
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

Volume:12Issue:04| Apr 2025 www.irjet.net



International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

Volume:12Issue:04| Apr 2025 www.irjet.net

Pavani1 , K. Rishitha2 , G. Navaneetha3 , Dr. D. Sreenivasulu4
1B-Tech 4th year, Dept. CSE(DS), Institute of Aeronautical Engineering
2B-Tech 4th year, Dept. CSE(DS), Institute of Aeronautical Engineering
3B-Tech 4th year, Dept. CSE(DS), Institute of Aeronautical Engineering
4Associate Professor, Dept. CSE(DS), Institute of Aeronautical Engineering, Telangana, India
Abstract – In the modern world, information protection and maintenance are vital, and they should receive a lot of attention due to the rapid development of Information and Communication Technologies and the vulnerabilities endangering human societies. The Secure Hashed Identity Message Authentication (SHIMA) generates fixed length outputs, leadingto potential collisions where distinct messages produces the same hash value, compromising integrity. To resolve these issues, we propose a HMAC (Hash-based Message Authentication Code) in network security which helps to verify the authenticity and integrity of data or a message transmitted between two parties. In cryptography usingHashBased Message Authentication Code (HMAC), we can ensure the authenticity of a message. The entitled HMAC which enhance and improve the cryptographic characteristics of SHIMA. The improved algorithm offers a greater resistance to birthday attacks.
Key Words: Cryptography, Hash Based Message AuthenticationCode (HMAC), Network Security, Message Integrity, Authentication, Secure Communication
Inthemoderndigitalage,theintegrityandauthenticityof datatransmittedovernetworkareparamount.Asdataflows across various nodes in a network, it is susceptible to interception,alteration,andunauthorizedaccess.Ensuring thesecurity ofthis data isa critical challengefor network administratorsandcybersecurityprofessionals.Oneofthe robustsolutionstothischallengeistousetheHash-Based MessageAuthenticationCode(HMAC). ApopularcryptographicmethodcalledHash-BasedMessage AuthenticationCode(HMAC)isusedtoconfirmamessage’s authenticity and data integrity. This is accomplished by mixingthemessagecontentswithasecretcryptographickey, whichissubsequentlyprocessedusingacryptographichash function. The output that is produced, called the message authenticationcode(MAC),isspecifictothekeyandmessage,

thusanychangesmadetothedatawillresultinadifferent MAC.
The primary purpose of HMAC in network security is to provide a means for verifying that data has not been tamperedduringtransmissionandthatitoriginatesfroma trustedsource.Thisiscrucialinpreventingvarioustypesof cyberattacks.
HMAC is employed in numerous network protocols to securedatatransmission. Forinstance,inSSL/TLS,which underpinssecurewebcommunications,HMACensuresthe authenticityandintegrityofdataexchangedbetweenweb browsersandservers.Similarly,inIPsec,HMACisusedto secureinternetprotocolcommunicationsbyverifyingthat thedatapacketshavenotbeentamperedwithandthatthey comefromalegitimatesource.SSH,usedforsecureremote logins,alsoreliesonHMACtoprotecttheauthenticityand integrityofthetransmitteddata.
InsideAscybersecuritythreatscontinuetoevolve,sotoo mustthemechanismsdesignedtocounter them. Recent advancements in HMAC and cryptographic security aim toenhancetherobustness, efficiency,andadaptability of these techniques in the face of emerging challenges. Enhancing the security, effectiveness, and suitability of thesealgorithmstocounternewthreatsincontemporary network environments has been the main goal of developmentsinhash-basedmessageauthenticationcode (HMAC)andcryptographicsecurity.
Enhanced Key Management: Good key management is essential to HMAC security. Modern key management techniques, like secure key distribution systems and automated key rotation, reduce the possibility of key compromise. Additionallayersofsecurityforcryptographic keys are offered by methods like secure enclaves and


Volume:12Issue:04| Apr 2025 www.irjet.net
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

hardware security modules. Hardware Security Modules (HSMs) offer scalable solutions for enterprise use and tamper-proofkeystorageenvironments.Secure,centralized key handling in cloud environments is made possible by cloud-based key management services (KMS), whereas hybridsolutionshandlekeysacrosson-premisesandcloud infrastructures. Incomplicatedsystems,interoperabilityis guaranteedbystandardizedprotocolssuch asKMIP.
Integration with Emerging Technologies: Integration withEmergingTechnologies:HMACintegrationiscrucial forpreservingsecurityinsystemsthatusenewprotocols andtechnologies. Forinstance,theextensivenetworkof connected devices can safely transmit and authenticate datathankstotheuseofHMACinInternetofThings(IoT) devicesandprotocols.HMACensuresdataauthenticityin resource-constrained contexts by securing device communicationsintheInternetofThings.Itstrengthens ledger integrity by securing node interactions and authenticating transactions on blockchain. HMAC safeguards data both in transit and at rest, which is essentialformulti-tenantdesignsincloudcomputing.

Hash Based Message Authentication Code (HMAC) a cryptographictechniqueisusedtoconfirmtheauthenticity and integrity of data. It prevents unauthorized alterations and message manipulation by combining a cryptographic hash function with a secret key. In order to handle changing security issues, research is also concentrated on hybrid models and lightweight IoT implementations. [1] Inan effort toaddress the issues,


we suggest Secure Hashed Identity Message Authentication, which helps to confirm the message's authenticityandintegrity.Re-encryptionduetonetwork security is predicted to be quite expensive. The SHIMA techniquedecreasesend-usercontroloverthedevice'sendto-endencryptionanddecryption.Studiesonsecurityand performance have been finished, and the findings indicate that our approach is more effective and efficient, lasts longer, and lowers latency. [3] Ad hoc networks are wireless networks which doesn’t have permanent infrastructure that are typically put together sometimes to carry out certain tasks like combat communications or emergency rescue. [8] The general purposeofattackinMANETsistofailthefirsttimetosend packetsortomodifymessagesthatdonotmatch,causing nodes to pass the wrong packets, thus depleting them. > Nodethebattery.[11]ItdoesthisbyusingtheStatistical Uniqueness and Cryptographic Verifiability (SUCV) property of some entities; this information refers to the SUCV identifier and address or the Encrypted code. Its propertiesallowthemtopreventcertaintypesofdenialof serviceattacksandhijackingattacks.Sexproblemfinding Optimization (CSA) algorithm. Among them, data encryption and key symbols are made using the RSA encryptionsystemtoprotectdatafromunauthorizedusers. TheCSAalgorithmhelpsinoptimizingtheencryptionkeyto avoid brute force attacks.[17] The algorithm uses a lightweight implicit certificate and combines public and private keys to create temporary session keys, thus encrypting and protecting data transfer and solving the problemofsecuritydatatransfer.cooperatingnodeswhen entering. The solution is not easy, but the key finding solution both has more indexing overhead and has disadvantages.
Hash-based Message Authentication Code is a popular cryptographicalgorithmthatmakessuredataislegitimate andintactwhilebeingtransferredacrossnetworks.Ithasto dowiththeuseofahashfunctionincryptographycombined withasecretkeytoproduceanauthenticationmessage.This approachenhancessecuritybyensuringthateachHMACis uniqueto itsspecificcontext,makingitsignificantlymore resistant to replay and prediction attacks. The dynamic elements introduce variability, so even if an attacker intercepts multiple HMAC values, they cannot easily anticipate future ones. HMAC is widely used in secure communication protocols like TLS and IPsec, as well as in APIauthentication,duetoitsflexibilitywithdifferent hash


Volume:12Issue:04| Apr 2025 www.irjet.net
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

functions, efficiency, and well- understood security properties.However,effectivekeymanagement iscrucialto maintainingitssecurity.
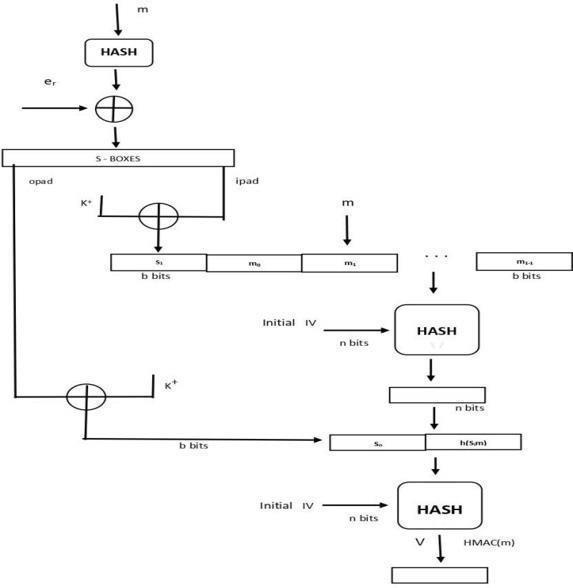
Fig-2:FlowchartofProposedTechnique
A.Input:
AcryptographichashfunctionHHH.
AsecretkeyKKK. ThemessageMMMtobeauthenticated.
B. Keylength adjustments:
Ifthekeylengthisgreaterthantheblocksize(B): Hashthekeyusingthehashfunctiontoreduceitslengthto thehashfunction'soutputlength(L).
Ifthekeylengthislessthantheblocksize(B):Padthekey withzerostomakeitequaltotheblocksize.
C. Preparation:
Twofixed-sizepadsaredefined:
Innerpad(ipad): Astringoftheblocksize,eachbyteisthe XORofthekeybyteandthebyte0x36.
Outer pad (opad): Astringoftheblocksize,eachbyteis theXORofthekeybyteandthebyte0x5c.
D. Paddingthekey:
Inner Padding (K_ipad): XOR the adjusted key with the innerpadconstant(0x36repeatedBtimes).
Outer Padding (K_opad): XORtheadjustedkeywiththe outerpadconstant(0x5crepeatedBtimes).
E. Computingtheinnerhash:


Concatenate the original message (M) with K_ipad. To generatetheinnerhashvalue,hashtheconcatenatedvalue usingtheselectedhashfunction
F. Computingtheouterhash:
Concatenate the inner hash value with K_opad. The final HMACvalueisobtainedbyhashingtheconcatenatedvalue usingthehashalgorithm.
G. Output:
The result is the HMAC value, which offers authenticity anddataintegrity.
4.1
ExtensivesecurityanalyseshavebeenconductedonHMAC since its introduction. Bellare, Canetti, and Krawczyk's originalworkprovidedfoundationalproofsthatestablished HMAC'sresistancetocollisionattacksandlengthextension attacks.Subsequentresearchhasreinforcedthesefindings, showingthatHMACmaintainsitssecuritypropertieswhen usedwithvarioushashfunctions.However,duetoknown vulnerabilities in MD5 and SHA-1, SHA-256 and other membersoftheSHA-2andSHA-3familiesarepreferredfor modernapplications
4.2Performance Considerations
TheperformanceofHMAChasbeenasubjectofsignificant research, particularly in the context of its efficiency in differentenvironments.Krawczyk'swork,alongwithother studies,hasshownthatHMACiscomputationallyefficient and suitable for both software and hardware implementations. Performance tests in contexts with limited resources, such Internet of Things (IoT) devices, show that even while HMAC adds some computing overhead, it is still practical for secure communication. Utilizingparallelprocessingcapabilitiesandothermethods to improve speed, research has been concentrated on optimizingHMACforparticularhardwarearchitectures. Withstrongsecurityfeaturesthatovercomethedrawbacks of basic hash-based message authentication methods, HMAChasmadeanameforitselfasakeytoolinthefieldof cryptography. It is a commonly used solution in many security protocolsandapplicationsdue toitstheoretical soundness, demonstrated security, and practical effectiveness. HMAC’sperformanceandapplicabilityare being improved by ongoing research, guaranteeing its relevance in the rapidly changing field of cryptographic security. HMAC’s resilience and adaptability will remain crucialcomponentsofitsongoingimportanceasnewthreat materializeandcomputationalcapabilitiesdevelop.


Volume:12Issue:04| Apr 2025 www.irjet.net
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

:TransmissionofMessage
TheresultofimplementingthedynamicHMACalgorithmis ahighlysecureandcontext-specificmessageauthentication code that ensures the integrity and authenticity of transmitteddata.Byincorporatingdynamicelementssuch as timestamps, or session- specific data, each generated HMAC is unique and resistant to replay attacks and prediction. This results in robust protection against unauthorized alterations and ensures that the sender's identity can be reliably verified. HMAC significantly strengthens the security of communication protocols, providing a reliable method for safeguarding sensitive information in different applications, including financial transactions,communications,anddatatransferprocesses.
5.1 Time Complexity
By implementing HMAC encryption technology on the network, additional data possibilities are created. The suggestedmethod’scomplexityisdecreasedbycomparingit toearlierapproaches.
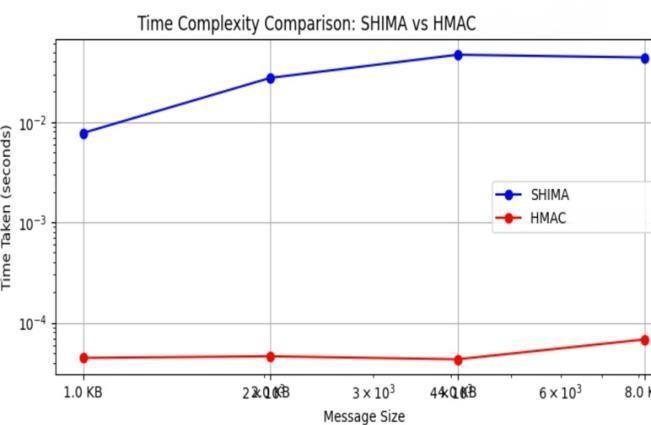
Chart-1:TimeComplexityofSHIMAvsHMAC


Inthebelowgraphx-axisrepresentsproposedandexisting algorithmnamesandy-axisrepresents‘StorageCost’and in these both techniques HMAC got less storage when comparedtoSHIMAalgorithm.
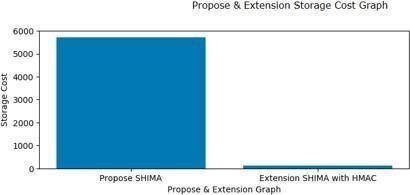
Chart-2:StoragecostofSHIMAvsHMAC
Inconclusion,HMACrepresentsasignificantadvancementin cryptographicsecuritybyintegratingchangingelementslike timestamps or session-specific data into the HMAC generationprocess.ThisintegrationensureseachHMACis unique to its context, providing strong protection against replay and prediction attacks. The enhanced security of HMAC makes it particularly suitable for safeguarding sensitivedata,securingfinancialtransactions,andensuring theintegrityandauthenticityofcommunicationsinvarious high-security applications. By adapting to the dynamic aspectsofitsenvironment,HMACoffersarobustandreliable methodformaintainingdataintegrityandauthenticationin anincreasinglycomplexdigitallandscape.
[1] Sakshi Pandey, Saurabh Lahoti, ”Cryptography based NetworkSecurityAnalysisusingSecureHashedIdentity MessageAuthentication“,April2023.
[2] Y. Zhang, W. Lee, and Y. Huang, ―Intrusion Detection Techniques for Mobile Wireless Networksǁ, ACM WirelessNetworksJournal(ACMWINET),Vol.9,No.5, September2003.
[3] S.Al-OtaibiS,F.Siewe,“SecureRoutingProtocolBaseon Secure Path in Ad hoc Wireless Networks”, IEEE InternationalForumonComputerScience-Technology andApplicationsIFCSTA2009.


Volume:12Issue:04| Apr 2025 www.irjet.net
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 p-ISSN: 2395-0072

[4] S. Al-Otaibi, F. environments based on the history of nodes in ad hoc networks”, IEEE the First Asian HimalayasInternationalConferenceonInternetAH-ICI 2009.Siewe,“Securityofaccessinhostile
[5] AliHilalMohamad,H.Zedan,A.Cau,―SecuritySolution for Mobile Ad Hoc Network of Networks (MANoN)ǁ, IEEEFifthInternationalConferenceofNetworkingand ServicesICNS2009.
[6] Esa Hyytiä and Jorma Virtamo, “Random waypoint model in n- dimensional space”, Operations Research Letters,vol.33/6,pp.567–571,2005.
[7] Haas Z. J., Pearlman M. R., and Samar P., “The Zone RoutingProtocol(ZRP)”,IETFInternetDraft,draft-ietfmanet-zone-zrp-04.txt,July2002.
[8] C. Siva Ram Murthy and B.S Manoj, “Ad Hoc Wireless Networks, Architecture and Protocols”, Prentice Hall PTR,2004.
[9] L.ZhouandZ.JHaas,“SecuringAdHocnetworks,”IEEE NetworkMagazine,vol.13,no.6,December1999.
[10] M.O.Pervaiz,M.Cardei,andJ.Wu,"RoutingSecurityin AdHocWirelessNetworks,"NetworkSecurity,S.Huang, D.MacCallum,andD.-Z.Du(eds.),Springer,2008.
[11] Gabriel Montenegro and Claude Castelluccia, “CryptoBasedIdentifiers(CBIDs):ConceptsandApplications’” ACMTransactionsonInformationandSystemSecurity, February2004.
[12] S Neelavathy Pari, Sbrish Jayapal and Sridharan Draisamy,“ATrustSecurityinMANETwithSecureKey AuthenticationMechanism”,ICRTIT–2012.
[13] X. Duan and X. Wang, ‘‘Authentication handover and privacyprotectionin5Ghetnetsusingsoftware-defined networking,’’IEEECommun.Mag vol.53,no.4,pp.28–35,Apr2015.
[14] S.R.Shree,A.C.Chelvan,andM.Rajesh,‘‘anefficientRSA cryptosystembyapplyingcuckoosearchoptimization algorithm,’’ Concurrency Computer, Pract. Exper., vol. 31,no.12,Jun2019.
[15] W.Jiajia,Y.Chuanwei,W.Lei,andS.Jiaqi,‘‘Researchon LTE decryption Method based on air interface,’’ Electron.ProductsWorld,vol.26,no.8,pp.40–42,2019.
[16] Liu,F.,Huo,W.,Han,Y.,Yang,S.,&Li,X.(2020).Studyon NetworkSecurityBasedonPCAandBPNeuralNetwork Under Green Communication. IEEE Access, 8, 53733–53749.


[17] Chen,B.,Wu,L.,Wang,H.,Zhou,L.,&He,D.(2019).A Block chain Based Searchable Public-Key Encryption withForwardandBackwardPrivacyforCloud-Assisted Vehicular Social Networks. IEEE Transactions on VehicularTechnology,1–1.
