan 2023 www.irjet.net p-ISSN: 2395-0072
Two applications have been created. One provides a user interface for election commission and another one for Voters.
•Electioncommissioncanregisteracandidate,startorend anelection,andstartthewalletinitializationphase.
•Votergetstoperformfollowingfunction: –Registerwiththesecretcontracttogetatoken.
–Checkregisteredcandidates.
–Casttheirvote.
–Checkandverifyresults.
To integrate smart contract with android web3j library is usedtofirstcreatewrapperjavaclassesforsmartcontract and then functions of this class are called to interact with blockchain.Alsoinfuraisusedtoactasethereumclient.Itis a cloud based service that provides access to blockchain servicesfordeviceswhichcannotruntheirownnodes.
This paper introduces a blockchain-based frameworkandprotocoltoperforme-Votinginadistributed manner.Alongwiththeblockchain,theproposedframework usessecretcontractstoaddresstheproblemsofmaintaining voteranonymityandtheconfidentialityofthevotecastby him. The proposed framework uses a secure multiparty computationplatformEngimatodesignsecretcontracts.The protocol also focuses on decentralizing verification in a securemanner,whichmeansthatthecentralauthoritycan nottraceavotebacktothevoterevenifwantedto.Protocol analysis shows that the proposed framework and the protocolachievemostoftherequirementstoconductfree andfairelections.
Wethank,Dr.ThomasPJohn(Chairman),Dr.Suresh VenugopalP(Principal),DrSrinivasaHP(Vice-principal), Ms.SumaR(HOD–CSEDepartment),Dr.JohnTMesiaDhas (AssociateProfessor &ProjectCoordinator), Mr Prashant Koparde.(AssistantProfessor&ProjectGuide),Teaching& Non-Teaching Staffs of T. John Institute of Technology, Bengaluru–560083.
[1] Y. Abuidris, R. Kumar, and W. Wenyong, “A survey of blockchainbasedone-votingsystems,”inProceedingsofthe 2019 2nd International Conference on Blockchain TechnologyandApplications,pp.99–104,2019.
[2] K. M. Khan, J. Arshad, and M. M. Khan, “Investigating performance constraints for blockchain based secure evotingsystem,”FutureGenerationComputerSystems,vol. 105,pp.13–26,2020.
[3] B. Singhal, G. Dhameja, and P. S. Panda, Beginning Blockchain: A Beginner’s Guide to Building Blockchain Solutions.Springer,2018.
[4] G. M. C. Sravani, “Secure electronic voting using blockchain and homomorphic encryption,” International JournalofRecentTechnologyandEngineering(IJRTE),vol.8, 2019.
[5] “Enigma Protocol Overview.” https://enigma.co/protocol.Accessed:2020-6-5.
[6]V.Buterinetal.,“Anext-generationsmartcontractand decentralizedapplicationplatform,”whitepaper,vol.3,no. 37,2014.
[7] G. Zyskind, O. Nathan, et al., “Decentralizing privacy: Using blockchain to protect personal data,” in 2015 IEEE SecurityandPrivacyWorkshops,pp.180–184,IEEE,2015.
[8] G. Zyskind, O. Nathan, and A. Pentland, “Enigma: Decentralized computation platform with guaranteed privacy,”arXivpreprintarXiv:1506.03471,2015.
[9]Y.Zhou,Y.Liu,C.Jiang,andS.Wang,“Animprovedfoo voting scheme using blockchain,” International Journal of InformationSecurity,vol.19,no.3,pp.303–310,2020.
[10]A.Fujioka,T.Okamoto,andK.Ohta,“Apracticalsecret voting scheme for large scale elections,” in International WorkshopontheTheoryandApplicationofCryptographic Techniques,pp.244–251,Springer,1992.
[11]F..Hj´almarsson,G.K.Hreiarsson,M.Hamdaqa,andG. Hj´almt`ysson,“Blockchain-basede-votingsystem,”in2018 IEEE 11th International Conference on Cloud Computing (CLOUD),pp.983–986,IEEE,2018.
[12]H.-D.Park,“Adecentralizede-votingsystembasedon blockchain network,” International Journal of Innovative TechnologyandExploringEngineering(IJITEE),vol.8,2019. [13]M.Kumar,S.Chand,andC.P.Katti,“Asecureend-to-end verifiableinternet-votingsystemusingidentity-basedblind signature,” IEEE Systems Journal, vol. 14, no. 2, pp. 2032–2041,2020.
[14]G.Zeng,M.He,andS.M.Yiu,“Asecureandself-tallying e-voting system based on blockchain,” in International WorkshoponInformationSecurityApplications,pp.67–76, Springer,2019.
[15] F. S. Hardwick, A. Gioulis, R. N. Akram, and K. Markantonakis, “Evoting with blockchain: An e-voting protocolwithdecentralisationandvoterprivacy,”in2018 IEEE International Conference on Internet of Things (iThings)andIEEEGreenComputingandCommunications (GreenCom)andIEEECyber,PhysicalandSocialComputing (CPSCom)andIEEESmartData(SmartData),pp.1561–1567, IEEE,2018.