






The evolution of women in security is an ongoing and relentless journey, one that continues to transform both the fabric and the future of the industry.
There is always more to strive for, more boundaries to shatter and countless new opportunities to create. Progress is not a journey to a fixed destination but a journey to a constantly moving frontier, shaped by those bold enough to push forward and redefine what is possible.
BOUNDARIES AND OPPORTUNITIES
As the landscape of security undergoes rapid change women are playing increasingly pivotal roles in overcoming old stereotypes and driving innovation. Their journey is marked by resilience amidst challenges such as networking gaps, work isolation, inflexible hours and pay inequality. Each challenge faced becomes a springboard for growth as women step confidently into leadership, policymaking and technical excellence roles across government, industry and academia.

I believe we are no longer just participants, but that we are architects, designing the next chapter of the industry. Building equitable, inclusive teams ensures that talent is sourced from a broad array of backgrounds and perspectives, unlocking new problem-solving approaches and fuelling creative collaboration. Programs like the Tangible Uplift and Secure-by-Design initiatives prove that, when equipped with the right skills and supported by champions, women can, and do, redefine all that security can achieve.
Industry leaders and executive voices increasingly recognise that empowering women is essential for navigating the complex threats posed by cyber risks and the shift to AI-driven defence. By proactively challenging the status quo and advocating for more diversity at every level these changemakers are building stronger, more adaptable organisations.


Flexible, innovative work cultures and focused mentorship empower more women to pursue and achieve leadership roles. A new generation of superwomen is arising, ready to tackle the cybersecurity challenges of the future.
Evolution is never complete. Each milestone becomes the foundation for further breakthroughs. Today’s pioneers become tomorrow’s mentors, advocates and visionaries. There remains a critical need to invite more women to the table; to amplify their voices and to actively nurture a culture in which every challenge is an opportunity.
So, let us be the architects, redefining all that is possible and inspiring perpetual innovation, inclusion and progress. The unstoppable evolution of women in security is proof not only of collective accomplishment but of the limitless potential when boundaries are pushed and opportunities created for all.
PUBLISHER, and CEO of Source2Create
www.linkedin.com/in/abigail-swabey-95145312
aby@source2create.com.au












































Imagine a world where every system, product and policy is built not to cater for women as an afterthought, but with women at the centre from the very beginning. In the world of security—physical and digital alike—this vision is overdue. More than a matter of inclusion, designing with women in mind is now essential for genuine safety, resilience and progress.
History is full of well-intentioned design oversights: crash test dummies based on the ‘average’ male form, uniforms that gape, PPE in sizes that don’t fit, safety apps that miss women’s daily realities, and algorithms that fail those outside default data sets. These design gaps are not just unfortunate, they are dangerous. When women are left out, everyone’s safety is compromised.
Redesigning with women in mind is not only a ‘nice-to-have’, it is the only path to fairness, smarter outcomes and a world where no one is left exposed. Recent industry statistics show women still account for less than a quarter of security professionals worldwide, but their impact is revolutionising how we manage risks and strengthen systems.
LAYING A NEW FOUNDATION: INCLUSION AT EVERY STEP
Truly inclusive security means moving beyond patching up the past and, instead, building for a future that works for all. The security industry, and every
sector it protects, must make a real commitment to design, develop and lead with the full range of women’s experiences and insights at the table.
WHAT WOULD THAT LOOK LIKE IN PRACTICE?
• Representation at every design table. Women from diverse cultural, social and neurodivergent backgrounds would drive conversations, create prototypes, probe risks and make final calls on the products and processes shaping our future.
• Technology and policy for the real world . Testing new tools and policies across actual, diverse scenarios would ensure solutions meet everyone’s needs, not just ‘majority reference cases’.
• Championing leadership . Women would belong on boards, intelligence teams, crisis cells and privacy and ethics panels as top decision-makers and visible mentors for those following.
• Elevating voices and stories . Sharing the journeys and expertise of women who have overcome barriers or who lead by example would fuel new thinking that no system or algorithm could replicate on its own.
Awards programs, professional forums and magazines dedicated to women in security are already amplifying change and challenging design blind spots. Every win for women-centred design shrinks long-standing gaps and unlocks collaborative potential that benefits all.
Genuine security exists only when everyone’s reality shapes the solution. Some of the most effective initiatives are those that crowdsource women’s lived safety data, design wearables for diverse bodies and bring ‘privacy by design’ thinking to caregiving and advocacy. ‘Inclusion’ should not be remedial work; it should be the starting line.
Equity should be embedded into AI, leadership and learning using technology and policy, and codesigned with women as experts and end-users.
When women’s insights set the agenda, solutions get sharper, smarter and more broadly effective. Women anticipate vulnerabilities others miss. Issues like workplace safety, harassment, accessibility and data bias—often overlooked—move to centre stage, and resilience is built in for all.
It’s time to move beyond box-ticking and see inclusion as the innovation driver it truly is. Redesigning the world with women in mind futureproofs security. It creates workplaces where every voice matters, and communities where everyone’s safety is protected, not only that of the ‘average’ person.
• Ask whose voices are missing from every project and decision.
• Sponsor emerging women leaders and create platforms for new stories.
• Invite tough feedback and keep widening the circle, from grassroots to boardroom.
Redesigning our world with women in mind is practical, bold and just. It’s about asking, “Does this work for every woman, not just for some?” and letting that question drive every new solution. When we lead, build and innovate with women as true partners, we don’t just close gaps, we craft possibilities for future generations.
Now is the moment to imagine and build a world secured by all, for all. Let’s make designing with women in mind the rule, not the exception. The future of security, and of society, depends on it.


Craig is an experienced cyber security professional with various qualifications including two master’s degrees. He is the Head Unicorn (co-founder and director) of Cyber Unicorns, in which he acts as a vCISO to clients such as Baidam Solutions, Wesley Mission, PCYC, Hungry Jacks and Ipswich City Council. He was CTO (Chief Technology Officer) for Baidam Solutions between January 2022 to June 2023, where he led the technical services team, helping to build out the internal services capability for Baidam. Craig was QLD chair for AISA for two years until he was appointed to the national board of directors in December 2022.

Evolution is a funny thing. Species slowly evolve and adapt to better suit their environment. Fish grow legs and develop lungs that enable them to breathe out of water. Monkeys learn to walk upright and lose all their hair to become the first humans, if you believe that’s how humans came to be. Alternatively you might believe we are descended from aliens who became marooned on this planet, or that God made us in his image.
I won’t argue your beliefs, whichever way you lean. So let’s just go with the Darwinian theory of evolution for this article. Creatures adapt. That’s the key point here; they change to survive and thrive.
Humans (all of us) have changed our environment, whether for the better or worse remains to be seen But, change it we have, through technology and science. We have moved beyond nature’s control
Craig is a published author with three different book series – ‘A Hacker I Am’ cyber education series, ‘Foresight’ is his Cyberpunk/hacker fantasy novel series and then there is ‘The Shadow World’, a co-authored kids cyber education book. He is a freelance cyber security journalist and is a regular columnist with the Women in Security Magazine, as well as a freelance contributor for Cyber Today, Top Cyber News, SecureGov, Careers with STEM and Cyber Australia magazines.

of how we live and how we can influence our environment. This has helped us to live longer, better lives (or at least easier lives).
We are no longer restricted to the locations in which we were born: transport has made world travel easier. Communication through phones, satellites and the internet have made it possible to interact with anyone, anywhere in the world. We are not isolated. No matter where we are in the world we have the means to learn and consume information, instantly and with minimal restrictions. (Some locations in the world still have very limited access to technology, but their number is reducing every day).
However, this human-created evolution of the world we live in, this convenience, comes at a cost. People have become so connected they have lost control of their data, their privacy. We cannot participate in the modern world without being connected to the digital world in some sense, and that means we lose choice: the choice to share or not share our information with the world; to share our personal information only with the loved ones in our lives. For most people living today, and for those to come, that choice is no longer available.
So, how can we evolve? How can we gain better control of what we share? Is it too late to put the cat back in the bag? Can we go back and put more controls around who can access our information, and how? Can we put that control back into each individual’s hands?
Honestly, I think the change will be difficult, and we will need to work very hard to change what people find acceptable, but it is very important we try. We must
make a real effort to ensure people understand the risks and benefits associated with sharing their personal data: what it can be used for and how they can take control of what they agree to allow others to see and use on their behalf.
If, as a society, we could find a way to enable realtime authorisation and enable people to easily understand what they are giving access to and give them the ability to revoke that access as fast as it has been given we would achieve greater privacy and security across the board.
Evolution is painful, and a very slow process, which seems at odds with our modern world. We have forged ahead at lightning speed with little concern or consideration for what our progress means for us as a society.
We need to press pause on this self-inflicted evolution and make choices that will positively affect the lives of future generations. So, let’s embrace this evolution and glean all the benefits it can give us, but let’s ensure we understand the risks before we march forward to a point of no return.
Let’s make smart choices now, not try to go back and fix them later with band-aids.
www.cyberunicorns.com.au
www.linkedin.com/in/craig-ford-cybersecurity
www.facebook.com/CyberUnicorns
www.instagram.com/cyberunicorns.com.au



Pallavi Kaul Associate Director, Deloitte
Pallavi Kaul, Associate Director at Deloitte, has carved a distinct path in cybersecurity, focusing on Governance, Risk, and Compliance (GRC). Reflecting on the early stages of her career, she recalls, “In the early stages of my career, the turning point came when I was hired into the GRC team at HCL. That opportunity gave me hands-on exposure to governance, risk, and compliance, and helped me see how cybersecurity underpins business trust and resilience. From there, I consciously deepened my skills, pursued certifications, and built on that foundation to shape a professional path in cybersecurity.”
From the outset, Pallavi had clarity about the direction she wanted to take. “When I started my journey in cybersecurity, I did have a sense of direction — I was always more drawn to the governance and risk management side than to purely technical roles. I wanted to understand how organizations can build trust, ensure compliance, and embed security into business strategy. So my career choices were quite intentional, focusing on Governance, Risk, and Compliance as my core path.”
For those beginning their journey, Pallavi advises, “I’d remind myself to stay curious and not be intimidated by how vast cybersecurity seems. No one masters it
“I’d remind myself to stay curious and not be intimidated by how vast cybersecurity seems. No one masters it all. Start with fundamentals, but be flexible to explore different domains. Eventually, you’ll find your niche — for me, that turned out to be Governance, Risk, and Compliance.”
all. Start with fundamentals, but be flexible to explore different domains. Eventually, you’ll find your niche — for me, that turned out to be Governance, Risk, and Compliance.”
She emphasises the importance of a strong foundational knowledge for aspiring cybersecurity professionals: understanding regulations, risk frameworks, and business strategy is critical to translating security into actionable and effective solutions.
Looking forward, Pallavi foresees transformative changes in the industry. “Over the next two years, I believe the most transformative shift in cybersecurity will be the move toward AI by design. Instead of deploying AI as an add-on tool, we’ll see it embedded directly into architectures, policies, and controls making security systems more intelligent, adaptive, and self-healing. This will elevate the industry from reactive defense to predictive resilience.” She also warns of the growing sophistication of threats: “The real threat will not just be more attacks, but the intelligence behind adversaries using AI to scale precision phishing, deepfakes, and automated exploits. At the same time, the quantum threat to encryption will shift from theory to urgent boardroom conversations, forcing adoption of PostQuantum Cryptography.”
The aspects of her role that bring the most fulfillment are clear: “As a Cybersecurity GRC practitioner, what fulfills me most is the ability to translate regulatory complexity and risk into clear, actionable strategies that help organisations operate with confidence. I take
pride in enabling leaders to see cybersecurity not just as compliance, but as a competitive advantage built on trust and resilience. Knowing that my work helps protect critical assets while empowering growth is what gives me the greatest satisfaction.”
Pallavi also stresses the importance of work-life balance in a demanding field. “I’m a mother to a 6-year-old son, who was born in Sydney, and my husband works with Google — so family time is precious. I make it a priority to be present with them, while also carving out time for fitness and reflection. That balance not only keeps me grounded but also makes me more effective as a Cybersecurity GRC practitioner.”
To remain effective and informed in an ever-evolving landscape, she combines structured learning with real-time insights: “I actively follow ET CIO forums, leading news articles, and regulatory updates to capture both global trends and local perspectives. I complement this with professional certifications and peer exchanges.”
Pallavi Kaul’s journey highlights the value of intentionality, continuous learning, and the pursuit of a meaningful niche. For those aspiring to enter cybersecurity, her story underscores that curiosity with strategic focus can lead not only to professional success but also to the satisfaction of making a tangible impact on organisational trust and resilience.
www.linkedin.com/in/pallavi-kaul-bb1360b

Erin Carroll
Cyber Risk Consultant
Erin Carroll’s journey into cybersecurity is anything but conventional. “I was a high school History teacher from 2007 until 2023, with a full-time teaching career from 2007-2020. In this role I was also an IT Administrator, coming into the role through curiosity, proficiency, and a love for all things IT,” she explains.
“Being amongst the rapid changes that happened over this period was a key driver for my initial interest in cybersecurity, from overhead projectors to Smart Boards, MP3 players to iPods to Smart Phones, and the onset and rapid continual evolution of social media, the exposure teenagers had to the online environment was something that came up in my everyday conversations whether I prepared for them or not.
” It was in late 2019 that Erin felt the need to transition from teaching to cybersecurity full-time, making the move in early March 2020—just before the first COVID-19 lockdowns in NSW.
Erin wasted no time turning her interest into action. “Whilst teaching I had a desire to work in the cybersecurity field, and within two days of resigning from my teaching position I had enrolled in university. At that point in time, all I knew was that I wanted to work in cybersecurity in a way that I could help those who used ‘The Internet’ stay safe.” Completing her degree at UTS opened the doors to a role at KPMG as a Cyber Risk Consultant. “Instead of helping just one business establish and maintain cyber safety, I could work with multiple clients on a long-term basis, keeping them secure whilst the cyber world changed around them,” she says.
Reflecting on her transition, Erin notes the importance of embracing skills from her previous career. “On paper, my professional background as a high school History teacher was very different from cybersecurity, but I was doing IT Administration and policy development in the background in roles I put my hand up for out of interest and curiosity. My skills as a historian have been exceptionally valuable when
it comes to gathering and analysing evidence, and standing in front of classrooms full of teenagers for years has meant I have learned how to talk to, do the best for, and get the best out of a diverse group of individuals. As a consultant, these ingrained analytical and interpersonal skills are crucial for establishing and maintaining strong relationships.”
Her work at KPMG has been pivotal in shaping her professional trajectory. “KPMG has exerted the most substantial influence on my cybersecurity career, and in particular one of the Directors—Stuart Jones. Stuart was one of my interviewers and could see how my combination of cybersecurity expertise, policy and compliance knowledge, and teaching career could make me a valuable addition to the Tech Risk & Cyber Business Resilience Team, even before I knew that team existed. Him providing me the initial opportunities has made a huge impact on my professional journey, and his continued mentorship has led me to find a niche passion in business resilience and CPS 230.”
Erin thrives on problem-solving and delivering practical guidance. “The aspect of my current role that brings me the most satisfaction and fulfillment is problem-solving real-time risks and concerns and being able to provide clients with strategies and advice on how to keep their cybersecurity environment stable and protected. I find it quite fun being able to analyse the tech environment and policy requirements and turn it into practical application that is customised to the client’s needs.”
Her advice to those considering cybersecurity is rooted in her own experience. “As someone who has made a mid-life career transition, the first thing I will say is that if you’re considering it, absolutely give it a try! Even if you feel that your current or past roles and skills aren’t relevant, there will be something that makes you stand out.”
Beyond her consultancy work, Erin actively contributes to the broader community. “I am involved in KPMG’s In Her Hands organisation, Women4STEM, and the Australian Women in Security Network (AWSN). These women-centred organisations connect both aspiring and experienced women in the security industry. Being part of these organisations has provided me with regular opportunities to network with and learn from experts across different technology and security areas. I find these connections highly valuable to both my professional and personal development.”
Erin Carroll’s journey illustrates that career paths are rarely linear, and that curiosity, adaptability, and a willingness to embrace new challenges can open doors to exciting, unexpected opportunities. From guiding teenagers in a classroom to safeguarding businesses in cyberspace, her story is a testament to the power of following your interests and leveraging the skills you already have to make an impact.
www.linkedin.com/in/erinlouisecarroll


Cybersecurity Intern, SPYINT
Anisha Dad, now a Cybersecurity Intern at SPYINT, recalls the moment her fascination began. “My interest in cybersecurity began during my undergraduate studies in commerce and while I was reading newspapers about cybercrime and digital threats. I have always wondered about what happens ‘behind the screen’; I find it fascinating how deleted files and hidden data can be recovered, and how systems act. When I found cybersecurity, my interest transitioned from curiosity about systems, to actively learning how to secure them, investigate threats, and make a positive difference in the digital world.”
Her leap into the field wasn’t straightforward. “Having a non-technical background with a B.Com degree, my first important step was pursuing a diploma in Cyber Forensics and Information Security. At the same time, I also took the initiative to go for internships in Cyber Security, OSINT, and Python programming to get practical experience. Attending CTFs and workshops gave me experience in dealing with real world problems while building my confidence. Every step,
from the certifications like the Google Cybersecurity Specialization to internships with Gurugram Police and Grras Solutions molded me from a state of curiosity to a career path.”
Anisha says the most challenging part of her current role is keeping pace with the speed of change. “There are exciting and new tools, vulnerabilities, and attack techniques that seem to show up almost daily and it does feel daunting. I guess to get around that, I have formed an ongoing learning habit. I have relied on tools such as Burp Suite, Nmap and Shodan, I am in communities of LinkedIn and Discord, such as TryHackMe, and I have given some thought to trending attacks on Twitter. In addition to keeping me current, I joined community groups such as Women in CyberSecurity (WiCyS), Women in Security and Privacy (WISP), and local cybersecurity community groups, which have all provided me with a sense of community, support, and mentorship. I have been able to stay consistently engaged with ongoing learning and not lose enthusiasm by breaking learning challenges into smaller objectives.”
She admits there were moments of doubt about whether she was “technical enough” to make it in the field. “Yes, I did a degree in commerce previously and I used to wonder whether I was ‘technical enough’ to make it? It sometimes felt like there was a high learning curve particularly with regards to programming and more advanced technical concepts. Having curiosity in mind and keeping my goal to where I began and using the mentoring of Layee Joshi while working as a Grras Solutions intern, and community professionals such as Lakshit Verma, who led me to learn about OSINT research and dark web research better, was what drove me forward. Through their mentorship, I came to know that determination is far more significant than beginning from a specific position.”
Her career unfolded naturally. “When I started, I didn’t know what exact role I wanted to pursue, I just knew I wanted to work in cybersecurity. I just let it unfold naturally. I started by looking into digital forensics and OSINT because I enjoyed the challenge of finding data that was once hidden and connecting the dots. Then, I moved into offensive security, where I learned tools like Burp Suite, Metasploit and Shodan. Each of my internships, certifications, and CTFs has helped me narrow my focus and clarify my path. Today, I would say my career is a combination of curiosity, exploration, and continual growth.”
If she could speak to her younger self, her advice would be simple but powerful. “I would say, ‘Don’t be afraid of starting small. Be consistent, practice every day, and grab every opportunity to learn, even if it feels basic.’ Cybersecurity is not about being perfect from day one; it’s about being curious, resilient, and persistent. Every small skill connects over time. I’d also stress joining communities early; learning alongside others in groups like TryHackMe, WiCyS, or Discord study circles makes the journey less overwhelming and far more inspiring.”
Anisha also believes in building a strong technical foundation. “For a firm foundation, fundamentals of computers, networking, operating systems, and scripting (such as Python) are necessary. In addition to that, a good understanding of cybersecurity fundamentals—threat intelligence, digital forensics, and ethical hacking—is useful. OSINT (Open-Source Intelligence) is also an underappreciated but strong skill set. A combination of theory, lab practice, and certifications such as Google Cybersecurity, CEH, or CompTIA+ really can establish a firm foundation.”
Looking ahead, she expects major shifts in the threat landscape. “I anticipate seeing more attacks and threats driven by AI and taking the form of deepfakes. Attackers are already hacking around security. And that will probably get worse, not better, since attackers already use machine learning to evade security. As businesses increasingly migrate sensitive data to the cloud, they will have more and more demand for cloud security and digital forensics.
The near-term future of how cybersecurity is evolving involves a confluence of areas: cloud security, OSINT and AI.”
She’s also watching emerging threats closely. “As ransomware and phishing get better and more common, new dangers like supply chain attacks and social engineering with fakes are becoming bigger problems. Hackers are now more focused on fooling people rather than breaking into systems, and AI helps them create fake identities and voices that are really hard to spot. Alongside AI-powered social engineering, there’s also an increase in threats connected to cryptocurrency, like phishing attacks for wallet keys, fake NFTs, and DeFi scams. As more people use cryptocurrency, these attacks are getting more profitable and harder to follow. Because of this, tools like OSINT, blockchain analysis, and threat intelligence will be more important than ever.”
Beyond salary, Anisha looks for growth, mentorship and well-being in an employer. “Besides salary, I also care about chances to grow and learn from others. This means having access to better tools, regular training, and working on real projects that help me improve. I also value if a company supports teamwork and sharing knowledge, like going to events or helping with free projects. Work-life balance and having a team that cares about well-being are important, especially in busy areas like cybersecurity, where looking after mental health makes a big difference.”
Anisha Dad’s journey from a commerce graduate curious about hidden data to a cybersecurity intern shaping her path through continual learning and community involvement is proof that determination and curiosity can bridge any gap. Her story reflects the evolving face of cybersecurity: diverse, fastmoving, and built on the resilience of those who choose to protect the digital world.
www.linkedin.com/in/anisha-d-54b7751a0

Security Researcher with (Confidential) and Host of Secure Kids Now! Network, a Podcast/ Show on protecting children online
Susan Verdin began cybersecurity long before most people even know the field exists. “I was 11 years old, and I became very interested in how malware and anomalous behaviours worked on computers. I downloaded Microsoft Virtual PC 2007, and would use that as a lab to observe malware samples, and then I taught myself my first programming language, which was Javascript at the time,” she recalls. Over the years, her fascination has deepened. “Since then I have developed an interest in the internals of operating systems, and observe all kinds of malware as well as other types of attack vectors and procedures. These things have taught me how to better serve the public, and share new information as it comes.”
Turning childhood curiosity into a professional pursuit required both persistence and hands-on experience. “I constantly studied, got my hands into different technologies and how they worked. While certifications have helped me get a foot in the door, experience has trumped those certifications for me. Having knowledge in different technical domains has allowed me to grow as a security professional, and take care of people who come to me for help,” she explains.
For Susan, one of the most complex aspects of her work is understanding the human motivations behind cyber threats. “The most challenging and complex aspect of what I do is diving into the root cause of a threat actor’s behavior, understanding not
only the technical aspect but the psychology and motivations behind what they do. Each aspect should be explored to come to the best answer as to how an incident occurred.”
Like many professionals, Susan has faced moments of self-doubt. “Yes. I thought in the beginning that I wasn’t cut out for this. That I didn’t have the smarts or capabilities, but that was my imposter syndrome talking. I navigate this by boosting confidence in myself by gaining new information and researching.”
From the outset, she had a clear vision for her career. “I wanted to become a researcher who specializes in malware analysis. But I’ve learned that malware analysis can be applied to many different roles in information security.” Looking back, she offers advice to her younger self: “To continue going down the path I began and staying determined. Staying curious, and asking many, many questions. Don’t settle or hold yourself back. Nothing is truly impossible to achieve.”
When considering education for aspiring cybersecurity professionals, Susan emphasizes a hands-on understanding of the technologies they aim to protect. “You don’t necessarily have to become a programmer, as there are all kinds of aspects to information security, but starting out from a background where you are exposed to the very thing you are protecting is important. Whether it is technical, compliance, government, etc...”
Looking ahead, Susan predicts both challenges and opportunities in the cybersecurity landscape. “Most certainly the rise of AI-driven malware and other
attacks… Another is the growth of cloud security, as well as increased attacks on critical infrastructure technologies, and internet of things.” She notes that human behavior remains central to security breaches: “I foresee the use of AI continuing to be used to develop new attack methods… and an increase in teaching the public how human behaviours and psychology shape the way security breaches happen at times.”
For Susan, fulfillment comes from tackling difficult problems and using her expertise to protect others. “Challenging, complex problems that are presented in code” are what drive her, balanced with a routine that includes hobbies and time with loved ones. “This helps me to stay current on the latest events and developments in the field,” she adds, highlighting her commitment to lifelong learning.
Influenced early on by her family, who encouraged her interest in technology, Susan continues to grow both as a professional and as an advocate. She plans to expand her knowledge in machine learning, exploit development, and advanced malware behaviors, while also focusing on programs to protect the public—including children—online. Her journey reflects the combination of curiosity, determination, and continuous learning that defines her as a cybersecurity leader and role model.
hmalwaremaycry.medium.com
www.linkedin.com/in/susan-verdin-31b8b4104
“To
continue going
down the
path
I
began and staying determined. Staying curious, and asking many, many questions. Don’t settle or hold yourself back. Nothing is truly impossible to achieve.”

Naomi Onuoha
Cybersecurity Engineer
Naomi Onuoha, a Cybersecurity Engineer, recalls the moment her interest in cybersecurity first took off. “I didn’t like the fact that I could be in my home and be vulnerable to a cyberattack by someone across the globe. I wanted to take charge of my security and do something about it,” she explains. This initial spark of self-preservation quickly evolved into a professional pursuit, driven by curiosity and determination.
Reflecting on the early stages of her career, Naomi shares, “I took training courses in cybersecurity and spent time studying and learning the basics, as well as writing exams. I was very inquisitive and that made me grasp as much knowledge as I could.” Her methodical approach to learning laid the foundation for a successful career in cyber defence.
While Naomi has not encountered extreme technical challenges in her role, she identifies collaboration as an area requiring persistence. “The only thing I find a
bit challenging right now is getting other departments to effectively help resolve problems. For example, a bunch of my work relies on the IT department as access to certain assets is constrained,” she notes. Nevertheless, she navigates uncertainty with confidence. “Yes, I did experience moments of doubt, but I didn’t dwell on them. I just continued studying, and the more I studied, I realised I loved the path I chose.”
Naomi’s cybersecurity journey was organic rather than meticulously mapped. “I didn’t have a clear vision. I wanted to become ‘everything’ but as I continued, it was then that I realised I had more passion for cyber defence (Blue Team), as opposed to Red Team work,” she says. Her advice to her younger self underscores the importance of clarity and focus: “You must know what Cybersecurity is all about first and then choose the path of cybersecurity you want to follow, then be very skilled in it.”
In her view, a strong foundation in networking, Linux, and security fundamentals is critical for aspiring professionals. Looking ahead, she anticipates transformative changes in the industry: “I believe it will be the use of AI to anticipate threats and respond to them in ways the industry has never seen before. It could learn behavioural activity and impersonate users. AI is powerful, but the question is, ‘who’s using it better? The good guys or the bad guys?’”
When evaluating career opportunities, Naomi prioritises workplace culture alongside career
advancement. “It’s not just skilling up and making money or having connections but working with good people who are very non-toxic. Our work or career is just an aspect of our lives, and you’d be surprised how toxic work environments can affect us in other areas,” she explains.
Driven by a desire to strengthen security postures, Naomi emphasises the broader impact of her work. “I want to be able to join an organisation and set up or significantly improve the security posture, setting up layers and layers of security and making sure that we ourselves (users) are alert and trained enough to not be the point of entry for malicious users.” Looking ahead, she plans to pursue certifications such as CISM, CISSP, and cloud-focused networking and security qualifications to continue building expertise.
What brings Naomi the most satisfaction in her current role is the assurance that all security tools are functioning optimally across her organisation. “I enjoy doing security coverage, making sure all our tools are installed and working properly on ALL assets. This involves optimisation and reporting also,” she says.
Maintaining work/life balance is equally important, and she achieves this through remote and hybrid work arrangements that allow for rest and flexibility.
Naomi’s approach to staying current in the fastevolving field of cybersecurity involves continual learning and active engagement with professional networks. “I am active on platforms like LinkedIn that give me current cyber information, and I always study from time to time to keep my mind updated and refreshed and also learn new things,” she notes.
For those transitioning into cybersecurity from other backgrounds, Naomi offers a clear message: “You must have a real passion for the work and not money. You must know the areas of cybersecurity you want to specialise in. You must be ready to study hard and also study consistently as you grow.” Her journey reflects a blend of curiosity, resilience, and a steadfast commitment to defending the digital frontier—qualities that define her as a formidable presence in cybersecurity today.
www.linkedin.com/in/naomi-onuoha-31a016201


Marivell Alicea-Gamlin
Marivell Alicea-Gamlin, now a Senior Cybersecurity BISO Analyst, didn’t begin her career with the title “cybersecurity” attached to her name. “I spent many years in IT operations and support, where I was already doing security-related work before cybersecurity became a buzzword,” she recalls. “As the field gained attention and began trending, I wanted to be part of the movement and saw it as the natural next step in my career.”
Initially, she imagined herself in highly technical, investigative roles—tracking malicious activity, working alongside network teams, or diving into forensics. “At first, I envisioned myself doing more technical investigative work,” she says. “Instead, my path shifted toward governance, risk, and compliance. I initially missed the technical side and questioned whether I had made the right move.”
That shift ultimately proved transformative. “What surprised me most was realizing that my primary audience would be business decision-makers rather than technical teams,” she explains. “While I sometimes missed being hands-on, I discovered real fulfillment in working with leaders, shaping decisions, and connecting cybersecurity to business priorities. Having a seat at the table, influencing direction, and making an impact has been truly empowering.”
Reflecting on her early career, Marivell pinpoints two pivotal steps that shaped her path. “One was taking on a network administration role, a job I initially thought I could not do,” she says. “It was challenging, and I had to learn quickly under pressure, often troubleshooting issues while users were losing connectivity. I also enjoyed being responsible for managing access to data, systems, and even physical buildings, which gave me an early appreciation for security.”
Another defining step was returning to school to pursue her master’s degree while balancing the demands of work and parenthood. “I felt it was imperative to invest in my education,” she says. “In a competitive field where I am a minority in many ways, I knew the degree would help me stand out. While I initially aimed for network security, the rapid growth of cybersecurity opened the door to a broader career path that has shaped where I am today.”
Interestingly, the most complex part of her current role has little to do with technology. “It’s relationship building,” she admits. “Navigating conversations with individuals who have different personalities, communication styles, and priorities can be challenging. Over time, I’ve learned that adapting my approach based on the person I’m engaging with makes all the difference.” She’s found that recognizing personality types and adjusting how she communicates has helped her build stronger relationships, reduce friction, and collaborate more effectively across the business.
Looking back, her path unfolded organically. “To be clear, I thought I had been doing cybersecurity work for at least a decade before stepping into my first official role,” she laughs. “At that point, I was surprised by how much of it involved administrative responsibilities, which felt very different from what I had envisioned. Over time, my path grew organically into governance, risk, and compliance.”
Yet her love for incident response still lingers. “I thrived under pressure. I stayed calm when situations escalated, and I enjoyed being the person others relied on to figure out what was happening, communicate with leadership, and help restore operations,” she says. “It felt good to contribute in a way that made a real difference. Looking back, my real aspiration was to be a trusted source, and that is still the role I strive to fulfill.”
Marivell also has a keen eye on the future. “In the next two years, one of the most impactful developments in cybersecurity will be the creation of stronger governance and guardrails around artificial
intelligence,” she predicts. “Reliable generative AI will begin to support better decision-making, but it comes with risks, especially as Agentic AI systems operate with less direct human oversight. Strong governance will be critical to setting boundaries, ensuring accountability, and keeping these systems aligned with ethical and regulatory expectations.”
She expects similar advances in vulnerability management. “Tools will become more accurate and less burdensome, helping organizations detect issues faster, simplify remediation, and reduce the operational strain that often slows progress today,” she notes.
What brings her the greatest satisfaction today is trust. “The most fulfilling aspect of my current role is the ability to establish trust with clients, business leaders, and technical teams,” she says. “I find deep satisfaction in learning about the technology solutions we use and translating that knowledge into meaningful guidance that supports both security and business goals. Understanding the technical landscape allows me to have informed conversations and build credibility, which in turn strengthens relationships and reinforces my role as a trusted partner. That sense of trust and influence is what truly drives me.”
Staying current in such a fast-moving field requires intentional effort. “I stay engaged in professional communities like ISSA Puget Sound, where I also serve in a leadership role and connect with peers on emerging trends,” she explains. “I regularly attend conferences and summits to gain fresh perspectives and stay ahead of industry developments. On the learning side, I hold the ISC2 Certified in Cybersecurity (CC) and I’m actively studying for the CISSP. I also read extensively to stay informed and knowledgeable about emerging risks, evolving technologies, and best practices. In addition, I mentor students, which challenges me to keep my knowledge fresh and explain complex topics in simple terms.”
Industry involvement has also been a cornerstone of her growth. “I currently serve on the board of



Sarita Padmini
Senior Director – Cyber Security
Sarita Padmini, Senior Director –Cybersecurity, reflects on a career defined by continuous learning, strategic thinking, and the balance of technical expertise with leadership. When asked about the most complex aspect of her current role, she states, “The toughest aspect is balancing business priorities with security requirements. My approach has been to frame cybersecurity in terms of business risk and value, making it easier for leadership to support security-first decisions and not an afterthought.”
Her journey into cybersecurity was organic rather than pre-planned. “Honestly, my path unfolded organically. I initially just wanted to ‘work in Information security,’ but as I gained exposure, I discovered areas like Application Security, Governance, risk, and compliance, Solution architecture,Data Privacy, Security Operation Centre and later, cloud security, that shaped my long-term career goals.” Yet even in moments of uncertainty, such as managing the fast pace of change in threats and tools while becoming a
new mother, Sarita remained committed. “I navigated it by focusing on continuous learning, thinking beyond boundaries and building a professional network where I could share challenges and learn from others’ journeys,” she explains.
Reflecting on advice she would give her younger self, Sarita emphasizes resilience and curiosity: “Don’t let the technical battle scare you off. Start small, practice regularly, and remember cybersecurity is about problem-solving, not just coding. So just a women thing. Women are born problem solvers.” For aspiring professionals considering university studies, she recommends focusing on AI Model security, quantum computing, API security, cryptography, data privacy laws, programming basics, and strong analytical thinking skills.
Looking ahead, Sarita anticipates transformative changes in the cybersecurity landscape. “AIdriven threat detection and the rise of zero-trust architectures will transform how organizations defend
themselves. Additionally, global privacy regulations will force companies to rethink data security practices.” She also warns of emerging threats: “Two stand out: AI-powered cyberattacks like deepfakes and malware attacks, and supply chain attacks where attackers exploit third-parties to infiltrate larger organisations.”
When considering career advancements, she looks beyond remuneration. “I’d evaluate the clear scope of responsibilities and how it is aligned with Company’s vision, the people culture of the organisation which depicts the mindset of the leaders, opportunities for growth, and whether the role allows me to make a measurable impact.” Mentorship has played a crucial role in her growth. “Mentors have been the biggest influence. Shri Indu Bhushan, Former CEO of Ayushman Bharat, Rama Vedasree, Former CEO of DSCI, and Shri J Satyanarayana, WEF Advisor, are three mentors whose guidance I would like to acknowledge. Learning from leaders who balanced technical expertise with strategic thinking inspired me to grow beyond being ‘just technical’ and develop leadership qualities.”
The most rewarding part of her work, she says, is tangible impact: “Seeing how my work directly prevents breaches and protects customer trust. There’s immense satisfaction in knowing my team’s efforts keep critical systems safe.” Achieving work-life balance is equally important, and Sarita credits clear boundaries, delegation, and downtime with family as
“Your diverse experience is an asset. Whether you come from IT, compliance, or even nontechnical fields, transferable skills like problem-solving, communication, and risk analysis are highly valued. Start with foundational certifications, and gradually specialize.”
"Don’t
let the technical battle scare you off. Start small, practice regularly, and remember cybersecurity is about problemsolving, not just coding. So just a women thing. Women are born problem solvers.”
her strategy: “Spirituality and spending time with my little ones help me recharge.”
To remain effective in a fast-evolving field, she relies on multiple learning channels: “I rely on threat intelligence feeds, professional forums, and continuous training. I also attend webinars and conferences to keep a pulse on both global and regional threat landscapes.” Her professional affiliations, including ISACA and WiCyS, have been instrumental in providing best practices, certifications, and a network of experts.
For those transitioning into cybersecurity from other backgrounds, Sarita emphasises the value of diverse experiences. “Your diverse experience is an asset. Whether you come from IT, compliance, or even non-technical fields, transferable skills like problemsolving, communication, and risk analysis are highly valued. Start with foundational certifications, and gradually specialize.”
Sarita Padmini’s journey embodies a blend of technical expertise, leadership, and strategic vision, offering a blueprint for women aspiring to make a meaningful impact in cybersecurity.
www.linkedin.com/in/spadmini

Lauren Webber’s cybersecurity path was inspired by her family background, a unique blend of corporate and law enforcement influences. “My initial interest in cybersecurity was sparked by my family background. My mother works in the corporate sector, while my father is in law enforcement. Growing up, I was fascinated by the idea of combining the strategic, business-focused mindset from the corporate world with the investigative and protective nature of law enforcement. Cybersecurity felt like the perfect intersection of these two fields, allowing me to help organisations protect their assets while also contributing to broader societal safety.”
Her professional path began to take shape during her final year at university, when a chance encounter with a KPMG director opened her eyes to consulting within the Big Four. “That conversation opened my eyes to the possibility of combining my interest in cybersecurity with a dynamic, client-facing environment. I was inspired by that encounter and decided to focus my efforts on consulting
roles that specialised in cyber and digital risk. This decision set me on a path of preparation through researching the industry, building my technical and business knowledge, and practicing for the interview processes.”
Like many entering cybersecurity, Lauren faced moments of doubt and uncertainty. “Absolutely, and to be honest, I still experience moments of uncertainty from time to time. In the first few months of my career, I struggled with a strong sense of impostor syndrome, especially since my background was more non-technical compared to some of my peers. It was easy to question whether I truly belonged in the field or if I could keep up with the rapid pace of change in cybersecurity.” Her approach to overcoming these doubts was rooted in community and self-reflection: “I made a conscious effort to reach out to my support systems—mentors, colleagues, and friends—who reassured me that most professionals have faced similar challenges. Over time, I learned to reframe my doubts as opportunities for growth.”
“One of the most satisfying aspects of my role is knowing that the work I do generates meaningful outcomes and helps organisations defend against malicious threats. Knowing that my efforts contribute to the ability of these organisations to serve Australian citizens and protect critical services is incredibly rewarding.”
of how cybersecurity fits into broader business objectives. I also explored my interest in human, political, and military security, which helped me appreciate the wider context in which cyber threats and solutions operate. Understanding how cyber risks impact organizations, governments, and society is just as important as knowing technical details.”
When it comes to professional growth, she advocates for exploring the full range of opportunities before specialising. “Beginner-friendly certifications such as the Google Cybersecurity Professional Certificate, CompTIA Security+, and Microsoft SC-900 are great starting points. These courses can provide a pathway into cybersecurity and offer valuable learning experiences for those starting out in the field.”
Lauren’s career path has unfolded organically rather than following a rigid roadmap. “Initially, I applied to join KPMG’s audit team, not because I was certain it was the right fit, but because I wanted to explore my options and gain experience at a reputable firm. Although I wasn’t successful in securing the audit role, one of the talent acquisition staff reached out to me about a cyber consulting position in risk services, having matched my profile from the talent pool. In many ways, the role found me rather than the other way around.”
Reflecting on her early education, Lauren wishes she had explored cybersecurity sooner. “During high school there were no ‘cyber’ or ‘technology’ subjects. I’d suggest seeking out online resources, workshops, and being proactive in researching emerging fields. It’s okay not to have everything figured out right away; sometimes the best opportunities come from being open to new experiences and following your curiosity.”
Lauren believes a multidisciplinary approach is key for building a strong foundation in cybersecurity. “Grounding my studies in Commerce gave me valuable commercial acumen and a deep understanding
The most fulfilling part of her current role? “One of the most satisfying aspects of my role is knowing that the work I do generates meaningful outcomes and helps organisations defend against malicious threats. Knowing that my efforts contribute to the ability of these organisations to serve Australian citizens and protect critical services is incredibly rewarding.”
Balancing a demanding career with personal life has also been a learning process. “A turning point came after a conversation with my people manager. She encouraged me to introduce non-negotiables into my routine—clear boundaries and priorities that I wouldn’t compromise on. Implementing these non-negotiables made it much easier to balance work and life, because I knew what was truly important for my wellbeing and could make time for myself without guilt.”
Lauren Webber’s journey demonstrates that cybersecurity is not only about technical expertise—it is about resilience, adaptability, and the ability to bridge multiple perspectives. Her story is an inspiring reminder that curiosity, perseverance, and openness to unexpected opportunities can lead to a meaningful and impactful career.
www.linkedin.com/in/lauren-webber-

Sakshi Kishore
Associate Director, Technology Risk and Cyber, KPMG Australia
Sakshi Kishore, Associate Director of Technology Risk and Cyber at KPMG Australia, has built her career on a foundation of curiosity, resilience, and a passion for empowering others.
“My initial interest in cybersecurity was sparked by a combination of curiosity, upbringing, and circumstance,” she recalls. “I come from a state in India historically known for its scholars and academics, but post-colonisation, it has faced significant challenges in literacy and poverty. It is not common for people from my region to explore the world beyond their hometowns, but my father was determined to change that for his children. He instilled in us a strong academic foundation and a habit of reading the newspaper end-to-end every day. I remember playing games based on what we read in the newspaper. I still look back and cherish the fun educational times with my siblings. He encouraged us to ask questions, stay curious, and never stop learning.”
Growing up in a household with talented siblings and a hardworking mother, Sakshi was inspired to explore the unknown. That curiosity guided her through her electrical and electronics engineering degree and an initial trajectory in the energy sector. “As I stood at the threshold of my career, I realised that path didn’t ignite my passion,” she says. Drawn to one of the emerging buzzwords of the time “cyber”, Sakshi found herself captivated by the real-world impact of cyberattacks and the strategic decisions that could prevent them. “What started as curiosity quickly evolved into a mission. Over time, I found purpose in mentoring others, advocating for diversity, and building inclusive teams to tackle complex challenges. I embraced opportunities to speak at forums, lead social committees, and create knowledge-sharing platforms, realizing that cybersecurity thrives on collaboration, continuous learning, and a deep understanding of people.”
Reflecting on her early career, Sakshi identifies a series of bold decisions that transformed her interest into a profession. “I began my journey as a subject matter expert in Third-Party Risk Management at KPMG India, where I spent five years building deep expertise in regulatory compliance, supplier risk, and governance frameworks,” she explains. “The first pivotal step was choosing to pivot from a specialised TPRM role into the wider cybersecurity domain. This meant stepping out of my comfort zone and embracing a field that was vast, dynamic, and constantly changing.”
Her journey also spanned continents. “Moving from India to Singapore, and eventually to Australia, meant restarting from scratch each time, rebuilding networks, learning new regulatory landscapes, and adapting to different workplace cultures. These transitions were not easy, but they taught me resilience, adaptability, and the importance of continuous learning. Each move gave me fresh exposure to new sectors, clients, and challenges, helping me evolve from a technical contributor to a strategic advisor.”
The challenges Sakshi faced from geographic transitions to shifting from a specialist to a broader leadership role became defining moments. “Another challenge was evolving from a subject matter expert in Third-Party Risk Management to a broader cybersecurity leadership role. This transition demanded not only technical upskilling but also a shift in mindset from being a specialist to becoming a strategic advisor. I approached this by actively investing in professional development, earning certifications like the Certificate of the Business Continuity Institute (CBCI) and Azure Fundamentals, and participating in KPMG’s Women in Leadership Program while managing full-time client delivery. Currently, I am pursuing CISSP,” she shares.
Doubts also emerged along the way. “Yes, I have experienced moments of uncertainty, especially during the early transitions in my cybersecurity journey. Shifting from a specialized role in TPRM to the broader, fast-paced world of cybersecurity
was both exciting and intimidating,” she says. “The doubts became more pronounced as I moved across countries and transitioned from an execution to a leadership role. Each transition meant starting over and adapting to the unknown. At times, I questioned whether I could keep up, whether I belonged, and whether I could re-establish myself in a new environment without the comfort of familiarity. Staying grounded in my values and leaning into the discomfort helped me navigate those doubts.”
She credits cybersecurity with giving her stability and purpose during personally challenging times. “During that time, my work became more than just a profession; it became a source of stability and purpose. Cybersecurity gave me structure, a sense of impact, and a second life when I needed it most. Looking back, those moments of uncertainty were not setbacks; they were turning points. They taught me that resilience isn’t just about pushing through; it is about growing through.”
When she began her journey in cybersecurity, Sakshi did not have a clear roadmap. “I doubted whether consulting was the right fit for me. As an introvert who prefers meaningful connections over surface-level socializing, the idea of thriving in environments that seemed to reward loud voices and dominant personalities felt daunting,” she reflects. “But as I began exploring the field, I discovered that cybersecurity and consulting allow for diverse personalities and approaches. I didn’t need to be the most outspoken person in the room to make an impact. Instead, I leaned into authenticity, deep listening, and building trust, which became my strengths.”
Her path unfolded organically, driven by curiosity and openness to new challenges. “Rather than chasing titles or rigid goals, I allowed my path to unfold organically. I embraced variety, working across industries and geographies, from cyber risk quantification for global insurers to regulatory uplift, understanding cyber in quantum computing, and cyber risks in multiple sectors, including energy, telecommunication, and higher education.”
Looking ahead, Sakshi is attuned to emerging threats. “From where I stand, one of the most pressing and complex threats in the cybersecurity landscape over the next two years is the rise of human-centric cyber risk,” she warns. “Attackers now have the capability to craft hyper-personalized phishing campaigns and automate social engineering tactics at scale. At the same time, many employees are experiencing cyber fatigue, which can lead to lapses in judgment and reduced vigilance. Ultimately, the future of cybersecurity will hinge not just on tech innovation but also on our ability to understand, support, and empower people. Human cyber risk isn’t just a technical issue; it is a leadership challenge.”
When evaluating new career opportunities, Sakshi looks beyond the obvious. “I have learned to prioritise roles that offer meaningful growth, cross-sector exposure, and the chance to deepen my expertise. I look for environments that foster intellectual challenge, ethical leadership, and long-term impact. Liking the people you work with is a deeply underrated but critical factor when considering a career move,” she explains. “Beyond titles, compensation, or prestige, I always ask: Will I enjoy working with this team? Will I feel supported, challenged, and inspired? Because in the long run, it is the people who shape your experience, your growth, and your legacy.”
Sakshi also credits her first boss at KPMG India with profoundly influencing her career. “Their leadership style left a lasting impression on me: every team member was treated as a leader, with tasks assigned based on willingness and appetite rather than designation,” she recalls. “One lesson that has stayed with me is their advice after a tough client meeting: ‘Sometimes the only way to arrive at the
right outcome is by meeting people halfway. Not every time will you get results by following your way or the standard steps. Make everyone a part of the process to achieve a desired outcome.’ That approach has helped me resolve conflicts and build consensus throughout my career.”
For Sakshi, work/life balance is non-negotiable. “Maintaining work/life balance in cybersecurity isn’t just important; it is essential for long-term sustainability and personal fulfilment,” she says. “I dance, run, swim, explore pottery, and take spontaneous classes that spark curiosity. These hobbies aren’t just distractions; they’re intentional ways to recharge. Nature plays a big role, too. Hiking and coastal walks offer a sense of calm and perspective. But what truly makes this balance meaningful are the personal moments, video calls with my nephew back home, watching my dog play over video calls, or simply enjoying quiet time.”
She has advice for those transitioning into cybersecurity from other professional backgrounds. “In life, some people are offered stairs, some get escalators, and others have elevators. But what truly matters is not how quickly you reach the top; it is how well you are able to sustain yourself once you are there,” she says. “When transitioning into cybersecurity from another professional background, my advice is simple: cybersecurity is not fundamentally different from any other field. It is built on three foundational principles: be diligent, be curious, and do every part of your job right. Technical skills will come with time and experience, but what truly sets you apart is your attitude and aptitude.”
Her journey demonstrates that resilience and authenticity can be powerful forces in shaping a career. “If ever you feel like you can’t keep swimming, just let yourself float,” she says with a smile. “By staying curious and open to new challenges, I have found purpose not in chasing a title, but in empowering others, making a difference, and growing alongside my teams.”
www.linkedin.com/in/sakshikishore

Karen Stephens is the co-founder and CEO of BCyber. After more than 25 years in financial services, Karen moved into SME cybersecurity risk management. She works with SMEs to protect and grow their businesses by demystifying the technical aspects of cybersecurity and helping them to identify and address cybersecurity and governance risk gaps. She was recently named inaugural Female Cyber Leader of the Year at the 2023 CyberSecurity Connect Awards in Canberra.
We should all be familiar with the boiling frog fable lest we become that frog. Because, trust me, the cyber world is littered with many fallen ‘frog’.
Here is a little memory jogger.
If a poor old frog is placed in boiling water, it immediately jumps out. In my line of work, we call that “acknowledging you have a cyber resilience issue and actually doing something to address it.”
But, if you put a frog into a pot of water that is gradually brought to the boil, the poor unsuspecting frog will stay put and perish. It’s a cautionary tale about the need to be aware of even gradual changes lest you suffer the undesirable consequence of being unaware of changes in your surroundings and failing to adapt.
Welcome to the world of cybersecurity, where the risk clock is sitting at five minutes to midnight and where business evolution, or possibly a revolution, is needed. Rather than being dry and theoretical, I thought I would lead by example and provide a real-life case study into the evolution of the BCyber business.
At BCyber our business evolution started with a problem: cybersecurity Governance, Risk and Compliance (‘GRC’) being treated the same today as it was last year, and the year prior, and the year before that. Meanwhile, the cyber criminals have not been sitting still. AI is a fast and furious mover. Yet the cybersecurity market today often presents a choice between two extremes. On one hand you have traditional, manual tools like Excel spreadsheets and forms. While familiar, they are static and insecure and create profound inefficiencies; they simply

weren’t built for the dynamic, high-stakes world of cybersecurity GRC. On the other hand, you have a flood of complex platforms and AI point solutions, many siloed; you might get an AI-powered log analyser or a basic automation tool, but they don’t connect governance to resilience.
The BCyber evolution (aka our solution) is to provide a single, integrated ecosystem built on our GRACE (Governance, Resilience, Assurance, Compliance and Education) framework. It’s a total solution, not a collection of disparate parts. It’s a collection of proprietary apps that provides a holistic and integrated approach to cybersecurity GRC, moving beyond traditional, inefficient methods and siloed solutions. This is our answer to helping that boiling frog.
BCyber’s business evolution is underway. We have even started finding some like-minded ‘anti-boiling froggers’ and the business has been named a finalist in the 2024 and 2025 Australian AI Awards in the AI Innovator - Cyber Security category
And why am I telling you all this? Well, if you want to succeed you need to adapt. Let’s save those frogs together.
Evolution has three simple steps: see a problem, develop a solution and release it.
And for those whose interest has been piqued, or who are detail focussed, here are a few words about the evolutionary apps we have developed to help lift our clients out of that boiling pot.

Dynamic Mind Map provides an interactive visual guide for understanding cyber frameworks, making governance and education accessible. Where one activity allows you to meet the requirements for multiple frameworks eliminating double handling.
Paradigm is an enterprise-grade app offering a consolidated view of compliance frameworks (Essential 8, NIST, ISO 27001 etc), streamlining management, reducing complexity and cutting costs through features like a universal control framework and AI-powered consultants.
TopSpin delivers predictive data management, crucial for informed decisions, preventing costly data space shortages and ensuring service continuity.
PerfectStorm helps organisations prepare for breaches by using the MITRE ATT&CK framework
to build real-life scenarios, allowing for practice, identifying security gaps and prioritising defences.
Cyber Triage guides corporates through the initial steps of a data breach using AI for real-time, NISTcompliant incident classification to reduce response times, to prevent time being wasted on false positives and to mitigate the impact of breaches.
www.linkedin.com/in/karen-stephens-bcyber
www.bcyber.com.au x.com/bcyber2
karen@bcyber.com.au youtube.bcyber.com.au/2mux

Global CISO Programs Director
often say that I didn’t choose cybersecurity but cybersecurity chose me,” reflects Amandine Nury, Global CISO Programs Director. Back in 2018, she was working as a consultant in the Technology Strategy & Architecture practice at Deloitte Australia in Sydney. One day, the Cyber Advisory team needed someone who could manage a large project and translate highly technical findings into something the client’s C-suite could understand and act on. “I volunteered, just for what was supposed to be a three-month assignment,” she recalls.
That assignment proved to be a turning point. It was with Sydney Trains, focused on assessing the maturity of both their IT and OT environments and developing a strategy around it. “I was surrounded by brilliant subject matter experts, and I quickly became fascinated by the content and the real-world impact of our work,” Amandine says. “We weren’t just solving technical problems, we were helping, in a way, protect critical infrastructure that thousands of commuters relied on every day.”
“That experience opened my eyes to the purpose and impact behind cybersecurity. It wasn’t just about tech anymore, it was about people, safety, and trust. I joined the Cyber practice shortly after and have been immersed in the field ever since. Over time, my interest has only deepened as I’ve continued to explore the evolving landscape of cyber threats, resilience, and strategy.”
Amandine’s path was far from linear, and at times, it was marked by uncertainty. “Yes, I definitely experienced moments of uncertainty, particularly right after the COVID-19 pandemic,” she says. “I was about two and a half years into my cybersecurity journey at the time, and I found myself in a couple of projects that didn’t feel impactful. Without the right leadership and mentorship support, I started to lose sight of what initially drew me to the field.”
She sought help. “To navigate that period, I decided to work with a professional coach,” Amandine explains. “Through a series of reflective exercises,
I reconnected with some aspects of cybersecurity that truly motivated me. More importantly, I gained clarity on what I wanted to pursue, but also on what I didn’t. Those realizations weren’t necessarily about cybersecurity itself, but about the environment I was working in, which I believe is just as important, especially early in your career.”
Her journey has also been shaped by a willingness to embrace the unknown. “When I began my journey in cybersecurity, I didn’t have a clearly defined vision of the roles I aspired to. My path unfolded quite organically,” she says. “Part of the challenge was internal as I often questioned my place in the field because I entered cybersecurity later in my career and didn’t come from a technical background. I also resisted the idea of limiting myself to one niche or capability. What I did know, however, was that I had a strong drive to learn continuously, to never settle, and to apply what I learned to solve complex problems and contribute to broader cybersecurity strategies.”
In her current role, she is candid about the complexity of the work. “One of the most complex aspects of my role, especially from a non-technical perspective, is navigating the rapid evolution of the cybersecurity landscape,” Amandine explains. “As threats grow more sophisticated, the defensive tools and platforms we rely on are becoming increasingly specialized. This specialization is necessary, but it also introduces a challenge: the pace of tool adoption often outstrips the development of supporting processes and cross-functional alignment. This is where I believe governance plays a pivotal role. While it’s sometimes perceived as a bottleneck, I see governance as a strategic enabler. Governance, when well established, helps reduce silos, clarify ownership, and ensure that innovation doesn’t come at the cost of coordination. In my experience, strong governance is what allows organizations to move fast without breaking things.”
She is also attuned to the horizon of emerging threats. “There are definitely several emerging threats, but two stand out to me,” she shares. “The first is the threat posed by quantum computing. As this technology advances, the risk of it breaking current encryption standards and exposing sensitive data becomes very
real. It’s not just theoretical anymore, it’s a looming challenge that requires proactive planning today. The second is AI-driven cyber attacks. This one feels like a no-brainer, but it’s worth mentioning: AI is making attacks faster, more scalable, and significantly harder to detect using traditional methods. Whether at the corporate level or in our personal lives, we’re only beginning to understand how to defend against this new wave of intelligent threats… and that is scary as much as it is fascinating.”
Beyond technical focus, Amandine values roles that allow her to see the bigger picture. “Beyond remuneration, one of the most important factors I consider is the scope of the role, specifically, how much exposure it offers both within and outside the organisation,” she says. “I thrive in roles where I can connect the dots across teams, capabilities, and strategies. My motivation comes from thinking big, not just focusing on a single cybersecurity service or technical function, but understanding how everything fits together to drive business value. I don’t want to be a fish in a fishbowl, I want to be a fish in the ocean, with the freedom and perspective to navigate complexity and contribute meaningfully at scale.”
“Through a series of reflective exercises, I reconnected with some aspects of cybersecurity that truly motivated me. More importantly, I gained clarity on what I wanted to pursue, but also on what I didn’t. Those realizations weren’t necessarily about cybersecurity itself, but about the environment I was working in, which I believe is just as important, especially early in your career.”
“I used to believe, mistakenly and more than once, that you had to be highly technical to enter the field. While technical expertise is absolutely essential in many areas, it’s far from the only path. Cybersecurity is a vast, multidisciplinary space. We need people who are curious, eager to learn, and capable of connecting the dots across different domains."
She is passionate about encouraging others to enter the field, especially those from non-traditional backgrounds. “From my experience, one of the most important things I’ve learned is that there truly is a place for everyone in cybersecurity,” she says. “I used to believe, mistakenly and more than once, that you had to be highly technical to enter the field. While technical expertise is absolutely essential in many areas, it’s far from the only path. Cybersecurity is a vast, multidisciplinary space. We need people who are curious, eager to learn, and capable of connecting the dots across different domains. Various backgrounds and perspectives can add real value! So my advice is: don’t count yourself out. If you’re curious, adaptable, and driven to make an impact, there’s a place for you in cybersecurity. Your unique experience might be exactly what a team needs to see things differently and move forward more effectively.”
Amandine attributes much of her growth to the people she has met along the way. “I consider myself incredibly fortunate to have crossed paths with some truly inspiring leaders, coaches, and mentors throughout my cybersecurity journey,” she says. “From them, I learned that success in cybersecurity isn’t about knowing everything. It’s about being open to learning, staying curious, and understanding that soft skills can be just as powerful as technical expertise in driving meaningful outcomes. At the same time, I’ve also been deeply influenced by subject matter experts who’ve mastered a single capability with incredible depth. Their unwavering focus and delivery mindset showed me the value of precision, resilience, and execution under pressure. Cybersecurity is a team sport, and I’m grateful to have been surrounded by people who challenged me, supported me, and consistently offered feedback that helped me grow.”
For Amandine, the real satisfaction comes from the impact she creates. “What brings me the most satisfaction in my current role is the opportunity to connect the dots and solve complex problems alongside others,” she shares. “I genuinely enjoy working across teams and engaging with a wide range of stakeholders. It gives me a real sense of purpose to feel like we’re all part of one big team tackling meaningful challenges together. I especially appreciate the small wins that lead to big impact, and there’s nothing more rewarding than hearing from stakeholders that our work has made a difference. The excitement of what’s possible, how we can evolve, improve, and even influence things beyond our immediate scope, is incredibly energising. That sense of momentum and purpose is what makes this work so fulfilling for me.”
In her own words, Amandine Nury may not have chosen cybersecurity, but she’s made it her own— turning a three-month assignment into a career defined by purpose, impact, and the drive to shape the future of security.
www.linkedin.com/in/amandine-nury-95345914
For the past four years , Source2Create has proudly delivered Women in Security Magazine to the industry free of charge , championing diversity, inclusion, and the incredible contributions of women in cybersecurity. As we continue to grow, we now need partners to help us sustain and expand this vital platform.
By supporting this package, you’re not just backing us—you’re investing in the magazine, its community, and the future of women in security. To ensure we can keep delivering this high-value publication, we’re introducing a nominal fee for $900 Ex GST, an exceptional package that provides extensive coverage and visibility.






Cherie Burgett Director, Cyber Intelligence Operations
Cherie Burgett’s story begins with a spark of curiosity and a love for technology that would ultimately shape her life. “One of my first jobs was working at a Radio Shack in the 90s,” she recalls. “I was also really into playing video games and I would build my own gaming computers as a hobby. On a whim, I took a 4-day bus trip to Defcon, a major hacker conference in the US, and that is where I met the connections that led me to where I am today.”
For Cherie, attending conferences was the turning point that transformed her interest into a thriving career. “Attending conferences is what transformed my interest into a career,” she explains. “I met a lot of great people in the industry, learned a lot, and someone offered to mentor me to help me reach the next steps.” Today, as Director of Cyber Intelligence Operations, she leads with a sense of purpose born out of these formative experiences.
Working within the mining industry, Cherie has encountered unique challenges in her field. “The most complex challenges in working for the mining industry is that there isn’t a whole lot of research done within the sector as far as threat intelligence,” she says. “Working for the Mining and Metals ISAC, we are able to help address that by pooling resources and knowledge by sharing what intelligence we have to help build that bigger picture.”
Her journey has not been without moments of doubt. “Yes, for sure! I had a 15-year gap in my resume. I paused working outside the home to raise four children while my husband served in the military. When I decided I wanted to go back to work, I thought for sure the best I could do was working for Geek Squad. When they rejected me, I nearly gave up. But I continued going to conferences and learning all I could.” It was persistence and the encouragement of others that kept her moving forward.
Like many in cybersecurity, Cherie’s path unfolded organically. “Initially, I had no idea what I wanted to do,” she reflects. “But the process of obtaining industry certifications and exploring the various domains available led me to discover a passion for research and threat intelligence.”
Asked what advice she would give her high school self, she offers words of encouragement beyond the technical: “Pursue your interests: art, music, games, and puzzles. Many of the technical skills may be lost over time, but the pursuit of learning something new that you love will stay with you.”
Her view of education for aspiring cybersecurity professionals underscores this. “Humanities courses, such as psychology and philosophy, are often overlooked but essential in this field. For aspiring leadership roles, many CISOs recommend an MBA.”
Looking to the future, Cherie is both realistic and forward-thinking about the industry’s evolution. “We are still learning about the impact of AI on the industry, and quantum computing is closer than we think,” she says. “The geopolitical landscape is heating up, with countries like China and the Typhoons positioning themselves to cause serious disruption.”
When considering new career opportunities, Cherie weighs far more than salary. “I’d ask myself, do I respect/admire the leadership? Will I be challenged, and can I grow, either personally or professionally? And is what I am doing making a difference?”
One of the greatest influences on her career goes back to that first Defcon trip. “This goes back to the first person I was fortunate enough to meet at Defcon 11 years ago. Rob Labbe, after a couple of years of asking me why I wasn’t yet in the industry, convinced me that there was a place for me, took the time to mentor me, and helped me develop a personalized pathway into the industry.”
Professional development remains a priority for Cherie. “I am working on a CISSP, but I am also considering a couple of applied hermeneutic courses this year because I spend a lot of time interpreting written text.”
What she finds most fulfilling about her role today is the immediate impact of her work. “That is when I learn something new, such as a new tactic or information about a specific threat actor, and I can immediately share it with those who will benefit the most.”
Even in a demanding field, Cherie is intentional about maintaining balance. “I travel a lot for work and split the remaining time between a city apartment in Calgary, Canada, and a small homestead in Maine, US. I spend time with my family and pets, and I also tend to my garden. My homestead in Maine helps ground me, offsetting the fast-paced jet-setting life that my work life takes me.”
Her strategy for staying effective is rooted in curiosity and community. “I spend a lot of time reading current news articles and attending conferences and events to learn from others. It’s important to know what advances are being made in technology as well as what potential impacts that technology may have on cybersecurity.”
For those entering threat intelligence, Cherie highlights the tools that matter. “For a role in cyber threat intelligence, a good sandbox for safely investigating phishing and malware, threat intelligence research tools like Recorded Future, enrichment tools like Shodan for looking up IP addresses and domains, and a threat intelligence platform for sharing findings with the community.”
Cherie is equally passionate about lifting others up. “Honestly, we have the opposite problem in our organisation; there are so many amazing people with the right skills or aptitude that they can be trained. We don’t look for perfection on paper, we look for potential. Sometimes we find someone who is exceptionally motivated to learn, so we find a way to make it work. When we don’t have the resources to hire them, we often write referrals for these individuals to ensure their talents don’t go unnoticed.”
Her advice to those entering cybersecurity later in life is heartfelt: “Cybersecurity is a great career to start later in life. You have experience and wisdom that comes from living an interesting life, which will form a great foundation. We are not protecting machines from malicious code; we are protecting people from people.”
From a young woman building gaming computers for fun to a global leader in cyber intelligence operations, Cherie Burgett’s journey is a testament to resilience, mentorship, and the power of curiosity. Her path serves as both inspiration and roadmap for anyone seeking to make their mark in cybersecurity at any stage of life.
www.linkedin.com/in/cherieburgett

Faith Nsikak
SOC Analyst/Incident Responder
Faith Nsikak’s journey into cybersecurity began with a simple, relatable question: how could she protect her social media accounts from being hacked? “Back in 2018, I was curious about how to protect my social media accounts from being hacked. Account hacking was trending at the time, and I didn’t want to be a victim,” Faith recalls. “So I began learning how to secure my accounts using strong passwords, multi-factor authentication, and a password manager. At the time, I had no idea I was practicing basic cybersecurity, I just wanted to stay safe online.”
That initial curiosity quickly evolved into a deeper passion. “I never blindly trust anything online. I question voice calls, suspicious messages, emails, and links. I’ve faced many attempts, voice scams, phishing SMS, spam emails, but I’ve never fallen victim. I even took it upon myself to educate friends and family on staying safe online. Safety became a priority for me, and cybersecurity naturally became a part of who I am.”
Though Faith studied Sociology at university, her path took a technological turn during a church program that introduced her to coding. “I didn’t have a laptop then, so I started learning to code on my Android phone using platforms like freeCodeCamp. It was frustrating. By December 2018, a cousin gifted me a laptop, and I dove deep into HTML, CSS, and JavaScript. I stayed up late learning, attended meetups, watched YouTube tutorials, and set a personal goal to become a software engineer in five years.”
Challenges arose along the way. After graduating in 2019, Faith’s laptop was stolen while she served in Nigeria’s National Youth Service Corps (NYSC). “It was a tough time, but I didn’t stop. I continued learning with my phone and saved enough to buy another laptop in 2021,” she says.
Her breakthrough came in 2022 when a friend told her about the CyberGirls Fellowship, a seven-month intensive cybersecurity program for women across
seven African countries organised by Cybersafe Foundation. “Out of 3,000 applicants, I was one of 300 selected. The program was intense with handson projects and exams. I initially planned to combine coding with cybersecurity, but the program demanded my full focus,” Faith explains. She graduated with distinction, and the program opened doors to interviews and opportunities that would shape her career.
In 2023, Faith began her professional journey as a Cybersecurity Engineer with a Managed Security Service Provider (MSSP), earning the Exceptional Performer Award in October 2024. Earlier this year, she transitioned to a FinTech company as a SOC Analyst/Incident Responder. “Cybersecurity is dynamic; there’s never a dull moment. The field is always evolving, and I love knowing that my work helps protect people’s privacy and livelihoods,” she says.
Faith emphasises the importance of learning from challenges. “One of the most complex aspects of my current role is keeping up with the ever-evolving nature of cyber threats. The volume of alerts and incidents can be overwhelming, and making the right decision quickly is critical. To overcome these challenges, I’ve built a personal cyber lab, dedicate time to threat intelligence, and focus on cross-team collaboration. Every challenge is an opportunity to grow.”
Doubt was also part of her journey. “At the beginning of the CyberGirls Fellowship, I was torn between continuing my coding journey and diving fully into cybersecurity. A mentor reminded me that this was a rare opportunity, and coding could always be revisited later. That guidance gave me clarity, and I made the intentional decision to focus fully on cybersecurity. Looking back, it was the right choice,” Faith reflects.
Faith’s advice to her younger self underscores her philosophy: “Stay curious and don’t wait for the perfect conditions to start. Cybersecurity isn’t just about technical skills—it’s about solving problems, protecting people, and thinking critically. Every
setback is a setup for something greater. And most importantly, you belong here.”
She highlights essential areas for aspiring cybersecurity professionals: “Focus on computer science fundamentals, networking, operating systems, cybersecurity principles, programming, digital forensics, ethical hacking, and cloud security. Complement theory with hands-on labs, challenges, internships, and community involvement.”
Looking forward, Faith sees AI-driven threats, cloud security, and identity management as pivotal. “Attackers are using AI to automate scams and evade detection. Organizations are shifting to the cloud, making misconfigurations and poor access control risks. Identity is the new security perimeter, and Zero Trust models are critical. The field will continue to demand continuous learning and adaptability.”
Faith also emphasizes the value of community and mentorship. “I’m a member of Diary of Hackers and WiCyS. These communities have provided mentorship, exposure, and opportunities that accelerated my growth. I landed my first job through a referral from someone I met in the community.”
Her journey from protecting her own social media to defending complex enterprise systems demonstrates resilience, determination, and passion. “The most fulfilling part of my role is knowing that my work directly protects people and systems from real threats. No two days are the same, and every incident is an opportunity to learn and improve. Cybersecurity has purpose, and that sense of impact keeps me motivated and proud to be in this field.”
Faith Nsikak’s story is a testament to curiosity, persistence, and the power of embracing opportunity. From humble beginnings to an award-winning cybersecurity professional, her journey shows that passion, focus, and continuous learning can transform a simple interest into a meaningful, impactful career.
www.linkedin.com/in/faithnsikak-cybersecurityprofessional

Sana Talwar
Product Security Engineer
For Sana Talwar, a Product Security Engineer, the spark that ignited her passion for cybersecurity began early in high school. “My journey into cybersecurity started when I participated in the CyberPatriots Competition and Technovation Challenge,” she recalls. “Here I was able to secure vulnerable systems and build an app concept to solve a community problem. Those experiences showed me how technology can create change.” What began as curiosity quickly evolved into a lifelong commitment to protecting systems and data. “Over time, I became drawn to the idea of protecting systems themselves, keeping them trustworthy and secure,” she says. “Today, as a Product Security Engineer, I work with development teams to build security into products from the start.”
Turning that early interest into a professional pursuit took dedication and a clear focus on building technical depth. “Early on, I focused on building a technical foundation. I studied computer science,
completed security-focused internships, and earned hands-on certifications,” she explains. Capture the Flag (CTF) competitions and research projects gave her the real-world exposure she needed to apply theory to practice. “Those experiences in offensive security helped me understand how attackers think which makes me a better defender.”
“Cybersecurity benefits from diverse backgrounds: developers, analysts, and even educators bring useful perspectives. Start small, get hands-on experience, and keep learning. The best security professionals stay curious.”
“Learning in cybersecurity is continuous, and no one knows everything. Stay curious, ask questions, and take opportunities even if they seem out of reach.”
Yet, even with strong technical expertise, Sana admits the biggest challenge isn’t always in the code. “The most complex part is balancing security and business priorities,” she says. “As a Product Security Engineer, I work closely with developers and product teams, so I focus on building relationships and communicating security issues in a way that supports innovation instead of blocking it.”
Her journey hasn’t been without uncertainty, but Sana believes that doubt can be a powerful motivator. “Don’t wait to feel ready before you start,” she advises. “Learning in cybersecurity is continuous, and no one knows everything. Stay curious, ask questions, and take opportunities even if they seem out of reach.” Her willingness to explore has been instrumental in shaping her path. “The best thing I did was a variety of internships in different specialties. I got to try things, figure out what I like doing.
When it comes to education, Sana encourages aspiring cybersecurity professionals to focus on the fundamentals. “Computer science, networking, and operating systems are key,” she says. “Students should also learn scripting, web technologies, and cloud concepts early. Understanding how systems are built makes it easier to understand how they break.”
Looking ahead, Sana is closely watching the evolution of artificial intelligence in cybersecurity. “AI integration will shape both attack and defense,” she notes. “We’ll see more automation in threat detection and code analysis, but also more AI-driven social engineering and prompt injection attacks that target trust in data and systems.”
Mentorship has played a defining role in her professional growth. “Early mentors encouraged me
to explore offensive security, and later ones helped me see how to align technical depth with business impact,” she reflects. “That balance guides how I approach my work today.”
In a field that often demands long hours and constant vigilance, Sana is deliberate about maintaining balance. “I set clear boundaries and take breaks away from screens,” she says. “Outside of work, I focus on activities that reset my mind doing yoga and meditation, reading, or connecting with friends and family.”
Staying current is another non-negotiable. “I follow security researchers, read advisories, and take part in security communities,” she explains. “I also dedicate time each week for learning whether it’s a lab, a writeup, or a new podcast or YouTube video.”
For those transitioning into cybersecurity from other fields, Sana’s message is clear: every skill counts. “Leverage your existing skills,” she says. “Cybersecurity benefits from diverse backgrounds: developers, analysts, and even educators bring useful perspectives. Start small, get hands-on experience, and keep learning. The best security professionals stay curious.”
From her high school competitions to shaping secure products in the corporate world, Sana Talwar’s journey is a testament to the power of curiosity, persistence, and purpose. In her own words: “Security isn’t just about defending systems it’s about empowering people and technology to thrive safely.”
www.linkedin.com/in/sana-talwar

Cyber Psychologist & Psychotherapist, Founder Cyber Wellness Foundation, Director of V4WEB, A Web Solutions & Cyber Security Company
Nirali R Bhatia’s cybersecurity career is far from conventional. “My entry into cybersecurity wasn’t through a traditional IT pathway—it began with a deep fascination for human behaviour in the digital space. Being a usability analyst & running a web company got me focusing on the users and how the web impacts their decisions. I realised early on that the most sophisticated security systems could be bypassed not by code, but by manipulating people. Over time, this curiosity evolved into a commitment to bridging psychology with cybersecurity—helping individuals and organisations understand that technology alone cannot solve the human factor in security.”
Her pivot from curiosity to a professional pursuit was shaped by her work on cyberbullying and online safety cases. “The turning point came when I began working on cyberbullying and online safety cases. I pursued
certifications in internet addiction therapy and cyberpsychology, blending them with my two decades in technology & psychology. Speaking at schools, corporate forums, and law enforcement workshops gave me both the credibility and the platform to formally step into the cybersecurity ecosystem from a human-behaviour perspective.”
Yet, navigating this unique intersection of psychology and technology came with challenges. “The most challenging aspect is changing mindsets. People often underestimate the role of emotions, impulsivity, and cognitive bias in cybersecurity breaches. Cybersecurity is still understood as the IT or Tech stream career and it’s very difficult for people to comprehend the role of a psychologist in technology. I address this through storytelling, case studies, and experiential learning that make people feel the risks rather than just hear about them.”
"Bring your unique lens with you. Whether you come from law, education, psychology, or finance, your domain expertise can uncover vulnerabilities tech experts might overlook. Cybersecurity is richer when it’s interdisciplinary.”
Moments of doubt were inevitable. “Yes—especially because my path was unconventional. At times, I wondered if the industry would accept a psychologist in a field dominated by engineers. I navigated these doubts by staying evidence-based, continuously upgrading my skills, and letting results from my workshops and interventions speak for themselves.”
Her career path unfolded organically. “I didn’t set out to become a ‘cyberpsychologist’ because the term barely existed in mainstream In India or rather globally at the time. The role evolved as I responded to the rising need for someone to interpret human behaviour in digital crimes and risks, someone to counsel for the emotional invisible wounds of being a victim of whether a breach or a scam or bullying.”
Nirali emphasises the importance of interdisciplinary learning for aspiring cybersecurity professionals. “In addition to computer science and networking, I’d strongly recommend modules on behavioural science, criminology, digital forensics and ethics.” Looking ahead, she anticipates significant developments in the field. “One of the most impactful developments will be the rise of AI-augmented defense and adaptive threat hunting that uses generative and AI agents to detect anomalies in real time and anticipate socialengineering patterns. We’ll also see evolution in ransomware response, implementation of privacy by design, more sophisticated misinformation detection and integrity tooling, and hopefully the formal integration of psychological safety and mental-health support into incident response to preserve trust and wellbeing.”
She also foresees the most profound threats emerging from AI-driven manipulation. “In the next two years, the biggest cyber threat won’t be hackers breaking into systems, but AI breaking into minds. Beyond technical breaches, the most significant threats will be rooted in large-scale psychological manipulation… Combating this won’t just require advanced detection systems—it will demand building human firewalls through emotional literacy, cognitive bias awareness, and resilience training, so people can pause, verify, and resist manipulation.”
When considering career opportunities, Nirali prioritises purpose over pay. “I’d look at whether the organisation values the human factor in cybersecurity, offers scope for inter-disciplinary work, and is willing to invest in preventive education, not just incident response.” She credits the victims she has worked with for shaping her path. “Hearing their stories and seeing the emotional aftermath of scams, breaches reinforced my mission to make cybersecurity about people, not just systems.”
Nirali finds deep fulfillment in witnessing behavioural change. “When someone tells me, ‘I’ll never look at a suspicious link the same way again,’ I know I’ve created a behavioural shift. That’s more powerful than any firewall. What is most satisfying is when a cybercrime victim feels safe again online.” Maintaining balance is key: “While the field is demanding, thankfully my role gives me freedom to strike a healthy work life balance. Practicing digital well-being is the key and only then do I preach it.”
Her daily work spans counselling, training, consulting, and research. “No two days are alike, but a mix of them includes counselling victims, designing awareness modules, conducting training sessions, consulting schools or corporates on cyber safe practices, and reviewing the latest cybercrime cases for behavioural patterns.” Networking through professional organisations and NGOs keeps her grounded in interdisciplinary learning.
Her advice to those entering cybersecurity from other fields is clear: “Bring your unique lens with you. Whether you come from law, education, psychology, or finance, your domain expertise can uncover vulnerabilities tech experts might overlook. Cybersecurity is richer when it’s interdisciplinary.”
For Nirali, cybersecurity is ultimately about people as much as it is about technology. Through her work, she continues to illuminate the human side of digital safety, ensuring that as our systems evolve, so too does our understanding of the minds that interact with them.
www.linkedin.com/in/nirali-bhatia

Namrata Barpanda
Staff Information Security Engineer
For Namrata Barpanda, curiosity wasn’t just a spark, it was the fuel that ignited a lifelong passion for cybersecurity. “My initial interest in cybersecurity was sparked by curiosity about how systems could be both protected and exploited,” she recalls. “Early on, I was fascinated by how a small misconfiguration or vulnerability could open the door to large-scale breaches. I used to read forums, follow the news, and constantly ask myself, ‘How do these things happen?’ The more I learned, the more curious I became.”
That curiosity evolved into a deep professional pursuit. Namrata’s journey began with building a strong technical foundation in networking, operating systems, and security fundamentals.“I started by understanding how things work before learning how to secure them,” she explains. “I spent time in online labs, practiced ethical hacking, log analysis, and packet capture. There’s no shortcut in cybersecurity; it’s all about study, study, and study.”
Her persistence paid off. Each project, from security monitoring to identity management, transformed her theoretical understanding into practical mastery.
“Continuous learning, hands-on experience, and persistence helped me turn my interest into a solid professional path,” she says.
Now a Staff Information Security Engineer, Namrata thrives on tackling complex challenges. “One of the most challenging aspects of my role is dealing with the constantly evolving threat landscape especially zero-day vulnerabilities,” she notes. “Detecting and responding to such threats in real time requires both technical depth and collaboration across teams.” Her solution? “I focus on writing detection-as-code to proactively identify suspicious patterns and potential exploit behaviour. It’s all about designing smarter, detecting faster, and responding more effectively.”
But the journey hasn’t been without moments of doubt. “There were times I felt overwhelmed,” she admits. “As an Incident Responder, the 24/7 shifts and pressure to respond instantly to every alert were mentally and physically exhausting. I even considered switching roles.” What kept her going was remembering her ‘why’. “My curiosity and passion for solving complex problems reminded me why I started. I focused on smarter ways to work — automating repetitive tasks, documenting lessons learned, and improving response playbooks. Those challenges taught me resilience and balance.”
Namrata’s path wasn’t a straight line. “When I started, I didn’t have a clear vision of the exact role I wanted. I explored everything about network security, incident response, log analysis and learned through trial and error. Over time, I gravitated toward threat intelligence, detection engineering, and automation.”
If she could speak to her younger self, her message would be simple: patience, curiosity, and depth. “Cybersecurity isn’t something you master overnight. Learn the fundamentals networking, operating systems, scripting because you can’t secure what you don’t understand. Go beyond theory. Break systems in a lab, analyse logs, and explore why things work the way they do.”
Looking ahead, Namrata predicts the next few years will be shaped by AI-driven threats and identity-
centric security. “Attackers are using AI to automate reconnaissance and evade detection,” she explains. “Defenders will need to harness AI responsibly for behavioural analytics and faster incident response. Identity will continue to be the new perimeter, and automation will be central in SOC and DevSecOps.”
As for emerging threats, she’s keeping a close eye on AI-enabled attacks, supply chain compromises, and quantum computing. “AI is making attacks faster and more adaptive,” she warns. “And as quantum computing evolves, it poses long-term risks to cryptography and data protection.”
Namrata approaches career advancement with thoughtful precision. “Beyond remuneration, I consider whether a role allows me to deepen my expertise, grow through mentorship, and contribute meaningfully to an organisation’s security posture,” she says. “Work-life balance is also critical. Cybersecurity can be demanding, so I prioritise environments that value flexibility and collaboration.”
Mentorship has also played a defining role in her growth. “My previous manager and senior colleagues shaped how I think under pressure,” she reflects. “They taught me not just how to solve problems, but why certain approaches are more effective. That guidance along with my own curiosity has been instrumental.”
Currently, Namrata is pursuing advanced certifications to strengthen her technical and governance expertise. “I recently earned my AIGP certification, and I plan to pursue CISSP, SANS, and ISO 27001 Lead Auditor to deepen my understanding of compliance and risk management.”
What brings her the most satisfaction is seeing the direct impact of her work. “I love solving complex security challenges and making systems more resilient. There’s a sense of accomplishment when a detection rule catches a threat before it escalates or when automation improves efficiency. Mentoring others and collaborating across teams is also incredibly rewarding.”
Even with her demanding schedule, Namrata remains mindful of balance. “Maintaining work-life balance isn’t always easy,” she admits. “I plan my day, automate where possible, and set boundaries for after-hours work. Exercise, hobbies, and downtime help me recharge and stay focused.”
Her learning never stops. “I stay current through continuous learning following security news, participating in forums, attending conferences, and taking training courses. The community plays a huge role in keeping me sharp.”
Namrata is also an active member of organisations like ISACA, (ISC)², IAPP, MITRE, CSA, and SANS, which she says have enriched her professional journey. “These affiliations provide insights into evolving attack vectors, detection strategies, and industry standards. They’ve also helped me network, share knowledge, and stay proactive.”
Reflecting on the global skill shortage, she notes, “Roles like AI security engineers, incident responders, and compliance analysts are especially hard to fill. With AI-driven threats on the rise, we need more experts who can secure AI systems and ensure regulatory compliance.”
For those transitioning into cybersecurity, her advice is both practical and encouraging. “Stay curious, get hands-on, and build foundational skills. Read forums, follow real-world breaches, and experiment safely. It’s not about where you start, but how persistent you are. Every bit of effort adds up to confidence and expertise.”
Through curiosity, continuous learning, and an unwavering drive to adapt, Namrata Barpanda has built a career defined by purpose and growth. “Cybersecurity isn’t just a career,” she says with conviction. “It’s a mindset one that challenges you to stay curious, stay ethical, and keep digging deeper.”
www.linkedin.com/in/namrata-barpanda-0a9750a9


by Lisa Ventura MBE FCIIS , Chief Executive and Founder, AI and Cyber Security Association
Two technological forces are rapidly and fundamentally reshaping how we approach security: artificial intelligence and cybersecurity. This convergence represents more than a simple technological evolution; it constitutes a paradigm shift that needs urgent attention from leaders across industries, governments and civil society.
As AI systems become increasingly sophisticated and ubiquitous they simultaneously serve as powerful defensive tools and potential attack vectors. This duality creates a complex security ecosystem where traditional approaches to cyber defence are proving inadequate against emerging threats.
THE AI REVOLUTION IN CYBERSECURITY DEFENCE: BEYOND TRADITIONAL SECURITY MODELS
The limitations of conventional cybersecurity approaches have become increasingly apparent in our hyperconnected world. Signature-based detection systems, static firewalls and rule-based security protocols were designed for a different era, one where threats were more predictable and attack vectors more limited.
Modern AI-powered security systems represent a quantum leap forward in defensive capabilities. These systems leverage machine learning algorithms to

analyse vast datasets, identify subtle patterns and detect anomalies that would be impossible for human analysts to spot. The speed and scale at which AI can process information, analysing terabytes of data in real-time, provides a crucial advantage in an environment where threats can propagate globally within minutes.
The application of AI in cybersecurity extends far beyond basic threat detection. Behavioural analytics powered by machine learning can establish baseline patterns of normal user and system behaviour enabling the identification of subtle deviations that may indicate compromise. Predictive threat modelling uses historical data and pattern recognition to anticipate potential attack vectors before they materialise.
Automated incident response systems can execute complex remediation procedures in milliseconds, containing threats before they spread. Natural language processing capabilities enable the detection of sophisticated social engineering attempts, including context-aware phishing campaigns that adapt their messaging based on target profiles.
Perhaps most significant, though, is how adaptive learning systems continuously evolve their defensive strategies based on new threat intelligence, creating a dynamic defence posture that can respond to novel attack methods without human intervention.
THE DARK MIRROR: AI AS A CYBER WEAPON
THE WEAPONISATION OF INTELLIGENCE
The same characteristics that make AI a powerful defensive tool—autonomy, adaptability and scale— also make it an extraordinarily dangerous weapon in the hands of malicious actors. This weaponisation of AI represents one of the most significant security challenges of our time.
Autonomous attack systems can now operate independently, learning from each attempt and refining their approach without human oversight. These systems can conduct reconnaissance, identify vulnerabilities and execute attacks with a level of sophistication that was previously impossible.
Deepfake technology has evolved to the point where synthetic media can be generated in real-time, enabling unprecedented levels of impersonation and fraud. AI-powered social engineering can create
highly personalised phishing campaigns that leverage vast amounts of publicly available data to craft convincing communications.
The proliferation of AI tools and frameworks has dramatically lowered the barrier to entry for conducting sophisticated cyber attacks. Open-source machine learning libraries, commercial AI APIs and generative models are now accessible to individuals with minimal technical expertise.
This democratisation creates a profound asymmetry in the cyber domain. While defenders must secure every potential entry point, attackers need only find one vulnerability to exploit. The automation capabilities of AI amplify this asymmetry, enabling single actors to conduct attacks that would have previously required large, well-resourced teams.
NEXT-GENERATION THREATS
The intersection of AI and cybersecurity is giving rise to entirely new categories of threats that challenge fundamental assumptions about digital security.
These threats are characterised by their ability to adapt, scale and operate autonomously across global networks.
Polymorphic malware powered by machine learning can continuously alter its code structure to evade detection while maintaining its core functionality. AI-driven botnets can coordinate distributed attacks with unprecedented precision, learning from defensive responses and adapting their strategies in real time.
Supply chain attacks enhanced by AI can map complex digital ecosystems, identify the weakest links, and strike with surgical precision. Synthetic identity fraud leverages AI to create convincing false identities that can pass increasingly sophisticated verification processes.
The cybersecurity domain is experiencing an intelligence arms race where the ability to process information, identify patterns and respond rapidly has become the determining factor in security outcomes. This race is not just about computational power, it’s about the quality of data, the sophistication of algorithms and the speed of adaptation.
Adversarial machine learning represents a particularly concerning development. Attackers deliberately feed malicious data to AI systems to corrupt their learning processes or trigger specific behaviours. This creates a cat-and-mouse game where defenders must constantly evolve their models to resist manipulation.
The cybersecurity industry faces a fundamental skills shortage that is exacerbated by its convergence with AI. Traditional cybersecurity professionals often lack the data science and machine learning expertise needed to effectively deploy and manage AI-powered security systems. Conversely, AI specialists may not understand the nuances of security operations, threat landscapes and risk management.
This skills gap creates vulnerabilities that extend beyond individual organisations to affect entire sectors and national security. The demand for professionals who can bridge both domains far exceeds the current supply, creating a critical bottleneck in the deployment of effective AIpowered defences.
Organisations must invest in developing hybrid roles that combine cybersecurity expertise with AI fluency. This requires not just technical training but also a fundamental shift in how we approach professional development in both fields.
Cross-disciplinary education programs that integrate cybersecurity principles with data science methodologies are essential. Continuous learning platforms that enable professionals to acquire new skills rapidly are becoming critical infrastructure for organisational resilience.
Diversity and inclusion initiatives are particularly important in this context. Expanding the talent pipeline to include underrepresented groups, including women and neurodivergent individuals, brings
fresh perspectives and innovative approaches to complex problems.
ELEVATING AI SECURITY TO STRATEGIC
The intersection of AI and cybersecurity should be recognised as a strategic imperative that extends beyond the IT department. This requires fundamental changes in how organisations approach risk management, governance and strategic planning.
Board-level engagement is essential to ensure AI security receives appropriate attention and resources. Enterprise risk frameworks should be updated to account for AI-specific vulnerabilities and threats. Digital transformation strategies must integrate security considerations from the outset rather than treating them as afterthoughts.
Organisations must adopt architectures that are designed for resilience in an AI-powered threat environment. This includes implementing zero-trust security models that assume no entity is inherently trustworthy, continuous monitoring systems that provide real-time visibility into system behaviour and adaptive defence mechanisms that can respond to new threats automatically.
The establishment of organisations like the new global AI and Cyber Security Association (AICSA) represents a crucial step in addressing the challenges created by the intersection of AI and cybersecurity. Bodies like this exist as catalysts for collaboration, knowledge sharing and standards development across the AI and cybersecurity ecosystem.
Thought leadership initiatives help establish best practices and frameworks that guide organisations in developing secure AI systems while community
building creates networks of professionals who can collaborate on solving complex challenges that no single organisation could address alone.
Standards development processes ensure that security considerations are embedded into AI development practices from the beginning. Global coordination efforts help align regulatory approaches and facilitate information sharing across borders.
The regulatory environment for AI and cybersecurity is becoming increasingly complex with multiple jurisdictions developing overlapping and sometimes conflicting requirements. The European Union’s AI Act, the UK’s AI governance initiatives and similar efforts worldwide create a layered compliance environment that organisations must navigate carefully.
These regulations intersect with existing data protection laws, cybersecurity directives and industryspecific requirements, creating a complex web of obligations that can be difficult to understand and implement effectively.
The use of AI in cybersecurity raises profound ethical questions that extend beyond technical considerations. Surveillance capabilities enabled by AI systems must be balanced against privacy rights and civil liberties. Bias in AI models used for threat detection could lead to discriminatory outcomes or false positives that disproportionately affect certain groups.
Accountability frameworks must be established to ensure decisions made by AI systems can be explained and justified, particularly in highstakes environments where security decisions can have significant consequences for individuals and organisations.
Then, of course, there is shadow AI, which refers to the unauthorised or unmanaged use of artificial
intelligence tools and services within organisations, often deployed by employees without IT oversight or formal approval. Similar to the concept of ‘shadow IT’, shadow AI emerges when workers adopt AI-powered applications such as ChatGPT, GitHub Copilot or other generative AI tools to enhance productivity without going through proper security reviews or governance processes.
These practices create significant risks, including data exposure, compliance violations, intellectual property leakage and potential bias, or accuracy issues that could impact business decisions. Organisations are increasingly recognising the need to establish clear AI governance frameworks and policies to manage shadow AI while still enabling innovation and productivity gains, balancing the benefits of AI adoption with necessary security and regulatory controls.
Organisations should begin by conducting comprehensive assessments of their current AI and cybersecurity capabilities, identifying gaps and vulnerabilities that need to be addressed. Investment in hybrid talent through recruitment, training and development programs is also essential.
Pilot programs that demonstrate the effectiveness of AI-powered security tools can help build organisational confidence and expertise. Partnerships with industry bodies and other organisations such as AICSA can accelerate learning and reduce individual risk.
The convergence of AI and cybersecurity will continue to evolve rapidly, requiring organisations to maintain agility and adaptability in their approaches. Continuous learning and adaptation must become core organisational capabilities.
Innovation partnerships with research institutions, technology vendors and industry peers can help

organisations stay ahead of emerging trends and threats, while scenario planning exercises can help prepare for different potential futures and ensure that strategies remain relevant as the landscape evolves.
CONCLUSION: SHAPING THE FUTURE OF DIGITAL SECURITY
The intersection of AI and cybersecurity represents both the greatest challenge and the greatest opportunity facing digital security today. Organisations that embrace this intersection with foresight, collaboration and ethical clarity will not only secure their future but will help shape the digital landscape for generations to come.
The path forward requires the courage to embrace new technologies, the wisdom to anticipate their implications and the commitment to ensuring that the benefits of AI are realised while its risks are effectively managed. The future of digital security, and perhaps digital civilisation itself, depends on our collective ability to navigate this convergence successfully.
As we stand at this critical juncture, the decisions made today will determine whether AI becomes humanity’s greatest ally in the fight for digital security or its most formidable adversary. The choice is ours, and the time to act is now.
x.com/cybergeekgirl
www.linkedin.com/in/lisasventura
www.facebook.com/lisasventurauk
www.instagram.com/lsventurauk

bsky.app/profile/cybergeekgirl.bsky.social
www.youtube.com/@CyberSecurityLisa
www.linkedin.com/company/csunity
x.com/CyberSecUnity
www.facebook.com/CyberSecUnityUK
Lisa Ventura MBE FCIIS is an award-winning cybersecurity specialist, published writer/author, journalist and keynote speaker. She is the chief executive and founder of the AI and Cyber Security Association and Cyber Security Unity, a global community organisation dedicated to bringing individuals and organisations together who actively work in cybersecurity to help combat the growing cyber threat. As a consultant Lisa also provides cybersecurity awareness and culture change training along with neurodiversity in the workplace training and works with cybersecurity leadership teams to help them collaborate more effectively. She has specialist knowledge in the intersection of AI and cybersecurity, the human factors of cybersecurity/social engineering, cyber psychology, neurodiversity and diversity, equity, belonging and inclusion (DEIB). More information about Lisa can be found on www.lisaventura.co.uk or the Cyber Security Unity website www.csu.org.uk

By Joanne Cooper, Founder - ID Exchange
In the early days of the internet many people were not quite sure what the first web browsers represented, where information was presented in new graphic rich forms on demand. eBusiness was the catch phase, and publications went digital as the digital age surged ahead.
This connected era called for new regulatory regimes—guide rails, standards and appropriate policies—to provide assurance so the digital economy could operate efficiently with trust and adequate levels of governance. Meanwhile, tech startups sprouted everywhere, and tech titans became the powerhouses of the fourth industrial revolution.

Technology has continued to evolve. We are now witnessing the onslaught of artificial intelligence, robotics and machine learning enabled by network infrastructure with ever increasing power and speed. At the same time the possibility of data weaponisation has left many feeling uncomfortable about the impacts of increased surveillance and the threats to critical national infrastructure. We have all felt the impact of a sudden bank outage that left us high and dry when our e-payment device or plastic card failed to work.
As technology advances, are we on the threshold of another tech revolution, this time driven by AI agents? Is your constantly connected digital helper going to prove to be friend or foe? The jury is still out, but the stakes are getting higher and a data fuelled future is unfolding, with or without the individual’s comprehension of what it brings.
In the early days the web was decentralised and peer-to-peer. But over the last three decades the internet ecosystem has been carved up and captured by dominant players. Layer by layer, interface by interface, device by device the web gets bigger. Tech giants control the network infrastructure, the pipes to

feed the distribution channels, the algorithms and the digital storefronts. Crucially, they own access to you and I.
However, as customers we still have a level of control over our access connections and what we do with the data about us that flows through them.
Consider this: the 2020 Australian Community Attitudes to Privacy Survey (ACAPS) conducted by the Office of the Australian Information Commissioner, (OAIC) found that:
• 70 percent of Australians see privacy as a major concern.
• 59 percent have experienced mishandling of their personal data, including its collection and use without their full understanding or consent
But what if we flipped the script and consumers control over the value of their personal data and how their personal data is used rather than these parameters being determined by service providers?
Could AI agents work for us individually to achieve this, and turn the data economy on its head?
From our seat at ID Exchange we see this rise of AI agents as the opportunity for a redistribution of digital power. What if instead of being mined, profiled and monetised, people controlled their data and access to their personal information through real-time opt-
in and opt-out mechanisms under domestic and international data protection and privacy laws? What if we made consumers more active participants in the digital economy with compliance tools that worked in their favour to manage their data rights?
This is the promise of human-centric, bilateral data consent where individuals own and control their personal data—the raw material that fuels AI—and hold the power to grant, revoke or limit access to their data based on context, time or intent.
It’s not just privacy, it’s digital equity
Imagine a system in which your personal data lives in a secure, user-controlled digital wallet, one to which every AI platform or agent that wants access must request permission.
Such a system would enable you to opt in or out of sharing your data for specific uses, in near real-time, and to grant consent not with a one-time checkbox but through a dynamic, verified, living agreement that is specific to the use and the data sets involved, equally revocable with the right to be forgotten.
With such controls in place, data becomes trustenabled infrastructure. And this architecture does something radical: it levels the playing field. Suddenly, individuals aren’t just giving away data for convenience. They’re curating access and in doing so offering AI platforms higher quality, permissioned, ethical data, on their terms.
This isn’t just a shift in user experience; it’s a shift in economic power.
This is no longer simply a tech revolution, it is a personal rights revolution, and it’s long overdue.
www.idexchange.me
www.linkedin.com/in/joanne-cooper-50369734
x.com/idexchange_me





by
Erin Carroll , Consultant, Business Resilience and Cyber Risk, KPMG
Shruti Kamath , Consultant, Business Resilience, KPMG
Maryam Moradi , Consultant, Tech Risk & Cyber Consulting, KPMG
Sakshi Kishore , Associate Director, Tech Risk and Cyber Consulting, KPMG
Jay Hira , Cyber Director – Financial Services, KPMG
For years, flying the plane was the only thing that mattered. The flight path was a straight line, the engines were humming, systems stable, and our focus fixed on one thing: getting the aircraft from point A to point B. We were so good at the mechanics of the flight that we almost forgot about the people in the seats behind us.
But the new era of digital financial services has changed the flight plan entirely. With an astonishing 99.3 percent of banking interactions now happening through digital channels, the journey is no longer just about flying the aircraft; it’s about protecting every passenger, every step of the way.
This shift perfectly mirrors the new operational risk requirements outlined in APRA’s CPS 230 This regulation, which came into effect on 1 July, is like a new set of flight safety protocols. It expands our responsibility from the aircraft to the entire passenger experience. The standard applies to a broad set of financial services organisations, from banks to super funds to insurers.
The Australian Banking Association’s (ABA) Bank on It: Customer Trends 2025 report is our new flight manifest, revealing that our passengers’ priorities have fundamentally shifted. Today, customers care most about data security, fraud protection and privacy. This means our new flight plan must address a new kind of turbulence: the rising tide of scams and financial crime.
What’s striking is how resilience is being reframed, not as a defensive posture, but as a strategic differentiator. The financial institutions that can maintain service, protect data and adapt under pressure will retain trust. Resilience now means seamless digital experiences, secure platforms and the ability to pivot quickly when systems fail or threats emerge.
The old flight plan assumed that a major disruption was a system outage or a broken engine. But the modern journey faces a new, far more insidious form of disruption: a high-profile scam or data breach
that can erode customer confidence in minutes. The ABA report highlights that phishing, identity theft and unauthorised transactions are becoming increasingly common.
Under CPS 230, ‘material disruption’ is measured not only in terms of reputational damage but is now explicitly defined through levels of disruptions to critical operations, data loss and services.
This forces us to ask some provocative questions:
• How do we define ‘material disruption’ not just in terms of a system outage, but in the context of customer confidence?
• Should our resilience frameworks be prioritising the needs of our customers as much as the needs of the institution?
• Should we be thinking about “customer and ecosystem centric tolerance levels’ alongside our operational tolerance levels?
This is where the real ‘Aha!’ moment happens. Resilience isn’t just about recovery, it’s about reputation. No amount of backup systems can protect against a reputational crisis if customers feel their financial institution doesn’t have their best interests at heart. And in today’s environment that includes safeguarding them from scams and financial crime.
CPS 230 is our new flight plan, and it compels us to be more than just pilots; we must become captains of trust. The standard provides a perfect platform for us to go further and build resilience that is customercentric and inclusive of the broader ecosystem.
The standard and its accompanying guidance reflect many aspects of better practice in operational risk management globally. APRA has given regulated entities more flexibility in how they achieve stronger resilience outcomes by applying a risk-based approach. The standard came into force on 1 July 2025. It’s worth remembering that non-significant financial institutions have an additional 12 months to comply with specific requirements related to business continuity and scenario analysis. This is more than

just compliance; it’s about building a safer, more resilient journey for everyone on board.
The flight crews (financial institutions) that are leading the way aren’t just focused on compliance; they’re using CPS 230 as a catalyst to rethink their entire approach to the flight journey: operational risk, customer outcomes and the overall financial ecosystem. This is where we tie our proactive compliance efforts to the core themes of preparedness, resilience and effective service provider risk management.
This mission is twofold: protecting our passengers and safeguarding the entire financial ecosystem.
We can use our uplift in capabilities to:
• Elevate fraud detection. Strengthen fraud detection systems using advanced technologies like AI and machine learning to proactively spot threats and keep our passengers safe.
• Empower our passengers. Improve customer education about scams, ensuring our customers are equipped to recognise and avoid fraudulent activities.
• Coordinate with ground crew . Strengthen collaboration between banks, regulators and law enforcement to combat financial crime, much like coordinating with air traffic control to ensure a safe journey for all.
This is a fundamental shift in our role. We’re not just flying the aircraft; we’re safeguarding trust at every altitude. As we chart this new course, it’s clear that resilience in the CPS 230 era isn’t just about following a checklist; it’s about making deliberate choices at every altitude. Choices that protect not only the aircraft, but every passenger on board, and the trust that keeps our industry flying.
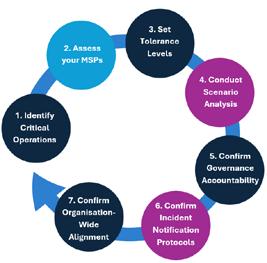
Before take-off regulated entities are expected to complete some key pre-flight checks to ensure resilience is operational, customer focused and inclusive of the financial ecosystem. This isn’t a checklist to pass an audit, but the foundation for being a captain of trust.
• Identify critical operations. These are the functions that, if disrupted, could materially impact customers or the financial system. They include, at a minimum, payments, deposit-taking, custody, settlements/clearing (for ADIs), claims processing (for insurers), investment management and fund administration (for super funds) and customer enquiries with supporting systems. This is your essential operational footprint.
• Assess your material service providers (MSPs). Evaluate interdependencies, risk profiles and contingency plans. A chain is only as strong as its weakest link. We must know the strength of our ground crew.
• Set tolerance levels. Define appropriate tolerances for service disruptions and evaluate their impact on customers.
• Conduct scenario analysis. Simulate severe but plausible operational risk events to assess your capacity to adhere to established tolerance levels. We build resilience by learning from near-failures.
• Confirm governance accountability. Just as every flight has a captain and crew with defined responsibilities, CPS 230 makes it clear that the board is ultimately accountable for operational resilience, with senior management responsible for day-to-day execution and reporting. This governance structure ensures oversight and accountability at every level.
• Confirm incident notification protocols. Review processes to meet APRA’s requirements. Entities must notify APRA of material operational incidents within 72 hours and within 24 hours if a critical operation falls outside tolerance.
• Confirm organisation-wide alignment. Verify that CPS 230 requirements are consistently applied across all entities within the group, including risk frameworks, tolerance levels and governance structures.
CPS 230 isn’t just a compliance exercise; it is a chance to lead with trust and resilience. By embedding its principles into our organisations we move away from basic compliance checks to ensuring meaningful, risk-aware decisions that protect customers and the financial system.
This is our opportunity to not just fly safely, but to lead confidently into a more resilient financial future. Are we ready to chart our new flight plan and become the captains of trust?
www.linkedin.com/in/erinlouisecarroll
www.linkedin.com/in/shruti-kamath
www.linkedin.com/in/maryam-moradi-61133527b
www.linkedin.com/in/sakshikishore
www.linkedin.com/in/jayhira
Madhuri Nandi, Head of security at Nuvei, AWSN Board Chair, author of Cyber Smart

Cybersecurity has changed dramatically over the past 20 years. What started as a purely technical function has now become a strategic driver of business resilience and innovation. Along the way we’ve seen advances in defensive tools, new ways of responding to incidents and a clear shift in the roles people play in this space.
Back then, security was all about reacting. Firewalls, intrusion detection systems and endless log reviews formed the foundation. They worked, but they also buried teams in alerts, most of which turned out to be false alarms. Burnout and alert fatigue were inevitable.
AI has completely changed this picture. Instead of drowning in data, teams now have tools that can spot patterns and anomalies in real time. Think of AI catching the smallest shift in network traffic, something a human might easily overlook, and flagging it before it snowballs into a major breach.
Of course, AI is not perfect. Relying too heavily on AI can backfire if models are poorly trained or manipulated by attackers. The real power lies in combining AI’s speed with human judgment and expertise.
Incident response used to live in a silo. Security teams focused on containment and fixes, often without seeing the bigger business picture. Today, it’s different. Response is integrated into operations with a sharp focus on business continuity, reputation compliance.
Take the 2017 NotPetya attack. It was a wake-up call that showed how a single cyber event could disrupt global operations, proving that resilience goes far beyond technical patching.
Modern response is agile and collaborative. Threat intelligence, cross-team coordination and lessons learnt after every incident are now the norm.
The people side of cybersecurity has transformed just as much as the technology. Analysts are no longer just watching screens for alerts; they’re translating data into business risk. Engineers are embedding security into every step of product development. And CISOs have moved from technical overseers to trusted business advisors, helping boards and executives make risk-informed decisions.
This shift proves one thing: technology alone can’t solve cybersecurity. Success depends on people, their skills, their awareness and their ability to weave security into the culture of an organisation.
The journey of cybersecurity reflects the speed at which the digital world keeps moving. To stay ahead, organisations must embrace smart technologies like AI, build incident response frameworks that are tied to business goals and invest in people who can lead with both technical and strategic thinking.
Cybersecurity today is no longer just about protecting systems. It’s about enabling business, driving innovation and ensuring long-term resilience in a connected world.
www.linkedin.com/in/madhurinandi

By Marina Toailoa, Business Risk & Compliance
My journey into the realm of security has been unconventional, leading me from the dark realities of correctional facilities to the heart of our communities, driven by a singular, powerful purpose: to empower parents and protect the most vulnerable among us. This article is the story of that transformation, of how a career focused on the consequences of crime illuminated the urgent need for proactive protection, leading to the birth of the Mummy Safety Security Project
My professional life once revolved around the complex, often challenging, environment of correctional facilities. It was a world of strict protocols, intricate security measures and with a constant focus on managing risk. When I first stepped into that world my understanding of crime was largely theoretical, shaped by legal frameworks and societal narratives. However, the daily realities of those environments quickly reshaped my perspective. I encountered individuals whose lives had been irrevocably altered by their actions, but more profoundly, I bore witness to the devastating ripple effects of crimes, particularly those that touched the innocent.
It was within this environment that I began to see a recurring and deeply disturbing thread: the pervasive issue of crimes committed against children. These weren’t just statistics; they were stories, often heartbreaking, that underscored a critical vulnerability in our society. I always struggled to deal with incidents and operations involving children who were the victims. The sheer volume and nature of these cases was a stark awakening. It became clear that, while the justice system dealt with the aftermath, there was a desperate, unmet, need for preventative measures, for knowledge that could shield our children from harm before it occurred. This realisation wasn’t just professional; it was deeply personal, and hit me hard.
As a mother, these insights struck me with unparalleled force. The theoretical understanding of crime transformed into a very protective instinct. I began to scrutinise every aspect of my own children’s safety with a newfound intensity, applying the lessons learnt from the most difficult circumstances. I delved into understanding the nuances of vulnerability, the tactics of predators and, crucially, the practical

strategies for deterrence and protection. This wasn’t just about my family; it was about every family. The knowledge I gained from such a challenging environment felt too vital to keep to myself. It ignited a burning desire to share these critical protection tips with the larger community so that, together, we could build a stronger, safer shield around all our children.
The realisation that the very strategies used to understand and mitigate criminal behaviour could be inverted and applied to preventative child protection became the cornerstone of my new mission.
My goal was clear: to translate complex security principles and real-world insights into accessible, actionable protection tips for parents and caregivers. This project is built on the belief that empowerment, not fear, is the most potent tool in a parent’s arsenal. We aim to equip families with the knowledge and confidence to navigate the modern world’s challenges, from the digital landscape to physical environments.
The Mummy Safety Security Project focuses on critical areas vital for contemporary child safety. We delve into the complexities of online safety, teaching parents how to create secure digital environments and foster responsible online habits. We address antibullying strategies, empowering children and parents to identify, prevent and respond to bullying effectively.
Emergency preparedness is another cornerstone, ensuring families have the plans and skills to act decisively when unforeseen events occur. We also emphasise situational awareness and public child safety, providing practical techniques for navigating public spaces with confidence and addressing the ever-present concern of stranger danger by teaching children vital personal boundary skills. Each module is meticulously developed to be practical, relevant and easy to implement, ensuring every parent can become their child’s most effective security agent.
Child safety is not, and cannot be, a solitary endeavour. It is a collective responsibility, a shared commitment that requires the active participation of every member of our community. My experiences have reinforced the undeniable truth that, when we work together, when we share knowledge and support one another, we create an impenetrable shield around our children. The project actively seeks to foster this sense of collective responsibility, transforming isolated concerns into a powerful, unified front.
Looking ahead, the vision for the Mummy Safety Security Project is ambitious yet deeply rooted in necessity. We aim to scale our reach significantly, extending our training and resources to 200 schools across Sydney within the next year. This expansion is not merely about numbers; it’s about initiating a broader, national conversation about child protection, elevating awareness and embedding safety as a fundamental value into every household. We envision a future where every parent feels equipped, every child feels secure, and every community stands united in its commitment to protecting its youngest members.
This is more than a project; it’s a movement, building a legacy of safety, one family, one school, one community at a time. By empowering parents with knowledge, fostering community collaboration and promoting proactive safety strategies, we are not just reacting to threats; we are building a resilient future.
www.linkedin.com/in/mia-azar-toailoa-66259511a
www.instagram.com/mummysafetysecurityproject
Something special unfolded recently in Xero’s Auckland office.
A collaboration between Xero, Secure Code Warrior (SCW) and She Sharp brought together an inspiring group of 60 women interested in technology for a day of hands-on learning, connection and empowerment, the Code Secure. Lead the Future: Women in Cybersecurity event.
This was not just another technology workshop. It was a vibrant, gamified experience that gave participants a supportive and encouraging environment in which to explore the world of application security and learn how to write secure, resilient code.

“You didn’t just attend an event: you built connections, formed a community and proved that the future of cybersecurity in Aotearoa is diverse, brilliant and unstoppable.”
Secure Code Warrior designs learning platforms that make security second nature for developers. Through interactive challenges and real-world coding scenarios its tools help transform cybersecurity from a checklist task into a habit of excellence, encouraging developers to think securely from the very first line of code.
At the heart of the event was She Sharp, a non-profit organisation working tirelessly to close the gender gap in STEM, one woman at a time. The organisation connects women with mentors and opportunities that help them build confidence, technical skills and leadership potential. Events such as this bring that mission to life, creating space for women to learn, collaborate and realise what is possible when barriers are replaced with belonging.
The event featured a remarkable line-up of speakers who shared their wisdom and personal experiences.
• Suzy Clarke, executive general manager of security at Xero, set the tone with her three guiding principles: resilience, growth mindset and reflection. She reminded attendees that these qualities form the foundation for learning and thriving in cybersecurity.

• Dr Mahsa McCauley, founder of She Sharp, encouraged participants to adopt what she calls a ‘spongy mindset’ in the ever-evolving world of AI. “Soak, squeeze and spring back. Soak in the best, let go of the rest, and keep learning, unlearning and relearning,” she says.

• Fatemah Beydoun, chief customer officer at Secure Code Warrior, offered a powerful reflection on confidence and presence, saying: “In maledominated spaces, never doubt your place or your voice. Others will see you the way you see yourself.”
• Mehika Manocha, lead software engineer at Xero, spoke about courage and community, highlighting how surrounding one’s self with the right people can make all the difference.
• Xero organiser, Ben Amadi, who is a senior cybersecurity education analyst at Xero, shared his perspective on LinkedIn after the event.





“To every woman who showed up on Friday: your active engagement, curiosity and willingness to dive into challenges you’d never faced before were absolutely inspiring,” he says. “You didn’t just attend an event: you built connections, formed a community and proved that the future of cybersecurity in Aotearoa is diverse, brilliant and unstoppable.”
Xero’s role as host was integral to the event’s success. Its support, leadership and hospitality provided an environment where learning, inclusion and collaboration could flourish. It was a clear demonstration of Xero’s commitment to building a more diverse and secure technology community.
Behind the scenes a dedicated planning committee— Jeanette Gill, Smita Pati, the She Sharp team, Ben Amadi and Mehika Manocha—made it all happen. This diverse team worked tirelessly to ensure every detail of the Code Secure. Lead the Future event ran smoothly; from speaker coordination to the engaging, hands-on challenges. What started as a simple conversation between colleagues has now produced a measurable ripple effect, giving talented women ways to enter or advance in the field, and successfully creating a supportive community that continues to grow beyond the event day.
The Code Secure. Lead the Future: Women in Cybersecurity event became more than a day of learning. It served as a reminder of what can be achieved when organisations unite around a shared purpose: empowering women, strengthening communities and shaping a safer digital world for everyone. Participants left with new skills, new friendships and a renewed sense of confidence, ready to continue their journeys in cybersecurity.
The most exciting part? This was just the beginning. The energy, the connections, the enthusiasm among attendees were palpable. Participants are already asking for this to become an annual event. The appetite for practical, hands-on learning and mentorship for women in cybersecurity across the region is undeniable. #SheSecuresAotearoa is here. And it’s only going to get stronger.
Follow Xero, Secure Code Warrior (SCW) and She Sharp on social media so you don’t miss out on future opportunities to learn and connect.
www.linkedin.com/company/xero
www.facebook.com/xero
www.instagram.com/xero
www.nz.linkedin.com/company/shesharpnz
www.facebook.com/shesharpnz
www.instagram.com/shesharpnz
SECURE CODE WARRIOR
www.linkedin.com/company/secure-code-warrior
www.instagram.com/securecodewarrior


in
Are you a student passionate about shaping the future of security? Do you have innovative ideas and insights to share with a global audience? Join us in contributing to the Women in Security Magazine and become a voice for the next generation of security leaders!
Gain valuable exposure: Reach over 11000 subscribers globally and showcase your expertise to industry professionals.
Make an impact: Share your experiences, challenges, and aspirations to inspire others and shape the future of security.
Let us know you are interested. We will send you a series of questions of which you can choose which ones you would like to answer. Submit those back to us in an email. We will then edit to be a concise and flowing edited Q&A.

Don't miss this opportunity to be part of a vibrant community of students driving change in the security industry. Contact us today to learn more about how you can contribute to the Women in Security Magazine!
Contact: jane@source2create.com.au

AKINDEHIN
By Ibitola Akindehin , AI Governance Risk and Compliance Specialist
Bridging the gap between checkboxes and compassion in the age of algorithmic power
“Is this system fair?”
“Can this algorithm harm someone?”
“Would I trust this if I didn’t build it?”
These are not just technical question; they are deeply human ones. And yet so much of AI governance today still feels like it lives in the world of spreadsheets, policy documents and audit trails, as though we can regulate machines without understanding people.
As someone working in governance, risk and compliance (GRC), I’ve seen how organisations often start their AI risk conversations with legal checklists or compliance frameworks. That’s important. But if that’s where it ends, we miss the heart of the issue: AI doesn’t just need governance. It needs empathy. It needs ethics. It needs humans who care not just about regulations, but about real lives.
This article explores the shift from treating AI governance as a compliance function to embedding it into the culture of organisations; a culture where human judgment, inclusion and accountability drive our systems, not just our policies.
WHY COMPLIANCE IS NO LONGER ENOUGH
When companies talk about AI governance the first thing they often reach for is a policy or a control framework: ISO 42001, NIST AI RMF or the EU AI Act. These frameworks are essential; they give us structure, accountability and global standards. But here’s the problem: compliance can be met without actual care.
You can check every box and still deploy an AI system that marginalises communities, reinforces bias or creates harm. If the people using these frameworks don’t understand why fairness matters or don’t feel safe raising concerns internally, then compliance creates a false sense of security.
We’ve seen examples already: a major tech firm scoring well on internal AI ethics reports while its facial recognition system misidentified people of colour; a hiring algorithm screening out qualified female applicants, not because of a malicious coder, but because the historical data was biased. None of these failures were purely technical: they were cultural.
Culture shapes how risk is identified, who gets heard in a room and what gets flagged before deployment. If fairness, transparency and responsibility aren’t part of the everyday conversation , no checklist can save us.
Let’s be honest: governance documents don’t talk back. People do.
An AI ethics guideline sitting in a shared folder won’t challenge a risky decision. But a data scientist who feels empowered to raise ethical flags — that can change outcomes.
Building an AI governance culture means:
• Creating psychological safety: where junior engineers can ask, “Is this right?” without fear.
• Diversifying decision-making teams: because lived experiences shape how risks are seen and understood.
• Encouraging slow thinking: not every AI model needs to be deployed just because it works. Sometimes, the right move is to pause.
One of the companies I worked with had an internal AI red team, a voluntary cross-functional group that tested models for fairness, security and explainability. Its members were not compliance officers, they were curious employees with diverse perspectives. And guess what? They caught risks that formal audits missed, because they were trained to think like humans, not just auditors.
That’s the power of culture: it lives in conversations, not control sheets.
Too often, ‘governance’ sounds like something done to teams, top-down reviews, red tape or latestage vetoes. However, true governance is shared. It’s embedded early. And it empowers.
If you want your AI governance to be more than performative, ask:

• Are governance conversations happening across teams, not just in the legal department?
• Is AI accountability part of onboarding, not just training slides?
• Do users or affected communities have a voice in how systems are built or corrected?
Governance should feel like a conversation, not a constraint. When people understand why certain risks matter, they become champions not resisters.
In African contexts—where community, trust and lived experience are vital—this shift is even more urgent. The systems we build must align with local realities, not just imported policies. A human-centred approach ensures that AI works with us, not around or above us.
AI governance is evolving, and so must we. What worked in the era of data protection audits won’t be enough for a world where autonomous systems make hiring decisions, assess credit risk or interact with children.
We need policies, but more importantly, we need people who care enough to challenge those policies when necessary.
Let’s stop thinking of AI governance as something you ‘install’ and start thinking of it as something you nurture. Let’s build cultures where trust, transparency and empathy aren’t buzzwords but behaviours.
Because, in the end, every algorithm affects a human life. And it’s time our governance systems reflected that truth.
www.linkedin.com/in/ibitola-akindehin

By Marise-Marie Alphonso, Cyber Security GRC Specialist
Effective discussions on information or cybersecurity risk management require a multi-faceted approach with cross-dimension linkages and the consideration of dimensions such as possible threat actors, threat events, vulnerabilities, asset types and components, control implementation and effectiveness, and the impacts of loss exposure.
Decisions based on relevant data points can then be made which allow for resource allocation to address information or cybersecurity risks thereby preventing impacts such as financial loss, business disruption or legal/regulatory consequences.
In the rest of this article, reference to information security risk management encompasses security risks in the areas of cybersecurity and operational security as they relate to processes managed by an organisation’s personnel and physical security systems. These are sub-areas that relate to managing risks to information and upholding confidentiality, integrity and availability.
Risk management is the core of information security with the interlinkages essentially an economics problem related to opportunity cost. Organisations have limited resources and must balance managing all the risks faced, of which information security, or cybersecurity, is only one category.
One of the best definitions of risk management I have found is from the book Measuring and Managing Information Risk: A FAIR Approach by Jack Freund and Jack Jones, where risk management is defined as “The combination of personnel, policies, processes and technologies that enable an organisation to costeffectively achieve and maintain an acceptable level of loss exposure.”
An organisation’s employees must evolve to be security risk champions by providing insights from their domains of expertise. The above risk management definition, which includes the words ‘personnel, policies, processes and technologies’, means the span of domain knowledge that must be incorporated for effective information security risk management is wide. To tap into this organisational collective knowledge a risk culture must be developed. Culture is a set of behaviours, values and norms that set the tone for ‘this is how we do things’. In the context of security risk management, a positive risk culture should be cultivated where employees feel empowered to speak up, to contribute to security risk management discussions and to challenge security practices.
This culture must be promoted, particularly where roles and responsibilities are clear. Even in cases where these are not explicit, promoting a risk
culture is key for effective information security risk management. Examples of the contributions organisational employees can make towards security risk management by providing insights from their areas of expertise include:
• Threats and vulnerabilities . Threat intelligence considers data points from various sources, including: recent cyber threat reports on how organisations are being targeted, alerts from security tooling, weak third party supplier security practices, risky internal staff behaviours that can contribute to accidental insider threats such as poor data handling practices or weak access control measures. Vulnerabilities could include information on known weaknesses or gaps in security posture that can provide opportunities for threats to cause the materialisation of risk events. For example, end of life support systems in use with critical technical vulnerabilities, legacy technology components that are incompatible with modern authentication methods and poor staff training on secure information handling.
• Assets. Assets are anything the organisation considers valuable. In the context of information security risk, assets are generally information and the technology that supports the transfer, storage or processing of information. Individual information assets have different lifecycles requiring different security control protections with asset owners typically responsible for ensuring that the protection measures for their information assets are implemented. Information asset custodians also play a role which is typically closer to the information asset requiring protection. They may have insights into how assets, and therefore their protection mechanisms, change across their lifecycles.
• Control design and operational effectiveness
According to the international standard ISO/IEC 27001, a control is a measure that modifies or maintains a risk. Controls have an objective or an intent that could be technical, administrative/ managerial or physical in nature. The ‘intent’ of a control could have varying levels of rigour depending on the organisation, its economic
sector, risk appetite and legal or regulatory environment. One could think of the level of rigour as a maturity level on a capability maturity model scale. Control owners within an organisation are responsible for the effective operation and maintenance of a control. These employees are often best placed to provide details on where controls have gaps in either their design or operation. Control design may be dictated by a security standard such as the Australian Signals Directorate’s Essential Eight, for example, Multifactor authentication must be used on an organisation’s internet facing services. Alternatively, controls could be architected by security teams to comprise documentation such as policies, standards or solution designs. Control designers and operators could provide the greatest insights into holes in an organisation’s security control fabric that need to be addressed.
Information security practices link with business processes across an organisation giving employees opportunities to contribute to information security risk management discussions. In these discussions employees can liaise with other employees across the organisation, have a chance to develop an understanding of security practices in other areas of the organisation and, in so doing, improve the security risk culture.
www.linkedin.com/in/marisealphonso


JO STEWART-RATTRAY
by Jo Stewart-Rattray , Oceania Ambassador, ISACA
Cybersecurity has always been defined by change. Each new wave of technology, from the World Wide Web to cloud and now, artificial intelligence and quantum computing, forces security and tech professionals to adapt. What’s different today is the speed and scale of that change.
AI, in particular, is reshaping business operations, customer interactions and risk itself. With that shift comes a pressing question: how do we ensure professionals have the right skills, recognition and pathways to meet these new demands?
ISACA’s 2025 AI Pulse Poll reinforces the urgency. While 81 percent of professionals report AI is being used in their workplace, only 28 percent of organisations have a formal AI policy in place. Even more concerning, just 22 percent of organisations provide AI training to all staff, despite 89 percent of digital trust professionals saying they will need AI training within the next two years simply to advance, or keep, their roles. This disconnect between adoption and oversight highlights why evolution in workforce capability is non-negotiable.
LEADING SECURELY IN THE FACE OF AI
That’s where ISACA’s new ISACA Advanced in AI Security Management (AAISM) —the first credential of its kind globally—comes in. AAISM is designed for experienced professionals who already hold senior certifications such as CISM or CISSP. It equips leaders with the skills to govern AI responsibly, manage AIspecific risks and integrate AI into security operations without compromising resilience or privacy.
The program covers three core domains:
• AI governance and program management
• AI risk management
• AI technologies and controls
Boards across Australia and New Zealand are already grappling with how to balance innovation with transparency, privacy and resilience. The AI Pulse Poll shows that 61 percent of professionals are extremely or very worried that AI will be exploited by bad actors. Yet only 21 percent of organisations are investing in tools to detect deep fakes; a gap that highlights the need for skilled leaders.
AAISM provides the credibility and structure for security professionals to step into that conversation with confidence. For women already in management roles—in a sector where they remain underrepresented—AAISM provides an opportunity to amplify their leadership, visibility and influence at the boardroom table. It’s a credential that validates not just technical expertise but strategic leadership and the ability to advise the boardroom on one of the most urgent technology questions today: how to integrate AI safely and responsibly.
The theme of evolution captures this moment perfectly. The poll shows nearly a third of organisations plan to increase jobs for AI-related functions within the next year, reflecting how AI is already altering career paths. At the same time, 84 percent of professionals say they are only at beginner
or intermediate AI skill levels, highlighting the challenge of building effective frameworks, but also the opportunity to rapidly upskill the workforce.
AI is transforming how decisions are made, how data is used and how organisations operate. Credentials can no longer remain static, but must evolve to keep pace with new threats and responsibilities. ISACA’s suite of AI-focused certifications—from AI Fundamentals through to AAISM—are designed with that evolution in mind, ensuring professionals have a pathway from entry-level learning to boardroom influence.
The future of cybersecurity will be defined by those who can lead through change. ISACA’s AI Pulse Poll reveals both the scale of adoption and the depth of unpreparedness. With credentials like AAISM ISACA is equipping professionals with the recognition and skills not just to survive this transformation, but to lead it.
For women in security it’s a chance to shape how AI evolves in our workplaces, our industries and our communities. The next generation of cybersecurity leaders will be those who can translate AI’s potential into trusted, ethical and secure practice.
Jo has over 25 years’ experience in the security sector. She consults in risk and technology issues with a particular emphasis on governance and cybersecurity as a director with BRM Advisory.
Jo is the Oceania Ambassador for global IT professional association, ISACA, and an ISACA Hall of Fame inductee. Jo is the former Vice President, Communities of the Australian Computer Society and Ambassador of the National Rural Women’s Coalition. She regularly provides strategic advice and consulting to the banking and finance, utilities, healthcare, tertiary education, retail and government sectors. www.linkedin.com/in/jo-stewart-rattray-gaicd-4991a12

CyberWest Hub, hosted by Edith Cowan University (ECU), has launched Cyber Queens, an innovative initiative designed to support women and non-binary students studying cybersecurity by connecting them with the broader cyber community.
With women making up only 15% of cyber students across tertiary institutions, many find themselves as the sole female presence in classrooms, leading to feelings of isolation and uncertainty about their place in the industry.
Cyber Queens aims to change that by fostering a sense of belonging beyond the classroom through meaningful connections with peers, mentors, and industry leaders.
Emma O’Neil, Director of CyberWest and the driving force behind the program, said:
“Cyber Queens is more than just networking—it’s about creating a sense of belonging. We need a diversity of people bringing a diversity of thinking to cyber. When women and non-binary students see themselves reflected in the cybersecurity community, they’re more likely to stay, thrive, and lead. This initiative is a step toward a more inclusive and resilient cyber sector, where diversity is not just welcomed but celebrated.”
Held at the start of each semester, the event brings together cybersecurity students from various universities with professionals across the sector.
The Semester 2, 2025 meetup featured keynote speaker Caitriona Forde, ECU alumna and Women in Technology WA award winner, who shared her career journey and advice for thriving in the industry.

Students were introduced to key industry bodies and networking opportunities, followed by small group discussions with cyber leaders who attended as mentors. One mentor, Danielle, reflected:
“It was a great opportunity to talk to students from all different backgrounds, hear about their experiences, and discuss what support exists for women in the industry—and what’s still missing.”
For students, the event was both empowering and inspiring.
Disha Sharma, a current ECU student, spoke of the valuable experience and inspiration she gained. “Meeting people, especially women in cyber, gives me the encouragement to be more like them in my future career,” Disha said.
Vanilla Tran, from UWA said, “We are the only girl in the class, the only girl in the project, so to build a community like this where we can have other girls to talk to is an amazing thing, I love it.”
“All my life I’ve been in spaces where I’m the only girl in class but coming to an event like this, seeing all these women, and talking to people breaking barriers
in cyber, I’ve been inspired,” said Fransisca Akareut, a final year student at ECU.
Tahia Bhuiyn also from ECU, said that “being a Cyber Queen, not only are we building our network, but we are building our future through meeting industry mentors who have shown us an idea of the path we should take.”
An exciting outcome from the recent event is the initiation on a a female and non-binary cohort to undertake the Certificate IV in Cyber Security at North Metropolitan TAFE in 2026.
CyberWest Hub will sponsor 10 scholarship places in the cohort, covering course fees and resource allowance.
Maree Tabb of North Metropolitan TAFE said she was delighted with the support, while Ms O’Neil added “ECU provides generous recognition of prior learning for this course, which provides an excellent pipeline for people wishing to further their studies at university.”
Find out more at CyberWest Hub



- Addressing critical skills gaps through learning innovation
- Advancing the representation of women
The Challenge: Market Demand and Talent Shortage
Cyber Security Architects are in high demand globally. Remuneration for these roles is typically $160k to $220k in Australia. Comparable roles in the US and UK often exceed $150,000 USD or £100,000 GBP. The high wages for this role are due to the demand for extensive experience, advanced certifications (e.g., SABSA, CISSP), and cross -functional skills in architecture, risk, and business strategy. This creates a significant talent shortage which is further compounded by:
▷ Rapid digital transformation across industries.
▷ Increasing complexity of cyber threats.
▷ A limited pipeline of professionals with both deep technical expertise and strategic business acumen.


Common Definition:
A Cyber Security Architect is a senior-level professional who designs, builds, and oversees the implementation of secure IT systems They bridge the gap between business needs and technical solutions, ensuring that security is embedded into the architecture of digital systems from the ground up
▷ Designing Secure Architectures: Develop end-toend security frameworks for systems, networks, and applications.
▷ Risk Assessment: Identify vulnerabilities and recommend mitigation strategies.
▷ Stakeholder Engagement: Translate business requirements into secure technical solutions.
▷ Technology Evaluation: Assess and select security tools and platforms.
▷ Compliance & Governance: Ensure systems meet regulatory and organisational security standards.
▷ Mentoring & Leadership: Guide teams on secure design principles and best practices.

The Opportunity: Innovative Learning Program:

▷ Morning: Review threat intelligence reports and assess implications for current projects.
▷ Midday: Collaborate with enterprise architects, developers, and business leaders to align security with project goals.
▷ Afternoon: Design or review security architectures, conduct risk assessments, and document security controls. Work with GRC teams and auditors.
▷ Ongoing: Updating on emerging threats, technologies, and compliance requirements. This could be talking to vendors, research, or participating in conferences, and working groups
As noted above, there is a supply and demand challenge. Competing for experienced architects is costly and unsustainable. Poaching between organisations and high churn further drives wave inflation. At the same time, there is a good supply of talent for entry level positions, which includes career changers, and underrepresented cohorts such as women. A potential solution to this problem involves developing a graduate-style and immersive learning program that:
▷ Introduces foundational IT and cyber theory.
▷ Builds architecture skills (e.g., TOGAF, design thinking).
▷ Layers in SABSA certification for strategic security architecture.
▷ Provides practical experience through IT, security operations, sales, and consulting domains to develop understanding of the inputs and outputs of those roles, typical challenges, and how the cyber security architect supports those roles as part of the enterprise IT value chain.
▷ Through the combination of learning above, practical experience, and exposure to an enterprise environment, this learning program also supports individuals in understanding the context of an organisation’s environment and supports professional skills development.
In terms of economic rationale, this program has a lower up-front cost, with training for an entry-level candidate over 3 months being significantly cheaper than hiring a seasoned architect. It can also cultivate a loyal, skilled workforce tailore d to organisational needs by creating pathways for new entrants, particularly those from non -traditional pathways. This can lead to improved diversity and inclusion within the workforce, which is known to have benefits around workforce culture and innovation, driving competitive advantage. Without over -reliance on a limited senior talent pool, this solution is scalable as an external program, and further, by embedding strategic thinking and security -by-design principles early in careers, it can support future proofing individual talent.
While there are many non-technical roles in the cyber industry, there are eight priority roles that all have some degree of assumed technical knowledge Many individuals use certifications as a baseline for industry entry however there can sometimes be a significant disconnect between industry certifications, foundational skills and practical application While obtaining cyber security certifications is a valuable step, true expertise hinges on a strong foundation in core technical skills Many individuals possess certifications in specific areas without possessing the underlying knowledge of essential IT and DevOps principles
Most training programs, particularly those geared towards vendor-specific platforms and frameworks like SABSA, prioritise their specific domain areas This approach neglects the importance of fundamental skills like network protocols, web services, and operating systems These foundational skills provide a critical understanding of the underlying infrastructure that cyber security professionals are tasked with protecting Without strong theoretical foundations, using advanced security tools, techniques and frameworks becomes challenging Conversely, some programs may emphasise theoretical knowledge over practical application
This can result in a skills gap where individuals struggle to apply their knowledge to real-world scenarios encountered during security assessments and incident response situations Effective cyber security professionals require the ability to think critically, troubleshoot problems, and adapt to new situations Training programs that lack a focus on hands-on exercises and real-world simulations may not adequately prepare individuals for the demands of the job As an example, the following diagram illustrates an approximation of the minimum assumed technical skills required for priority cyber security roles for entry level talent:
▷ Understanding the basic cyber security principles.
▷ Understanding the basic computing, software and networking foundations.

Moderately Assumed Technical Knowledge
▷ Understanding of high-level cyber security principles.

▷ Good applied technical skills across software, networking, and IT broadly. Possibly expert level in one of these areas.
▷ Expert understanding of cyber security principles.

▷ Excellent applied technical skills in multiple IT domains and expert level knowledge in two or more domains.

Assumed Technical Acumen
Cyber Security Manager


Cyber Security Analyst


Incident Responder


Cyber Security Engineer


DevSecOps Developer


Penetration Tester


Forensic Computer Analyst


Cyber Security Architect


Specific technical skills are required for these prioritised roles, with a range of foundational technical expertise requirements across the roles Of note, the forensic computer analyst, Cyber Security Architect, and penetration tester roles have high expert level assumed technical knowledge however the specific areas of expertise will differ, especially for the cyber security architect role, versus the forensic computer analyst and penetration tester which are closer together in terms of skill sets
The conclusion that can be drawn from this is that learning pathways should factor in how we develop the knowledge for those roles that have an assumed expert level of technical knowledge if we want to address those high demand areas Currently, a lot of pathways and expectations from prospective employers rely on ‘time on the tools’ and have unnecessary experience requirements Filling those roles requires development of new and innovative pathways and learning programs that can accelerate that knowledge acquisition At the same time, moving from knowledge-based testing to application based testing is crucial in cyber security certifications Lab-based scenarios can better evaluate a candidate's ability to apply their knowledge in real-world situations by requiring the candidate to show evidence that they know how to apply these skills in multiple steps Regular updates to the certification tests at least once a year ensure they stay relevant with industry advancements
Using the cyber security architect as an example, one of the popular training courses is the SABSA Foundation certification. This is typically run as a five day course, and when looking at the syllabus for that certification, it doesn’t cover the background knowledge because it’s assumed that only people with tenure and experience will undertake the course To be able to fill the high demand cyber security architect role from a strong pipeline of entry level talent, we need to consider new courses that blend the SABSA learning objectives with the background theoretical knowledge and practical experience
As an indicative guide, this is how the SABSA syllabus (in blue), could be augmented with a broader curriculum and practical experience to draw from a graduate pipeline to develop a job ready Cyber Security Architect where there is supply shortage:




Theoretical Knowledge Acquired:
• Risk management principles
• Defence in Depth and the CIA Triad
• Data security concepts
• AAA concepts and access controls
• Regulations, standards and policies
• GRC, IT and cyber security frameworks
• Data centres and enterprise IT
• Cloud computing concepts
• Artificial Intelligence (AI)
• OT technologies
• Networking concepts and OSI model
• Cryptography concepts
• How operating systems work
• Application architectures
• Secure software development
• API functions and security principles
• Infrastructure as Code (IaC)
• DevOps methodologies
• IT resilience and high availability
• Backup DR, and business continuity
• Network and IT operational monitoring
• ITSM and the ITIL framework
• Service integration and management
• System lifecycle management
• Configuration management
• Threat actors and adversary psychology
• Cyber threat intelligence
• Vulnerabilities and management
• The cyber kill chain and MITRE ATT&CK
• Common attack types/vectors
• Security testing methodologies
• Physical and logical security controls
• Security operations
• Logging and email security principles
• Malware analysis (static and dynamic)
• Threat hunting and purple teaming
• Cyber/IT incident response processes
Professional Skills Developed:
• Taking accountability for own learning
• Tracking IT and security trends
• Developing industry and sector specific contextualisation

Theoretical Knowledge Acquired:
• Organisational strategy
• Factors shaping business outcomes
• Business analysis techniques
• Functional/non-functional requirements
• Problem solving customer challenges
• Human centred design principles
• Researching and evaluating solutions
• Using technical artefacts (BRS, HLD, LLD, Network Diagrams, DFD's, API specs)
• Developing technical artefacts for technical and business stakeholders
• Linking contextual, conceptual, logical, physical, operational components
• Systems thinking approach
• Converting requirements to RFQ/RFT
• Procurement and commercial models
• Identifying key suppliers and partners
• Leveraging vendor material and support
• Calculating total cost of ownership of proposed solutions
• Project management methodologies
• Agile methodologies
• Creating project artefacts
• Developing implementation plans
• Defining/developing a proof of concept
• Functional (unit, component, smoke, integration, regression, sanity, UAT) and non-functional testing (Stress, volume, maintainability, security, scalability, failover, usability, configuration, load)
Professional Skills Developed:
• Identifying challenges/opportunities
• Core consulting skills
• Risk and secure-by-design mindset
• Maintaining strategic relationships
• Negotiation and influence skills
• Commercial acumen
• Managing organisational change
• Thinking critically
• Managing ambiguous or changing requirements


Theoretical Knowledge Acquired:
• SABSA Executive Summary
• SABSA Certification Programme
• SABSA Principles & Objectives
• SABSA Framework Overview
• Business Requirements & SABSA Attributes Profile Concept
• SABSA Risk & Opportunity Concept
• SABSA Policy Architecture
• SABSA Architecture Strength-in-Depth Engineering Concepts
• SABSA Governance, Roles & Responsibilities
• SABSA Domain Concepts
• SABSA Time & Performance Management
• Asset Architecture & Management
• Risk & Policy Management Architecture
• Transformation & Service Architecture
• Entity & Trust Framework
• Inter-domain Security Associations
• Service Sequencing & Performance
Professional Skills Developed:
• Application of the SABSA cyber security architecture methodology
• Ongoing career management and development plans













Improving Gender Representation Through Strategic Learning Pathways
Women are significantly underrepresented in cyber security architecture roles, often making up less than 20% of the workforce in advanced technical and strategic positions. This gap is not due to capability, but rather systemic barriers such as limited access to mentorship, visibility of role models, and pathways that align with diverse learning styles and career trajectories.
Yet, women are inherently well-suited to these roles with many employers looking for traits such as:
▷ Systems thinking
▷ Empathy for user experience
▷ Strong communication and collaboration
▷ Risk awareness and strategic foresight
These are areas where women often excel, bringing diverse cognitive approaches that enhance team performance, innovation, and resilience. An innovative learning program blending introductory IT and cyber theory, architecture training, and advanced SABSA certification creates a structured, inclusive pathway for women to enter and thrive.
Further, by investing in early-stage talent, and tailoring a program like this, organisations can:
▷ Improve gender representation in high-value roles
▷ Foster inclusive team cultures
▷ Drive innovation through diverse perspectives
▷ Reduce reliance on expensive senior hires
This approach is not just equitable, it’s economically smart building a sustainable talent pipeline while transforming the culture and capability of cyber security teams. It isn’t just about equity though, it is a strategic business advantage; Women bring diverse perspectives, collaborative problem -solving styles, and holistic thinking that are critical in cyber defence where anticipating threats from multiple angles is essential. Diverse teams consistently outperform homogeneous ones in innovation, adaptability, and decision-making. In cyber architecture, this translates to more resilient systems, creative threat mitigation strategies, and better alignment with user and business needs. Moreover, increasing representation improves team culture, fostering psychological safety, empathy, and inclusive leadership. These cultural shifts enhance retention, reduce burnout, and attract broader talent pools. By embedding diversity into the talent pipeline through targeted programs, organisations not only future -proof their cyber capabilities but also cultivate environments where innovation thrives and people want to stay.




CHRISTOPHER HARRELL
by Christopher Harrell , Chief Executive Officer
Passwords are on their way out and passkeys are replacing them. According to Yubico, passwords are on their way out. In their place is a new form of login called passkeys that promises stronger security and less frustration. All passkeys offer the rare combination of improved usability and stronger security, especially when compared to passwords alone. But, unless we act now, millions could be left more vulnerable than ever.
“The global momentum behind passkeys represents one of the most exciting shifts in authentication history,” says Christopher Harrell, chief technology officer at Yubico.
“The technical specifications that enable this shift are FIDO2 and WebAuthn, and their implementations are now widely known by the consumer-friendly name ‘passkeys’. As the creator of the first passkeys, passkeys in security keys, Yubico is proud and humbled to have helped initiate and to be continuing
to drive this transformation. Yet, the work isn’t done. Not all passkeys are equal. Not all users have the same needs, and leaving insecure fallback methods in place can provide a false sense of security.”
This is how security leaders, builders, product managers, and individuals can make sure passkeys work for everyone
SYNCED VERSUS. DEVICE-BOUND PASSKEYS: THE CRITICAL DIFFERENCE
Synced passkeys
For many people, passkeys are synonymous with synced passkeys where the private key is stored in the cloud and copied between devices. Synced passkeys offer a practical, user-friendly solution for some use cases, but they depend heavily on the security and availability of the synchronisation mechanism, recovery systems and processes, and the cloud accounts they are tied to.
For people and organisations that face higher risks, have greater sensitivity or accessibility needs, or individuals who just want the best protection for their finances or other critical accounts, synced passkeys are insufficient.
Device-bound passkeys never leave the secure hardware on which they are created. They provide the strongest protection against phishing, account takeover and recovery abuse. There are two primary implementations:
• Smartphone/laptop-based. These can be convenient, but are not always an available option and can provide inconsistent experiences. For example, most smartphone-based passkey solutions have usability challenges because of confusing QR codes, buggy or missing Bluetooth and unreliable relay access.
• Hardware security keys (like YubiKeys). These are the , and the gold standard. They offer the highest security assurance by providing portable, crossplatform and consistent passkey experiences. They serve as a root of trust for every use case, across borders and in high-risk situations.
Bottom line: synced passkeys should be the baseline. Device-bound passkeys must be an option, and in some cases, the requirement.
Even with device-bound passkeys enabled, accounts remain vulnerable if weaker recovery methods are still allowed:
• Text messages
• Code-generation apps
• Push notification approvals
• Number matching prompts
Harrell says: “Attackers understand this and actively downgrade to insecure, phishable mechanisms to avoid the phishing-resistant security passkeys provide.”

According to Harrell, enterprise-grade protection means control over authentication policies. “Passkeys in YubiKeys and Windows Hello for Business are better together, offering non-exportable credentials that cannot be silently synced, phished or copied. These passkeys can provide clear visibility into how and where they are stored, which enables more consistent support, audit and incident response processes.”
Key requirements to demand from identity providers and partners are that they:
• Ensure all identity providers use only devicebound passkeys.
• Require device-bound passkeys, even for services outside the single sign on.
• Disable synced passkeys for enterprise use.
• Use passkeys in security keys as a root of trust for self-service recovery, transition, and step-up.
• Remove all non-FIDO fallback methods.
• Enforce identity providers use only devicebound passkeys.
• Require device-bound passkeys even for services outside the SSO.
• Disable synced passkeys for enterprise use.
• Use passkeys in security keys as a root of trust for self-service recovery, transition and step-up.
• Remove all non-FIDO fallback methods.
Hassall says: “To make this work, the services used have to allow it. Organisations should demand configurability from identity providers, workforce tools and partners. Think about protecting your organisation with authentication designed for the realities of your threat landscape. Organisations that do this see fewer recovery events, lower costs and greater resilience.”
He adds: “Don’t exclude security keys; it often takes more effort to block them than to support them. And if you’re stuck, technically or from a usability perspective, Yubico is here to help. We’ve partnered with governments, Fortune 500s and identity platforms to solve many challenges at scale across the globe.
“As a product leader or engineer rolling out passkey support in your application you are shaping the future of digital identity and safety. If you’re building a banking app, social network, government portal, an identity provider or anything else, you are also deciding who gets access to higher levels of protection.”
• Enterprises that offer strong security policies can save time and money and harden recovery flows against social engineering.
• High-value accounts can use the strongest phishing resistance to protect all assets.
• At-risk individuals and organisations, ranging from journalists and whistleblowers to those securing political processes or members of marginalised communities depend on YubiKeys as a lifeline
• People with accessibility needs often prefer, or need, portable hardware security keys because of their predictable, tactile and cross-platform experience that reduces screen reader challenges and eliminates complex or unfamiliar gestures.
• The stakes are global and personal: build a passkey future that works for everyone.
“Authentication should be adaptable and flexible, not rigid and monolithic. Higher-assurance security is not just for the enterprise; it’s a lifeline for millions,” says Harrell.
Here are just a few people and groups who need the strongest passkey protections:
• Government officials, diplomats and military leaders.
• Legal workers, judges and law enforcement.
• High-profile executives, influencers and celebrities.
• Developers and maintainers of software and systems.
• Security practitioners and researchers.
• Survivors of domestic violence or trafficking.
• Activists, journalists and other vulnerable populations or organisations.
• Those without reliable access to a personal phone or computer.
• People with accessibility needs.
• Everyday individuals who want the best protection.
A person or organisation can become ‘at-risk’ overnight through a political event, security incident or public exposure. Having the ability to quickly improve security posture can dramatically increase safety and peace of mind.
Whether you lead a security program, build products for millions or care about your own accounts:
• Support or require security keys as a core part of your passkey strategy.
• Demand configurability and the ability to disable insecure fallbacks.
• Ensure everyone has the option to choose the protection level they need.
For more information on passkeys see Yubico’s new infographic and eBook
www.linkedin.com/in/cnhcnh


by Ema Correia , Senior Cybersecurity Consultant, KPMG Portugal
Imagine waking up on a Monday morning. You splash cold water on your face, grab some breakfast and open your phone to scroll through the news. Everything feels perfectly normal—until you see your face on a video saying things you never said, advertising a product you never agreed to promote, or even appearing attached to a naked body that isn’t yours.
This may sound like a nightmare, but for many people, it’s already a reality. Taylor Swift, Jennifer Lawrence, Tom Hanks, Justin Trudeau, Penny Wong and Katy Gallagher are just a few of the high-profile victims of scams and disinformation campaigns powered by artificial intelligence.
From Hollywood stars to well-known politicians, from world leaders to teenage girls, deepfakes are one of the clearest signs of our evolving security threat landscape.
THE DOUBLE-EDGED SWORD OF AI Artificial intelligence has brought undeniable progress and benefits to society.
• In healthcare, AI-powered imaging tools can detect cancers and other diseases earlier and with greater precision than humans.

• In accessibility, innovations like vision assistance technologies and AI-driven prosthetics that adapt in real time are breaking down barriers and creating opportunities for inclusion.
• Even in cybersecurity, AI helps defend organisations by detecting anomalies in real time and preventing millions of dollars worth of fraud each day.
However, like any powerful tool, AI has a dark side. While a lot of organisations are relying on this technology for well-intentioned purposes, others exploit it for harm. It is, in many ways, like a balance: on one side sits innovation and progress, and on the other an increasingly frightening set of risks.
CYBER THREATS ARE NO LONGER ABOUT STEALING YOUR PASSWORD, THEY’RE ABOUT STEALING WHO YOU ARE
While it may still be too early to determine—at least for me—whether AI’s benefits outweigh its risks, the threats it creates are already impossible for us, as a society, to ignore.
Voice cloning and realistic, manipulated images are now being used to spread disinformation at scale, to create abusive content such as non-consensual pornography and so-called ‘revenge porn’, and to

amplify scams in ways that feel like phishing attacks on steroids.
In one shocking case in early 2023, a woman in the United States received a phone call with a voice that sounded exactly like that of her daughter, crying for help. She was tricked into believing her child had been kidnapped, only to learn later that AI-generated voice cloning was being used to extort money.
The line between reality and fabrication is blurring fast, and there are two key reasons these threats are so difficult to fight. First, the technology has become widely accessible. Tasks that once demanded specialised skills and expensive tools can now be performed quickly and cheaply by almost anyone with a smartphone and an internet connection. Second, social media amplifies the problem by allowing fake content to spread at incredible speed. A single manipulated video can go viral in minutes, leaving little time to contain the damage.
As the threat landscape evolves, gender plays a central role. Multiple studies highlight that generative AI is facilitating gender-based violence in unprecedented ways. While AI-driven threats affect everyone, women and girls bear the heaviest burden. They face not only reputational harm but also emotional trauma and personal safety risks.
According to a 2024 report by Internet Matters, four in every thirty school-aged children in the UK have encountered AI-generated explicit imagery, most often targeting girls. The same report warns that an estimated 99 percent of all nude deepfakes worldwide feature women and girls, showing just how this technology harms them disproportionately.
There are several reasons for this imbalance. Many AI detection tools struggle to identify manipulated female faces because training datasets are often biased and underrepresent women, as highlighted in a 2023 UNESCO report on gender and AI. In addition, public figures—especially women in leadership roles in politics and business—are deliberately targeted to undermine their credibility and influence. At the same time, the proliferation of ‘nudifying’ apps has
left young girls particularly vulnerable, with altered images easily created and shared on group chats and social media.
A STEP TOWARDS DIGITAL TRUST
We are at a turning point in the evolution of technology. AI has the power to heal or harm, to protect or exploit. As AI shifts from stealing our data to stealing our identities, we need stronger ways to prove what’s real and what’s not. And this requires a collective effort.
Awareness is the first line of defence. Education must become our strongest weapon. By understanding the risks, thinking twice before sharing personal images and being mindful of who we trust online, we create a safer digital world.
Deepfake harassment crosses borders. Stronger laws and international cooperation are essential to track offenders and hold them accountable. Policymakers must also encourage and push tech companies to address gender bias in AI systems, ensuring detection is accurate and fair for everyone.
This is where the real transformation happens. The future lies in ‘proof of personhood’; secure ways to confirm if someone online is human or AI. Imagine every photo or video carrying a hidden digital signature, like a tamper-proof seal of authenticity.
• Adobe’s Content Authenticity Initiative and Apple’s watermarking projects are leading the way, embedding these seals into images and videos to make manipulation easier to detect.
• Meanwhile, Worldcoin and Microsoft are exploring the use of global identity verification systems to build a foundation of digital trust.
By acting now as individuals, organisations and societies we can ensure that this technology strengthens trust instead of destroying it. After all, the fight is no longer about firewalls and passwords but about protecting what makes us human.
www.linkedin.com/in/emamcorreia
Cybercrime is big business, thanks to technical advancement and interconnectivity creating more opportunities. This regular column will explore various aspects of cybercrime in an easy-to-understand manner to help everyone become more cyber safe.
There is an alarming trend of threat actors exploiting advanced artificial intelligence models to enable, enhance or create cybercrime campaigns. They are using legitimate GenAI offerings as well as creating their own, and the sophistication of these operations makes even the most informed very vulnerable to AI enhanced cyber threats.
Using GenAI criminals and nation state threat actors can scale their cybercrime operations to higher levels. They can automate the creation of malware and phishing templates and believable faked live video meetings, as well as contact a larger number of potential victims with very little human involvement.
Cybercrime-as-a-service marketplaces are offering GenAI constructed phishing kits and ransomware malware kits at low cost, and are also providing manipulated GenAI models for other criminals to use. There are deep fake and other photo and live video masking techniques created by GenAI that allow for the manipulation of imagery to spoof company executives as part of the modern approach to business email compromise fraud. This technology also allows for the creation or manipulation of images for use in child exploitation or child sexual abuse and is used to ‘nudify’ images to publicly embarrass, exploit or shame individuals.
GenAI is making it easier for malicious actors to create large volumes of believable material for their illicit use. However, campaigns are still largely relying on tricking humans or exploiting information or imagery discovered about their targets. This means that the basic rules of online security hygiene still apply.

• Be considered and cautious about what images or information about yourself or others you share online.
• Help children in your care understand safe digital practices and help them to engage with the ideas of privacy and security from a young age.
• Use multifactor authentication and advanced credential practices, such as passkey, where possible.
• Verify the veracity of requests for information or payments before actioning them.
• Understand the types of cyber-enabled crime that are out there.
• Know where to go for help if you or someone you know is a victim of cybercrime.
The volume and sophistication of cybercrime campaigns will only increase with the use of GenAI. So, as a community, we need to stay vigilant.
Stay safe everyone.
www.linkedin.com/in/amandajane1
www.empressbat.com





In a casual conversation with someone unfamiliar with the field, how do you articulate the excitement and potential of a career in cybersecurity, aiming to spark their interest?
When I talk about cybersecurity, I like to highlight just how many different paths there are not only for people who are technically inclined but also for those interested in strategy, policy, or communication. A lot of people still picture cybersecurity as just “hackers in hoodies,” but it’s so much broader than that. It’s a growing field that truly needs capable people who are willing to stay and grow with it. With the number of connected devices constantly increasing, the need for strong security will only keep expanding. That’s why I see cybersecurity as such an exciting and stable industry to join. It’s not going anywhere anytime soon.
Upon graduation, which specific cybersecurity role do you aspire to secure employment in, and what motivates your choice?
My long-term goal is to move into the GRC side of cybersecurity. I’m aware that it’s not usually something you can step straight into without experience, so I’m planning to build my foundation first in roles like SOC Analyst or on an Incident Response team. I’m genuinely fascinated by the standards and regulations that shape security
practices — not just what they are, but why they exist and how they’re developed. I find it really interesting to see how these rules and frameworks influence the way organizations approach security, and that’s what draws me to GRC.
Who or what has been the most influential factor in shaping your journey in cybersecurity so far, and how has it impacted your career aspirations?
My friend has been the biggest influence on my cybersecurity journey so far. She’s an Incident Response Team Manager at an insurance company and was actually the one who first suggested I try the ISC² Certified in Cybersecurity (CC) course. At the time, I was wrapping up seven years of teaching English in Japan and feeling unsure about what to do next when I returned to Canada. We spent a lot of time talking about my options, and she quickly said, “You should try cybersecurity.”
I took her advice and completed the ISC² CC online course while I was still teaching — and I loved it. She’s also the one who encouraged me to explore GRC, and from everything I’ve read so far, it feels like the perfect direction for me to grow into.
The cybersecurity industry offers various certifications from different organisations. Have you pursued, or do you plan to pursue any of these certifications? If so, which ones, and what factors influenced your choice?
I’m currently working toward my ISC² CC certification and have my exam scheduled for early September 2025. Once that’s complete, I’m planning to jump straight into the CompTIA Security+ as my next step. I chose these two certifications because they’re solid entry-level credentials — a perfect match for where I’ll be at the end of my course. Looking ahead, I’m excited to keep building on this foundation by earning more certifications as I grow in my career.

What aspect of your cybersecurity studies excites you the most, and why?
I’m really looking forward to diving into standards and regulations, because that’s the part of cybersecurity I genuinely enjoy. I’ve always been fascinated by rules and figuring out how to navigate them smartly without breaking them. We haven’t reached the GRC section of my course yet, but I’m excited to explore which regulations and standards apply in different situations, why they exist, and how they shape the way organisations handle security.
Considering the holistic requirements of a future role, do you see the need for additional training in non-cyber skills, such as interpersonal communication or management? If yes, why?
I think everyone can benefit from improving their communication skills — it’s such a vital part of any job. Clear and respectful communication can make all the difference, while misunderstandings or poor communication can create tension within a team or organisation. I’ve met plenty of people who thought they were great communicators but weren’t always getting their message across. In the workplace, strong communication can really lift a team and help people thrive, while weak communication can hold everything back.
What is your preferred source for staying informed about cybersecurity trends and general information?
I keep up with the latest in cybersecurity by reading TLDR InfoSec articles and listening to the CyberWire Daily podcast about five days a week. I do like to take a break now and then, though with how much is happening in the field these days, it can get a bit overwhelming to stay on top of everything every single day.
What measures do you have in place to enhance your personal cybersecurity in today’s digital landscape?
I take my personal cybersecurity pretty seriously. I always have a VPN running on my devices, and I make it a point to change my passwords every three months, keeping them strong with at least 16 characters, a mix of uppercase and lowercase letters, numbers, and symbols. Any email from an unknown sender gets a quick Google check — or I just delete it if it seems suspicious. I also keep my social media accounts private, so anyone who wants to follow me has to be approved first. It might not help me build a huge online following, but I’d much rather be safe than sorry.
www.linkedin.com/in/oasis-kauppila-5280b0161

Nandini Sivarathri is currently pursuing her Master of Cyber Security & Digital Forensics at Auckland University of Technology.
Master of Cyber Security & Digital Forensics student at Auckland University of Technology

In a casual conversation with someone unfamiliar with the field, how do you articulate the excitement and potential of a career in cybersecurity, aiming to spark their interest?
I like to think of cybersecurity as a kind of digital detective work — almost like being a modern-day Sherlock Holmes. But instead of chasing criminals through dark alleys, you’re following their footprints through networks, systems, and data logs. What excites me most is that no two days ever feel the same. Threats evolve constantly, and so do we. In this field you’re not just solving puzzles; you’re protecting people, organisations, and sometimes even whole nations. It’s a career where curiosity is a strength and where the work you do truly makes a difference.
Reflecting on your initial perceptions of cybersecurity when you first considered studying it, how does the reality of your experiences today compare?
When I first heard about cybersecurity, I honestly thought it was all about hacking and stopping viruses. But as I went deeper into my studies, I realised it’s so much more than that. It’s this huge, multidisciplinary field that brings together governance, risk management, forensics, ethical hacking, compliance — even psychology. The range
of roles and the sheer complexity of it all turned out to be far bigger and more fascinating than I ever expected.
Who or what has been the most influential factor in shaping your journey in cybersecurity so far, and how has it impacted your career aspirations?
One of the biggest turning points for me came at Infosys, when I got to work on a live client issue involving cloud security and incident response. Seeing cybersecurity in action like that — not just in theory — completely ignited my passion for the field. Since then, the mentors I’ve met during my master’s program, along with the guest speakers who’ve shared their own journeys, have been hugely influential in helping me refine my path and discover my interests in threat detection and digital forensics.
Recount the most memorable or significant event in your cybersecurity journey to date, highlighting why it left a lasting impression. One of the moments that really shaped my journey was working on a project focused on Privileged Access Management for a healthcare company in New Zealand. I got to dive into hands-on work, assessing solutions like BeyondTrust and PAM360. It wasn’t just technical, it gave me a firsthand look at the vital intersection of security, ethics, and healthcare. Experiencing that real-world consulting environment really reinforced why I love this field.
Beyond your academic studies, what practical experience have you gained in the field of cybersecurity through employment or internships?
I spent over three years working as a QA Engineer, where I got hands-on experience automating security regression scripts, validating APIs, and running smoke and integration tests across cloud-hosted applications. More recently, I had the opportunity to be part of a consulting project at Aroa Biosurgery, where I helped assess cybersecurity tools and
risks. It was exciting to take the theory I’d learned in my studies and apply it in a real, business-critical environment — seeing the direct impact of good security practices was incredibly rewarding.
The cybersecurity industry offers various certifications from different organisations. Have you pursued, or do you plan to pursue any of these certifications? If so, which ones, and what factors influenced your choice?
Yes, I’ve already completed certifications like Microsoft AZ-900 (Azure Fundamentals), SC-900 (Security, Compliance & Identity), and AI-900, and I also hold AWS Cloud Practitioner and Architect certifications. Next on my list are CompTIA Security+ and CEH. I chose these certifications because they’re widely recognized and directly relevant to the kind of roles I’m aiming for. Each one feels like another step toward building the skills I’m most excited to use in the field.
What aspect of your cybersecurity studies excites you the most, and why?
I find it fascinating to trace the origin of a breach, piece together exactly what happened, and uncover digital evidence that could hold up in a court of law. It’s that mix of technology, investigation, and legal process that really excites me — it keeps you thinking, problem-solving, and constantly learning.
Are there specific aspects of your cybersecurity studies that you find particularly challenging? If so, what are they, and how do you approach overcoming these challenges?
Yes, one of the challenges I’ve faced is getting to grips with advanced cryptography and network packet analysis. Both can be pretty intense, with all the math, protocols, and complex data to interpret — especially under time pressure. What helps me is breaking the topics into smaller, manageable chunks and pairing theory with hands-on labs. I also rely on online tools like Wireshark tutorials and cryptography simulators to see how things work in real situations.
Studying with peers has been a gamechanger too — explaining concepts to others really helps cement my own understanding.
What is your preferred source for staying informed about cybersecurity trends and general information?

I keep up with cybersecurity news through a mix of formal and informal sources. I turn to organizations like the SANS Institute, CISA, and ISACA for indepth research and official alerts, but I also love the community side — platforms like Reddit’s /r/ netsec, LinkedIn discussions, and GitHub are great for learning about new tools and attack patterns. For quick daily updates, I follow newsletters like CyberWire, Krebs on Security, and Dark Reading. Using a mix of these sources helps me stay on top of real-world threats while complementing what I’m learning academically.
Have you ever encountered situations where being a woman in cybersecurity made you feel disadvantaged or discriminated against? If so, please share your experiences.
Yes, I’ve definitely faced challenges. Early in my IT career, I often felt I had to prove my technical skills more than my male colleagues. In meetings, I noticed my ideas sometimes went unheard until someone else repeated them. It wasn’t always blatant, but the subtle biases were there. I’ve tried to turn those experiences into motivation — by upskilling, speaking up with more confidence, and mentoring other women starting out in tech. Being part of women-in-tech networks has also made a huge difference, helping me feel supported and more visible in the industry.
www.linkedin.com/in/sivarathri-nandini


In a casual conversation with someone unfamiliar with the field, how do you articulate the excitement and potential of a career in cybersecurity, aiming to spark their interest?
We’re in the middle of a technological revolution, and cybersecurity sits right at the heart of it. Technology touches almost every part of our lives, which makes protecting it more important than ever. What I love about a career in cybersecurity is that it’s never boring; you’re always learning, solving problems, and staying one step ahead of the next challenge.”
Reflecting on your initial perceptions of cybersecurity when you first considered studying it, how does the reality of your experiences today compare?
My thoughts of cybersecurity from when I started my degree three years ago to today have vastly changed. I initially fell to believe the stereotype of what a person in the tech field does and who they are; or in short a lack of education and exposure to what tech is, and can be. To me the description was, a male coding behind a screen not seeing daylight (which is so far from the truth).
The biggest perspective shift for me was how much collaboration is needed in cybersecurity, which is something I really enjoy. I’ve found it’s not all about theory and coding, there’s a lot of hands-on
skills I’ve gained. Understanding how important cybersecurity is to businesses and organisations was really fascinating to me. My perception now for my degree isn’t limited to high level grades, it’s about learning more, and creating opportunities for others, especially women and underrepresented groups, to enter the field.
I’ve been able to meet a wide range of people, I’m privileged to have so many women and mentors who have wanted to uplift me through my career which was great because I feel like it’s a supportive community I want to be a part of and in the future help others like they did to me.
Upon graduation, which specific cybersecurity role do you aspire to secure employment in, and what motivates your choice?
I’ve been exploring roles in governance, risk, and compliance (GRC), and a cybersecurity paper I’m currently doing in this area has really sparked my interest. I love how GRC blends both technical knowledge and people skills, and with AI becoming more prevalent, it’s exciting to think about how this field will continue to evolve.
I’m also thrilled to have secured a role as a Security Analyst with Xero starting in 2026. I was really excited to accept the opportunity because of their strong well-established graduate program and the chance to rotate through different teams. I see it as an amazing way to gain exposure, hands-on experience, and a deeper understanding of the field.
When you decided to pursue a career in cybersecurity, how did your parents, peers, or career advisors react? Did you encounter any opposition, and if so, how did you navigate those challenges?
When I finished high school, cybersecurity wasn’t really on anyone’s radar. My friends often didn’t understand what it was or why I’d chosen it.
Thankfully, my family were incredibly supportive. They encouraged me to follow this path, and I’m really grateful for that.
Who or what has been the most influential factor in shaping your journey in cybersecurity so far, and how has it impacted your career aspirations?
The people I’ve met along the way have been the biggest influence on my journey in cybersecurity. Seeing women thrive in a field where representation is still limited has been incredibly inspiring and has motivated me to carve my own path. I’ve also been fortunate to have mentors and peers who genuinely want to see me succeed. They’ve encouraged me to take on challenges I might never have tried on my own. Tutoring has been another highlight, giving me the chance to engage with more students and see new ideas/perspectives.
Beyond your academic studies, what practical experience have you gained in the field of cybersecurity through employment or internships?
In my penultimate year, I had the chance to intern with Deloitte in their Risk Advisory team. It was really exciting to take the theory I’d been learning at university and see it in action in a real work environment. The experience understanding how cybersecurity is viewed in a corporate setting, and it changed how I approached my studies. I started relating what I was learning at university back to the business and people side of security, which made my learning feel more connected.

The cybersecurity industry offers various certifications from different organisations. Have you pursued, or do you plan to pursue any of these certifications? If so, which ones, and what factors influenced your choice?
I haven’t pursued certifications yet, but I plan to once I finish my degree and settle into my role.
I’m interested in some of the security and risk management certifications as it’s the career path I’m going down. I’ve had a look at CompTIA Security+ because it gives a broad foundation and if I continue down the governance, risk, and compliance track I’d like to look into CGRC or CCRP.
Given the rapid evolution of cybersecurity threats, do you feel that your academic program adequately keeps pace with the industry’s current landscape?
I believe we live in a fast paced world especially when it comes to technology, therefore I can understand how it could be difficult to keep our education relevant. However some of these papers haven’t changed since 2018. One lecturer advised us that the content we were learning was outdated. Talking to employers and discussing topics from the classroom is sometimes met with raised eyebrows as they can often agree about areas being outdated.
What aspect of your cybersecurity studies excites you the most, and why?
What excites me most about my cybersecurity studies is how practical it can be. I like that it’s more than theory. We get to see how attacks work, figure out defences on a technical and theoretical level, and see how decisions play out in real scenarios. It keeps me on my toes because there’s always a new way to think about the same problem. I’ve also really enjoyed learning the foundational side of things, for example how the internet works at a low level. These basics come across simple, but they’re still at the foundation of cybersecurity today, and understanding them makes me feel more grounded in the field. I enjoy that both of these aspects connect to real people and real risks.
Conversely, which aspect of your studies do you find least interesting or useful, and how do you navigate through it?
I find some of the more abstract topics, like cryptography theory, less engaging. I understand its importance, but it can feel disconnected from the problems I enjoy solving. To stay motivated, I try connecting theory to real-world applications, which helps me get through it.
Are there specific aspects of your cybersecurity studies that you find particularly challenging? If so, what are they, and how do you approach overcoming these challenges?
A challenge is that the course structure doesn’t always reflect what’s most in demand in jobs, so I’ve had to seek out extra learning whether that be from the internship, networking events, and self-study. While it’s difficult to balance on top of university’s workload, it pushed me to take more initiative in my own learning.
Do you believe there are areas in cybersecurity that deserve more emphasis in your coursework or areas that could receive less focus?
I think concepts like governance, risk, and compliance should be introduced earlier. When I first started applying for jobs in first and second year, most roles mentioned GRC, but I didn’t learn about it properly until my final year. Earlier exposure would have helped prepare us for those opportunities.

Considering the holistic requirements of a future role, do you see the need for additional training in non-cyber skills, such as interpersonal communication or management? If yes, why?
Yes, I definitely think non-technical skills are just as important. Strong interpersonal skills come from communities, such as part time jobs, sports or even hackathons. There should always be a door to access those opportunities, which I’ve found at university there are so many. I’ve also enjoyed elective papers like management, which gave me a chance to use a different side of my brain and see how leadership and communication can relate back to my degree.
Are you actively engaged in the broader cybersecurity community? If so, what has been your involvement, and how has it enriched your experience?
Since my first year of university I’ve been attending Project Wednesday which is a monthly cybersecurity networking event. I remember my first time attending one of these events, I felt incredibly out of place. I was evidently the youngest person at 17 and the amount of women was not as half of what it is today; let alone students.
I really had to convince myself to attend the next one, and I tried to think of ways I could make it less confronting. From there it opened my eyes to the importance of building relationships and being able to hold a conversation. The second time I attended I did a bit of a Hannah Montana fake it till you make it, and made small goals of talking to five people I haven’t met. That’s still something I try to be proactive in despite knowing more members. I like to say an event is only unsuccessful if I don’t meet someone new. Now I’ve met such a range of people from the Project Wednesday community.
I’m currently talking with one of the cofounders, Annabella, to introduce a platform for project Wednesday members to connect pre and post events to have more of those meaningful long lasting connections and draw in more students.
More recently I’ve found a group of women in cybersecurity space within Wellington. There’s a range of us, and I look to some of them as rolemodels with the amount of time they’ve been in the industry and perhaps in a more difficult time than what I’m facing as of now.
What is your preferred source for staying informed about cybersecurity trends and general information?
I have this app on my phone called NewBlur, and I’ve subscribed to different newsletters from various places on their technology sections and it makes it easy to access and read on the way to uni or work. Additionally attending Project Wednesday and AI Connect is great for hearing what professionals are speaking about and what’s going on in the business setting when it comes to trends.
Have you ever encountered situations where being a woman in cybersecurity made you feel disadvantaged or discriminated against? If so, please share your experiences.
I have been fortunate not to face direct discrimination, but being a woman in STEM has definitely come with moments of feeling out of place. When I started out, walking into lecture theatres and networking events where the gender balance was heavily skewed made me second-guess whether I belonged. Over time, I’ve learned to see that difference as a strength rather than a disadvantage. Surrounding myself with mentors, many of them strong women in the field, has helped me shift that perspective. Those experiences have made me want to contribute to building a more inclusive space, so future students feel supported from the get go.
What measures do you have in place to enhance your personal cybersecurity in today’s digital landscape?
I keep it basic, using strong passwords stored in a password manager, and I always enable multi-factor authentication. I’m cautious about what I share online, and I regularly update my devices. I also make a habit of reviewing my digital footprint every now
and then, and keeping an eye out for any unusual activity. For me, it’s about practicing the same habits I’d recommend to others.
Reflecting on your journey this far, would you, with the benefit of hindsight, make any changes to your career trajectory? If yes, what adjustments would you consider? Looking back, I feel like every step has taught me something valuable. If I could change one thing, I would have built a stronger technical foundation before starting my degree. In my first year I often felt like I was playing catch up, but that experience taught me how to work under pressure. Additionally showing me not everyone needs to start at the same starting point to reach the same goal.
Have you actively sought employment opportunities in the cybersecurity field, and if so, what has been your experience with the application and interview process?
I’ve been fortunate that my job search so far has gone well. I’ve used platforms like Summer of Tech (SoT), which are great for getting your foot in the door. I encourage new students to sign up to SoT, because there’s an abundance of events, feedback sessions, meet/greets, etc, which is great and the people are truly supportive when you’re navigating the beginning of your career.
So far the biggest challenge for me has been dealing with the automated parts of the process, CV scanners, AI filters, and sometimes instant acceptances or rejections in the span of 10 minutes, without much feedback. That can be disheartening, but networking has made a big difference. Talking directly to people in the industry I’ve found often opens more doors than just applying online at times. The biggest takeaway I’ve learnt is to just keep applying, ask for feedback and to always try.
www.linkedin.com/in/krishapatel-


Sneha Banerjee is currently pursuing a Master of Science in Artificial Intelligence and Machine Learning (Full-Time) at the University of Birmingham, while also completing a Master of Technology in Artificial Intelligence and Machine Learning (Part-Time) at BITS Pilani.
Master of Science in Artificial Intelligence and Machine Learning student at the University of Birmingham and Master of Technology in Artificial Intelligence and Machine Learning student at BITS Pilani.
If you thrive on learning fast, thinking on your feet, and knowing that your work truly makes a difference, cybersecurity offers an incredibly dynamic and fulfilling journey.
Reflecting on your initial perceptions of cybersecurity when you first considered studying it, how does the reality of your experiences today compare?
In a casual conversation with someone unfamiliar with the field, how do you articulate the excitement and potential of a career in cybersecurity, aiming to spark their interest?
A career in cybersecurity feels like solving an ever-changing puzzle, one where every day brings something new to uncover. There’s always a fresh challenge, a new threat to analyse, or a system to strengthen, and that constant evolution keeps things exciting. No two days ever feel the same, and the decisions made in the heat of a cyber incident can genuinely influence the direction of an entire company.
What I love most about this field is how it blends problem-solving, critical thinking, and quick decisionmaking. It’s not just about defending systems it’s about staying one step ahead, testing your limits, and learning from real-world scenarios through things like penetration testing, threat hunting, and incident response.
When I first discovered cybersecurity, I was instantly captivated by its core concepts—threats, attacks, and vulnerabilities and how a single weakness in a system could spiral into a full-scale incident. The idea that cybersecurity plays such a vital role in protecting data, software, and hardware really drew me in. I was fascinated by principles like the CIA triad Confidentiality, Integrity, and Availability along with Authentication and Accountability, and how they all work together to keep systems secure. Learning about attack vectors like SSRF, CSRF, XSS, and SQL injection, and seeing how new technologies such as cloud computing, IoT, and AI introduce fresh risks like LLM poisoning, agentic AI threats, and exposed APIs made the field feel endlessly dynamic and intellectually stimulating.
But theory is only part of the story. In the real world, cybersecurity often means working under pressure, in the middle of an active threat, where every decision counts. The conceptual knowledge you start with becomes the foundation for much deeper, hands-on challenges like designing high-fidelity detections, staying ahead of emerging attack trends, managing stakeholder expectations, and navigating complex organisational hurdles just to gain access to the right tools and data.
What truly defines this field is how unpredictable and creative it can be. You might learn about something like a Golden SAML attack in theory, but when it happens in the wild perhaps combined with AIdriven tactics it rarely looks like the textbook version. Defending against these evolving threats demands curiosity, strategic thinking, and a willingness to
experiment. It’s a constant learning curve, and over time, those real-world experiences shape a kind of intuition that no lecture or certification can teach. That’s what makes cybersecurity not just a career, but a journey of continuous growth and discovery.
Upon graduation, which specific cybersecurity role do you aspire to secure employment in, and what motivates your choice?
As I continue my studies in AI and Machine Learning, I’m eager to move into a role that blends these technologies with cybersecurity specifically, building AI models that strengthen threat detection. I’ve already explored this intersection by developing anomaly detection systems that integrate cascaded signature-based methods, and I’ve seen firsthand how these can dramatically improve accuracy, precision, and recall in existing security detection frameworks.
Since my specialisation is in Natural Language Processing (NLP), I have a deep understanding of how techniques like word embeddings, POS tagging, and parsing work behind the scenes. I’m excited about applying that knowledge to create Conversational AI and Agentic AI tools that not only push innovation forward but also uphold principles of responsible and ethical AI.
My motivation to pursue a more AI-focused path in security really took shape during a project I worked on at Microsoft. In that project, I mapped data sources to MITRE ATT&CK TTPs and used machine learning to classify those sources based on the type of information they contained. I then built a knowledge graph using Neo4j, which allowed threat hunters to query it in natural language and instantly identify which data sources to investigate for a specific TTP. The project felt ahead of its time and gave me a glimpse of just how transformative AI can be when applied thoughtfully to cybersecurity.
Looking ahead, I aspire to take on roles such as AI Security Researcher, AI/ML Engineer (with a
cybersecurity focus), or Security Data Scientist— positions that would allow me to continue bridging the gap between artificial intelligence and security innovation.
When you decided to pursue a career in cybersecurity, how did your parents, peers, or career advisors react? Did you encounter any opposition, and if so, how did you navigate those challenges?
After graduation, I’m excited to pursue a career at the intersection of AI, machine learning, and cybersecurity roles like AI Security Researcher, Security focused ML Engineer, or Security Data Scientist really align with my interests. My motivation comes from my current studies in AI and ML, especially in areas like anomaly detection, NLP, and responsible AI.
I’ve had hands-on experience building cascaded anomaly and signature-based detection systems, and it was incredible to see how AI can dramatically improve the accuracy, precision, and recall of threat detection. With my NLP specialisation, I’m particularly drawn to applying techniques like word embeddings, POS tagging, and parsing to create Conversational and Agentic AI tools that make threat analysis more intuitive, efficient, and scalable.
One project that really shaped this goal was during my time at Microsoft. I developed a system that used machine learning to classify enterprise data sources, mapped them to relevant TTPs (Tactics, Techniques, and Procedures), and built an interactive knowledge graph in Neo4j. This allowed threat hunters to query data in natural language and instantly find the datasets most relevant to a specific TTP.

SNEHA BANERJEE
Seeing the impact and innovation behind that project convinced me of the power of merging AI with cybersecurity.
This blend of cutting-edge AI and meaningful security outcomes is exactly where I see myself making the most impact—developing solutions that not only advance technology but also help protect organizations in smarter, more effective ways.
Who or what has been the most influential factor in shaping your journey in cybersecurity so far, and how has it impacted your career aspirations?
I’d say my journey in cybersecurity has been shaped by a mix of people, experiences, and personal drive, rather than a single defining moment.
First and foremost, my parents played a huge role by encouraging me to take a leap into cybersecurity at a time when it wasn’t a well known career path. Their belief in my potential gave me the confidence to explore a challenging and unconventional field.
I’ve also been lucky to have mentors who introduced me to ethical hacking and stressed the importance of mastering the fundamentals, something that’s been invaluable as the tech landscape continues to evolve. Their guidance taught me to approach problems with both curiosity and discipline.
On my part, my own motivation to keep learning, upskilling, and staying ahead of emerging trends has been a constant driver. Cybersecurity moves fast, and that pace keeps me energized and eager to grow.
Finally, the real-world projects I’ve worked on across different organizations have had a big impact on me. They’ve given me the chance to turn theory into practice, tackle complex problems, and see firsthand how innovative approaches, especially those involving AI and ML, can transform security operations.
All of these experiences together have not only shaped my career path but have also reinforced my goal of working at the cutting edge of cybersecurity and AI.
Recount the most memorable or significant event in your cybersecurity journey to date, highlighting why it left a lasting impression. One of the most impactful milestones in my cybersecurity journey was leading a project focused on data modeling key security events across Azure, Windows, and Linux platforms. The goal was to define, connect, and analyze data objects in a way that could drive meaningful threat analytics and validate the detection of adversary techniques.
What made this project especially memorable was seeing abstract detection concepts come to life as actionable insights. I built a proof of concept using ARMProd Logs and Scuba Caspian Logs, prioritizing adversary techniques based on real operational data. For example, I found that a storage operation tied to the SAS URI Generation technique (AZT701.2) made up 36.36% of tracked techniques in Azure Resource Manager Logs. Along with two other operations, these accounted for nearly 80% of detected techniques, which highlighted key areas for focused detection efforts.
To support the wider security teams, I created heat maps aligning Azure TTP coverage with the MITRE ATT&CK framework and visualized relationships in Neo4j. This allowed Hunt, Detection Engineering, and SOC teams to explore how events, techniques, and log sources were interconnected in a more intuitive way. I also developed Jupyter notebooks to make the analysis reproducible and easily shareable across teams.
This project was a turning point for me because it bridged the gap between raw telemetry and strategic detection engineering. It strengthened my technical skills—from data modeling and visualisation to TTP
mapping—while reinforcing my belief in the power of data-driven security. It was a clear example of how thoughtful engineering can make a real impact on enterprise level threat detection.
Beyond your academic studies, what practical experience have you gained in the field of cybersecurity through employment or internships?
Beyond my academic studies, I’ve been fortunate to gain hands-on experience across multiple areas of cybersecurity, building a well-rounded and practical skill set along the way.
Currently, I work as a Security Researcher at Microsoft, where I get to apply advanced AI and ML techniques to real-world cybersecurity challenges. Some highlights include deploying an LSTM-based anomaly detection system that boosted detection accuracy by 25%, and designing HMM and BiLSTM models to identify DGA-based domains—greatly improving command-and-control (C2) detection. I also led a project simulating adversarial scenarios using game theory to optimize incident response strategies and built self-service SOC analytics dashboards, giving analysts deeper, real-time insights and streamlining root cause analysis.
Before that, as a Senior Cyber Threat Analyst at Nike, I focused on automating alert triaging through SOAR integration, which cut mean time to detect (MTTD) by 35%. I designed dynamic dashboards to analyze over 27TB of threat telemetry, enhancing triage and response efficiency, and worked closely with DevSecOps teams to embed security controls into CI/CD pipelines, ensuring security was considered from the start of development.
Earlier in my career, I worked as a Penetration Tester at Aujas, performing application and network-layer assessments that uncovered critical vulnerabilities. My recommendations helped clients shorten patch cycles and strengthen their overall security posture.

Together, these experiences have given me a strong foundation in threat detection, incident response, offensive security, and secure system design—all within large-scale, real-world environments. They’ve also reinforced my belief in the power of combining automation, datadriven insights, and cross-functional collaboration to deliver meaningful security outcomes.
The cybersecurity industry offers various certifications from different organisations. Have you pursued, or do you plan to pursue any of these certifications? If so, which ones, and what factors influenced your choice? Yes, I’ve pursued several industry-recognized certifications that closely align with my technical focus and long-term goals in cybersecurity.
For example, the GIAC Certified Incident Handler (GCIH) helped me deepen my skills in detecting and responding to complex security incidents, giving me hands-on experience with advanced attack scenarios. The Certified Azure Red Team Professional (CARTP) reflected my interest in offensive security within cloud environments, allowing me to explore Azure-specific attack vectors and adversary simulation techniques.
To strengthen my understanding of secure cloud design, I earned the AWS Certified Solutions Architect – Associate, which taught me how to build and deploy systems with strong security principles in mind. I also completed the Certified Ethical Hacker (CEH v10), which provided a solid foundation in penetration testing, vulnerability analysis, and ethical hacking methodologies.
I chose these certifications with three things in mind: practical applicability to real-world scenarios,
relevance to my current and future roles, and the credibility of the issuing organizations. I’ve intentionally focused on programs that include hands-on labs and challenge exercises, because I truly believe that experiential learning is what makes you effective in cybersecurity.
Given the rapid evolution of cybersecurity threats, do you feel that your academic program adequately keeps pace with the industry’s current landscape?
Yes, I feel that my M.Tech in Artificial Intelligence and Machine Learning at BITS Pilani does a great job of staying relevant to the evolving cybersecurity landscape, especially where AI intersects with security. The program offers forward-looking courses like AI/ML in Cybersecurity, Deep Reinforcement Learning, and Statistical Modeling, all of which directly apply to areas such as behavioral analytics, advanced threat detection, and adversarial resilience.
That said, I recognize that the pace of change in cybersecurity often moves faster than any academic program can cover. To bridge that gap, I actively complement my studies with hands-on experience. At Microsoft, for example, I work on real-world applications of AI in cybersecurity—everything from DGA detection and adversarial simulations to SOC alert analytics—giving me the opportunity to apply cutting-edge research in operational settings.

I also pursue industry certifications and lead independent projects to stay current with the latest tools, tactics, and trends. Combining academic rigor with practical experience helps me remain adaptable and prepared for emerging threats and technologies.
In short, while no academic program can capture the full speed of change in cybersecurity,
my M.Tech provides a solid foundation—one that I continuously expand through real-world experience and self-driven learning.
What aspect of your cybersecurity studies excites you the most, and why?
What excites me most about my cybersecurity studies is the way AI and machine learning can be applied to real-world threat detection—especially the chance to uncover sophisticated attack patterns that traditional rule-based systems often miss.
I’m particularly drawn to areas like anomaly detection, adversarial simulation, and generative AI input auditing, where innovative approaches can directly strengthen defenses. Working on projects like building BiLSTM and HMM models to detect DGAbased domains, or deploying LSTM-based systems to spot malicious behaviors, has shown me just how powerful intelligent systems can be in proactively mitigating threats.
What makes this field truly thrilling is the opportunity to model attacker behavior, anticipate compromises before they happen, and design adaptive, explainable defense mechanisms. It’s a space that constantly challenges me to learn, think creatively, and problemsolve—but every solution also has a tangible, realworld impact.
That combination of technical depth, innovation, and purpose is what keeps me motivated and excited to push the boundaries of what’s possible in cybersecurity.
Conversely, which aspect of your studies do you find least interesting or useful, and how do you navigate through it?
One part of my studies that I find particularly valuable is exploring foundational security models and earlier cryptographic protocols. While they might not show up in the latest technologies every day, they provide crucial context for how today’s cybersecurity frameworks have developed.
Learning these core principles helps me understand the reasoning behind modern system designs and equips me to work effectively with legacy infrastructure when needed. I really enjoy connecting these foundational concepts to real-world applications and seeing how they continue to shape current best practices—it’s like uncovering the roots of the security decisions we rely on today.
Are there specific aspects of your cybersecurity studies that you find particularly challenging? If so, what are they, and how do you approach overcoming these challenges? Yes—one of the trickiest parts of studying cybersecurity is finding the right balance between depth and breadth in such a vast, fast-moving field. From cryptographic algorithms and cloud security to adversarial machine learning and software supply chain risks, there’s always more to explore. Juggling both AI/ML and application security, I sometimes feel like diving deep in one area means I’m falling behind in another.
To handle this, I use a rotational focus approach. I dedicate focused “learning sprints” to specific domains—like LLM security, cloud incident response, or advanced evasion techniques—while keeping a broader awareness of other areas through curated reading lists, security podcasts, GitHub projects, and threat intelligence feeds.
Adversarial machine learning and model robustness are particularly challenging for me. The research is often cutting-edge and abstract, so I make it more tangible by translating academic papers into small, reproducible experiments using real-world data like DNS or API logs. This helps bridge the gap between theory and practice.
Ultimately, I view these challenges as opportunities— they point to areas with the greatest potential for learning, growth, and innovation. Embracing them has been essential to staying engaged, adaptable, and excited in a field that never stops evolving.
Do you believe there are areas in cybersecurity that deserve more emphasis in your coursework or areas that could receive less focus?
Overall, I think the curriculum does an excellent job of covering both foundational cybersecurity principles and emerging areas like AI-driven threat detection and adversarial machine learning—topics that feel especially relevant as the industry shifts toward intelligent, proactive defense.
That said, I would love to see even more handson exposure to these advanced subjects through labs, real-world case studies, or simulations that mimic active threat environments. Experiences like these can really bridge the gap between academic knowledge and operational readiness, which is especially valuable for students aiming for highimpact security roles.
On the other hand, some of the more traditional topics—like legacy perimeter-based defense models or deep dives into specific protocols—could potentially be streamlined. While they provide useful historical context, their direct application in modern, cloud-native environments is sometimes limited.
Overall, I really appreciate how the program balances core theory with forward-looking innovation. It’s encouraging to see coursework that evolves alongside industry trends while still grounding students in the essentials of cybersecurity.
Considering the holistic requirements of a future role, do you see the need for additional training in non-cyber skills, such as interpersonal communication or management? If yes, why?
Yes, absolutely. I’ve come to realize that as cybersecurity roles evolve, non-technical skills— like communication, strategic thinking, and leadership—are just as important as technical expertise, especially in cross-functional and enterprise environments.
Through my experience leading projects in anomaly detection, SOC analytics, and adversarial simulation, I’ve learned how crucial it is to clearly communicate complex technical insights to non-technical stakeholders, collaborate across diverse teams, and align cybersecurity initiatives with broader business goals. Whether it’s translating a machine learning model’s output into actionable insights for SOC analysts or explaining threat impact to executive leadership, strong communication can make all the difference in driving informed decisions and meaningful action.
I also see immense value in developing management and leadership skills—coordinating projects, engaging stakeholders, and mentoring others—so I can take on roles that combine deep technical expertise with organizational influence.
While technical proficiency remains my core focus, I view these non-technical skills as essential for creating long-term impact, leading teams effectively, and navigating the increasingly interdisciplinary nature of cybersecurity.
Are you actively engaged in the broader cybersecurity community? If so, what has been your involvement, and how has it enriched your experience?

Yes, I’m actively involved in the broader cybersecurity community, and it has been one of the most rewarding parts of my journey. My participation spans technical contributions, mentorship, public speaking, and engagement in global forums and competitions.
I’ve been honored to be recognized as a Cybersecurity Women Influencer by BSides Bangalore, a Woman Trailblazer in Cybersecurity by
NASSCOM, and selected as a Global Representative for Microsoft Women in Cyber. These opportunities have allowed me to share insights on AI/ML in cybersecurity, advocate for responsible AI, and collaborate with professionals from diverse backgrounds and regions.
On the technical side, I’ve taken part in competitions like the SANS SEC504 CTF, earning a Capture the Flag coin, and I regularly contribute to the community through open-source projects, including Jupyter notebooks and Neo4j visualizations for TTP and attack technique mapping.
Being involved in the community has not only kept me up to date with emerging threats and tools, but it has also helped me sharpen skills like leadership, public speaking, and collaborative problem-solving. It’s a space where I get to continuously learn, give back, and grow—not just as a cybersecurity professional, but as someone contributing meaningfully to the field.
What is your preferred source for staying informed about cybersecurity trends and general information?
I take a multi-channel approach to staying current in cybersecurity, combining industry intelligence, technical deep dives, academic research, and community engagement.
For high-level trends and threat intelligence, I regularly follow trusted sources like Microsoft Threat Intelligence, MITRE ATT&CK updates, Mandiant, CISA, and CrowdStrike reports. These help me stay aware of evolving threat actors, TTPs, and industrywide risk patterns.
To dive deeper into technical developments, I rely on blogs and GitHub repositories from leading research teams, including Google Project Zero, NCC Group, OpenAI, and other contributors in the AI/ML and security communities. These sources often provide cutting-edge research, adversarial techniques, and
practical toolkits. I also track preprints on arXiv to stay updated on developments in adversarial ML, model robustness, and secure AI.
Community platforms like Twitter/X, Reddit’s r/ netsec, and LinkedIn groups offer timely insights, niche findings, and ongoing discussion threads that surface emerging topics not yet covered in formal publications.
For hands-on learning, I follow resources like the Threat Hunting Project, Malware Traffic Analysis, and regularly participate in CTFs and lab exercises. This blended approach allows me to stay grounded in both research-driven innovation and practical, realworld application—essential in a field that evolves as quickly as cybersecurity
Have you ever encountered situations where being a woman in cybersecurity made you feel disadvantaged or discriminated against? If so, please share your experiences.
While I’ve been lucky to work in environments that value skill and impact, there have definitely been moments—especially earlier in my career—where being a woman in cybersecurity came with subtle challenges. These weren’t always overt, but often meant having to work harder to be heard or taken seriously, particularly in technical discussions or male-dominated teams. Sometimes assumptions were made about my role or expertise, and I had to consistently prove myself before being seen as a peer.
Rather than letting these experiences discourage me, I used them as motivation to strengthen my skills, lead meaningful projects, and mentor others entering the field. Over time, I’ve found support and inspiration through networks like Microsoft Women in Cyber, BSides, and NASSCOM’s Women in Cybersecurity initiative. Being able to give back and be recognised in these communities has really highlighted for me the power of representation, allyship, and advocacy.
While challenges still exist, I’m encouraged by the growing awareness and support for women in cybersecurity, and I’m committed to being part of that progress.
What measures do you have in place to enhance your personal cybersecurity in today’s digital landscape?
As a cybersecurity professional, I approach my personal security with the same care I would for an organisation. I like to think of it as a layered approach—covering everything from accounts and devices to data and online habits.
At the basics, I make sure every account has a strong, unique password stored in a trusted password manager, and I enable multi-factor authentication wherever I can. I also separate my digital life into different environments—financial, personal, and professional—to reduce risk.
On my devices, I keep systems and software up to date, use trusted endpoint protection, and avoid installing anything unverified. I also follow safe browsing habits, using privacy-focused tools and script blockers to stay protected online.
When it comes to data, I regularly audit app permissions, encrypt sensitive files, monitor account activity, and maintain strict controls in the cloud reviewing connected apps and managing tokens to keep things secure.
I also stay up to date with threat intelligence and security alerts so I can act quickly if new vulnerabilities arise. For me, personal cybersecurity isn’t a one-time setup—it’s an ongoing mindset of awareness, adaptation, and proactive protection.
Reflecting on your journey thus far, would you, with the benefit of hindsight, make any changes to your career trajectory? If yes, what adjustments would you consider?
Looking back, I’m really proud of the path I’ve taken— from penetration testing to threat analytics, and now into AI-driven cybersecurity research. Each stage has taught me something valuable and helped shape both my technical skills and strategic thinking.
That said, if I could go back, I might have explored the intersection of AI/ML and cybersecurity earlier. That’s where I find the biggest challenges—and the most impact. The early part of my career gave me a strong foundation in traditional security, which has been invaluable, but diving into applied AI sooner— especially in areas like behavioral analytics and adversarial ML might have accelerated some of what I’m doing today.
I also think I would have sought out more interdisciplinary experiences earlier on, like working with data science or policy teams, to better understand the broader context behind security decisions.
Even so, I don’t see these reflections as regrets— they’re lessons that now guide how I mentor others and shape the direction I want to take next. The journey so far has been incredibly rewarding, and I’m excited to keep evolving alongside this everchanging field
Have you actively sought employment opportunities in the cybersecurity field, and if so, what has been your experience with the application and interview process?
Yes, I’m actively looking for opportunities in cybersecurity, especially roles at the intersection of AI research and security. I’m excited by the chance to work on things like adversarial machine learning, AI-driven threat detection, LLM security, and secure MLOps.
So far, the application and interview process has been both engaging and eye-opening. These roles really test a mix of technical knowledge, research
thinking, and practical problem-solving. Interviews often involve exercises on model design and robustness, technical discussions, and case studies to see how well you can apply AI/ML to real-world security challenges.
What I’ve found most rewarding is that many teams value cross-disciplinary experience—the ability to think like a threat analyst, build like a data scientist, and design like a security engineer. I’ve received encouraging feedback when sharing projects like BiLSTM-based DGA detection, adversarial simulation frameworks, and SOC alert analytics tools built with deep learning and behavioral models.
I’m really looking forward to continuing this journey, growing as a research-driven practitioner, contributing to responsible AI in cybersecurity, and helping shape the next generation of intelligent defenses.
www.linkedin.com/in/sneha-banerjee-b10a2b1aa




How We Got Cyber Smart addresses cyber safety, cyber bullying and online safety for elementary school-aged children.

Lisa has partnered with Cool.Org , and her content is found on the Department of Education website

Author of How We Got Cyber Smart | Amazon Bestseller
Olivia and Jack had been looking forward to their Saturday outing all week. Their grandparents, Nanna and Pappa, had promised to take them to see the new adventure film everyone had been talking about. The four of them were standing in the cinema lobby, the smell of popcorn drifting around them, when Pappa pulled out his card to pay.
The cashier tapped a few buttons, swiped the card again, then frowned. “I’m sorry, sir,” she said. “It’s been declined.”
“That can’t be right,” Pappa muttered, trying again. Nanna frowned too, adding, “The account was fine yesterday.” But the same error message flashed up: Insufficient funds.
Olivia and Jack exchanged a look. Something was very wrong.
On the drive back to their grandparents’ house the car was silent. Pappa gripped the wheel tighter than usual. “Perhaps it’s a system glitch,” he said at last, but he didn’t sound convincing.
By the time they reached home their parents had already arrived, called over by a worrying text message. Everyone sat down around the old dining table. Nanna finally sighed and began to explain.
“We had a call yesterday,” she said slowly. “A man rang and said he was from the bank’s security team. He told us our

account had been compromised and that he needed to verify our details to stop fraudulent charges.”
Olivia, always quick with questions, frowned. “Did he call you, or did you call the bank?”
“He called us,” Nanna admitted. “He knew our names and even our address. He sounded so professional. He said he just needed our account number and password so he could secure things.”
Olivia and Jack’s mother groaned quietly and covered her face with her hands. Their father rubbed his temples. “That was the fraud. Banks don’t ask for those details over the phone.”
The grandparents looked stricken. “But we thought we were protecting ourselves,” said Pappa.
“It isn’t your fault,” Olivia and Jack’s mother reassured the grandparents. “These scammers are clever. They know how to make people panic so they react instead of questioning things.”
Olivia piped up, remembering something her teacher had said. “Our teacher told us that if someone makes you feel rushed on the phone it’s probably a trick. They want you to say yes before you think clearly.”
“And remember how we learnt never to click links from random emails or texts?” Jack said earnestly. “It’s the same with calls. If
somebody says they’re from the bank you hang up and call the number on the back of your actual card.”
The grandparents listened carefully. It hurt them to realise they had been deceived, especially since they had always tried to be cautious.
Their father rang the real bank straight away and reported the fraud. The staff were friendly but firm. The money had already been taken and moved through several accounts, which meant it might not come back. They froze the old account, helped to open a new one, and promised to investigate.
Olivia and Jack stayed close while all of this was sorted out, throwing in ideas they had picked up in school or online. “Make sure you add two factor authentication,” Olivia said, trying to sound like an expert. Jack added, “And maybe you can use a password manager so you don’t have to write everything down.”
Their parents looked at the twins with pride. At their age they already had a good grasp of what security meant in a digital world.
That night Nanna sat at the kitchen table quietly sipping her tea. “I feel foolish,” she admitted. “We’ve always done our best to be careful with money, and then this happens.”
Jack gave her a hug and said, “You’re not foolish. You just trusted someone who sounded real. That’s what good people do.”
Olivia leant against Pappa’s chair. “And now we know how to spot the signs. You taught us how to be careful crossing the road when we were little. Now we can remind you how to be careful with calls and messages.”

The following weekend Olivia and Jack finally went back to the movies. This time their parents paid for the tickets, just to be safe. Pappa joked that he might stick to plain old cash for a while.
As they sat in the dark with their snacks waiting for the opening scene, Olivia leaned over to Jack; “You know, maybe the scammers didn’t win. We all learnt something.”
Jack grinned back. “Exactly. And we’ll keep an eye out for Nanna and Pappa until they feel confident again.”
The film’s heroes soon filled the screen, but for Olivia and Jack the real lesson had been hidden in an ordinary phone call. And they knew it would stick with them far longer than the movie.
www.linkedin.com/in/lisarothfield-kirschner
howwegotcybersmart.com


















1. CRAIG FORD
Head Unicorn – Cofounder and Executive Director, Cyber Unicorns. Australian Best Selling Author of A Hacker I Am, Foresight and The Shadow World book series. vCISO – Hungry Jacks, Wesley Mission, PCYC and Baidam Solutions
2. PALLAVI KAUL
Associate Director, Deloitte
3. ERIN CARROLL
Cyber Risk Consultant
4. ANISHA DAD
Cybersecurity Intern, SPYINT
5. SUSAN VERDIN
Security Researcher with (Confidential) and Host of Secure Kids Now! Network, a Podcast/Show on protecting children online
6. NAOMI ONUOHA
Cybersecurity Engineer
7. MARIVELL ALICEA-GAMLIN
Senior Cybersecurity BISO Analyst
8. SARITA PADMINI
Senior Director – Cyber Security
9. LAUREN WEBBER
Cyber Consultant, KPMG
10. SAKSHI KISHORE
Associate Director, Technology Risk and Cyber, KPMG Australia
11. KAREN STEPHENS
CEO and co-founder of BCyber
12. AMANDINE NURY
Global CISO Programs Director
13. CHERIE BURGETT
Director, Cyber Intelligence Operations
14. FAITH NSIKAK
SOC Analyst/Incident Responder
15. SANA TALWAR
Product Security Engineer
16. NIRALI R BHATIA
Cyber Psychologist & Psychotherapist, Founder Cyber Wellness Foundation, Director of V4WEB, A Web Solutions & Cyber
Security Company
17. NAMRATA BARPANDA
Staff Information Security Engineer
18. LISA VENTURA MBE FCIIS
Chief Executive and Founder, AI and Cyber Security Association


















19. JOANNE COOPER
Founder - ID Exchange
20. SHRUTI KAMATH
Consultant, Business Resilience, KPMG
21. MARYAM MORADI
Consultant, Tech Risk & Cyber Consulting, KPMG
22. JAY HIRA
Cyber Director – Financial Services, KPMG
23. MADHURI NANDI
Madhuri Nandi, Head of security at Nuvei, AWSN Board Chair, author of Cyber Smart
24. MARINA TOAILOA
Business Risk & Compliance
25. IBITOLA AKINDEHIN
AI Governance Risk and Compliance Specialist
26. MARISE-MARIE ALPHONSO
Cyber Security GRC Specialist
27. JO STEWART-RATTRAY
Oceania Ambassador, ISACA
28. JAKUB ZVERINA
Head of Cyber Workforce Growth and Partnerships, CyberCX
29. CHRISTOPHER HARRELL
Chief Executive Officer
30. EMA CORREIA
Senior Cybersecurity Consultant, KPMG Portugal
31. AMANDA-JANE TURNER
Author of the Demystifying Cybercrime series and Women in Tech books. Conference Speaker and Cybercrime specialist
32. OASIS KAUPPILA Online Cyber Security Student
33. NANDINI SIVARATHRI
Master of Cyber Security & Digital Forensics student at Auckland University of Technology
34. KRISHA PATEL
Cyber security student at Victoria University of Wellington
35. SNEHA BANERJEE
Master of Science in Artificial Intelligence and Machine Learning student at the University of Birmingham and Master of Technology in Artificial Intelligence and Machine Learning student at BITS Pilani.
36. LISA ROTHFIELD-KIRSCHNER
Author of How We Got Cyber Smart | Amazon Bestseller

Check Point Software Technologies Ltd. is a leading provider of cybersecurity solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyberattacks with an industry-leading catch rate of malware, ransomware, and other types of attacks. Check Point offers multilevel security architecture, “Infinity” Total Protection with Gen V advanced threat prevention, which defends enterprises’ cloud, network, and mobile device-held information. Check Point provides the most comprehensive and intuitive one point of control security management system. Check Point protects over 100,000 organizations of all sizes.


Cybersecurity affects everyone, including in the delivery of basic products and services. If you or your organization want to better understand how to address your cybersecurity, this is the course for you and your colleagues to take -- from seasoned professionals to your nontechnical colleagues. Your instructor, Dr. Charles Harry, has served on the front lines with the NSA (National Security Agency) and as an expert advising corporate and institutional leaders on managing cybersecurity risk. And he brings a rare and engaging perspective to help you learn cybersecurity from the ground up.

In this introduction to the field of computing security, you will be given an extensive overview of the various branches of computing security. You will learn cybersecurity concepts, issues, and tools that are critical in solving problems in the computing security domain.




Want to know more about ethical hacking? Sign up for our free course and learn about ethical hacking and offensive security. The course is conveniently self-paced, and will also introduce you to the legal boundaries that distinguish “ethical” from “unethical” hacking, and the careers ethical hackers can pursue.

This course is designed to provide an understanding of key cybersecurity concepts. The modules you'll explore include Physical Security, where you will learn about effective data destruction techniques and the importance of physical access control to protect critical assets; Security Assessment, to understand how to conduct thorough vulnerability scans and identify potential security weaknesses; Incident Response and Digital Forensics: to discover the tools and techniques used for incident detection and response, and how to apply digital forensic concepts to investigate security breaches; and Security Standards and Policies: to gain insights into the frameworks and standards that guide cybersecurity practices and ensure regulatory compliance.
In an era where cyber threats are becoming increasingly sophisticated and pervasive, traditional security models that rely on perimeter defenses are no longer adequate to protect sensitive data and critical systems. This e-lesson on Zero Trust Architecture (ZTA) offers a comprehensive exploration of the Zero Trust security model, which fundamentally shifts the approach to cybersecurity by adopting the principle of "never trust, always verify.
VISIT HERE



This is CS50's introduction to cybersecurity for technical and nontechnical audiences alike. Learn how to protect your own data, devices, and systems from today's threats and how to recognize and evaluate tomorrow's as well, both at home and at work. Learn to view cybersecurity not in absolute terms but relative, a function of risks and rewards (for an adversary) and costs and benefits (for you). Learn to recognize cybersecurity as a trade-off with usability itself. Course presents both high-level and low-level examples of threats, providing students with all they need know technically to understand both. Assignments inspired by real-world events.
VISIT HERE


Prepare for a new career in the high-growth field of cybersecurity, no degree or experience required. Get professional training designed and delivered by subject matter experts at Google and have the opportunity to connect with top employers. Organizations must continuously protect themselves and the people they serve from cyber-related threats, like fraud and phishing. They rely on cybersecurity to maintain the confidentiality, integrity, and availability of their internal systems and information. Cybersecurity analysts use a collection of methods and technologies to safeguard against threats and unauthorized access — and to create and implement solutions should a threat get through.
VISIT HERE

This course will teach you how to digitalize the 'conventional' grid and which digital technologies you can use for this, including but not limited to, AI, machine learning, blockchain and computer simulations.
VISIT HERE



The Cyber Wardens program is a simple education tool designed to make your small business cyber-safe. Educating your team about cyber threats will help to protect your small business against cyber threats and recover from a cyber attack.
VISIT HERE
Cybersecurity is more than just a technical issue, it is deeply shaped by policy decisions, regulatory frameworks, and user behavior. This course takes an interdisciplinary approach, combining political science, law, psychology and more, to examine:
• Cyber risk governance: How governments, industries, and institutions regulate digital threats.
• Regulatory frameworks and compliance: Understanding evolving cybersecurity laws and norms.
• Human behavior and cybersecurity: How individuals make security decisions online and the psychology behind cyber risk.
VISIT HERE
In developing the digital ecosystem, a CIO adds value by strategically infusing business with innovative digital technologies. This requires an understanding of the range of technologies that are transforming the way business is done. Additionally, a successful CIO must be able to manage the adoption, implementation, and diffusion of tech within an organization. This includes analyzing the role of innovation and executing change strategies.
VISIT HERE



With Hacker Valley Studio
This unique podcast is about the stories behind the people in cybersecurity. From former hackers turned executives to infosec professionals navigating burnout, imposter syndrome, and growth, the show highlights the emotional and personal side of a deeply demanding industry.

Produced by CISOS in car (Kelly Haydu)
Kelly Haydu, VP, Information Security, Technology & Enterprise Applications, in a Tesla Cybertruck around SF at the RSA Conference as they discuss building rapport with engineers, building a data privacy practice, and moving from QA to head of cybersecurity. They talk about data breach reporting and how public companies can approach cybersecurity

With SIW
Women have made significant strides in the security industry in recent years. Greater efforts by organizations like SIA and ASIS have been made to encourage women to enter the cybersecurity workforce, building foundational resources they did not have before. As the cyber talent shortage stretches on with no end in sight, women might provide the burst of energy the industry needs.

With Shielded
Each episode brings you actionable insights, real-world case studies, and expert interviews with cryptographers, industry leaders, and policymakers shaping the future of cybersecurity. From demystifying quantumresistant protocols to addressing compliance challenges and implementation strategies, Shielded moves the conversation from why to how in building a quantum-safe world.

With 401 Access Denied Podcast
In this episode, Joseph Carson interviews Myrna Soto, former Global CISO for Comcast, about the changing role of CISOs. Myrna shares her journey into cybersecurity and highlights the importance of business relationships and brand protection. She also offers tips on communicating with the board and staying informed. Tune in for valuable insights and practical advice!

With Hacker and the Fed Chris Tarbell and Hector Monsegur kick off Cybersecurity Awareness Month with big news—Hector announces the launch of his new company, SafeHill. The guys dig into continuous threat exposure management, the dangers of malicious Chrome extensions, why ransomware claims are dropping, and how free tools from Cybersecurity and Infrastructure Security Agency (CISA) can strengthen defenses.

With AISA (Zoe Adam)
In this insightful episode of Cyber Voices, David Willett interviews Zoe Adam, a seasoned cybersecurity professional leading dynamic teams at CyberCX. Newly energised after her talk at AdelaideSEC, Zoe shares her revolutionary approach to security operations.

With Cyber Security Sauna Cyber Security Sauna brings you expert guests with sizzling insight into the latest information security trends and topics. WithSecure's Janne Kauhanen hosts the show to make sure you know all you need to about the hotter-than-ever infosec game. Join us as we sweat out the hot topics in security.

Hosted by Human Factor Security
Continuing the six-part series CISO Voices, where Jenny talks to CISOs about how they view their role, the industry and the threat landscape, in partnership with Proofpoint, we welcome Bridget Kenyon.People love working in cybersecurity for those high-drama moments. But Bridget discusses with Jenny, that infosec teams should be an everyday part of the business, not an emergency service.
CLICK TO LISTEN

With The Pivot Podcast Jane is a tech entrepreneur, book author, international speaker, and passionate women’s change agent. She is the founder of the IN Security Movement and the author of In Security: Why a Failure to Attract and Retain Women in Cybersecurity is Making Us All Less Safe. With more than 25 years of experience in the field, Jane has built her own penetration company and held senior executive roles at information technology organizations
CLICK TO LISTEN
CLICK TO LISTEN

With Redefining CyberSecurity AI-driven automation with no-code tools is empowering business teams to move fast—but at what risk? In this episode, Walter Haydock, founder of StackAware, joins Sean Martin to outline the hidden dangers, governance gaps, and practical safeguards every organization needs to understand before letting no-code AI fly free. CLICK TO LISTEN
CLICK TO LISTEN
With The Public Sector Podcast: In this episode we are joined by Jacqui Loustau (Executive Director of the Australian Women in Security Network) and Professor Matthew Warren (Director of the RMIT Centre for Cyber Security Research and Innovation) for an eye-opening conversation on advancing gender diversity in Australia’s cybersecurity sector. This episode unpacks the findings from a comprehensive study on the representation and retention of women in cybersecurity—and the steps needed to build a more inclusive, resilient cyber workforce.
CLICK TO LISTEN

Author // Jessica Barker
The world is more digitally connected than ever before, and with this connectivity, comes vulnerability. It is therefore vital that all professionals understand cyber risk and how to minimize it. This means that cyber security skills are in huge demand, and there are vast career opportunities to be taken.

Author // Carol Stewart
"You don't look like an introvert" was a statement made to the author whilst at a networking event, and she thought to herself, what on earth is an introvert supposed to look like... Many misconceptions exist about what introversion is, and this was just one of them.

Author // Sherry Turkle
“In a time in which the ways we communicate and connect are constantly changing, and not always for the better, Sherry Turkle provides a much needed voice of caution and reason to help explain what the f*** is going on.” —Aziz Ansari, author of Modern Romance

Author // Sherry Turkle
Technology has become the architect of our intimacies. Online, we fall prey to the illusion of companionship, gathering thousands of Twitter and Facebook friends, and confusing tweets and wall posts with authentic communication. But this relentless connection leads to a deep solitude.




Author // April Falcon Doss
"Chilling, eye-opening, and timely, Cyber Privacy makes a strong case for the urgent need to reform the laws and policies that protect our personal data. If your reaction to that statement is to shrug your shoulders, think again. As April Falcon Doss expertly explains, data tracking is a real problem that affects every single one of us on a daily basis." —General Michael V. Hayden, USAF, Ret., former Director of CIA and NSA and former Principal Deputy Director of National Intelligence
Author // Nicole Perlroth
Filled with spies, hackers, arms dealers, and a few unsung heroes, written like a thriller and a reference, This Is How They Tell Me the World Ends is an astonishing feat of journalism. Based on years of reporting and hundreds of interviews, Nicole Perlroth lifts the curtain on a market in shadow, revealing the urgent threat faced by us all if we cannot bring the global cyber arms race to heel.
BUY THE BOOK
Authors // Lisa Ventura, Lauren Zink, Goonjeta Malhotra, Liz Banbury, Cheryl Torano, Celine Rowan Pypaert, Annie Jamshed, Lucy McGrother, Dr Semire Yekta, Stephanie Luangraj
“The Rise of the Cyber Women” is a compilation of inspiring stories from women in the cyber security industry from all over the world who are pioneers and leading the way in helping to protect the world from the growing cyber threat. Those who are included and featured in this book shared not only their stories but also their hints, tips and advice to women who are looking to pursue a career in cyber security or change their career path into cyber security.
Author // Shari Mitchell
In a digital age where the virtual realm intersects with our daily lives, cybersecurity stands as the guardian of our digital domains. ""Cyber Crown"" is a powerful and comprehensive guide that not only beckons women to seize their rightful place in this dynamic field but empowers all, regardless of gender, with essential knowledge for navigating the digital landscape safely.




Author // Cheryl Cooper
Imagine this: you've worked tirelessly, honed your skills, and dreamed of making a lasting impact in the dynamic worlds of cybersecurity and technology. Yet, the path forward feels like navigating a labyrinth-blocked by invisible barriers and unspoken rules. In an era where technology evolves at lightning speed, the demand for cybersecurity professionals has never been greater.
BUY THE BOOK
Author // Debra A. Christofferson
This volume examines core areas of development in security, emphasizing the pivotal contributions of women to the field’s evolution. The author first covers a broad spectrum of key topics, including how security is created, where innovation occurs, what the underpinnings are, and who supports it and how.
Author // Chris Oxlade - Illustrator // Nik Neves
Upgrade your tech knowledge with this beautifully illustrated, inspirational, and accessible guide to the fascinating field of computing. From the simplest software to electronic brains, and from smartphone apps to social media and video games, there are gigabytes of data for you to unravel.
Author // Ms Susana Pentland
Welcome to the exciting world of the internet! �� From playing games and watching videos to learning new things, the online world is an amazing place full of opportunities and adventures. But just like the real world, it’s important to stay safe, be smart, and make good choices. That’s where this guide comes in!




By HackerNoon
The most promising cybersecurity innovations are increasingly being developed by former incident responders, red teamers, SOC leads, and threat analysts, but there's a lack of them, according to a HackerNoon blog post.

By CSO
Cybercriminals are no longer focused on big targets alone. They want reach. Everyone is in scope. Many of the most organized groups now operate like legitimate businesses, with payrolls, benefits, and development cycles. Some are backed by nation-states. That gives them resources most private organizations cannot match.

By CDA Press
Cybercrime will cost the global economy over $10.5 trillion annually by the end of 2025, according to Cybercrime Magazine, making strong defenses a necessity for every organization. Hackers are faster and more resourceful than ever, which means businesses can't afford to wait until after a breach to take action.
READ BLOG

By Tommorrow Women
Let’s face it – society often feels unsafe for women thanks to the complexities of cultural, social, and systemic factors. These factors result in gender-based violence, harassment, and discrimination – a disturbing, yet organic part of our society’s fabric.
And it’s not as if these issues are a rare occurrence. Sexual assualt, harassment and domestic violence is rife across every society on the planet. Let’s take a look at a few foundational jarring insights:
READ BLOG
READ BLOG

By Security Boulevard
Telecommunications networks are the foundation of today’s digital infrastructure, linking billions of people and devices across the globe. This critical position makes them particularly vulnerable to sophisticated cyberthreats that constantly evolve and target these essential systems with increasing frequency and intensity. The consequences of security breaches in telecom networks extend far beyond the sector itself, potentially affecting national security, economic stability and critical services.
READ BLOG

UNLOCKING POTENTIAL: GROWING AS A WOMAN IN CYBERSECURITY
By women in cybersecurity (Gurdeep Gill)
I still remember the turning point for me: the first time I decided to speak up in a meeting. I was nervous, my heart was racing but I knew I had something valuable to contribute. When I finally shared my thoughts, it wasn’t about having the perfect idea; it was about allowing myself to take up space and be heard. That moment made me realize that my voice did matter. Each time I found the courage to speak up after that, I felt myself growing more confident and capable.
READ BLOG



By Bernard Marr (Forbes)
In 2025, cyberattacks have continued to grow in both frequency and scale, and 2026 is unlikely to bring reprieve. Emerging technologies like agentic AI and quantum computing create new opportunities for both good guys and bad guys. But as usual, we humans are likely to be the weakest link as well as the most potent defense.
By Bolde
Cyberattacks are no longer distant threats affecting only big corporations; they’re personal, pervasive, and potentially crippling. A report by Cybersecurity Ventures predicted cybercrime damages will cost the world $10.5 trillion annually by 2025, outpacing the damage inflicted by natural disasters.
By Huntress (Rachel Bishop)
I can vouch for the fact that imposter syndrome is one factor. I’ve always been interested in computers and have wanted a career that would help me make the world a better place. I remember talking to my uncle through HyperTerminal when I was a kid, thinking it was the coolest thing ever. I would feed entries into Command Prompt just to see what they did.

By Bloomberg
Bloomberg reports that a recent surge in high-profile cyberattacks is offering an opportunity for insurers including Munich Re AG and Chubb Ltd. to cash in from a rapidly expanding market — and prompting a rethink on premiums. As artificial intelligence makes attacks more widespread and devastating, Munich Re expects the global cyber insurance market to reach $16.3 billion in 2025, up from $15.3 billion in 2024.

By Gizmodo Deals
Today’s world is more connected than ever but that has made it even more dangerous behind the scenes and the numbers are frankly worrying. In just the past year, global cybercrime damages soared past $10.5 trillion according to Cybersecurity Ventures, and the U.S. alone has seen victim losses in the billions – over $2.1 billion lost by Californians and more than $1 billion for Texans, according to FBI data. READ

DEVOPS TOOLS OPEN THE GATES FOR HIGH-PROFILE CYBERATTACKS
By TechRadar Pro
Recent breaches at householdname enterprises reveal an uncomfortable truth: DevOps data is the top priority for cybercriminals. Mercedes-Benz, The New York Times, Schneider Electric — all of them operate in different industries, though there is something in common... each fell victim to DevOps security failures, a reminder that no organization, however advanced, is immune when innovation outpaces protection.

CYBERSECURITY - IDENTITY AND ACCESS MANAGEMENT (SAILPOINT) - SR ASSOCIATE | PWC
FULL TIME UNITED STATES
THE OPPORTUNITY
As part of the Cybersecurity, Privacy and Forensics team you are expected to focus on identity and access management. As a Senior Associate you are expected to analyze complex problems, mentor others, and maintain rigorous standards. You are expected to manage client engagements related to IAM, utilize IAM products, and build meaningful client relationships.
RESPONSIBILITIES
• Manage client engagements related to IAM
• Utilize IAM products effectively


• Analyze complex problems and mentor team members
• Maintain top standards in project deliverables
• Build and sustain client relationships
• Develop a deeper understanding of business contexts
• Utilize professional skepticism to confirm quality work
CYBERSECURITY ENGINEER | INFOSYS
FULL TIME INDIA
ABOUT THE JOB
• 3–4 years of hands-on experience in cybersecurity across multiple domains.
• Strong understanding of security principles, risk management, and threat mitigation.
• Experience implementing security baselines and standards (e.g., CIS, NIST, OWASP).
• Familiarity with security tools such as Tenable, Qualys, CrowdStrike, Splunk, Palo Alto, etc.
• Knowledge of identity and access management (IAM), secure authentication, and least privilege principles.
• Exposure to cloud security (AWS, Azure, GCP) and secure configuration practices.
• Strong analytical and problem-solving skills with attention to detail

• Monitor security tools such as SIEM, endpoint protection, vulnerability scanners, and firewalls to ensure continuous visibility across the environment.
• Ensure all systems, devices, and components within the network are consistently compliant with defined security policies, standards, and configurations.
FULL TIME CANADA
WHAT WILL YOUR TYPICAL DAY LOOK LIKE?
The Technical CRMR Manager is a multifaceted leadership role responsible for overseeing the technical operations and output of the Cybersecurity Risk Management and Reporting (CRMR) team. This includes providing expert technical guidance, ensuring the timely and accurate delivery of reporting / data extraction services, and managing projects effectively to meet stakeholder or business needs. The Technical

CRMR Manager fosters a culture of technical excellence, collaboration, and continuous improvement within the team, while also staying abreast of emerging technologies and industry best practices.
APPLY HERE




FULL TIME ENGLAND
KEY RESPONSIBILITIES:
• Design and implement cloud security architectures that meet client requirements and industry best practices
• Conduct security assessments and provide recommendations to enhance the security posture of cloud environments
• Develop and maintain security policies, standards, and procedures to ensure compliance with regulatory requirements



• Collaborate with clients to understand their security needs and provide tailored solutions
• Lead security assurance activities, including risk assessments, vulnerability assessments, penetration testing, and threat modelling techniques such as MITRE ATT&CK, STRIDE, DREAD, and PASTA
FULL TIME NEW ZEALAND HYBRID
KŌRERO MŌ TE TŪRANGA | ABOUT THE ROLE What your days might look like:
• Delivering security expertise to projects, BAU tasks, and incident response – you’ll get your hands on everything from vulnerability management to security approvals and investigations.
• Jumping into a variety of tools (think MS Sentinel, Netskope, CrowdStrike – but if you’ve used similar, we’re happy to cross-train).
• Creating and updating documentation, running security awareness training, and helping Contact stay ahead of threats.
• Working on exciting projects like the email gateway replacement, vulnerability management, and identity security enhancement.
• Being a trusted advisor, helping teams across the business understand and manage risk, and making sure security is baked into everything we do.
FULL TIME AUSTRALIA
WHAT YOU'LL DO
Global Networks & Technology - Security & Operations is responsible for Telstra's security and operations, protecting Telstra's assets and infrastructure.
• Strategic Relationship Management: Establish and maintain strong partnerships with Group & Technical Product Owners to align on evolving priorities, expectations, and strategic outcomes.
• Cybersecurity Advocacy: Champion effective cybersecurity communication across internal business units, fostering a culture of security awareness and collaboration.

• Security Assessment Engagement: Stay actively involved in mission-critical security assessments, ensuring alignment with enterprise security standards and risk posture.
• Operational Efficiency: Identify and eliminate barriers that impede streamlined cybersecurity assessments, driving continuous improvement in assessment processes.
12 MONTHS SOUTH AFRICA
BRIEF DESCRIPTION
• Manage the Security and Privacy by Design Assurance (SPDA) processes
• Ensure that all projects follow the security-by-design principles, and that privacy and security risks are mitigated from the design phase to implementation.
• Conduct internal and external penetration tests on the company’s infrastructure, web applications, APIs, and network systems to identify vulnerabilities.



• Assess the security of new and existing systems, products, and services to ensure compliance with company security policies, industry standards, and best practices.
• Safely exploit vulnerabilities to determine the risks of unauthorized access or data compromise.
FULL TIME UNITED ARAB EMIRATES
ROLE AND RESPONSIBILITIES
Work as a Cyber Threat Intel Analyst in DTS Solution –HawkEye CSOC cyber command center.
• Analyze and research known indicators, correlate events, identify malicious activity, and discover new sources to provide early warning related to a variety of Cyber threats.
• Monitor Open Source information feeds and threat actor activity to identify activity levels and indicators for Cyber threats and Cyber-attacks.

• Identify Open Source Intelligence (OSINT) threats relevant to the DTS Solution - HawkEye CSOC customer’s environment and develop relevant reports.
• Provide daily (business day) collections, reviews, analysis and filtering of Open Source Intelligence (OSINT) and SOCMINT (Social Media Intelligence)
FULL TIME AUSTRALIA
YOUR NEW ROLE AND RESPONSIBILITIES
We have an exciting opportunity for a Junior Cyber Security Analyst to join our 24/7 Security Operations Centre shift team. In this role you will perform crucial, high value and comprehensive cybersecurity services to support and protect our personnel and systems in the Australian Defence Force. You will be working with our deployed Defence personal in a rapidly maturing environment where you can make a real difference and

influence the future. The shift cycle is over 12-hour blocks, when cycling off shift you will enjoy 4 or 5 days off before starting 4 or 5 on cycle with combination of days then nights




FULL TIME NIGERIA
JOB DESCRIPTION/REQUIREMENTS Responsibilities:
• Identify, assess, and monitor IT-related risks across all subsidiaries.
• Ensure IT and data management policies meet regulatory and cybersecurity standards.
• Monitor system access controls, data protection practices, and disaster recovery plans.
• Collaborate with IT teams to ensure secure digital infrastructure and services.
• Support audits, penetration testing, and business continuity planning.
FULL TIME HUNGARY
KEY RESPONSIBILITIES:
• Shift Left: Ensure good security posture in the terms of application development, always keep security in mind, be a technical help under when remediating pentest/SAST/other issues, evangelize the cyber security requirements and/or give a hand with a solution’s technical details
• Lead the development and implementation of robust security architectures in alignment with industry best practices and regulatory requirements.
• Security Standards: Facilitate compliance with DevSecOps standards and oversee integratation of security measures into the CI/CD pipeline.
FULL TIME ITALY
WHAT YOU’LL BRING: Your experience includes:
• A minimum of 1-2 years of proven experience as a Help Desk Technician or other IT support role
• Tech-savvy with working knowledge of IT equipment, hardware and software
• Good understanding of Apple MacOS and iOS



• Follow up on IT audit findings and ensure timely implementation of corrective actions.
• Help develop awareness programs on cybersecurity and IT compliance.
• Monitor compliance with data privacy regulations (e.g., NDPR, GDPR).
• Stay updated on emerging risks in fintech, remittance, and digital banking environments.
HERE

• Collaboration: Work closely with IT, development, and operations teams to ensure security is integrated into all aspects of the organization's infrastructure.
• Monitoring and Response: Establish and maintain security monitoring, incident response, and disaster recovery plans.
APPLY HERE

• Ability to diagnose and resolve basic technical issues
• Information Security and compliance awareness
• Basic knowledge of IT networking, IPs, DHCP, DNS








As the applause faded and attendees lingered amid the buzz of shared achievement, the 2025 Australian Women in Security Awards gala dinner left the community energised and brimming with pride. The event, marking the awards’ seventh year, was more than a night of recognition. It was a powerful testament to how far the sector has come, and the impact of every individual, team, mentor and advocate working toward an equitable future.

The evening brought together new faces and returning legends under a canopy of spectacular storytelling entertainment, lights, stories and music. For many it was a heartening reunion; for others, their first moment in the spotlight. There was emotion, laughter, tears and inspiration as the award in category after category revealed women, nonbinary professionals and supportive allies raising the bar in IT, cyber, protective security, quantum computing and AI.
This year was not only about technical mastery (although there was plenty of that). The awards honoured innovators tackling tomorrow’s threats, founders creating opportunities, educators who light the way, volunteers, mentors, unsung heroes, and entire workplaces pioneering new standards for
diversity and inclusion. From major companies to boutique consultancies, and from school programs to quantum researchers, the spectrum of achievement was breathtaking.
Sponsors, judges and organisers echoed the gratitude felt throughout the room, recognising that none of these milestones would be possible without the enduring support of a deeply invested community. The judges faced an unenviable challenge: hundreds of nominations across dozens of categories, each one a story of excellence and hard-won progress. Their care and discernment ensured that every finalist, highly commended entrant and winner was celebrated not just for ‘what’ they had achieved, but ‘how’ they had inspired others along the way.
Highlights included the celebration of Australia’s first female-founded SOC, led by Virginia Calegare, and the unwavering leadership of mentors like Sanja Petrovic, Giuliana De Bellis and security champions like Carla Tulloch, Belinda Noel and Nikki Saunders. Initiatives with meaningful impact, from workplace culture to public cyber awareness, stood side by side with technical breakthroughs and groundbreaking industry programs.
More than an awards night, the event reaffirmed a collective truth: security is stronger when every voice is heard and every barrier dismantled. As the industry grows, so too does the responsibility of members to keep opening doors and to support, mentor and lift the next wave of talent.
The legacy of these awards is still being written. But the messages delivered—messages of resilience, inclusion, courage and innovation—will reverberate long after the last award is handed out.
Congratulations again to all this year’s honourees, and to all whose daily efforts ensure that the future of security in Australia is not just safer but brighter, fairer and more inspiring for all.

CONGRATULATIONS TO OUR HONOUREES
MVP OF THE IT SECURITY INDUSTRY
Winner: Craig Ford
BEST VOLUNTEER
Winner: Sarah Barnbrook
BEST SECURITY STUDENT
Winner: Mila Fisher
Highly Commended: Belinda Zhou
THE ONE TO WATCH IN PROTECTIVE SECURITY
Winner: Felicity Le

Highly Commended: Kylee Dennis
BEST PROGRAM FOR YOUNG INDIVIDUALS IN SECURITY
Winner: La Trobe Cybersecurity Program
Highly Commended: The Summer of Cyber Program by AWSN
BEST SECURE CODER
Winner: Neelkamal Gaharwar
MOST INNOVATIVE EDUCATOR IN CYBERSECURITY
Winner: Girls Talk Cyber
Highly Commended: Adara Campbell
Special Recognition: Laura Christie
CHAMPION OF CHANGE
Winner: Jakub Zverina
Highly Commended: Rhys Shobbrook
UNSUNG HERO
Winner: Tracey Edwards
Highly Commended: Steph Burr
Highly Commended: Kim Chandler McDonald
More than an awards night, the event reaffirmed a collective truth: security is stronger when every voice is heard and every barrier dismantled.

BEST INDUSTRY INITIATIVE FOR DIVERSITY, INCLUSION, AND EQUALITY
Winner: AWSN Women in Security Mentoring Program
Highly Commended: Telstra’s Internship Program
BEST IN QUANTUM CYBER CHAMPION
Winner: Sushmita Ruj
AI IN CYBER CHAMPION
Winner: Ganna Pogrebna
BEST PLACE TO WORK IN SECURITY
Winner: Phronesis Security
Highly Commended: Solis Security
Highly Commended: Grant Thornton Australia
Special Recognition: ANZ Group Cyber Security team
PROTECTIVE SECURITY CHAMPION
Winner: Adrienne Maxted
CONVERGED SECURITY RESILIENCE CHAMPION
Winner: Maryam Shoraka
Highly Commended: Rhiana Cooke

BEST SECURITY MENTOR
Winner: Giuliana De Bellis
Highly Commended: Sanja Petrovic
CYBERSECURITY CHAMPION
Winner: Nikki Saunders
Highly Commended: Belinda Noel
Special Recognition: Carla Tulloch
NEURODIVERSITY CHAMPION
Winner: Sam McGillian
BEST USE OF AI IN CYBERSECURITY
Winner: Asou Aminnezhad
AUSTRALIA’S MOST OUTSTANDING IN IT SECURITY
Winner: Shannon Lorimer
Highly Commended: Virginia Calegare
Special Recognition: Farina Riaz
AUSTRALIA’S MOST OUTSTANDING IN PROTECTIVE SECURITY
Winner: Hayley van Loon
Highly Commended: Niam Cunningham






















NORA FUSIYAO
by Nora Fusiyao, Director, Security Architecture and Engagement at NSW Department of Customer Service
Cybersecurity is one of the fastest-evolving fields of our time. Once considered a niche technical discipline, it has become a global priority shaping economies, organisations and daily life. The story of cybersecurity’s rapid growth is also the story of the people making up the workforce behind it.

Historically dominated by men, the industry is now witnessing a steady shift as more women enter and shape the field. At the NSW Department of Customer Service (DCS) this evolution is not only visible but measurable: as of July 2025, women made up 37 percent of the overall cyber team and held 42 percent of manager and leadership roles. That progress is far ahead of the Australian industry average of 17 percent and the global benchmark of 22 percent.
The numbers tell part of the story, but what sets DCS apart is how its people describe an environment where careers are shaped by opportunity, fairness and inclusion.
EQUITY AT THE HEART OF CULTURE
“This was the first workplace where my transferable skills were truly recognised,” says Kelsey Workman, business information security officer for Building Commission NSW. “I was given opportunities based on potential, not just on what was on my CV. Leaders backed me, and that completely changed the trajectory of my career.”

Fairness and inclusivity are not abstract values— they are built into structures. Under the DCS Gender Equality Action Plan, the Department has
committed to embedding equity into every level of decision-making.
That commitment then drives measurable outcomes. The Workplace Gender Equality Agency (WGEA) reports that, nationally, the gender pay gap is still 21.8 percent, meaning women earn just 78 cents for every dollar earned by men. The NSW public sector, however, has narrowed this gap to 7.2 percent, reflecting state-wide commitments under the NSW Women’s Strategy (2023–2026). Within this context, the achievement of DCS is groundbreaking: in the Cyber and Information Security Office (CISO), the gender pay gap has been eliminated entirely. This milestone would be impressive in any field, but it is particularly powerful in cybersecurity, where women have historically been underrepresented and where pay gaps in technology remain entrenched.
started. “Everything I learnt was on the job, through mentors and early opportunities. It was daunting, but that’s what made it exciting.”

Yisha Zhang, principal security architect, came into cyber through short-term IT contracts. “Cybersecurity is about curiosity and continuous learning, not about gender. What I value is that it feels more merit-based than many traditional tech fields. Recognition comes from skills, knowledge and passion.” she says.



For Shammi Shah, manager of security architecture, this fairness has been central. “I can’t remember a time at DCS where being a woman gave me an edge or took an opportunity away. Development and progression here are unbiased. Diversity, fairness and psychological safety define the environment.”
For some, entering cyber was the result of deliberate planning and study. For others, it was an unexpected opportunity or an unconventional start.
Alena Alisyevich, senior security analyst, took a structured route, building her career on a foundation of degrees and certifications.
“Upskilling continuously is key,” she says. “Don’t worry if you don’t know everything at the start—none of us did.”

Cindy Ngo, business information security officer for the NSW Registry of Births, Deaths and Marriages, had no formal qualifications in cyber when she

Rachel Saunders, manager of security capabilities, began in a TAFE library supporting AV equipment. “I often joke I’d like to go back there because books don’t vandalise themselves or randomly jump off shelves,” she laughs. “But in truth, both roles required me to combine technical problem-solving with adaptability and customer service. I consider myself very lucky that I’ve found a role where I get to challenge myself in many ways.”
And Ishi Arora, manager of security policy and governance, brings a cross-cultural perspective. “Coming from a semi-urban town in India, there was no blueprint for women in cyber. I stumbled, learnt and kept at it.”

For many women entering cybersecurity the steep learning curve can trigger feelings of imposter syndrome. As one describes it: “You’ll likely start with a slight paranoia as you learn the myriad ways people and organisations may be at risk. But that soon transforms into empowerment as you realise the important role of cyber professionals in protecting, educating and defending.”
Aditi Upadhyay, business information security officer for NSW Spatial Services, offered this advice: “Cyber is broad, and the best way to learn is on the job.


Try different roles to understand the business as a whole—it makes you a stronger security leader.”
Her perspective reframes imposter syndrome: rather than a weakness, it can be a reminder that learning and adapting are the very essence of the field. This is backed up by Ishi Arora, “Don’t wait to feel ready. None of us ever feels 100 percent ready, and that’s okay. Dive in, ask questions, find mentors and build your voice.”
Across the CISO team one theme emerges strongly: the impact of women supporting each other. Kelsey Workman describes DCS as the first workplace where her transferable skills were truly recognised and says it was women leaders who recognised her potential and championed her. “DCS provides strong female role models across leadership who show what’s possible and inspire us to aim higher.”
"...as of July 2025, women made up 37 percent of the overall cyber team and held 42 percent of manager and leadership roles. That progress is far ahead of the Australian industry average of 17 percent and the global benchmark of 22 percent.
This article draws on insights from:


Her voice is echoed by Emma Neiberding, manager, cyber risk “I work under an inspirational female leader. I’ve also noticed women stepping into acting roles at manager and executive level, which shows me that opportunities to progress are genuinely supported and recognised. Across DCS the strong presence of female leaders has been motivating for me and gives me confidence to keep developing.”
Together, these reflections show how progress is not just about numbers—it is about women amplifying each other’s voices, creating space for growth and redefining what leadership looks like. In an industry still tackling gender imbalance, these networks of support are one of DCS’s greatest strengths.
The evolution of cybersecurity is inseparable from the evolution of the people who shape it. DCS is leading the way—not only in securing systems, but in shaping what an inclusive, forward-looking workplace can be. Behind this progress are many remarkable women who have broken stereotypes, found their voices and proven that leadership is not defined by background, but by courage, curiosity and persistence.
• Aditi Upadhyay, Business Information Security Officer, Spatial Services.
• Alena Alisyevich, Senior Security Analyst.
• Cindy Ngo, Business Information Security Officer, NSW Registry of Births, Deaths and Marriages.
• Emma Neiberding, Manager, Cyber Risk.
• Ishi Arora, Manager, Security Policy and Governance.
• Kari Beckley, Executive Officer.
• Kelsey Workman, Business Information Security Officer, Building Commission NSW.
• Kristy Randall, Security Project Manager.
• Rachel Saunders, Manager, Security Capabilities.
• Shammi Shah, Manager, Security Architecture.
• Yisha Zhang, Principal Security Architect.

























Proudly Sponsored by



Neelkamal Gaharwar
Security Architect from IBM
Tatyana Stojnic
Cloud Architect
Neelkamal Gaharwar
Security Architect from IBM
Gurmeen Kaur
Software Engineer from Telstra
Anita Regi
Cyber Security Intern for Cyber Audit Team

Henriette Elise Onarheim
Angelica Juturu
April Reyes
Brooke Rakowitz
Antra Saxena
Medha Mishra
Heena Sahare

Gurmeen Kaur
Natasha Liang
Viana Rumao
Ana Prusevic
Anita Regi
Neelkamal Gaharwar
Tatyana Stojnic

I’m truly grateful to you and your team for creating a platform like Source2Create that recognises women’s contributions in cybersecurity. This field is highly technical and demanding, and too often women don’t get the visibility or recognition they deserve for their skills and expertise. Awards like this really help boost confidence, motivation, and provide that much-needed visibility. You’re doing wonderful work, and this award has meant so much to me. I also wanted to thank CyberCX for sponsoring this. Thank you guys.

Neelkamal Gaharwar’s awarding of the Best Secure Coder trophy this year, proudly sponsored by CyberCX, represents more than technical prowess; it marks the arrival of a coder whose hands-on expertise has transformed the security of multiple mission-critical systems in real, measurable ways.
At Persistent Systems Ltd, Neelkamal became indispensable during a high-pressure review of a UK-based baby monitor platform. Facing a daunting initial scan of over 15,000 flagged vulnerabilities,
she applied both technical rigour and seasoned judgement: stripping away false positives to isolate over 15 critical and 500 high-severity flaws. With her findings adopted and remediated by development teams, the platform’s security underwent tangible improvement, directly protecting the privacy and safety of end users. Her determined approach showcased the confidence clients placed in her expertise and the impact her remediation recommendations could produce.
Her forensic attention to detail emerged again when she tackled the code of a System Management Appliance written in C for the same firm. Identifying and successfully demonstrating a buffer overflow vulnerability, Neelkamal navigated low-level software, where such risks can be catastrophic, with an assured understanding rarely seen among her peers.
Her success was not confined to one organisation. At Happiestminds Technologies, she joined midway through a Pascal driver project for Dell, quickly familiarising herself with both a new language and a fragmented documentation trail. Within a week, she delivered comprehensive security assessments, precisely articulated and well-timed, satisfying stringent client requirements on both depth and delivery.
At DevOn, her skills in the analysis of an ASP.NET application proved just as influential: she uncovered complex business logic flaws, demonstrating an ability to spot problems missed during ordinary testing, a capability often reserved for the very best secure coders in the industry.
Neelkamal’s recent work at IBM shines a light on her versatility. Working across Go, Python and .NET codebases for cloud services, she championed secure-by-design principles, merging technical depth with a holistic understanding of how software functions in modern enterprises.
What sets Neelkamal apart is her ability not just to identify threats, but to triage and communicate the essentials. Automated analysis routinely produces more noise than signal, yet her capacity to distinguish genuine vulnerabilities from false alarms remains exemplary. Where documentation stumbles, she compensates with analytical prowess and active collaboration, ensuring nothing is missed.
Beyond the code itself, Neelkamal’s passion rests in the problem-solving process, the intellectual thrill of dissecting languages, decoding business logic, and preventing threats from developing unseen. The notion that minor oversights can compromise
an entire system motivates her constant vigilance. She also takes pride in influencing organisational software culture: mentoring developers, establishing standards, and advocating for security-first mindsets.
As she transitions to Security Architect, Neelkamal will be tasked with guiding the integration of security into design itself, using proven threat modelling frameworks, codifying standards with reference to OWASP and NIST, automating SAST and DAST testing in CI/CD pipelines, and educating teams on the pitfalls highlighted by the OWASP Top 10 and CWE. Her role will move upstream, influencing not just remediation, but the architectural and operational DNA of the organisation’s software.

Neelkamal’s unique blend of technical mastery, communication, and passionate advocacy for secure coding renders her a truly deserving recipient of this award. Her work is shaping not only projects and products, but the very culture and practice of secure software development within the industry.




Proudly Sponsored by



Sushmita Ruj UNSW
Rita Gatt
National Lead Partner - Regulation, Cyber Security and Risk Client Agenda
Muria Roberts
Director from QTM-X
Sushmita Ruj
Faculty of Engineering Lead, IFCyber from UNSW
Yasaman Samadi
PhD Candidate from RMIT University

Rita Gatt
Tara Lie
Katherine Robins
Sushmita Ruj
Muria Roberts
Karina Savicka
Yasaman Samadi


At the cutting edge of cybersecurity, where quantum computing collides with the realities of digital defence, Associate Professor Sushmita Ruj stands out as one of Australia’s foremost innovators. Winner of the “Best in Quantum in Cybersecurity Excellence” at the 2025 Australian Women in Security Awards, Sushmita’s work is shaping tomorrow’s secure landscape, where new threats demand not just technical brilliance, but collaborative, global vision.

Sushmita leads research at UNSW’s Institute for Cybersecurity, focusing on post-quantum cryptography: the urgent race to design and deploy algorithms that can withstand quantum attacks. As quantum computers grow in power, the cryptographic foundations of today’s internet, used for everything from online banking to identity management, face obsolescence. Sushmita’s research bridges theory and practice, ensuring quantum-safe algorithms are scalable, interoperable, and ready for real-world implementation.
Her groundbreaking digital signature schemes and network protocols are not only robust in theory, they have already influenced standards, supply chain security projects, and data protection frameworks. Sushmita’s collaborative work with KU Leuven and other academic giants targets vulnerabilities in widely
used network protocols like DNSSEC, proposing solutions that secure infrastructure long before quantum computers threaten widespread disruption. Her leadership in the UNSW PQC Migration Initiative brings together government, industry, and academia to map the technical, regulatory, and compliance challenges of rolling out quantum-resistant systems for critical infrastructure.
Innovation is at the core of Sushmita’s career. Her published algorithms for secure digital signatures, verifiable random functions (integral to major blockchain platforms), and novel identity verification protocols have set new benchmarks. In recognition of her global impact, she’s been a driving force behind multi-million dollar Defence projects partnering with companies such as Guardware Australia, translating complex quantum research into practical tools for medical and national security applications.
Sushmita’s influence is multiplied by her dedication to collaboration and education. She works alongside global teams in North America, Asia, and Europe, regularly engaging with IBM, Microsoft, CISCO, and major academic centres. She mentors PhD, undergraduate, and M.Phil students in quantumsafe technology, and incorporates post-quantum


cryptography into the UNSW curriculum to ensure the next generation is ready for the quantum era. Her outreach extends to keynote addresses and workshops, most notably convening Australia’s PQC Migration Workshop, featuring industry and government heavyweights in the ongoing quest to future-proof the nation’s digital assets.
The reach of Sushmita’s advocacy and thought leadership is felt far beyond Australia’s borders. Her technical papers are highly cited and have become foundational in the global quantum-safe movement. Through public engagement, including accessible
articles and media appearances, she ensures that quantum security isn’t just left to elite researchers— she makes it tangible, urgent, and relevant to businesses, policymakers, and ordinary citizens alike.
Sushmita Ruj’s feature at the frontier of quantum cybersecurity shows that impactful research must anticipate tomorrow’s threats while building resilience in today’s systems. Whether developing novel cryptographic architecture, fostering strategic alliances, or empowering students and stakeholders, her vision is clear: a secured digital future, prepared, and not just reactive, for the quantum revolution.




Proudly Sponsored by



Phronesis Security



Solis Security
Phronesis Security
Grant Thornton Australia
ANZ Cyber Security Team
FTI Consulting
Avanade Australia
KPMG Australia
Mitchell Personnel Solutions
Trend Micro





Infoblox
Nova Systems
KPMG Australia
Cyber Security Directorate, Office of the Chief Information Officer, Government of South Australia
Avanade Australia
Grant Thornton Australia
Phronesis Security
Aurecon
Identifly
TAL
Trend Micro Pty Ltd
Mitchell Personnel Solutions
Phriendly Phishing
HUB24
Telstra
FTI Consulting
Secolve
Solis Security
Digital Resilience
Simple Training Academy

“We are incredibly honoured to have received this recognition. What it means to us is not only being acknowledged for our commitment to women in cybersecurity, but also for creating a culture where they feel supported, valued, and able to thrive long-term.
I’m deeply proud of the women in our team and the environment we’ve created, where they feel safe, empowered to be themselves, confident to challenge, and inspired to dream big. I look forward to seeing them continue to flourish as mentors, advocates, and leaders both within Phronesis and across the wider cybersecurity community.”

Phronesis Security’s 2025 win as Best Place to Work in Security is no accident—it’s the result of years spent deliberately designing a workplace where diversity and inclusion go well beyond slogans, manifesting in daily practice and lasting policy. From the top down and bottom up, the organisation is devoted to empowering women and non-binary professionals, and it shows in every corner of the company.
At Phronesis, women not only find a seat at the table, they occupy crucial roles at every level, from Chief Humanist and consulting leads to technical specialists in governance, risk and compliance, incident response, and infrastructure. Standout
team members Emily, Queen, Karen, and Dominique have led projects ranging from bespoke security frameworks for major clients to awareness training, business impact assessments, and threat detection across a wide array of organisations. Their visibility demonstrates to staff and aspiring talent alike that advancement and influence are not bound by gender or identity.
The company’s leadership actively cultivates and supports this balance, achieving a workforce that is 27% women, nearly double the industry average. It’s clear evidence of success for strategies such as paid internships targeting early-career women, a training allowance and study days for continuous

professional growth, and policies accommodating flexible and remote work, including a pioneering “work from anywhere” scheme that’s seen staff seamlessly contribute from overseas while managing study, family, or personal milestones.
Culture is key, at Phronesis Security, backed by systems designed for fairness and transparency. The company’s proactive parental, miscarriage, and domestic violence leave policies are designed to keep women and non-binary people progressing in their careers through life’s disruptions. The provision of free period care products in office bathrooms and the prioritisation of well-being through an Employee Assistance Program make daily work life welcoming and stress conscious.
Recruitment and advancement are equally inclusive: job ads are deliberately written to encourage applications from those who may not tick every box, hiring panels are gender-diverse, and there is regular consultation with female industry leaders to ensure outreach is truly equitable. Issues of bias, discrimination and harassment are met with a clear zero-tolerance policy, robust investigations, and a transparent complaints process, while quarterly anonymous surveys and a digital suggestion box create accountability and a genuine feedback loop.

Mentorship is woven throughout the company, with seasoned professionals like CEO Elliot providing personal, ongoing support for women entering the sector, even extending help to candidates who ultimately take jobs with competitors. Employees— many connected to industry networks like AWSN— mentor and support others both within and beyond the company, setting the example for industry-wide allyship and shared progress.
The result of these efforts is a workplace where 100% of employees regard Phronesis Security as a “great place to work,” according to independent ratings, with full marks in areas like gender justice, age equity and safety. Women and non-binary professionals thrive through flexibility, a sense of belonging and safety, visible leadership opportunities, and a commitment from male colleagues to call out and eliminate discrimination or unconscious bias. The atmosphere is summed up by a simple motto: everyone’s contribution is valued, and everyone’s needs matter.
Ultimately, what sets Phronesis Security apart is not simply generous benefits or strong policies, but the cultivation of a living, breathing culture of care, respect, and opportunity, where women and nonbinary professionals are deeply empowered to shape the future of Australian cybersecurity.

We were absolutely thrilled just to be part of the Women in Security Awards evening and to be surrounded by so many inspiring women in our industry. When our name was read out, we were over the moon. Being highly commended in the Best Place to Work in Security category means the world to us — it’s a powerful reminder that we’re on the right track and it motivates us to keep building an even better, more inclusive and empowering workplace at Solis.

At first glance, Solis Security’s nimble team may seem a world apart from sprawling tech giants. Yet, within this Australian firm’s sunlit offices and remote work hubs, the future of the security industry is quietly being crafted, one inclusive and empowering hire at a time.
With 41% of the 34-member workforce identifying as women, Solis Security is something of an outlier and a trailblazer: here, gender balance isn’t a goal, it’s reality. And it isn’t just about numbers. Women lead the charge as General Manager, Machine Learning Engineer (pushing the boundaries of AIdriven security), Technical Engagement Advisor, Data Mining Team Lead, and among three Project Leads responsible for major technical delivery streams. Five women Data Analysts move between the worlds
of code and stakeholder, while another ensures the business’s financial health—further proof that opportunity flourishes at every level.
What’s special about Solis isn’t just who’s in the room, it’s the experience every team member builds. Internships and work placements welcome women and non-binary people into the heart of cyber, with structured mentorship guiding them from first project to promotion. Flexibility isn’t a buzzword: it’s working around school pickups, caregiving, and life, with a genuine commitment to return-to-work parents. Across the globe, internal mentorship links the Australian and US teams, and ensures women in the Security Operations Center can see their own career possibilities reflected.


Recruitment and promotion are more than process, they’re protected. Bias training, transparent interviews, and equity policies mean advancement happens by merit, not by seniority or sameness.
Structured career development plans and paid time for certifications keep learning continuous, while the “Women in Security Network” and ACS membership solidify open industry doors at every turn.
Mental health, and the distinct needs of neurodiverse team members, is actively supported, with EAP, regular check-ins, and strategy sessions on how
everyone can do their best work, their way. Most striking, perhaps, is how every person—from data specialist to team lead—knows they’re trusted, respected, and backed to be their authentic self.
At Solis Security, proving that small business can set a national example, every day. Here, DEI isn’t an initiative, it’s rocket fuel powering a culture where talent rises, confidence grows, and the security industry moves closer, one career at a time, to genuine equity.

Stepping into the global nerve centre of ANZ Group Cyber Security, you’ll find more than the glow of monitors or the rhythm of technical problem-solving. Here, women and non-binary professionals are at the forefront, leading threat response, shaping strategy or driving the bank’s digital horizon from the boardroom to the operations floor. It’s a place where diverse voices don’t just contribute - they set the pace for defending Australia’s digital future.

It starts at the top, with Dr Maria Milosavljevic, a pioneering CISO who brings the value of representation to life from lived experience. Under her leadership, 42% of her executive team are women, a diversity reflected throughout the department, not just at the surface. In Australia, women now make up 41% of ANZ’s cyber security workforce, well above industry average of around 17% nationally. This isn’t a coincidence: it’s culture by design, where policy becomes practice.
The engine driving ANZ’s inclusive cyber culture is a blend of grassroots energy and executive commitment. CybHER Alliance, a vibrant network for women and non-binary staff, brings members together monthly for honest conversations, support, and professional growth – connecting members from Melbourne to India and the Philippines.
The Technology Executive Sponsorship Program, partners high-potential women with senior sponsors who strategise, champion their careers, and open new doors. Add to this a focus on future leaders through the Chief Executive Women network and external programs like Women Rising, giving women a launchpad to reach new heights.
As Dr Maria Milosavljevic says, “When we create space for every voice, we unlock new ways of thinking and solving problems. Inclusion isn’t just good for our people, it’s essential for our security.”
Internally, training is purposeful and woven into daily life. Everyone receives Lead@ANZ learning, making diversity and bias part of regular conversation, not a separate module. Promotions are rigorously reviewed, interview panels always include a woman,
As Dr Maria Milosavljevic says, “When we create space for every voice, we unlock new ways of thinking and solving problems. Inclusion isn’t just good for our people, it’s essential for our security.”


and shortlists must make space for diverse candidates. Salary and advancement are checked for parity, with responsive action taken to close gaps. Flexibility is built in - job share, remote working, career breaks and returns - so no one has to choose between life and leadership.
For younger generations, ANZ’s commitment shines through sponsorship of Go Girl, Go for IT -Australia’s largest school-aged STEM event for girls - and strategic engagement in initiatives like Cyber STEPs. At every stage, ANZ’s policies and working groups listen, survey, and respond, ensuring every voice, every experience, shapes a culture where people not only stay, but thrive.
“When people feel valued and included, they bring their best ideas and energy to the mission. That’s how we build a stronger, safer cyber communitytogether”, says Dr Maria Milosavljevic.
The results speak for themselves - engagement scores for women are rising, wellbeing metrics improving, and more women are advancing through
“When people feel valued and included, they bring their best ideas and energy to the mission. That’s how we build a stronger, safer cyber community - together”, says Dr Maria Milosavljevic.
promotion cycles each year. But it’s most keenly felt in the stories: women and non-binary staff who feel truly seen, supported, and empowered to defend one of Australia’s most important networks.
In an industry where “not enough” is the norm, ANZ Group Cyber Security has built a community where everyone belongs. In this team, inclusion isn’t a checkbox, it’s the secret to its security. And it may just be the key to Australia’s cyber resilience going forward.



Proudly Sponsored by



Ganna Pogrebna
Executive Director at the AI and Cyber Futures Institute
Ganna Pogrebna
Executive Director at the AI and Cyber Futures Institute
Harriet Farlow
CEO of Mileva Security Labs
Jennifer Valderrama
Co Founder /Director of Small Robot
Asou Aminnezhad
Industry Lead/Security Architect at Microsoft

Asou Aminnezhad
Laurie Tonks
Shannon Lorimer
Hazel Chen
Jax Fong
Evan Morrison

Jennifer Valderrama
Harriet Farlow
Ganna Pogrebna River Nygryn

Professor Ganna Pogrebna, Non-Resident Fellow at the Australian Strategic Policy Institute (ASPI) and Honourary Professor at the University of Sydney, is driving transformative change at the intersection of artificial intelligence and cybersecurity. Winner of the Australian Women in Security Award for AI in Cyber Champion, Ganna’s career is defined by visionary leadership, rigorous innovation, and an unwavering commitment to ethical and inclusive progress in digital security.

From pioneering AI-driven solutions for threat detection to mentoring the next generation of tech leaders, Ganna’s influence reaches across critical sectors. One signature achievement is the ONIfunded Cyber MLOps Digital Twin—a cutting-edge machine learning operations platform that enables real-time threat detection and incident forecasting while ensuring transparency, explainability, and ethical oversight. This AI tool is now central to secure systems design for Chief Information Security Officers, and its ability to simulate adversarial escalation has proven invaluable for defence, telecommunications, and crisis response teams globally.

Ganna’s embrace of behavioural data science has set her work apart. Her co-leadership of the inclusiVe InSider Threat tAxonomy (VISTA) introduced a ground-breaking, context-aware behavioural-AI framework—detecting a full spectrum of insider threats, including both intentional and accidental risks. By accounting for cognitive diversity and integrating neurodiverse profiles, VISTA makes cyber defences more accurate, ethical, and inclusive.
Her practical innovation extends to the Digital Personas Tool, transforming a behavioural modelling system into a practical training mechanism for understanding insider threats, AI biases, and ethical risks, widely adopted for cybersecurity education in government and academia.
to European bodies, or shaping the strategic direction of institutions from the Alan Turing Institute to the University of Sydney, her far-reaching collaborations span continents, domains, and disciplines.
Her approach is truly interdisciplinary: bridging behavioural science, computer engineering, risk





At Fujitsu Cyber, we enable resilience through security by delivering end-to-end solutions — strategic roadmaps, virtual CISO services, advanced threat intelligence, and rapid incident response. Leveraging ServiceNow’s platform, we empower organisations with integrated risk management and proactive SecOps for faster, smarter threat detection and response.
We’re proud to support the 2025 Australian Women in Security Awards, celebrating the incredible talent and leadership shaping a stronger, more secure future for us all.



Giuliana De Bellis
GPN/ATLASIAN


Sanja Petrovic HUB24
Juliana Bachtold
Security Director Avanade
Natasha Passley
Senior Managing Director FTI Consulting
Giuliana De Bellis
GPN Security Industry Rep / Security Testing Engineer from Girls Programming Network / Atlassian
Sanja Petrovic
General Manager, Cyber Security and Governance from HUB24
Pattigrace Lupari
Group Head of Marketing from Spirit Technologies
Dr Ana Forsyth
Director from KPMG Australia

Paula Sillars
Roma Singh
Peter Gigengack
Paula Sillars
Leila Assadi
Karandeep Singh
Dan Goldberg
Peter Gigengack
Adri Leite
Juliana Bachtold
Danielle Di Rosa
Gyle Dela Cruz
Rannee Li
Maleehah Lohani
Maeesha Lohani
Natasha Passley

Sakshi Kishore
Lesley Honeyman
Laurie Tonks
Giuliana De Bellis
Gyle dela Cruz
Sanja Petrovic
Sujatha Santhosh
Matt Goor
Farhana Dawood
Dr Ana Forsyth
Ankita Saxena
Remy Coll
Jasmin Krapf
Paula Sillars
Pattigrace Lupari
Saleshni Sharma

“I’m incredibly honoured to have received the Best Security Mentor Award at the 2025 Australian Women in Security Awards. I’m eternally grateful to the mentors I’ve had throughout my career so far, who have inspired me and helped me pay it forward. GPN is where I first discovered security as a student, and it’s been so rewarding volunteering as a tutor each term and giving girls the space to find their confidence in tech and amplify their impact. Receiving this award is a great reminder that this work doesn’t go unnoticed and is deeply appreciated by the security industry. Thank you!”

Giuliana De Bellis is redefining what it means to be a mentor in cybersecurity, seamlessly blending technical excellence with profound human connection. By day, Giuliana works as a penetration tester at Atlassian, serving as a crucial line of defence for one of the world’s leading technology companies. She scours code, uncovers vulnerabilities, and guides teams to remediate issues before products reach customers, ensuring security is everyone’s business. Her approach is deeply collaborative, integrating security into every stage of development and fostering a culture where developers feel supported, rather than scrutinised.
Yet it’s after hours that Giuliana’s influence arguably grows even more transformative. As the Security Industry Representative for the Girls’ Programming
Network (GPN), Giuliana plays a pivotal role in inspiring high-school girls to see themselves in technology. Her commitment to mentorship is visible through engaging lectures, hands-on workshops, and 1:1 guidance, demystifying the pathways into coding and security. She invites keen students to Atlassian for practical work experience, opens doors to industry contacts, and helps them discover the diverse roles tech can offer,well beyond outdated stereotypes.
Her impact stretches through university, where she’s a well-respected guest lecturer at UNSW, teaching secure software practices and common security pitfalls to future engineers. As a former leader of the UNSW Security Society, Giuliana ran large-scale peer mentoring, women-in-tech panels, and outreach


programs that have directly helped over 1,000 students. At Atlassian, she extends her guidance to junior staff through the Trust Mentorship Program, helping early-career professionals find their stride in a complex and competitive field.
What sets Giuliana apart as a mentor is her empathetic style and approachability. She understands the barriers, imposter syndrome, underconfidence, and the lack of visible role models, that often deter women and gender-diverse people from entering cybersecurity. By candidly sharing her own journey, including struggles and setbacks, she creates relatable role models for students who might otherwise feel excluded. Her mentorship does not end with a workshop or a course; she stays in touch with many mentees as they transition into university, internships, and even their first industry roles.
Success stories abound. Several of Giuliana’s high school mentees are now pursuing computer science, with one focusing on cybersecurity, others
gaining industry placements, and some returning as mentors themselves. At the university level, she has guided countless students towards internships, graduate jobs, and leadership opportunities, often being cited as the catalyst for their career confidence and ambition.
Giuliana’s inspiration springs from her own experience, having attended an all-girls high school where coding wasn’t the norm, she saw firsthand the difference support and visible champions could make. From launching coding clubs, inviting industry speakers, and building grassroots communities, to mentoring at scale as an industry professional, she continues to shape the next generation of security talent.
As Australia’s Best Security Mentor, Giuliana De Bellis proves that technical mastery and compassion are not only compatible, they are the foundation of an inclusive, resilient, and high-achieving security industry.

Sanja Petrovic, General Manager of Cyber Security and Governance at HUB24 Group – including HUB24, Class and my prosperity, is responsible for safeguarding one of Australia’s leading investment platforms. If you ask anyone on her team, her true legacy extends beyond technical solutions. It’s found in the people she’s mentored, empowered, and helped to transform throughout her career.
Sanja’s journey began in a university lecture theatre within the traditionally male-dominated technology industry. That experience inspired her ongoing commitment to creating environments where everyone feels welcome and valued. As a leader at HUB24, she has promoted a culture in which diversity flourishes organically. This is a result of Sanja’s ability to recognise potential in people from all backgrounds, ages, languages, and life experiences.
She is known as someone who talks honestly about the invisible barriers women and non-binary people often face. Beyond one-on-one guidance, she’s engineered multi-layered mentorship within her team, enlisting her senior staff to train and champion the next cohort. This progression can be described as a cascade, where knowledge leads to confidence, which in turn creates further opportunities.


Her mentorship is both intentional and deeply personal. For those starting out in entry-level roles with a clear ambition to grow, she recognises that drive and offers opportunities to progress into more complex areas. Graduates are guided towards becoming confident and independent professionals, while individuals seeking a more technical path find in her a supportive advocate who helps them establish themselves in specialised teams. Every achievement begins with someone’s potential, her trust, and the freedom to experiment, make mistakes, and return stronger each time.
Sanja’s influence isn’t confined by her formal title.
Ask her team what sets Sanja apart, and the answer is simple: she recognises people for their potential and what they can achieve, not what’s just on their resume. She offers genuine workplace flexibility, shapes hiring pipelines from diverse pools, and celebrates every victory.
Her motivation extends beyond witnessing career advancement; she is driven by the understanding that supporting others helps shape the dynamic landscape of cybersecurity in Australia, with every individual achievement making a difference. For Sanja, effective mentorship is truly transformative, equipping individuals with the confidence and guidance needed to thrive and develop within the field.
Sanja Petrovic is creating a resilient team defined by confidence, diversity, and spirit as its core strength.
Proudly Sponsored by



Sarah Barnbrook Away From Keyboard
Paula Sillars
Security Operations Manager from Cyber Audit Team
Renee Noble
CEO from Girls’ Programming Network
Sarah Barnbrook Founder from Away from Keyboard Inc.
Jeanine French
Security Change and Adoption Lead from Bupa

Hande Arici
Kat Loaiza del Pozo
Azrar (Ez) Ismail
Jeannette Ngau
Roma Singh
Dibya Sinha
Renee Noble
Jeanine French

Bat-ami Naim
Pranali
Mandewalkar
Emily Holyoake
Paula Sillars
Amina Aggarwal
Sarah Barnbrook
Kelly Howell

"Winning the Best Volunteer Award is deeply humbling because it represents the heart of why I do this work: to hold a light in the dark for those who feel lost, and to be a voice for those still finding their own. Volunteering isn’t just something we do in our spare time; it’s how we create safer, kinder communities.”

Sarah Barnbrook has been announced as the winner of the Best Volunteer Award at the 2025 Australian Women in Security Awards, recognised for her extraordinary volunteer contributions to cybersecurity, online safety, and advocacy for underrepresented communities across Australia and beyond. Her work has continually bridged grassroots education with global policy advocacy, earning her a reputation as both a community leader and an international voice in digital safety and ethical technology.
At the heart of Sarah’s achievements is her role as the Founder and President of Away From Keyboard Inc. (AFK), a not-for-profit organisation dedicated to digital wellbeing, online safety, and ethical technology use. Through AFK, Sarah has led workshops and campaigns that have reached thousands of people across Australia, with a particular focus on carers, educators, young people, neurodiverse individuals, and women—groups that often face disproportionate risks online. Her ability to connect
complex cybersecurity and ethical challenges with lived experiences has made AFK a vital educational resource, driving both awareness and resilience in communities vulnerable to online harms.
A true systems-thinker, Sarah also founded the Unsafe by Design Network, a global initiative that challenges technology developers, governments, and policymakers to adopt stronger safety-bydesign principles. This work came to international recognition when she presented the Unsafe by Design workshop at the United Nations Commission on the Status of Women (CSW), where she addressed how emerging technologies often intensify risks for women and girls, particularly in online and digital contexts. Beyond that, Sarah has advocated directly to UN bodies such as WIPO and the ILO, pressing for the adoption of cyber safety frameworks and protections that align with human rights principles. These efforts signal the breadth of her influence, spanning from grassroots classrooms to international conference halls.
Her dedication to advancing women’s leadership in science and technology is also evident in her voluntary service as Chief Revenue Officer for Women 4 STEM, where she plays a key role in supporting women to enter and thrive in STEM fields while embedding discussions of cybersecurity and safety into these career pathways. She extends this same passion through her involvement with influential organisations such as Soroptimist International South East Asia Pacific, the National Council of Women Victoria and Australia, Women with Disabilities Victoria, Gender Equity Victoria, the International Alliance of Women, and the UNAA Status of Women Committee, to name just a few. These roles reflect her holistic approach to advocacy—working at the intersections of technology, gender, and human rights to influence both policy and practical change.
Sarah’s volunteer leadership has also focused on raising public awareness of online harms and campaigning for stronger accountability. She has consistently spoken out about the dangers of graphic online content and the need for regulation that balances innovation with protection, especially for women, children, and vulnerable users. Her advocacy for ethical AI development and responsible governance of emerging technologies reflects her commitment to ensuring that future systems are designed with inclusivity and safety in mind. By promoting cybersecurity as not only a technical necessity but also a human rights imperative, Sarah has helped reshape the way policymakers, industries, and communities think about digital security.
Recognition of her work extends beyond Australia. In London, she has been honoured with the Volunteer of the Year Award and the Youth Impact Award at the Women Changing the World Awards, presented by Sarah Ferguson, the Duchess of York. These accolades, alongside her achievements at home, highlight the truly international scope of her influence and the difference her voluntary advocacy has made across multiple sectors.
Looking ahead, Sarah is focused on expanding her efforts to ensure safer digital environments for


future generations. She is currently authoring a book that weaves her lived experience as a survivor of technology-facilitated gender-based violence (TFGBV) with practical tools and policy guidance for navigating the risks of technology in everyday life. To deepen her impact further, she is pursuing advanced studies in cybersecurity to marry technical expertise with her established leadership in advocacy and community education. Alongside academic pursuits, she continues to grow AFK’s ambassador and education programs nationally, while building the Unsafe by Design Network into a powerful international coalition dedicated to safer technology design and development.
Sarah’s vision is bold but clear: a future where technology advances without leaving safety and ethics behind. Her tireless voluntary contributions have already influenced global and national policy, informed thousands of individuals about how to engage safely online, and pushed organisations to adopt more responsible practices. Winning the Best Volunteer Award is not only a recognition of her past achievements but also a celebration of her ongoing commitment to shaping cybersecurity as both a technical and societal safeguard. Through her dedication, passion, and lived experience, Sarah Barnbrook reminds us all that volunteering is not just a contribution—it is a force that can drive systemic change across communities, industries, and international borders.

You’ll be at the forefront of cyber security and part of a diverse team at ASD.
An exceptional career awaits at ASD.gov.au/careers


Proudly Sponsored by
Winner


La Trobe Cybersecurity Program LA TROBE



The Summer of Cyber Program AWSN HighlyCommended
ySafe by Qoria
La Trobe Cybersecurity Program
Kids SecuriDay
The Summer of Cyber Program by AWSN
Girls Programming Network Junior by Tech Inclusion
CyberFit Nation Program by Palo Alto Networks

See Yourself in Cyber Program
SheLeadsTech Program
Kids SecuriDay
WorkPath Australia
The Summer of Cyber Program
Girls Programming Network Junior
CyberFit Nation Program
La Trobe Cybersecurity Team
Early Talent Cybersecurity Internship Program by FTI Consulting
SA Power Networks
Cyber Kickstart Pathways Program
ySafe by Qoria
ANZ Group Cyber Security Industry Based Learning Program


La Trobe University’s Cybersecurity Program has earned the title of Best Program for Young Individuals in Security, proudly sponsored by the Australian Signals Directorate. . Since its inception in 2016, the program has woven together outreach, learning, mentoring, and professional development to build a diverse and dynamic pipeline of cyber professionals, especially among women and non-binary students, at all stages of their education and careers.
SHAPING THE PIPELINE
The program’s vision is clear: create meaningful access points for students from high school through to postgraduate study, focusing on confidencebuilding and hands-on experience. More than 100,000 high schoolers have engaged with La Trobe’s outreach programmes, cyber career days, hackathons, and interactive challenges, sparking interest and ambition in cybersecurity, often in communities where such exposure is rare. Students
find a place, and a pathway, into the sector through flexible micro-credentials, which have attracted over 6,000 learners, enabling study alongside work or family commitments.
FOSTERING LEADERSHIP AND BELONGING
La Trobe’s strategy is not just about numbers; it’s about culture. The program has built strong peer mentoring systems and communities, including Australia’s first university WiCyS Student Chapter. Led by a team of women from diverse backgrounds, this chapter offers leadership, peer support, and a visible network, developing skills and confidence in an environment where underrepresentation and isolation can be persistent challenges. Personalised support flows through career readiness workshops and industry mentoring, ensuring every participant gets the guidance needed to transition from education to employment.
Associate Professor Leanne Ngo anchors the program’s inclusive culture. Her commitment to mentoring and supporting early-career women and diverse students—whether through informal campus meetings or coaching sessions for remote learners— means students and staff alike find a champion who opens doors and builds confidence from the ground up.
The results are striking. More than 600 women and non-binary individuals have benefitted directly from the program’s tailored initiatives: securing internships, completing industry work placements, and being paired with mentors across the cyber landscape. Collaboration with industry is key, more than 215 work-based placements and 100 unique matches with cyber mentors ensure practical experience and networking. Industry partners codesign content and provide opportunities, making sure students are work-ready for a rapidly changing digital economy.
Participant success stories have made national headlines and set new standards. Student leaders have received major scholarships, awards, and grants from organisations like AISA, ISACA, AWSN, and the Australian Computer Society. Graduates and current students alike have stepped into visible leadership, academic excellence, and professional achievement.
By directly connecting industry needs with student learning and development, La Trobe’s Cybersecurity Program is breaking down long-standing barriers and setting its sights firmly on the future. Each layer, from high school outreach and flexible entry points to peer mentoring and professional placements, is designed to cultivate not just technical capability, but resilience, leadership, and personal growth.
With Australia’s cybersecurity workforce still struggling to achieve gender balance, La Trobe’s program is a blueprint for industry-wide change, empowering individuals, lifting communities, and building a safer, more dynamic digital future.



AWSN was deeply honoured to receive this award. It’s a wonderful recognition of the impact women are making in shaping the future of security and reflects what is possible when we invest in inclusive pathways and build strong support systems that enable women to thrive in this industry. We wish to thank the Victorian Government for partnering with us on this initiative and to all the amazing women and partners who have helped this initiative come to life! We are committed to find ways to expand this initiative nationally, opening doors for more women to pursue meaningful careers across Australia, strengthening Australia’s small businesses and empowering academic institutions to lead the next generation of security leaders.





“The mentorship and feedback helped me grow in confidence…and truly see how cyber supports business,”
This was the Summer of Cyber: a bold pilot launched by the Australian Women in Security Network (AWSN) and the Victorian Government to break the oldest codes of all, those barring young, diverse talent from transformative cybersecurity roles.
For 10-12 weeks, 44 women and gender-diverse students (and career changers), hailing from city towers, country towns, and regional heartlands, were dropped into the real world. Their mission: to help 22 small businesses discover, map, and defend against the invisible threats stalking the digital landscape. Instead of endless theory, they delivered, crafting risk assessments, building incident response plans, rewriting policies, and training staff on how to spot a scam before it became a disaster.
But they never walked alone. Each duo was matched with a dedicated mentor and tertiary supervisor. Many of them were female, who didn’t just teach, but believed in them. “The mentorship and feedback helped me grow in confidence…and truly see how cyber supports business,” said one participant, echoing dozens of others.
Why did this matter? Because for every empowered intern or career-returner, there had once been a gaping void:
• Too few jobs in the country.
• Too many unpaid, exclusive internships or programs.
• Not enough role models, networks, or guidance— especially for those coming back after caregiving or starting anew.
• Cultural and confidence barriers that saw women and non-binary talent slipping out of, not into, cyber.
Summer of Cyber turned the cycle on its head: paid placements, real work, live mentorship, and most importantly, a community that had their back. “I learned to apply technical, consulting, and communication skills in the wild,” another student said. “Now, I believe I can do this for real.”
And those businesses? They were the winners too: 100% saw their cyber readiness leap, with fitness scores doubling the industry average. Over 70 bespoke security documents and playbooks created, legacy artefacts for a safer digital economy.

But the biggest win was intangible: confidence. Every participant left not just with technical skills, but with the knowledge that they belonged. More than 100% said their ability, confidence, and networks to get a cyber job had grown, —and so had the sector’s capacity to finally be inclusive.
As industry partners cheered and the closing showcase ended, one fact was clear: this Victoriaborn program didn’t just fill vacancies. It changed lives, inspired possibility, and redefined who gets to shape the future of cybersecurity. The Summer of Cyber proved that, when you hand the keys to those long kept waiting outside, they drive innovation—and bring everyone safely along for the ride.
AWSN and Victoria’s Summer of Cyber isn’t just an award-worthy initiative. It’s a new blueprint for building real skills, real confidence, and real diversity—one summer, and one empowered student, at a time.
“I learned to apply technical, consulting, and communication skills in the wild,” another student said. “Now, I believe I can do this for real.”




With
People
We
Proudly Sponsored by



AWSN Women in Security Mentoring Program AWSN
Girls’ Programming Network by Tech Inclusion
ISACA SheLeadsTech Melbourne
AWSN Women in Security Mentoring Program in partnership with ASD & OK RDY
Telstra Internship Program



Telstra Internship Program TELSTRA HighlyCommended

Women in Systems Engineering Program, collaborated on by Chloe Pui and REA Group
WorkPath Australia by Vertical Scope Group (VSG)
AWSN Women in Security Mentoring Program, in partnership with Australian Signals Directorate & OK RDY
University of Technology
Sydney Cyber Resilience Program, supported by the Kyndryl Foundation
Tangible Uplift Program (TUP)
Girls Programming Network by Tech Inclusion
ySafe by Qoria
ISACA Foundation Melbourne SheLeadsTech
Women in Cybersecurity Summit by Infoblox, Australian Information Security Association (AISA) & Hemisphere East Telstra Internship Program


The AWSN Women in Security Mentoring Program is much more than a matching service: it is a dynamic, technology-driven network fostering genuine human connections, holistic career development, and industry-wide cultural shift. Its creators recognised that advancing women in Australian cybersecurity required new thinking—so they harnessed partnerships, purpose-built digital infrastructure, and tailored support to meet the real-world needs of mentees and mentors alike.
At its core, the initiative directly addresses foundational barriers in security—loneliness, lack of confidence, limited access, and the scarcity of role models—especially for women and other underrepresented groups. By using an AI-driven app, AWSN makes mentoring accessible, relevant,
and scalable. This innovation bypasses the administrative bottlenecks of traditional programs, enabling immediate connection, resource sharing, and support, wherever participants are located across Australia.
The statistics speak volumes, yet the human impact is even greater. With 1,200 engaged members, over 3,700 mentoring sessions and more than 4,500 new connections, AWSN has created a thriving community that supports more than just career goals. Mentees find themselves flourishing— reporting improved self-belief, expanded professional networks, real growth in both technical and soft skills, and even landing new roles and promotions thanks to their participation.

Beyond one-to-one mentoring, the program regularly delivers workshops, learning events, and curated content to nurture community engagement and foster ongoing development. Annual certificates, newsletters, recognition awards, and inspirational messaging reinforce a sense of belonging and celebration. These features motivate participants to stay involved and to encourage others to join, driving ripple effects throughout the sector.
A standout feature is the program’s partnership with ASD, which goes well beyond financial backing. With ASD’s support, inspiring leadership stories—such as those of trailblazers like Abigail Bradshaw—are shared widely, bringing national visibility to female role models and showcasing varied pathways to success in security. This storytelling dimension helps break stereotypes, encouraging diverse women to see themselves as future leaders, not just entrylevel contributors.

Success stories continue to surface: mentees who were once hesitant now confidently lead projects, secure promotions, or even return as mentors themselves, perpetuating a cycle of support and empowerment. Mentors describe the process as transformative—not only for their mentees but for their own professional growth and satisfaction.
Importantly, the AWSN initiative is recognised not just by its community but also by external bodies, routinely earning national and global awards for innovation and diversity impact. Its reputation encourages other organisations and industries to adopt similar approaches, heightening its influence and ensuring that momentum for equality and inclusion continues well into the future.
Ultimately, the AWSN Women in Security Mentoring Program stands as a model for how strategic collaboration, smart technology, and authentic care can reshape an industry. With each connection made and each barrier broken, the program is crafting a security sector that is more welcoming, innovative, and resilient than ever before.

Once upon a time, cybersecurity at Telstra, like much of the tech world, was a field of familiar faces: brilliant, passionate, but overwhelmingly similar. In 2021, as Australia’s leading telco looked to the future, its Global CISO, Narelle Devine, realised something needed to change. Only 22% of the cyber team were women, and the Security Operations Centre, the nerve centre of Telstra’s cyber defence, experienced higher turnover than other teams and the opportunity to improve diversity was top of mind.
What followed wasn’t just a new program, but a bold leap into uncharted territory. Narelle and her team decided: “Let’s not just fill seats, let’s transform the industry.” With this, the Telstra Cyber Security Internship was born: a 12-month adventure with a game-changing promise, no cyber experience required, just courage, curiosity, and a willingness to reinvent yourself.
“vulnerability management”, it was innovation, growth, leadership, and customer focus. It was about tomorrow's security, learned today.

The atmosphere across Telstra began to shift. New voices brought new ideas, and as the interns blossomed, so did the wider team. One rose to lead a key Security Operations Centre shift. Another pivoted into risk then protective security. Success stories began to multiply, stories that started in the program but now stretch across the industry as alumni carry that spark into other corners of the cyber world.

The program was designed for ten women, each stepping out of careers derailed by the pandemic or old dreams grown dusty. They were brought in not to blend in, but to belong. Telstra hired the interns as a cohort, wrapped them in peer support and mentorship, and set them loose in the high-stakes world of cyber ops, equipped with technical training tailor-made for real threats and a “Future Ready” toolkit brimming with soft skills.
Success was defined as “these women stay in the industry”. The women forged friendships and resilience together, learning, stumbling, and levelling up side by side. Handpicked mentors and Slack channels with AWSN became lifelines, and the curriculum wasn’t just “incident response” or
This wasn’t ever designed to be just a win for Telstra, but for all of Australia. The internship is a declaration: great cyber talent can flourish anywhere, when they are backed by belief, structure, and sincere inclusion. What began with a small group of women now inspires requests for advice from businesses nationwide.
Telstra’s investment proved something crucial: it isn’t enough to hope for diversity, you must build pathways for it, nurture it, and applaud each barrier that tumbles. The cohort’s laughter and tenacity echo in a security workforce forever changed, with new faces, new mindsets, and stronger networks than ever before.
For Telstra, a new day in cyber dawned with an invitation: come as you are. The rest, together, they’d learn, and lead.



Mila Fisher ORRO
Isabella Burton
OSINT Specialist/ Junior Cyber Security Specialist from Cyburton
Carla Vieira
Cybersecurity Ambassador from The University of the Sunshine Coast
Dominique Piccolo
Cyber Security Consultant from Phronesis Security



Belinda Zhou Queensland University of Technology
Mila Fisher
Cybersecurity intern at Orro
Belinda Zhou Associate, Information Security Governance, Risk and Compliance from Queensland University of Technology
Georgia Forster
Cyber Security Advisor from Australian Taxation Office Paige

Alissa

Mila Fisher’s ascent in cybersecurity is marked by resilience, curiosity, and service, a journey that’s now been honoured with the Best Security Student award. As an Information Technology Intern at Orro Group and a Bachelor of IT student at the University of Technology Sydney (UTS), Mila stands out not only for technical competence but for her commitment to using cybersecurity as a force for good.


Her path was anything but linear. Leaving high school early, then returning via TAFE to complete her HSC, graduating on time, Mila’s journey began with a Law degree at UTS motivated by a desire to help others. But discovering her true calling in cybersecurity, she courageously changed degrees, overcame self-doubt, and tackled the unfamiliar world of IT. Her commitment paid off: a distinction average, selection for the Dean’s List, and the prestigious Orro Scholarship in Engineering and IT, which led to her transformative internship at Orro.
During her placement, Mila rapidly made an impact. She revised network documentation for clients, audited infrastructure across sites, orchestrated an automation project, and coordinated technical teams under tight deadlines. On the security front, she contributed to third-party assessments with the TPSA framework, used tools like UpGuard for vendor risk, and reviewed ISO 27001 and SOC 2 Type 2 reports. Within Orro, Mila’s membership in oGuards saw her actively improve security policies and raise awareness across the organisation.
Her achievements have come in the face of considerable challenges: financial pressure, self-reliance, and the emotional toll of switching disciplines in a male-dominated field. The imposter syndrome common among women in tech was a familiar adversary, but instead of withdrawing, she leaned in—becoming Vice President of the UTS Cyber Security Society, a student representative

on the Academic Board, and an advocate for underrepresented voices.
Mila’s leadership potential shines in roles where her influence extends beyond technical tasks. As Vice President, she is strategic about planning and inclusivity, building support for learning and diversity. Her advocacy was reflected in key policy roles— liaising with university leadership, championing representation, and speaking at events focused on women in STEM. Consistently on the Dean’s List, Mila models dedication, peer encouragement, and a values-driven approach to the profession.
Beyond her official responsibilities, Mila’s impact grows through community engagement—organising student conferences, participating in industry events


like BSides Canberra, and contributing to professional networks such as ISACA. Her proactive approach is driven by a vision of cybersecurity where mentorship, inclusion, and ethics count as much as technical skill.
This sense of purpose defines Mila’s future plans and her leadership aspirations. She is committed to mentoring others, breaking down barriers for newcomers, and championing a culture where empathy and governance are integral to cybersecurity. For her, security is ultimately about protecting people, aligning policy, process, and technology so that risk is reduced and resilience built from every direction. In all her work, Mila strives to show that perseverance, compassion, and advocacy are not just complementary to technical excellence, they are inseparable from it.

If you visit the Information Security Team at Queensland University of Technology (QUT), you’ll likely find Belinda Zhou in the thick of collaborating on compliance, risk assessments, or helping colleagues prepare for an audit. As an Associate in Information Security Governance, Risk, and Compliance (GRC) at QUT, and a final-year Bachelor of Information Technology student majoring in Computer Science,. Belinda is not only working at the intersection of technology and policy, she’s actively shaping the industry’s future.


Belinda’s path began just two years ago. As a firstyear student in 2023, she dove headfirst into the deep end, attending every tech event and cyber meet-up she could find, building the network and confidence needed to break into security. Her curiosity soon attracted opportunity; she applied for a casual position in QUT’s Information Security team and was selected for her exceptional analytical skills and warm, professional manner, traits that quickly earned her trust within the GRC team.
But Belinda’s journey hasn’t been without obstacles. She’s faced the twin challenges of being a woman and a minority entering a field where representation is scarce. She’s confronted gender biases, and the lack of visible role models sometimes made the prospect of success feel more distant. But she persisted, drawing resilience and resolve from a community of mentors, often women who’d forged their own paths through similar barriers. Their support, paired with her tenacity, turned setbacks into stepping stones.
Balancing academic distinction (as a QUT Faculty of Science Dean’s Scholar), professional growth, and leadership was no easy feat. Yet Belinda thrived. She joined QUT Women in Tech, first as Secretary and now as President, transforming it into a thriving hub for aspiring female and non-binary technologists. She helped guide strategic events, created mentorship initiatives, and made space for discussion about cybersecurity careers, so others would have fewer barriers to overcome.

Her accomplishments offer tangible evidence of future leadership. Belinda interned at EY on the Digital Risk team, contributing to projects for major government clients and strengthening her expertise. She co-founded the QUT AI and Machine Learning Society, bridging critical domains and sparking campus-wide engagement. As an ACS Young Tech Ambassador, she regularly speaks at schools, inspiring the next generation before they even step on campus. And she continues mentoring others, offering wisdom and encouragement to students just starting out.
The broader security community quickly took notice. Belinda is a regular at industry events, from major summits to grassroots networking sessions. She’s spoken publicly on cybersecurity careers and the challenges of breaking into the sector, always with her characteristic clarity and warmth. For International Girls in ICT Day, she shared her journey


to inspire secondary school students, showing that excellence in security is open to everyone willing to reach for it.
So what keeps Belinda passionate? She is excited by the blend of governance, risk, compliance, and emerging threats, especially with the rise of AI. She sees cyber not as a set of boxes to tick, but the backbone of ethical innovation. Guided by the belief that security enables progress, she’s committed to making a tangible difference and championing inclusion for all.
For Belinda, the support of women who went before her, and the joy of making a difference for those who will come next, is what gives her strength. As she prepares for new qualifications and adds new achievements to her resume, there’s little doubt that her future will be marked by continued leadership, advocacy for diversity, and lasting impact.





Shannon Lorimer KPMG





Virginia Calegare RIGHTSEC

Farina Riaz CSIRO
Farina Riaz
Researcher Scientist from CSIRO
Daniela Fernandez
Division Director, Technology and Cyber
Security Risk from Macquarie Group
Maryam Shoraka
Head of OT Cyber Security Operations from Sydney Trains
Shannon Lorimer
Chief Information Security Officer –Australia, Fiji, PNG from KPMG
Reshma Devi
Data & AI Risk, and Information Management from Transurban
Jasmin Krapf
Head of Security Culture and Trust from Bupa
Virginia Calegare
CEO/Founding Director from RightSec
Jessica Jones
Head of Cyber Security from Grant Thornton
Australia

Smitha Anilkumar
Laura-Rose Carbone
Jess Dodson
Natasha Passley
Shannon Lorimer
Virginia Calegare
Kylie Watson
Laura Hartley-Quinn
Farina Riaz
Deeksha
Kelly Henney
Linda-Clare Chilvers
Jeevitha
Vijayakumar
Amila Elcic
Sarah McAvoy
Priya Gnanasekaran
Anneliese McDowell
Hardeep Sandhu
Becky Wan
Katherine Downing
Jasmin Krapf
Daniela Fernandez
Gabe Marzano
Nikki Peever
Reshma Devi
Grace Zhang
Jessica Jones
Maryam Shoraka
Patricia Ortiz
Shelley Godden

In the ever-evolving world of IT security, few names shine as brightly as Shannon Lorimer. As the only female CISO across KPMG’s 119 global member firms, Shannon has not only ascended to the top of her profession but has fundamentally changed what leadership looks like in cybersecurity. Her journey is defined by strategic vision, relentless innovation, and a passion for elevating others while never compromising on the integrity or mission of her work.

At KPMG, Shannon has been at the heart of a sweeping security transformation, leading a multiyear programme that radically reduced cyber risk and set new standards for operational excellence. She built out advanced capabilities in threat intelligence and insider risk, developing not just robust technical controls but also an industryleading approach to data loss prevention and cyber investigations. Her leadership did not just protect information and reputation; it raised KPMG’s status as a trusted and forward-thinking organisation, ready to respond to the challenges of a data-rich, risksensitive landscape.
Innovation is embedded in Shannon’s approach. She has spearheaded secure enablement for new technologies, working closely with business and technical units to safely leverage groundbreaking capabilities like agentic AI in Copilot Studio and analytics in Microsoft Fabric. By implementing agile methodologies, remote browser isolation, and secure proof-of-concept environments, she has given her teams the freedom to experiment and grow without making sacrifices in security or compliance. Her work directly influenced Microsoft’s own cloud security initiatives, a rare testament to her credibility and impact at the bleeding edge of tech.
Shannon’s leadership style is truly collaborative, she brings diverse voices to the table, mentors women and those from non-cyber backgrounds, and creates cross-functional alliances that embed security in the DNA of every project. Her development and operationalisation of the KPMG Global Information Risk Management Framework have become a benchmark, enabling firms to measure, manage, and mature risk with clarity and unity across disparate geographies. Her efforts have fostered


not just technical innovation but a lasting shift in cybersecurity culture, where inclusion and trust drive performance.
Her rise has not been without obstacles. Shannon has had to weather entrenched gender bias and prove herself in a traditionally male-dominated sector, but instead of seeing this as a barrier, she has turned it into her mission. She is both champion and role model for the next generation, ensuring that her climb clears a path for more diverse, high-achieving, and fulfilled teams. Shannon understands the power of representation, and her passion is as much about mentoring others as it is about technical excellence or programme delivery.
Recognition has followed in kind. Her partnership with Microsoft led to global improvements in cloud monitoring and defence. Her risk frameworks and security models have become standards not only for KPMG but for the industry at large. Her reputation is cemented by peers and leaders who cite her clarity, authenticity, and capacity to deliver results at scale, whether operational, strategic, or cultural.
Shannon Lorimer’s story is a blueprint for what IT security excellence looks like in the modern era: technical mastery married to empathy, strategy fused with action, and talent grown not in isolation, but alongside and with others. Her legacy is found in the systems she secures, the people she mentors, and the industry she inspires to be safer, more inclusive, and endlessly innovative.

The story of Virginia Calegare doesn’t begin in Australia, not by a long stretch. Picture her in Brazil: a navy uniform, the weight of national critical infrastructure on her mind, and the quiet resolve of someone who knows her calm might be the only one in the room. As an Cyber and intelligence officer, she helped steer a nuclear submarine project, bringing rigor and focus to an environment where there was little margin for error.
When Virginia made a daring leap, leaving behind her homeland and starting over in a country where everything was new, she didn’t arrive with connections, but she did arrive with a vision. Australia was on the brink of a cyber reckoning, its critical infrastructure exposed to the unknown, ready for someone to reimagine what protection looked like.

Through grit and humility, Virginia built her own company, RightSec, Australia’s first and only femalefounded Security Operations Centre. It wasn’t enough for her to offer standard incident response; she embedded herself in each client’s mission, using the experience honed in navy crisis rooms to cut through noise and guide teams through ransomware, insider threats, and even attacks from hostile nations.
She did it differently: the RightSec SOC, under her hand, is known just as much for cultural fluency, tailored intelligence, and fresh thinking as for technical clout. Virginia is right there in a crisis, making the call, leading the forensics, absorbing pressure for organisations who feel the world closing in. But what truly sets her apart is her insistence that the table be widened. Almost half her SOC team are women, a radical achievement in an
industry still fighting to reach parity. She’s unflinching in her belief that diversity isn’t just good ethics, but essential resilience. She mentors, she speaks, she challenges other founders and clients: “How many voices do you invite? Are you building a team or just a skills matrix?”

Virginia’s journey isn’t just one of triumph, it’s survival and adaptation. Facing cancer surgeries, leading through recovery, she continued steering clients, mentoring staff, and evolving her company’s capabilities, never dropping the standards she brought from the navy. Peers and clients nominate her, year after year, not just for the incidents she’s solved, but for the new culture she’s growing. As a finalist and recipient of major awards, her story reverberates from Australian cyber conferences to government advisories, where her trademark style clear, concise, unfailingly human, stands out in a field too often dominated by jargon and bravado.
Virginia Calegare is more than a security leader; she’s proof you can rewrite the industry playbook: rigor layered with empathy, intelligence fused with openness, and resilience that endures every migration, every crisis, every battle, personal or professional. And as Australia’s cyber threat landscape changes, it’s leaders like her who’ll keep watch—always ready, always inclusive, always redefining what it means to defend.
The room where Farina Riaz does her best thinking is rarely quiet. It’s filled with the sounds of possibility: quantum equations scrawled on tablets, lab partners debating over anomaly patterns, gentle interruptions from her children, and, often, the deep, steady focus of innovation at the edge of what’s possible in AI and security.
Farina’s journey wasn’t mapped out by mentors before her; she charted her own course, often as the only woman, and always as one of the boldest voices in uncharted territory. As Australia’s pioneering Quantum AI researcher, she didn’t just accept the rules of cybersecurity; she rewrote them. Developing a breakthrough single-qubit quantum encoding architecture, she made it possible for tiny IoT devices to protect themselves with tools previously only imagined for supercomputers, future-proofing entire smart cities and critical systems against threats that traditional AI can’t even spot.

And Farina’s ideas don’t just live in papers. They animate real tools: speech emotion recognition models to defend against deepfakes, time-series anomaly detectors for live video and sensor data streams, and CSIRO’s first industry quantum AI application, monitoring greenhouses to protect Australia’s food security in a changing climate. Every innovation comes with fewer assumptions, lighter computational loads, and fresh hope for vulnerable or resource-limited sites and users.
But her greatest impact comes from what she shares. Step into any panel, from IBM workshops to CSIRO expert groups, to Quantum Women’s leadership circles, and Farina’s there, demystifying quantum threats, calling for “secure by design” principles, and mentoring the next cohort of women and non-binary quantum scientists. She’s not just a researcher, but a judge for the Women in AI Australia Awards, a speaker shaping national dialogue, and


an advocate for connecting “what’s possible” with “what matters.”
All the while, she balances the pressures of family, culture, and academia with small acts of self-care and the fierce drive to break new ground, honoured as a Mental Health Champion, Woman in Technology, and a leader highlighted across Australia for both her technical excellence and her human warmth.
Farina’s story is still unfolding, but one thing is clear: she’s not content just to imagine the future, she’s building it. Her work, recognised by the “Best in Quantum in Cyber Champion” and now “Most Outstanding in IT Security” awards, isn’t just about

complexity for its own sake. It’s about ensuring that as technology leans forward, it does so safely, inclusively, and with a vision for impact that touches daily life from scientific labs to smart classrooms to farms growing tomorrow’s food.
For every rising star in quantum, every parent balancing work and dreams, every underrepresented student scanning for a role model, Farina is more than a leader. She’s proof that excellence comes not just from intellect, but from empathy, persistence, and a passion to make innovation a force for good. In the symphony of Australia’s IT security future, hers is a voice and vision that will echo for years to come.


Hayley van Loon CRIME STOPPERS INTERNATIONAL



Niamh Cunningham CANVA
Sara Trimboli Associate –Security, Aurecon
Hayley van Loon
Deputy CEO Crime
Stoppers International / Managing Partner Harod Asia Pacific
Niamh Cunnigham
Head of Protective Security, Canva
BridieThomas
Chief Operating Officer, Certis Security Australia
Jodee Pollard
Security Director, Macquarie’s Global Security team
Radha Ramadev Manager, Cyber Threat Management, TAL
Marina Azar
Toailoa
Business Risk and Compliance Manager / Director, IKEA & Mummy
Safety Security Project

Marina Azar Toailoa
Jodee Pollard
Maryam Shoraka
Virginia Calegare
Belinda E.
Brooke Rakowitz
Sara Trimboli
Nadiya Zachari
Saba Bagheri
Radha Ramadev
Christina Rose
Niamh Cunningham
Sarah Edwards
Bridie Thomas
Hayley van Loon


“I’m humbled to be recognised alongside leaders who are shaping the future of security. Protective security is, to me, the starting point for every other layer of safety and resilience. My focus is on lifting Australia’s protective security to meet tomorrow’s threats, and that only happens when we’re in the trenches together, working side by side, sharing knowledge, and building trust until the hardest problems are solved.”

Hayley van Loon has carved an extraordinary path across the worlds of intelligence, protective security, and global risk—a career marked by operational excellence, industry reform, and inclusive, people-first leadership. From the earliest days in the Australian Intelligence Community, where by 22 she was working in counter-terror operations, to her current dual position as CEO of Crime Stoppers International and Founder, Magnolia Intelligence, Hayley has been a catalyst for lasting change across Australia, the US, and beyond.
Her hands-on experience is legendary: whether spearheading red team penetration tests on critical US infrastructure or guiding investigations that have unearthed corruption, Hayley’s work is operational, not theoretical. One celebrated case involved covertly breaching the control room of a major US state’s energy grid, proving, in real time, where physical defences and human vigilance could be outwitted and where true resilience required new thinking and cultural change.
Hayley’s drive, though, reaches beyond frontline action. As CEO of Crime Stoppers International, she coordinates a 33-country network fighting transnational crimes, from child exploitation and financial fraud to wildlife trafficking and online harm. Her approach, bringing together law enforcement, policymakers, NGOs, and technology leaders, is credited with major advances, such as repurposing proprietary content detection technology from the adult industry to fight child abuse and extremist propaganda globally. In boardrooms and international coalitions, like the World Economic Forum’s Digital Safety coalition and the Global Coalition to Fight Financial Crime, she advocates for intelligence-led responses to the risks of a rapidly converging world.
Hayley hasn’t just transformed organisations, she’s reshaped the protective security industry itself. Her team at Magnolia Intelligence is over 50% female, proving that diversity and operational performance go hand in hand. By mentoring women and nonbinary professionals, and refusing to accept invisible barriers, she has redefined what leadership and success look like in protective and intelligence roles. Her inclusive, supportive approach is echoed at every level, with mentees and colleagues reporting not only greater opportunity, but a deeper sense of purpose and belonging within the sector.
Her impact is underscored by a string of prestigious awards: the 2024 David Irvine AO Memorial Award, recognition as Outstanding Female Security Professional at the OSPAs, and the 2025 Silver Global Impact Award from the Women Changing the World Awards in London, a testament to the global relevance of her work. As a finalist in the Global OSPAs and a key advisor to both CI-ISAC Australia and RMIT’s Centre for Cyber Security Research and Innovation, Hayley is setting strategic priorities for the entire field, and ensuring Australia meets emerging threats with both agility and humanity.
Yet it is Hayley’s personal qualities, her willingness to “roll up her sleeves,” her practical, direct approach, her generosity with knowledge and connections,


and her relentless focus on outcomes, that make her a true standout. She leads from the front in every sense, building bridges across sectors and continents, ensuring protective security stays relevant, modern, and ethically grounded. In a sector often marked by resistance to change, Hayley van Loon exemplifies the future: collaborative, innovative, inclusive, and dedicated to the safety of both people and critical systems.



Proudly



Jakub Zverina CYBER CX


Rhys Shobbrook SWINBURNE UNI
Wayne Rodrigues
Security Architecture
Practice Lead from Insignia Financial
Alex Hogue
Volunteer from Tech Inclusion
Rahul Anand
Acting CISO from Nova Systems
Stuart Jones
Director Technology
Risk and Cyber from KPMG Australia
Marty Simon
Director from Fujitsu
Jakub Zverina
Program Manager from Cyber CX
Phil Boadi
Information Security Manager from Hub24
Rhys Shobbrook
Associate Dean
Education from Swinburne University

Simon Mbizwo
Rahul Anand
Danny Flint
Dan Goldberg
Aniket Patil
Sajeeb Lohani
Marty Simon
Rhys Shobbrook
Jim Boughton
Jakub Zverina
Devruchir Jain

Bryan Nolen
Stuart Jones
Wayne Rodrigues
Adam Jorgensen
Peter Evans
Ashley Deuble
Alex Hogue
Errol Abrahams
Richard Addiscot
Barry Warnes

Jakub Zverina has quickly become one of Australia’s most influential champions for diversity, equity, and inclusion (DEI) within cybersecurity. Coming from a technical background, Jakub pivoted towards people two years ago as part of CyberCX’s where he was responsible for building the technical capabilities for CyberCX’s 1400 team members. More recently, he transitioned into a newly created role as Head of Cyber Workforce Growth and Partnerships. In this new role, his focus shifted externally around industry outreach, engagement, and partnership-building, using his platform to drive sector-wide change on gender equity and broader inclusion.

Jakub’s impact is felt at every level. Nationally, he serves on the Executive Cyber Council’s Cyber Workforce Working Group, collaborating with impactful organisations such as the Australian Women in Security Network (AWSN), Tech Council Australia, and Project F to provide frameworks that builds diversity and inclusion by design as a standard for workforce planning throughout the employee lifecycle. He’s a regular contributor to public policy discussions, shaping industry standards on pay transparency, flexible work, and inclusive hiring. Across working groups and advisory boards, Jakub brings a logical, balanced approach, considering
every angle and providing practical, scalable strategies that industry leaders increasingly adopt.
Recognising that advancing the representation of women means attracting and inspiring the future workforce early, Jakub also collaborates extensively with schools and academia. A key message he drives is the diversity of opportunities available in cyber, the different pathways available, and the business case of why the cyber security workforce needs to reflect the diversity of communities we are securing. He facilitates careers sessions, panel discussions, and engaging activities supported by women, enabling girls to visualise themselves in the industry.
Within CyberCX, Jakub advocated for adoption of the TEDI Standards, creating a platform for updating company policies and driving step change to create a more welcoming environment for women and diverse professionals. He has been tireless in access advocacy: arranging technical training for women in typically non-technical roles, cyber workshops, and encouraging women to speak up at industry events— helping those who feel shy gain confidence in a safe environment, and helping colleagues grow as public role models.
Jakub’s commitment doesn’t stop with the clock and he is very active in the community. He supports grant applications, coordinating events, and building engaging learning opportunities to uplift skills for women. He also acts as a mentor to numerous women, supporting their development, skill acquisition, and advancement. His sponsorship for awards and recognition means women he’s supported see their achievements elevated and celebrated.
Jakub doesn’t stop at gender equity, his vision encompasses first nations, neurodiverse individuals, veterans, and anyone who faces systemic barriers to participation. By leveraging external partnerships with NGOs, start-ups, and educational institutions, including face-to-face sessions with university students in non-cyber disciplines, Jakub breaks down stereotypes and broadens access to the sector.
The success indicators are profound. Both within CyberCX and across the sector he has impacted hundreds, producing lasting culture change and empowering women in technical and leadership roles. Acknowledging every initiative comes with opportunity cost, he drives initiatives that are scalable, repeatable and can amplify reach. Workshops, panels, and learning programs coordinated by Jakub have seen adoption and replication by others, guided by his example. He is frequently sought out for advice, even by competitors, such is his reputation for integrity, approachability, and deep subject matter expertise. Jakub’s contributions to key strategic documents such as the Australian Cyber Workforce Playbook, ensure diversity and inclusion are woven into sectorwide best practices.
Navigating obstacles is part of Jakub’s DNA. He has met resistance head-on, building the case for change through data, storytelling, and courageous conversations. Tackling limited resources, he has mobilised both internal volunteers and external partners to pool effort and maximise impact, even as industry budgets tighten. Against tokenism, he insists on strategic planning, measurable outcomes, and enduring structural change.


Jakub’s efforts have provided hundreds of women with career advancement, increased confidence, and access to training and mentoring. His influence is visible in changed lives as well as changed policies. Those he mentors credit him with their increased skills and professional visibility; colleagues feeling supported and celebrated, not marginalised. He is described as a sponsor, advocate, and genuine leader who uplifts others both privately and publicly.
Motivated by experiencing and witnessing the impacts of discrimination firsthand, Jakub brings personal resilience, empathy, and bravery to his work. He risks speaking up and takes satisfaction in driving transformation and watching individuals overcome their own challenges and grow. Through his advocacy, Australia’s cyber industry is becoming fairer, more inclusive, and ready to face the future with a truly diverse workforce at its core. Jakub Zverina’s “Champion of Change” award is a testament to the impact one dedicated individual can have across organisations, communities, and an industry.

Rhys was deeply honoured to be nominated for this award by a former student he first taught 18 years ago. “To look back and remember when she was one of a handful of females in a room with hundreds of males, and to see her now as a senior leader in cyber security, I cannot feel prouder! This award will be a cherished reminder of the important work we have to do and why I love my career”.

When you step onto the Swinburne University campus, it’s easy to spot the traces of change: labs bustling with diverse students, confident graduates stepping into cybersecurity roles, and a culture that recognises talent for what it truly is, passion, persistence, and potential. At the heart of these shifts stands Associate Dean Rhys Shobbrook, a quiet but unwavering force championing inclusive education and opportunity in technology.
Rhys’s journey isn’t marked by grand speeches or headline-making initiatives. Instead, his influence flows from a steady commitment to principle-based leadership. Throughout his years as a lecturer in
computer networking, and now as Associate Dean of Education in the School of Science, Computing and Emerging Technologies, Rhys has built pathways for those who rarely saw themselves reflected in STEM: women, neuro-diverse individuals, and students from migrant backgrounds.
His approach is deeply personal, reaching out to students who lack confidence but possess untapped capability, encouraging them to apply for tutor and lab support roles. These aren’t just opportunities to earn; they’re confidence-building, skill-sharpening steps on the road to real careers. Thanks to this mentorship, the Microsoft and Cisco CCNA convenor
roles, once exclusively male, are now 75% female, many staffed by former students Rhys personally encouraged and supported.
Small shifts have created seismic impacts. In 2023, Rhys and colleague Gavin Walsh piloted the IT Scouts program, hiring a majority of women to test lab technology and giving them authentic workplace experience. Every woman in that first cohort landed employment in cyber security, including paid placements and WISA award nominations.
“It’s amazing to help students who once doubted themselves become industry leaders and award finalists,” Rhys reflects.
Rhys’s reach extends to new programs like the Deloitte Cyber Academy, where 38% of participants are women, twice the industry average, and more than 90% stay the course. His vision for a Cyber Security Precinct at Swinburne aims to make belonging an everyday experience, with posters of diverse alumni as role models for every aspiring student.
Yet not every step has been easy. Administrative hurdles, budget cuts, and the slow-moving wheels of academia often threatened new initiatives. More challenging still was the quiet work of encouraging students, again and again, that they were worthy of opportunity, that their moment was now.
Women who benefited from Rhys’s advocacy tell stories of being offered their first tutoring job, landing cybersecurity roles, or entering postgraduate study against the odds. His support is direct: references, internships, and mentorship that doesn’t end at graduation. His philosophy is simple, students should be judged by what they can do, not who they are when they arrive.
Rhys’s legacy is living proof that persistent, valuesdriven action builds sustainable change. He has helped transform team cultures, inspired faculty hiring practices, and built a reputation as a trusted mentor for anyone striving to break through.


When asked what drives him, Rhys points to the joy of seeing “highly capable students who, like me when I was young, lacked the self-belief to put themselves forward” go on to succeed. That joy—quiet, powerful, and contagious—continues to ripple across Swinburne and beyond, reshaping the landscape of Australian cyber and STEM with every student who discovers they truly belong.
Rhys Shobbrook’s story is proof that you don’t need a megaphone to lead a movement—just vision, kindness, and the courage to nudge open doors for others. That is real, enduring change, in action.




Proudly Sponsored by


Felicity Le RISK & SECURITY MANAGMENT Winner



Kylee Dennis TWO-FACE INVESTIGATIONS
Kylee Dennis
Founder from Two-Faced Investigations
Felicity Le
Locations Officer from Risk & Security Management Pty Ltd
Rhiana Cooke
OT Cybersecurity Architect from Secolve
Demi Carlton
Protective Security Risk Specialist from Canva
Madeleine Dupont
Manager Security Operations and Response Team from nbn

Kiera Farrell
Kao Hansell
Bianca Stanghieri
Rhiana Cooke
Phoebe Wong
Elakiya Devi
Kishok Kumar
Az Ismail
Aditi Upadhyay
Nirja Mehta
Anjali Varghese
Ully Gamarra Martins
Madeleine Dupont
Felicity Le
Annabelle Harrison
Kylee Dennis
Demi Carlton

This award means a lot to me but not because its' prestige. Rather, because of what it represents - a rising star. A rising star can by anyone, but it is especially those who started from the bottom. Where we start our lives is not how we end it. Life is what we make it out to be, and so I hope future generations (particularly those from minorities) see this award and feel inspired to reach their dreams regardless of the hardships and prejudice that may surround them.

Felicity Le’s journey into Australia’s protective security sector is one marked by an unrelenting drive and a keen ability to turn every challenge into opportunity. Crowned the recipient of the 2025 “One to Watch in Protective Security” award, proudly sponsored by Sekuro. Felicity stands out not because she’s arrived, but because her capacity for impact is still unfolding.
Graduating with distinction in Law (Honours) and Justice from Queensland University of Technology, Felicity quickly moved beyond academic accolades, establishing herself as a dynamic force within the intelligence profession while still a student. At just 19, she joined a private investigations firm as an investigative officer and began her professional journey balancing full-time study, internships, and voluntary work. Her early commitment saw her contribute to the Australian Institute of Professional Intelligence Officers (AIPIO), where she not only assisted at events but also undertook a major independent research project through her internship. By 23, she became the youngest general duties Board Member in AIPIO’s history—signalling to industry observers that a new talent had arrived who
understood the profession, inside and out.
What sets Felicity apart, however, is not the speed of her rise, but the deliberate way she shapes opportunity for others. As Head of Social Media at AIPIO, she has transformed the organisation’s outward-facing platforms. She pores over academic research and sector news, promoting career opportunities, sharing insights and critical thinking, and turning online engagement into tangible results: registrations for events and membership numbers have surged since she took the helm. But beyond metrics, Felicity’s posts foster a sense of belonging and progress amongst emerging intelligence professionals. She ensures the industry’s digital voice is current, informed, and reaches young talent who might otherwise remain on the margins.
Her influence stretches well beyond digital boundaries. Felicity has become a mentor and guide for young interns, directly shaping AIPIO’s Emerging Intelligence Professionals Community of Practice. She is also a published researcher, with peer-reviewed articles in both The Journal of the
Australian Institute of Professional Intelligence Officers and The Australian Young Lawyer—an unusual accomplishment for someone at such an early stage in their career. More recently, she co-developed a leadership programme with Aya Leadership, ensuring new entrants to intelligence learn how to build resilience, communicate with impact, and link personal purpose with organisational excellence. Her perspective is consistently futurefocused, advocating that the next wave of leaders not only stay technically sharp but be anchored in meaningful contributions.
Felicity’s accolades—AIPIO Emerging Intelligence Professional of the Year (2021) and Australian Women in Security Awards Best Security Student (2024), are proof of her standing in the industry. But her achievements are more remarkable in light of the challenges she has surmounted. Growing up as the child of first-generation immigrant parents, Felicity faced economic hardship and the ripple effects of generational trauma. Juggling family obligations, academic responsibilities, and demanding professional roles, she has persevered through bouts of anxiety and depression without losing sight of her ambitions. It’s her drive to give back, both to family and to Australia, that animates her resilience; she channels private challenges into public service and leadership.
Looking forward, Felicity’s intentions are clear. She aims to serve in government intelligence, dedicating her skills, and her sense of responsibility, to protecting the nation’s security. She remains committed to opening doors for other aspiring intelligence professionals, breaking down barriers, and connecting young women and new entrants with mentors and pathways to success. She wants future generations to inherit an industry that’s both robust and welcoming, where hardship is met with opportunity and support.
Felicity Le’s award is not an endpoint, but a signal that her potential is only beginning to be realised. With each new role, initiative, and accomplishment,
she raises the standard for protective security and intelligence work in Australia, and carries with her the promise of a sector shaped by vision, inclusivity, and excellence.



It began as a calling, a drive to protect others, even when the path was uncertain or the risks were high. For over a decade, Kylee Dennis served on the frontlines of Australian law enforcement, walking a career path shaped by intelligence operations, highstakes undercover cases, and crisis negotiations where every word could make the difference between safety and loss. In the male-dominated world of policing, she built a reputation for unshakeable calm and sharp instinct, but also for a deep, unwavering empathy for victims so often left on the margins.

Yet, for Kylee, simply responding to risk was never enough. She saw the digital world morph: criminals were now just as likely to attack with keystrokes as with threats in person. The gaps in support for everyday Australians, those defrauded, coerced, or manipulated through screens—grew wider. Kylee knew that modern-day security demanded something more than policing could provide.
She stepped away from her badge to forge something new, something necessary. She founded Two Face Investigations, a private agency built on her experience, her courage, and her vision for a better way to keep people safe in an era of digital deception. The challenges were many: starting over as a woman entrepreneur in an industry slow to change; staring
down sceptics; bearing the real, emotional weight of supporting survivors of new forms of online abuse. Yet Kylee turned every stumbling block into a cornerstone for her mission.
It didn’t take long for her impact to be felt. In just two years, Kylee became a national go-to expert, not only guiding clients through the aftermath of scams, social media hijacks, and coercive control, but explaining, with remarkable clarity, how these new threats unfold. Her commentary rang out through ABC News and 7News, the Herald Sun and The Morning Show, on airwaves and in podcasts across the country. She translated technical threats not just into plain English, but into hope and practical advice for everyday people.
In 2025, Kylee was invited to stand on a global stage, co-facilitating a United Nations webinar with Away From Keyboard (AFK) Inc. She spotlighted the emerging dangers of artificial intelligence for girls and vulnerable people, making a passionate case for trauma-informed, client-centred protective security, a model built on the real challenges, and the real courage of the digital age.
Kylee’s influence runs far beyond expert advice or technical know-how. She is shifting the very culture


of protective security in Australia. Through every investigation, every interview, and every partnership, she champions a new approach, where recovery and aftercare matter as much as risk management, and where every story of harm is met not only with skill, but with compassion. With her agency, she offers survivors more than “protection”; she offers understanding, support, and the tools to reclaim their autonomy.
Her journey has not been without cost. It takes grit to step into the spotlight, speaking publicly about abuses that many would rather ignore. It takes even more resilience to hold space for survivors while fighting for systemic change, especially as a woman setting new standards in a sector slow to evolve. Yet every tough moment has only steeled Kylee’s
resolve. Her story is one of reinvention, courage, and vision. A reminder that the best protectors are those who see the person behind the incident and build practices that honour that truth.
To call Kylee Dennis “One to Watch” doesn’t just capture her trajectory, it recognises a rising leader with the power to remake the world of protective security for good, for everyone. And as her journey continues, Australia’s future will be safer, and kinder, in her hands.
“Being highly commended as One to Watch in the Women’s Security Awards was a moment of quiet pride. Standing among such formidable women fuels my drive to keep going, to speak louder, reach further, and protect those most at risk.”
“Being highly commended as One to Watch in the Women’s Security Awards was a moment of quiet pride. Standing among such formidable women fuels my driv e to keep going, to speak louder, reach further, and protect those most at risk.”
Proudly Sponsored by




Craig Ford
The MVP of the Security Industry Award at the Australian Women in Security Awards is a unique, open category, proudly honouring women, non-binary professionals, and male allies who go above and beyond in championing security, inclusion, and community. The award acknowledges those who quietly shape the future, act as selfless mentors, and drive real change, regardless of gender— ensuring security becomes everyone’s business.


The MVP of the Security Industry Award, presented annually by Source2Create as part of the Australian Women in Security Awards, exists to honour one exceptional leader whose quiet achievements and unwavering commitment have left an indelible mark on the industry. This year, that leader is Craig Ford, a professional whose influence resonates far beyond technical boundaries, inspiring the entire security sector.
Craig’s pathway to becoming MVP is testament to the breadth and depth of his contribution. Over more than two decades, Ford has traversed every shade of the cybersecurity spectrum, from blue, to red, to purple teams. He has not only engineered robust security frameworks for major organisations but also founded his own company, committed to raising standards and innovating solutions for safeguarding data, systems, and people across Australia. Yet Ford’s focus is never purely technical. He recognises that successful security is founded not only on tools and protocols, but on a culture of learning, inclusion, and shared responsibility.
What truly sets Ford apart is his drive to make cybersecurity open and accessible for all. His empathy and belief in equality guide his efforts to dismantle the barriers facing women, nonbinary individuals, and all those traditionally underrepresented in the security profession. These ideals extend well outside his own company and into the wider network of professionals, where Ford’s leadership as Director of the Australian Information Security Association (AISA) has been pivotal. He actively steers national conversations around diversity, balance, and creating pathways for new talent, making knowledge-sharing and mentorship cornerstones of industry success.
Ford’s impact is also evident in the classroom, in boardrooms, and on the stage. As a keynote speaker, best-selling author, and tireless educator, he reaches learners at every age and level, demystifying the digital threats of today and empowering school students, job-seekers, and retirees alike. His message is clear: security belongs to everyone, and everyone should be supported in their quest to understand and navigate our complex digital world safely.
The qualities celebrated by the MVP award are not just about technical prowess, but about humanity: being a mentor, a volunteer, an advocate. Ford’s generosity of spirit can be seen in the countless hours devoted to supporting industry initiatives, mentoring rising professionals, and making security practices truly accessible. His guidance reminds us all that the future of security depends on collaboration, empathy, and bold vision, just as much as on innovation and expertise.
The applause that greeted Craig Ford as he accepted the MVP of the Security Industry award was not only for his personal accomplishments, but for his tireless work in lifting others up. Ford personifies what it means to be a hero in security, not because he works alone, but because he consistently makes space for others, breaks down walls, and ensures opportunity is never out of reach.
As the curtain closes on this year’s gala, Ford's legacy stands as a benchmark for professionals across Australia and beyond. He reminds us daily that there are no small roles in cybersecurity, that every act of mentorship and advocacy matters, and that progress depends on unity, purpose, and heart. Congratulations once again to Craig Ford, the MVP of the Security Industry for 2025.






Proudly


Nikki Saunders Schneider Electric





Belinda Noel
Secolve

Carla Anita Tulloch
Domino’s Pizza Enterprises
Carla Anita Tulloch
Domino’s Pizza Enterprises
Jyoti Sharma
Monash University
Nikki Saunders
Schneider Electric
Sara Lelliott BUPA
Caity Randall
Sustainabil.IT
Belinda Noel Secolve
Keryn McMartin
IdentityXP

Amina Aggarwal
Roma Singh
Sara Lelliott
Jyoti Sharma
Karissa Breen
Juhi Mishra
Carla Anita Tulloch
Heidi Victoria Winter
Melina Ryan
Swapnali Kesarkar
Dibya Sinha
Celia Oakley
Alaina Lawson
Sakshi Kishore
Isabella Baker
Pooja Tyagi
Jocelyn Fenlon
Roshin Quental
Carrie Smyth
Elese Cox
Chloe Pang
Tian Liu
Anubha Sinha
Keryn McMartin
Emma Seaman
Priya Gnanasekaran
Lara Hemmaty
Leila Assadi
Linda Zeng
Leah Mooney
Nikki Saunders
Serena Earsman
Georgia Forster
Sheena Shrivastava
Belinda Noel
Sarah Drysdale
Claire Shoko
Sahiti Poosarla
Cindy Ngo
Laura Dominguez
Azrar (Ez) Ismail Manager
Anna Obruchkova
Sapna Kumari
Biljana Roksandic
Prapurna Uppuluri
Caity Randall
Isabella Parkman
Amina Aggarwal
Kersti Eesmaa
Heather Copland

Nikki Saunders, recently named Cybersecurity Champion at the 2025 Australian Women in Security Awards, has established herself as a transformative leader at the intersection of operational technology (OT) security, business innovation, and diversity advocacy. As the Regional Cybersecurity Solutions and Services Lead at Schneider Electric, Nikki has redefined what it means to champion security, not only building highly effective cybersecurity frameworks across the Asia-Pacific, but reshaping how the industry recognises and elevates underrepresented voices.

Behind the impressive title is a leader whose vision extends well beyond compliance and sales targets. Nikki is responsible for overseeing the delivery of high-impact cybersecurity projects, such as the world’s largest OT security program in rail, an initiative that now serves as a benchmark for safeguarding critical infrastructure. She was the architect and launch leader for Schneider Electric’s Managed Security Services business across APAC, constructing a new revenue engine, fostering
strategic alliances, and delivering an extraordinary three-year run of unprecedented growth: 727%, 275%, and 183% increases year-on-year.
But perhaps Nikki’s greatest legacy lies in her determination to make cybersecurity a more inclusive space. She is a sought-after mentor, championing women and non-binary individuals within her teams and far beyond, cultivating talent, supporting career growth, and always placing diversity at the centre of strategic planning. She founded enablement and development programs designed to give underrepresented groups the resources and confidence they need to step into leadership. Stories abound of junior employees, graduates, and peers who found their place in the industry thanks to her practical support, authentic encouragement, and visibility as a strong female leader within a maledominated domain.
Nikki’s advocacy does not stop at the workplace. She actively participates in—and helps shape—regional and national industry initiatives, from the ARN


Women in ICT Awards to working groups with the Property Council of Australia. These platforms have amplified her own voice as well as those of countless others, improving policy, growing the talent pipeline, and driving awareness of the social and business imperatives for embedding security at every level.
Her achievements have come through resilience. Nikki has navigated organisational complexity, cultural resistance, and the technical and operational challenges of scaling cybersecurity across diverse regional markets. She overcame dismissive attitudes, unconscious bias, and even overt scepticism about her age, gender, and suitability for leadership. Instead of being deterred, Nikki turned these moments into fuel—modeling transparency, embracing collaboration, and, above all, delivering outcomes that no one could ignore.
Fundamentally, Nikki Saunders’ leadership is defined by both business value and human impact. Her strategic foresight and technical expertise have directly raised the cyber posture of critical infrastructure—securing communities, enabling innovation, and challenging old ways of thinking. Simultaneously, her commitment to inclusion, mentorship, and speaking truth to power has opened doors, inspired hope, and paved the way for a new generation of cyber professionals ready to lead with integrity and impact. Surpassing titles and milestones, Nikki remains the authentic “voice of security”—bridging boardrooms and technical teams, policy circles and grassroots communities, to ensure the future of cybersecurity is both secure and inclusive.

Scene 1: A cafe table in Melbourne, three years ago. Belinda taps out a quick message, “Anyone want to talk OT security? Let’s compare notes.” Eight people show up. The conversation flows, tentative at first, then lively. At the table, she notices—a student, a plant manager, a recent career-changer. No one is more “expert” than the others. Belinda lets the room breathe, makes introductions, then steps back and listens. The first of many connections.
Scene 2: An event in Sydney, a year later. “Women in OT” is now five events strong. There’s a queue for coffee and a welcome table with Belinda’s friendly hand-written name tags. A CISO confides in a grad about early mistakes. A career-break returner asks about certifications. Belinda laughs, sharing her own blunders and doubts. At WIOT, no one is expected to perform, only to belong.

Scene 3: The back end of a Secolve project. Belinda sits with two mentees, one a newly arrived refugee, the other a young engineer on her first OT project. They work late, reviewing a security checklist line by line. Belinda cheerleads, asks hard questions, shares a hack she learned last month from a peer in the UK. At Secolve, learning is not passed down from a pedestal, it’s handed across the table.
Scene 4: Perth, a conference networking hour. Belinda stands aside, watching two WIOT alumni swap business cards and stories from their week on site. She ducks out to send a Slack message, lining up the next event speaker. She’s happy not to be
needed in every conversation; her legacy is in the network, not the spotlight.

Scene 5: Post-panel, nerves still buzzing. It took guts to speak honestly about imposter syndrome in front of 200, especially admitting that, yes, even founders freeze up sometimes. The Q&A goes overtime. Several women linger after, asking how to get started, how to stay, how to climb higher. Belinda jots down contacts for introductions, cracks a joke, and leaves with one new idea for the next WIOT session.
What keeps these scenes—and behind them, a movement together? It’s the invisible “and” at the core of Belinda’s work: Engineer and student. Refugee and leader. Mentor and mentee. Technical and human. Story and solution. Local and global. Success and self-doubt. Where others see only individual achievements, Belinda notices the ties between people, and quietly knots them until a community stands where none existed before. For OT security, that changes everything.
At WIOT, at Secolve, at affinity events and Slack channels and in late-night project reviews, Belinda draws the industry’s future forward, not by marching alone, but by putting her hand out and saying, “Come join us. There’s space here for you too.” In Belinda Noel’s world, resilience is a team effort, and nobody, ever, goes unconnected.
If you happened to stroll past the Domino’s head office a few years ago, you wouldn’t have flagged Carla Tulloch as a future cybersecurity champion. Back then, she was showing homes, chatting rent rolls, and rushing between real estate deals, cyber was barely a word in her world. But curiosity is a powerful thing. One day, a single “try-it-and-see” shadowing session with the Domino’s security team upended everything. She’d found her new calling.
Carla’s first days in cybersecurity felt like learning a new language in a storm. There were acronyms, threats, and technical puzzles she’d never imagined. But she didn’t flinch. Instead, she broke it down, lesson by lesson, asking questions, and inviting others along for the ride. Her journey soon became the open door she wished she’d found sooner.
Fast-forward, and Carla is the mastermind behind Domino’s global cyber awareness, her work quietly woven into the lives of 100,000 employees across 12 countries. She’s not just sending out policy emails. She’s sculpting digital rally stands, rolling out the brand’s very first customer scam awareness pages, and making security simple, relatable, and inclusive no matter your role—store manager, delivery driver, office team, or customer ordering a pizza in a language she’s made sure is available for you.
When cyber threats threatened the frontline, she launched Domino’s first-ever phishing simulation campaigns for store crews, meeting skepticism with games, lightbulb moments, and honest

conversations. She created regionally tailored training and hands-on fairs, transforming security from the “boring stuff” into something fun enough to talk about at the staff table.
But ask Carla what matters most, and she won’t rattle off metrics, despite a global drop in phishing click rates. She’ll tell you about the pride in someone saying, “I never thought I could understand this,” or about a young woman inspired to try cyber because Carla’s own story made it possible. She’s the mentor in the background, the voice on the help call, the champion for making cyber a language everyone can speak.
It’s her relentless pursuit to put security in everyone’s hands, across languages, cultures, and experience levels, that makes Carla Tulloch not just Domino’s cyber champion, but a hero whose greatest act is shining a light on the unexpected potential, in herself and everyone she reaches.
Because in every store, every office, every team chat, someone else is now wondering: If Carla can carve a new path, what could be possible for me?
That’s real resilience, and a story worth celebrating.




At Fujitsu Cyber, we enable resilience through security by delivering end-to-end solutions — strategic roadmaps, virtual CISO services, advanced threat intelligence, and rapid incident response. Leveraging ServiceNow’s platform, we empower organisations with integrated risk management and proactive SecOps for faster, smarter threat detection and response.
We’re proud to support the 2025 Australian Women in Security Awards, celebrating the incredible talent and leadership shaping a stronger, more secure future for us all.



Girls Talk Cyber


Laura Christie
Senior Security Culture and Trust Manager from Bupa
Girls Talk Cyber
by Emily Pendlebury and Julia Wulf-Rhodes
Tech Inclusion’s Girls’ Programming Network (GPN)
Adara Campbell
Cyber Experience and Culture Senior Analyst from TAL Australia
Mikaela Green
Teaching Fellow – Applied Technologies, University College; PhD Candidate – School of ICT, College of Science and Engineering at University of Tasmania
Nicola O’Brien
Cybersecurity Engagement and Awareness Manager from University Of Technology Sydney



Christie BUPA

GirlsTalkCyber
Podcast: Emily and Julia are CoFounders and Podcast Co-Hosts
Richa Sharma
Laura Christie
Nicola O'Brien
Mikaela Green
CyberFit Nation Holiday Workshops
Adara Campbell
Kathryn Sundstrom and Shona Henderson
HUB24 Cyber Security and Governance Team HUB24
Kelsy Zalfelds
ISACA Melbourne
Chapter - c/o
Bharat Bajaj
Catherine Schnell
Girls Programming Network
Belinda Noel
Donna Graham

"We were in complete disbelief when our names were called to the stage. From GTC starting as an idea between two friends to where it is today - it was truly such a surprise to take out the category for Most Innovative Educator and we are so grateful for the recognition. We hope the ripple effect of its acceptance will support us to continue sharing our Cyber Queen energy with more audiences and assist more people to "Redefine how they act online".

Girls Talk Cyber, founded by Emily Pendlebury and Julia Wulf-Rhodes, has redefined cybersecurity education in Australia with its vibrant, relatable, and highly accessible approach, earning recognition as the Most Innovative Educators in Cybersecurity.
Their journey began as two young professionals in the cybersecurity sector, acutely aware of both the complexity of cyber issues and the lack of engaging resources for everyday Australians. Girls Talk Cyber was born out of their desire to demystify the field
and break down the barriers that deter non-experts, particularly young women, from getting involved. Instead of lecture-style education, they opted for a podcast format filled with powerful analogies, reallife listener stories, and a conversational tone that feels more like the latest gossip than a technical deep dive.
Their innovation is evident in methods like the “Fraud Files” segment, where stories from listeners equip others with relevant, actionable lessons. By
continually employing analogies—likening cyber hygiene to “patching your parachute” or likening account hacking with a burglar entering through an unlocked door, Emily and Julia ensure cybersecurity concepts are immediate and memorable for all listeners. Their overtly feminine, high-energy language (“Cyber Queen energy”) and use of small, achievable micro-habits turn what could be overwhelming advice into realistic actions for building robust digital resilience.
Girls Talk Cyber’s measurable impact is demonstrable. In its first year, the podcast notched up over 2500 downloads, reaching 6,000 by mid-2025 and maintaining near-perfect ratings across Spotify and Apple Podcasts. Social media engagement flourished, and feedback from followers underscores its effectiveness: listeners report adopting password managers, setting up multi-factor authentication, and feeling confident discussing online risks for the first time. Their audience now spans Australia, New Zealand, the UK, and the US.
Their success is amplified by partnerships with industry leaders such as CyberCX and support from the Commonwealth, which enabled classroom workshops for high school students. These workshops, launching in Victoria, ACT, and NSW, bring Girls Talk Cyber’s signature accessible style off the airwaves and into the classroom—ensuring even the most digital-native students have a solid, practical foundation in cyber safety.
For industry professionals, Girls Talk Cyber has become a go-to resource to refresh basic digital security skills and a tool to help them educate friends and family. Its array of offerings, podcast, social media, live events, and upcoming YouTube content, caters to story-driven, visual, and aural learners alike, from technical specialists to the general public.
Emily and Julia’s vision is to keep pushing boundaries: expanding workshop campaigns, furthering collaborations, and keeping cybersecurity a topic for everyday conversations in schools, group chats, and at the dinner table. By normalising


cybersecurity and making it approachable, Girls Talk Cyber empowers a new generation to take charge of their digital safety and become proactive, rather than reactive, defenders online.

Cybersecurity education in the workplace meant dry slides, long policy documents, and yawning eyes. But at Bupa, something different is happening, and at the centre of it all is Laura Christie, a force for creativity who has transformed learning from a compliance checkbox into a company-wide celebration.

It all started with a question: “What if learning about cyber could feel as exciting as a festival?” With that, Laura unleashed CyberFest, a week-long series of events so lively and engaging, people across Bupa competed to take part. There was a buzz in the air, a sense that security was everyone’s business, and there was something in it for everyone.
The heart of this innovation is the “CyberX Talks.” Borrowing inspiration from TEDx, Laura curated fast-paced, story-driven sessions where experts, survivors, and industry insiders delivered rapid-fire learning that stuck with people long after the event. In just two days, ten diverse topics came alive: from real-world scams and AI-powered threats to digital
parenting and careers in security. Each session was open, inclusive, clear—and designed to spark not just awareness, but real action.
But Laura’s festival was more than just talks. She brought cybersecurity to life through playful competition in the “Cyber Games”, think “Phish Pong,” “Malware or Merlot,” and “Exposure Patch Toss”—activities that left participants laughing and learning in equal measure. And for those curious about their own career prospects, the Cyber Career Corner paired everyday employees with security professionals, demystifying the industry and opening new doors.
The impact was electric: over 2,000 employees registered (a 32% jump from the year before), feedback scores soared, and the Net Promoter Score hit an unheard-of 87. More importantly, the energy didn’t fade when CyberFest ended. Employees left empowered, eager, and ready to bring a security mindset into their day-to-day work.


Laura’s innovation works because it’s truly for everyone . She designs layered, accessible programs: deep-dive technical sessions for specialists, approachable learning for the general workforce, and even digital safety lessons for families. She reaches into Bupa’s aged care homes to ensure every generation—from young professionals to the elderly—has access to digital citizenship and safety.
Collaboration is her secret weapon. Laura’s Security Coach Program trains more than 100 volunteer coaches to spread good habits at every level. By joining forces with Bupa’s risk and business resilience teams, she embeds cybersecurity into the company’s DNA, not just as a technical issue, but as a vital pillar of everyday culture. And on the industry stage, she shares her playbook, encouraging other organisations to embrace fun, relevance, and empathy in security learning.
As Laura steps onto conference stages and mentors her peers, her influence only grows. She dreams of a future where cyber education is less about memorising threats and more about empowering humans—where serious play, behaviour science, and emotional intelligence are as valued as firewalls and patching.
Thanks to Laura Christie and her team, cybersecurity at Bupa is no longer just a topic for IT. It’s a culture, a conversation, and most of all, a collective celebration of how everyone, no matter their background, can help keep the digital world safe.
And that is how you make a security educator unforgettable.


Edwards NBN


HighlyCommended


Kim Chandler McDonald 3 STEPS DATA
HighlyCommended


Steph Burr MICROSOFT
Kim Chandler McDonald
CEO/Co-Founder from 3 Steps Data
Tracey Edwards General Manager GRC and Advisory Services from nbn
Steph Burr
SecTalks HBA organiser | Senior Security Researcher from Microsoft
Sheavy Kaur
Information Security Specialist from Air Force Association (Western Australian Division) Incorporated trading as RAAFA
Alex Penna COO from Girls Programming Network
Michelle Ribeiro Cyber Security Awareness & Organizational Engagement Lead from UNSW
Roma Singh GRC Specialist from Risk Management Consulting
Melanie Truscott
Executive Director Engagement & Communication from CyberCX
Liz
Kaur
Amy
Alex Penna
Kim
Tracey
Dominika ZerbeAnders Michelle Ribeiro
Hayley van Loon



“I am genuinely appreciative to receive this award. This recognition isn’t about me – it is a testament to the incredible individuals who have supported and inspired me throughout my career. I am immensely grateful for the opportunity to support and uplift others in our community, in-turn. Together, we are creating a more inclusive and resilient cybersecurity landscape. Thank you Australian Women in Security Awards / Source2Create, for your dedication and for believing in the power of collective effort to build a better future for everyone.”

With a career spanning more than three decades, Tracey Edwards has become one of the most influential, yet quietly selfless, heroes in Australian cybersecurity. As General Manager for Governance, Risk, Compliance, and Advisory Services at nbn, Tracey leads the organisation’s security posture, ensuring national infrastructure remains robust, compliant, and ready for any threat. But her impact is felt far beyond the boundaries of her formal responsibilities.
Tracey’s journey has taken her from small start-ups to leading banks, insurers, and national enterprises. She has long been a pioneer in the security arena, breaking through glass ceilings and paving paths for women and minorities in a field that once excluded them. Early in her career, she faced a landscape where women were expected to “take minutes” at leadership meetings; today, she is shaping policy at the highest levels.
Her heroic, unsung work includes mentoring countless women entering security, uplifting those from non-traditional backgrounds, and expanding access for neurodiverse individuals. At NAB, Tracey spearheaded the industry’s first neurodiversity employment programme, opening doors for candidates on the autism spectrum. This initiative now extends across multiple organisations, with cohorts thriving under her guidance. Tracey’s efforts are life-changing; she has given some their first real career—earning heartfelt thanks from families whose futures she has transformed.
Tracey is also a founding member of AWSN and a director on the AISA board. Through RMIT’s Cyber Advisory Board, she ensures students receive an education suited to a rapidly evolving industry, keeping Australia’s cyber talent pipeline strong. At nbn, her leadership over the graduate scheme has set new benchmarks, with hundreds of applicants vying for roles in a programme consistently rated among the nation’s top, serving as a launchpad for Australia’s next generation of security professionals.
But Tracey’s legacy endures through the people she’s empowered. She has mentored women from every walk of life, including those who never saw themselves as technologists, a truck driver, now an analyst, credits her career to Tracey’s guidance. Her mentorship relationships are long-term and genuine, built on integrity and a drive to see others succeed.
Challenges have never deterred Tracey. She’s faced bias, career barriers, and resistance, yet answers adversity with strength and authenticity. Being the first female voice in ex-military security teams, she broke down unspoken barriers and helped other women rise. Her story is one of resilience, empathy, and relentless advocacy.
She is also a passionate ambassador for Genius Armoury, designing modules to make cybersecurity accessible to anyone, no matter their age, background, or neurotype. Her advocacy doesn’t stop at women, it extends to anyone who wants to belong in security, championing diversity as the sector’s greatest asset.


Tracey Edwards remains driven by a belief that everyone deserves a chance to add their value in fields they care about. She is known for her ability to recognise and nurture unique strengths, especially among those once overlooked. “Security is tangible, and the difference we make is real,” Tracey says. “Seeing the impact of diverse thinking in this industry is a privilege, and I’m honoured to be part of it.”
Quietly, persistently, Tracey has shaped policy, elevated communities, and built a better industry, without fanfare. The Unsung Hero award is a wellearned tribute to a career, and a life, devoted to security excellence and genuine human impact.

Reflecting on the recognition, Kim says: “Being Highly Commended in the Unsung Hero category is deeply meaningful. So much of this work happens beh ind the scenes — encouraging others, building safer systems, and showing up even when it’s hard. To be recognised among such remarkable women is an honour I’ll carry with pride — not for the spotlight, but for what it shines a light on: the quiet power of community, care, and persistence.”

When Kim Chandler-Mcdonald first launched 3 Steps Data, few could imagine that a privacy-first, encrypted data platform tailored for the world’s smallest businesses could one day set a global standard. “Unachievable,” some said. Kim only heard: “challenge accepted.”
From her earliest days, Kim was never content to color inside someone else’s lines. With no technical pedigree and no old boys’ network to open doors, she co-founded 3 Steps Data on sheer will and the conviction that every Australian, every business, deserved digital trust. Where others might have followed trends, Kim built her own: researching, funding, and coding a secure ecosystem that didn’t simply sell safety but actually delivered it to the most vulnerable and overlooked.
As CEO, her work was visionary, but her leadership style was always grounded and personal. Kim blended her background in the arts, storytelling, empathy, connection—with radical technological innovation. For her, building a product was never enough. She wanted to build pathways, confidence, and communities.
It’s this philosophy that also underpins Kim’s role as Global VP of the Cybersecurity Advisors Network (CyAN). With the (In)Securities newsletter, Kim became the unlikely weaver at the center of an international web: amplifying new voices, celebrating unsung contributors, and spotlighting critical policy issues. Impressions soared, conversations deepened, and a dispersed community started to feel like a movement.


Her advocacy didn’t stop at digital borders. Kim’s energy and attention turned outward, supporting survivors of tech-facilitated abuse, raising six-figure sums for women’s refuges through her anthologies, and fusing cyber with purpose in every project she touched. Keynotes that leaf through stories. Products that blend power with usability. Mentorship without ego or expectation.
Instead of envy, she offers encouragement; instead of bravado, quiet persistence. She’s happiest shining a light on others, whether celebrating a young coder’s breakthrough or helping a peer untangle an ethical dilemma.
The road she travelled was never smooth: building a tech startup with self-funding and no safety net, bridging continents from the periphery, as an
Australian-based outsider, facing skeptics who could only see obstacles. But Kim’s creative defiance, her capacity to imagine, then actualise, systems the world had not yet considered, turned those obstacles into stepping stones.
Kim Chandler-McDonald isn’t just an unsung hero, she’s the force singing a different tune, whispering courage, and rewriting what positive change in cybersecurity can look like, every single day.
Ask Kim about her passion and she’ll tell you: cybersecurity is about people first, not systems. Her legacy is not just in the secure architectures she has built, but in the culture of dignity and inclusion that her work models for the next generation, a future in which safety, human rights, and technological empowerment are one and the same.
Let Us Join Your Team Now !!!
"Get skilled support to fill your team’s gaps at the same wage rate.
Source2Create provides a team of professionals across marketing, social media, admin, and content management, ready to enhance productivity without adding strain to your budget."


DO YOU CURRENTLY HAVE ANY OF THE FOLLOWING REMOTE OPEN POSITIONS?
Marketing support
Marketing strategy
Event coordinators/managers
Telemarketers
Linkedin/Instagram managers
Admin support
Canva ad creators
Wordpress content administrator
Admin and Data Entry
SCHEDULE A CALL TODAY OR EMAIL ABY
ABY@SOURCE2CREATE.COM.AU
Proudly Sponsored by



Sam McGillian Cyber CX
Sam McGillian Consultant, Governance, Risk & Compliance from Cyber CX
Tracey Edwards
General Manager, GRC and Advisory Services from nbn
Mina Zaki
Director Cyber in Deals Lead from KPMG Australia
Tas Ahmed Cyber Security Specialist

Mina Zaki
Tracey Edwards
Samantha McGillian
Tas Ahmed


In an industry that thrives on precision, logic, and problem-solving, Sam McGillian is proving that empathy and openness are equally essential. Recognised as the 2025 Neurodivergent Champion, Sam’s leadership and advocacy are helping reshape how the cybersecurity sector understands and supports neurodiversity.

When Sam joined CyberCX in 2023 through its Academy program, she brought more than a decade of experience in nursing and community service. What she may have lacked in tenure within cybersecurity, she quickly made up for in authenticity, insight, and courage. From day one, Sam chose to be open about her neurodivergent identity—a decision that, while deeply personal, has had a transformative effect on her colleagues and the wider organisation.
“I don’t really think of myself as a role model,” Sam has said. “But being open helps others feel less alone, and that’s what matters most.”
That openness has changed the conversation at CyberCX. By sharing her lived experience, Sam
has helped make neurodiversity a recognised and valued part of workplace culture. Her courage has encouraged others to self-identify, seek the support they need, and engage in honest discussions about communication, flexibility, and belonging.
As a mentor, Sam is known for her empathy and practicality. She supports neurodivergent colleagues who are learning how to navigate the workplace, as well as managers seeking to lead more inclusively. Her advice, rooted in real-world understanding, has earned her the trust of people across all levels of the company. “Sam is a fantastic presence in the team,” one of her leaders shared. “She helps everyone, including neurodiverse people, communicate more effectively with clients and with one another.”
Beyond mentorship, Sam’s impact can be measured in the systemic change she’s helped drive. In 2024, she became one of the founding members of the CyberCX Neurodiversity Employee Resource Group, part of the organisation’s “Be Yourself” diversity and inclusion pillar. Through this group, Sam has led internal initiatives including Neurodiversity
Celebration Week, and she’s personally encouraged many colleagues to join and share their stories. Her advocacy has helped shape more accessible work environments, from adaptable communication tools to sensory-friendly spaces.
Her influence also extends to the broader industry. In November 2024, Sam took to the stage at AISA CyberCon, presenting her talk “Neurodiversity in Cyber: Building Solutions for Success.” Drawing from her own journey from healthcare into cybersecurity, she explored how understanding human difference can drive stronger, more creative, and more inclusive teams. The presentation was widely praised for its honesty and impact, positioning Sam as a leading voice in the national conversation around neurodiversity in tech.
Balancing advocacy with her role in CyberCX’s Government, Risk and Compliance practice, Sam continues to lead by example. She coaches leaders on how to engage neurodiverse team members effectively and collaborates on strategies to ensure that every individual, regardless of cognitive profile, can thrive. Her efforts have helped spark a cultural shift at CyberCX, where discussions around neurodiversity are now normalised and supported at all levels.
What makes Sam’s work remarkable is not just its reach but its depth. She operates one conversation, one awareness session, one act of mentorship at a time—creating lasting, human-centred change. In an industry that often speaks the language of systems, Sam has built one rooted in connection.
Her recognition as the Neurodivergent Champion acknowledges more than her personal achievements; it celebrates the power of vulnerability, advocacy, and authenticity to drive real inclusion. In every sense, Sam McGillian is showing that a safer, smarter, and stronger cybersecurity industry begins with creating space for every kind of mind.


Proudly Sponsored by



Adrienne Maxted DELOITTE
FINALISTS NOMINEES
Hayley van Loon
Managing Partner Harod Asia Pacific
Adrienne Maxted
Cyber Partner from Deloitte
Angela Kamaru
Principal Cybersecurity Operations from BHP

Hayley van Loon
Adrienne Maxted
Monica Zhu
Tanya Jefferis
Jessamy Perkins
Luisa Amanda
Angela Kamaru


Adrienne Maxted’s impact as the 2025 Protective Security Champion springs from her unwavering dedication to lifting others as she leads, especially women and non-binary individuals within Australia’s protective security sector. As Deloitte’s Global Women in Cyber Sponsor and a senior Partner in the national Technology and Transformation practice team, Adrienne has built a reputation for fostering diversity, inclusion, and genuine human connection in an industry where those values have too often lagged behind technical innovation.
Her leadership style is founded on integrity and warmth. Adrienne has steered Deloitte's Executive Women in Technology Program, connecting women in cyber with influential mentors, industry networks, and supportive communities. Under her guidance, more than 300 women have benefited directly from mentorship and career support. Locally, she’s driven initiatives like Women in Cyber Connect and the Cyber Awards, which shine a spotlight on trailblazers, expanding role models for underrepresented groups.
Adrienne’s drive comes from lived experience. Raised far from urban tech hubs, she was one of few women in her computer science cohort, and three in her graduating class—giving her first-hand insight into the challenges faced by women entering technology careers. Inspired by a desire to build the network and support she once lacked, Adrienne fuels her passion for making space for others. Her efforts have paid off: her own Deloitte Cyber & Application Security team boasts 65% women, a stark contrast to industry averages.
She is a tireless champion for wellbeing and career progression. Adrienne’s partnership with Cybermindz prioritises mental health, tackling burnout and promoting resilience within the profession. She also supports early talent through the Cyber Academy, school-based hackathons, and Capture the Flag events, actively growing the industry’s future talent pool.

Adrienne’s advocacy is shaped by overcoming barriers—moving from rural Victoria to the city, navigating male-dominated academic and workplace environments, and balancing a demanding career with family life. Driven by a commitment to social justice and community, she ensures Deloitte’s global initiatives, such as the Cyber XChange program, guarantee equal participation and global collaboration for women.
Adrienne Maxted’s approach to leadership is guided by curiosity, empathy, and a belief that everyone’s story can inspire change. She fosters ‘can-do’ attitudes, broadens the talent pipeline, and creates new opportunities for women and non-binary individuals to thrive in protective security. Through generosity, mentorship, and visionary leadership, Adrienne is not just changing the culture of her team, she’s helping to shape the future of the entire industry.




Proudly Sponsored by


Maryam Shoraka
SYDNEY TRAINS

HighlyCommended


Rhiana Cooke SECOLVE
Rhiana Cooke
OT Cybersecurity Architect from Secolve
Maryam Shoraka
Head Of OT Cybersecurity Operations from Sydney Trains
Saba Bagheri
Cyber Threat Intelligence Manager from Bupa
Anna Poole
Partner, Tech Risk & Cyber from KPMG Australia
Claire Elevato
Senior Manager Security Governance, Security Group from nbn

Arati Chalise
Hayley van Loon
Rhiana Cooke
Maryam Shoraka
Zoe Thompson
Anna Poole
Alina Limbu
Saba Bagheri
Claire Elevato


With nearly two decades of experience in information technology and operational technology security, Maryam Shoraka has become a benchmark for converged security resilience, seamlessly integrating digital and physical protections across Australia’s most critical infrastructure. Her leadership at the Department of Communities and Justice saw her design and deliver a 24/7 Security Operations Centre (SOC) for IT security within a tight six-month timeframe. She rapidly upskilled the team to ensure around-the-clock monitoring and alerting were in place, achieving a sustainable 24/7 capability. This first-of-its-kind initiative not only strengthened the department’s cyber defence posture but also saved both budget and time over the long term by reducing reliance on external providers and building inhouse resilience.
Maryam’s success at local and state government agencies rested on breaking down traditional silos, fostering trust and collaborative workflows

between engineering, IT security, and physical protection teams. Maryam led the establishment of a highly capable cybersecurity team and a 24/7 Security Operations Centre (SOC) designed to meet the department’s immediate requirements while remaining adaptable to future challenges. Under her leadership, the SOC matured into a resilient capability that ensures real-time monitoring and rapid response to cyber incidents, positioning the Department of Communities and Justice with long-term strength and agility in its security posture.
At the NSW Department of Communities and Justice (DCJ), Maryam has further advanced convergence as Acting CISO and now Head of Cybersecurity Operations at Sydney Trains. She instituted a “security by design” framework, embedding cyber risk analysis directly into the development of both physical and digital systems. Under her leadership, converged threat responses became the norm, with incident playbooks that anticipate and mitigate


both digital and real-world threats to critical state infrastructure and services supporting vulnerable communities. Maryam led the introduction of cross-functional training and joint exercises between IT, facilities, and security teams, ensuring coordinated crisis response and enabling swift, datadriven action.
Maryam’s innovative thinking is grounded in her belief that the convergence of physical and cyber security must begin with people. She has placed cyber specialists within physical operations teams and created inclusive forums for cross-disciplinary learning, helping staff from both domains understand each other’s priorities and points of view. Her leadership in embedding “security first” cultures in both public sector and transport environments has empowered teams to collectively own and respond to risk. Initiatives like shared incident dashboards, converged risk management frameworks, and celebrating collaborative milestones have rewritten the playbook on organisational resilience.
Her cultural impact is tangible. Through her articles, including Bridging Cybersecurity and Biosecurity With Threat Modeling and Cybersecurity Operations and AI Carry Hidden Climate Costs (ISMG), Maryam has extended the cybersecurity conversation into new and underexplored domains. At events such as OT Security Melbourne and the Digital As Usual Roadshow, she has championed practical blueprints for converged SOCs, secure OT cloud environments, and risk frameworks that connect physical controls with digital risk. These contributions have established her as a sought-after thought leader and advisor, recognised for advancing both technical practice and strategic insight.
What sets Maryam Shoraka apart is not just her technical vision but her capacity for inclusive leadership, breaking down barriers and fostering a culture where cybersecurity and physical protection teams work side by side, transforming how Australia’s most vital assets and services are secured.

Much like I said on the day I was given the recognition of the award it was such an honour to be recognised alongside such incredibly inspiring, powerful and influential women and non-binary professionals. It was an honour to be recognised as a finalist, let alone the highly commended award I won. Thank you so much to yourself, Abigail and the Source2Create team and I look forward to coming back next year.
In the dim hum of an Australian mining control room, where every dial, datapoint, and whirring conveyor belt spells livelihood or disruption, Rhiana Cooke found her calling. She wasn’t just visiting as an OT Security Architect; she was there to blur the line between two worlds: the highly physical and the digital.

Rhiana’s days rarely look the same. One moment, she’s coordinating a segmented network rebuild for a hydro-power station, meticulously separating IT traffic from the critical OT systems that keep the turbines humming. The next, she’s donning a hard hat, walking a dusty site, explaining to tradespeople how a seemingly innocuous WiFi dongle could someday bring entire operations to a halt.
What makes Rhiana rare is not just her technical acumen, deploying solutions like Nozomi and Rapid7 to spot trouble before it erupts, but her ability to frame cyber risk as a tangible thing: a physical vulnerability as real as an unlocked door. In workshops lit by fluorescent tubes and table-top exercises crowded with network maps and coffee-
stained paperwork, she brings together security analysts and boiler operators, digital forensics teams and front-line managers, fostering a language everyone can understand. She knows true resilience is built not from isolated fixes but anchored in human connection and collaborative action.
Rhiana’s projects ripple across entire industries: a mining company’s three-site cyber overhaul, an airport’s improved network segmentation, hands-on training that takes cyber jargon and grounds it in operational reality. She’s responded to more than 200 system incidents, sometimes all in a single rolling week, always pairing technical rigour with empathy. Each deployment isn’t just a set of rules; it’s a roadmap for a safer, smarter system where IT and OT no longer work at cross purposes.
In her biggest moments of success, Rhiana looks not for personal glory, but for growth, in her mentees, the interns she’s guided into their first roles, and the women sitting in on OT luncheons feeling, finally, that they belong. She’s pushed vendors to update their offerings for the rough edges of industrial reality,
pioneered predictive maintenance tech by weaving security and operational value, and advocated for new ways to see and protect the invisible seams joining cyber and physical.
Rhiana’s secret is simple: she listens. To the operators who fear shutdowns, to the analysts wary of missing a threat, to the voices historically left outside the door. In every challenge, she sees an invitation to bring together the hands that keep Australia’s essential services alive.
For Rhiana Cooke, converged security isn’t the future. It’s now, and it’s in every person, every server, every circuit she has helped protect, proof that resilience is strongest when it’s built as a bridge, not a barrier.
With over 35 years of security vetting experience for the Federal Government, MPS People Security Risk Management has partnered with US based Clinical Psychologist and former Intelligence Officer, Dr Eric Shaw (Insider Risk Group, IRG) to develop innovative insider threat and security awareness training and consulting services – designed to help Australian businesses and government agencies strengthen their security posture and mitigate the risks posed by insiders
MPS People Security provides specialised security risk management and training services tailored for both government and private sector organisations Their offerings include insider threat management programs, personnel security risk assessments, and compliancealigned training courses covering insider threat awareness, cyber security, and general security practices MPS also delivers strategic consulting and digital tools to help organisations identify, assess, and mitigate insider risks, with services aligned to frameworks such as the Protective Security Policy Framework (PSPF) and the Security of Critical Infrastructure (SOCI) Act Their holistic approach combines behavioural analysis, investigative techniques, and practical training to strengthen organisational resilience and safeguard critical assets






Proudly Sponsored by



Asou Aminnezhad
Industry Lead/Security Architect at Microsoft
Yasaman Samadi
PhD Candidate from RMIT University
Asou Aminnezhad
Industry Lead/Security Architect from Microsoft
Farina Riaz
Researcher Scientist from CSIRO
Mandy Ho
Senior Consultant from Fujitsu

Mina Zaki
Donna Tsonis
Leonard Ng
Mandy Ho
Asou Aminnezhad
Farina Riaz
Yasaman Samadi


Asou Aminnezhad, Master of Security in Computing, published author, and winner of the Best Use of AI in Cybersecurity at the 2025 Australian Women in Security Awards, is recognised for her commitment to using AI responsibly and ethically. She has supported projects developing AI tools to address technology-facilitated domestic violence, embedding privacy, safety, and trust at the core. Her contributions demonstrate that AI innovation can and should be applied to protect vulnerable communities.
She also contributed to a clinical-grade AI platform for cancer detection, ensuring strong governance, regulatory compliance, and secure architectures were integrated from the outset by applying Microsoft Defender for Cloud AI, Content Safety APIs, and advanced monitoring practices.
Beyond her project work, Asou invests in people. She mentors professionals worldwide, offering hands-on guidance in securing multicloud and AI applications. She has helped review university curricula in Australia by advocating for modules on adversarial machine learning, hallucination risks, and evasion techniques. By embedding OWASP’s LLM Top 10 and Microsoft assessment frameworks into coursework, she has ensured students gain practical skills to defend AI systems in the real world. She also volunteers her time to deliver Learn and Lunch sessions for students across Australia, providing mentorship and real-world perspectives to inspire the next generation.
Committed to diversity and inclusion, Asou founded a peer-led network for underrepresented women

in cybersecurity living and working in Australia. This initiative builds both technical and leadership capacity while creating a supportive community that raises visibility and empowers future leaders in the industry.
Her technical expertise spans Well-Architected Framework security assessments, Zero Trust principles, and large-scale deployments of Microsoft AI security tools. She has delivered security assessments and executive workshops on multicloud and AI platforms, ensuring their safe and responsible adoption across healthcare, financial services, government, and education.
“Winning this award highlights the responsibility that comes with AI innovation. It is not only about efficiency or productivity. It is about protecting people, safeguarding privacy, and ensuring that the technology we build contributes to a safer, fairer world,” Asou says.
Asou is an Industry Lead and Security Architect at Microsoft whose work blends technical depth with community leadership, ensuring cloud and AI are secure, ethical, and inclusive by design.

We need your support to continue this important initiative into its 8th year.

JOIN US IN MELBOURNE FOR 2026
The 2026 Awards will be hosted in Melbourne. To ensure this initiative continues, we invite you to partner with us as a sponsor.
Your sponsorship will help us continue to celebrate and elevate the achievements of women in security across Australia.
Packages available from $6,000 to $50,000 Custom packages tailored to your organisation’s needs
To discuss how you can support and sponsor next year’s awards, please reach out to Aby at Aby@source2create.com.au .
We look forward to partnering with you to make the 2026 Australian Women in Security Awards our best yet.